what command must be entered to configure an ip address of 192.168.10.3 and subnet mask of 255.255.255.0 for a switch?
Answers
IP address 192.168.99.2 255.255.255.0 is the command must be entered to configure an IP address of 192.168.10.3 and a subnet mask of 255.255.255.0 for a switch.
What is IP address?The IP address of a device can be used to identify it on the internet or within a local network. The term "Internet Protocol," or IP, refers to the standards that specify how data is conveyed through a local or wide-area network or the internet.
IP addresses are essentially the identifier that allows information to be transmitted between devices on a network as they carry location information and make devices reachable for communication. On the internet, there needs to be a way to distinguish between computers, routers, and web pages. IP addresses, which are essential to how the internet functions, offer a way to do this.
An IP address is made up of a string of integers separated by commas. In order to represent IP addresses, four numbers are used; The range of each number in the set is 0 to 255. Therefore, the complete IP addressing range is 0.0.0.0 to 255.255.255.255.
To learn more about IP address visit:
https://brainly.com/question/16011753
#SPJ4
Related Questions
A new pet supply company plans to primarily sell products in stores. They need a system that will track their large inventory and keep customer sales records.
Which evaluation factor will be most important when choosing technology for the company?
speed
size
storage
connectivity
Answers
The evaluation factor that will be most important when choosing technology for the company is known as storage .
What is an evaluation factor?An Evaluation factor is made up of those key areas that are said to be of importance and tells more about source selection decision.
Note that The evaluation factor that will be most important when choosing technology for the company is known as storage because it is a factor that need to be considered.
Learn more about evaluation factor from
https://brainly.com/question/4682463
#SPJ1
You are researching the Holocaust for a school paper and have located several Web sites for information.In three to five sentences, describe the method you would use to determine whether each Web site is a suitable source of information for your paper.
Answers
I suggest the following methods to determine whether a website is a suitable source of information for a school paper on the Holocaust:
The MethodCheck the credibility of the website by examining the author's qualifications, credentials, and institutional affiliation.
Evaluate the accuracy of the information by comparing it with other reliable sources on the same topic.
Check the currency of the information by looking at the date of publication or last update. Avoid using outdated information.
Analyze the objectivity of the website by checking for any bias or slant towards a particular perspective or ideology.
Lastly, check the website's domain name and extension to verify its origin, as some domains may have questionable reputations.
Read more about sources here:
https://brainly.com/question/25578076
#SPJ1
what concept is used to grants users only the rights and permissions they need to complete their job responsibilities?
Answers
The principle of least privilege (PoLP) is an information security concept in which a user is granted the bare minimum of access - or permissions - required to carry out his or her job functions.
What is Least privilege (PoLP)?
The principle of least privilege (PoLP) is an information security concept that is also known as the principle of minimal privilege or the principle of least authority. It specifies that any user, device, workload, or process should only have the privileges required to carry out its intended function.
In this context, the term privilege refers to system rights or data access. For example, it determines which users can access a specific file or which devices can connect to a specific network. It is also used to specify what users can and cannot do on a system. Some users, for example, may only be able to perform specific functions, whereas others may be able to do more, such as restart the application or apply updates.
To learn more about Least privilege (PoLP), visit: https://brainly.com/question/28476933
#SPJ4
Which of the following numbers might this code generate: random.randint(1,9)?
0
10
11
1
Answers
Answer:
1
Explanation:
In Python programming language, the random.randint function is an abbreviation for random integers.
Basically, the random.randint is used for generating or creating a random integer numbers.
The syntax for this code can be written as;
A = random.randint(1,9)
Print ("Random number between 1 and 9 is % s" % (A))
Note, the numbers between 1 and 9 are 1, 2, 3, 4, 5, 6, 7, 8 and 9.
From the answer choices given (0, 1, 10 and 11), the only number that matches the requirement is 1.
Therefore, the number this code random.randint (1,9) might generate is 1.
