ProjectSTEM CS Python Fundamentals - Lesson 3.3 Question 2 - RGB Value:
Test 6: Using 256 for all inputs, this test case checks that your program has no output. / Examine the upper condition for each color.
Test 10: This test case sets the input for blue beyond the limit, while red and green are below. It checks if your program's output contains “Blue number is not correct”, but not “Red number is not correct”, or “Green number is not correct” / Check that you output the correct phrase when the number is outside the range. Make sure that only the incorrect color phrases are output.

Answers
While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).Make the variable "alien color" and give it the values "green," "yellow," or "red." To determine whether the alien is green, create an if statement.
How does Python find the RGB color?Colors can only be stored in Python as 3-Tuples of (Red, Green, Blue). 255,0,0 for red, 0 for green, and 255,0 for blue (0,0,255) Numerous libraries use them. Of course, you may also create your own functions to use with them.The rgb to hex() function, which takes three RGB values, is defined in line 1.The ":X" formatter, which automatically converts decimal data to hex values, is used in line 2 to construct the hex values. The outcome is then returned.Line 4 is where we finally call the function and supply the RGB values.Verify the accuracy of the RGB color code provided. While CMYK is frequently used to print out colors, RGB is utilized when the colors need to be presented on a computer monitor (such as a website).To learn more about Python refer to:
https://brainly.com/question/26497128
#SPJ1
Related Questions
Which of the following are true about firewalls?
I. They are an important part of any network security strategy
II. They are the electronic equivalent of a guard at a gate
III. They can be hardware or software
IV. They are used to checks all data passing in or out to make sure it is legit
V. They should allow users access to all the resources they need
VI. They should keep out any malicious users or programs
I - III only
IV-VI only
I-IV and VI
I - Vl all
Answers
Answer:
It is I - Vl all
Explanation:
Hope this helps ❤️❤️❤️❤️❤️
#KeepOnLearning❤️❤️❤️❤️❤️
#StaySafe❤️❤️❤️❤️❤️
Which of these symbols is the assignment operator?
{ }
( )
#
=
Answers
Answer:
# i think
Explanation:
Its = (D) I made my own game in python
e) Created in the system walkthough a) Models that describe processes without suggesting how they are conducted b) Coded logic models c) Models based upon implementing the if-then-else programming structure d) Developed by the infrastructure analyst
Answers
Answer:
d
Explanation:
HELP ASAP 100 points as i need answer soon
You join Mountain Water Co – an expanding bottled water company as an information security officer. The company wants to do a lot of advertising of its bottled water products through its website. The CEO asks you to review the company website and report if it is secure. After talking to the webmaster you find out the following:
The Web server accepts all connections
No authentication is required
Self-registration is allowed
The web server is connected to the Internet
Is the situation secure? Select all that apply.
a. Yes. There is no threat to a bottled water company so it is secure.
b. There is insufficient information available to answer this question.
c. No. Anything that is connected to the Internet is insecure.
d. No. The system is allowing everyone to register. Only individuals who are associated with the company should be able to register.
e. No. If there is no authentication, then anyone with access to the website online can access it. For good security only individuals with certain authorized roles should access a website.
Answers
Answer:
yes
Explanation:
but you need to open the website before asking this question
discuss seven multimedia keys
Answers
Answer:
Any seven multimedia keys are :-
□Special keys
□Alphabet keys
□Number keys
□Control keys
□Navigation keys
□Punctuation keys
□Symbol keys
____allow(s) visually impaired users to access magnified content on the screen in relation to other parts of the screen.
Head pointers
Screen magnifiers
Tracking devices
Zoom features
Answers
Answer: screen magnifiers
Explanation: got it right on edgen
Simon Says" is a memory game where "Simon" outputs a sequence of 10 characters (R, G, B, Y) and the user must repeat the sequence. Create a for loop that compares the two strings starting from index 0. For each match, add one point to userScore. Upon a mismatch, exit the loop using a break statement. C++
Ex: The following patterns yield a userScore of 4:
Ex: The following patterns yield a userScore of 9:
simonPattern: R, R, G, B, R, Y, Y, B, G, Y
userPattern: R, R, G, B, B, R, Y, B, G, Y
Answers
Answer:
#include <iostream>
#include <string.h>
using namespace std;
int main()
{
string simonPattern = "RRGBRYYBGY";
string userPattern = "RRGBBRYBGY";
int score = 0;
for (int i = 0; i < simonPattern.length(); i++) {
if (userPattern[i] == simonPattern[i])
score++;
else
break;
}
cout << "Score is " << score << endl;
return 0;
}
Explanation:
Initialize the simonPattern, userPattern and score
Create a for loop that checks the each chracter in simonPattern with userPattern. If a character matches, increase the score by 1. Otherwise, stop the loop.
