________ processing occurs when a program runs from beginning to end without any user interaction.
Answers
Batch processing occurs when a program runs from beginning to end without any user interaction.
Batch processing refers to the execution of a program or set of tasks without any user interaction or intervention. In batch processing, programs are typically designed to process a large volume of data or perform repetitive tasks automatically.
The program runs from start to finish, processing the data or performing the specified operations according to a predefined set of instructions, without requiring any input or interaction from the user during the execution. Batch processing is commonly used in various applications, such as data processing, batch jobs, and automated tasks.
Learn more about data processing visit:
https://brainly.com/question/30094947
#SPJ11
Related Questions
Which of the following is an example of a compressed file format?
Answers
Answer:
.zip, .7z, .rar.
Explanation:
A car showroom consists of N numbered spaces. Each space can hold at most one car. The spaces are indexed starting from 0 though the last space, N - 1. No two cars in the showroom are the same model. Write the CarShowroom method findCarSpace. This method returns the index of the space in which the car with the specified model is located. If there is no car of that model in the showroom, the method returns -1. Then write the CarShowroom method consolidate. This method should move the cars so that cars in adjacent spaces, starting at index 0, have no empty spaces between any two cars. Keep the order of the cars the same as the array in the code shows.
Answers
The CarShowroom method find function of CarSpace takes a car model as a parameter and returns the index of the space containing the car with that model. The Car Showroom method consolidate moves the cars in the showroom so that no empty spaces are between any two cars, while preserving the order of the cars.
The CarShowroom class contains two methods: findCarSpace and consolidate. The findCarSpace method takes a car model as a parameter and returns the index of the space in which the car with the specified model is located. If no car with that model is present in the showroom, the method returns -1. This method is useful for finding a car in a showroom with many cars. The consolidate method moves the cars in the showroom so that no empty spaces exist between any two cars. This method preserves the order of the cars, so that the cars are still in the same order as the array in the code shows. This method is useful for organizing a showroom with many cars, as it ensures that cars are spaced evenly and that no cars are hidden behind other cars.
Learn more about functions here-
brainly.com/question/28939774
#SPJ4
PLEASE ANSWER ASAP
Type the correct answer in the box. Spell all words correctly.
What was the name of the database that Tim Berners-Lee built?
Tim Berners-Lee built a database called [BLANK].
Answers
Answer:
ENQUIRE database.
Explanation:
I am not sure but I guess this is the answer.
An insect population doubles every generation. Write a while loop that iterates numgeneration times. Inside the while loop, write a statement that doubles currentpopulation in each iteration of the while loop.
Answers
The initialPopulation variable to currentPopulation the value.
till i is less than numGeneration, continue the while loop.
What are the Python variables?Only alphanumeric characters and underscores can be used to create variables in Python. Additionally, they keep the case sensitivity. The lifespan of a Python variable depends on the range of Python variables.
function currentPopulation = CalculatePopulation(numGeneration, initialPopulation)
i = 1;
currentPopulation = initialPopulation;
while(i <= numGeneration)
currentPopulation = 2* currentPopulation;
i= i+1;
end
end
To learn more about python click here :
https://brainly.com/question/18502436
#SPJ1
Drag the tiles to the correct boxes to complete the pairs.
Match the benefit with its detailed explanation.

Answers
The detailed explanation and their benefits are:
1st box - Improved Planning Session2nd box - Integrated Organisation3rd box - Improved Data Entry4th box - Reduced Inventory Costs.What are enterprise systems?Enterprise systems are known to be software packages in large-scale which help businesses or enterprises to track and control their complex business operations. They are used as a hub where businesses are automated.
We can see that the above has been be arranged with the detailed explanation and the benefits that follow.
Learn more about enterprise systems on https://brainly.com/question/18257319
________ is a technique for intercepting computer communications through a physical connection to a network or without a physical connection in the case of wireless networks. Spoofing Sniffing Pretexting Phishing
Answers
Sniffing is a technique for intercepting computer communications through a physical connection to a network or without a physical connection in the case of wireless networks. Sniffing involves capturing and analyzing network traffic to extract sensitive information, such as usernames, passwords, credit card numbers, and other confidential data.
