T/F. one reason to apply one transition to one slide and a different transition to all of the other slides in the presentation is to draw attention to the slide that has a different transition applied to it.
Answers
Applying one transition to one slide and another transition to all of the other slides in the presentation draws attention to the slide with the different transition, So the given statement is true.
What is transition in a presentation?During a presentation, a slide transition is the visual effect that occurs when you move from one slide to the next. Transition effects can be customized in terms of speed, sound, and appearance. Slide transitions improve the slideshow's professional appearance and draw attention to specific important slides.Most commonly used transition is fade. Many seasoned presenters rely on this tried-and-true classic. It's easy to understand why. A pleasing fade transition among slides is usually all you need, and only that hint of motion and gradient provides a lot of texture.Animation can help us make a PowerPoint presentation more dynamic, and actually make information more memorable. Entrances and exits are the most common types of animation effects. You can also use sound to enhance the impact of your animation effects.To learn more about presentations refer to :
https://brainly.com/question/23714390
#SPJ4
Related Questions
PLEASE QUICK IM TIMED.
Write a program that assigns the value 14 to a variable. Then print out the type of the variable. What will the output of the program be?
Answers
This is for Python
Code:
variable = 14
print(type(variable))
Output:
<class 'int'>
states that processing power for computers would double every two years
Answers
Answer:
Moore's Law
Explanation:
implement the fcfs (non preemptive) cpu scheduling algorithm. use any programming language. the code will be submitted with the report. simulate and evaluate with the set of processes described below. for each algorithm (fcfs, sjf, and mlfq) calculate the cpu utilization, response time (rt) per process and average, waiting time (wt) per process and average, and turnaround time (tt) per process and average.
Answers
Yes, I'm willing to assist you in putting the FCFS (First-Come, First-Serve) scheduling method into practise. Here is a Python implementation of the algorithm.
How would you define the non-preemptive nature of the FCFS scheduling algorithm?On a first-come, first-served basis, jobs are completed. A preemptive, non-preemptive scheduling approach is used. Simple to comprehend and use. The implementation makes use of a FIFO queue.
class Process:def __init__(self, pid, arrival_time, burst_time):
self.pid = pid
self.arrival_time = arrival_time
self.burst_time = burst_time
self.start_time = None
self.completion_time = None
def fcfs(processes):
"""FCFS (First-Come, First-Serve) scheduling algorithm"""
n = len(processes)
current_time = 0
waiting_time = 0
turnaround_time = 0
response_time = 0
for i in range(n):
# Set start time of the process
if current_time < processes[i].arrival_time:
current_time = processes[i].arrival_time
processes[i].start_time = current_time
# Update waiting time, response time and current time
waiting_time += current_time - processes[i].arrival_time
response_time += current_time - processes[i].arrival_time
current_time += processes[i].burst_time
# Set completion time of the process
processes[i].completion_time = current_time
# Update turnaround time
turnaround_time += current_time - processes[i].arrival_time
# Determine the average turnaround, response, and waiting times.
avg_waiting_time = waiting_time / n
avg_response_time = response_time / n
avg_turnaround_time = turnaround_time / n
# Calculate CPU utilization
total_burst_time = sum(process.burst_time for process in processes)
cpu_utilization = total_burst_time / current_time
# Return the results
return (avg_waiting_time, avg_response_time, avg_turnaround_time, cpu_utilization)
To know more about Python visit:-
https://brainly.com/question/30427047
#SPJ1
How can a company that collects and uses private customer data ensure it will move forward in a sustainable culture of privacy?
Select an answer:
1- by creating a culture of privacy in every facet of the company's operations
2- by developing an internal data privacy policy that can apply to all current and new products
3- by asking the hard questions, and struggling to get the right answers
4- by making sure the privacy policies provided to customers are up-to-date
Answers
The company that collects and uses private customer data will need to ensure that it will move forward in a sustainable culture of privacy if they act by:
Option 1: creating a culture of privacy in every facet of the company's operations.Option 4- by making sure the privacy policies provided to customers are up-to-date.What is Data Protection and Privacy?The terms data protection and data privacy is known to be one that is said to be used a lot and also interchangeably.
