The most basic moral question involved in stem cell research is
a. what constitutes human life.
b. who "owns" the embryo.
c. the use to which the results of the research will be applied.
d. who will benefit from the research.
Answers
The most basic moral question involved in stem cell research is what constitutes human life. The study of stem cells' characteristics and possible applications in medicine is known as stem-cell research. Understanding stem cells' characteristics aids in our comprehension of how the development and homeostasis of the healthy and diseased body occur. Stem cells are the origin of all tissues.
What exactly is considered human life in the context of stem cell research is the most fundamental moral concern. This is because the use of embryonic stem cells involves the destruction of an embryo, which some argue is equivalent to ending a human life. Therefore, there is much debate surrounding the ethical implications of using embryonic stem cells for research purposes. It is important to consider both the potential benefits of stem cell research for medical advancements as well as the ethical concerns surrounding the use of embryos in this research. Ultimately, the decision about the use of embryonic stem cells must balance these competing interests and considerations.
To know more about stem cell research :
https://brainly.com/question/15093865
#SPJ11
The most basic moral question involved in stem cell research is what constitutes human life.
What exactly is considered human life in the context of stem cell research is the most fundamental moral concern. This is because the use of embryonic stem cells involves the destruction of an embryo, which some argue is equivalent to ending a human life. Therefore, there is much debate surrounding the ethical implications of using embryonic stem cells for research purposes. It is important to consider both the potential benefits of stem cell research for medical advancements as well as the ethical concerns surrounding the use of embryos in this research. Ultimately, the decision about the use of embryonic stem cells must balance these competing interests and considerations.
To know more about stem cell research :
brainly.com/question/15093865?
#SPJ11
Related Questions
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
Which of the following is NOT correct?
A. Computer is capable of processing only
digital signals.
B. Appropriate software is required for
processing the data.
C. Computer is capable of processing digital
as well as analog signals.
D. Computer is capable of analyzing both
quantitative and qualitative data.
Answers
Answer:A
Explanation:
resource limitations of smartphones, including limited screen size, help explain the popularity of question 3 options: web browsers. magnifying glasses. desktop computers. mobile apps. docs.
Answers
Smartphones have limited screen size, so web browsers, mobile apps, and docs are all popular options for users because they are designed to fit the smaller screen size.
Smartphones have limited screen sizeMagnifying glasses are also popular because they allow users to easily zoom in and out on text or images.Desktop computers are not as popular, because they require more space and resources.The limited screen size of smartphones can make it difficult to view content, so web browsers provide a solution by allowing users to access the internet.Web browsers use a zoom feature to allow users to enlarge the page, making it easier to read text and interact with content.Magnifying glasses are another popular option for those who need to zoom in on small texts or images.Desktop computers, on the other hand, offer a much larger screen and allow for more efficient multitasking.Mobile apps are also gaining popularity as they provide users with the convenience of accessing content on the go.Finally, documents such as PDFs are often used to share content that requires a magnifying glass to read.All of these options provide a solution to the limited screen size of smartphones, making them all popular choices for those with this issue.To learn more about Smartphones have limited screen size refer to:
https://brainly.com/question/5014488
#SPJ4
Danielle wants to record a voice-over to add to a presentation. Other than a microphone, what does danielle need to record the audio?.
Answers
Answer:
Sound recorder software
Explanation:
Pls answer this
The figure above is a type of thread known as
A. Acme thread B. Buttress thread
C. Square thread D. Vee thread

Answers
Answer:
It looks like an Acme thread.
Explanation:
Convert decimal number to octal
(76)decimal
Answers
Answer:
76 is 114 in octal form
Explanation:
Step 1: Divide (76)10 successively by 8 until the quotient is 0:
76/8 = 9, remainder is 4
9/8 = 1, remainder is 1
1/8 = 0, remainder is 1
Step 2: Read from the bottom (MSB) to top (LSB) as 114.
So, 114 is the octal equivalent to the decimal number 76 (Answer).
Accounts Receivable/Highland School and Accounts Receivable/Sam Jones are both classified as?
Answers
Answer: Current Assets or just Assets
Explanation:
Accounts Receivables refer to those that purchased goods or services from the business but have not paid for them i.e. they purchased the goods on credit. They therefore owe the business.
