A LAN Uses category 6 cabling. An issue with the connection results in network link to get degeneration and Only one device can communicate at a time. What is the connection operating at?
Half duplex
Simplex
Partial
Full Duplex
Answers
Answer:
partial
Explanation:
Related Questions
Which action refers to the unauthorized and illegal duplication or sale of software?
Answers
What formatting changes do spreadsheet applications permit in the rows and columns of a spreadsheet?
Answers
Answer: There are manny ways, best is to extract a document from excel sheets and change the spreadsheet to a number to organise it.
Message: If this was helpful, let me know by giving me a thanks! :)
Which statement best describes a flexible algorithm?
Answers
Answer:
It can perform a task or solve a problem even if various inputs are involved.
Explanation:
Information censorship is used to____. (4 options)
1. Promote Authorization Government
2. Polarize the Public
3. Create Confusion
4. Promote Independent Media
Answers
Information censorship is used to control the flow of information and restrict access to certain content.
While the specific motives and methods behind information censorship can vary, it generally serves to exert authority and influence over the dissemination of information within a society.
Option 1: Promote Authorization Government - This option suggests that information censorship is used to support authoritarian or autocratic regimes by controlling the narrative and limiting dissenting viewpoints. Censorship can be employed as a means of consolidating power and suppressing opposition.
Option 2: Polarize the Public - Censorship can be used to manipulate public opinion by selectively suppressing or amplifying certain information, thereby influencing people's perspectives and potentially creating divisions within society.
Option 3: Create Confusion - Censorship can contribute to confusion by limiting access to accurate and reliable information. This can lead to a lack of transparency, misinformation, and the distortion of facts, making it challenging for individuals to form informed opinions.
Option 4: Promote Independent Media - This option is not typically associated with information censorship. Rather, independent media thrives in an environment that upholds freedom of speech and opposes censorship.
Overall, options 1, 2, and 3 align more closely with the potential outcomes of information censorship, while option 4 contradicts the nature and purpose of censorship.
For more questions on Information censorship
https://brainly.com/question/29828735
#SPJ8
What is cybersecurity? Cybersecurity refers to the protection of hardware?

Answers
Cybersecurity is the practice of safeguarding computer systems, networks, and mathematical data from unauthorized approach, theft, damage, or additional malicious attacks.
What is cybersecurity?It involves the use of differing technologies, processes, and practices to secure digital maneuvers, networks, and data from a wide range of dangers, including cybercrime, cyber-spying, cyber-terrorism, and different forms of malicious endeavor.
While cybersecurity does involve protecting fittings, it also involves looking after software, networks, and digital dossier. In addition to protecting against external warnings, etc.
Learn more about cybersecurity from
https://brainly.com/question/28004913
#SPJ1
Software Security Integration involves which attributes? Select the correct option(s) and click submit. Estimation of Software Security Efforts & Software Security Budget Requirements Estimation of Software Security Efforts & Sign Off Criteria Definition Software Security Budget Requirements & Sign Off Criteria Definition Software Security Effort Estimation and Budget Requirements, Identification of teams to perform reviews & Defining Sign Off Criteria Submit
Answers
Software Security Integration concerns which attributes to Estimation of Software Security Efforts & Software Security Budget Requirements
What is software security requirements?
A security requirement is a statement of needed security functionality that provides one of many different security properties of software is being satisfied. Security requirements are emanated from industry standards, applicable laws, and a history of past exposures.
What is software safety courses?The types of security software for business websites contain computer antivirus, network security, SaaS security, content control system, e-commerce software, payment gateway software, content delivery network, bot comfort, and monitoring tool.
To learn more about security requirement, refer
https://brainly.com/question/2818423
#SPJ9
Which of the following is the MOST economical way for Sandy, a technician, to implement 10- Gigabit Ethernet at a datacenter?A. 10GBaseLRB. 10GBaseSRC. 10GBaseXD. 10GBaseT
Answers
The most economical way for Sandy, a technician, to implement 10-Gigabit Ethernet at a datacenter is likely to be 10GBaseT. This option uses twisted pair copper cables, which are widely available and relatively inexpensive.
