Create a list called numbers containing the values from 1 through 15, then use slices to perform the following operations consecutively: a. Select number’s even integers. b. Replace the elements at indices 5 through 9 with 0s, then show the resulting list. c. Keep only the first five elements, then show the resulting list. d. Delete all the remaining elements by assigning to a slice. Show the resulting list.
Answers
Answer:
Kindly check explanation
Explanation:
From python :
List containing values from 1 through 15:
my_list = list(range(1,16))
#creates a list of values from 1 to 15,(16 is excluded)
B.) select even integers :
for digits in my_list :
if digit%2 == 0;
print(digit)
# prints numbers in the list which does not leave a remainder when divided by .
C.)
for digits in my_list[4,9]:
my_digit[digits] = 0
my_digits
#Replaces the elements at indices 5 through 9 with 0s, then show the resulting list.
D.)
my_digits[:5]
#selects digits with index 0 up to 4
E.)
del my_digits[:5]
#DELETE elements in my digits starting from the fifth index
Related Questions
Write a program that reads two numbers from the user, and proceeds as follows: If the input numbers are equal, the program displays: both numbers are the same. Otherwise, the program logs all the integers in the range of the input numbers from the smaller value to the larger value in the console. For example, if the user enters 22 and 16, the program displays: 16 17 18 19 20 21 22. Note that all the numbers are displayed in one line separated by a single space. . If any of the input values are invalid, the program displays an error message and terminates.
Answers
import sys
x = input("enter number 1: ") #ask for user input
y = input("enter number 2: ")
output = "" #the output string
try: #try integering them (this also has error message and will check if input is valid)
x = int(x)
except:
print("error! number 1 was not a number :(")
sys.exit() #leave
try:
y = int(y)
except:
print("error! number 2 was not a number :(")
sys.exit()
if x == y: #check they are not the same
print("both numbers are the same")
else: #do the thing
if y > x: #otherwise swap the order
for i in range (x, y + 1): #+1 for inclusive
output = (output + str(i) + " ")
else:
for i in range (y, x + 1):
output = (output + str(i) + " ")
print(output) #so it's all in one line
ed 4. As a network administrator of Wheeling Communications, you must ensure that the switches used in the organization are secured and there is trusted access to the entire network. To maintain this security standard, you have decided to disable all the unused physical and virtual ports on your Huawei switches. Which one of the following commands will you use to bring your plan to action? a. shutdown b. switchport port-security c. port-security d. disable
Answers
To disable unused physical and virtual ports on Huawei switches, the command you would use is " shutdown"
How doe this work?The "shutdown" command is used to administratively disable a specific port on a switch.
By issuing this command on the unused ports, you effectively disable those ports, preventing any network traffic from passing through them.
This helps enhance security by closing off access to unused ports, reducing the potential attack surface and unauthorized access to the network.
Therefore, the correct command in this scenario would be "shutdown."
Learn more about virtual ports:
https://brainly.com/question/29848607
#SPJ1
Arnie is planning an action shot and wants the camera to move smoothly alongside his running characters. He is working on a tight budget and can’t afford expensive equipment. What alternatives could you suggest?
Mount the camera on a wagon, wheelchair, or vehicle and move it next to the characters.
Rearrange your script so you don’t need to capture the motion in that way.
Try running next to the characters while keeping the camera balanced.
See if you can simulate the running with virtual reality.
Answers
Where did the name "QWERTY" come from?
Answers
Answer:
From the keyboard layout invented by Christopher Lathem Sholes. It is now the most used keyboard layout throughout the world
Which of the following is the main federal law protecting job applicants against discrimination based on race, color, religion, national origin,
disability, or genetic information?
Answers
The main federal law protecting job applicants against discrimination based on race, color, religion, national origin, disability, or genetic information is Title VII. The correct option is c.
