Aniyah is setting up a group of computers in her office that will share several devices. Which type of operating system should she use?
A. Client OS
B. Network OS
C. Server OS
D. Embedded OS
Answers
Answer:
B
Explanation:
the software needs to share thus should be networked
Related Questions
I need help please !!!!

Answers
Answer:
Second one
Explanation:
evaluation of ur problems
5.if a customer intends to transmit more data than they receive, which forms of dsl would be appropriate?
Answers
If a customer intends to transmit more data than they receive, the appropriate form of DSL would be Asymmetric Digital Subscriber Line (ADSL).
ADSL provides higher upload speeds compared to download speeds, making it suitable for users who need to send more data than they receive. To use ADSL, the customer would need an ADSL modem and a subscription from a DSL service provider.
#SPJ11
Learn more about DSL: https://brainly.com/question/12859851
If a customer intends to transmit more data than they receive, Asymmetric Digital Subscriber Line (ADSL) and Symmetric Digital Subscriber Line (SDSL) are the two DSL types that would be appropriate.
The following are some distinctions between the two:ADSL (Asymmetric Digital Subscriber Line): ADSL allows for a faster download speed than upload speed, making it suitable for customers who prefer to download more content than upload. ADSL is an acronym for Asymmetric Digital Subscriber Line. The speed is determined by the type of ADSL service you have subscribed to; for instance, ADSL2+ has a speed limit of 24 Mbit/s downstream and 1 Mbit/s upstream.SDSL (Symmetric Digital Subscriber Line): SDSL is a type of DSL that provides equal upload and download speeds, making it appropriate for customers who require a balanced amount of download and upload speed. SDSL is an acronym for Symmetric Digital Subscriber Line. The speed is the same for uploading and downloading, with a range of 128 Kbps to 3 Mbps.Learn more about data: https://brainly.com/question/179886
#SPJ11
Which of the following IS NOT a way that functions make code more readable?
A. O Function names can describe what the function is completing
B.
Functions break code into smaller, separate parts
C.
Each function contains one command
D.
Functions shorten code by reusing code that has already been written
Answers
Answer:
C
Explanation:
Functions can contain any number of commands.
low frequency radio wave travel in straight line and high frequency radio wave can travel in all direction true or false
Answers
Answer:
The correct answer is True.
Explanation:
The electromagnetic spectrum consists of various waves. The Radio waves are categorized to be at the low-frequency end of this spectrum.
Radio Waves have multiple communication uses. Some of them are television and radio broadcasting, communications, and satellite transmissions.
Radio waves are not harmful to biotic life when absorbed by living matter and their transmission is unimpeded by air. Their transmission can also be absorbed, deflected, reflected, refracted, or diffracted by air molecules and the earth's surface.
Cheers
When an operator has two operands of different data types, c++ always converts them both to double before performing the operation.
a. true
b. false
Answers
When an operator has two operands of different data types, c++ always converts them both to double before performing the operation is false statement.
What is operands and example?In regards to computer programming, an operand is seen as a term that is often used to tell more any object that is often capable of being altered.
A good example, in "1 + 2" the "1" and "2" are said to be operands and the plus symbol is known to be called the operator.
In regards to mathematics, an operand is seen as the object of a any form any mathematical operation.
Therefore, When an operator has two operands of different data types, c++ always converts them both to double before performing the operation is false statement.
Learn more about operands from
https://brainly.com/question/27014457
#SPJ1
while t >= 1 for i 2:length(t) =
T_ppc (i) (T water T cork (i- = - 1)) (exp (cst_1*t)) + T cork (i-1);
T cork (i) (T_ppc (i) - T pet (i- = 1)) (exp (cst_2*t)) + T_pet (i-1);
T_pet (i) (T cork (i)
=
T_air) (exp (cst_3*t)) + T_air;
end
T final ppc = T_ppc (t);
disp (newline + "The temperature of the water at + num2str(t) + "seconds is:" + newline + T_final_ppc + " Kelvin" + newline + "or" + newline +num2str(T_final_ppc-273) + degrees Celsius" + newline newline);
ansl = input (prompt, 's');
switch ansl case 'Yes', 'yes'} Z = input (IntroText); continue case {'No', 'no'} break otherwise error ('Please type "Yes" or "No"')
end
end
Answers
The given code describes a temperature change model that predicts the final temperature of water based on various input parameters such as the temperatures of cork, pet, and air.