Additionally, 10GBaseT is backwards compatible with existing 1 Gigabit Ethernet infrastructure, which means that Sandy may be able to use some existing cables and switches, further reducing costs. 10GBaseLR, 10GBaseSR and 10GBaseX are other options for 10-Gigabit Ethernet, but they require specialized and expensive optical fibers and equipment.
Learn more about ethernet: https://brainly.com/question/13441312
#SPJ4
Console.Write(" Apple: $");
apple = Convert.ToDecimal(Console.ReadLine());
Answers
Below is a sample C# program that calculates the subtotal, tax, and total based on user input:
using System;
using System.Globalization;
class Program
{
static void Main()
{
decimal apple;
decimal banana;
decimal orange;
decimal subtotal;
decimal tax;
decimal total;
Console.Write("Apple: $");
apple = Convert.ToDecimal(Console.ReadLine());
Console.Write("Banana: $");
banana = Convert.ToDecimal(Console.ReadLine());
Console.Write("Orange: $");
orange = Convert.ToDecimal(Console.ReadLine());
subtotal = apple + banana + orange;
tax = subtotal * 0.065M;
total = subtotal + tax;
Console.WriteLine("");
Console.WriteLine("Subtotal: ${0}", String.Format("{0:0.00}", subtotal));
Console.WriteLine("Tax: ${0}", String.Format("{0:0.00}", tax));
Console.WriteLine("Total: ${0}", String.Format("{0:0.00}", total));
}
}
What is the code about?The above program takes user input for the prices of apple, banana, and orange. It then calculates the subtotal by adding the prices of all three items, the tax by multiplying the subtotal by 0.065, and the total by adding the subtotal and tax.
Finally, it displays the subtotal, tax and total to the user with two digits after the decimal point.
Learn more about Console from
https://brainly.com/question/13437184
#SPJ1
See full question below
Write a Console program, let users to enter prices calculate subtotal, tax, and total.
- Delcare variable data type as decimal (6 variables needed)
decimal apple;
- Conver string to decimal from input
apple = Convert.ToDecimal(Console.ReadLine());
- Do addition for subtotal
- Multiplication for tax (0.065M) --- M or m stands for money value, read page 94.
- Addition for total
- You need to show only two digits after decimal point
Console.WriteLine(" Subtotal: ${0}", String.Format("{0:0.00}", subTotal));
blank line: Console.WriteLine("")
Console.Write(" Apple: $");
apple = Convert.ToDecimal(Console.ReadLine());

10+2 is 12 but it said 13 im very confused can u please help mee
Answers
Mathematically, 10+2 is 12. So your answer is correct. However, if you are trying to write a code that adds 10 + 2, you may need to troubleshoot the code to find where the bug is.
What is troubleshooting?Troubleshooting is described as the process through which programmers detect problems that arise inside a specific system. It exists at a higher level than debugging since it applies to many more aspects of the system.
As previously stated, debugging is a subset of troubleshooting. While debugging focuses on small, local instances that can be identified and fixed in a single session, troubleshooting is a holistic process that considers all of the components in a system, including team processes, and how they interact with one another.
Learn more about Math operations:
https://brainly.com/question/199119
#SPJ1
a customer calls complaining their laptop wont start what should I say
Answers
Answer:
tell them to bring there laptop to you so you can explain how to get them out of situations like those. Or maybe do a video call so the person can show you whats going on and you can take it on from there guiding her on how to fix it...
Explanation:
In 3D animation, movement is displayed as

Answers
identify the following

Answers
Answer:
attachment sign
Explanation:
that is the attachment sign.
PLEASE HELP!
A primary school teacher wants a computer program to test the basic arithmetic skills of her students.
The program should generate a quiz consisting of a series of random questions, using in each case any two numbers and addition, subtraction and multiplication
The system should ask the student’s name, then ask 10 questions, output if the answer to each question is correct or not and produce a final score out of 10.
The program should save the scores to an external file and offer an option to view the high score table.
Analyse the requirements in detail and design, code, test and evaluate a program to meet these requirements.