Sniffing attacks can be carried out using specialized hardware or software tools, such as packet sniffers, network analyzers, or intrusion detection systems. These tools allow attackers to monitor and capture network traffic in real-time, and then use various methods to extract and decode the information contained in the packets.
Wireless networks are particularly vulnerable to sniffing attacks, as they broadcast their signals over the airwaves, making them accessible to anyone within range of the wireless signal. Attackers can use specialized antennas and sniffing software to intercept and analyze wireless traffic, even if the network is encrypted.
To protect against sniffing attacks, it is important to use encryption and secure protocols, such as SSL/TLS, SSH, and VPN, to protect sensitive data in transit. Additionally, network administrators should monitor network traffic and use intrusion detection and prevention systems to detect and block sniffing attacks.
Learn more about Sniffing here:
https://brainly.com/question/13068615
#SPJ11
Which should you try first if your device can't connect to a remembered public wireless network?
A. Increase the transmit power on the SOHO router
B. Connect to the SOHO router with a cable
C. Reset the SOHO router to factory defaults
D. Delete the profile and try to connect again
Answers
Deleting the profile and try to connect again should be tried first if your device can't connect to a remembered public wireless network. The correct option is D.
If your device is unable to connect to a previously remembered public wifi network, the first step in troubleshooting is to erase the profile associated with that network and then reconnect.
Sometimes the stored profile contains old or erroneous information, which causes connectivity issues. By erasing the profile and restarting the device, you enable it to establish a new profile with the right settings.
The other techniques presented may be useful in some situations, but they are not the first suggested step for addressing connection troubles with a previously established public wireless network.
Thus, the correct option is D.
For more details regarding wireless network, visit:
https://brainly.com/question/13014458
#SPJ4
the type of mic that can be used as a miniature clip-on mic or a high quality studio mic that requires batteries or an external power source is the:
Answers
A condenser microphone is a type of device that can be used as a little clip-on microphone or a premium studio microphone that runs on batteries or an external power source.
The type of mic that can be used as a miniature clip-on mic or a high quality studio mic is known as a condenser mic. It is a type of microphone that uses a condenser (or capacitor) to convert sound waves into electrical energy. These types of mics are known for their high sensitivity and accurate sound reproduction. They can be used in a variety of settings, including as a miniature clip-on mic for live performances or as a high-quality studio mic for recording. However, they typically require batteries or an external power source to function properly.
To learn more about Clip-on Mic Please click the given link:
https://brainly.com/question/24015857
#SPJ4
Your team is about to introduce and lunch a product never seen before in Barbados, an Ultrasonic Pest Repellent, that repels pests (small insects) while causing no harm to your pets, yourself, or any animals in range.
1) In your own word, state the market objectives your team wishes to attain with the lunch of this new product. Ensure your objective are written clearly and S.M.A.R.T.
ii) Identify any concerns that may affect the completion of the objective.
Answers
Market Objectives are Increase Market Share, Generate Revenue and Build Brand Awareness. Concerns are as follows Market Acceptance, Competitive Landscape and Regulatory Compliance.
i) Market Objectives:
1. Increase Market Share: Increase the market share of the Ultrasonic Pest Repellent in Barbados by 20% within the first year of launch.
(Specific: Increase market share, Measurable: 20% increase, Achievable: Based on market demand and competition, Relevant: Aligns with the product launch, Time-bound: Within the first year)
2. Generate Revenue: Achieve a sales target of $100,000 in the first six months after product launch.
(Specific: Achieve sales target, Measurable: $100,000, Achievable: Based on market potential and pricing strategy, Relevant: Revenue generation, Time-bound: Within the first six months)
3. Build Brand Awareness: Increase brand recognition and awareness of the Ultrasonic Pest Repellent among the target audience by implementing a comprehensive marketing campaign, resulting in 75% brand recognition within the first year.
(Specific: Increase brand awareness, Measurable: 75% brand recognition, Achievable: Through effective marketing strategies, Relevant: Brand building, Time-bound: Within the first year)
ii) Concerns:
1. Market Acceptance: There may be concerns regarding the acceptance and adoption of the Ultrasonic Pest Repellent among consumers in Barbados. Awareness and education campaigns may be required to overcome skepticism and build trust in the product's effectiveness.