It appears that you are providing a code snippet written in MATLAB or a similar programming language. The code seems to involve a temperature calculation involving variables such as T_ppc, T_water, T_cork, T_pet, and T_air. The calculations involve exponential functions and iterative updates based on previous values.
The model uses a set of equations to calculate the temperature changes for each component.
The equations used in the model are as follows:
T_ppc(i) = (T_water – T_cork(i-1)) * (exp(cst_1 * t)) + T_cork(i-1)T_cork(i) = (T_ppc(i) – T_pet(i-1)) * (exp(cst_2 * t)) + T_pet(i-1)T_pet(i) = (T_cork(i) – T_air) * (exp(cst_3 * t)) + T_airThese equations are implemented within a for loop, where the input variables t, T_water, T_cork, T_pet, cst_1, cst_2, cst_3 are provided, and the output variable T_final_ppc represents the final temperature of the water after the temperature change.
Additionally, the code includes a prompt that allows the user to enter "Yes" or "No." Choosing "Yes" continues the execution of the code, while selecting "No" stops the code.
Overall, the code simulates and predicts the temperature changes of water based on the given inputs and equations, and offers the option to continue or terminate the execution based on user input.
Learn more about MATLAB: https://brainly.com/question/13715760
#SPJ11
Assume the variable temps has been assigned a list that contains floatingpoint values representing temperatures. Write code that calculates the average temperature and assign it to a variable named avg temp. Besides temps and avg_temp, you may use two other variables −k and total.
Answers
To calculate the average temperature from a list of floating-point values assigned to the variable temps, we need to create two additional variables − k and total.
The variable k will keep track of the number of temperatures in the list, while the variable total will store the sum of all the temperatures in the list.
We can use a for loop to iterate through the list of temperatures and add each value to the total variable. We will also increment the k variable by 1 for each temperature in the list.
Once we have the sum of all temperatures and the total number of temperatures, we can calculate the average temperature by dividing the total by k.
The code to calculate the average temperature and assign it to a variable named avg_temp is as follows:
```
temps = [25.5, 28.0, 26.8, 30.2, 27.6]
total = 0
k = 0
for temp in temps:
total += temp
k += 1
avg_temp = total / k
print("The average temperature is:", avg_temp)
```
In this example, we have assigned a list of five temperatures to the variable temps. The for loop iterates through the list of temperatures and adds each value to the total variable while incrementing the k variable. Finally, the average temperature is calculated by dividing the total by k and assigned to the variable avg_temp.
The output will be:
```
The average temperature is: 27.82
```
Therefore, the average temperature of the given list of temperatures is 27.82.
To know more about average temperature visit:
https://brainly.com/question/21853806
#SPJ11
which packet type is user-generated and forwarded by a router?
Answers
The packet type that is user-generated and forwarded by a router is an IP (Internet Protocol) packet.
IP packets are the fundamental units of data transmission in computer networks, and they carry information from the source to the destination across different networks.
When a user initiates a communication request, such as sending an email, browsing a website, or streaming a video, their computer or device generates an IP packet encapsulating the data to be transmitted. This user-generated IP packet contains the source and destination IP addresses, as well as the payload, which is the actual data being transmitted.
The payload could include application-layer data, such as the contents of an email or a web page.
Once the user-generated IP packet is created, it is handed over to the network layer of the operating system, where the router comes into play. The router receives the IP packet from the user's device and examines the destination IP address.
Based on its routing table and routing algorithms, the router determines the appropriate next hop or interface to forward the packet towards its destination.
The router then encapsulates the user-generated IP packet into a new data link layer frame, such as an Ethernet frame, with source and destination MAC (Media Access Control) addresses. This frame is then transmitted over the network to the next router or network device along the path to the destination.
In summary, user-generated IP packets are forwarded by routers as they traverse the network from the source device to the destination device. The router's role is to examine the destination IP address and make decisions on how to efficiently route the packet towards its destination.