Answers
The program that will execute as required above is:
import random
def generate_question():
num1 = random.randint(1, 10)
num2 = random.randint(1, 10)
operator = random.choice(['+', '-', '*'])
question = f"What is {num1} {operator} {num2}? "
if operator == '+':
answer = num1 + num2
elif operator == '-':
answer = num1 - num2
else:
answer = num1 * num2
return question, answer
def save_score(name, score):
with open('scores.txt', 'a') as file:
file.write(f"{name}: {score}/10\n")
def view_high_scores():
with open('scores.txt', 'r') as file:
scores = file.readlines()
scores.sort(reverse=True)
print("High Score Table:")
for score in scores:
print(score.strip())
def arithmetic_quiz():
name = input("Enter your name: ")
score = 0
for _ in range(10):
question, answer = generate_question()
user_answer = int(input(question))
if user_answer == answer:
print("Correct!")
score += 1
else:
print("Incorrect!")
print(f"Final score: {score}/10")
save_score(name, score)
option = input("Do you want to view the high score table? (y/n) ")
if option.lower() == 'y':
view_high_scores()
arithmetic_quiz()
What is the objective of the above program?The objective of the above program is to create a computer program that tests the basic arithmetic skills of primary school students.
The program generates a quiz with random arithmetic questions, allows users to answer them, provides feedback on the correctness of their answers, saves scores, and offers a high score table for viewing.
Learn more about program:
https://brainly.com/question/30613605
#SPJ1
Look at the attached photos! I need urgent help! Please answer each of the questions. If you have any, I will take them!


Answers
The greatest challenge the analyst is likely to face in solving this problem is A. Making sure the price and volume numbers are accurate
The skill practiced is Consensus building.
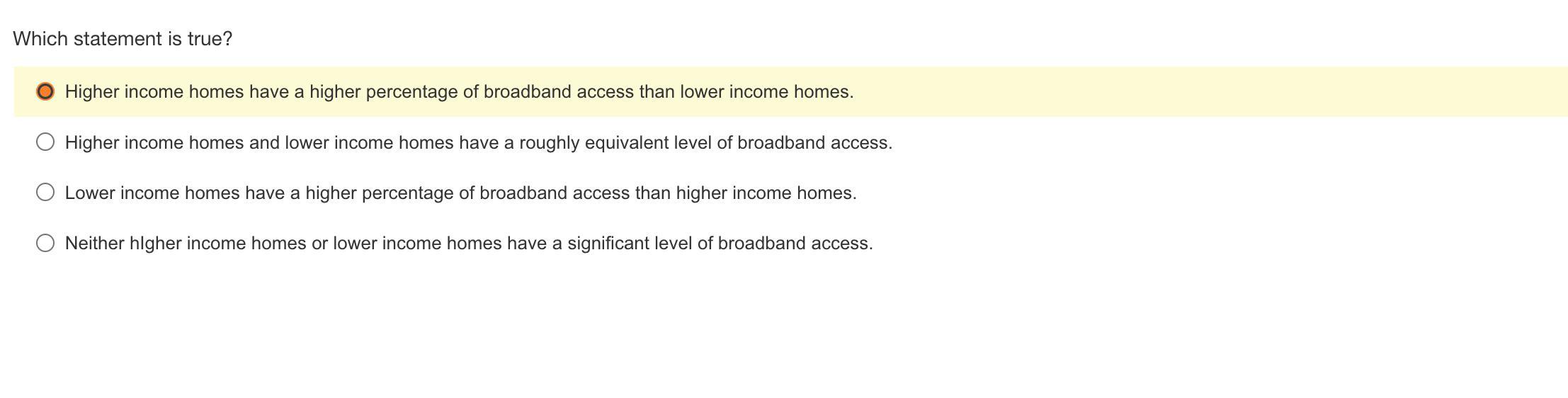
The true statement is that A. Higher income homes have a higher percentage of broadband access than lower income homes
How to convey the informationThe greatest challenge the analyst is likely to face in solving this problem is likely to be finding meaningful patterns in the stock market data that can accurately predict future behavior.
Higher income homes have a higher percentage of broadband access than lower income homes. This disparity in broadband access is commonly referred to as the "digital divide".
Learn more about market on:
https://brainly.com/question/25369230
#SPJ1
For Questions 3-5, consider the following code:
stuff = []
stuff.append(1.0)
stuff.append(2.0)
stuff.append(3.0)
stuff.append(4.0)
stuff.append(5.0)
print(stuff)
What data type are the elements in stuff?
