Write short notes on a. Transaction Processing System (TPS)
Answers
Answer: A Transaction Processing System (TPS) is a type of information system that collects, stores, modifies and retrieves the data transactions of an enterprise. Rather than allowing the user to run arbitrary programs as time-sharing, transaction processing allows only predefined, structured transactions.
Three cycles: Transaction processing systems generally go through a five-stage cycle of 1) Data entry activities 2) Transaction processing activities 3) File and database processing 4) Document and report generation 5) Inquiry processing activities.
Explanation: hope this helps!
Related Questions
Keisha is trying to set the primary key on a table that already contains data. However, Microsoft Access is not allowing her to save the changes to the table design. Give two possible reasons for this.
Answers
Exclusive lock is required for saving design changes to Access objects. You do not currently have exclusive access to the database. If you make changes, you might not be able to save them later.
What is the use of Access?Microsoft Access is a database management system that combines the relational Access Database Engine with a graphical user interface and software development tools from Microsoft. It is part of the Microsoft 365 suite of applications, which is included in Professional and higher editions or can be purchased separately. Microsoft Access is a well-known information management tool that allows you to store various types of data for reporting, analysis, and reference. Microsoft Access allows you to manage data more efficiently and analyse large amounts of data.Access has been around for over 25 years and is the most widely used desktop, team, and small/medium sized business database product. Microsoft also released a new retail/perpetual licence version in late 2021, which will be fully supported until late 2026.To learn more about Access refer :
https://brainly.com/question/24643423
#SPJ1
If Anime Characters were real , Who Would Your Anime Wife Would Be (Tell Who And Why)
Answers
Answer:
Runa, because she’s like me I r l lol
Explanation:
PLS HELP!! TAKINT TEST
A _____ is a network geographically confined to one building.
A) VPN
B) MAN
C) LAN
D) WAN
Answers
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
which is NOT a basic human sense used in collecting collecting data?
Answers
Answer:
Explanation:This section outlines some of the key considerations that may arise during various steps in the data collection process. There is no requirement that these steps be followed or pursued in the order that they are written. The model presented is offered as a reference tool. How data is gathered and analyzed depends on many factors, including the context, the issue that needs to be monitored, the purpose of the data collection, and the nature and size of the organization.
PLEASE HELP I REALLY NEED IT ASAP
Select the correct answer. Layla and her team have installed a fire alarm system in an office. The alarm system connects to a wireless network, so it can be monitored using smartphones and computers connected to the same network. Which wireless technology does the fire alarm system use?
OA satellite
OB. Bluetooth
O C. infrared
OD. WI-FI
Answers
Answer:
wifi
Explanation:
if it's running on the same network that's wifi
Answer:
The correct answer is D. Wi-Fi.
Explanation:
I got it right on the Edmentum test.
On the AdvertisingCosts worksheet, create a Line chart of the data for the total spent on advertising each month from January through June. The primary horizontal axis should be the months of the year, and the Vertical (value) Axis should be the total spent on advertising each month.
Answers
I can provide you with general instructions on how to create a line chart in Microsoft Excel based on the data you have mentioned.
How to create the line chartTo create a line chart of the data for the total spent on advertising each month from January through June in Microsoft Excel, you can follow these steps:
Open Microsoft Excel and open the AdvertisingCosts worksheet.
Select the data range for the months and total spent on advertising from January through June.
Click on the "Insert" tab on the Excel ribbon.
Click on the "Line" chart type under the "Charts" section.
Select the chart subtype that you prefer from the drop-down menu. For example, you can choose a simple line chart or a chart with markers for each data point.
Your chart will be created, but it may need some adjustments to make it look better. For example, you may want to add a chart title, axis titles, and legend to the chart.
Click on the chart to activate the "Chart Tools" tab on the Excel ribbon.
Use the options on this tab to customize your chart as needed. For example, you can add a chart title by clicking on the "Chart Title" button, or you can change the axis titles by clicking on the "Axis Titles" button.
