which of the following are common options for backing up mobile device data? group of answer choices to the cloud to a desktop system to magnetic tape snapshots
Answers
The common options for backing up mobile device data include backing up data to the cloud and to a desktop system. Options A and B are answers.
Backing up data to the cloud involves storing data on remote servers that are accessible over the internet. This option provides a convenient and secure way to backup data, as users can access their data from any device with an internet connection. Backing up data to a desktop system involves transferring data from a mobile device to a computer. This option can be done either through a USB cable or over a wireless network. This method allows users to have more control over their data, as it is stored locally on their computer. Options A and B are answers.
You can learn more about Backing up data at
https://brainly.com/question/29453587
#SPJ11
Related Questions
What is a lean operating system installed on the Windoows 10/8/7 setup DVD and on the Windows volume that can be used to troubleshoot problems when Windows refuses to start
Answers
The lean operating system installed on the Windows 10/8/7 setup DVD and on the Windows volume that can be used to troubleshoot problems when Windows refuses to start is called "Windows Recovery Environment" or "Windows RE."
Windows RE is a minimalistic version of the Windows operating system that provides various tools and options to diagnose and repair startup issues. It is typically accessed by booting from the Windows installation DVD or a dedicated recovery partition on the Windows volume.Windows RE includes features such as: Repair: Automatically detects and attempts to fix common startup problems.System Restore: Allows you to restore the system to a previous working state.Command Prompt: Provides a command-line interface to execute various commands for troubleshooting and repair.Windows Memory Diagnostic: Allows you to test your computer's memory for errors.Automatic Repair: Attempts to automatically repair issues preventing Windows from startingThese tools and options within Windows RE help diagnose and fix problems with the operating system, allowing users to restore functionality or perform repair tasks without requiring a fully functional Windows environment.
learn more about Environment here :
https://brainly.com/question/5511643
#SPJ11
The Help Link is being discussed. Technician A says that the Help Guide in Service Lane is specific to Service Lane.
Technician B says that you can switch between Service Lane and TIS help pages within the Help Guide. Who is correct? 1. Technician A only 2. Technician B only 3 Both Technicians A and B 4. Neither Technician A nor B
Answers
The Help Link is being discussed. According to the given option only A is true- Technician A only.
What exactly does a technician do?A technician is a person who installs, examines, maintains, alters, or performs mechanical or diagnostic testing on complex systems. IT technicians, repairers, automotive technicians, lab workers, dental technicians, and pharmacy technicians are among the several categories of technicians.
What is required to be a technician?A technician is a person whose employment involves performing skilled practical work, such as in a lab, using scientific equipment. a technician at a lab counting noun A technician is a person who excels at the intricate technical components of a task. It's challenging, but worthwhile. Even though it could take some time, there is nothing better than helping someone out with a situation they are having.
To learn more about Technician visit:
https://brainly.com/question/29803506
#SPJ4
What size is 16:9 in pixels?
Answers
The size of 16:9 in pixels is 1920x1080.
The size of a 16:9 aspect ratio in pixels will depend on the specific resolution of the display or screen. A 16:9 aspect ratio means that the width of the display is 16 units while the height is 9 units. Some common resolutions that use the 16:9 aspect ratio are:
- 1280 x 720 pixels (also known as 720p)
- 1920 x 1080 pixels (also known as 1080p or Full HD)
- 2560 x 1440 pixels (also known as 1440p or Quad HD)
- 3840 x 2160 pixels (also known as 2160p or 4K)
So, the size of a 16:9 aspect ratio in pixels will vary depending on the resolution. For example, a 1080p display will have a size of 1920 x 1080 pixels, while a 4K display will have a size of 3840 x 2160 pixels.
Learn more about pixels:
https://brainly.com/question/2894159
#SPJ11
100 POINTS. DO NOT SPAM. OR I WILL REPORT.
Write about various image degradation function.(minimum 5)
Answers
Answer:
Explanation:
In digital image processing, degradation is a process of introducing defects to the image. Understanding the degradation function will allow restoration of the original image.
There are many different causes for image degradation such as motion blur, digital noise and lens off-focus. In cases like motion blur, it is possible to come up with an very good estimate of the actual blurring function and "undo" the blur to restore the original image. For digital noise, a statistical model can be set up to compensate for the degradation it caused. Similarly lens focus can be compensate by an optical model if the mis-focus is known.
