what activity involves simply observing someone's screen or keyboard to get information, often passwords?
Answers
The activity that involves observing someone's screen or keyboard to get information, often passwords, is called "shoulder surfing." Shoulder surfing is a form of spying or surveillance in which a person observes another person's screen or keyboard in order to obtain sensitive information, such as passwords, credit card numbers, or personal identification numbers. This type of activity is often done without the knowledge or consent of the person being observed, and it can be done in person or remotely using a camera or other recording device. Shoulder surfing is considered a security risk because it allows an attacker to gain access to sensitive information without the need for hacking or other technical skills. To protect against shoulder surfing, it is important to be aware of your surroundings and to keep your screen and keyboard out of view of others whenever possible.
Related Questions
Which of the following describe audio-editing software? Choose all that apply.
syncs audio with video
is used only by professionals
modifies analog sound
modifies sound quality
mixes sound
Answers
Answer:
1,4,5
Explanation:
The objectcontext instance has been disposed and can no longer be used for operations that require a connection
Answers
It must be recreated if it is to be used again. The best practice is to ensure that the Object Context instance is properly disposed of when it is no longer needed.
What is object ?
Object-oriented programming (OOP) is a programming paradigm based on the concept of objects, which contain data and methods. Objects are used to interact with one another to design applications and computer programs. In OOP, an object is an entity that has a defined boundary, state, and behavior. It can be used to represent a real-world entity or an abstract concept. Objects can also be used to group related data and functions, which can be accessed and used by other objects.
To know more about Object
https://brainly.com/question/21113563
#SPJ4
print 3 numbers before asking a user to input an integer

Answers
Answer:
you can use an array to do this
Explanation:
(I've written this in java - I think it should work out):
Scanner input = new Scanner(System.in);
System.out.println("Enter an integer: ");
int userInt = input.nextInt();
int[] array = new int[userInt - 1];
for(int i = userInt-1; i < userInt; i--)
System.out.println(array[i]);
The lifetime of a new 6S hard-drive follows a Uniform
distribution over the range of [1.5, 3.0 years]. A 6S hard-drive
has been used for 2 years and is still working. What is the
probability that it i
Answers
The given hard-drive has been used for 2 years and is still working. We are to find the probability that it is still working after 2 years. Let A denote the event that the hard-drive lasts beyond 2 years. Then we can write the probability of A as follows:P(A) = P(the lifetime of the hard-drive exceeds 2 years).By definition of Uniform distribution, the probability density function of the lifetime of the hard-drive is given by:
f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.where a = 1.5 years and b = 3.0 years are the minimum and maximum possible lifetimes of the hard-drive, respectively. Since the probability density function is uniform, the probability of the hard-lifetime of a new 6S hard-drive follows a Uniform distribution over the range of [1.5, 3.0 years]. We are to find the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years.Let X denote the lifetime of the hard-drive in years.
Then X follows the Uniform distribution with a = 1.5 and b = 3.0. Thus, the probability density function of X is given by:f(x) = 1/(b - a) if a ≤ x ≤ b; 0 otherwise.Substituting the given values, we get:f(x) = 1/(3.0 - 1.5) = 1/1.5 if 1.5 ≤ x ≤ 3.0; 0 the integral is taken over the interval [2, 3] (since we want to find the probability that the hard-drive lasts beyond 2 years). Hence,P(A) = ∫f(x) dx = ∫1/1.5 dx = x/1.5 between the limits x = 2 and x = 3= [3/1.5] - [2/1.5] = 2/3Thus, the probability that a 6S hard-drive, which has been used for 2 years and is still working, will continue to work beyond 2 years is 2/3.