They are classified as assets to the business because they represent money that will come into the business and they are classified as current assets because they will pay the money within the period.
Question 1:
An output device sends data to a computer.
True
False
Question 2:
An input device receives data from a computer
True
False
Answers
Answer:
1) False
2) False
Explanation:
I don't mean to be rude or anything but, how do you not know the answer to this question? You can even look it up online and you will get an answer.
Input sends data because it goes IN your pc.
Output receives data because it goes OUT of your computer.
Corinne would like to click on the link at the bottom of a Web page but she only sees the top portion of the page. She should _____. A.click twice on the status bar
B.use the scroll bar to scroll down to the bottom of the page
C.click on the back button
D.click on the display window and drag it up
Answers
Answer:
B
Explanation:
from 3dg3
Answer:
D.click on the display window and drag it up
your public cloud provider has located an availability zone data center in a large industrial park with no company signage, deployed extensive video cameras around the property, erected tall security fences, and deployed biometrics at the guard shack. what type of security is the cloud provider implementing?
Answers
The public cloud provider is implementing physical security measures to protect the availability zone data center.
These measures include deploying video cameras, tall security fences, and biometrics at the guard shack to prevent unauthorized access to the data center. By locating the data center in a large industrial park with no company signage, the cloud provider is also implementing the concept of "security through obscurity." This approach aims to increase security by making it difficult for potential attackers to locate and identify the data center. Overall, the cloud provider is implementing a comprehensive physical security strategy to protect the confidentiality, integrity, and availability of the data center and the resources hosted within it.
To learn more about physical security
https://brainly.com/question/30295176
#SPJ11
a binary cycle geothermal system uses a heat exchanger and two different fluids
Answers
A binary cycle geothermal system generates electricity using a heat exchanger and two different fluids
How does binary cycle geothermal work?A binary cycle geothermal system is a geothermal power plant that employs a heat exchanger and two different fluids for energy conversion. Geothermal fluid, such as hot water or steam, is extracted from underground reservoirs and passed through a heat exchanger. In the heat exchanger, the geothermal fluid transfers its heat to a secondary working fluid, known as the binary fluid, which has a lower boiling point.
The binary fluid vaporizes, driving a turbine connected to a generator to produce electricity. The vaporized binary fluid is then condensed back into a liquid state and circulated back to the heat exchanger to repeat the cycle. This approach allows for efficient utilization of lower-temperature geothermal resources in electricity generation.
Learn more about binary cycle
brainly.com/question/29749798
#SPJ11
Which of the following is an object-oriented programming language?
- Ada
- COBOL
- Pascal
- Python
Answers
Explanation:
This is the correct answer
pythonAnswer:
[D] Python
Explanation:
With the exception of control flow, everything in Python is an object.
Thus, python is an object-oriented programming language.
~Learn with Lenvy~
What is the output of this program? Assume the user enters 3, 6, and 11.
numA = 0
for count in range(3):
answer = input ("Enter a number: ")
fltAnswer = float(answer)
numA = numA + fltAnswer
print (numA)
Output:
Answers
Answer:
Output: 23.0
Explanation:
1) numA += 3; (3)
2) numA += 9 (12) #3 + 9 = 12
3) numA += 11 (23) #12 + 11 = 23
float(23) = 23.0
Answer: 20
Explanation:
it is a basic python code
fitAnswer intoduses loop into the given variable
==> intial A=[0]
after addind 3
A=[0,3]=0+3=3
A=[0,3,6]=0+3+6=9
A=[0,3,6,11]=0+3+6+11=20
Rafi is developing an application to send urgent information about global health crises over the Internet to hospitals. He is worried about packets getting lost along the way and the effect that will have on the accuracy of the information. What is his best option for dealing with lost packets
Answers
Answer:
Rafi can use the Transmission Control Protocol for communication since TCP has ways to recover when packets are lost.
Explanation:
TCP is a data transport protocol that works on top of IP and includes mechanisms to handle lost packets, such as the retransmission of lost packets.
what are the answers for these question?