When the loop is done print the score
The code above will print 4 because the first four characters matches in the strings
Help, needed right now!!!

Answers
Answer: its code
Explanation:
Type the correct answer in the box. Spell all words correctly.
Which certification can help Natalia pursue a career as a penetration tester?
Natalia wants to pursue a career as a penetration tester. It would be advisable for her to be a
least two years of work experience. The International Council of E-Commerce Consultants (EC-Council) provides this certification.
, which requires at
Answers
Your career in penetration testing can get off to a strong start with the PenTest+ certification from CompTIA. To thoroughly assess your abilities, it has a multiple-choice section and a performance-based test.
Which certification for penetration testing is the best?One of the pentesting certifications provided by GIAC is the GIAC Penetration Tester (GPEN) credential. As a member of SANS, GIAC is regarded as a premier cert authority for a number of credentials. GPEN concentrates on pentesting methodology, best practices, and related legal concerns. The certification is good for four years.
What kind of evaluation is carried out by a penetration tester to try to find every flaw discovered in an application or on a system?White-box testing looks for potential flaws in a variety of areas, including logical weaknesses, security exposures, security configuration errors, poorly written development code, and a lack of protective measures.
to know more about E-Commerce Consultants here:
brainly.com/question/14157556
#SPJ1
Answer: Your answer is Certified Ethical Hacker
Explanation: The EC-Council provides this certification and you have to have at least 2 years of experience :) hope this helped
Explain how mobile phone production could be more sustainable
Answers
Answer:
Sustainable design - the key features for sustainable phones are: use of sustainable and recycled materials, the use of less energy and efficient charging, durability, and last but not least they should be easy and inexpensive to repair.
Answer:
One of the best ways to change this is to voice your concern to cell phone manufacturers for more sustainable products. Request smartphones that are made with fewer hazardous chemicals, manufactured in plants powered by renewable energy, and that contain recycled materials.
Explanation:
quick IM BEGGING
What is the value of the variable result after these lines of code are executed?
>>> a = 12
>>> b = 0
>>> c = 2
>>> result = a * b - b / c
0
0
It has no value since an error occurred.
It has no value since an error occurred.
20
20
6
6
Answers
Answer:
Explanation:
The value of the result variable after these lines of code are executed is -0.0.
Answer:
The value of result after these lines of code are executed would be 0.
Explanation:
This is because the expression a * b - b / c is evaluated as follows:
result = a * b - b / c
= 12 * 0 - 0 / 2
= 0 - 0
= 0
No errors occur in this code, so result will have a value of 0.
Sukhi needs to insert a container into her form to collect a particular type of information.
Which object should she insert?
Answers
Answer:
text box
Explanation:
on edge 2020
Answer:
A- text box
Explanation: ;)
Which strategy helps job seekers organize and track their job search progress efficiently?
Answers
A job seeker who is using an online resources for the job search shows that how technology as well as the internet in the particular has been helped to simplify our everyday life.
What is the use of online resources in finding a job?The use of the online resources in the job search provides a much faster way of reaching and covering a wide range of available jobs within and far beyond your immediate geographical range.
Before the internet, the job searches were typically done manually, and the process has been consumed a lot of time and the resources and was mostly limited a certain geographical range.
Therefore, nowadays, someone in the US can easily apply for a job post on the internet all the way in Germany.
Learn more about internet on:
https://brainly.com/question/13308791
#SPJ9
Which of the following is a true statement comparing a horizontal flowchart with a vertical flowchart?