2. Competitive Landscape: Competitors already offering pest control solutions may pose a challenge. It is important to differentiate the Ultrasonic Pest Repellent and effectively communicate its unique selling points to gain a competitive advantage.
3. Regulatory Compliance: Ensuring compliance with local regulations and safety standards regarding the sale and usage of pest control products is crucial. Failure to meet regulatory requirements could result in delays or restrictions on product launch.
Learn more about marketing campaign :
https://brainly.com/question/30237897
#SPJ11
what is is a widely-used method of data encryption using a private (secret) key that was judged so difficult to break by the u.s. government that it was restricted for exportation to other countries?
Answers
The U.S. government limited the export of the widely used Data Encryption Standard because it was deemed to be too hard to crack. This technique of data encryption uses a private (secret) key.
Data Encryption Standard: What is it?The Data Encryption Standards is a block cipher, which means that instead of applying a cryptographic key & algorithm to each piece of data individually, they do so simultaneously to a block of data. The DES algorithm divides a plaintext message into 64-bit blocks.
The block size and key size of DES are both 64 bits. It is a symmetric block cipher. Since it is susceptible to some attacks, it is not very widely utilized.
The DES algorithm is now necessary for all financial transactions involving digital money transfers conducted by the U.S. government, including those performed by institutions that are Federal Reserve System members.
To learn more about Data Encryption Standard refers to;
brainly.com/question/30030407
#SPJ4
Your development team is planning to host a development environment on the cloud. This consists of EC2 and RDS instances. This environment will probably only be required for 2 months. Which types of instances would you use for this purpose
Answers
The type of instances would you use for this purpose is known as On-Demand.
What is an on demand instance?On-Demand Instances is known to be one that allows a person to pay for compute capacity usually by the hour or second with no long-term payment.
This is one that gives one a level of freedom from the costs and complexities of planning, purchasing, and keeping hardware.
Learn more about cloud from
https://brainly.com/question/25130975
Supply Chain strategy often optimizes supply chain networks for "average" performance. Explain why this is or is not the right approach? Edit View Insert Format Tools Table 12pt Paragraph BIU AQV T²V : When locating facilities in a network, the transportation economies about the potential facility location should be considered. What does this mean with respect to where the facility is located and how the network is configured? Edit View Insert Format Tools Table 12pt Paragraph ✓ B I U AV 2V T²V ⠀
Answers
Supply Chain strategy is essential in every organization that involves the planning and management of all activities involved in sourcing, procurement, conversion, and logistics. In doing so, the goal is to optimize supply chain networks for average performance.
It is the right approach to optimize supply chain networks for "average" performance because it helps the company attain its objectives and improve its performance. It makes the planning and management of activities in sourcing, procurement, conversion, and logistics more efficient by making use of resources at an optimal level. Also, this approach allows the company to maintain the right balance between supply and demand by producing enough products to meet the customers' demands. By doing so, the company reduces costs, increases efficiency, and enhances customer satisfaction. However, sometimes, optimizing supply chain networks for "average" performance may not be the right approach. This is because customers' preferences are not average. Also, different customers have different needs. Thus, optimizing the supply chain for an average performance level may result in dissatisfied customers who may opt to seek services from the competitors. Thus, it is essential to ensure that the optimization strategy considers the customers' needs and preferences, and a balance is achieved. In conclusion, optimizing the supply chain for average performance is the right approach in most cases. However, this approach should consider the customers' needs and preferences to achieve a balance between supply and demand. Therefore, when locating facilities in a network, transportation economies about the potential facility location should be considered. This means that the facility should be located in an area that is easily accessible to transportation. Additionally, the network should be configured in such a way that the facility is linked to other facilities in the supply chain network to allow for efficient transportation.
To learn more about Supply Chain strategy, visit:
https://brainly.com/question/27670727
#SPJ11
Take an example of old communication technology and compare it with the new communication technology which is solving the same use case and describe how new communication technology has changed the future of communication
Answers
Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Thus, Software, computer programs, gadgets, and message systems are examples of this technology. Technologies for effective communication are quick, effective, practical, and simple to use. They frequently make it possible for people to connect with one another from anywhere in the world.