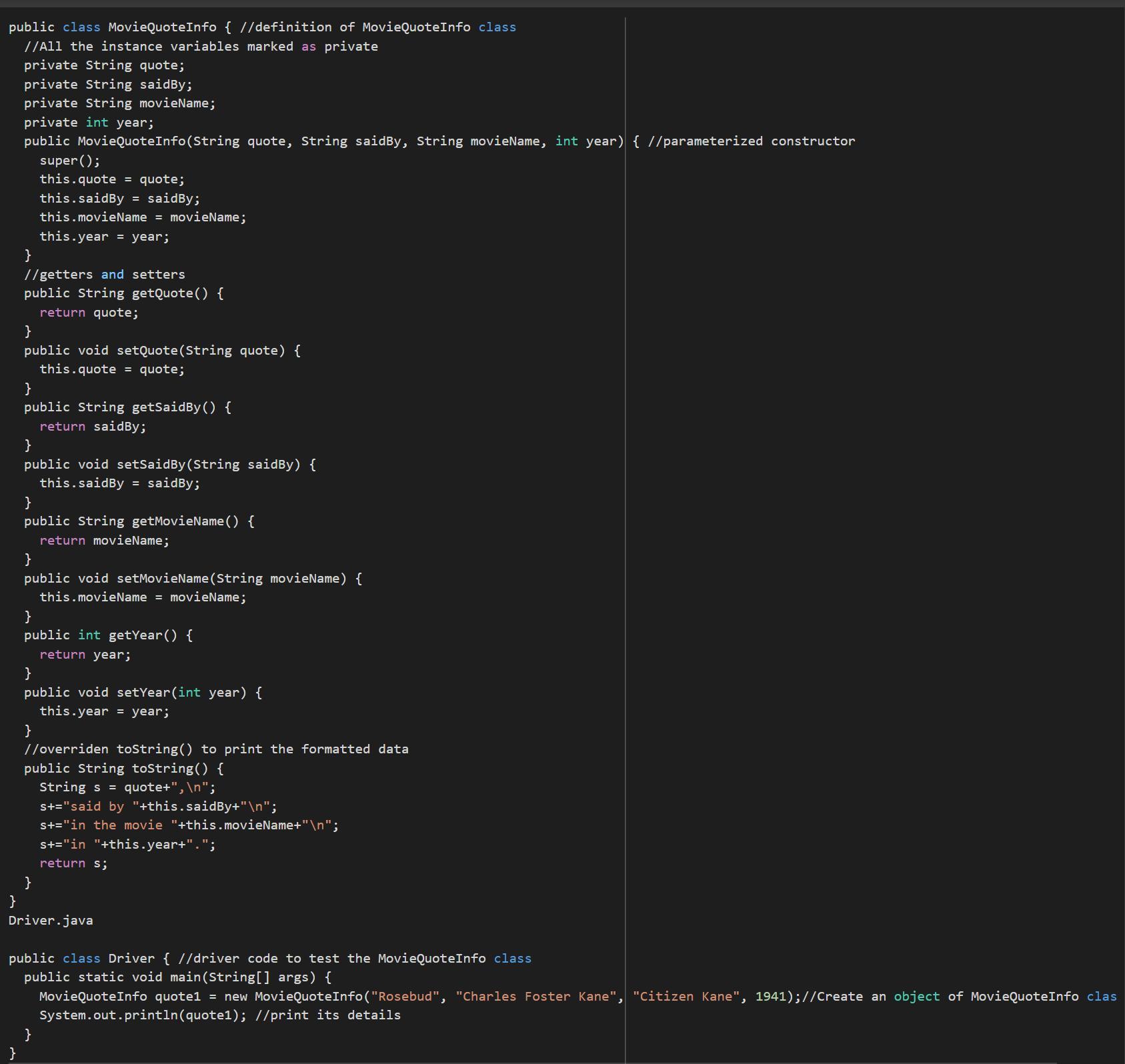
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
(True or False) The speed at which data travels on a bus is referred to as the word size.