A. A horizontal flowchart does not provide as broad a picture at a glance.
B. A horizontal flowchart brings into sharper focus the assignment of duties and independent checks on performance.
C. A horizontal flowchart provides more room for written descriptions that parallel the symbols.
D. A horizontal flowchart is usually longer.
Answers
The true statement comparing a horizontal flowchart with a vertical flowchart is:
C. A horizontal flowchart provides more room for written descriptions that parallel the symbols.
A horizontal flowchart is a type of diagram that lays out the steps of a process in a horizontal line, rather than in a vertical line like a vertical flowchart.
In a horizontal flowchart, there is more room for written descriptions that parallel the symbols used to represent the steps in the process. This makes it easier to understand the process and how it works.
Additionally, horizontal flowcharts can bring into sharper focus the assignment of duties and independent checks on performance, providing a more thorough overview of the process.
Horizontal flowcharts are particularly useful when there is a need to clearly depict the various steps of a process, as well as the tasks that are associated with each step.
The symbols used to represent each step can be accompanied by detailed descriptions, which makes it easier to understand how the process works.
Furthermore, a horizontal flowchart can clearly show the assignment of duties and independent checks on performance that are used to ensure that the process is completed in an efficient and effective manner.
Learn more about comparing horizontal flowchart with vertical flowchart:
brainly.com/question/29317974
#SPJ4
Which type of evidence should victims collect to help officials catch cyber bullies ?
-home addresses
-birthdays
-social media
-usernames user
-passwords
Answers
Answer:
Social media
Explanation:
List 3 specifications for the electromagnet
Answers
Answer:
Holding Force
Maximum Magnetic Field
Residual Induction, Br
Coercive force
Intrinsic coercive force
Activity
Online security is a major issue for internet users. Threats may affect your data and applications (both online and offline), or infect your system and use up system resources.
Part A
Check your email account. Check if your email provider has a spam filter. Don’t open the email messages, but determine as much information as you can from the subject lines. Does it contain any emails that you can identify as spam? What kind of emails are they? Do they have anything in common?
Answers
Unwanted emails known as spam are distributed to several recipients in bulk. They frequently include false information, including promotions for goods or services that seem too good to be true.
Is sending bulk, unsolicited emails that you haven't requested considered spamming?Spam is any sort of bulk, unsolicited communication (Unsolicited Bulk Email, or UBE). A business email sent to many addresses is the most common form (Unsolicited Commercial Email, or UCE)
Unsolicited bulk email means that the recipient did not consent to receiving it.Unsolicited bulk email is referred to as "Spam" when used in reference to email. Unsolicited signifies that the recipient has not given the communication their explicit consent.
To know more about emails visit:-
https://brainly.com/question/14666241
#SPJ1
Write code which takes a double input from the user and creates a circle with that radius. The code should calculate the area of the circle, then double the radius of the circle and print the new area of the circle. Sample run: Enter radius: > 2.0 Area: 12.566370614359172 Radius is being doubled... Area: 50.26548245743669
Answers
Answer:import java.util.Scanner;
import (*software used for shapes*);
public class (*enter class name*){
public static void main(String[] args){
Scanner scan = new Scanner(System.in);
System.out.println("Enter radius: ");
double r = scan.nextDouble();
Circle c = new Circle(r);
double area = c.getArea();
System.out.println("Area: "+area);
System.out.println("Radius is being doubled...");
r = c.getRadius();
c.setRadius(r*2);
area = c.getArea();
System.out.println("Area: "+area);
Explanation:
I know this is late, but I am putting this here for future people trying to solve this problem.
The C code is given by:
void areaCircle(double r){
double A;
A = pi*r*r;
printf("Area: %lf\n", A);
r *= 2;
A = pi*r*r;
printf("Radius is being doubled \n");
printf("Area: %lf\n", A);
}
The input is taken in:
int main(){
double r;
scanf("%lf\n", &r);
return 0;
}
--------------------
The function is declared as void, as it does not return anything, and has the radius as input, thus:
void areaCircle(double r){
}
The area is \(A = \pi r^2\), thus, inserting and printing in the code.
void areaCircle(double r){
double A;
A = pi*r*r;
printf("Area: %lf\n", A);
}
Doubling the radius and printing the new area, the complete code is:
void areaCircle(double r){
double A;
A = pi*r*r;
printf("Area: %lf\n", A);
r *= 2;
A = pi*r*r;
printf("Radius is being doubled \n");
printf("Area: %lf\n", A);
}
As for the input:
int main(){
double r;
scanf("%lf\n", &r);
return 0;
}
A similar problem is given at https://brainly.com/question/14316064
At north wind headquarters, where were penguins first reported missing on the giant TV screen? And what did the penguins react?