Once you have completed these steps, you should have a line chart of the data for the total spent on advertising each month from January through June. The primary horizontal axis should be the months of the year, and the Vertical (value) Axis should be the total spent on advertising each month.
Read more about spreadsheets here:
https://brainly.com/question/26919847
#SPJ1
Build an NFA that accepts strings over the digits 0-9 which do not contain 777 anywhere in the string.
Answers
To construct NFA that will accept strings over the digits 0-9 which do not contain the sequence "777" anywhere in the string we need the specific implementation of the NFA which will depend on the notation or tool used to represent NFAs, such as state diagrams or transition tables.
To build an NFA (Non-Deterministic Finite Automaton) that accepts strings over the digits 0-9 without containing the sequence "777" anywhere in the string, we can follow these steps:
Start by creating the initial state of the NFA.
Add transitions from the initial state to a set of states labeled with each digit from 0 to 9. These transitions represent the possibility of encountering any digit at the beginning of the string.
From each digit state, add transitions to the corresponding digit state for the next character in the string. This allows the NFA to read and accept any digit in the string.
Add transitions from each digit state to a separate state labeled "7" when encountering the digit 7. These transitions represent the possibility of encountering the first digit of the sequence "777".
From the "7" state, add transitions to another state labeled "77" when encountering another digit 7. This accounts for the second digit of the sequence "777".
From the "77" state, add transitions to a final state when encountering a third digit 7. This represents the completion of the sequence "777". The final state signifies that the string should not be accepted.
Finally, add transitions from all states to themselves for any other digit (0-6, 8, 9). This allows the NFA to continue reading the string without any constraints.
Ensure that the final state is non-accepting to reject strings that contain the sequence "777" anywhere in the string.
In conclusion, the constructed NFA will accept strings over the digits 0-9 that do not contain the sequence "777" anywhere in the string. The specific implementation of the NFA will depend on the notation or tool used to represent NFAs, such as state diagrams or transition tables.
For more such questions on NFA, click on:
https://brainly.com/question/30846815
#SPJ8
25 POINTS! PLEASE ANSWER! Karrie would like to draw attention to some short statements in her document. What is the best way to draw the readers deeper into the text? A. insert pull quotes B. change the text color C. use a large font D. highlight the text
Answers
Answer: I would say D. because it is highlighted text draws the attention of the reader
Explanation:
Answer:
D. highlight the text
Explanation:
if your were trying to grab a readers attention highlighting the text is the most noticeble.
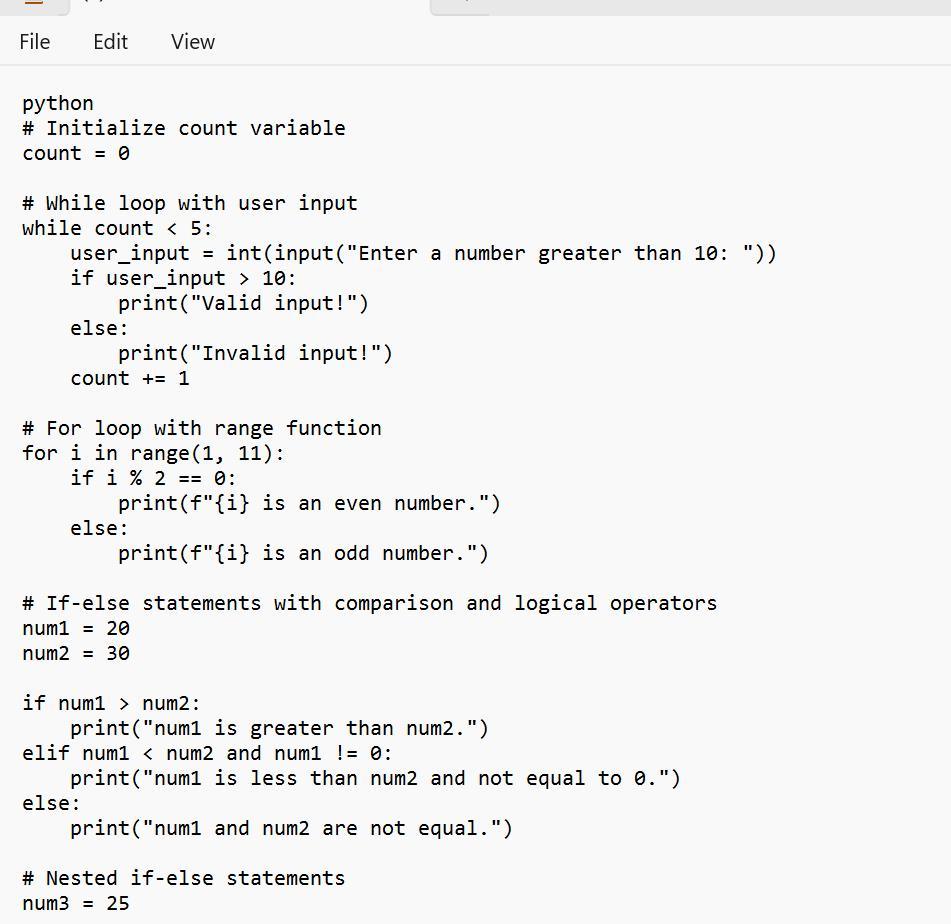
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

pe ethics trish is an unlicensed software engineer and has wondered why licensing of engineers is important.