Note that Data privacy is one that tells about who has the ability or permission to access to data, and data protection is one that gives tools and policies to be able to restrict access to the data.
Hence, The company that collects and uses private customer data will need to ensure that it will move forward in a sustainable culture of privacy if they act by:
Option 1: creating a culture of privacy in every facet of the company's operations.Option 4- by making sure the privacy policies provided to customers are up-to-date.Learn more about privacy policies from
https://brainly.com/question/13335106
#SPJ1
1. The US Constitution establishes that only a natural born citizen who is at least thirty-five years of age is eligible to be President of the US (Article 2/section 1). Create a Java program to help a user determine if s/he is eligible to be President. (Use Dialog boxes for input/output).
Answers
Answer:
import javax.swing.JOptionPane;
public class PresidentEligibility {
public static void main(String[] args) {
String ageInput = JOptionPane.showInputDialog("Please enter your age:");
int age = Integer.parseInt(ageInput);
String citizenshipInput = JOptionPane.showInputDialog("Please enter your citizenship status:");
String citizenship = citizenshipInput.toLowerCase();
if(age >= 35 && citizenship.equals("natural born citizen")) {
JOptionPane.showMessageDialog(null, "You are eligible to be President!");
} else {
JOptionPane.showMessageDialog(null, "Sorry, you are not eligible to be President.");
}
}
}
Thale cress is a plant that is genetically engineered with genes that break down toxic materials. Which type of organism is described?
recombinant
transgenic
transverse
restriction
Answers
Answer: Transgenic
Explanation:
Since the thale cress is a plant that is genetically engineered with genes that break down toxic materials, the type of organism that is described here is the transgenic plant.
Transgene is when a gene is naturally transferred or transferred from an organism to another organism by genetic engineering method.
Therefore, the correct option is transgenic.
Answer:
The answer is B (transgenic)
Explanation:
What is a business proposal? Select one.
Question 5 options:
A request for approval that has been solicited by an external party
Documents designed to make a persuasive appeal to the audience to achieve a defined outcome, often proposing a solution to a problem
A letter from a CEO discussing the organization’s vacation policy
A statement listing the organization’s profits and losses for the year
Answers
Answer:
Documents designed to make a persuasive appeal to the audience to achieve a defined outcome, often proposing a solution to a problem
Documents designed to make a persuasive appeal to the audience to achieve a defined outcome, often proposing a solution to a problem
Use a method from the JOptionPane class to request values from the user to initialize the instance variables of Election objects and assign these objects to the array. The array must be filled.

Answers
To use the JOptionPane class in Java to request values from the user and initialize instance variables of Election objects and assign them to an array, you can follow the steps given in the image:
What is the JOptionPane class
The code uses JOptionPane. showInputDialog to show a message box and get information from the user. IntegerparseInt changes text into a number.
After completing a process, the elections list will have Election items, and each item will have the information given by the user.
Learn more about JOptionPane class from
brainly.com/question/30974617
#SPJ1

steps to copy and paste text/information from website to Ms-word using keyboard
Answers
Answer: Highlight the text you want to copy. Use the shortcut key combination Ctrl + C on a PC or Command + C on a Mac to copy the text. Move the text cursor to where you want to paste the text. Press Ctrl + V on a PC or Command + V on a Mac to paste the text
Explanation:
just copy and past by highlighting the text you want and clicking ctrl and c at the same time then ctrl and v to put it on word
write an algorithm and draw a flowchat that show the steps involved in determining the grade of a student in letters in E.T.U SL. if it is already known in number Hint: 75-10-A, 65-74= 3, 50-64 = C 30-49 = 0, 20-29 = E and
Answers
Algorithm to determine student grade in letters:
The Input and Outputscore obtained by the student (out of 100)
Output:
grade in letter format
Step 1: Check if the score obtained is within the range of 0 to 100. If not, output "Invalid score" and exit the algorithm.
Step 2: If the score is within the range of 75 to 100, output "A".
Step 3: If the score is within the range of 65 to 74, output "B".
