What is the first step you should take when you want to open a savings account make your initial deposit go to the bank and fill out an application present your photo ID to the bank representative review the different savings account options at your bank offers
Answers
Related Questions
Which of the following statements is true regarding input and output?
Input is the raw data that is entered into the computer for processing.
Input devices, such as a printer, are used to convey interpretations to users after processing.
Output devices, such as a keyboard, are used to enter data into a computer.
Output is data before it is processed and is not necessarily meaningful.
Answers
Answer:
Input is the raw data that is entered into the computer for processing.
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
On a circuit board, 1 corresponds to on, and 0 corresponds to off. True False
Answers
Answer:
The answer is true
Explanation:
Have a great day
What is Moore's law? (in simple terms please)
Answers
Transistors' density will be doubled every two years. In a simpler term, computers should be twice faster every two years.
Jackie is planning a birthday party for her little brother and is researching different trampoline parks. She receives a pop-up asking for her name, address, and date of birth so she can receive a special promotion from the trampoline park. What should Jackie do?
a
Ignore the request and not enter any personal information.
b
Provide only her name and date of birth.
c
Provide only her name and address.
d
Provide the requested information to receive the discount.
Answers
Answer:
a
Explanation:
sis is gonna get scammed
Answer:
a
Explanation:
You dont know who is getting your information and it is not someone you know. STRANGER DANGER!
georgenotfound??? question mark??
Answers
Answer:
hi
Explanation:
Identify a factor that is unlikely to influence the length of time people wait in the lunch line.
Answers
Answer:
Music.
Explanation:
Music or sound alone wont speed things up or slow them down
Answer:
the time they spent
Explanation:
Play the Scratch Game Chase HQ, Pay special attention to the animation, sounds, and colors used. Then answer the following questions in word processing document:
What kinds of sounds were used? How did the sounds affect the feel of the game?
How did the colors affect the mood and feel of the game?
What kinds of animation principles were used?
Answers
Answer:
Please mark me brainiest. It took a lot of time to compile this answer.
What kinds of sounds were used? How did the sounds affect the feel of the game?
Many sound effects were used, such as the screeching of the tyres, the sudden acceleration and the crashing or bumping of the car. The sound affects made the game feel more realistic
How did the colors affect the mood and feel of the game?
The main color used in the game is blue, which dominates the background and the color of the player's car. Blue is often associated with calmness and serenity, which is an interesting contrast to the high-intensity action of the game.
Red is also used prominently in ChaseHQ, which is often associated with danger, urgency, and excitement. In the game, red is used to indicate the presence of criminals and other hazards that the player must avoid or confront.
Overall, the color palette of ChaseHQ is intended to create a sense of high-speed action and excitement, while also providing a clear visual contrast between the player's car and the other elements in the game. The use of blue and red also helps to create a sense of urgency and danger, which is a key element of the game's gameplay and story.
What kinds of animation principles were used?
Chase HQ used a variety of animation principles to create movement and visual effects in its projects. Some of the key animation principles used in Scratch include:
Squash and Stretch: This principle involves stretching an object in one direction and compressing it in another to give the impression of weight and movement.
Timing: The timing of an animation can greatly affect its impact. In Scratch, users can control the timing of their animations by adjusting the duration and speed of individual blocks.
Anticipation: This principle involves adding a small movement in the opposite direction of the intended action to help build anticipation and create a more dynamic animation.
Follow-Through and Overlapping Action: These principles involve creating secondary movements that follow the main action of the animation, helping to create a more natural flow of movement.
Arcs: This principle involves using curved paths of motion to create more organic and appealing movement.
Overall, Scratch provides a range of tools and features that allow users to incorporate these animation principles and create engaging and dynamic projects.
Explanation:
Answer: Please mark me brainiest. It took a lot of time to compile this answer.
What kinds of sounds were used? How did the sounds affect the feel of the game?
Many sound effects were used, such as the screeching of the tyres, the sudden acceleration and the crashing or bumping of the car. The sound affects made the game feel more realistic
How did the colors affect the mood and feel of the game?
The main color used in the game is blue, which dominates the background and the color of the player's car. Blue is often associated with calmness and serenity, which is an interesting contrast to the high-intensity action of the game.