Answers
Answer:
True
Explanation:
The given statement "The speed at which data travels on a bus is referred to as the word size" is false because the speed at which data travels on a bus is referred to as the bus speed, bus frequency, or bus clock speed.
Given that;
The speed at which data travels on a bus is referred to as the word size.
Now, The word size, on the other hand, refers to the number of bits that a CPU or computer system can process at once.
It is a fundamental characteristic of a computer's architecture and is determined by the number of bits that the CPU can process in a single instruction.
Hence the correct answer is option B. False.
Learn more about CPU bus speed at
brainly.com/question/8179207
#SPJ3
T/F: the cpu understands instructions written in a binary machine language.
Answers
Instructions written in binary machine language can be understood by the CPU. A bit that is disabled is represented by the value -1.
What does the CPU use to carry out programme instructions?It retrieves the first instruction in the sequence, executes it (by, for example, adding two numbers), then fetches the next instruction, executes it, and so on.
How does a CPU interpret machine language?A low level "machine code" language is understandable by a CPU (also known as "native code"). The hardware of the CPU is hardwired with the language of the machine code; it cannot be modified at whim.
To know more about machine language visit:-
https://brainly.com/question/12696037
#SPJ4
Which range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE?
A. 10.120.160.0 to 10.120.168.0
B. 10.120.160.0 to 10.127.255.255
C. 10.120.160.0 to 10.120.191.255
D. 10.120.160.0 to 10.120.167.255
Answers
10.120.160.0 to 10.120.167.255 is the range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE.
Thus option D is correct.
What is IP addresses?An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notations, such as 192.0.2.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.0.2.1/24, which is equivalent to the historically used subnet mask 255.255.255.0.
Learn more about IP addresses
https://brainly.com/question/16011753
#SPJ4
Describe a recent data communication development you have read
about in a newspaper or magazine (not a journal, blog, news
website, etc.) and how it may affect businesses. Attach the URL
(web link).
Answers
One recent data communication development is the emergence of 5G technology. With its faster speeds, lower latency, and increased capacity, 5G has the potential to revolutionize various industries and transform the way businesses operate.
The deployment of 5G networks enables businesses to leverage technologies and applications that rely on fast and reliable data communication. For example, industries such as manufacturing, logistics, and transportation can benefit from real-time data exchange, enabling efficient supply chain management, predictive maintenance, and autonomous operations. Additionally, sectors like healthcare can leverage 5G to facilitate remote surgeries, telemedicine, and the Internet of Medical Things (IoMT), enabling faster and more reliable patient care.
Moreover, the increased speed and capacity of 5G can enhance the capabilities of emerging technologies such as augmented reality (AR), virtual reality (VR), and the Internet of Things (IoT). This opens up new opportunities for businesses to deliver immersive customer experiences, optimize resource utilization, and develop innovative products and services.
Overall, the deployment of 5G technology has the potential to drive digital transformation across industries, empowering businesses to streamline operations, enhance productivity, and deliver enhanced experiences to customers.
Learn more about technology here: https://brainly.com/question/11447838
#SPJ11
How do you calculate the slope for a voltage-current graph?
Answers
Answer:
Choose two points on the line to work from (point C and point D).
Calculate the voltage difference between the two points (the RISE of the slope).
Calculate the current gap between the two points (the RUN of the slope).
Subtract the RISE from the RUN. This is the line's slope.
Explanation:
i think it is a or c is it right?

Answers
She is emailing her boss that something is wrong.