Learn more about router:
https://brainly.com/question/24812743
#SPJ11
For me it’s 1-4 2-3 3-2 4-1 hope this helps
Answers
Answer: Thx
Explanation:
A teacher has a proprietary software on their computer that they would like all their students to have access to. What type of license would they need to make sure they have before this is legal?(1 point)
freeware
site
proprietary
single-user
Answers
Answer:
freeware
Explanation:
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The following statement would provide the information by utilising data-collection technology: Buying a new shirt on an e-commerce site.
What is data collection?
The process of obtaining and analysing data on certain variables in an established system is known as data collection or data gathering. This procedure allows one to analyse outcomes and provide answers to pertinent queries. In all academic disciplines, including the physical and social sciences, the humanities, and business, data collecting is a necessary component of research. Although techniques differ depending on the profession, the importance of ensuring accurate and truthful collection does not change. All data gathering efforts should aim to gather high-caliber information that will enable analysis to result in the creation of arguments that are believable and convincing in response to the issues that have been addressed. When conducting a census, data collection and validation takes four processes, while sampling requires seven steps.
To learn more about data collection
https://brainly.com/question/25836560
#SPJ13
Give an E-R diagram for database showing fatherhood, motherhood and spouse relationship among men and women.
Answers
An Entry Relationship (ER) data model is a type of data model that is used to represent the relationships between entities in a database.
What is database?A database is a collection of organized data, stored and accessed electronically. Databases provide a structure for storing and organizing data that is easily accessed, managed and updated.
It is a type of logical data model that is used to illustrate the logical relationships between entities in a database. An ER diagram is a graphical representation of an ER data model.
Below is an ER diagram for a database showing fatherhood, motherhood and spouse relationship among men and women:
Fatherhood Relationship:
Father -----------------------------> Son/Daughter
Motherhood Relationship:
Mother -----------------------------> Son/Daughter
Spouse Relationship:
Husband ---------------------------> Wife
Wife ---------------------------> Husband
To learn more about database
https://brainly.com/question/29804491
#SPJ1
Complete Question:
what is entry relationship data model ?give an ER diagram for a database showing fatherhood,motherhood and spouse relationship among men and womean.
ADVENTURE BOOKS 123
time 4 a story and questions
(this is just a made up story........)
One groggy day The President shows up on the news and he starts arguing with the news woman and he tells her he wants to be the one who informs everyone and guess what? thats what happened.so he walks up to the camera and spills the beans this is what he said Fellow humans i figured you would like to hear this news ........
26harrisona avatar
we are going to have to go into lockdown so if you would like to leave the state you may,.................
ADVENTURE BOOKS 123
time 4 a story and questions
(this is just a made up story........)
One groggy day The President shows up on the news and he starts arguing with the news woman and he tells her he wants to be the one who informs everyone and guess what? thats what happened.so he walks up to the camera and spills the beans this is what he said Fellow humans i figured you would like to hear this news ........we are going to have to go into lockdown so if you would like to leave the state you may,.................cov-id is going to become the ap-ocal-yp-se ......(you)so you have decided to go to an island that is called ----------- (made up name.....)cov-id is going to become the ap-ocal-yp-se ......(you)so you have decided to go to an island that is called ----------- (made up name.....)so you gather your supplies you can chose (20) things only 20 you have to name everything before you leave the state .
Answers
Please! I need help matching this.
Answers
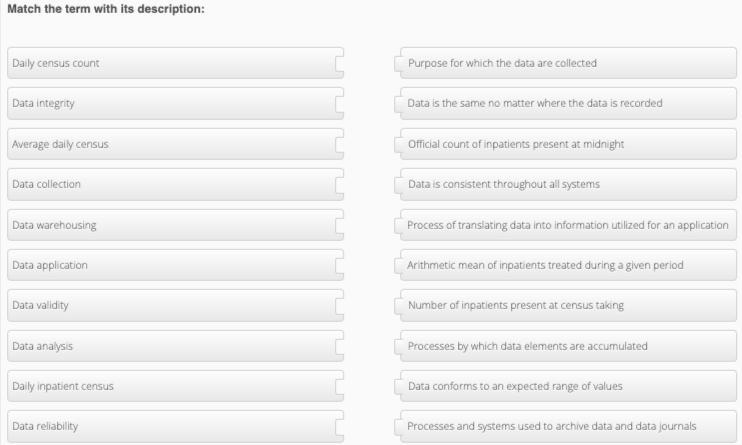
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
The interns at Amazon were assigned a task to analyze the stock prices of Amazon over a period of n months.