What is Title VII of federal law?Federal laws are standards that have been evaluated by both legislatures of Congress, have the signature of the president, have counteracted the president's vote, or have otherwise been given the go-ahead to become a legal document.
Employment discrimination based on racial, ethnic, religious, sexual, and national origin is illegal under Title VII.
Therefore, the correct option is c. Title VII.
To learn more about federal law, refer to the link:
https://brainly.com/question/14443349
#SPJ9
The question is incomplete. The missing options are given below:
a. Title I
b. Title IV
c. Title VII
d. Title III
The ethical and appropriate use of a computer includes_____. Select 4 options.
Answers
The ethical and appropriate use of a computer encompasses several key principles that promote responsible and respectful behavior in the digital realm.
Four important options include:
1. Always ensuring that the information you use is correct: It is essential to verify the accuracy and reliability of the information we use and share to avoid spreading false or misleading content.
Critical evaluation of sources and fact-checking are vital in maintaining integrity.
2. Never interfering with other people's devices: Respecting the privacy and property rights of others is crucial. Unauthorized access, hacking, or tampering with someone else's computer or devices without their consent is unethical and a violation of their privacy.
3. Always ensuring that the programs you write are ethical: When developing software or coding, it is important to consider the potential impact of your creations.
Ethical programming involves avoiding harmful or malicious intent, ensuring user safety, respecting user privacy, and adhering to legal and ethical standards.
4. Never interfering with other people's work: It is essential to respect the intellectual property and work of others. Plagiarism, unauthorized use, or copying of someone else's work without proper attribution or permission is unethical and undermines the original creator's rights and efforts.
In summary, the ethical and appropriate use of a computer involves verifying information accuracy, respecting privacy and property rights, developing ethical programs, and avoiding interference with other people's work.
These principles promote a responsible and respectful digital environment that benefits all users.
For more such questions on ethical,click on
https://brainly.com/question/30018288
#SPJ8
The probable question may be:
The ethical and appropriate use of a computer includes_____.
Select 4 options.
-always ensuring that the information you use is correct
-never interfering with other people's devices
-always ensuring that the programs you write are ethical
-never interfering with other people's work
What is an online payment gateway?
Answers
Answer:
it is the key component of the electronic payment processing system, or through which type of payment you are giving through.
Explanation:
brainiliest
What number does this binary code represent?
(don’t mind the 36)

Answers
By using your own data, search engines and other sites try to make your web experience more personalized. However, by doing this, certain information is being hidden from you. Which of the following terms is used to describe the virtual environment a person ends up in when sites choose to show them only certain, customized information?
A filter bubble
A clustered circle
A relational table
An indexed environment
Answers
Answer:
A filter bubble
Explanation:
Assume a large shared LLC that is tiled and distributed on the chip. Assume that the OS page size is 16KB. The entire LLC has a size of 32 MB, uses 64-byte blocks, and is 32-way set-associative. What is the maximum number of tiles such that the OS has full flexibility in placing a page in a tile of its choosing?
Answers
Answer:
19 - 22 bits ( maximum number of tiles )
Explanation:
from the given data :
There is 60 k sets ( 6 blocks offset bits , 16 index bits and 18 tag bits )Address has 13-bit page offset and 27 page number bits14-22 bits are used for page number and index bitstherefore any tour of these bits can be used to designate/assign tile number
so the maximum number of tiles such that the OS has full flexibility in placing a page in a tile of its choosing can be between 19 -22 bits
Select the correct answer.
Linda wants to apply for a job in a company of her choice. Which information would her potential employers likely review in her social profile?
O A. comments about her past job and work performance
O B. hobbies that she enjoys on weekends
• C. details about her planned vacations
© D. friends and contacts from her friends list
E.photographs uploaded by her
Answers
A. Comments about her past job and work performance.
Match the different aspects of the marketing information systems to the scenarios that portray them.