Answers
The quality of life for every individual is directly and significantly impacted by engineering. As a result, engineers must provide services with integrity, objectivity, fairness, and equity, and they must be committed to preserving the health, safety, and welfare software of the general public.
Why is ethics significant for engineers?The two best examples I am aware of both deal with problems that almost every engineer encounters. The engineer is forced to decide between professional and financial success and the welfare of the community, the client, or the entire globe as a result of these ethical dilemmas.
What are an engineer's morals?The public's safety, health, and welfare must come first for engineers as they carry out their professional responsibilities. Engineers must only work in the designated locations.
To know more about software visit:-
https://brainly.com/question/1022352
#SPJ4
Write a program that INCLUDES A FUNCTION to calculate the Julian Day.
The function should take three inputs: year, month, and day.
The function should return the Julian Day.
In your main program, prompt the user to input the year, month, and day. Call the function to calculate the Julian Day, and print this value from your main program.
Example:
>python program6_2.py
Enter year month day
2011 2 16
Julian day for 2011 2 16 is 2455609.500000
Answers
The Phyton program that performs the above function is:
import math
def calculate_julian_day(year, month, day):
a = math.floor((14 - month) / 12)
y = year + 4800 - a
m = month + 12*a - 3
julian_day = day + math.floor((153*m + 2) / 5) + 365*y + math.floor(y/4) - math.floor(y/100) + math.floor(y/400) - 32045
julian_day += 0.5
return julian_day
year = int(input("Enter year: "))
month = int(input("Enter month: "))
day = int(input("Enter day: "))
julian_day = calculate_julian_day(year, month, day)
print(f"Julian day for {year} {month} {day} is {julian_day}")
How does the above program work?In this program, the calculate_julian_day() function takes three inputs (year, month, and day) and returns the Julian Day for the given date. The formula used in this function is known as the Julian Day Calculation, which is a widely used algorithm to calculate the Julian Day.
The input() function is used to prompt the user to input the year, month, and day values. These inputs are then passed as arguments to the calculate_julian_day() function, which calculates the Julian Day and returns it. Finally, the program prints the calculated Julian Day for the given date.
Learn more about programs:
https://brainly.com/question/11023419
#SPJ1
Upon returning from a year long working holiday, Alberta, the youngest of 4 sisters, announced her whirlwind marriage. Her 3 sisters, Carla, Paula, and Roberta,
were amazed by her husband's name.
• The 4 men are Albert, Carl, Paul, and Robert. Their last names are Albertson, Carlson, Paulson, and Robertson.
• No woman's husband has a first name that consists of her first name without the final "a"; no woman's last name consists of her first name without the final
"a" and with "son" on the end; and, no man's last name consists of his first name with "son" added at the end.
• Paul is not married to Roberta, and Robert is not married to Paula.