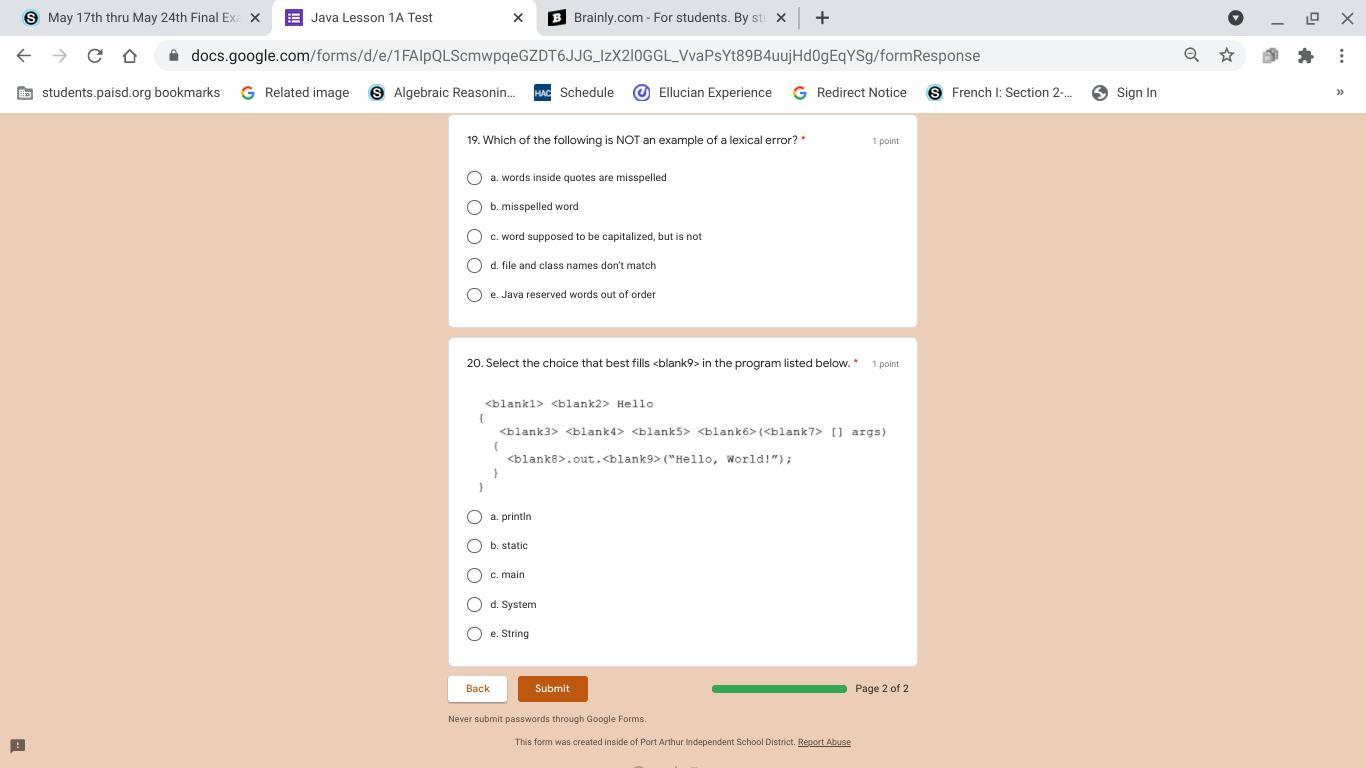
Answers
Answer:
tbh u gotta give more points in order for me to solve that:)
Explanation:
Which are characteristics of flowcharts? Choose all that apply.
1. use numbers to outline steps
2. are graphical representations of the set of instructions used to solve a problem
3. use predefined symbols
4. can be used to communicate the solution to a problem
Answers
The characteristics of flowcharts are presented for options: 2, 3 and 4. Therefore, flowcharts are graphical representations of the set of instructions used to solve a problem from predefined symbols. Moreover, they can be used to communicate the solution to a problem.
Flowcharts
The flowchart is a diagram that indicates the steps and the sequence of a process. Hence, it allows understanding of the beginning and the end of a set of tasks, from specific symbols such as boxes, flow lines, arrows, and others.