To know more about Uniform distribution visit:
brainly.com/question/13941002
#SPJ11
The _________ file system manages metadata information. Metadata includes all of the file-system structure except the actual data (or contents of the files). The ________ file system manages the directory structure to provide the file-organization module with the information the latter needs, given a symbolic file name. It maintains file structure via file-control blocks
Answers
The metadata file system manages metadata information. Metadata includes all of the file-system structure except the actual data (or contents of the files). The directory file system manages the directory structure to provide the file-organization module with the information the latter needs, given a symbolic file name. It maintains file structure via file-control blocks
The metadata file system is responsible for storing information about files such as file size, creation date, and permissions. The directory file system manages the directory structure and provides the file organization module with information. The directory file system uses file-control blocks to maintain the file structure and keep track of where files are located within the directory tree. Both the metadata file system and directory file system work together to ensure that content is loaded and accessed efficiently.
Learn more about metadata and directory file systems:https://brainly.com/question/14960489
#SPJ11
The metadata file system manages metadata information. Metadata includes all of the file-system structure except the actual data (or contents of the files). The directory file system manages.
the directory structure to provide the file-organization module with the information the latter needs, given a symbolic file name. It maintains file structure via file-control blocks The metadata file system is responsible for storing information about files such as file size, creation date, and permissions. The directory file system manages the directory structure and provides the file organization module with information. The directory file system uses file-control blocks to maintain the file structure and keep track of where files are located within the directory tree. Both the metadata file system and directory file system work together to ensure that content is loaded and accessed efficiently.
Learn more about metadata file here:
brainly.com/question/14960489
#SPJ11
how does digital and hybrid computers differ in portability
Answers
Answer:
Digital computers perform functions like mathimatical,compex calculations. while hybrid computers work with the duo combinations like analog and tempature.
Explanation:
I passed the class A+
yourwelcome :)
thank me if it was correct for you too.
Physical Geography of the Middle East
Answers
Answer:
Explanation:
He’s wright SS7G5 The student will locate selected features in
Southwestern Asia (Middle East).
a. Locate on a world and regional political-physical map:
Euphrates River, Jordan River, Tigris River, Suez Canal,
Persian Gulf, Strait of Hormuz, Arabian Sea, Red Sea, and
Gaza Strip.
b. Locate on a world and regional political-physical map the
nations of Afghanistan, Iran, Iraq, Israel, Saudi Arabia, and
Turkey
Which of the following internet connection technologies requires that the location be within a limited distance of the telephone company central office?SatelliteWirelessDSLCable modem
Answers
Out of the given internet connection technologies, the one that requires the location to be within a limited distance of the telephone company central office is DSL (Digital Subscriber Line).
DSL technology utilizes the existing telephone lines to transmit data signals between the central office and the user's location. However, the quality of the DSL connection is highly dependent on the distance between the central office and the user's location. If the user's location is too far away from the central office, the signal can weaken, leading to slow internet speed or even complete disconnection. On the other hand, satellite internet does not have any geographical limitations as it uses a satellite orbiting the Earth to transmit signals.
Wireless internet, as the name suggests, is wireless and can be accessed within a certain range of a wireless access point. Finally, cable modem technology uses the cable television infrastructure to provide internet access and does not have any limitations based on the location distance from a central office. In conclusion, DSL internet technology requires that the user's location be within a limited distance of the telephone company central office, while the other mentioned technologies do not have such limitations.
Learn more about internet here: https://brainly.com/question/28347559
#SPJ11
What is computer virus?

Answers
Answer:
A computer virus is a malicious software program loaded onto a user's computer without the user's knowledge and performs malicious actions.
Explanation:
................................................
Please tell answer fast

Answers
Answer:
a sonos wireless speakers
when adjusting the driver's seat, ensure there is at least (_how_many_) inches between the driver's chest and the steering wheel for the best access to foot controls.
Answers
There should be at least 10 inches between the driver's chest and the steering wheel when adjusting the driver's seat for the best access to foot controls.
Maintaining a distance of at least 10 inches between the driver's chest and the steering wheel ensures optimal access to foot controls, provides better visibility, and minimizes the risk of injury in case the airbag deploys during a collision.
This is because having the right distance between the driver and the steering wheel helps to ensure that the driver can comfortably reach the pedals and also have enough room for their airbag to deploy in the event of an accident. It is important to remember that this is a general guideline and drivers should adjust their seat to their own individual comfort level while also keeping safety in mind.