1. Marketing intelligence system
2. Internal reporting system
3. Marketing model
4. Marketing research system
A. includes number of orders received, stock holdings, and sales invoices
B. MIS collects, regulates, and analyzes data for marketing plan
C. gathers information such as demographic data
D. includes time series, sales model, and linear programming
Answers
Answer:
1. Marketing intelligence system - C
2. Internal reporting system - A
3. Marketing model - D
4. Marketing research system - B
Explanation:
Design a class named StockTransaction that holds a stock symbol (typically one to four characters), stock name, number of shares bought or sold, and price per share. Include methods to set and get the values for each data field. Create the class diagram and write the pseudocode that defines the class.
Design a class named FeeBearingStockTransaction that descends from StockTransaction and includes fields that hold the commission rate charged for the transaction and the dollar amount of the fee. The FeeBearingStockTransaction class contains a method that sets the commission rate and computes the fee by multiplying the rate by transaction price, which is the number of shares times the price per share. The class also contains get methods for each field.
Create the appropriate class diagram for the FeeBearingStockTransaction class and write the pseudocode that defines the class and the methods.
Design an application that instantiates a FeeBearingStockTransaction object and demonstrates the functionality for all its methods.
Answers
The class diagram and pseudocode for the StockTransaction class is given below
What is the class?plaintext
Class: StockTransaction
-----------------------
- symbol: string
- name: string
- shares: int
- pricePerShare: float
+ setSymbol(symbol: string)
+ getSymbol(): string
+ setName(name: string)
+ getName(): string
+ setShares(shares: int)
+ getShares(): int
+ setPricePerShare(price: float)
+ getPricePerShare(): float
Pseudocode for the StockTransaction class:
plaintext
Class StockTransaction
Private symbol as String
Private name as String
Private shares as Integer
Private pricePerShare as Float
Method setSymbol(symbol: String)
Set this.symbol to symbol
Method getSymbol(): String
Return this.symbol
Method setName(name: String)
Set this.name to name
Method getName(): String
Return this.name
Method setShares(shares: Integer)
Set this.shares to shares
Method getShares(): Integer
Return this.shares
Method setPricePerShare(price: Float)
Set this.pricePerShare to price
Method getPricePerShare(): Float
Return this.pricePerShare
End Class
Read more about StockTransaction here:
https://brainly.com/question/33049560
#SPJ1
Write a function longer_string() with two string input parameters that returns the string that has more characters in it. If the strings are the same size, return the string that occurs later according to the dictionary order. Use the function in a program that takes two string inputs, and outputs the string that is longer.
Answers
Answer:
Here you go :)
Explanation:
Change this to your liking:
def longer_string(s1, s2):
if len(s1) > len(s2):
return s1
elif len(s1) < len(s2):
return s2
else:
return s2
x = input("Enter string 1: ")
y = input("Enter string 2: ")
print(longer_string(x, y))
Your laptop was recently upgraded to Windows 10 but is now running more slowly due to the increased memory requirements. You have decided to install some additional RAM to speed up the laptop. Which of the following should you install?
Answers
Answer:
To increase the speed of your laptop, you should consider installing additional Random Access Memory (RAM). RAM is a type of computer memory that is used to store data that is being actively used or accessed by the system. The more RAM a computer has, the more data it can store in memory and the faster it can access and use that data.
When choosing additional RAM for your laptop, there are a few things you should consider:
Compatibility: Make sure the RAM you choose is compatible with your laptop's hardware and operating system. You can check the specifications of your laptop to determine the type of RAM it supports (e.g. DDR4, DDR3, etc.) and the maximum amount of RAM it can handle.
Capacity: Consider how much additional RAM you need to improve the performance of your laptop. If you are using resource-intensive applications or running multiple programs at once, you may want to install more RAM to help your laptop handle the load.
Speed: Look for RAM with a higher speed rating, as this can help improve the performance of your laptop. However, keep in mind that faster RAM may also be more expensive.