The flowcharts are used for the definition, the standardization, the communication, the solution, and the improvement of a process.
According to the previous definition, the characteristics of flowcharts are presented below:
they represent graphically the set of instructions used to solve a problem;they use predefined symbols;they can be used to communicate the solution to a problem.Learn more about the flowchart here:
https://brainly.com/question/6532130
Answer:
1 2 and 4 are right :)
Explanation:
Trust me

You are a robot in an animal shelter, and must learn to discriminate Dogs from Cats. You are given the following training data set.
Example Sound Fur Color Class
Example #1 Meow Coarse Brown Dog
Example #2 Bark Fine Brown Dog
Example #3 Bark Coarse Black
Do
1) Which attribute would information gain choose as the root of the tree?
2) Draw the decision tree that would be constructed by recursively applying information gain to select roots of sub-trees.
3) Classify the following new example as Dog or Cat using your decision tree above. What class is [Sound=Bark, Fur=Coarse, Color=Brown]?
Show transcribed image text
Example Sound Fur Color Class Example #1 Meow Coarse Brown Dog Example #2 Bark Fine Brown Dog Example #3 Bark Coarse Black Dog Example #4 Bark Coarse Black Dog Example #5 Meow Fine Brown Cat Example #6 Meow Coarse Black Cat Example #7 Bark Fine Black Cat Example #8 Meow Fine Brown Cat
Answers
Answer:
1. The attribute that information gain would choose as the tree's root is Sound. This is because the information gain of Sound is 0.75, which is higher than the information gain of Fur (0.5) and Color (0.25).
2. The decision tree that would be constructed by recursively applying information gain to select roots of sub-trees is as follows:
```
Root: Sound
* Meow: Cat
* Bark:
* Fine: Dog
* Coarse: Dog
```
3. The new example [Sound=Bark, Fur=Coarse, Color=Brown] would be classified as Dog. This is because the decision tree shows that all dogs bark and all dogs with coarse fur are dogs.
Here is a more detailed explanation of how the decision tree is constructed:
1. The first step is to calculate the information gain of each attribute. The information gain of an attribute is a measure of how much information about the class is contained in that attribute. The higher the information gain, the more valuable the point is for classification.
2. The attribute with the highest information gain is chosen as the tree's root. In this case, the attribute with the highest information gain is Sound.
3. The data is then partitioned into two groups based on the value of the root attribute. In this case, the data is partitioned into two groups: dogs and cats.
4. The process is then repeated recursively for each group. In this case, the process is repeated for the dogs and the cats.
5. The process continues until all of the data has been classified.
The decision tree is a powerful tool for classification. It can be used to classify data that is not linearly separable. In this case, the data is not linearly separable because there are dogs that bark and cats that meow. However, the decision tree can classify the data correctly using the information gained from each attribute.
Click on the arrow in A. What will enable you to do?
Answers
Answer:
We need a picture
Explanation:
Need the answer ASAP!!!!!!!!
I’ll mark brainliest if correct
Drag each label to the correct location on the image. Match the correct component to the part on the flowchart
Procedure 1
subroutine
procedure 2
decision
input
End
Start

Answers
Answer:
Start
subroutine
imput
decision
Procedure 1
procedure 2
End
Explanation:
When adding a new record, which key can be pressed to move to the next field?
O Alt
Ctrl
O Shift
O Tab
Answers
Answer:
O Tab
Explanation:
In order to add a new record the key that should be used to move to the next field is tab key
while the other keys are used for the other purpose
But for adding a new field, new record, a tab key should be used
Therefore the last option is correct
Select the correct answer from each drop down menu
What computing and payment model does cloud computing follow?