The above are three degradations that I could find. A lot more information can be found about restoration functions. If you search for image degradation online, you will find a discussion on Quora and an interesting introduction from Rice University. Good luck!
Answer:
Explanation:
image degradation function helps 2 understand how a digital image has degraded n how 2 restore it
to come up w the function, start by observing the degraded image. look 4 areas w less degradation n use them as reference of the original
if equipment used 2 take the degraded image is available, try finding the exact conditions which produce the same degradation. dat will provide clues for restoration
if the degraded image can be scanned, it can be manipulated digitally w various pre-programmed functions n look 4 any improvement
one of the above should help in restoring the degraded image
how will you be notified of an account suspension (aside from the merchant center diagnostic interface)?
Answers
Your account has been suspended, and you'll get an email telling you about it along with all the pertinent details regarding the problems with the data quality and what to do next. The Home and Diagnostics pages of your Merchant Center account will display your suspension status.
How can a merchant center be verified?manual actions
Log in to your account with Merchant Center.Click the tools icon in the navigation menu.Choose Business information from the Tools menu.On the Website tab, click.Then click Next.To verify the website, select one of the following alternatives.By enabling direct communication between apps and the Merchant Center platform, the Content API for Shopping greatly improves the effectiveness of managing complicated or big Merchant Center accounts.
Powerful technologies are used by eCheck payment processors to validate an eCheck's identity, bank account number, status, and availability of cash. Electronic check verification lowers the risk of check fraud for businesses.
To learn more about Diagnostics refer to:
https://brainly.com/question/27807893
#SPJ4
Hello guys where's bios chip in this motherboard help me

Answers
Answer:
Explanation:
Hey there!
Do you see the lower corner?
on the right beside the anti surge thingy
its rectangular, its also black from the center its here
computer scientists are great at reading data and crunching numbers to draw conclusions. we live in a data-rich world that offers more information than has ever been present before. companies often do not hire computer scientists on their own and will often group the computer science experts with team members from other fields. which of the following is the best reason for a computer scientist to work with someone outside their field? elimination tool select one answer a create optimal algorithms. b explain the meanings of headers on data. c write documentation. d collaborate to draft the main goals of a project.
Answers
Given that computer scientists are great at reading data and crunching numbers to draw conclusions the best reason for a computer scientist to work with someone outside their field is: " collaborate to draft the main goals of a project." (Option D)
Why are the goals of a project essential to a computer scientist?Before the inception of any project, it is important to establish the goal. This is not different with IT-related projects. This is the reason why computer scientists must collaborate with professionals that are outside of their field.
Setting goals is an important aspect of planning for personal transformation and achieving project objectives. Well-written objectives motivate, concentrate attention, and provide as a foundation for controlling performance and assessing improvement.
The first are project result objectives. These are the task statements that must be fulfilled in order for the project to be regarded "complete." The second type of project management performance objective is high-level project management performance goals that relate to the overall performance of the team and project manager.
Learn more bout computer scientists:
https://brainly.com/question/27127548
#SPJ1
Sayid listed the steps for adding a recurring event in Outlook.
1: Click on Calendar in the Navigation Pane.
2: On the Home tab in the New group of the Ribbon, click New Appointment
3: Click the box for “All day event” and enter the subject.
4: Enter the details in the Recurrence dialog box and click OK.
5: Click Save & Close.
Answers
Sayid's error in setting up reminder for recurrent activities in Microsoft Outlook is that he missed the next step after Step 3 which is " after step 3, click the recurrence button." (Option C) See the attached for the full question.
What is a recurrent event in Outlook?In Microsoft Outlook, the recurrent button serves the function of enabling uses set up reminders that are recurrent hence increasing their efficiency and reducing the possibility of forgetting such an important event.
Thus, the correct steps for Sayid to take are:
1: Click on Calendar in the Navigation Pane.
2: On the Home tab in the New group of the Ribbon, click New Appointment
3: Click the box for “All day event” and enter the subject.
4: Click the recurrence button
4: Enter the details in the Recurrence dialog box and click OK.
5: Click Save & Close.
Learn more about outlook at:
https://brainly.com/question/1538272
#SPJ1
What order does a computer work in?
*
A) Output, Processing, Storage, Input
B) Processing, Output, Storage, Input
C) Input, Storage, Processing, Output
D) Output, Input, Storage, Processing
Answers
Answer:
C
Explanation:
Input, Storage, Processing, Output
Describe an efficient algorithm that, given a set {x1, x2, . . . , xn} of n points on the real line, determines the smallest set of closed unit-length intervals that contains all of the given points. Prove that your algorithm is correct. Note that the word "efficient" means that the complexity is no worse than polynomial-time.