In summary, to speed up your laptop, you should install additional RAM that is compatible with your laptop's hardware and operating system, has sufficient capacity to meet your needs, and has a high speed rating.
Explanation:
Learning Task 3: Write the safety requirement indicated in each number on a
separate sheet of paper
Answers
Answer:
Please find the complete question in the attached file.
Explanation:
Recall that its SIS consists of one or even more Safety - management Functions (SIFs), which can include a mixture of the device(s), logic when and), and a complete component (elements), along with all user interface as well as power sources, such that two sets of criteria are delineated for each SIF by SRS: the System Requirement Set as well as the Integrate Requisites Set.

CHALLENGE ACTIVITY 2.1.2: Assigning a sum. Write a statement that assigns total_coins with the sum of nickel_count and dime_count. Sample output for 100 nickels and 200 dimes is: 300
Answers
Answer:
Assuming python language:
total_coins = nickel_count + dime_count
Explanation:
The values of nickel_count and dime_count are added together and stored into total_coins.
Cheers.
Following are the code to the given question:
Program Explanation:
Defining a variable "nickel_count, dime_count" that initializes the value that is "100, 200" within it.In the next step, the "total_coins" variable is declared that initializes with 0.After initializing into the "total_coins" we add the above variable value and print its value.Program:
nickel_count = 100#defining a variable nickel_count that holds an integer value
dime_count = 200#defining a variable dime_count that holds an integer value
total_coins = 0#defining a variable total_coins that initilize the value with 0
total_coins = nickel_count + dime_count#using total_coins that adds nickel and dime value
print(total_coins)#print total_coins value
Output:
Please find the attached file.
Learn more:
brainly.com/question/17027551

1. Design a DC power supply for the Fan which have a rating of 12V/1A
Answers
To design a DC power supply for a fan with a rating of 12V/1A, you would need to follow these steps:
1. Determine the power requirements: The fan has a rating of 12V/1A, which means it requires a voltage of 12V and a current of 1A to operate.
2. Choose a transformer: Start by selecting a transformer that can provide the desired output voltage of 12V. Look for a transformer with a suitable secondary voltage rating of 12V.
3. Select a rectifier: To convert the AC voltage from the transformer to DC voltage, you need a rectifier. A commonly used rectifier is a bridge rectifier, which converts AC to pulsating DC.
4. Add a smoothing capacitor: Connect a smoothing capacitor across the output of the rectifier to reduce the ripple voltage and obtain a more stable DC output.
5. Regulate the voltage: If necessary, add a voltage regulator to ensure a constant output voltage of 12V. A popular choice is a linear voltage regulator such as the LM7812, which regulates the voltage to a fixed 12V.
6. Include current limiting: To prevent excessive current draw and protect the fan, you can add a current-limiting circuit using a resistor or a current-limiting IC.
7. Assemble the circuit: Connect the transformer, rectifier, smoothing capacitor, voltage regulator, and current-limiting circuitry according to the chosen design.
8. Test and troubleshoot: Once the circuit is assembled, test it with appropriate load conditions to ensure it provides a stable 12V output at 1A. Troubleshoot any issues that may arise during testing.
Note: It is essential to consider safety precautions when designing and building a power supply. Ensure proper insulation, grounding, and protection against short circuits or overloads.
For more such answers on design
https://brainly.com/question/29989001
#SPJ8
How would you show an external document in a running presentation?
Answers
There are a few steps that show an external document in a running presentation.
What are the steps needed?
1. On the slide, select the icon or link to the object that you want to set to run.
2. On the Insert tab, in the Links group, click Action.
3. In the Action Settings dialog box, do one of the following:
4. To click the embedded icon or link in order to open the program, click the Mouse Click tab.
5. To move the mouse pointer over the embedded icon or link in order to open the program, click the Mouse Over tab.
6. Under Action on click or Action on mouse-over, select one of the options, then select from the list at that option. For example, you can select Run Program and then browse to a program that you want to run, such as a web browser. Or if the object is a document, you can select Object action and then select Open to display the document or edit to work on it during your presentation.
