You've just finished installing a wireless access point for a client. What should you do to prevent unauthorized users from using the access point (AP) configuration utility
Answers
Answer:
Change the administrative password on the access point (AP). In addition, you can restrict access and keeping your AP software patched and up to date while also maintaining and installing a firewall and antivirus.
Related Questions
"Blackflow Device" is a term used to describe a device that?
a. connects three inlet lines with one outlet line
b. lets air into valve vaults
c. prevents backflow of potentially contaminated source into drinking water d. prevents backflow of water through an out-of-service pump
Answers
"Backflow Device" is a term used to describe a device that prevents the reverse flow of potentially contaminated water or other fluids from flowing back into a drinking water system.
Backflow can occur when there is a drop in pressure in a plumbing system, causing fluids to flow in the opposite direction of their intended flow. This can create a risk of contamination if the fluids flowing back into the system are from a potentially contaminated source, such as a chemical tank, irrigation system, or swimming pool. A backflow device, also known as a backflow preventer, is designed to prevent this from happening by allowing water to flow in only one direction. It is typically installed at the point where the plumbing system connects to a public water supply or other potable water sources. Backflow devices can be required by local or national plumbing codes and may need to be inspected and tested periodically to ensure they are functioning properly. In summary, a backflow device is a device that prevents the reverse flow of potentially contaminated water or other fluids from flowing back into a drinking water system. It is typically required by plumbing codes and is designed to ensure the safety and quality of the drinking water supply.
Learn more about Backflow Device here:
https://brainly.com/question/31481844
#SPJ11
building entire search tree prior to searching can be impossible for some state spaces. true or false?
Answers
No, It may be hard for some state spaces to construct the whole search tree before searching.
what types of trees are binary search?The following characteristics of the node-based binary tree data structure known as Binary Search Tree include: Only nodes with keys lower than a node's key are found in the node's left subtree. Only nodes with keys higher than the node's key are found in a node's right subtree.
What does the name "binary search tree" mean?An efficient way to keep track of a sorted list of integers is through a binary search tree. Because each tree node can only have two offspring, it is known as a binary tree.
To know more about Binary Search Tree visit:
https://brainly.com/question/12946457
#SPJ4
for every supplier that supplies green part and red part, print the name of the supplier and the price of the most expensive part that he supplies
Answers
To determine the name of suppliers and the prices of the most expensive parts they supply, we need to identify suppliers who provide both green and red parts. Then, we compare the prices of these parts from each supplier and select the highest-priced one.
To find the suppliers who offer both green and red parts, we can analyze a database or dataset containing information about suppliers and their provided parts. We need to filter out the suppliers who supply both green and red parts, as they are the ones we are interested in.
Once we have identified these suppliers, we can proceed to compare the prices of the green and red parts they supply. For each supplier, we look at the prices of both types of parts and determine the highest-priced one. This information allows us to identify the price of the most expensive part each supplier supplies.
By iterating through the list of suppliers who offer both green and red parts, we can obtain the names of these suppliers along with the prices of the most expensive parts they supply. This analysis helps in understanding which suppliers provide the highest-priced parts and enables businesses to make informed decisions when selecting suppliers based on the prices and quality of their offerings.
learn more about suppliers and the prices here:
https://brainly.com/question/29562759
#SPJ11
the processing is done in the
Answers
Answer:
CPU Central Processing Unit
Answer:
CPU.... I'm not sure but it might be right or can u put the full question because it sorta don't make any sense
Exercise #3: Write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I). Your program should read the data from a file called " "
Answers
To find students with the highest and lowest average marks in the first two CS (I) homework, read data from a file, calculate averages, and print the corresponding student names using the provided Python code.
To write a program that finds all students who score the highest and lowest average marks of the first two homework in CS (I),
Read data from the file.First of all, the program should read data from a file. The file name is " ". Calculate the average of the first two homework for each student. Then the program should calculate the average of the first two homework for each student, and store it in a dictionary with the student's name as the key.Find the highest and lowest averages.After that, the program should find the highest and lowest averages and the corresponding student names.Print the names of the students who have the highest and lowest average marks.Finally, the program should print the names of the students who have the highest and lowest average marks.Below is the Python code that can be used to find the students who score the highest and lowest average marks of the first two homework in CS (I):
```python#open the filefile = open('filename', 'r')#initialize a dictionary to store the average of first two homework marks for each studentdata = {}#iterate through each line of the filefor line in file:#split the line into a list of valuesvalues = line.strip().split()#get the student's name and the first two homework marksname = values[0]marks = [int(x) for x in values[1:3]]#calculate the average of the first two homework marksaverage = sum(marks)/len(marks)#store the average in the dictionarydata[name] = average#find the highest and lowest averageshighest = max(data.values())lowest = min(data.values())#find the students with the highest and lowest averageshighest_students = [name for name, average in data.items() if average == highest]lowest_students = [name for name, average in data.items() if average == lowest]#print the names of the studentsprint('Students with highest average:', ', '.join(highest_students))print('Students with lowest average:', ', '.join(lowest_students))```
Note: Replace the 'filename' with the actual name of the file that contains the data.