Answers
Answer:
Berlin zoo
The penguins reacted that they must respond with action ASAP
Answer:
Berlin zoo, the penguins reacted that "It's time to go".
This means that the penguins care about each other and must rescue each other.
Hello, I have to figure out how to modify the program to print the maximum and minimum scores entered. I have a basic idea of how to do this, but I am unsure of how to continue. Here is the code:
game_scores = []
more_scores = "y"
total_scores = 0.0
while more_scores == "y":
score = int(input("Enter a game score: "))
game_scores.append(score)
more_scores = input("enter y to enter more scores or n to end the program ")
for values in game_scores:
total_scores += values
print("total game points in the game score list: ", total_scores)
average_points = (total_scores/len(game_scores))
print("average points in the game score list: ", format(average_points, "7.2f"))
import numpy as np
np_game_scores = np.array(game_scores)
print("The values in the game score array are: ", np_game_scores)
np_game_scores.sort()
print("The sorted values in the game score array are: ", np_game_scores)
Answers
To print the maximum and minimum scores entered, you can use the max() and min() functions on the game_scores list.
Add the following code after the for loop that calculates the average points:
The Programmax_score = max(game_scores)
min_score = min(game_scores)
print("Maximum score: ", max_score)
print("Minimum score: ", min_score)
This will find and print the highest and lowest values in the game_scores list.
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
True or false a mirrorless camera has a pentaprism
Answers
Answer:
No the pentaprism or pentamirror are both optical viewfinder viewing systems and are not part of the mirrorless camera. Some thing the pentaprism actually operates better than the electronic viewfinder of mirrorless cameras.
Explanation:
What was the Internet originally created to do? (select all that apply)
Answers
The Internet was initially constituted for various purposes. it is was originally created to options a, c and d:
share researchcommunicateshare documentsWhat is InternetCommunication: The Internet was planned to aid ideas and data exchange 'tween analysts and chemists. It proposed to combine various calculating and networks to authorize logical ideas and cooperation.
Research and Development: The Internet's production was driven for one need to share research verdicts, experimental dossier, and possessions among academies, research organizations, and administration institutions.
Read more about Internet here:
https://brainly.com/question/21527655
#SPJ4
You have read about the beginnings of the Internet and how it was created. What was the Internet originally created to do? (select all that apply)
share research.
Play games.
Communicate.
Share documents.
Sell toys
2
3
oooq
ABCD
5
10
Frankie is in charge of writing a script for a television show, along with six other writers. The script must be
finished by the end of the week. Frankie's co-workers all bring slightly different strengths to the table, but all are at
least competent. Frankie wants to write the best possible script in the generous amount of time he has to work
with. In this example, which style of leadership would be most effective for Frankie's goals?
a. Authoritarian
b. Coaching
c. Democratic
d. Delegative
Please select the best answer from the choices provided
Mark this and return
Save and Exit
01:20:28
Next
Submit
Answers
Based on the information provided in the question, it seems that a democratic leadership style would be most effective for Frankie’s goals. In a democratic leadership style, the leader involves team members in the decision-making process and encourages collaboration and open communication. This approach can help to ensure that everyone’s strengths are utilized and that the best possible script is written within the given time frame.
The choice database does not have any impact on the relevancy of search results true or false
Answers
True. The search results a user received have no correlation with the choice of database.
How do you optimise search results in a database?It is recommended that the best way to optimise search results lies in adjusting how the query is been made. This implies that a user can make their search results more relevant by using key phrases or making direct quotations in the search box.
For example, to achieve relevant search results of a home address in a database, making a direct quotation of the home address in the search box would yield the desired results than simply typing a few phrases.
You can learn more search results here https://brainly.com/question/14024902
#SPJ1
Write a paragraph discussing privacy issues on the internet
and their impact on human lives.
Answers
Explanation:
internent had a impact on human lives because it is very popular and it brought in phones so about evrbody in the world has internent and it impacted work around the world and changed the world alot.
what's another name for white -colored wire?