For each month m, the analysis determines the most profitable month with respect to the month m (denoted by most profitable_month[m]) as the earliest month after m such that the stock prices of all months beyond that month are greater than the minimum value of stock price in the first m months. More formally, considering 0-based indexing, most profitable_month[m] (let's denote it by x), is the smallest month satisfying m
Given the stock prices of n months denoted by stockPrice, find the most profitable month with respect to each month considering 0- based indexing. If such a month does not exist for a given month, return -1 for that month.
Example
There are n = 5 months of data, and the stock prices are stockPrice - [4, 2, 5, 8, 6].
The most profitable months are calculated as follows:
• Month 0: We can observe that most profitable_month[0]-2, because min(stockPrice[0])-4 which is less than stockPricelk] for all 2sk<5 but the condition is not satisfied for an earlier month.
5>4
5
8>4
8
6>4
2
min(4)-4
⚫ Month 1: We can observe that most profitable_month[1]=2, because min(stockPrice[0], stockPrice[1])=2which is less than stockPrice[k] for all 2 sk<5 but the condition is not satisfied for an earlier month.
4
2
5>2
5
8>2
6>2
min(4, 2) 2
⚫ Month 2: We can observe that most profitable month[2]-3, because
Answers
The task is to analyze stock prices over a period of n months and find the most profitable month for each month based on specific conditions, such as comparing stock prices and minimum values.
What is the task in the given problem and how can the most profitable month be determined for each month?The given problem involves analyzing stock prices over a period of n months to determine the most profitable month for each month.
The most profitable month is defined as the earliest month after the current month where all subsequent months have stock prices higher than the minimum stock price in the first m months.
The task is to find the most profitable month for each month and return -1 if such a month does not exist.
The example provided demonstrates the calculation of the most profitable months for the given stock prices.
By iterating through each month and comparing the stock prices, the most profitable month can be identified based on the defined conditions.
Learn more about task
brainly.com/question/29734723
#SPJ11
https://the term syntax refers to a. a step-by-step set of instructions b. the rules for forming legal statements c. the meaning of statements d. a type of programming language/337956292/midterm-review-flash-cards/
Answers
Syntax is the set of rules for forming legal statements in a programming language.
Syntax is the set of rules that define the structure of a programming language. It is the way we structure the code written in that language. Syntax is important because it helps to make sure the code written is valid and organized. Syntax defines the way the code should be written and the order in which certain elements should appear. For example, certain keywords or symbols must be used in a specific order in order for the code to be valid. Syntax also defines the way the code should be separated into individual parts or elements. This helps to make the code easier to read and understand. Syntax is an important part of coding and understanding how to write code in a given language.
Learn more about Language here:
brainly.com/question/28266804
#SPJ4
Which layer of the protocol stack is responsible for the physical transportation of the packets?
Group of answer choices
Answers
The layer of the protocol stack is responsible for the physical transportation of the packets is option C: The transport layer.
What is the transport layer?Through flow control, segmentation as well as desegmentation, and error management, the transport layer is said manages the dependability of a specific link. Some protocols focus on connections and states.
Therefore, The transport layer manages the entire data transmission process and is capable of managing many data streams at once. Transmission Control Protocol (TCP), the primary transport layer protocol, offers a dependable, as well as connection-oriented service.
Learn more about The transport layer from
https://brainly.com/question/27961606
#SPJ1
See full question below
Which layer of the protocol stack is responsible for the physical transportation of the packets?
Group of answer choices
A) Physical layer
B) Data link layer
C)The transport layer
D) Presentation layer
a typical computer monitor is which type of display?
Answers
Answer:
a typical computer moniter would be an LCD display
The typical computer monitor has a film-transistor liquid-crystal type display.