Answers
The algorithm efficiently finds the smallest set of closed unit-length intervals to cover all given points. Its correctness is proven by ensuring coverage of all points while minimizing interval size.
The algorithm presented efficiently finds the smallest set of closed unit-length intervals to encompass all given points.
By sorting the points, selecting the leftmost uncovered point, and iteratively adding intervals, the algorithm ensures coverage of all points. The proof of correctness demonstrates that the algorithm guarantees a solution that covers all points and is no larger than any other optimal set of intervals.
This algorithm provides a reliable and efficient method for solving the problem of finding the smallest set of closed unit-length intervals that contain a given set of points on the real line.
Learn more about The algorithm: brainly.com/question/13902805
#SPJ11
What are the most common malware types? How do you safeguard computer systems against malware? Why do you need to train users of computer systems to be vigilant about malware? What are some of the most recent malware attacks that you read or herd about in the news media?
Answers
Common Malware Types:
· Viruses
· Worms
· Trojans
· Ransomware
· Spyware
· Adware
Protections From Malware:
· Firewall Software
· Anti-Virus Software
A compile-time error occurs because obj1 is declared as type C1 but instantiated as type C2. A compile-time error occurs because obj1 is declared as type C1 but instantiated as type C2. A A runtime error occurs because method m1 does not appear in C2. A runtime error occurs because method m1 does not appear in C2. B Method m1 is not executed because it does not appear in C2. Method m1 is not executed because it does not appear in C2. C Method m2 is executed from the subclass instead of the superclass because obj1 is instantiated as a C2 object. Method m2 is executed from the subclass instead of the superclass because obj1 is instantiated as a C2 object. D Method m2 is executed twice (once in the subclass and once in the superclass) because it appears in both classes
Answers
The code segment doesn't produce the intended output (AB) because "method m1" was not executed since it does not appear in C2.
What is a method?In computer programming, a method can be defined as sets of instruction or a block of executable codes that are used to break down a complex problem into small but manageable fragments.
Thus, methods are typically used by programmers to break down a complex problem into simple, small and manageable fragments. In this scenario, the code segment doesn't produce the intended output (AB) because "method m1" was not executed since it does not appear in C2.
Read more on methods here: brainly.com/question/25619349
PLS HELP ILL GIVE BRAINLY) enter the answer) desktop publishing software enables users to create products for print or __________ distribution
Answers
Answer:
Electronic
Explanation:
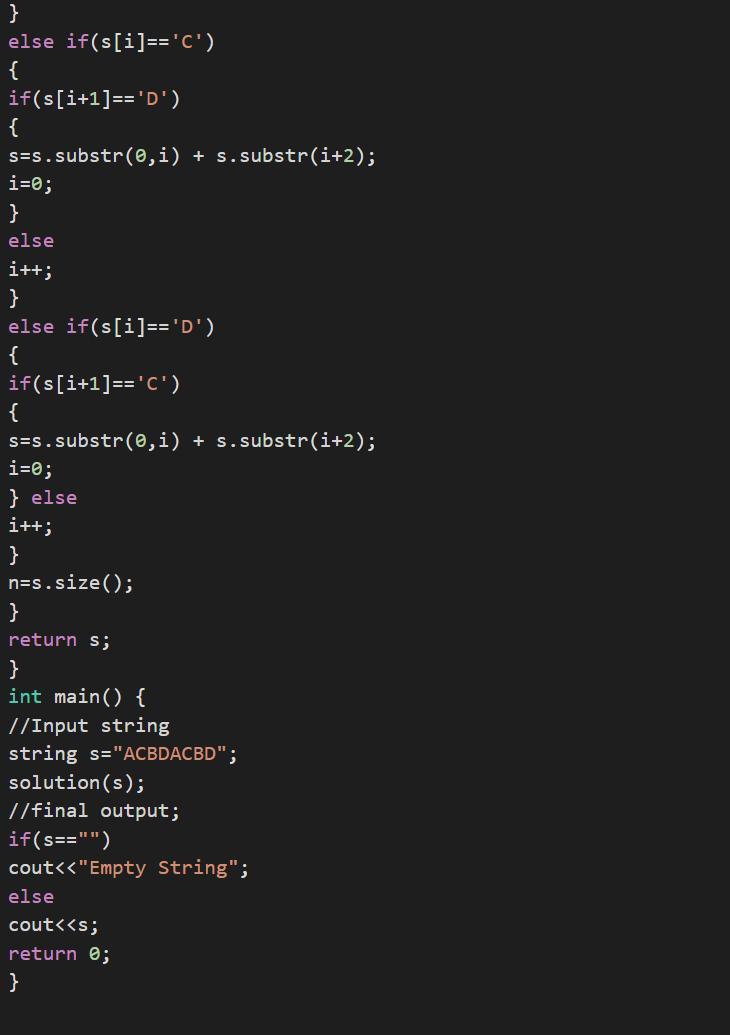
A string consisting of the letters a, b, c and d is given. the string can be transformed either by removing a letter a together with an adjacent letter b or by removing a letter c together with an adjacent letter d. write a function so that the given string s consisting of n characters returns any string
Answers
Using the knowledge in computational language in C++ it is possible to write a code that write a function so that the given string s consisting of n characters returns any string
Writting in C++ code:#include <iostream>
#include <string>