Step 4: If the score is within the range of 50 to 64, output "C".
Step 5: If the score is within the range of 30 to 49, output "D".
Step 6: If the score is within the range of 20 to 29, output "E".
Step 7: If the score is within the range of 0 to 19, output "F".
The Flowchart
Start
|
V
[Input score]
|
V
Is score valid? ----> No -----> [Output "Invalid score"]
|
Yes
|
V
Score >= 75? ----> Yes ----> [Output "A"]
|
No
|
V
Score >= 65? ----> Yes ----> [Output "B"]
|
No
|
V
Score >= 50? ----> Yes ----> [Output "C"]
|
No
|
V
Score >= 30? ----> Yes ----> [Output "D"]
|
No
|
V
Score >= 20? ----> Yes ----> [Output "E"]
|
No
|
V
[Output "F"]
|
V
End
Read more about algorithms here:
https://brainly.com/question/24953880
#SPJ1
How could you use a spreadsheet you didn't like to simplify access also the problem
Answers
Explanation:
......
complete the expression so that userpoints is assigned with 0 if useritems is greater than 20 (second branch). otherwise, userpoints is assigned with 10 (first branch).
Answers
The expression provided is an example of a ternary operator, which is a type of operator that takes three operands.
userpoints = (useritems > 20 ? 0 : 10);In this case, the first operand is the comparison of useritems being greater than 20, the second operand is the value that should be assigned to userpoints if the comparison is true (in this case 0), and the third operand is the value that should be assigned to userpoints if the comparison is false (in this case 10). The expression 'userpoints = (useritems > 20 ? 0 : 10);' is complete and assigns 0 to userpoints if useritems is greater than 20, otherwise it assigns 10 to userpoints.
Learn more about programming: https://brainly.com/question/26134656
#SPJ4
What type of 3-phase connection requires only two transformers?
Answers
The use of two single-phase transformers to step down a high 3-phase voltage to a lower 3-phase voltage is possible using a rudimentary configuration dubbed an "open delta."
What is a single-phase transformer?For industrial applications, three phase transformers perform significantly better. Most heating, air conditioning, lighting, and house applications employ single phase systems in residential settings. When compared to low-power industrial systems and machines, they are less productive. A specific type of transformer called a single phase transformer functions using only one phase of power. This device carries electrical power from one circuit to another by the mechanism of electromagnetic induction. It is a passive electrical device. A transformer cannot change single-phase electricity into three-phase power, even if single-phase power can be produced from a three-phase power source. Phase converters or variable frequency drives are needed to convert single-phase electricity to three-phase power.To learn more about single phase transformers, refer to:
https://brainly.com/question/29665451
A trace table is used for
Answers
Answer:
Trace tables are used to allow programmers to trace the value of variables as each line of code is executed.
Explanation:
The values of the variables are displayed in a table and assist the programmer in identifying any potential errors.
Answer:
Trace tables can enable a programmer to trace the values of variables as each line is executed/processed/ran through the program. And yes, can aid programmers to identify potential errors in the code.
Explanation:
Question 10 of 10
What information system would be most useful in determining what direction
to go in the next two years?
A. Decision support system
B. Transaction processing system
C. Executive information system
D. Management information system
SUBMIT
Answers
Answer: C. Executive information system
Explanation: The information system that would be most useful in determining what direction to go in the next two years is an Executive Information System (EIS). An EIS is designed to provide senior management with the information they need to make strategic decisions.
An Executive Information System (EIS) would be the most useful information system in determining what direction to go in the next two years. So, Option C is true.
Given that,
Most useful information about determining what direction to go in the next two years.
Since Executive Information System is specifically designed to provide senior executives with the necessary information and insights to support strategic decision-making.
It consolidates data from various sources, both internal and external, and presents it in a user-friendly format, such as dashboards or reports.
This enables executives to analyze trends, identify opportunities, and make informed decisions about the future direction of the organization.
EIS typically focuses on high-level, strategic information and is tailored to meet the specific needs of top-level executives.