Cloud computing allows users to ____ computing resources and follows the ___________ payment model
First blank choices are
1. Buy
2. Own
3. Rent
4. Sell
Second blank choices are
1. Pay as you go
2. Pay anytime anywhere
3. Pay once use multiple times
Answers
Answer:
buy and pay as you go
Explanation:
Create a Python program that prints all the numbers from 0 to 4 except two distinct numbers entered by the user. Note : Use 'continue' statement. If user input is
```
3
2
```
Expected Output :
'0 1 4'
"""
Answers
Here's a Python program that accomplishes the given task using the 'continue' statement:
python
Copy code
def print_numbers_except_two(num1, num2):
for num in range(5):
if num == num1 or num == num2:
continue
print(num, end=' ')
# Get user input for the two distinct numbers
num1, num2 = map(int, input("Enter two distinct numbers: ").split())
# Print the numbers from 0 to 4 excluding the two entered numbers
print_numbers_except_two(num1, num2)
The program defines a function print_numbers_except_two that takes two parameters num1 and num2. It then uses a for loop to iterate over the range of numbers from 0 to 4 (inclusive). Within the loop, an `if
Learn more about Python program here; brainly.com/question/28248633
#SPJ11
Where does the revolver get the IP address of a site not visited before?
the file server
the name server
the IP provider
the print spooler
Answers
Answer: The name server
Explanation:
Nameservers are part of a large database called the Domain Name System (DNS), which acts like a directory for devices and the IP addresses attached to them. What nameservers do is use this information to translate domain names into numerical IP addresses – the language our computers understand
Joel needs to write a research paper. What is the best application to use?
Answers
Answer: Britannica High School
Explanation:
https://school-eb-com.content.elibrarymn.org/levels/high
Answer:
g
o
o
g
l
e
s
h
e
e
t
s
Explanation:
Mail Tips can be displayed on the top of the message address bar for different circumstances, such as
automatic replies when the recipient is
and can refer the sender to another
a moderated group where the message requires
before it can be sent to the recipients.
Answers
Answer:
automatic replies when the recipient is
✔ out of the office
and can refer the sender to another
✔ recipient
.
a moderated group where the message requires
✔ approval
before it can be sent to the recipients.
Explanation:
got it right on edge 2020-2021
Automatic replies when the recipient is out of the office and can refer the sender to another recipient. A moderated group where the message requires approval. Before it can be sent to the recipients.
What are office gestures?In the workplace, gestures can communicate a lot of information without the speaker ever saying a word. Employees respond to other people's body language as perceived at work.
Interactions at work are influenced by facial expressions, eye contact, and touch. Some refer to it as body language. Some refer to it as kinesics. A gesture is a visible body activity that conveys specific messages in place of or in addition to words. It is a type of nonverbal or nonvocal communication.
Therefore, Automatic responses can direct the sender to another destination if the intended recipient is unavailable. A discussion forum where messages must be approved. Before the recipients can receive it.
To learn more about office gestures, refer to the link:
https://brainly.com/question/25547729
#SPJ2
Points 10 Score No.3. Select an e-commerce company that has participated in an incubator program such as Y Combinator, Startupbootcamp, Seedcamp, or INITS, or another of your choosing, and write a short report on its business model and the amount and sources of capital it has raised thus far. Include your views on the company's future prospects for success. Then create an elevator pitch for the company.
Answers
E-commerce companies that have participated in an incubator program are companies that are just starting up and need assistance to grow. For instance, Y Combinator, Startupbootcamp, Seedcamp, or INITS are incubator programs that provide support to new businesses.
The company I have chosen for this report is a business that has participated in an incubator program, namely, Y Combinator. The business model of the company is an online retail store that sells a variety of products. They offer their services to customers worldwide. The website is user-friendly, and customers can easily navigate to find what they need. The company's primary source of capital was from investors. To date, they have raised $10 million in seed capital from venture capitalists. This money was used to expand the business by improving its website and hiring more employees. The company has good prospects for success in the future. They have a well-organized business model and a clear vision of what they want to achieve. They have an excellent team of professionals who are passionate about the business, and they are continually working to improve their services.
The Elevator Pitch for the company:
Are you tired of struggling to find the products you need? Look no further than our online retail store. We offer a wide variety of products to customers worldwide. Our user-friendly website makes it easy to find what you need quickly. With $10 million in seed capital from venture capitalists, we have been able to expand our business and improve our services. We have a clear vision of what we want to achieve, and we are continually working to improve our services. Try us out today and experience a new level of online shopping!
To learn more about e-commerce click on,
brainly.com/question/31765401
#SPJ11
according to _______, "responding within 24 hours is a good rule of thumb," in regard to handling negative reviews on social media.