![For Questions 3-5, consider the following code:stuff = []stuff.append(1.0)stuff.append(2.0)stuff.append(3.0)stuff.append(4.0)stuff.append(5.0)print(stuff)What](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/JydpDR99ndBtKsJ9MrQaX2Tg81GrNIvG.jpeg)
![For Questions 3-5, consider the following code:stuff = []stuff.append(1.0)stuff.append(2.0)stuff.append(3.0)stuff.append(4.0)stuff.append(5.0)print(stuff)What](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/J5cM80gwkxawkrVT6SboBlrFv80zsd1C.jpeg)
Answers
Answer:
Data type of the elements in stuff is floatprint(len(stuff)) will output 5print(stuff[0]) will output 1.0Explanation:
Data type of the elements in stuff is float
print(len(stuff)) will output 5
print(stuff[0]) will output 1.0
There are several reasons to specify a data type, including resemblance, practicality, and attention-getting. The ability to understand complex terminology is frequently aided by effective data type.
The concept of a data type is explicitly included in almost all programming languages, albeit the range of acceptable data types is frequently constrained by factors like simplicity, computability, or regularity.
The compiler can often select an effective machine representation with an explicit data type declaration, but the conceptual organization provided by data types should not be undervalued.
To learn more about Data type, refer to the link:
https://brainly.com/question/14581918
#SPJ2
An index of all the files stored on the computer is/are the??
Answers
Answer:
File Allocation Table (FAT)
Explanation:
true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
Assume a 2^20 byte memory:
a) What are the lowest and highest addresses if memory is byte-addressable?
b) What are the lowest and highest addresses if memory is word-addressable, assuming a 16-bit word?
c) What are the lowest and highest addresses if memory is word-addressable, assuming a 32-bit word?
Answers
a) Lowest address: 0, Highest address: (2^20) - 1. b) Lowest address: 0, Highest address: ((2^20) / 2) - 1. c) Lowest address: 0, Highest address: ((2^20) / 4) - 1.
a) If memory is byte-addressable, the lowest address would be 0 and the highest address would be (2^20) - 1.
This is because each byte in the memory requires a unique address, and since there are 2^20 bytes in total, the highest address would be one less than the total number of bytes.
b) If memory is word-addressable with a 16-bit word, each word would consist of 2 bytes.
Therefore, the lowest address would be 0 (representing the first word), and the highest address would be ((2^20) / 2) - 1.
This is because the total number of words is equal to the total number of bytes divided by 2.
Subtracting 1 gives us the highest address, as the addresses are zero-based.
c) If memory is word-addressable with a 32-bit word, each word would consist of 4 bytes.
In this case, the lowest address would still be 0 (representing the first word), and the highest address would be ((2^20) / 4) - 1.
Similar to the previous case, the total number of words is equal to the total number of bytes divided by 4.
Subtracting 1 gives us the highest address.
For more questions on address
https://brainly.com/question/30273425
#SPJ8
Individuals and organizations are moving to highly integrated enterprise systems
Select one:
True
False
Answers
The statement "Individuals and organizations are moving to highly integrated enterprise systems" is true.
What is enterprise system integration?An ERP system tells you exactly how much stock you need for each job and when you need it. ERP software also enables you to automate many of your procedures, resulting in increased efficiencies across the manufacturing process.
This implies less duplication, better resource scheduling, and less downtime. Enterprise integration allows for smooth cooperation by merging functionality and data interchange across many apps.
Therefore, the correct statement is true.
To learn more about enterprise, refer to the link:
https://brainly.com/question/18551533
#SPJ1
Which part of the name of a document indicates the program that was used to edit it?
Answers
Answer:
extension
Explanation:
The extension is the part of the name of a document which helps in showing the program that was used for the edit.
The extension is simply a three letter word or sometimes four-letter abbreviation depending on the document.
Extension helps in showing the type of file. For example, different forms of extension are "docx", "pdf", "exe", "html" etc. They are useful as one can know the application that will be used in opening such files.
Read related link on:
https://brainly.com/question/16280230
Which character is midway between the 3rd character from left and 6lh character from rights
a. 2
b. 3 ANS
c. 8
d. Y
Answers
Answer:
D
Explanation:
Please help out with this question

Answers
Using a programme that highlights the changes between the two portions, such as a version control tool or a plagiarism checker, is one technique to compare different sections of a work.