To know more about External document, Check out:
https://brainly.com/question/13947276
#SPJ1
.
Which core business etiquette is missing in Jane
Answers
Answer:
As the question does not provide any context about who Jane is and what she has done, I cannot provide a specific answer about which core business etiquette is missing in Jane. However, in general, some of the key core business etiquettes that are important to follow in a professional setting include:
Punctuality: Arriving on time for meetings and appointments is a sign of respect for others and their time.
Professionalism: Maintaining a professional demeanor, dressing appropriately, and using appropriate language and tone of voice are important in projecting a positive image and establishing credibility.
Communication: Effective communication skills such as active listening, clear speaking, and appropriate use of technology are essential for building relationships and achieving business goals.
Respect: Treating others with respect, including acknowledging their opinions and perspectives, is key to building positive relationships and fostering a positive work environment.
Business etiquette: Familiarity with and adherence to appropriate business etiquette, such as proper introductions, handshakes, and business card exchanges, can help establish a positive first impression and build relationships.
It is important to note that specific business etiquettes may vary depending on the cultural and social norms of the particular workplace or industry.
Data Privacy may not be applicable in which of the following scenarios?
Answers
Answer:
A platform being hosted in a country with no DP laws but targeted at data subjects from a country with stringent laws.
Explanation:
No Data Privacy laws mean that there is a high likelihood of data being leaked to various third parties and unwanted websites.
Countries with stringent laws like China have a government that wants full control over the data of their people and the transaction of data from each of them in order to better monitor them.
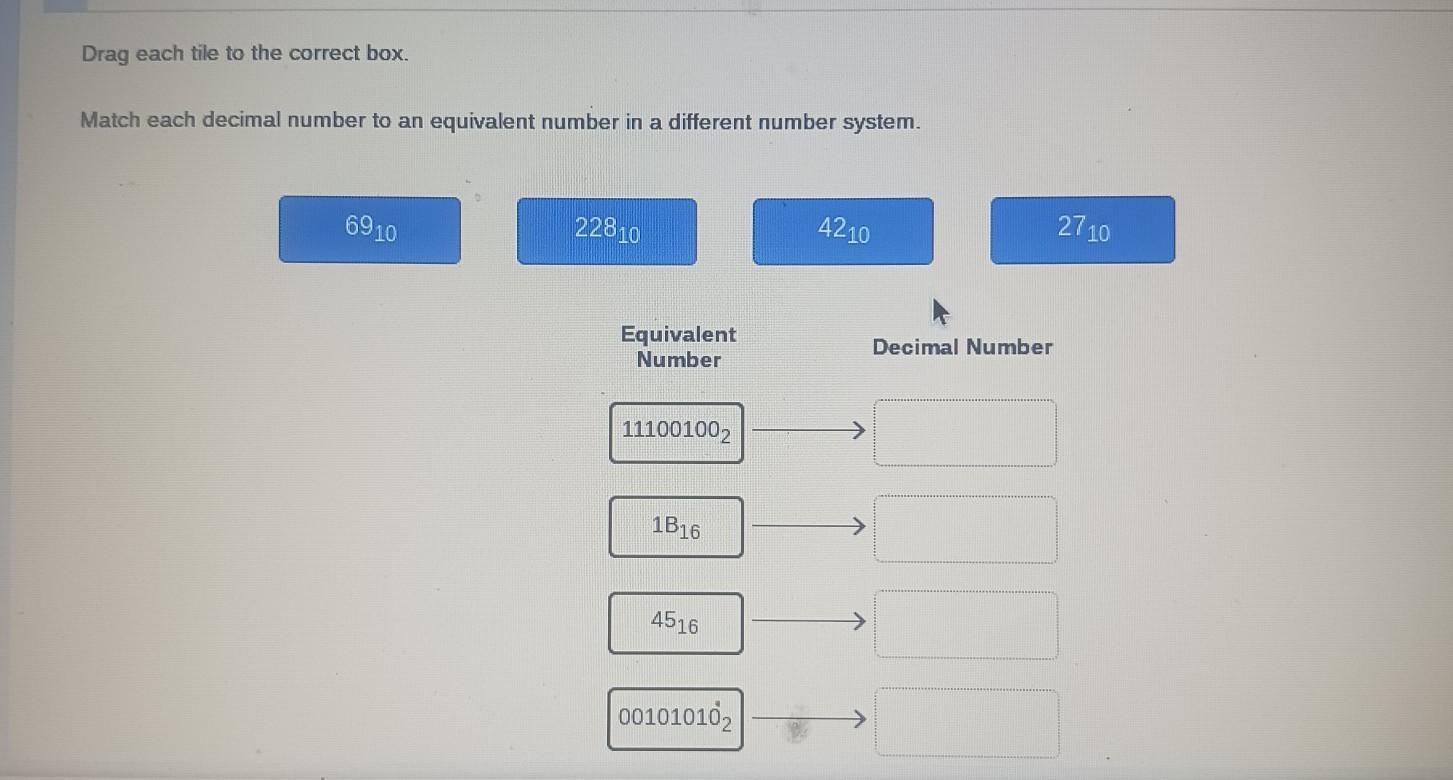
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
Answers
Explanation:
you can do that with calculator only

Consider the code block below. What is the value of amount when this method is called twice, the first time using cookieJar(7) and then using cookieJar(22)?
public static int cookieJar(int addCookies) {
int amount = 0;