What is a computer?A computer is a digital electronic appliance that may be programmed to automatically perform a series of logical or mathematical operations. Programs are generic sequences of operations that can be carried out by modern computers.
Modern monitors often include TFT-LCD displays as its display technology, with LED backlighting having taken the role of cold-cathode fluorescent lamp (CCFL) illumination.
As we know, the most popular sort of monitor you can find right now, along with LED, is LCD. In order to arrange the liquid between the two glass panes that make up an LCD display, hundreds of rows of pixels are used.
Cathode-ray tube (CRT) and plasma (also known as gas-plasma) displays were utilized in earlier monitors.
Thus, a typical computer monitor has a film-transistor liquid-crystal type display.
Learn more about computers here:
brainly.com/question/21080395
#SPJ2
A car is fitted with the latest GPS navigation system. This device is controlled by an embedded system in the form of a microcontroller. (a) Describe the inputs needed by the embedded system and describe which outputs you would expect it to produce
Answers
Inputs: The GPS navigation system would provide the embedded system with location data such as latitude, longitude, and altitude. Additionally, it may also receive input from other sensors such as speed sensors, gyroscopes, and accelerometers.
Outputs: The embedded system would produce outputs such as navigation directions, estimated time of arrival, distance to destination, and speed information. It may also control other functions of the car such as automatic headlights, cruise control, and emergency braking.
The GPS navigation system relies on location data to determine the car's position and calculate the best route to the destination. This data is fed into the embedded system which processes it to provide useful information to the driver such as navigation directions and estimated time of arrival. Additionally, the embedded system may receive input from other sensors to improve the accuracy of the location data and provide additional features such as automatic headlights and emergency braking. Overall, the embedded system acts as the control center for the GPS navigation system, receiving inputs and producing outputs to enhance the driving experience.
Learn more about navigation system here:
https://brainly.com/question/31453773
#SPJ11
Queries are a very useful object in a database, please explain why.
Answers
Answer:
they tell the producer what to do to make their website better
Explanation:
Python help!
Input a grade level (Freshman, Sophomore, Junior, or Senior) and print the corresponding grade number [9-12]. If it is not one of those grade levels, print Not in High School.
Hint: Since this lesson uses else-if statements, remember to use at least one else-if statement in your answer to receive full credit
Sample Run 1
What year of high school are you in? Freshman
Sample Output 1
You are in grade: 9
Sample Run 2
What year of high school are you in?
Kindergarten
Sample Output 2
Not in High School
Answers
Answer:
print("What year of high school are you in?")
grade = input()
grade = grade.lower()
if grade == "freshman":
print("You are in grade: 9")
elif grade == "sophomore":
print("You are in grade: 10")
elif grade == "junior":
print("You are in grade: 11")
elif grade == "senior":
print("You are in grade: 12")
else:
print("Not in high school")
Explanation:
The first line prints the question. "grade = input()" stores the answer the user will type in the terminal into the variable 'grade'.
grade.lower():
The third line lowercases the entire string ("FreshMan" would turn to "freshman"). Python is case-sensitive.
Then, test the string to see if it matches freshman, sophomore, junior, or senior. If the input string matches print the statement inside the if block. The last statement is the else. It prints if nothing else matches.
The words, the computer is the future, has how many bits?
Answers
The words, the computer is the future, has 64 bits.Modern computer has
two types of processors which include:
32 bit64 bitBitsThis is referred to as the smallest unit of data which is used in a computer.
The 32 bit computer are the old types which have a smaller processor and is
relatively slow.
The 64 bit computer on the other hand are the modern types with large
processors and are relatively fast.
Read more about Computer here https://brainly.com/question/13380788
___________ is a special type of virus fills a computer system with self-replicating activity, clogging the system so that its operations are slowed or stopped.
Answers
A computer worm is a type of malicious software that can self-replicate and spread through computer networks without the need for human intervention. Once it infects a computer system, the worm can consume system resources and cause the system to slow down or crash.
One of the most famous computer worms was the Morris worm, which infected thousands of computers in 1988. The Morris worm exploited a vulnerability in the UNIX operating system and caused significant damage to computer systems worldwide.