• No husband and wife have "bert" in both their first names, but there is a man who has "bert" in his first and last names.
Carl's last name is not Paulson.
Work out Alberta's husband's first and last name, as well as Carla's, Paula's, and Roberta's husbands' first and last name
Answers
The couples, considering the patterns in the problem, are listed as follows:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.What are the couples?We use the information from the bullet points to find the couples.
The first information is:
No woman's husband has a first name that consists of her first name without the final "a".
Hence:
Alberta is married to either Carl, Paul or Robert.Carla is married to either Albert, Paul or Robert.Paula is married to either Albert, Carl or Robert.Roberta is married to either Albert, Carl or Paul.The second information is:
Paul is not married to Roberta, and Robert is not married to Paula.
Hence:
Roberta is married to either Albert or Carl.Paula is married to either Albert or Carl.No husband and wife have "bert" in both their first names, hence:
Roberta is married to Carl.Paula is married to Albert.Alberta is married to Paul.Carla is married to Robert.No woman's last name consists of her first name without the final "a" and with "son" on the end, and no man's last name consists of his first name with "son" added at the end, hence:
Roberta and Carl are either Albertson or Paulson.Paula and Albert are either Carlson or Robertson.Alberta and Paul are either Carlson or Robertson.Carla and Robert are either Albertson or Paulson.There is a man who has "bert" in his first and last names, hence either of these two can be couples.
Carla and Robert Albertson.Paula and Albert Robertson.Carl's last name is not Paulson, hence a couple is:
Carla and Robert Paulson.
Then Carla and Robert are Paulson, and the couples are:
Carla and Robert Paulson.Paula and Albert Robertson.Alberta and Paul Carlson.Roberta and Carl Albertson.More can be learned about patterns at https://brainly.com/question/18941199
#SPJ1
g Palindrome counting. Write a Python program stored in a file q3.py to calculate the number of occurrences of palindrome words and palindrome numbers in a sentence. Your program is case-insensitive, meaning that uppercase and lowercase of the same word should be considered the same. The program should print the palindromes sorted alphanumerically with their number of occurrences. Numbers must be printed first, and words must be printed nex
Answers
Answer:
The program is as follows:
sentence = input("Sentence: ")
numbers = []; words = []
for word in sentence.split():
if word.lower() == word[::-1].lower():
if word.isdigit() == False:
words.append(word)
else:
numbers.append(int(word))
words.sort(); numbers.sort()
print(numbers); print(words)
Explanation:
This gets input for sentence
sentence = input("Sentence: ")
This initializes two lists; one for numbers, the other for word palindromes
numbers = []; words = []
This iterates through each word of the sentence
for word in sentence.split():
This checks for palindromes
if word.lower() == word[::-1].lower():
If the current element is palindrome;
All word palindromes are added to word palindrome lists
if word.isdigit() == False:
words.append(word)
All number palindromes are added to number palindrome lists
else:
numbers.append(int(word))
This sorts both lists
words.sort(); numbers.sort()
This prints the sorted lists
print(numbers); print(words)
Write a program that rolls two dice until the user gets snake eyes. You should use a loop and a half to do this. Each round you should roll two dice (Hint: use the randint function!), and print out their values. If the values on both dice are 1, then it is called snake eyes, and you should break out of the loop. You should also use a variable to keep track of how many rolls it takes to get snake eyes.
Sample Run:
Rolled: 6 5
Rolled: 5 2
Rolled: 3 6
Rolled: 6 2
Rolled: 1 2
Rolled: 5 3
Rolled: 1 4
Rolled: 1 1
It took you 8 rolls to get snake eyes.
