Help fast pls
Think of a game you played recently. Would you say it’s a “good” game? Why or why not? What might someone who disagrees with you point to in a discussion about whether the game was good or not? Do you think you could ever enjoy a game even if you didn’t think it was a “good” game?
Answers
Answer:
I have been playing Rocket League and I would say that it is a good game. In it you will need to learn many mechanics and grow your game sense. The satisfaction of seeing yourself getting better in it is great and you would have fun playing it. It is a cycle of winning and losing and learning from your mistakes. I've seen some people disagree with me and say that it is too hard or it is for kids or its not fun, but at the bottom of the line everyone has his own taste in video games. I wouldn't see myself ever enjoy a game if it was not a good unless it was hilariously bad and I had some fun with it.
Related Questions
describe how to modify a nat router to prevent packets with spoofed ip addresses from exiting a private network.
Answers
The most popular technique for doing this is packet filtering. systems for filtering packets, which are frequently found in routers and firewalls.
the ability to identify discrepancies between the packet's IP address and the appropriate IP addresses listed on access control lists (ACLs). Additionally, they spot suspicious packages. This proves that NAT is not a technique for preventing spoofing. Similar to the scenarios without NAT illustrated previously in this chapter, it is necessary to check customer source addresses as close to the customer as possible even while employing NAT. Only then will it be possible to stop faked and/or untraceable packets from entering the Internet. Then, use a firewall, which employs a packet filter that examines IP packet headers, to keep an eye out for suspicious activity on your network. Visit only secure websites that employ the HTTPS protocol.
Learn more about addresses here-
https://brainly.com/question/29065228
#SPJ4
which frequency band is used by commercial am radio stations?
Answers
The frequency band used by commercial AM radio stations is in the range of 535 to 1605 kilohertz (kHz).
commercial AM radio stations use a frequency band in the range of 535 to 1605 kilohertz (kHz). This frequency range is also known as the Medium Wave (MW) band. AM radio stations transmit audio signals using the amplitude modulation (AM) technique. In AM modulation, the amplitude of the carrier wave is varied in accordance with the audio signal. This modulation allows the audio signal to be carried by the radio wave.
The frequency range of 535 to 1605 kHz is allocated specifically for AM radio broadcasting. The Federal Communications Commission (FCC) in the United States regulates the allocation of radio frequencies for different purposes, including AM radio broadcasting. The MW band is widely used by commercial AM radio stations to transmit news, talk shows, music, and other forms of audio content.
AM radio signals can travel long distances during the night due to the reflection and refraction of radio waves in the Earth's ionosphere. This phenomenon allows AM radio stations to reach listeners far away from the broadcasting station. However, during the day, the range of AM radio signals is limited due to interference from other sources and the absorption of radio waves by the Earth's atmosphere.
Learn more:
About commercial AM radio stations here:
https://brainly.com/question/251960
#SPJ11
The commercial AM radio stations typically use frequencies between 530 kilohertz (kHz) and 1,710 kilohertz (kHz) within the electromagnetic spectrum.
The allocation of radio frequency bands is done by the Federal Communications Commission (FCC) and the radio station operators must have a license issued by the FCC to operate within a particular frequency band. The allocation of frequency bands is done in a way that avoids any interference or overlapping between the channels to ensure that the radio signals do not interfere with each other. The FCC allocates frequency bands in order to preserve the radio spectrum for the future generations.
The frequency band used by the commercial AM radio stations is known as the Medium Wave (MW) band, which is part of the radio spectrum. The AM radio waves have a lower frequency range than the FM radio waves and they are longer. The AM radio signals have the ability to travel long distances and can pass through buildings and other obstacles. AM radio is used by many commercial radio stations because it is widely available, inexpensive, and has a wide range of coverage.
Learn more about commercial AM: https://brainly.com/question/1432446
#SPJ11
what is 9+10/2x^3?
Please answer ;D
Ratez?



Answers
Answer:
5
3
+
9
Explanation:
PLEASE HELP ASAPP!!! WILL MARK BRAINLIEST! IF YOU KNOW PSEUDOCODE HELP PLEASE!!
ACSL WHAT DOES THIS PROGRAM DO (LOOPING)

Answers
The program outputs 11 numbers which are the first 11 Fibonacci numbers. The program uses a loop that goes through each number and checks if the sum of two values, "a" and "b", is equal to the loop variable "x".