What is the plagiarism detection tool?A plagiarism detector searches for similarities between your content and other texts using sophisticated database tools. Universities employ them to scan student assignments. Additionally, you can utilise paid plagiarism detectors to examine your own work before submission.
What do we call the computer programme that can identify plagiarism by examining the uniqueness of a piece of writing?Software that detects plagiarism compares uploaded materials to other content databases to determine whether they are plagiarised. Checkers for plagiarism are used by writers and content producers to prevent unintentional
To know more about programme visit:-
https://brainly.com/question/30307771
#SPJ1
How to do a row of circles on python , with the commands , picture is with it .

Answers
Answer:
o.o
Explanation:
Describing How to Create a Self-Join Query
Use the drop-down menus to complete the steps for creating a self-join query.
1. Click the
tab.
2. In the Queries group, click Query Design.
3. In the Show Table dialog box, add
4. Click and drag a field from one copy of the table and drop it on the other table.
5. Add the fields to the query.
6. Click
to see the results.
е
Answers
Answer:1. Click the ✔ Create tab.
2. In the Queries group, click Query Design.
3. In the Show Table dialog box, add ✔ the same table twice
.
4. Click and drag a field from one copy of the table and drop it on the other table.
5. Add the fields to the query.
6. Click ✔ Run
to see the results.
Explanation:on edg
Describing How to Create a Self-Join Query Use the drop-down menus to complete the steps for creating a self-join query is by 1. Click the tick in the tab to design a Self-Join Query.
Why can we use self be a part of?A self-be a part of is a be a part of that may be used to sign up for a desk with itself. Hence, it's miles a unary relation. In a self-be, a part of, every row of the desk is joined with itself and all of the different rows of the equal desk.
The Query and View Designer assigns an alias to the second one example via way of means of including a sequential wide variety to the desk name. In addition, the Query and View Designer creates a be a part of line among the 2 occurrences of the desk or desk-valued item withinside the Diagram pane.
Read more about the Queries :
https://brainly.com/question/25694408
#SPJ2
Write an essay of at least 250 words describing the connections between people and computing and the role of equity in those connections.
As you research, consider that equity is affected by the actions of individuals, organizations, and governments. How is the equity question you choose as your topic affected by these players?
Answers
When used correctly, technology can make a significant contribution to equity. It removes obstacles to accessing educational materials, meets students where they are in various learning contexts and needs, and provides educators with better understanding into the educational contexts they are creating.
What is equity?Digital equity is defined by the National Digital Inclusion Alliance (NDIA) as "a condition in which all individuals and communities have the information technology capacity required for full participation in our society, democracy, and economy."
Computer science for all students necessitates that equity be prioritized in any reform effort.
When equity exists, appropriate supports are provided based on individual student needs, allowing all students to achieve similar levels of success.
Technology, when used correctly, can make a significant contribution to education equity.
It removes barriers to educational materials access, meets students where they are in diverse learning contexts and needs, and gives educators a better understanding of the educational contexts they are creating.
Thus, this is the connections between people and computing and the role of equity in those connections.
For more details regarding equity, visit:
https://brainly.com/question/13278063
#SPJ1
why is it important to o save a file when using a computer
Answers
Answer:
I think that it's important to save a file when using a computer so you won't lose it. Much like a document usually files are important and mark progress. Like if you're writing an essay and get tired simply save it to a file or document and continue it later. But if you weren't to do that you could lose all your saved work.
Explanation:
Hope that helps. there's not a lot of information to go off of
I think that it's important to save a file when using a computer so you won't lose it.
By watching the expression Mynum=4 * mynum + c from a programming language, what can we say about this language?
This is not an imperative programming language
This is a case sensitive language
This is not a case sensitive language
We can not determine if this language is case-sensitive or case-insensitive
Answers
Answer:
We can not determine if this language is case-sensitive or case-insensitive
Explanation:
It is unclear wether Mynum and mynum are intended to be different variables or the same variable. Both would work.
Having said that, mixing case like this is always a bad design.