So, the correct option is,
C. Executive information system
To learn more about Executive information systems visit:
https://brainly.com/question/16665679
#SPJ6
List 5 Examples of specialized computer
Answers
The 5 Examples of specialized computer
A file computersGame consoles (such as PlayStation)Set-top boxSmart TVsComputerized Analysis Scanner (CAS)What are Specialized Computers?The term Specialized computers is known to be a type of computer that is said to be custom form for specific and well designed kind of task.
Note that specialized computers are known to be powered by the use of a sealed power cell that is said to be made inside of it
Note also that are uniquely made for a special purpose and can only do those kind of task.
Therefore, The 5 Examples of specialized computer
A file computersGame consoles (such as PlayStation)Set-top boxSmart TVsComputerized Analysis Scanner (CAS)Learn more about specialized computer from
https://brainly.com/question/24540334
#SPJ1
We would like the set of points given in the following figure into 1D space. The set of points has been
generated using this instruction [X, y = make_moons(n_samples = 100)], where X are the 2D features
and y are the labels(blue or red).
How to do that while keeping separable data point with linear classification? Give the
mathematics and the full algorithm.
How to apply the SVM algorithm on this data without dimension reduction? Give the
mathematics and full algorithm.
Answers
One way to project the 2D data points onto a 1D space while preserving linear separability is through the use of a linear discriminant analysis (LDA) technique. LDA finds the linear combination of the original features that maximizes the separation between the different classes.
What is the mathematics in SVM algorithm?The mathematics behind LDA involve finding the eigenvectors of the within-class scatter matrix and the between-class scatter matrix and selecting the eigenvector that corresponds to the largest eigenvalue. The full algorithm for LDA can be outlined as follows:
Compute the mean vectors for each class
Compute the within-class scatter matrix (SW) and the between-class scatter matrix (SB)Compute the eigenvectors and eigenvalues of the matrix (SW⁻¹SB)Select the eigenvector that corresponds to the largest eigenvalue as the linear discriminantProject the original data onto the new 1D space using the linear discriminantRegarding the SVM algorithm, it can be applied directly to the original 2D data without the need for dimension reduction. The mathematics behind SVM involve finding the hyperplane that maximizes the margin, or the distance between the closest data points of each class, while also ensuring that the data points are correctly classified.
The full algorithm for SVM can be outlined as follows:
Select a kernel function (e.g. linear, polynomial, radial basis function)Train the model by solving the optimization problem that maximizes the marginUse the trained model to classify new data points by finding the hyperplane that separates the different classesIt is important to note that, in case of non-linearly separable data, SVM algorithm uses the kernel trick to map the original data into a higher dimensional space, where the data is linearly separable.Learn more about algorithm from
https://brainly.com/question/24953880
#SPJ1
A user attempts to send an email to an external domain and quickly receives a bounce-back message. The user then contacts the help desk stating the message is important and needs to be delivered immediately. While digging through the email logs, a systems administrator finds the email and bounce-back details: Your email has been rejected because It appears to contain SSN Information. Sending SSN information via email external recipients violates company policy. Which of the following technologies successfully stopped the email from being sent?
a. DLP
b. UTM
c. WAF
d. DEP
Answers
Answer:
1. DLP (Data Loss Prevention)
Explanation:
DLP tools are meant to protect sensitive information of an organization, by monitoring data transmissions and enforcing previously set policies
UTM means Unified Threat Management. It is a suite of security programs, usually including antivirus, antispam, firewall and others.
WAF stands for Web Application Firewall. It is a specific firewall used to protect web servers by monitoring HTTP traffic.
DEP or Data execution Prevention is a security feature in some operating systems that blocks applications trying to access restricted memory areas.
What can quantum computers do more efficiently than regular computers?
Answers
Quantum computers can also efficiently simulate quantum systems, which is not possible on classical computers. This is useful in fields such as quantum chemistry, where simulating the behavior of molecules can help in the discovery of new materials and drugs.
Quantum computers are capable of solving certain problems exponentially faster than classical or regular computers. This is because quantum computers use quantum bits or qubits, which can exist in multiple states simultaneously, allowing for parallel computations. One of the most well-known examples is Shor's algorithm, which is used to factor large numbers, a problem that is currently infeasible for classical computers to solve efficiently. This has significant implications for cryptography and data security.