What does this program do?
In the program, there is a "for" loop that iterates from 1 to 11. For each iteration, it inputs a number "n" and then calculates the value of "b" as the integer division of "n" by 10. If the condition "a + b == x" is satisfied, it outputs the value of "n".
Since the input values are the first 11 Fibonacci numbers (1, 1, 2, 3, 5, 8, 13, 21, 34, 55, 89), they will all be output because the condition "a + b == x" is always true.
To learn more about Fibonacci numbers, visit: https://brainly.com/question/14771443
#SPJ1
Where are some places that cyberbullying occurs? Check all that apply.
in classrooms
in text messages
on playgrounds
on websites
on social media networks
in chat rooms
Answers
Answer:
B, D, E, F
Explanation:
Brainliest??
These findings imply that bullying has found a new “playground” in internet. Bullying does happen online, and it happens regularly. Thus option B, D, E, F is correct.
What are the different place where cyberbullying occurs?Although it occurs frequently everywhere, cyberbullying is most common in India, Brazil, and the United States. Over 65% of parents worldwide list cyberbullying on social media as one of their top concerns, according to statistics on this topic.
Sending hurtful SMS or IMs to someone is one form of cyberbullying. Pranking a person's mobile device.
These aggressive acts can quickly and badly harm anyone and are extremely harmful. They occur in public forums, social media platforms, and other online discussion boards.
Therefore, Online bullying also refers to cyberbullying and cyberharassment.
Learn more about cyberbullying here:
https://brainly.com/question/8142675
#SPJ2
What are two examples of license conversions you can perform wiht windows server 2016? choose two.
Answers
Two examples of license conversions you can perform with Win-dows Server 2016 are:
1. Transition from Standard to Datacenter: Windows Server 2016 allows you to convert a Standard Edition license to a Datacenter Edition license. This conversion provides additional features and capabilities, such as unlimited virtual machine instances, software-defined networking, and storage features. To perform this conversion, you need to have a valid Datacenter Edition key, and then you can use the "DISM" command-line tool or the Volume Activation Management Tool (VAMT) to change the product key.
2. Downgrade from Datacenter to Standard: If you have a Windows Server 2016 Datacenter Edition license but want to use the Standard Edition instead, you can perform a license conversion. This allows you to reduce the number of features and virtual machine instances, resulting in cost savings. To downgrade, you need a valid Standard Edition key, and you can use the same tools mentioned above to change the product key.
In Windows Server 2016, license conversions enable you to change the edition of your server without reinstalling the operating system. This flexibility allows organizations to adapt their licensing needs as their requirements change. By converting licenses, you can take advantage of different features and adjust costs accordingly.
It's important to note that license conversions may have specific requirements and limitations, such as eligibility based on the Software Assurance program or the need to contact Microsoft support. Therefore, it is recommended to consult official Microsoft documentation or licensing experts for specific details and guidance regarding license conversions in Windows Server 2016.
Learn more about operating system: https://brainly.com/question/29532405
#SPJ11
The OpenMP clause "num_threads(16)" results in 16 threads being forked.true/false
Answers
True. The OpenMP clause "num_threads(16)" specifies that the program should create 16 threads, which is commonly referred to as "forking" in OpenMP terminology.
The OpenMP clause "num_threads(16)" specifies the number of threads to be used in the parallel region. Therefore, if this clause is used within a parallel region, it will result in the forking of the specified number of threads, in this case, 16 threads. So, the statement is true. When the "num_threads" clause is used in an OpenMP parallel region, it sets the number of threads to be created to execute the code within the region. If the number of threads specified is greater than the available hardware threads, the actual number of threads created will be the number of hardware threads available.