amount += addCookies;
return amount;
}
A. 7
B. 15
C. 22
D. 29
E. An error occurs

Answers
Answer:
C. 22
Explanation:
Given that the argument is being passed by value, there is no memory to consider. So cookieJar(7) returns 7 and cookieJar(22) returns 22.
If the argument parameter was passed by reference or pointer, then perhaps the value from cookieJar(7) would be considered with cookieJar(22).
Note, this code block really isn't doing anything other than returning the value passed into it. The "amount" variable is immediately set to 0, and then the value passed in is added to amount (which is 0), and returns. The following code could replace this function:
public static int cookieJar(int addCookies){
return addCookies;
}
The above code will return an equivalent output to the given code.
Notice, the function is not dependent on any previous call, so the value for each is unique to the call itself, i.e., cookieJar(22) returns 22 and cookieJar(7) returns 7.
So, C. 22 would be correct.
The keyboard is used to select pictures on the computer.
#True# or False#
Answers
We use the keyboard to type. it's false.
Answer:
False is the answer of your question
hope it is helpful to you
class Login: def __init__(self): self.login_name = 'none' self.login_password = 'none' # TODO: Define class method - check_credentials(self, user_login, user_passwd) if __name__ == "__main__": login = Login() timeout = 5 #variable used for login attempts login = input() password = input() # TODO: Create boolean variable that receives return value from # calling check_credentials(login, password) # TODO: Create a loop that will continue until login attempts run out or a successful login is returned # TODO: Create a loop that only allows 5 failed login attempts
Answers
Create boolean variable that receives return value from # calling check_credentials(login, password) # TODO a loop that will continue until login attempts run out or a successful login is returned # TODO #elegance Login elegance Login: #_init def _init_(self) #initializing login_name as none self.login_name = 'none'.
What is a code in programming?In laptop programming, laptop code refers back to the set of instructions, or a device of rules, written in a specific programming language (i.e., the supply code). It is likewise the time period used for the supply code after it's been processed via way of means of a compiler and made equipped to run at the laptop (i.e., the item code).