I have most of the code but when it prints it say you rolled 0 times every time.
import random
# Enter your code here
num_rolls = 0
import random
# Enter your code here
while True:
roll_one = random.randint(1,6)
roll_two = random.randint(1,6)
print ("Rolled: " +str(roll_one) +"," + str(roll_two))
if (roll_one == 1 and roll_two == 1):
print ("it took you " + str(num_rolls) + " rolls")
break
output:
Rolled: 3,5
Rolled: 6,4
Rolled: 2,4
Rolled: 3,6
Rolled: 5,2
Rolled: 1,1
it took you 0 rolls
suppose to say:
It took you (however many rolls) not 0
Answers
import random
num_rolls = 0
while True:
r1 = random.randint(1, 6)
r2 = random.randint(1, 6)
print("Rolled: " + str(r1) + "," + str(r2))
num_rolls += 1
if r1 == r2 == 1:
break
print("It took you "+str(num_rolls)+" rolls")
I added the working code. You don't appear to be adding to num_rolls at all. I wrote my code in python 3.8. I hope this helps.
The program uses loops and conditional statements.
Loops perform repetitive operations, while conditional statements are statements used to make decisions
The program in Python where comments are used to explain each line is as follows:
#This imports the random module
import random
#This initializes the number of rolls to 0
num_rolls = 0
#The following loop is repeated until both rolls are 1
while True:
#This simulates roll 1
roll_one = random.randint(1,6)
#This simulates roll 2
roll_two = random.randint(1,6)
#This prints the outcome of each roll
print ("Rolled: " +str(roll_one) +"," + str(roll_two))
#This counts the number of rolls
num_rolls+=1
#When both rolls are the 1
if (roll_one == 1 and roll_two == 1):
#This exits the loop
break
#This prints the number of rolls
print ("it took you " + str(num_rolls) + " rolls")
Read more about similar programs at:
https://brainly.com/question/14912735
When should students in a study session use flash cards to quiz one another?
while reviewing
while drilling
while discussing
while preparing`
Answers
When drilling, students in a study session use flashcards to quiz one another. thus, Option B is the correct statement.
What do you mean by drill and practice?
The term drill and practice can be described as a way of practice characterized by systematic repetition of concepts, examples, and exercise problems.
Drill and exercise is a disciplined and repetitious exercise, used as an average of coaching and perfecting an ability or procedure.
Thus, When drilling, students in a study session use flashcards to quiz one another. Option B is the correct statement.
Learn more about drill and practice:
https://brainly.com/question/27587324
#SPJ1
PLEASE HELP ME ANSWER THIS QUESTION. I REALLY REALLY NEED IT.
. According to IEEE, what is software engineering? (A) The study of
approaches (B) The development of software product using scientific
principles, methods, and procedures (C) The application of engineering
to software (D) All of the above
Answers
IEEE (Institute of Electrical and Electronics Engineers) describes software engineering as:
(D) All of the above.
Software engineering encompasses the study of approaches, and the development of software products using scientific principles, methods, and procedures. It also encompasses the application of engineering principles to software. It is a multidisciplinary field that combines technical knowledge, problem-solving skills, and systematic processes to design, develop, and maintain software systems efficiently and effectively.
What is the proper format of a speaker label (Speaker)?
Answers
The proper format of a speaker label in written transcripts or dialogue scripts is to include the speaker's name or identifier in all caps, followed by a colon and a space before the spoken words.
What is the speaker label (Speaker)?For example:
SPEAKER 1: Hello, how are you?
SPEAKER 2: I'm good, thank you. How about you?
If the speaker has a specific title or role, it can be included as part of the identifier. For example:
MODERATOR: Welcome to today's panel discussion. Our first speaker is Dr. Jane Smith.
DR. JANE SMITH: Thank you for having me. I'm excited to be here.
The use of speaker labels helps to clarify who is speaking in a conversation, especially when there are multiple participants or if the dialogue is presented in written form.
Learn more about speaker label from
https://brainly.com/question/29583504
#SPJ1
HI can someone help me write a code.
Products.csv contains the below data.
product,color,price
suit,black,250
suit,gray,275
shoes,brown,75
shoes,blue,68
shoes,tan,65
Write a function that creates a list of dictionaries from the file; each dictionary includes a product
(one line of data). For example, the dictionary for the first data line would be:
{'product': 'suit', 'color': 'black', 'price': '250'}
Print the list of dictionaries. Use “products.csv” included with this assignment
Answers
Using the knowledge in computational language in python it is possible to write a code that write a function that creates a list of dictionaries from the file; each dictionary includes a product.