using namespace std;
string solution(string &s)
{
//length of string
int n=s.size();
//index of string
int i=0;
while(i<n-1)
{
if(s[i]=='A')
{
if(s[i+1]=='B')
{
s=s.substr(0,i) + s.substr(i+2); i=0;
}
else
i++;
}
else if(s[i]=='B')
{
if(s[i+1]=='A')
{
s=s.substr(0,i) + s.substr(i+2); i=0;
}
else
i++;
}
else if(s[i]=='C')
{
if(s[i+1]=='D')
{
s=s.substr(0,i) + s.substr(i+2);
i=0;
}
else
i++;
}
else if(s[i]=='D')
{
if(s[i+1]=='C')
{
s=s.substr(0,i) + s.substr(i+2);
i=0;
} else
i++;
}
n=s.size();
}
return s;
}
int main() {
//Input string
string s="ACBDACBD";
solution(s);
//final output;
if(s=="")
cout<<"Empty String";
else
cout<<s;
return 0;
}
See more about C++ code at brainly.com/question/19705654
#SPJ1

What would happen if you fake a credit card number online on a website.
My 13 year old friend did that months ago and now he got a message saying his “chase account was locked due to suspicious activities”
I’m only asking because he’s freaking out
Answers
help
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van" how many binary decision variables would we need to code this data into a usable format?
Answers
If we are looking at the predictor "car type," which can take on the values "sedan" "coupe" "truck" "suv" "van", we would need 4 binary decision variables to code this data into a usable format.
A binary decision variable is a variable with only two possible values: 1 or 0. The variable is referred to as a binary variable, a binary indicator, or a 0-1 variable .The binary variable is used to answer yes/no questions. the binary variable " the binary variable is set to 0.To code the car type data into a usable format, we can use the binary decision variables.
We can use four binary variables to code the data into a usable format. We can use one variable for each category of car type. The values of the binary variables for the different categories are as follows:Sedan - 1000Coupe - 0100Truck - 0010SUV - 0001Using this format, if a car is a sedan, its binary decision variable would be set to 1000. If a car is a coupe, its binary decision variable would be set to 0100, and so on.
To know more about sedan visit:
https://brainly.com/question/24286177
SPJ11
Which of the following terms defines a small, single-user computer used in homes and businesses?
Personal computer
Work station
Mini computer
Supercomputer
Answers
Answer:
Mini Computer
Explanation:
Person Computer. small, single-user computer; used in homes and businesses; based on a microprocessor. Microprocessor. chip which is the master control circuit of a computer. Minicomputer.
Pa brainliest po thank you
The correct option is A. Personal computer is defined as a small, single-user computer used in homes and businesses.
What is a personal computer?A personal computer (PC) is a multifunctional microcomputer that can be used for a variety of tasks and is affordable enough for home use. Instead of being operated by a computer specialist or technician, personal computers are designed to be used directly by end users.
Personal computer (PC): compact, single-user computer with a microprocessor that is used in homes and businesses.
A personal computer (PC) is a compact computer made for solitary usage. A single-chip microprocessor serves as the central processing unit in a PC or microcomputer (CPU).
The right answer is A. Small, single-user computers used in homes and companies are referred to as personal computers.
Learn more about personal computers here:
https://brainly.com/question/14406548
#SPJ2
a language translator is a ???