Learn more about deploy visit:
https://brainly.com/question/29803616
#SPJ11
Testout Floor 1 Overview Office 1 Ofice Recycle Bin Scenario You are the IT administrator for a small corporate network. Currently, the computer in Office 1 has three hard disks in the computer. A single volume has been defined on each disk, taking up all of the space on that disk. Employees are running out of space on the the E: volume and would like additional space. You've installed a new hard drive in the computer and booted into Windows. In this lab, your task is to extend the E: drive using 300000 MB on Disk 3 using the GPT partition style. o Type here to search Lab Report Your Performance Your Score: 0 of 1 (0%) Elapsed Time: 1 minute 16 seconds Pass Status: Not Passed Required Score: 100% Task Summary Actions you were required to perform: * Extend the Art volume (E:) Show Details Explanation In this lab, your task is to extend the E: drive using 300000 MB on Disk 3 using the GPT partition style. Complete this lab as follows: 1. Right-click Start and select Disk Management. 2. Select GPT as the partition style. 3. Click OK to initialize the new disk. 4. Maximize the window for easier viewing. 5. Right-click Art (E:) and select Extend Volume 6. Click Next. 7. Under Available, select Disk 3. 8. Select Add. 9. In the Select the amount of space in MB, enter 300000 to be added to the existing volume. 10. Click Next. 11. Click Finish 12. Click Yes to extend the volume to non contiguous free space, the disks must be upgraded to dynamic disks. Done
Answers
To extend the E drive using 300000 MB on Disk 3 using the GPT partition style, you need to follow these steps, by completing these steps, you will be able to extend the E drive using the space on Disk 3. It is important to select the GPT partition style as it supports disks larger than 2 TB.
First, Right-click Start and select Disk Management, then Select GPT as the partition style, after that Click OK to initialize the new disk, then Maximize the window for easier viewing and Right-click Art E and select Extend Volume, then Click Next and Under Available, select Disk 3, Select Add. In the Select the amount of space in MB, enter 300000 to be added to the existing volume. Click Next. Click Finish. Click Yes to extend the volume to non contiguous free space, the disks must be upgraded to dynamic disks.
Initializing the new disk will prepare it for use and allow you to add it to the existing volumes. Adding the 300000 MB of space to the E drive will provide additional storage for employees. Finally, upgrading to dynamic disks will allow for non-contiguous free space to be used for volume extensions. By following these steps, you'll successfully extend the E drive using 300000 MB on Disk 3 with the GPT partition style.
To know more about GPT partition style visit:
https://brainly.com/question/31757218
#SPJ11
Adding pictures to a word 2019 document will affect the
text positioning
text style
text color
text size
Answers
Find the sum and product of each of these pairs of numbers. Express your answers as a hexadecimal expansion. (a) (1AE)16, (BBC)16(b) (20CBA)16, (A01)16(c) (ABCDE)16, (1111)16(d) (E0000E)16, (BAAA)16
Answers
The hexadecimal expansions of the pairs of numbers are:
(a) D6A and F04E8
(b) 20D5B and 20C3DC1A
(c) ABDEF and A52F02CE
(d) EBAAA8 and B4A4C4DC60
How to determine hexadecimal expansion?To find the hexadecimal expansions of the sum and product of each of these pairs of numbers can be calculated as:
(a)
Sum: 1AE + BBC = D6A
Product: (1AE)(BBC) = F04E8
(b)
Sum: 20CBA + A01 = 20D5B
Product: (20CBA)(A01) = 20C3DC1A
(c)
Sum: ABCDE + 1111 = ABDEF
Product: (ABCDE)(1111) = A52F02CE
(d)
Sum: E0000E + BAAA = EBAAA8
Product: (E0000E)(BAAA) = B4A4C4DC60
Find out more on hexadecimal expansion here: https://brainly.com/question/29958536
#SPJ4
When do you use a for loop instead of a while loop? (There may be more than one answer.)