Before communication technology, delivering even the most straightforward information took more time and effort than is possible to convey in 140 characters or less.
Information sharing is now simpler than ever because to the integration of technology into many forms of communication. Despite the huge number of devices, programs, and tools used in communication technology.
Thus, Any digital gadget that can be used to convey and receive information is referred to as communication technology.
Learn more about Communication technology, refer to the link:
https://brainly.com/question/1150014
#SPJ4
Which of these is NOT a way that technology can solve problems?
Group of answer choices
sorting quickly through data
storing data so that it is easily accessible
making value judgments
automating repetitive tasks
Answers
Answer:
making value judgements
Explanation:
honestly this is just a guess if there is any others pick that but this is just what I'm thinking
What tech tool snaps into expansion slots and provides LED readout of the device POST is currently testing
Answers
Answer:
POST Card.
Explanation:
I'm confused as to if subclasses can call the supers without any implementation and what the right answer is

Answers
Answer:
E
Explanation:
Since Example1 and Example2 inherit from Example0, all classes have the method doNothing() at their disposal, so you can call it from e0, e1 and e2.
However, the arguments of this method are Example1 and Example2, so you cannot pass Example0 as a first argument, and you cannot pass Example0 or 1 as a second argument. That only leaves answer E.
You can call the inheritance relation an "is a kind of" relation. So Example1 is a kind of Example0, and Example2 is a kind of Example1, but also Example2 is a kind of Example0.
Now you can understand why e2 can be passed as an argument for Example1, because e2 is a kind of Example1.
A typical report in landscape orientation is 11 inches wide and 8.5 inches tall.
a. True
b. False
Answers
False. A typical report in landscape orientation is not 11 inches wide and 8.5 inches tall.
The statement that a typical report in landscape orientation is 11 inches wide and 8.5 inches tall is incorrect. The dimensions mentioned correspond to a standard letter-size paper in portrait orientation, not landscape.
In the United States, a typical letter-size paper is 8.5 inches wide and 11 inches tall when used in portrait orientation, which means the shorter side is the width and the longer side is the height. However, in landscape orientation, the dimensions are reversed.
In landscape orientation, a typical report would be 11 inches wide and 8.5 inches tall. This orientation allows for a wider layout, with the longer side becoming the width and the shorter side becoming the height.
Landscape orientation is often used when the content of the report, such as charts, tables, or images, benefits from a wider display. It provides more horizontal space, accommodating content that is wider and better suited for presenting information in a horizontal format.
Therefore, the correct answer is b. False. A typical report in landscape orientation would have dimensions of 11 inches wide and 8.5 inches tall.
Learn more about orientation here :
https://brainly.com/question/29977388
#SPJ11
False. A typical report in landscape orientation is not 11 inches wide and 8.5 inches tall.
The statement that a typical report in landscape orientation is 11 inches wide and 8.5 inches tall is incorrect. The dimensions mentioned correspond to a standard letter-size paper in portrait orientation, not landscape.
In the United States, a typical letter-size paper is 8.5 inches wide and 11 inches tall when used in portrait orientation, which means the shorter side is the width and the longer side is the height. However, in landscape orientation, the dimensions are reversed.
In landscape orientation, a typical report would be 11 inches wide and 8.5 inches tall. This orientation allows for a wider layout, with the longer side becoming the width and the shorter side becoming the height.
Landscape orientation is often used when the content of the report, such as charts, tables, or images, benefits from a wider display. It provides more horizontal space, accommodating content that is wider and better suited for presenting information in a horizontal format.
Therefore, the correct answer is b. False. A typical report in landscape orientation would have dimensions of 11 inches wide and 8.5 inches tall.
Learn more about orientation here :
https://brainly.com/question/29977388
#SPJ11
Describe at least five ways in which information technology can
help students studying subjects other than computing.
Answers
Answer:
It can help with; learning how to work things out in other subjects, help children gain access to help with subjects. It can help with studying for a test for any subject. Computers can help with maths because you have access to a calculator and finally. Computers can help with geography as you have access to maps.
Explanation:
What kind of security threat is this?
O A.
О в.
OC.