Learn more about clause here-
https://brainly.com/question/19711531
#SPJ11
The answer to this problem
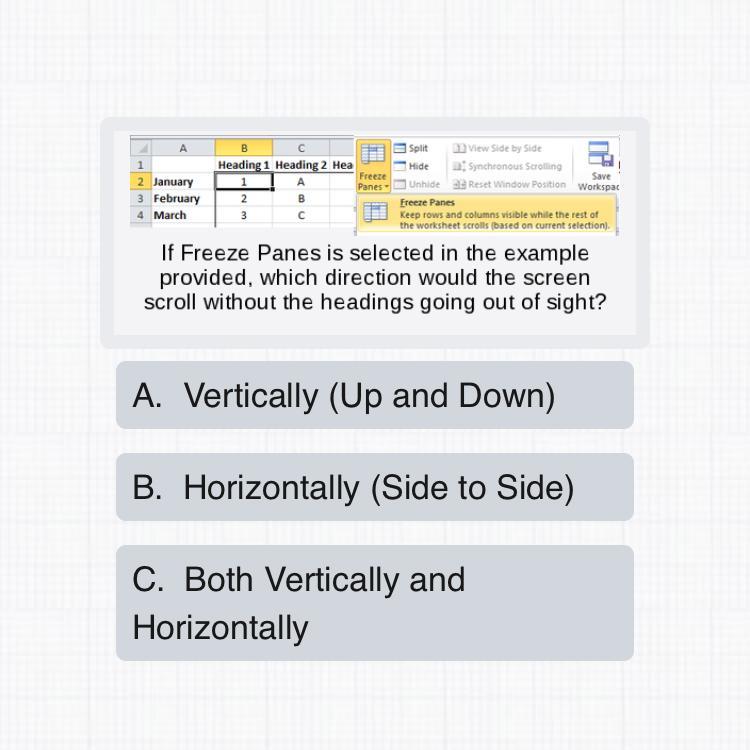
Answers
PLEASE HELP ME
Copy the following text into a word processing document:
We conducted a survey of 50 employees last week to determine what activity the
majority would want to do for the next company outing. The survey found that 27
mployees wanted to go bowling, 13 employees wanted to have a cookout, six
mployees wanted to watch a movie, and four employees wanted to volunteer at a
Ocal charity event. Based on the survey results, we are scheduling a bowling night
or next month."
Format your paragraph so it uses 1.5 line spacing and is justified. Submit your
ample to your teacher along with this worksheet. (1 point)

Answers
The steps to executing the above Desktop Publishing assignment is as follows:
Open Mic. rosoft Word on your computerHighlight the referenced text and paste onto the empty work spaceHighlight all the text using CTRL + ANavigate to the Justification Button/ Tool as shown in the image and clickWhile keeping the text highlighted, click on the "Line and Spacing Tool" as indicated in the imageSelect the "1.5" spacing action buttonUse CTRL + S to save your work.What is desktop publishing?Desktop publishing is the process of creating documents on a computer using page layout software. It was virtually solely used for print publications at initially, but it now now aids in the development of numerous types of web material.
A desktop publishing software (DTS), sometimes known as a "page layout program" or "publishing program," has full page design features, such as magazine-style columns, rules and borders, page, chapter, and caption numbering, and accurate typographic alignment.
Learn more about desktop publishing:
https://brainly.com/question/7221277
#SPJ1

What are some of the benefits of project
management? (choose all that apply)
The project is more likely to be finished on
time.
The project is free.
The project is completed by another team.
Tasks can be done more efficiently.
Answers
Answer:
The project is more likely to be finished on time.
Tasks can be done more efficiently.
Explanation:
Project management refers to the process involved in the management and accomplishment of the project. It includes the process, techniques, and guidance to carry on to complete a project. Project management helps in achieving the desired outcomes of the project. The efficient use of the resources and the proper management of the skills are ensured in project management. Better communication and an increase in satisfaction help in improving productivity.
Some of the benefits of project management are:
A. Projects are more likely to be finished on time.
D. Tasks can be done more efficiently
What is Project Management?Project Management can be defined as the application of processes, knowledge, techniques, skills and experience in other to execute project goals and objectives based on the agreed project parameters laid down as acceptable.Project management helps in efficiently completing a project in good time.Therefore, some of the benefits of project management are:
A. Projects are more likely to be finished on time.
D. Tasks can be done more efficiently
Learn more about project management on:
https://brainly.com/question/6500846
a network administrator is installing a device that uses redundant array of independent disks (raid) technologies for redundancy and provides employees remote access so that files can be accessed anywhere. the device does not require licensing and stores data at the file level. which device is the employee likely installing in the infrastructure?
Answers
The system is unlicensed and stores data at the file level. The employee is most likely installing the NAS device in the infrastructure.