To protect against computer worms, it's essential to keep software and operating systems up to date with the latest security patches. It's also crucial to practice safe browsing habits and avoid opening suspicious emails or downloading files from unknown sources. By staying vigilant and taking proactive steps to protect your computer systems, you can help prevent the spread of computer worms and other malicious software.
For more such question on computer worm
https://brainly.com/question/16582802
#SPJ11
what are best practices to prevent downloading of viruses and other malicious code?
Answers
Back up your files regularly are best practices to prevent downloading of viruses and other malicious code.
What does malware protection entail?
By taking advantage of information system weaknesses, malicious code insertions take place.
Examples of malicious code protection techniques include reputation-based systems and anti-virus signature definitions. The consequences of malicious code can be reduced or completely eliminated using a range of technologies and techniques.
How can malicious attacks be stopped?
If you must download something, make sure it is malware-free by using an antivirus tool before opening it. You may check the entirety of your computer for infection with antivirus software. To detect malware early and stop it from spreading, it's a good idea to do routine computer scans.
Learn more about Malicious code
brainly.com/question/29549959
#SPJ4
A program uses 4 bits to store numbers. When it adds 10 and 7, the result is 1. Which of the following best explains why?
1) the program is reporting the number of bits required to compute the sum
2) an overflow error led the program to reset to O at the number 16
3) 1" is an error code that indicates a rounding error
4) 4 bits is not enough to represent the number 10, so the computer reported only the tens value
Answers
Answer:
2
Explanation:
overflow
A data type overflow issue typically occurs when the data type used to store the data was unable to accommodate the data. In addition, some data types are limited in the size of the numbers they can hold. If a data type is a single byte and the amount of data to be saved is larger than 256, an overflow error will be generated. Thus, option B is correct.
What an overflow error led the program to reset?Using exception handling, these mistakes can be addressed. We will examine this exception handling in the section that follows.
We observed the Overflow error in the aforementioned programs, which happens when the current value exceeds the limit value. Furthermore, we must raise the overflow Error exception in order to manage this.
Therefore, When software encounters an overflow error, it means that it tried to write data outside the memory's capacity. Every program has memory set aside for a stack.
Learn more about overflow error here:
https://brainly.com/question/27493058
#SPJ2
The OSI reference model has seven distinct layers. Each layer performs functions that help applications to run on a network. Identify the layer responsible for end-to-end connection by clicking it.
Answers
The layer responsible for end-to-end connection in the OSI reference model is the Transport layer.
This layer is located between the Session layer and the Network layer and is responsible for the reliable transfer of data between two end systems.
It provides services such as segmentation and reassembly of data, flow control, and error checking to ensure that data is delivered accurately and in order.
The Transport layer establishes end-to-end connections between applications running on different systems by using port numbers to identify the applications.
It also manages the data flow to prevent congestion and ensure that data is delivered in a timely manner.
The two most common protocols used at this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP is a connection-oriented protocol that provides reliable and ordered delivery of data.
It establishes a connection between two end systems and ensures that all data is delivered in the correct order.
TCP also includes features such as flow control and error recovery to ensure that data is delivered accurately.
UDP, on the other hand, is a connectionless protocol that provides unreliable delivery of data.
It does not establish a connection between two end systems and does not include features such as flow control or error recovery.
UDP is useful for applications that require high-speed data transfer and can tolerate some data loss.
The Transport layer is responsible for end-to-end connection in the OSI reference model.
It provides services such as segmentation, reassembly, flow control, and error checking to ensure that data is delivered accurately and in order.
TCP and UDP are the two most common protocols used at this layer.
For similar questions on OSI
https://brainly.com/question/31023625
#SPJ11
Click this link to view O*NET’s Work Context section for Glass Blowers, Molders, Benders, and Finishers. Note that common contexts are listed toward the top, and less common contexts are listed toward the bottom. According to O*NET, what are common work contexts for Glass Blowers, Molders, Benders, and Finishers? Check all that apply.
face-to-face discussions
importance of being exact or accurate
wear common protective or safety equipment
in an open vehicle or equipment
spend time keeping or regaining balance
very hot or cold temperatures

Answers
Therefore, the correct options to check are:
Importance of Being Exact or Accurate Wear Common Protective or Safety Equipment Face-to-Face DiscussionsWhat is the O*NET’s Work Context?O*NET is a database that provides information on different occupations, including their work context. Work context refers to the physical, social, and environmental conditions under which a job is performed.