Writting the code:import pandas
import json
def listOfDictFromCSV(filename):
# reading the CSV file
# csvFile is a data frame returned by read_csv() method of pandas
csvFile = pandas.read_csv(filename)
#Column or Field Names
#['product','color','price']
fieldNames = []
#columns return the column names in first row of the csvFile
for column in csvFile.columns:
fieldNames.append(column)
#Open the output file with given name in write mode
output_file = open('products.txt','w')
#number of columns in the csvFile
numberOfColumns = len(csvFile.columns)
#number of actual data rows in the csvFile
numberOfRows = len(csvFile)
#List of dictionaries which is required to print in output file
listOfDict = []
#Iterate over each row
for index in range(numberOfRows):
#Declare an empty dictionary
dict = {}
#Iterate first two elements ,will iterate last element outside this for loop because it's value is of numpy INT64 type which needs to converted into python 'int' type
for rowElement in range(numberOfColumns-1):
#product and color keys and their corresponding values will be added in the dict
dict[fieldNames[rowElement]] = csvFile.iloc[index,rowElement]
#price will be converted to python 'int' type and then added to dictionary
dict[fieldNames[numberOfColumns-1]] = int(csvFile.iloc[index,numberOfColumns-1])
#Updated dictionary with data of one row as key,value pairs is appended to the final list
listOfDict.append(dict)
#Just print the list as it is to show in the terminal what will be printed in the output file line by line
print(listOfDict)
#Iterate the list of dictionaries and print line by line after converting dictionary/json type to string using json.dumps()
for dictElement in listOfDict:
output_file.write(json.dumps(dictElement))
output_file.write('\n')
listOfDictFromCSV('Products.csv')
See more about python at brainly.com/question/19705654
#SPJ1

By watching the expression Mynum=4 * mynum + c from a programming language, what can we say about this language?
This is not an imperative programming language
This is a case sensitive language
This is not a case sensitive language
We can not determine if this language is case-sensitive or case-insensitive
Answers
Answer:
We can not determine if this language is case-sensitive or case-insensitive
Explanation:
It is unclear wether Mynum and mynum are intended to be different variables or the same variable. Both would work.
Having said that, mixing case like this is always a bad design.
Answer:
we do not determine If this language is case
Which the following programs is considered an all in one program for graphic design 
Answers
The following applications are regarded as comprehensive graphic design programs.
For the creation of credits or opening sequences, film studios employ graphic designers.
For the creation of their logos, large corporations hire graphic designers.
Newspapers and magazines employ designers to format their articles so that readers will be interested.
A graphic design application is which of the following?The final stage frequently involves the use of Adobe Photoshop, a raster-based program for image editing, and Adobe Illustrator, a vector-based program for drawing. CorelDraw is employed by some designers worldwide. The Corel Corporation created and sells CorelDraw, a vector graphics editor.
To know more about graphic design visit:
https://brainly.com/question/10678312
#SPJ9
Which of the following activities can users do on a properly configured file storage server?
Answers
The activities that users do on a properly configured file storage server is option B: Modify shared files
What is the modifying of files?Clients can adjust shared records, get to a shared registry, and share records on a legitimately arranged record capacity server. Be that as it may, allowing a advanced certificate of believe isn't a normal action that clients would perform on a record capacity server.
Therefore, This action is more often than not performed by a certificate specialist or a trusted third-party substance that confirms the personality of a client or organization asking the certificate.
Learn more about file storage server from
https://brainly.com/question/4277691
#SPJ1
Which of the following activities can users do on a properly configured file storage server?
1 point
Grant a digital certificate of trust
Modify shared files
Access a shared directory
Share files
Sarah needs to send an email with important documents to her client. Which of the following protocols ensures that the email is secure?
a. S/MIME
b. SSH
c. SHTTP
d. SSL
Answers
If Sarah needs to send an email with important documents to her client, then S/MIME protocols ensures that the email is secure.