You know how many times you want the loop to run.
To do number calculations.
To repeat code.
When there is a defined start and end.
Answers
Answer:
- You know how many times you want the loop to run.
- When there is a defined start and end.
Explanation:
Required:
When to use for instead of while loop?
First, it should be noted that both for loop and while loop are used for iteration. However, depending on the scenario; there is preference on one to the other.
The basic syntax of for loop is:
\(for(start;end;condition)\{\}\)
The condition could either be increment or decrement
The basic syntax of while loop is:
\(while(condition)\{\}\)
The condition could be any condition whatsoever
Analyzing the options one after the other.
1. How many times the loop to run.
The for loop is preferred here because of the simplicity of the for loop.
2. & 3. Both the for and while loops are used for code repetition and to perform number calculations
4. Defined start and end.
From the syntax of the for loop
\(for(start;end;condition)\{\}\)
A for loop has a definite start and end in its basic syntax and is more preferable to use instead of a while loop.
Hence, 1 & 4 answer the question
For the network shown below, use two-pass method to determine the critical path, the project duration and each activity's slack time. (All durations shown are in weeks). (1 point)
Answers
The critical path for the network is A-C-E-G-I-K, with a project duration of 18 weeks. The slack time for each activity is as follows: Activity B has a slack time of 0 weeks, Activity D has a slack time of 1 week, Activity F has a slack time of 2 weeks, Activity H has a slack time of 0 weeks, and Activity J has a slack time of 3 weeks.
To determine the critical path, project duration, and slack time for each activity, we use the two-pass method.
First, we calculate the earliest start (ES) and earliest finish (EF) times for each activity. The ES for the first activity is 0, and the EF is the duration of that activity. For subsequent activities, the ES is the maximum EF of all preceding activities, and the EF is ES + duration.
Using this method, we find the following values:
Activity A: ES = 0, EF = 4
Activity B: ES = 4, EF = 4
Activity C: ES = 4, EF = 9
Activity D: ES = 9, EF = 10
Activity E: ES = 10, EF = 15
Activity F: ES = 15, EF = 17
Activity G: ES = 17, EF = 21
Activity H: ES = 4, EF = 4
Activity I: ES = 21, EF = 23
Activity J: ES = 23, EF = 26
Activity K: ES = 26, EF = 30
Next, we calculate the latest start (LS) and latest finish (LF) times for each activity. The LF for the last activity is the project duration, and the LS is LF - duration. For preceding activities, the LF is the minimum LS of all succeeding activities, and the LS is LF - duration.
Using this method, we find the following values:
Activity K: LS = 30, LF = 30
Activity J: LS = 26, LF = 30
Activity I: LS = 21, LF = 26
Activity H: LS = 4, LF = 4
Activity G: LS = 17, LF = 21
Activity F: LS = 15, LF = 17
Activity E: LS = 10, LF = 15
Activity D: LS = 9, LF = 10
Activity C: LS = 4, LF = 9
Activity B: LS = 4, LF = 4
Activity A: LS = 0, LF = 4
Finally, we calculate the slack time (ST) for each activity by subtracting EF from LS. The critical path consists of activities with zero slack time.
Using this calculation, we find the following slack times:
Activity A: ST = 0
Activity B: ST = 0
Activity C: ST = 0
Activity D: ST = 1
Activity E: ST = 0
Activity F: ST = 2
Activity G: ST = 0
Activity H: ST = 0
Activity I: ST = 0
Activity J: ST = 3
Activity K: ST = 0
The critical path for the network is A-C-E-G-I-K, with a project duration of 18 weeks. Activities B, H, and K have zero slack time, meaning any delay in these activities will cause a delay in the overall project. Activities D, F, and J have some slack time available, indicating that they can be delayed without impacting the project's duration.
To know more about network follow the link:
https://brainly.com/question/1326000
#SPJ11
Write a formula, without using named ranges, that would be entered in cell E11. The formula must be easy to replicate. It should display the name of the airport, using the Airport code from cell D11 and the list of Airport names.