Answers
Answer:
Explanation:
speech program
Answer:
hi
Explanation:
language translator is a program which is used to translate instructions that are written in the source code to object code i.e. from high-level language or assembly language into machine language.
hope it helps
have a nice day
The theoretical limit on the number of constraints that can be handled by a linear programming problem is:
3.
2.
4.
unlimited.
Answers
Option 4 is correct. The maximum number of restrictions that a linear programming problem can theoretically handle is limitless.
The vertices of the feasibility zone are where the objective function's maximum (or minimum) value always occurs, according to the Fundamental Theorem of Linear Programming. As a result, we shall list each of the feasibility region's vertices (corner points). Constraints refer to the linear equations, inequalities, or restrictions on the variables in a linear programming problem. The terms "x 0" and "y 0" are referred to as non-negative restrictions. The set of inequalities (1) to (4) in the example above serve as constraints.
Learn more about constraints here-
https://brainly.com/question/28186654
#SPJ4
Computer science student Jones has been assigned a project on how to set up sniffer. What must he keep in mind as part of the process
Answers
Setting up a sniffer requires certain considerations to be taken into account, such as ensuring that the sniffer is being used legally, selecting the appropriate hardware and software for the task, and configuring the sniffer correctly to capture and analyze network traffic.
The use of a sniffer or packet analyzer can be subject to legal restrictions and ethical considerations, as capturing and analyzing network traffic may violate privacy laws or ethical norms. As such, Jones needs to ensure that the use of the sniffer is authorized and that he is aware of any legal or ethical considerations that may apply.
When selecting hardware and software for the sniffer, Jones should consider factors such as the intended use of the sniffer, the complexity of the network, and the level of analysis required. Different sniffer tools may be better suited for different tasks, such as capturing traffic on wired or wireless networks, analyzing specific protocols, or detecting security threats.
Once the hardware and software have been selected, Jones needs to configure the sniffer correctly to ensure that it is capturing the desired traffic and providing accurate results. This may involve setting filters to capture specific types of traffic, configuring the interface to ensure that packets are being captured properly, and adjusting the settings to optimize the performance of the sniffer.
To learn more about Sniffer, visit:
https://brainly.com/question/29872178
#SPJ11
evaluate:15+5*(8-5)/14
Answers
Answer:
225/14
Explanation:
By BODMAS
15 + 5 × (8-5) ÷ 14
= 15 + 5 × 3 ÷ 14
= 15 + 5 × 3/14
= 15 + 15/14
= 210/14 + 15/14
= (210 + 15)/14
= 225/14
Interference is a common problem with ———— devices. Select all that apply.A) BluetoothB) USBC) HDMID) Wireless
Answers
With Bluetooth and wireless gadgets, interference is a prevalent issue.
What hardware requires no device drivers?Plug-and-play gadgets include keyboards, mouse, and monitors. The OS of the computer recognizes and installs plug-and-play device drivers automatically, thus they typically are generic and don't need to be installed manually.
Which of the following pointing devices for computers is most frequently used?The mouse is the most typical pointing device used with desktop computers. The touchpad is the most frequent pointing device used with laptop computers. Last but not least, using your finger on a touch screen is the most popular pointing mechanism for smartphones and tablets.
To know more about wireless visit :-
https://brainly.com/question/14921244
#SPJ4
In addition to the cost of legal services and the cost of treatment, which of the following are considered direct costs for workplace accidents?
Select the best option.
Answers
Answer:
what are the options for the question
Answer:
Hospital costs
Explanation:
I really don't know who to explain this.. I just pressed it and got it right ^^'
Which application development model approaches software development as a continuous, changing process with never-ending versions, bug fixes, and enhancements?
Answers
A software application development model that typically approaches software development as a continuous, changing process that has bug fixes, never-ending versions, and enhancements is Agile.
What is SDLC?SDLC is an abbreviation for software development life cycle and it can be defined as a strategic methodology that defines the key steps, phases, or stages for the design, development and implementation of high quality software programs.
What is Agile software development?In Agile software development, the software development team are generally more focused on the continuous production of working (active) software programs with less effort on documentation while creating bug fixes and never-ending versions.
In this context, we can infer and logically deduce that a software application development model that typically approaches software development as a continuous, changing process that has bug fixes, never-ending versions, and enhancements is Agile.
Read more on software development here: brainly.com/question/26324021
#SPJ1
Which statement is true?
A. A flowchart uses comments that can be kept as a permanent part of a program.
B. A comment line begins with #.
C. Pseudocode uses shapes such as rectangles and diamonds to plan a program.
D. You only use comments for pseudocode.
Answers
Answer:
B just took the test.