Quantum computers can also efficiently simulate quantum systems, which is not possible on classical computers. This is useful in fields such as quantum chemistry, where simulating the behavior of molecules can help in the discovery of new materials and drugs.
Quantum computers also have the potential to greatly improve machine learning and optimization algorithms, allowing for faster and more efficient solutions to complex problems. Overall, quantum computers are expected to have a significant impact on various fields such as cryptography, material science, and artificial intelligence.
For more such questions on Quantum computers, click on:
https://brainly.com/question/29576541
#SPJ11
Read the argument below and determine the underlying principle that was used to come to the conclusion presented: It is recommended that your diet should include at least 3-5 servings of vegetables a day. A serving of vegetables can be 1 cup of raw leafy greens, 1/2 cup of other cooked or raw vegetables, or 3/4 cup of vegetable juice. A diet that has less than 3-5 servings of vegetables a day may lead to health problems. Which other argument uses the same underlying principle as the argument above?
a. Driving a car can be dangerous, but if you learn how to properly drive a car then you can significantly reduce the risk involved,
b. Driving a car can be dangerous, therefore it's recommended that people not drive.
c. Driving a car can be dangerous and that is why states require that drivers pass a test to be licensed to drive.
Answers
Answer:
Hence option a is the correct one. Driving a car can be dangerous, but if you learn how to properly drive a car then you can significantly reduce the risk involved,
Explanation:
a) Driving a car can be dangerous, but if you learn how to properly drive a car then you can significantly reduce the risk involved.
As it belongs How to be a good car driving without risk as equivalent diet concept as a base.
Less than 3-5 servings of vegetables a day not taken equivalent car driving dangerous if no proper driving.
Hence option 1 is valid.
b) is wrong as it has negative feedback regarding the base case.
c) is a suggestion for the strong part which is also the wrong option
how do you copy a file
Answers
Answer:
right click and press control c
it is the process of combining the main document with the data source so that letters to different recipients can be sent
Answers
The mail merge is the process of combining the main document with the data source so that letters to different recipients can be sent.
Why is mail merge important?Mail merge allows you to produce a batch of customised documents for each recipient.
A standard letter, for example, might be customized to address each recipient by name.
The document is linked to a data source, such as a list, spreadsheet, or database.
Note that Mail merge was invented in the 1980s, specifically in 1984, by Jerome Perkel and Mark Perkins at Raytheon Corporation.
Learn more about mail merge at:
https://brainly.com/question/20904639
#SPJ1
Which of these are tools used to diagnose and test code? Check all of the boxes that apply.
debugging software
creating data sets
compiler software
error messages
Answers
Answer:
A C D
Explanation:
Answer:
Correct
Explanation:
1. Write a program in C++ that can convert a given integer value
into words. Assume the largest integer value to be 999 billion
For an input of say 1108 your out should be ONE THOUSAND
ONE HUNDRED AND EIGHT
Answers
Answer:
Hope this works
#include <iostream>
#include <string>
#include <vector>
using namespace std;
string digitName(int digit);
string teenName(int number);
string tensName(int number);
string intName(int number);