Data can be saved and kept in three different ways: in files, blocks, and objects. Digital information storage facilitates data tracking. You can locate certain records using the document management system's built-in search functions. These systems also allow you to sort data, which makes it simpler to find information. With a few clicks, you can access the information you need. Using HDD, SSD, and USB digital drives for data storage for external hard disks, you can use any of these methods, but I strongly advise choosing one of them. A solid-state drive (SSD) for an external backup is an excellent option if you plan to store the data for a long period.
Learn more about Data here:
https://brainly.com/question/29488896
#SPJ4
Wireless vulnerability assessment begins with the planning, scheduling, and notification of all Internet connections, and is usually performed on the organization's networks using every possible approach to penetration testing. a. True b. False
Answers
Wireless vulnerability assessment begins with the planning, scheduling, and notification of all Internet connections, and is usually performed on the organization's networks using every possible approach to penetration testing: B. False.
Vulnerability assessment can be defined as a systematic analysis and review of any form of security weakness in an information system (IS).
Hence, vulnerability assessment is used to determine if an information system (IS) is susceptible (prone) to attacks from users within and outside the network.
On a related note, wireless vulnerability assessment involves the analysis and review of a wireless network to verify its level of security.
Hence, it begins with planning and scheduling of the assessment of the organization's networks using every possible approach to penetration testing, at regular intervals.
However, you shouldn't notify all Internet connections when conducting a wireless vulnerability assessment because it defeats the aim and objective of security assessment.
Read more: https://brainly.com/question/24112967
which cellular technology is compromised of hspa and ev-do to provide higher data speeds than previous cellular data protocols?
Answers
The cellular technology that is compromised of HSPA and EV-DO to provide higher data speeds than previous cellular data protocols is called HSPA+ and EV-DO Rev A. Cellular technology refers to the various technologies and standards used for mobile telecommunication.
HSPA, which stands for High-Speed Packet Access, is a 3G (third generation) cellular technology that provides faster data speeds than previous 2G technologies. It uses a combination of Time Division Multiplexing (TDM) and Code Division Multiple Access (CDMA) to increase data transmission rates. HSPA is an evolution of WCDMA (Wideband Code Division Multiple Access), which is the technology used in 3G networks. HSPA+ is an enhanced version of HSPA, which provides even faster data speeds.
Learn more about HSPA, here https://brainly.com/question/14455214
#SPJ4
security activities such as use of security badges and guards, conducting background checks on applicants and using antivirus software and passwords, would be classified as:
Answers
Security activities such as the use of security badges and guards, conducting background checks on applicants, and utilizing antivirus software and passwords are crucial components of an organization's overall security strategy. These measures can be collectively classified as physical and information security practices.
For more such question on malware
https://brainly.com/question/399317
#SPJ11
Kari listens as her photography teacher discusses the pixel count of an image file. What is her teacher MOST LIKELY covering in class?
Answers
Since, Kari listens as her photography teacher, the thing that her teacher will MOST LIKELY be covering in class is Image pixel (Image size).
What does pixels mean in photography?The term Pixel is known to be used in digital imaging, a pixel(or picture element) is known to be a term that connote the smallest item of information in an image.
Therefore, Since, Kari listens as her photography teacher, the thing that her teacher will MOST LIKELY be covering in class is Image pixel (Image size).
Learn more about Image pixel from
https://brainly.com/question/13187073
#SPJ1
The table shows a company's income and expenses over the last 7 days.
day
of income expenses
week
sun. $ 169.56 $ 256.25
mon. $ 217.61 $ 195.79
tues. $ 150.89 $1208.55
wed. $ 409.73 $ 709.11
thurs. $ 687.45 $ 190.98
fri. $1563.09 $ 325.78
sat. $1267.92 $ 315.64
the company found that its weekly income and expenses were approximately the same from week to week.
select the correct definition of the variable x
o x = number of weeks
o x = weekly expenses
o x = day of the week
o x = weekly income
Answers
correct definition of the variable x is: x = number of weeks. So correct answer is A
Based on the information given in the table, the variable x represents the number of weeks. This is because the company found that its weekly income and expenses were approximately the same from week to week. Therefore, in order to analyze the company's overall income and expenses, we need to consider the data from multiple weeks.
The other variables listed are not the correct definition of x. Weekly expenses and weekly income are related to the company's financial performance, but they are not the variable being represented by x in this scenario. Day of the week is simply a descriptor of the data presented in the table, and is not a variable at all.