O D.
ransomware
phishing
identity theft
cyberbullying
Answers
Which of the following commands will install a package using the Red Hat Package Manager, showing all information, while printing pound signs to show the progress of installation
Answers
A command which will install a package on a Linux Computer system by using the Red Hat Package Manager, showing all information and printing pound signs to show the progress of installation is: rpm -ivh packagename.rpm.
What is a Linux command?A Linux command can be defined as a software program that is designed and developed to run on the command line, in order to enable an administrator (end user) of a Linux network perform both basic and advanced tasks by entering a line of text.
In this scenario, we can infer and logically deduce that a command which can be used by an administrator (end user) of a Linux network to install a package on a Linux Computer system by using the Red Hat Package Manager, showing all information and printing pound signs to show the progress of installation is "rpm -ivh packagename.rpm."
Read more on Linux commands here: brainly.com/question/25480553
#SPJ1
Complete Question:
Which of the following commands will install a package using the Red Hat Package Manager, showing all information, while printing pound signs to show the progress of installation?
rpm -iap packagename.rpm
rpm -ivp packagename.rpm
rpm -iah packagename.rpm
rpm -ivh packagename.rpm
Read the following code:
x = totalCost
print(x / 2)
What value will this code calculate?
Answers
Answer:
The value of totalCost divided by 2
Explanation:
Hope this helps! :)
please mark this answer as brainiest :)
Thanks
Melanie needs to ensure that readers are able to locate specific sections within a document easily. What should she include in
the document?
concordance
index
table of contents
bibliography
Answers
Answer:
according to me,she should include an index
Answer:
index
Explanation:
Of the attached Java code, the class RunTransitions.java (along with Transition.java and Controller.java) runs the following three concurrent processes, each consisting of a single transition: Implicitly, each process has two states (before the transition, and after). Now, the other class RunSyncTransitions. java (along with SyncTransition.java and Controller.java) differs from the above only in that it forces the processes to run always in the order: X, Y, Z (try out the attached code). For each of RunTransitions.java and RunSyncTransitions.java: (a) How many states does the corresponding composition of processes have? (b) How many traces does this composition have? (c) What (3D) structure (or shape) does this composition form?
Answers
The composition in RunTransitions.java allows concurrent execution, while RunSyncTransitions.java enforces a specific sequential order with synchronization.
How does the composition of processes differ between RunTransitions.java?The class RunTransitions.java, along with Transition.java and Controller.java, runs three concurrent processes, each consisting of a single transition.
The number of states in the composition of these processes can be determined by multiplying the number of states in each individual process.
The number of traces in the composition is equal to the product of the number of traces in each individual process. The composition forms a linear structure, where each process is executed sequentially.
Similarly, the class RunSyncTransitions.java, along with SyncTransition.java and Controller.java, enforces the processes to run in a specific order: X, Y, Z. The number of states and traces in the composition remain the same as in RunTransitions.java.
However, the composition forms a three-dimensional (3D) structure, where the processes are organized in a sequential order with explicit synchronization.
Learn more about RunTransitions.java
brainly.com/question/31959732
#SPJ11
Your company has assigned you to revise 22 scripts. Since you use the vi editor, how can you set it to automatically display lines as numbered so it is easier for you to work on these revisions
Answers
Answer:
To enable VI editor automatically display lines as numbered, the following steps must be taken:
Step 1: Press the Escape key to exit the insert or append mode.
Step 2. Press the colon key to trigger the cursor. The cursor will appear at the lower-left position of the screen next to a : prompt.
The Next step is to type the following command: set no number hit the enter button to execute the command. This will trigger a column of sequential line numbers will appear at the left side of the display. Each line number references the text located directly to the right of it.
Step 3: To enable this to happen automatically, the appropriate set statement as a line in must be inserted a file in your home directory named .exrc
Cheers!
System software cannot handle technical details without user intervention.a. Trueb. False
Answers
System software cannot handle technical aspects without user interaction. when a single physical computer runs a specialised programme called virtualization software.
The system software is it used by the user?Photo of Without user input, system software cannot handle technical details. The components of a computer system's user interface that enable user interaction. A user interface, sometimes referred to as a human-computer interface, is made up of both hardware and software elements. It manages communications between users and the system.