Which is the best approach to debugging?
A.
Don’t worry about it at all until after the program is written.
B.
Be sure the program will work perfectly before writing it.
C.
Anticipate errors before they happen, and find and fix errors that happen.
D.
Use an HTML encoder.
Answers
Reese is using a flight simulator. This program can help her
A. determine the best aviation headset
B. find the best flight simulation
C. identify how much time one needs to become proficient at flying
D. prepare for possible in-air emergencies
Answers
Eliza is the head instructor at a ballet academy. Eliza works in the ______ pathway of the Arts, AV Technology, and Communication cluster.
Question 11 options:
A. AV Technology and Film
B. Printing Technology
C. Journalism and Broadcasting
D. Performing Arts
Answers
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail?
Analysis report
Resources document
Scope
Scope creep
Answers
What are some machines, places or apparatus that sensors could be used in? Give at least five examples.
Answers
Answer:
Sorry
Explanation:
Name 10 reasons why computers are better than other electronic devices? :)
Answers
What are the four objectives of the Perseverance Rover?
Answers
Answer:
The rover's goals include identifying ancient Martian environments capable of supporting life, seeking out evidence of former microbial life existing in those environments, collecting rock and soil samples to store on the Martian surface, and testing oxygen production from the Martian atmosphere to prepare for future crewed missions.
Explanation:
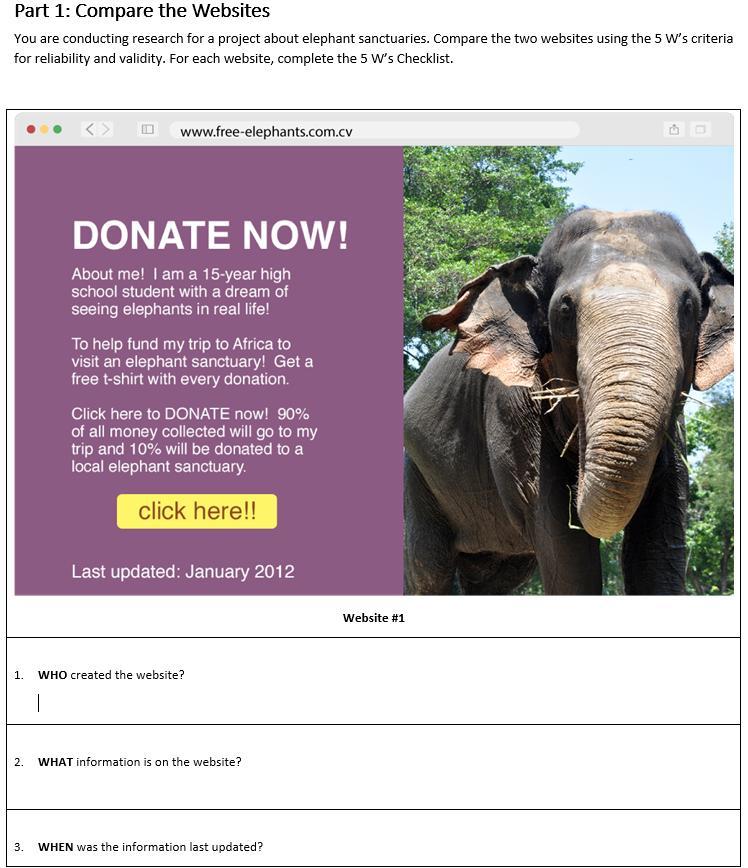
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
A web designer should test each link to make sure it is not _______ for the best user experience. This is known as __________ testing.
I know the second answer is broken link testing so you don't have to do the second one.
Answers
Answer:
Explanation:
it
computer
what is used to connect computers to the internet*Audio Ports
*Connector
*Display Port
*Ethernet Ports
*External Ports
*HDMI
*Internal Ports
*Memory Cards
*Ports
*Protocol
*Thunderbolt
*USB
*USB Type A
*USB Type B
*USB Type C
*Version
*VGA
Answers
Answer: it is HDMI, you had it on the list already
Answer:
The person on top is wrong, the first one is VGA PORT not HDMI PORT.
and the second one is HDMI PORT
Explanation:
Explain how to create a constant variable. Give an example of creating a speed constant that does not include a decimal.