To further explain, x is the independent variable that we are interested in studying. In this case, we want to understand how the company's income and expenses vary over multiple weeks. By examining the data from different weeks, we can identify trends and patterns in the company's financial performance. This information can then be used to make informed decisions about how to manage the company's finances going forward.
In summary, the variable x in this scenario represents the number of weeks, and it is important because it allows us to analyze the company's overall financial performance over time.
To know more about weeks visit:
brainly.com/question/23202659
#SPJ11
A forensic investigator gathers potential evidence from many software, hardware, and other sources. There is an order in which the evidence needs to be gathered. The order of volatility describes the process of capturing data based on the volatility of said data.
Place the following items in the correct order of volatility in the gathering of potential evidence:
swap/page file
remote logs
archived data
random access memory
hard drive
Answers
The correct order of volatility in the gathering of potential evidence is as follows "Random Access Memory (RAM), Swap/Page File, Remote Logs, Hard Drive, Archived Data".
The order of volatility refers to the sequence in which data should be collected during a forensic investigation based on its volatility or the likelihood of it being lost or changed. The most volatile data, which is easily lost or modified, is captured first, while less volatile data is collected later.
Random Access Memory (RAM) is the most volatile as it holds data that is lost when the system is powered off. Therefore, it is collected first. Swap/Page File is the next in order as it contains data that may be swapped in and out of RAM. Remote Logs are collected next, as they are typically stored on remote systems and may be modified or lost. Hard Drive data is collected next, followed by Archived Data, which is the least volatile as it is usually stored in long-term backups or archives.
Therefore, the correct order of volatility is RAM, Swap/Page File, Remote Logs, Hard Drive, and Archived Data.
You can learn more about order of volatility at
https://brainly.com/question/31929510
#SPJ11
Which of the following characters are wildcards in Excel? (Check all that apply.) O & Os #
Answers
The wildcards recognized in Excel are the * and ? characters.
In Excel, wildcards are special characters used to represent unknown or uncertain characters in a search string. The ? wildcard replaces a single character within a string, while the * wildcard can replace any number of characters within a string.
These wildcards are helpful when you need to perform searches or filtering operations with flexible criteria. However, it's important to note that characters like O, Os, and # are not recognized as wildcards in Excel. So, the correct answer to the question is that the wildcards in Excel are the * and ? characters.
Know more about wildcards recognized in Excel here:
https://brainly.com/question/31944796
#SPJ11
The wildcards in Excel are the asterisk (*), the question mark (?), and the tilde (~).
In Excel, there are three characters that are considered wildcards:
asterisk (*): The asterisk represents any number of characters. For example, if you search for 'cat*', it will match 'cat', 'cats', 'caterpillar', and so on.question mark (?): The question mark represents a single character. For example, if you search for 'c?t', it will match 'cat', 'cut', 'cot', and so on.tilde (~): The tilde is used as an escape character. If you want to search for the actual asterisk (*) or question mark (?) as a literal character, you can use the tilde (~) before them. For example, '~*' will search for the actual asterisk (*) character.These wildcards are useful when you want to find data that matches a specific pattern or when you are unsure about the exact value you are searching for.
Learn more:About wildcards here:
https://brainly.com/question/10248652
#SPJ11
consider the wide-flange beam shown in the figure below. calculate the maximum and minimum shear stresses in the web and sketch and shear stress distribution.
Answers
The maximum and minimum shear stresses in the web of the wide-flange beam can be calculated using the formula: where V is the shear force, Q is the first moment of area of the section above the point where shear stress is being calculated, t is the thickness of the web, and I is the moment of inertia of the entire section.
To sketch the shear stress distribution, we can plot the shear stress values at various points along the web. To calculate the maximum and minimum shear stresses in the web, we need to first find the shear force acting on the beam. Once we have the shear force, we can use the formula mentioned above to calculate the shear stress at different points along the web. To sketch the shear stress distribution, we need to plot the shear stress values at different points along the web. We can do this by calculating the shear stress at various points along the web and then plotting them on a graph. The x-axis of the graph will represent the distance along the web, while the y-axis will represent the shear stress values.
The resulting graph will show how the shear stress varies along the length of the web. We can use this information to determine the maximum and minimum shear stresses in the web. However, I can guide you through the process of calculating the maximum and minimum shear stresses in the web of a wide-flange beam. Please provide the necessary details such as the dimensions of the beam, load applied, and any other required information. Once you provide the required information, I will be able to give you an followed by a step-by-step on how to calculate the maximum and minimum shear stresses, as well as guide you on how to sketch the shear stress distribution.