CODE#elegance Loginelegance Login: #_init_ def _init_(self): #initializing login_name as none self.login_name = 'none' #initializing login_password as none self.login_password = 'none' #check_credentials() def check_credentials(self, user_login, user_passwd): #initializing simlogin as 'Test' simlogin = 'Test' #initializing simpass as 'Test' simpass = 'test1234' #if consumer despatched an appropriate credentials if user_login == simlogin and user_passwd == simpass: #print "Successful login!" print("Successful login!") #returns False go back False #returns False go back False #timeout variable used for login attempts timeout = five #spark off for password password = input() #if now no longer legitimate login else: #decrements timeout timeout = timeout - 1 #if timeout equals 0 if timeout == 0: #prints "five failed login attempts. No extra login attempts." print("five failed login attempts. No extra login attempts.") #exits the loop break #spark off for consumer call login = input()Read more about the code:
https://brainly.com/question/4514135
#SPJ1
What is the output?
answer = 0
for numA in [2,4]:
for numB in [3, 5]:
answer = answer + numA + numB
print (answer)
Output:
Answers
Answer:
The output is 28
Explanation:
Required
Determine the output of the code segment
The first line initializes "answer" to 0
The next two lines iterate through lists [2,4] and [3,5
Each of these lists have two elements; So, the number of iterations is 2 * 2 i.e. 4.
In the first iteration
numA = 2, numB = 3, answer = 0
So:
\(answer = answer + numA + numB= 0 + 2 + 3 = 5\)
In the second iteration
numA = 2, numB = 5, answer = 5
So:
\(answer = answer + numA + numB= 5 + 2 + 5 = 12\)
In the third iteration
numA = 4, numB = 3, answer = 12
So:
\(answer = answer + numA + numB= 12 + 4 + 3 = 19\)
In the fourth iteration
numA = 4, numB = 5, answer = 19
So:
\(answer = answer + numA + numB= 19 + 4 + 5 = 28\)
Lastly, the value of "answer" is printed
Hence, the output is 28
Answer: 28
Explanation: got it right on edgen
What is the impact of prior probability on the final outcome? You want to use conditional
probability to determine presidential candidate. Write a detail algorithm with example. Make necessary assumptions about procedure and data. What part of it is bio-inspired? How can you use reinforcement learning in this case? Define value function, rewards and penalties. Give detailed algorithm.
Answers
The prior probability plays a crucial role in determining the final outcome when using conditional probability. It represents our initial belief or expectation about an event before we have observed any specific evidence.
In the context of determining a presidential candidate using conditional probability, the prior probability would reflect our initial belief about the likelihood of each candidate winning, based on factors such as their popularity, track record, and campaign strategies.
To illustrate the algorithm, let's assume we have four presidential candidates: Candidate A, Candidate B, Candidate C, and Candidate D. We want to determine the probability of each candidate winning based on conditional probability, considering different factors such as public opinion polls, campaign spending, and endorsements.
Learn more about probability on:
https://brainly.com/question/31828911
#SPJ1
Formal Writing Assignment: CUNY WAN Modernization Project Spring 2023
The CUNY University System has begun developing programs for enterprising professionals and advanced degree students that want to complete their studies remotely. This emerging need originated when the CUNY University System was operating fully remote due to the Corona virus. There is significant interest in continuing to provide this remote mode of instruction and expand it to new outreach programs within the New York City region. The CUNY University System has hired you to provide help with their modernized WAN that will be needed for developing these new programs.
Providing WAN Services to Remote locations
CUNY University System plans to offer night and weekend classes for professionals and advanced degree students, paralegal students, and nurses, in five “Centers of Excellence” remote locations at each borough of the City of New York.. Its plan is to have professors offer the classes from the main campus site and to use video conferencing and multimedia options at these “Centers of Excellence” remote sites. The CUNY University System main site has a TCP/IP Ethernet network. The remote “Centers of Excellence” sites, which are not yet set up, will also have TCP/IP Ethernet networks.