Answer:
we do not determine If this language is case
What microphone is this

Answers
Answer:
Thats looks like a Sennheiser Pro Audio Wireless Microphone System, Black (MKE600) . also known as Sennheiser MKE 600
Where you can get it:
https://www.amazon.com/Sennheiser-MKE600-Camcorder-Shotgun-Microphone/dp/B00B0YPAYQ
Youre welcome. (pls give brainlest thanks)
Implement a binary search function in three substantially different programming languages. In each program (identical, except for the programming language), carry out the same 10,000,000 unsuccessful searches for eight different-sized arrays, namely arrays of sizes 128, 512, 2048, 8192, 32768, 131072, 524288, and 2,097,152. Measure in each of the three programs the time it takes to do the 10,000,000 searches for each of the eight arrays. Compare these timings to the theoretical timings the algorithm binary search provides. Are there differences between the three programs? Explain your timings and observations!!
Answers
Answer:
The code to this question can be defined as follows:
Explanation:
C language code:
#include <stdio.h>//defining header file
int binarySearch(int x[], int l, int y, int z)//defining method binarySearch that accepts four integer parameter
{
if (y >= l)//defining if block that check r value is greater the l
{
int m= l + (y - l)/2; //defining if block that holds mid value of array
if (x[m] == z)//use if block that check value in array
return m;// return array value
if (x[m] > z) //defining if block that check array value greater then x value
return binarySearch(x, l, m-1, z);//use return keyword to call method
return binarySearch(x, m+1, y, z);// in else it use return keyword to call method
}
return -1;//return value -1
}
int main()//defining main method
{
int x[] = {2, 3, 4, 10, 40};//defining array that hold integer values
int n = sizeof(x)/ sizeof(x[0]);//use n variable to hold its size value
int z = 10;//defining x varaiable that hold integer value
int r= binarySearch(x, 0, n-1, z);//use r varaiable to hold method return value
if(r== -1) //defining if block that check its value equal to -1
printf("Number is not foud in array ");//print message
else
printf("Number is present at %d position", r);//print value
return 0;
}
C++ language code:
#include <iostream>// header file
using namespace std;
int binarySearch(int x[], int l, int y, int z)//defining method binarySearch that accepts four integer parameter
{
if (y >= l)//defining if block that check r value is greater the l
{
int m= l + (y - l)/2; //defining if block that holds mid value of array
if (x[m] == z)//use if block that check value in array
return m;// return array value
if (x[m] > z) //defining if block that check array value greater then x value
return binarySearch(x, l, m-1, z);//use return keyword to call method
return binarySearch(x, m+1, y, z);// in else it use return keyword to call method
}
return -1;//return value -1
}
int main()//defining main method
{
int x[] = {2, 3, 4, 10, 40};//defining array that hold integer values
int n = sizeof(x)/ sizeof(x[0]);//use n variable to hold its size value
int z = 10;//defining x varaiable that hold integer value
int r= binarySearch(x, 0, n-1, z);//use r varaiable to hold method return value
if(r== -1) //defining if block that check its value equal to -1
cout<<"Number is not foud in array ";//print message
else
cout<<"Number is present at position "<< r;//print value
return 0;
}
Python language code:
def binarySearch (a, x, r, y):#defining a method binarySearch
if r >= x:#defining if block that checks r is greater than equal to x
m = x + (r - x)//2#defining m variable that hold mid value
if a[m] == y:#use if that check its input value equal y
return m#return m value
elif a[m] > y:#use array that check its value greaterthan y
return binarySearch(a,x, m-1, y) #use return keyword to call method
else:#defining else block
return binarySearch(a, m+1, r, y)#use return keyword to call method
else: #defining else block
return -1#return value -1
a = [ 2, 3, 4, 10, 40 ]#defining list a that holds value
y = 10#defining integer variable
r = binarySearch(a, 0, len(a)-1, y)#defining r variable that holds method value
if r != -1:#use if that check r is not equal to -1
print ("Number is available at ", r," position")#print value
else:#else block
print ("Number is not available in array")#print message
Computers were originally invented to
Group of answer choices
A.to share information on the Internet.
B.make complex mathematical calculations possible and make tasks easier for humans.
C.to play video games.
Answers
Answer:
B
Explanation:
It's B because why would it me made to play video games
Answer:
B
Explanation:
A, the internet didnt exist yet, so it cant be this
C, video games would require computers, so its ruled out on a similar basis as the previous