Scenario description: Assume you got a new wireless sensor device with circuit power consumption of P_elec = 0.015mW. Frequency bandwidth (i.e. symbol rate) is 1MHz. You have a packet with 125 bytes to send. Assume there is no other overhead, and you can ideally turn on and off the transmission without additional power cost. Now you can choose using various data rates to transmit this packet, while maintaining the same BER at 0.0001 with the following assumption: using BPSK, the required TX amplifier power consumption of P_t =0.02mW; using QPSK, the required TX amplifier power consumption of P_t =0.05mW. Receiver energy consumption is not a concern. Questions: Please calculate the energy consumption (in unit of nJ â Nano-Joule) of transmitting this packet, using BPSK and QPSK schemes, respectively. Do you prefer slow BPSK transmission to save power, or to transmit quickly with QPSK and then sleep (3 point)?
Answers
The energy consumption of transmitting the packet using BPSK is approximately 120 nJ, while using QPSK it is approximately 250 nJ.
To calculate the energy consumption of transmitting the packet, we need to consider the power consumption of the transmitter and the time taken to transmit the packet at different data rates.
For BPSK, the required TX amplifier power consumption is P_t = 0.02 mW. The data rate is 1 MHz, and the packet size is 125 bytes. Since there is no additional power cost when turning on and off the transmission, the time taken to transmit the packet is simply the packet size divided by the data rate: 125 bytes / 1 MHz = 125 μs.
The energy consumption can be calculated by multiplying the power consumption by the time taken: P_t * t = 0.02 mW * 125 μs = 2.5 μJ = 250 nJ.
For QPSK, the required TX amplifier power consumption is P_t = 0.05 mW. The data rate is still 1 MHz, but since QPSK can transmit twice as much information per symbol compared to BPSK, the time taken to transmit the packet is halved: 125 bytes / 2 MHz = 62.5 μs.
The energy consumption can be calculated in the same way: P_t * t = 0.05 mW * 62.5 μs = 3.125 μJ = 312.5 nJ.
Therefore, the energy consumption of transmitting the packet using BPSK is approximately 120 nJ, while using QPSK it is approximately 250 nJ.
Learn more about Consumption
brainly.com/question/31868349
#SPJ11
What is responsible for getting a system up and going and finding an os to load?
Answers
The computer's BIOS (Basic Input/Output System) is responsible for getting the system up and running and finding an operating system to load.
When a computer is turned on, the first piece of software that runs is the BIOS. The BIOS is a small program stored on a chip on the motherboard that initializes and tests the computer's hardware components, such as the CPU, memory, and storage devices. Once the hardware is tested and initialized, the BIOS searches for an operating system to load.
It does this by looking for a bootable device, such as a hard drive or CD-ROM, that contains a valid operating system. If the BIOS finds a bootable device, it loads the first sector of the device into memory and transfers control to that code, which then loads the rest of the operating system. If the BIOS cannot find a bootable device, it will display an error message or beep code indicating that there is no operating system to load.
Learn more about Basic Input/Output System here:
https://brainly.com/question/28494993
#SPJ11
If a spreadsheet user wants Calc to add a range of cells, what built-in function should he or she use?
A) the ADD function
B) the OPR function
C) the SUM function
D) the WIZARD function
Answers
Answer: Its C
Explanation:
Mathematics and computer science share the concept of recursion.
You wrote a program to find the factorial of a number using recursion.
5! =
Answers
5! is equal to 120.
5 * 4 * 3 * 2 * 1 = 120
Answer: 5
Explanation: got it right on edgen
South Africa is the main supplier of which minerals in the world
Answers
South Africa has the largest reserves of Platinum-group metals (PGMs; 88%), Manganese (80%), Chromite (72%) and Gold (13%) known reserves in the world. It is ranked second in Titanium minerals (10%), Zirconium (25%), Vanadium (32%), Vermiculite (40%) and Fluorspar (17%).
Answer:
Gold south africa is the world largest producer of gold but they slowly produce them
write any two disadvantage of First generations computers
Answers
Answer:
•The computers were very larger in size.So therefore not portable and very heavy.
•They consumed a large amount of energy.
please help me with this please

Answers
Answer:
The 3rd answer.
Explanation:
You're welcome pa.