What do you describe a type of computer application that routinely executes additional tasks without user input while running in the background?A background process is a computer operation that runs automatically without user involvement. These applications frequently handle activities related to logging, system monitoring, scheduling, and user notification.
To know more about system software visit:-
https://brainly.com/question/12908197
#SPJ4
write the order of tasks that each person completes in order to make mashed potatoes in the shortest time. in order to format your answer, write the sequence of tasks each person does, with commas between tasks of one person, and semicolons between task lists of different people. for example, if you submit 0,1,2,4;3,5, person 0 will do tasks 0, 1, 2, and 4 (in that order), and person 1 will do tasks 3 and 5 (in that order). this will take 33 minutes total. you may add spaces, and order the task lists in any order. for example, the autograder will consider the above answer as equivalent to the submission 3,5;0,1,2,4 and the submission 0, 1, 2 ,4 ;3 ,5
Answers
To make mashed potatoes in the shortest time, the tasks can be divided among multiple people. Here is one possible distribution of tasks:
Person 1: Peel and chop potatoes, Boil water, Drain potatoes, Mash potatoesPerson 2: Set the table, Prepare butter and milk, Season mashed potatoe Person 3: Make gravy, Serve mashed potatoes and gravyThe sequence of tasks for each person can be represented as follows:Person 1: Peel and chop potatoes, Boil water, Drain potatoes, Mash potatoesPerson 2: Set the table, Prepare butter and milk, Season mashed potatoesPerson 3: Make gravy, Serve mashed potatoes and gravyNote: The order of the task lists can be rearranged, and spaces can be added for clarity. The autograder will consider answers with equivalent task sequences as correct.
To know more about tasks click the link below:
brainly.com/question/32317663
#SPJ11
When do you use a while loop instead of a for loop? (Select multiple answers)
1. You do not know how many times a loop will need to run
2. To do number calculations
3. When using a count variable
4. To repeat code.
Answers
Answer:
1. You do not know how many times a loop will need to run
4. To repeat code.
Explanation:
Required
When to use while loop instead of for loop?
Option 1 and 4 answer the question
1. You do not know how many times a loop will need to run
Using while loop in this case is suitable to the for loop.
Take for instance
You want a set of instruction to be repeated until the user enters 1
e.g.
while a != 1:
print("abc")
print("def")
a = int(input("Input: "))
The above is written in Python
The print instructions will be repeated until the user enter 1.
Now, you do not know if the user will enter 1 the first time or the 100th time or the 10000th time.
In other words, you don't know how many times the loop will be executed.
In this case, while loop is preferred to for loop
4. To repeat code:
The same analysis as used in (1) above is applicable in (4).
The print statements in
while a != 1:
print("abc")
print("def")
a = int(input("Input: "))
will be repeated until the user enters 1
The for loop isn't preferable in this case
Other options (2) and (3) can be implemented using both the for loops and the while loops
The while loops allows the execution of a block of code over and over again until a condition or certain conditions are met. The while lop are used instead of the for loop in the following circumstances :
You do not know how many times a loop will need to runWhen using a count variableCertain loops requires that a condition is met before the loop terminates. While some loops have a clear and predictable number of runs, some do not. Hence, due to this unpredictability, while loops are preferred :
Code snippet in python :
num = int(input())
while num < 5 :
print('invalid')
num = int(input())
Also, when using a count variable, the while loops is more appropriate as also more appropriate ;
Code snippet in python :
count = 20
while count > 0 :
print('available')
count -= 1
Therefore, the while loop is more appropriate for a loop with an unknown number of runs and when using the count variable.
Learn more :https://brainly.com/question/15745784
YOOO CAN ANYONE SOLVE THIS IN JAVA??