According to the Work Context section for Glass Blowers, Molders, Benders, and Finishers on O*NET, the most common work contexts for this occupation are Importance of Being Exact or Accurate, Wear Common Protective or Safety Equipment, and Face-to-Face Discussions.
Based on O*NET's Work Context section for Glass Blowers, Molders, Benders, and Finishers, the common work contexts for this occupation are:
Importance of Being Exact or Accurate Wear Common Protective or Safety Equipment Face-to-Face DiscussionsRead more about O*NET’s Work Context here:
https://brainly.com/question/30736336
#SPJ1
Answer: A,B,C,F
Explanation: on edge
What is empowerment technology?
Answers
Create and run a query that displays all employees from the employee table who have the title Senior Sales Associate. This requires that you join related tables and select columns from all them but display only some of the columns. In the dynaset display each qualifying employee's last name, gender, and city, and state where they work (arrancge columns left to right in this way). Sort the dynaset in ascending order by state and then by last name within each state group. Assign aliases to the column as follows: Name, Gender, Work City, and Work State. Optimize the dynaset column widths. Print the resulting dynaset and write your name on the output.
Answers
Sure, I can help you create a query for this. However, to create an accurate SQL query, I need to know the exact table structures. In particular, I need to know:
1. The name of the employee table, and its column names.
2. The name of the related tables, and their column names.
3. The relationship between these tables (foreign keys).
4. Which tables contain the 'title', 'last name', 'gender', 'city', and 'state' data.
For the purpose of this answer, let's assume we have two tables: `employees` and `locations`.
The `employees` table has the following columns: `emp_id`, `first_name`, `last_name`, `gender`, `title`, and `location_id`.
The `locations` table has the following columns: `loc_id`, `city`, and `state`.
Here's an example of how your query might look:
```sql
SELECT
e.last_name AS 'Name',
e.gender AS 'Gender',
l.city AS 'Work City',
l.state AS 'Work State'
FROM
employees e
JOIN
locations l ON e.location_id = l.loc_id
WHERE
e.title = 'Senior Sales Associate'
ORDER BY
l.state ASC,
e.last_name ASC;
```
This query first selects the desired columns from the `employees` and `locations` tables, assigning them the requested aliases. It then joins the two tables on their shared `location_id`/`loc_id` column. The `WHERE` clause filters the results to only include rows where the title is 'Senior Sales Associate'. Finally, the `ORDER BY` clause sorts the results first by state in ascending order, and then by last name in ascending order within each state group.
As for optimizing the column widths, printing the resulting dynaset, and writing your name on the output, these are tasks typically handled by the application or tool you're using to run the SQL query, rather than within the SQL query itself. You'd need to check the documentation or help resources for that tool to see how to do this.
If your table structure is different, please provide the correct structure and I will adjust the query accordingly.
explain the types of computer on the basis of model
Answers
XT(extra technology) computer: it cannot support GUI Based operating system. its processing speed is 477MHz
AT(advanced technology):it supports GUI Operating system. Its processing speed is 2GHz
PS/2:is a laptop computer which is rechargeable
and battery powered. it's operated with OS/2 operating system.
PLEASE MARK AS BRAINLIEST
Answer:
XT Computers (Extended Technology)
AT Computers (Advanced Technology)
PS/2 Computers (Personal System 2)
Explanation:
XT Computers :
The computers having 8086 or 8088 microprocessor and processing speed of 4.77 Mhz are known as XT Computers. These computers are outdated now because they cannot run on latest software versions.
AT Computers :
The computers having 80286 or later versions of microprocessors are known as AT Computers. Their storage capacity as well as speed is much higher than XT computers. Besides that they have math co-processor to support main processors to perform complex mathematical calculations.
PS/2 Computers:
IBM developed another model of computer in 1990 that have much advanced architecture design that AT computers. They are known as PS/2 computers. They are much faster than AT computers. Most of the laptop computers based on PS/2 model use OS/2 or UNIX operating system and 1.44 MB floppy diskette.