A. grounded conductor
B.Grounding conductor
C.Hot
D.Hot neutral
Answers
Answer:
A
Explanation:
A. The correct answer is A. "Grounded conductor" is another name for a white-colored wire. It is also commonly referred to as a neutral wire.
Answer:A. grounded conductor. I hope this helps
Explanation:
The correct answer is A. Grounded conductor. The grounded conductor is also commonly referred to as the neutral wire and is typically color-coded white
A. Grounded conductor is another name for white-colored wire. The grounded conductor is also commonly referred to as the neutral wire, which carries current back to the source. It is distinguished from the hot wire which carries the current to the loads. The grounding conductor, on the other hand, is typically green or bare and serves to ground the system for safety purposes
A deferred annuity is an annuity which delays its payouts. This means that the payouts do not start until after a certain duration. Notice that a deferred annuity is just a deposit at the start, followed by an annuity. Your task is to define a Higher-order Function that returns a function that takes in a given interest rate and outputs the amount of money that is left in a deferred annuity.
Define a function new_balance(principal, gap, payout, duration) that returns a single-parameter function which takes in a monthly interest rate and outputs the balance in a deferred annuity. gap is the duration in months before the first payment, payout is monthly and duration is just the total number of payouts. Written in Python code.
Test Case:
new_balance(1000, 2, 100, 2)(0.1)
Output:
1121.0
Answers
Answer:
Explanation:
Here is the requested Python code for the new_balance function:
def new_balance(principal, gap, payout, duration):
def balance(interest_rate):
return principal * (1 + interest_rate)**gap + payout * ((1 + interest_rate)**(gap + duration) - (1 + interest_rate)**gap) / interest_rate
return balance
This function defines a single-parameter function balance which takes in a monthly interest rate and calculates the balance in a deferred annuity based on the given parameters. The balance is calculated using the formula for a deferred annuity, which accounts for the gap between the initial deposit and the start of the payouts, as well as the total number of payouts and the monthly payout amount.
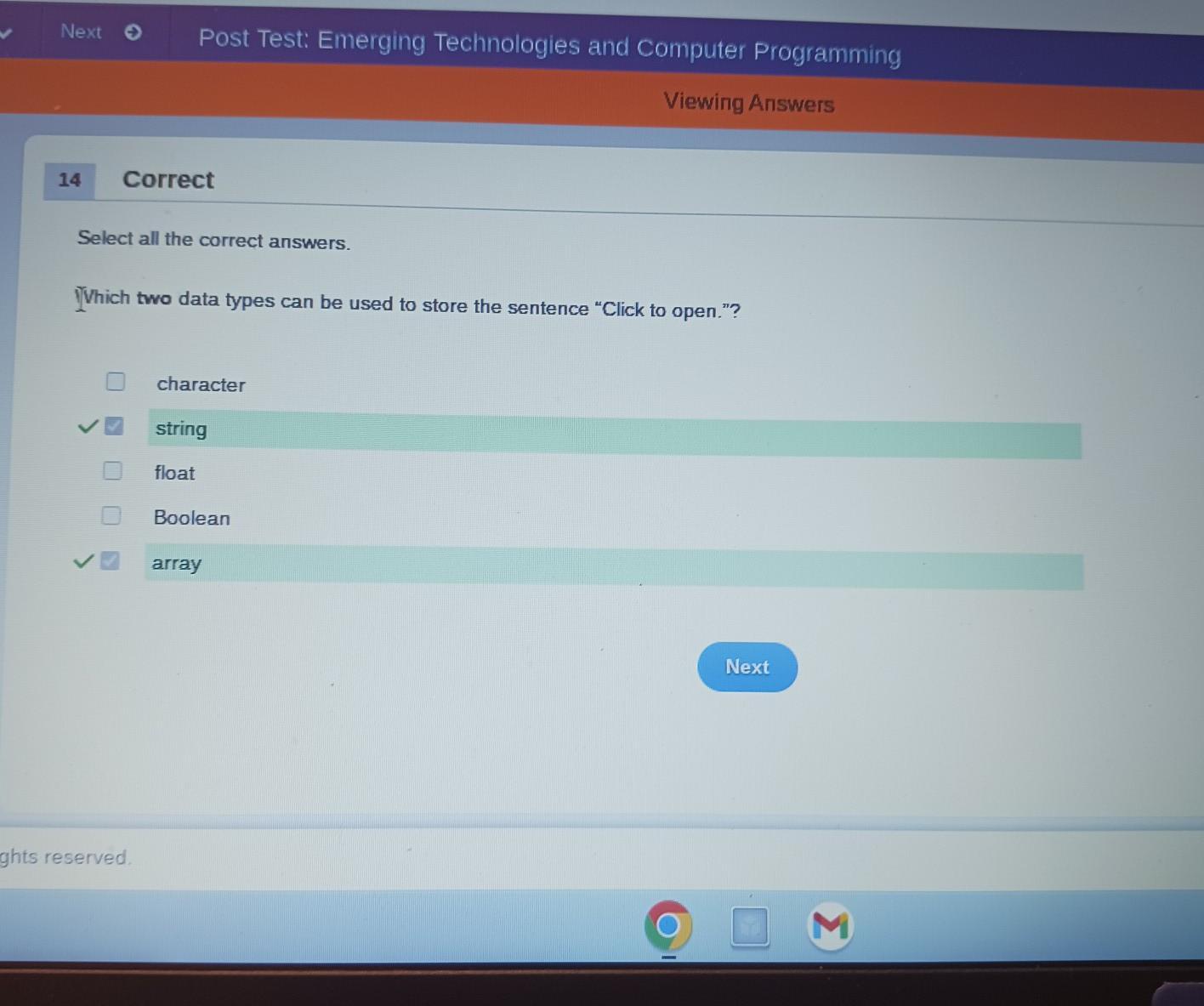
PLEASE HELP there are TWO ANSWERS
Select all the correct answers.
Which two data types can be used to store the sentence "Click to open."?
character
string
float
Boolean
array
Answers
Answer:
boolean is correct
Explanation:
Answer:
its string and array
Explanation:
Edmonton gang
_______ tools enable people to connect and exchange ideas.
A) Affective computing.
B) Social media.
C) Debugging
D) Computer forensics.
Answers
Social media is a tool that enables people to connect and exchange ideas. Thus the correct option is B.