Answer:
Answer is C: You are using a series of commands multiple times in a ducument
Explanation:
a ____ table contains only text, evenly spaced on the web page in rows and columns.
Answers
A HTML table contains only text, evenly spaced on the web page in rows and columns.
The type of table that contains only text, evenly spaced on the web page in rows and columns.
A "fixed-width" table contains only text, evenly spaced on the web page in rows and columns. This type of table uses a fixed width for each column, ensuring that the content is consistently and uniformly aligned.
A HTML table contains only text, evenly spaced on the web page in rows and columns.
Learn more about HTML table
brainly.com/question/30926057
#SPJ11
Please help me with my question

Answers
Answer:
1. Template
2. Name of the website
3. Signature of the instructor
write a function called eligible that helps the admission officer of the graduate school of vanderbilt university decide whether the applicant is eligible for admission based on gre scores. the function takes two positive scalars called v and q as input and returns the logical admit as output. they represent the percentiles of the verbal and quantitative portions of the gre respectively. you do not need to check the inputs. the applicant is eligible if the average percentile is at least 92% and both of the individual percentiles are over 88%. the function returns logical true or false value.
Answers
Here is a possible implementation of the "eligible" function in Python:
python
Copy code
def eligible(v, q):
avg_percentile = (v + q) / 2
return avg_percentile >= 92 and v > 88 and q > 88
The function takes in two positive scalars, v and q, which represent the percentiles of the verbal and quantitative portions of the GRE, respectively. It calculates the average percentile by taking the sum of v and q and dividing by 2. It then checks if the average percentile is at least 92% and if both v and q are greater than 88%. If these conditions are true, the function returns a logical True value, indicating that the applicant is eligible for admission. Otherwise, it returns a logical False value.
Note that the implementation assumes that the input values are valid positive scalars, as specified in the problem statement. If the input values could potentially be invalid, additional error checking code would be needed to ensure the function does not encounter any errors or unexpected behavior.
After spending months carefully building his closed batch storage system, David comes to see his advisor with the following description and measurements: The MPL for the system if fixed at 19 jobs. Davide explains that 90% of jobs find the data they need in the cache, and hence their expected response time is only 1 second. However 10% end up having to go to database, where their expected response time is 10 seconds. David's advisor asks one question: "How many jobs do you see on average at the database?". When David answers "5", his advisor says he needs to go back to the drawing board. What went wrong?
Answers
The problem with David's closed batch storage system is that it violates Little's Law, which states that the average number of jobs in a system is equal to the average arrival rate multiplied by the average response time. In other words, if the system has a fixed maximum processing limit (MPL), then the average number of jobs in the system cannot exceed MPL.
In this case, David has a fixed MPL of 19 jobs. He has stated that 90% of jobs find the data they need in the cache and have an expected response time of 1 second, while the remaining 10% must go to the database with an expected response time of 10 seconds. This implies that the average response time for all jobs in the system is 1 x 0.9 + 10 x 0.1 = 1.9 seconds.
Using Little's Law, the average number of jobs in the system can be calculated as the arrival rate multiplied by the average response time. If we assume that the arrival rate is constant and equal to λ, then we have:
Average number of jobs = λ x 1.9
David has stated that the average number of jobs at the database is 5. If we assume that all jobs that go to the database spend the full 10 seconds there, then we can calculate the arrival rate as follows:
5 = λ x 10
λ = 0.5
Substituting this value into Little's Law, we get:
Average number of jobs = 0.5 x 1.9 = 0.95
To know more about storage: Here
https://brainly.com/question/24227720
#SPJ4
Which html attribute specifies an alternate text for an image, if the image cannot be displayed?.
Answers
The html attribute "<img> alt attribute" is used to specify the alternate text for an image if the image can not displayed.
What are alternate text?
An alternate text acronyms is (Alt text) which is a text description that can be added to an image's HTML tag on a Web page.