Answers
Answer:
You use the Const statement to declare a constant and set its value. By declaring a constant, you assign a meaningful name to a value. Once a constant is declared, it cannot be modified or assigned a new value. You declare a constant within a procedure or in the declarations section of a module, class, or structure.
Explanation:
https://docs.microsoft.com/en-us/dotnet/visual-basic/programming-guide/language-features/constants-enums/how-to-declare-a-constant
Have a bless day <3 lve yall
Answer:
https://docs.microsoft.com/en-us/dotnet/visual-basic/programming-guide/language-features/constants-enums/how-to-declare-a-constant
Here's a link for the answer
Explanation:
PLZZZZZZZZZZZZZZZZZZZZZ HELP ME!!!!!!!!!!!!
Answer the three questions on the handout to map out your personalized media-balance strategy. Then, complete the personal challenge that follows.
1. Which media choices give you the most benefits? What are those benefits?
2.What is one step you can take right now to be more media balanced? Write a concrete and actionable step you will take. In your response, include any challenges you might face and how you will address them.
Answers
Place the following events in sequence: A) Feynman challenges people to build "nano-things;" B) The first nano-motor is built; C) The structure of DNA is discovered
Answers
Answer: C, A, B.....I think
Explanation:
The correct sequence of events is:
C) The structure of DNA is discovered.
A) Feynman challenges people to build "nano-things".
B) The first nanomotor is built.
What is nano-motor?A molecular or nanoscale device capable of transferring energy into movement is known as a nanomotor. It is capable of producing forces on the order of piconewtons.
The novel DNA-based nanomotor is made up of three parts: a base, a platform, and a rotor arm. The base is around 40 nanometers high and is attached to a glass plate in solution via chemical bonds. A rotor arm with a length of up to 500 nanometers is attached on the base and can rotate.
Nanomotors are molecular devices that use chemical energy to cause molecules to move. Virus genomes are packaged in preformed capsids or procapsids using nanomotors.
Therefore, the correct sequence of events is: C, A, and B.
To learn more about nano-motor, refer to the link:
https://brainly.com/question/15307678
#SPJ2
3 different ways that ultrasonic sensors can be used in everyday life.
Answers
Answer:
Ultrasonic Sensors Uses:
Anti-Collision DetectionPeople DetectionContouring or ProfilingPresence DetectionBox Sorting using a Multi-Transducer SystemEasy Control of Trash Collection VehiclesPallet Detection with ForkliftsBottle Counting on Drink Filling MachinesLearn more about Ultrasonic Sensors here
Visit —
https://brainly.in/question/19907919
https://brainly.ph/question/13809853
Hope my answer helps you ✌️
Mark BRAINLIEST
Ultrasonic retro-reflective sensors.
Ultrasonic through-beam sensors.
Match List
Match each term to its definition.
Put responses in the correct input to answer the question.
Correct answers:
1
a value that can be passed to a function
2
a group of instructions that can be used to organize a program or perform a repeated task
3
a value that can be passed from a function back to the calling part of a program

Answers
Parameter - A value … function
Function - A group
Answer:
parameter: a value that can be passed to a function
function: a group of instructions that can be used to organize a program or perform a repeated task
return value: a value that can be passed from a function back to the calling part of a program
Explanation:
This is for a test HELP!!!Sorry this was meant for history
What is a characteristic of a house slave?
A:children put into the work force at an early age
B:received better food than other slaves
C:lived in a certain section of town
D:received a portion of their money
Answers
Answer:
B
Explanation:
B
Please help me with these questions. Thanks o((>ω< ))o


Answers
Answer:
1: Browser 2: Compile 3: Web? 6: Search
Name three computer company's.
Answers
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
Which option identifies the type of variable recorded in the following chart?
Respondents % Yes Votes % No Votes Total Responses
Age 13 – 20 26.6 % 73.4 % 100 %
Age 21 – 35 50.7 % 49.3 % 100 %
Age 36 + 65.8 % 34.2 % 100 %
Nominal variable
Interval variable
Ordinal variable
Descriptive variable
help! Please!