Answers
According to experts in the field of social media management and customer service, responding within 24 hours is a good rule of thumb when handling negative reviews on social media. This is because social media users tend to expect a prompt response to their comments, questions, and concerns, especially when they are voicing a complaint or expressing dissatisfaction with a product or service.
By responding quickly and professionally to negative reviews, companies can demonstrate that they take customer feedback seriously and are committed to providing a high level of customer service.
However, it is also important to remember that responding quickly does not mean responding impulsively or defensively. It is important to take the time to read and fully understand the negative review, empathize with the customer's perspective, and formulate a thoughtful, constructive response. This can involve acknowledging the customer's concern, apologizing for any inconvenience or frustration they may have experienced, and offering a potential solution or next steps.
By taking a customer-centric approach to social media management, companies can not only address negative reviews in a timely and effective manner but also build stronger relationships with their customers over time. This can help to improve brand reputation, increase customer loyalty, and ultimately drive business growth and success.
To know more about management visit:
https://brainly.com/question/32216947
#SPJ11
_ clouds are more suitable for organizations that want to offer standard applications over the Web, such as e-mail, with little involvement by IT managers.
a.
Public
b.
Private
c.
Community
d.
Hybrid
Answers
The main answer to your question is option A, public clouds. Public clouds are managed by third-party providers and offer standard applications over the Web, making them a more suitable option for organizations that want to offer services such as e-mail without involving IT managers. This is because the provider takes care of maintenance, security, and upgrades, leaving IT managers with little involvement.
Public clouds are a type of cloud computing model where the infrastructure and services are provided by a third-party provider over the Internet. They are accessible to anyone who wants to use them and are usually offered on a pay-per-use basis. Public clouds are ideal for organizations that want to offer standard applications, such as e-mail, with little involvement by IT managers.
In a public cloud, the provider is responsible for managing the infrastructure, including maintenance, security, and upgrades. This makes it a more cost-effective solution for organizations that don't have the resources or expertise to manage their own IT infrastructure. Additionally, public clouds offer scalability and flexibility, allowing organizations to easily add or reduce resources as needed.
In contrast, private clouds are typically used by organizations that want more control over their IT infrastructure. Community clouds are shared by several organizations with similar needs, while hybrid clouds combine the features of both public and private clouds.
Learn more about standard applications:
https://brainly.com/question/29563268
#SPJ11
What type of camera is a cell phone camera? A.) DSLR B.) manual C.) compact D.) zoom
Answers
Answer:
The correct option is;
D.) Zoom
Explanation:
The six types of camera found on smart phones includes the monochrome, macro camera, ultra-wide camera, periscope zoom camera, the main phone camera, and the depth sensor camera
The zoom cameras on smart phones can be found mainly in the top range models of smart phones due to the costs of the camera components including the sensor.
Smart phones also have digital zooming that make use of the high mega pixels that come with the phone.
need to do this function for a calculator in visual studio. pls provide de code in c programing
Complex Numbers Multiplication
Answers
To perform the function of Complex Numbers Multiplication in C programming, the following code can be used:```#include struct complex{ float real; float imag;};int main() { struct complex a, b, c; printf("Enter real and imaginary parts of first complex number: ")
scanf("%f %f", &a.real, &a.imag); printf("Enter real and imaginary parts of second complex number: "); scanf("%f %f", &b.real, &b.imag); c.real = a.real*b.real - a.imag*b.imag; c.imag = a.real*b.imag + a.imag*b.real; printf("Multiplication of two complex numbers = %.2f + %.2fi", c.real, c.imag); return 0;}```Explanation:The above program includes a structure called ‘complex’. A structure is a user-defined data type in C/C++. The structure complex contains two float variables real and imag.
These variables will store the real and imaginary parts of the complex number. We declared three variables of struct complex data type a, b and c. The variables a and b will store the two complex numbers whose multiplication is to be performed. And the variable c will store the multiplication of a and b.We first prompt the user to enter the real and imaginary parts of the two complex numbers a and b.
To know more about C programming visit:
https://brainly.com/question/14338673
#SPJ11