What is communication?Communication is referred to the exchange of information between two individuals in the form of conversation, opinion, suggestion, or advice with the help of medium or direct interaction.
Social media is referred to as a tool of communication that enables people to share their ideas, thoughts, and opinions with a wide network of people and helps them to get information about the events happening in the world.
An internet tool for interaction, information sharing, and social networking is social media. Networking software that connects people around the world is an internet-based technology, strictly understood.
Therefore, option B is appropriate.
Learn more about Communication, here:
https://brainly.com/question/22558440
#SPJ5
Social media is a tool that enables people to connect and exchange ideas. Therefore, the correct answer is option B.
The exchange of information between two people in the form of conversation, opinion, suggestion, or advice with the use of a medium or direct interaction is referred to as communication.
Social media is referred to as a communication tool that enables individuals to communicate their thoughts, ideas, and opinions with a large network of people and assists them in learning about global events.
Social media is an online medium for communication, sharing of knowledge, and social networking. According to the definition of the term, internet-based technology includes networking software that links individuals worldwide.
Therefore, the correct answer is option B.
Learn more about communication here:
brainly.com/question/22558440
#SPJ6
What are the core steps to add revisions or features to a project?(1 point)
Responses
Evaluate feasibility of the goals, create a list of functionality requirements, and develop the requirements of the feature.
Evaluate feasibility of the goals, develop programming solutions, and evaluate how well the solutions address the goals.
understand the goals, evaluate the impact on the project, create a list of functionality requirements, and develop the requirements of the feature.
Communicate with the client, create a sprint backlog, develop the project, and evaluate how well the solution fits the requirements.
Answers
The core steps to add revisions or features to a project are ""Understand the goals, evaluate the impact on the project, create a list of functionality requirements, and develop the requirements of the feature." (Option C)
How is this so?
The core steps to add revisions or features to a project include understanding the goals,evaluating the impact on the project, creating a list of functionality requirements,and developing the requirements of the feature.
These steps ensure that the goals are clear, the impact is assessed, and the necessary functionality is identified and implemented effectively.
Learn more about project management at:
https://brainly.com/question/16927451
#SPJ1