To know more about web visit :
https://brainly.com/question/12913877
#SPJ11
the fact that everyone is a publisher means: a. all of these are correct. b. hiring a programmer to create a website is no longer necessary. c. there is content clutter. d. users can create and interact with the content they see. e. strong coding knowledge is no longer necessary to create a website.
Answers
Answer is option a) All of these are correct
Web Development :
While everyone was manually coding their sites in the early days of the internet, many websites are now built with a content management system (CMS). A CMS removes the need to code by offering a visual interface to build web pages and structure your site.
The website developer is a web development specialist. A professional website developer's web solution will be more technically complex and advanced than the website you build. They can have any sophisticated features you want. Front-end developers have more experience developing tools that improve the user experience. If you have a design concept that must work across multiple browsers and computers, you should hire a front-end developer. Back-end developers are essentially computer programmers who specialise in the development of Web applications. They are capable of developing content management systems, security features, and data management tools.
Web programmers, also known as web developers or web engineers, create web-based applications. Their work focuses on non-design aspects of web development, such as coding and markup. Coding is the process of writing software, whereas markup is the process of organising and formatting text. The web programmer receives user requests for a specific web application, converts the request into coding, and creates a working online application. Web designers typically lack experience with computer programming. They may understand the fundamentals of HTML, CSS, and other common tools, but they are not the people you want to hire to build a website.
To learn more web development refer:
https://brainly.com/question/25941596
#SPJ4
.............. 1010111 needs to be transferred w.ith odd parity and the answer is
A. 01010111
B.11010111
C.10101110
D.10101111
Answers
Answer:
A. 01010111
Explanation:
This is because in odd parity, the number on the far left (the 8th number) would always be a 0
Why is cyber security an important part of sending information using digital signals
Answers
Cyber security is an important part of sending information using digital signals. Because it keeps data safe while stored in the cloud and when they are transmitted. Option D is correct.
What are cybersecurity functions?Analysts in cybersecurity defend an organization's hardware and network infrastructure against hackers and cybercriminals looking to harm them or steal confidential data.
When conveying information via digital signals, cyber security is a crucial component. because it protects data as it is sent and stored in the cloud.
Hence, option D is correct.
To learn more about cybersecurity refer;
https://brainly.com/question/27560386
#SPJ1

What can you add to your presentation from the Insert tab?
Animations
Pictures
Variants
Transitions
Answers
Answer:
B. PICTURES
Explanation:
Answer:
I know its late but pictures is the answer.
Explanation:
I took the test and got it right.
Create a flowchart to find the total of 10 negative numbers start from -1.
Answers
Here is a simple flowchart to find the total of 10 negative numbers starting from -1:
```
Start
↓
Set total = 0
Set counter = 1
↓
While counter <= 10
|
├─ Yes ─┬─→ Add counter to total
│ ↓
│ Increment counter by 1
│
├─ No ──┬─→ Display total
↓
End
```
In this flowchart, we start by initializing the total to 0 and the counter to 1. Then, we enter a loop that continues as long as the counter is less than or equal to 10. Inside the loop, we add the current value of the counter to the total, and then we increment the counter by 1. Once the loop finishes, we display the total.
\(\huge{\mathfrak{\colorbox{black}{\textcolor{lime}{I\:hope\:this\:helps\:!\:\:}}}}\)
♥️ \(\large{\textcolor{red}{\underline{\mathcal{SUMIT\:\:ROY\:\:(:\:\:}}}}\)
A binding constraint limits the value of the objective function. If it could be ______________, an improved solution would be possible.
Answers
A binding constraint limits the value of the objective function. If it could be relaxed, an improved solution would be possible.
How can relaxing a binding constraint lead to an improved solution?A binding constraint is a constraint in a mathematical optimization problem that restricts the values that the variables can take on, thereby influencing the value of the objective function.
It acts as a limiting factor, defining the feasible region where optimal solutions can be found. When a constraint is binding, it means that the solution lies on the boundary of the feasible region.
In certain cases, relaxing or loosening a binding constraint can lead to an improved solution. By relaxing a constraint, the feasible region expands, allowing for a broader range of possible solutions. This can result in a better objective function value or a more optimal outcome.