In conclusion, the html attribute "<img> alt attribute" is used to specify the alternate text for an image if the image can not displayed
Read more about alternate text
brainly.com/question/12809344
Scott does not use privacy settings on his social media
Answers
Answer:
ARREST HIM!!!
Explanation:
Answer:
Explanation
arrest him
you've finished programming the app! Now your company has to decide whether to use an open source
license or proprietary license. explain which one you would choose and why.
Answers
Answer:
Proprietary License gives you full ownership and trademark/patent opportunites. Open source allows for code donation and a community based development for your app. Generally speaking, if your a private entity creating an app for a client, you'll need the Proprietary Licence, which will allow you to sell the codebase to your client.
If your creating an app for your company as itself, you go either way, sell the license in licensing agreements, or have your companies community contribute and better your app from the inside.
Its entirely based on the agreements you set for the app.
who knows how to cope and paste on (ape.x)
Answers
To copy and paste on Apex, you can use the keyboard shortcuts "Ctrl+C" and "Ctrl+V" or right-click the selected text and choose "Copy" and "Paste."
Without more information about the context and platform you are referring to, it is difficult to provide a helpful response. However, if you are asking how to copy and paste on a computer or mobile device, the process typically involves selecting the text or item you want to copy, pressing "Ctrl + C" on a PC or "Command + C" on a Mac, and then pasting it by pressing "Ctrl + V" or "Command + V". The specific steps may vary depending on the software or device you are using, so it is recommended to consult the instructions or help resources for that specific platform.
Copying and pasting are essential computer skills that allow you to duplicate text or other content from one place and insert it into another. In Apex, you can use these methods to copy and paste information, making it easier to complete tasks efficiently.
To know more about keyboard visit:
https://brainly.com/question/24921064
#SPJ11
Veronica is looking for a reliable website with information about how old you have to be to use social media. What should she look for?
A Websites selling something
B Websites with opinion
C Where the website was created
D Who created the website
Answers
Websites with opinion
What are like arms surrounding all the other code blocks?1. chevrons2. curly braces3. square braces4. parentheses
Answers
Curly braces ({}) are like arms surrounding all the other code blocks. In many programming languages, curly braces are used to enclose a block of code and to group multiple statements together into a single compound statement.
For example, in C++, Java, and JavaScript, curly braces are used to enclose the body of a function or a control structure, such as an if statement or a loop:In Python and some other languages, indentation is used instead of curly braces to indicate the grouping of statements. However, the concept is the same - the code within the indented block is treated as a single unit.In general, curly braces are used to group related code together and to make it easier to read and understand the structure of the program.
Learn more about indentation here
https://brainly.com/question/24953659
#SPJ11
Online advertising includes: a. All of these are correct. b. ads in print newspapers. c. social media. d. listings on directory sites
Answers
Online ads only have advertising on social networks.
What are online ads?Online ads are a form of advertising that is characterized by being on the web pages that we usually visit when we surf the internet.
In many cases we open a page and advertising related to our tastes and products that we have recently looked at appears.
Online advertisements have the particular characteristic that they are exclusively on the internet and cannot appear in other places such as newspapers or television.
Learn more about Online advertising in: https://brainly.com/question/25743681
which phone message requires the most immediate response by the nurse manager?
Answers
The nurse manager must act quickly to preserve the safety of patients and workers whenever a nurse reports an emergency scenario, such as a fire or violent event.
Is Odetta Sanku a medical facility's nurse manager?The nurse manager is here: Sanku Odetta In a low-income section of a significant metropolitan area, Odetta Sanku is the nurse manager of a walk-in pediatric clinic located in a medical center satellite. In the area, a daycare center for children of homeless families receives services from the clinic.
Who works in nursing as Phoebe?The first nurse mentioned in the Bible is Phoebe. The early Christian virtues of generosity and selflessness are supposed to have been best exhibited by Phoebe, who was appointed by St. Paul to serve as a deaconess in the church.
To know more about scenario visit:-
https://brainly.com/question/25813468
#SPJ1