vector<string> ones {"","one", "two", "three", "four", "five", "six", "seven", "eight", "nine"};
vector<string> teens {"ten", "eleven", "twelve", "thirteen", "fourteen", "fifteen","sixteen", "seventeen", "eighteen", "nineteen"};
vector<string> tens {"", "", "twenty", "thirty", "forty", "fifty", "sixty", "seventy", "eighty", "ninety"};
string nameForNumber (long number) {
if (number < 10) {
return ones[number];
} else if (number < 20) {
return teens [number - 10];
} else if (number < 100) {
return tens[number / 10] + ((number % 10 != 0) ? " " + nameForNumber(number % 10) : "");
} else if (number < 1000) {
return nameForNumber(number / 100) + " hundred" + ((number % 100 != 0) ? " " + nameForNumber(number % 100) : "");
} else if (number < 1000000) {
return nameForNumber(number / 1000) + " thousand" + ((number % 1000 != 0) ? " " + nameForNumber(number % 1000) : "");
} else if (number < 1000000000) {
return nameForNumber(number / 1000000) + " million" + ((number % 1000000 != 0) ? " " + nameForNumber(number % 1000000) : "");
} else if (number < 999000000001) {
return nameForNumber(number / 1000000000) + " billion" + ((number % 1000000000 != 0) ? " " + nameForNumber(number % 1000000000) : "");
}
return "error";
}
int main()
{
long input;
do
{
cout << "Please enter a positive integer: ";
cin >> input;
cout << "\n" << nameForNumber(input) << endl;
cout << "\n\n" << endl;
}while (input > 0);
return 0;
}
Need help with Exercise 6

Answers
The program based on the question requirements are given below:
The Programimport java.io.File;
import java.io.IOException;
import java.util.Scanner;
public class EncryptText {
// read file and return all content as a String
public static String readFile(String filename) throws IOException {
Scanner scanner = new Scanner(new File(filename));
String content = "";
while(scanner.hasNextLine()){
content += scanner.nextLine();
}
return content;
}
// fills entire grid with stars "*"
public static void initializeGrid(char [][] grid, int m, int n) {
for(int i = 0; i<m; i++)
for(int j = 0; j<n; j++)
grid[i][j] = '*';
}
// does the encryption
public static void fillGrid(char [][] grid, int m, int n, String filename) throws IOException {
// read file
String text = readFile(filename);
// fill entire grid with stars
initializeGrid(grid, m, n);
// i = row, j = column, for grid
int i = 0, j = 0;
// picks a char c from file text and populates the grid
for(int k=0; k<text.length(); k++) {
char c = text.charAt(k);
// even row - fill left to right
if(i % 2 == 0) {
grid[i][j] = c;
j++;
}
// odd row - fill right to left
else {
grid[i][n-j-1] = c;
j++;
}
// if end of column, go to next row and restart column
if(j == n) {
i++;
j = 0;
}
// if end of rows, stop populating grid
if(i == m) {
break;
}
}
}
// extract chars in column-major order
public static void displayGrid(char [][] grid, int m, int n) {
for(int j = 0; j<n; j++) { // cols
for(int i = 0; i<m; i++) // rows
System.out.print(grid[i][j]);
}
}
// start
public static void main(String[] args) throws IOException {
String filename = "input.in";
// define grid dimensions, m = rows, n = cols
int m = 4, n = 8;
// define the grid
char grid[][] = new char[m][n];
// call the function to fill grid
fillGrid(grid, m, n, filename);
// show encrypted text
displayGrid(grid, m, n);
}
}
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1




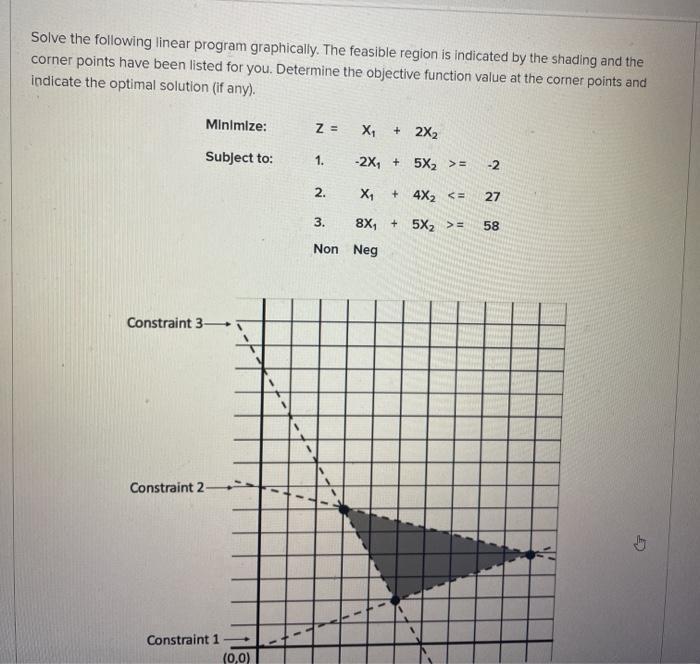
Solve the following linear program graphically (each line represents one unit). The feasible region is indicated by the shading and the corner points have been listed for you. Determine the objective function value at the corner points and indicate the optimal solution (if any). Minimize: Z
Answers
Answer:
(a): The value of the objective function at the corner points
\(Z = 10\)
\(Z = 19\)
\(Z = 15\)
(b) The optimal solution is \((6,2)\)
Explanation:
Given
\(Min\ Z = X_1 + 2X_2\)
Subject to:
\(-2X_1 + 5X_2 \ge -2\) ---- 1
\(X_1 + 4X_2 \le 27\) ---- 2
\(8X_1 + 5X_2 \ge 58\) --- 3
Solving (a): The value of the at the corner points
From the graph, the corner points are:
\((6,2)\ \ \ \ \ \ (11,4)\ \ \ \ \ \ \ \ (3,6)\)
So, we have:
\((6,2)\) ------- Corner point 1
\(Min\ Z = X_1 + 2X_2\)
\(Z = 6 + 2 * 2\)
\(Z = 6 + 4\)
\(Z = 10\)
\((11,4)\) ------ Corner point 2
\(Min\ Z = X_1 + 2X_2\)
\(Z = 11 + 2 * 4\)
\(Z = 11 + 8\)
\(Z = 19\)
\((3,6)\) --- Corner point 3
\(Min\ Z = X_1 + 2X_2\)
\(Z = 3 + 2 * 6\)
\(Z = 3 + 12\)
\(Z = 15\)
Solving (b): The optimal solution
Since we are to minimize Z, the optimal solution is at the corner point that gives the least value
In (a), the least value of Z is: \(Z = 10\)
So, the optimal solution is at: corner point 1
\((6,2)\)
There are a number of roles held by various users of online digital media, including contributors, conversationalists,
critics, organizers, spectators, and joiners. Often, people who have a strong presence online will hold two or more roles.
Describe at least three of these roles. Of the roles you described, why might someone act on two of them at the same
time? That is, what kind of online activity would result in a person taking on those two roles?
Answers
Answer:
The mass media is a huge phenomenon. Through the various different platforms, print or broadcast, the media is able to reach millions of people like no other force. Without the media, powerful speeches by politicians would affect no one, local events would remain local, and performances by great actors would be seen only by the people in the immediate audience. The media overcomes distances, and builds a direct relationship with the audience. Many sociologist
I hope she/he helps !
Explanation:
If you want to see the tab stops, what should you do?
Answers
Answer:
click on it
Explanation:
the coupon code free shipping code free shipping code for Science is it ok if I can help with her oo cool I don't know if you can help you out listen to the main office and you cross the road to the main one is a selfie stick to me when we
Write a recursive function called DrawTriangle() that outputs lines of '*' to form a right side up isosceles triangle. C++ ONLY
Answers
Explanation:
Write a recursive function called draw_triangle() that outputs lines of '*' to form a right side up isosceles triangle. Function draw_triangle() has one parameter, an integer representing the base length of the triangle. Assume the base length is always odd and less than 20. Output 9 spaces before the first '*' on the first line for correct formatting.
Any set of logic-gate types that can realize any logic function is called a complete set of logic gates. For example, 2-input AND gates, 2- input OR gates, and inverters are a complete set, because any logic function can be expressed as a sum of products of variables and their complements, and AND and OR gates with any number of inputs can be made from 2-input gates. Do 2-input NAND gates form a complete set of logic gates? Prove your answer.
Answers
Answer:
Explanation:
We can use the following method to solve the given problem.
The two input NAND gate logic expression is Y=(A*B)'
we can be able to make us of this function by using complete set AND, OR and NOT
we take one AND gate and one NOT gate
we are going to put the inputs to the AND gate it will give us the output = A*B
we collect the output from the AND and we put this as the input to the NOT gate
then we will get the output as = (A*B)' which is needed