Relaxing a binding constraint may be beneficial when the constraint is overly restrictive or when the problem circumstances change, allowing for more flexibility in the solution space.
However, it is important to consider the implications of relaxing a constraint, as it can impact the feasibility or validity of the solution and may have consequences for other aspects of the problem or system.
Overall, relaxing a binding constraint has the potential to open up new possibilities and improve the solution quality, but careful analysis and evaluation of the problem context are essential to determine the appropriateness and consequences of such relaxation.
Learn more about binding constraint
brainly.com/question/29988671
#SPJ11
Really need help ASAP

Answers
Answer:
D
was there a picture cause that question is dumb if there wasn
Explanation:
1)Which tool can you use to find duplicates in Excel?
Select an answer:
a. Flash Fill
b. VLOOKUP
c. Conditional Formatting
d. Concatenation
2)What does Power Query use to change to what it determines is the appropriate data type?
Select an answer:
a.the headers
b. the first real row of data
c. data in the formula bar
3)Combining the definitions of three words describes a data analyst. What are the three words?
Select an answer:
a. analysis, analyze, and technology
b. data, programs, and analysis
c. analyze, data, and programs
d. data, analysis, and analyze
Answers
The tool that you can use to find duplicates in Excel is c. Conditional Formatting
b. the first real row of datac. analyze, data, and programsWhat is Conditional Formatting?Excel makes use of Conditional Formatting as a means to identify duplicate records. Users can utilize this feature to identify cells or ranges that satisfy specific criteria, like possessing repetitive values, by highlighting them.
Using conditional formatting rules makes it effortless to spot repeated values and set them apart visually from the other information. This function enables users to swiftly identify and handle identical records within their Excel worksheets, useful for activities like data examination and sanitation.
Read more about Conditional Formatting here:
https://brainly.com/question/30652094
#SPJ4
what type of double data rate sdram uses 288 pins?
Answers
DDR4 SDRAM uses a 288-pin configuration, allowing for faster data transfer rates and improved performance compared to earlier generations.
DDR SDRAM (Double Data Rate Synchronous Dynamic Random Access Memory) is a type of computer memory that allows for faster data transfer rates compared to earlier generations of SDRAM. The number of pins on a DDR SDRAM module is an important factor that determines its compatibility with the motherboard and memory slots.
In the case of DDR4 SDRAM, it utilizes a 288-pin configuration. This means that the DDR4 memory module has 288 electrical contacts or pins on its edge connector. These pins are used for communication and data transfer between the memory module and the motherboard.
The increase in the number of pins from previous DDR memory standards (such as DDR3 with 240 pins) allows for more data channels and improved data transfer rates. DDR4 SDRAM offers higher bandwidth and better performance compared to its predecessors, making it a popular choice in modern computer systems.
The 288-pin configuration of DDR4 SDRAM ensures proper alignment and compatibility with motherboards that support DDR4 memory. It is important to note that DDR4 memory modules are not backward compatible with DDR3 or earlier memory slots, as the pin configurations and other technical specifications differ between the generations.
Learn more about SDRAM here:
https://brainly.com/question/32554435
#SPJ11
Question 38 of 40
What is efficiency?
A. Doing more than one task at a time
B. The activity of selecting what to do next
C. A measure of output for any given project, task, or activity
D. The ability to do something well without wasted time or effort
Answers
Answer:
The answer should be d i think.
Which ITIL concept could be described as a generic description for many varying types of demands that are placed upon the IT department by the users?
Answers
The ITIL concept that could be described as a generic description for many varying types of demands placed upon the IT department by users is "Service Request." This term encompasses various user-initiated requests for assistance, information, or access to IT resources and services.
The ITIL concept that could be described as a generic description for many varying types of demands that are placed upon the IT department by the users is "Service Request Management." Service Request Management is a process that deals with user requests for information, advice, or routine services. It is designed to manage the lifecycle of all service requests from initiation to fulfillment, providing a standardized and consistent way of handling requests from users. This concept includes the management of various types of requests, such as requests for access, information, assistance, or changes to existing services. In long answer, Service Request Management helps to ensure that the IT department meets the needs of users in a timely and efficient manner, thereby improving customer satisfaction and enhancing the reputation of the IT department.
To know more about demands visit :-
https://brainly.com/question/30402955
#SPJ11