Answers
discuss the concepts of total slack (float) and free slack
(float). 400-word minimum count.
Answers
Total slack, also known as float, and free slack, are concepts used in project management to measure the flexibility and scheduling of activities within a project.
Total slack represents the maximum amount of time an activity can be delayed without affecting the project's overall duration, while free slack represents the amount of time an activity can be delayed without delaying the early start of subsequent activities.
Total slack, or float, is a measure of the flexibility of an activity within a project schedule. It represents the amount of time that an activity can be delayed without affecting the overall project duration. Total slack is calculated by determining the difference between the late start and early start times of an activity or the late finish and early finish times of an activity. If an activity has zero total slack, it is considered a critical activity and any delay in its completion will directly impact the project's overall duration. On the other hand, activities with positive total slack can be delayed without causing project delays.
Free slack, also known as free float or independent float, measures the amount of time an activity can be delayed without delaying the early start of subsequent activities. It represents the buffer time available for an activity before it affects the start of the next dependent activity. Free slack is calculated by determining the difference between the early start of the next dependent activity and the early finish of the current activity. If an activity has zero free slack, any delay in its completion will directly impact the start of subsequent activities. Activities with positive free slack have more flexibility in their scheduling as they can be delayed without affecting the start of subsequent activities.
Learn more about project management here:
https://brainly.com/question/31545760
#SPJ11
What are somw pros and cons of a weak cabinet in the country?
Answers
A weak cabinet can enhance checks and balances, increase accountability for individual ministers, and provide flexibility in decision-making processes.
A weak cabinet can distribute power and prevent its concentration, fostering a system of checks and balances within the government. It allows for holding individual ministers accountable for their actions and decisions, as they have more autonomy. Moreover, a weak cabinet offers flexibility in decision-making, enabling ministers to make choices based on their expertise. This can result in more diverse perspectives and adaptability to specific issues.
To know more about enhance click the link below:
brainly.com/question/30205837
#SPJ11
list the first prime minister of St Vincent and the grenadines
Answers
Robert Milton Cato (June 3rd, 1915 - February 10, 1997)
Why PS5 10.2 teraflops is better than 12 teraflops on the Xbox series x?
give me the reason why?
Answers
I really don't know why, but this is a website for homework related problems, not comparing the two new consoles.
PS: I really don't know why.
Decrypt the message NXGQWFSLXG which was encrypted using the affine cipher: f(p)=(11p+5)mod26 Alphabet: A=0,B=1,…,Z=25 Message: You have attempted this problem 2 times. Your overall recorded score is 0%. You have unlimited attempts remaining.
Answers
One can be able to decrypt the entire message "NXGQWFSLXG" as "XJTHDQVZJM".
What is the message about?To decrypt the message "NXGQWFSLXG" that was encrypted using the affine cipher with the given encryption function f(p) = (11p + 5) mod 26, one need to know the inverse function that undoes the encryption process.
Within the relative cipher, the encryption work is f(p) = (a * p + b) mod 26, where "a" and "b" are the key values. To decrypt the message, we got to discover the inverse function of this encryption work.
Learn more about Decryption from
https://brainly.com/question/31177004
#SPJ4
if you need a professional-looking website with many features, you can
Answers
Choose a website building platform and select a suitable template. Customize it to fit your needs, add relevant content, integrate features, optimize for SEO, and launch.
If you need a professional-looking website with many features, you can:
1. Choose a website building platform: Select a platform to create your website. These platforms offer various templates and customization options to help you achieve a professional appearance.
2. Select a suitable template: Browse through the available templates on your chosen platform and select one that matches your desired look and functionality.
3. Customize your template: Modify the template to fit your specific needs by adding your branding, adjusting the layout, and incorporating the desired features.
4. Add relevant content: Populate your website with informative and engaging content, such as text, images, videos, and links to social media profiles.