The CUNY University System Director of Information Technology is asking you to write a proposal for three WAN options (possible candidates are: Frame Relay, Broad Band and MPLS) to connect the “Centers of Excellence” remote sites to the main campus and provide a rationale for each of these options. Your WAN options must provide for the use of voice over IP, video conferencing and multimedia applications. Each WAN option should provide details on the following factors:
How does the technology work?
Bandwidth costs
Bandwidth allocation (how much bandwidth is available/supported) by the method.
Equipment costs associated with the method.
Ability for the method to address future expanded bandwidth requirements.
Ability for the method to incorporate other applications such as voice and video.
Ability for the method to offers fault tolerant options to provide more guaranteed uptime—an important consideration for providing long-distance learning.
Teaching Classes from Home
The CUNY University System president enjoys participating in several classes once a week as a guest speaker or mentor, but she wants to do this from home, so she can spend more time with her family instead of driving back to the main CUNY University System campus, which is about ten miles away.
Write a 1–2-page letter to the CUNY University System president explaining how she might be connected to the main CUNY University System campus network through a particular WAN technology, and why you recommend that WAN technology. One of the requirements is that she needs to be able to use the telephone in her home office while she is connected to the CUNY network.
WAN Connectivity for a Business Incubator
The CUNY University System is starting a business incubator on the main campus. The business incubator provides one year of resources for up to five new small businesses, including a business location and office resources, such as computers, printers, scanners and Internet access. Write a 1–2-page letter to the CUNY University System president explaining to her the WAN connectivity options that are most appropriate for these small businesses, so that it is consistent with what they can use when they leave the incubator facilities.
Answers
In order to carry out this assignment, you want to make sure that you research and thouroughly understand the Wide Area Network (WAN) techologies of Frame Relay, Broad Bank, and MPLS.
What else needs to be done?You must present a proposal for each WAN alternative, describing the bandwidth prices, allocation, equipment costs, capacity to handle future bandwidth requirements, include audio and video, and offer fault-tolerant choices.
You would need to submit a letter outlining the proposed WAN technology to link her to the campus network while enabling her to use her phone in response to the CUNY University System president's request to participate in classes from home.
You would also need to produce another letter for the business incubator describing the best WAN connectivity alternatives for small enterprises to use once they depart the incubator facility. Thus,, the project necessitates good research abilities as well as the ability to communicate material clearly and concisely.
Learn more about WAN:
https://brainly.com/question/621746
#SPJ1
Conditionals often run on {} instructions.
A
if / else
B
if / then
C
unless / until
D
up to / at least
Answers
Answer: A
Explanation: This is a if/else Statement
In any programming language, the code has to make decisions and carry out actions depending on different inputs.
Select the answers that best describe showing respect for confidential data. Check all of the boxes that
apply.
A security administrator works for a leading aviation company that supplies military aircraft parts to the
government. Confidentiality is of utmost importance.
The security administrator takes the train to and from work. He often handles sensitive work issues
on his smartphone while commuting.
The security administrator makes sure to shred and properly dispose of any printed confidential
information.
The security administrator talks about his current classified projects with a friend at a restaurant.
The security administrator uses password-protected files and folders on his work computer.
Answers
Answer:
“The security administrator make sure to shred and properly dispose of any printed confidential information” and “The security administrator uses password-protected files and folders on his work computer”
Explanation:
Following are the correct options that gives the best description in the context of showing respect for confidential data:
The security administrator makes sure to shred and properly dispose of any printed confidential information.
The security administrator uses password-protected files and folders on his work computer.
Hence, Options C and E are correct.
What is confidential data?There are basically two types of data: one is available for everyone so that they can access all the data information, whatever they want to get in and edit it.
On the other hand, there is a kind of data that is available only to a few or an individual person, and when it is about to edit data, most of the time that data is not available to edit. The protection that has been provided to conference tension data is the sponge please of the security administrator.
Therefore, Options C and E are correct.
Learn more about confidential data from here:
https://brainly.com/question/28320936
#SPJ2