What is an email?Email, also known as e-mail or just "e mail," is a shortened term for electronic mail and refers to data that is stored on a computer and transferred between users via a network.
To put it simply, an email is a message with a possible attachment of text, files, images, or other media that is sent over a network to a specific person or group of people.
Ray Tomlinson sent the very first email in 1971. Tomlinson sent the email to himself as a test message with the subject line "something like QWERTYUIOP." The email was sent to himself, but it was still sent over ARPANET.
Learn more about email
https://brainly.com/question/24688558
#SPJ1
Identify two stages of processing instructions
Answers
Answer:
1. Fetch instruction from memory.
2. Decode the instruction.
define hexadecimal number system
Answers
Answer:
a positional numeral system that represents numbers using a radix (base) of 16
Which of the following is the correct sequence of the DIIRE
value chain?
Answers
A lot of events often takes plain in value chain. The correct sequence of events in the value chain are competitive strategy; value chain; business process and lastly the information systems.
A value chain is simply known as a business model that shows all the aspects or ranges of activities that is often needed to make a product or service.
Firms often conducts an indepth value-chain analysis through the act of evaluating the detailed procedures involved in each step of its business.
Learn more about Value chain from
https://brainly.com/question/1380316
Which of the following statements best describes the future of mass media? Responses It is likely that we will always need mass media, because social media cannot last. It is likely that we will always need mass media, because social media cannot last. We no longer need mass media at this point in our culture because of our use of social media. We no longer need mass media at this point in our culture because of our use of social media. Although we still need it now, we will one day no longer need mass media because of social media. Although we still need it now, we will one day no longer need mass media because of social media. We will always need mass media, but because of social media, we will rely on it less.
Answers
The statement "We will always need mass media, but because of social media,we will rely on it less" best describes the future of mass media.
How is this so?While social media has become a prominent platform for communication and information sharing,mass media continues to play a crucial role in delivering news, entertainment, and other forms of content to a wide audience.
However, the rise of social media may lead to a reduced reliance on mass media as peoplehave more direct access to information and content through online platforms.
Learn more about mass media at:
https://brainly.com/question/17658837
#SPJ1
If you had to tell that employee why it was not a good idea to send that e-mail, which of the following would you mention? (select all that apply)
The language was not professional.
The e-mail was not work-related.
The e-mail did not include an appropriate greeting.
The e-mail shows that the employee has been surfing the Internet instead of working.
the answers are A,B, and D. thats the only way I can give the answers on brainly.
Answers
The options that need to be mentioned are:
The language was not professional.The e-mail was not work-related.The e-mail shows that the employee has been surfing the Internet instead of working.Check more about email below.
What is non work email?In Email Management Guidelines, the term non-work related emails are known to be “those that are not related to either private or government business.
Note that if one is sent this email during working hours, one is obligated to live it and not open it.
Hence, The options that need to be mentioned are:
The language was not professional.The e-mail was not work-related.The e-mail shows that the employee has been surfing the Internet instead of working.Learn more about email from
https://brainly.com/question/24688558
#SPJ1
How does the habit win-win, along with the concepts of inclusivity and diversity help to grow an organization and help you increase your growth mindset
Answers
Answer: The key to success is to believe. Will power is everything.
Explanation: Most of the time, a person reaches his mental capacity before his physical limit. Therefore, it is important to train the mind and develop a growth mindset and in a way, always be "hungry and unsatisfied." To be cold turkey, you have to feel uncomfortable in what you are doing. If you are comfortable in your sphere, you are not learning or growing.
Need help with Exercise 7


Answers
The method signature in Java syntax based on the information will be:
public boolean has13Digits(String inputString) {
}
How to explain the informationIt should be noted that to design the method that takes a String and returns true if the String has 13 digits and false otherwise, we can follow the following steps:
Declare a method with a return type of boolean, which takes a String parameter.
Check if the length of the input String is exactly 13.
If the length is 13, check if all characters in the String are digits. If yes, return true; otherwise, return false.
Lean more about java on
https://brainly.com/question/25458754
#SPJ1