5. Integrate features and plugins: Use plugins or built-in tools to add desired features, such as contact forms, e-commerce functionality, or event calendars.
6. Optimize for SEO: Implement search engine optimization (SEO) best practices to improve your website's visibility on search engines.
7. Test and launch: Review your website for any issues and ensure it is fully functional before officially launching it.
By following these steps, you can create a professional-looking website with many features tailored to your specific needs.
To learn more about websites visit : https://brainly.com/question/28431103
#SPJ11
3.19 lab: convert from seconds people find it easier to read time in hours, minutes, and seconds rather than just seconds. write a program that reads in seconds as input, and outputs the time in hours, minutes, and seconds. ex: if the input is: 4000 the output is: hours: 1 minutes: 6 seconds: 40
Answers
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
seconds = int(input("Enter time in seconds: "))
hours = int(seconds / 3600)
minutes = int((seconds - (hours * 3600)) / 60)
seconds = seconds - ((hours * 3600) + (minutes * 60))
print("{} hour(s) {} minute(s) {} second(s)".format(hours, minutes, seconds))
*The code is in Python.
Ask the user to enter the time in seconds
Calculate the hours, divide the seconds by 3600 and cast it to the integer
Calculate the minutes, subtract the corresponding seconds in hours you previously found, divide it by 60 and cast the result to the integer
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
Learn more about print here-
https://brainly.com/question/14668983
#SPJ4
The first Web browser that could handle graphics was called which of the following?
a)mosaic
b)bob kahn and vint cerf
c)url
d)all the above
Answers
The first web browser that could handle graphics was called Mosaic. It was developed in 1993 by Marc Andreessen and Eric Bina at the National Center for Supercomputing Applications (NCSA) at the University of Illinois, Urbana-Champaign.
Mosaic was the first browser to display images inline with text instead of requiring users to click on a separate link to view the image. It was also the first browser to offer a graphical user interface and support for multiple operating systems, making it widely accessible to users across different platforms.Mosaic was a game-changer in the early days of the internet and paved the way for the modern web.
Its success led to the development of other web browsers, including Netscape Navigator and Internet Explorer. Today, there are numerous web browsers available for users to choose from, including Chrome, Firefox, Safari, and Edge. Each browser has its unique features and capabilities, but they all owe their existence to Mosaic, the browser that revolutionized the way we access and interact with the internet.
To know more about Supercomputing Applications visit:
https://brainly.com/question/28484249
#SPJ11
What is a geostationary satellite and what makes them special.
Answers
Answer: See explanation
Explanation:
A geostationary satellite is a satellite above the equator at an altitude of 22300 miles. It should be noted that it revolves exactly the same way the Earth does.
It is essential as it is used in the provision of infrared and visible images about the surface of the Earth which in turn is used for oceanography and also to observe the weather. Examples are
Fengyun of China, Geostationary Operational Environmental Satellite of USA, Himawari of Japan etc.
which of the following is not a variable data type default to the c language? group of answer choices short real int float
Answers
Short real is not a variable data type default to the c language.
What are Data Types?
Data types are categories of data that determine the type of operations that can be performed on it and the type of values it can possess. They are used to classify data into different categories and are important in designing computer programs. Examples of data types include text, numbers, boolean values, dates, and times. Text data types are used to store words, phrases, and sentences. Numbers data types are used to store numerical values such as integers, floating-point numbers, and decimals. Boolean values are used to store true or false data.