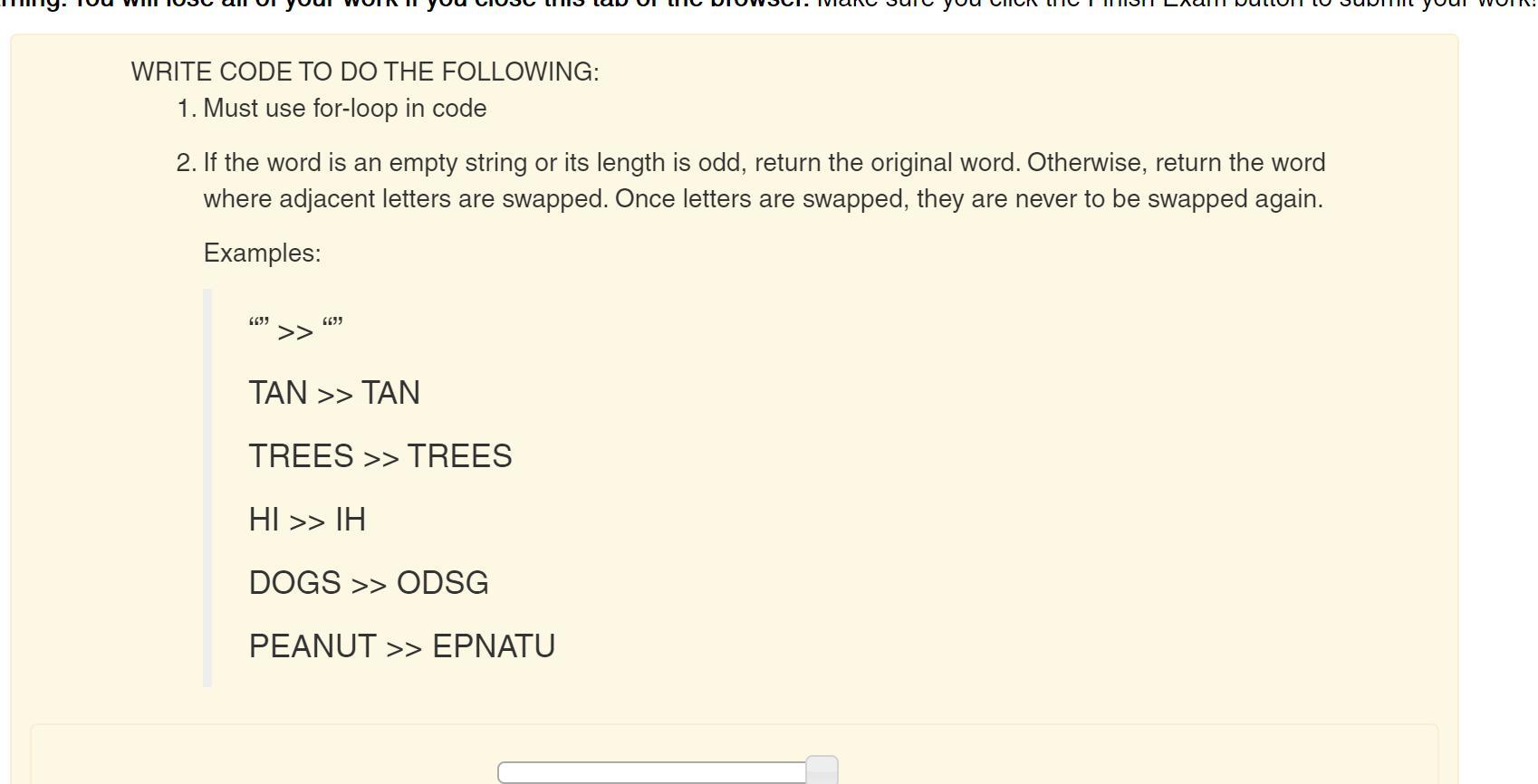
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
how and why Steve Jobs left Apple Computer.
Answers
Answer:
Jobs was forced out of Apple in 1985 after a long power struggle with the company's board and its then-CEO John Sculley. ... He was largely responsible for helping revive Apple, which had been on the verge of bankruptcy.
Explanation:
A user has multiple web pages open and is using email. Which layer of the Transmission Control Protocol/Internet Protocol (TCP/IP) model is responsible for sorting the data to send email and web pages to the appropriate location?
a) Transport
b) Network
c) Data link
d) Application
Answers
Answer:
This is the second question like this I've seen. They aren't the greatest.
Explanation:
The question is not good. The answer would be option a, Transport even though it doesn't make a whole lot of sense when you really go into detail.
It could also be option d, Application but I think they're going for the first.