Explanation:
Answer:
comment line begin with #
Explanation:
The cost of repairing a new desk's leg--broken accidentally by an employee moving the desk into place--is expensed immediately.
Answers
The cost of repairing a new desk's broken leg, caused by an employee moving the desk into place, is expensed immediately. This ensures that expenses are matched with the period in which they occur, following the accounting principle of matching.
The cost of repairing a new desk's leg, which was broken accidentally by an employee while moving the desk into place, is expensed immediately. This means that the cost of the repair will be recognized as an expense on the company's financial statements in the period in which it occurred.
Expensing the repair immediately is in line with the matching principle in accounting, which states that expenses should be recognized in the same period as the related revenues. Since the broken leg was a result of moving the desk into place, it can be considered a cost directly related to the acquisition of the desk and therefore should be expensed immediately.
To provide a clearer explanation, let's consider an example: Suppose a company purchased a new desk for $1,000. While an employee was moving the desk, one of its legs broke. The cost of repairing the leg is $200. In this case, the company would recognize a $200 expense in the period the leg broke, reducing the overall value of the desk to $800.
To know more about expenses visit:
brainly.com/question/29850561
#SPJ11
An SCM system coordinates all of the following functions except:
a. Procuring materials
b. Transforming materials into intermediate and finished products or services
c. Distributing finished products or services to customers
d. Advertising finished products to customers
Answers
The statement that's not coordinated a SCM is d. Advertising finished products to customers. Supply chain management is the process of delivering a product from raw material to the consumer.
Supply chain management contains supply planning, product planning, demand planning, sales and operations planning, and supply management. Supply chain management is critical because it can help gain several business objectives. For instance, it can be used to control manufacturing processes can decrease product quality, reducing the risk of recalls and lawsuits when helped to create a strong consumer brand. At the same time, controls over shipping procedures can increase customer service by avoiding costly shortages or periods of inventory oversupply. Supply chain management gives several benefits for companies to increase their profit margins and is especially crucial for companies with large and international operations.
Learn more about SCM, here https://brainly.com/question/29241738
#SPJ4
Aubrey uses the following formula to calculate a required value. Which elements of the formula use mixed cell referencing?

Answers
Answer:
$1A
brainiest plz
Explanation:
The elements of a formula only can have the following format:
1) Letter Number as C1
2) Letter $ Number as A$1
3) $ Letter Number as $A1
4) $ Letter $ Number as $A$1
The element $1A is not in the format
Answer:
A$1$A1Explanation:
Plato correct!
Which term is used to describe audiences who regularly watch cnn, home shopping network (hsn) and the weather channel?
Answers
The word is used to tell audiences who regularly watch CNN, home shopping network (HSN), and the weather channel to revisit the channel often.
What does channel mean in CNN?
In CNN this signifies that individually your filters get used to each of your tracks. Why? Because it might be that your filters get additional details from each of the media. And maybe they converge to different filters after each comprehending step as well. Follow this answer to receive notifications.
CNN has 36 units around the world and approximately 4,000 workers worldwide. CNN's range is grown and maintained by more than 900 affiliates worldwide.
To learn more about CNN, refer to:
https://brainly.com/question/17263283
#SPJ4
remember for a moment a recent trip you have made to the grocery store to pick up a few items. what pieces of data did the point of sale (pos) terminal and cashier collect from you and what pieces of data about the transaction did the pos terminal pull from a database to complete the sale? in addition to the data collected and retrieved what information was generated by the pos terminal at the end of the order, as it is being completed? this posting should offer an original and thoughtful response to the discussion topic. you are also required to respond to at least one original post.
Answers
The point of sale (POS) terminal and cashier will collect data from you such as your name and address if you are using a payment method such as a credit card, as well as any other information such as a loyalty card number or coupon code.
What is credit card?A credit card is a plastic card issued by a financial institution that allows the holder to purchase goods and services on credit. Credit cards are a form of revolving credit and can be used to pay for goods and services from any merchant that accepts the card.
The POS terminal will also pull data from a database to complete the sale such as the product’s price and any applicable discounts. The POS terminal will also generate information such as a customer receipt, the total price of the order, and any applicable taxes. At the end of the transaction, the POS terminal will generate a receipt with the customer’s name, address, and the items purchased, as well as the total cost of the order.
To learn more about credit card
https://brainly.com/question/28964146
#SPJ4