To know more about Data types
https://brainly.com/question/30459199
#SPJ4
Write a program that inserts 25 random integers from 0 to 100 in order into a LinkedList object.The program must:• sort the elements,• then calculate the sum of the elements, and• calculate the floating-point average of the elements.Utilizing Java htp 10 late objects approach
Answers
Answer:
Written in Java
import java.util.Collections;
import java.util.Random;
import java.util.LinkedList;
class Main {
public static void main(String[] args) {
LinkedList<Integer> myList = new LinkedList<Integer>();
Random rand = new Random();
int randnum;
int sum = 0;
for(int i = 0;i<25;i++) {
randnum = rand.nextInt(101);
myList.add(new Integer(randnum));
sum+=randnum;
}
Collections.sort(myList);
System.out.println(myList);
System.out.println("Average: "+(float)sum/25);
}
}
Explanation:
import java.util.Collections;
import java.util.Random;
import java.util.LinkedList;
class Main {
public static void main(String[] args) {
This declares a linkedlist as integer
LinkedList<Integer> myList = new LinkedList<Integer>();
This declares random variable rand
Random rand = new Random();
This declares randnum as integer
int randnum;
This declares and initializes sum to 0
int sum = 0;
The following iteration generates random numbers, inserts them into the linkedlist and also calculates the sum of the generated numbers
for(int i = 0;i<25;i++) {
randnum = rand.nextInt(101);
myList.add(new Integer(randnum));
sum+=randnum;
}
This sorts the list
Collections.sort(myList);
This prints the list
System.out.println(myList);
This calculates and prints a floating-point average
System.out.println("Average: "+(float)sum/25);
}
}
The program that inserts 25 random integers from 0 to 100 in order into a LinkedList and sort the elements, and then calculate the sum of the elements, and calculate the floating-point average of the elements is represented below:
import random
linkedList = []
for i in range(0, 25):
random_number = random.randint(0, 100)
linkedList.append(random_number)
sort = sorted(linkedList)
add = sum(sort)
average = add / len(sort)
print(sort)
print(add)
print(average)
The code is written in python.
An empty variable linkedList is declared and an empty list is stored in it.
we loop through a value from range 0 to 25.
Then get a random of 0 to 100.
The random 25 numbers are appended to the empty list linkedList.
The linkedList are then sorted and stored in a variable sort.
The sorted numbers are summed and stored in the variable add.
The floated average of the number is calculated and stored in the variable average.
The sorted numbers, sum and floated average are printed out.
The bolded value of the code are python keywords.
read more: https://brainly.com/question/18684565?referrer=searchResults

when configuring nat on a cisco router, what is the inside local ip address?
Answers
When configuring Network Address Translation (NAT) on a Cisco router, the Inside Local IP address refers to the private IP address assigned to a device within your internal network. This IP address is used for communication within the local network and is translated by NAT when accessing the internet. Here's a step-by-step explanation:
1. Identify the private IP address assigned to a device within your internal network. This is your Inside Local IP address.
2. Configure NAT on your Cisco router to perform the translation from the Inside Local IP address to an Inside Global IP address (a publicly routable IP address) when accessing the internet.
3. Configure the appropriate NAT rules, such as static or dynamic NAT, to map the Inside Local IP addresses to Inside Global IP addresses.
4. Save and apply the configuration to enable NAT on your Cisco router.
Know more about inside local ip address, here:
https://brainly.com/question/29590738
#SPJ11
Please! I need help matching this.
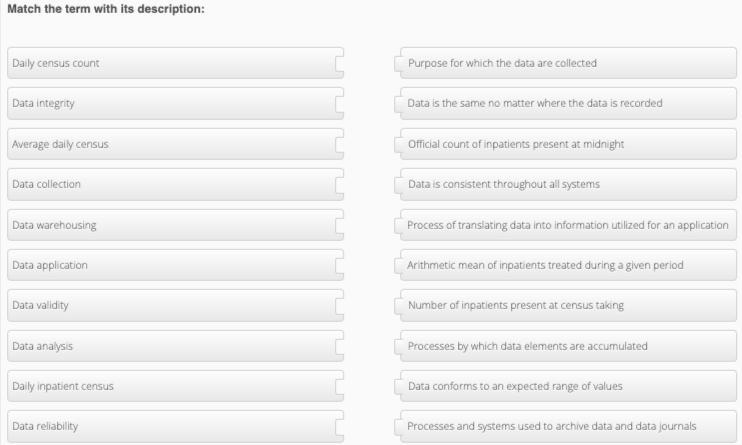
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1