Learn more about Python code: brainly.com/question/26497128
#SPJ11
send-mailmessage : mailbox unavailable. the server response was: 5.7.64 tenantattribution; relay access denied
Answers
The send-mailmessage : mailbox unavailable. the server response was: 5.7.64 tenantattribution; relay access denied is known to be due to
A person has use an inbound connector in Microsoft 365 that is said to be configured to employ the use of a certificate from on-premises to know or verify the presence or the identity of the submitting server.The IP address that's configured in the Microsoft 365 connector is one that do not match the IP address that is said to be used by the submitting server.What are the Symptoms of the case above?In the issue above, the likely symtoms occurs if the user has send mail externally, and they tend to receive the error message: 550 5.7.64 TenantAttribution; Relay Access Denied SMTP.
Therefore, The send-mailmessage : mailbox unavailable. the server response was: 5.7.64 tenantattribution; relay access denied is known to be due to
A person has use an inbound connector in Microsoft 365 that is said to be configured to employ the use of a certificate from on-premises to know or verify the presence or the identity of the submitting server.The IP address that's configured in the Microsoft 365 connector is one that do not match the IP address that is said to be used by the submitting server.Learn more about server response from
https://brainly.com/question/16830963
#SPJ1
T/F : The Windows Task Manager can be used to seek out Trojan programs on Microsoft Windows computers.
Answers
The Windows Task Manager can be used to seek out Trojan programs on Microsoft Windows computers. True.
While it is not a specialized anti-virus tool, Task Manager can help you identify suspicious processes running in the background that may be associated with Trojan programs or other malware.
To use the Task Manager for this purpose, follow these steps:
1. Press Ctrl + Shift + Esc on your keyboard to open the Task Manager.
2. Click on the "Processes" tab to see a list of all the running processes on your computer.
3. Look for any unfamiliar or suspicious processes that you don't recognize or that are using an unusually high amount of resources.
4. If you find a suspicious process, right-click on it and select "Open file location" to determine the source of the process.
5. Research the process online to determine if it is associated with a Trojan program or other malware. Be cautious and do not delete any files unless you are certain they are malicious.
Please note that Task Manager is not a foolproof method for detecting Trojan programs, as some may be hidden or disguised. It is always recommended to use a reliable anti-virus software to keep your computer protected from malware.
To know more about Windows Task Manager visit:
https://brainly.com/question/11889157
#SPJ11
While going through the network log, Sarah, a network security administrator, noticed substantial outbound network traffic. Which activity did Sarah perform
Answers
The activity Sarah, a network security administrator, performed by going through a network log and then noticing substantial outbound network traffic is: indicators of compromise (IOC).
Cybersecurity refers to the preventive practice adopted for the protection of computers, software applications (programs), servers, networks, and data from unauthorized access, attack, potential theft, or damage, through the use;
A body of technology.Processes.Frameworks.Policies.Network engineers.In Cybersecurity, it is very important to adopt certain security standards, policies, frameworks, technology, antivirus utility, and best practices, in order to achieve the following:
I. Prevent data theft and data corruption by malwares (viruses).
II. Enhance data integrity and secure (protect) data.
III. Mitigate any unauthorized access or usage of the system network by a hacker.
In conclusion, the indicators of compromise (IOC) refers to the factual evidence on a network device pointing to a security breach or data theft.
Read more: https://brainly.com/question/24112967
explore the data frame, identify and report the missing data. how will you deal with the missing data?
Answers
To identify missing data in a data frame, you can check for null values or use visualization techniques. Dealing with missing data can involve approaches such as deletion, imputation, or using categorical indicators, depending on the extent and nature of the missing values.
To explore a data frame and identify missing data, you can use various techniques such as checking for null values, visualizing missing data patterns, or using summary statistics.
Once the missing data is identified, you can employ different strategies to deal with it. Here are some common approaches:
1. Deleting Rows or Columns: If the missing data is minimal or doesn't significantly affect the analysis, you may choose to delete the rows or columns containing missing values. However, this approach should be used cautiously to ensure that valuable information is not lost.
2. Imputation: Missing values can be replaced with estimated or predicted values based on other data points. This can be done through mean, median, mode imputation, or using more advanced techniques like regression or machine learning algorithms.
3. Categorical Indicator: If missing values occur in categorical variables, you can create a separate category or indicator variable to represent missing data. This allows the missingness to be explicitly accounted for in the analysis.
4. Multiple Imputation: In cases where missing data is more extensive, multiple imputation methods can be employed. This involves creating multiple imputed datasets, filling in missing values using statistical models, and combining the results to obtain more accurate estimates.
5. Domain Knowledge: Depending on the context and the reason for missing data, domain knowledge can help inform the best approach.
For instance, if missing values are due to non-response in a survey, understanding the survey process and potential biases can guide imputation techniques.
The choice of how to deal with missing data depends on factors like the amount of missing data, the nature of the variables, the goals of the analysis, and assumptions made about the missingness.
It is important to carefully consider the impact of each method and the potential biases introduced to ensure the validity and reliability of the analysis.
Learn more about data frame:
https://brainly.com/question/30403325
#SPJ11
A worksheet is a multiple column form that facilitates the:.
Answers
A worksheet is a multiple column form that facilitates the following activities:1. Preparation of accounting entries,2. Adjustments, and3. Closing entries The worksheet is a form that is usually developed in the Excel Spreadsheet program.
It has several columns and is used to enter data and information that is used to produce financial reports. Worksheets are useful tools for preparing financial statements since they provide a way to record and summarize financial data before it is transferred to other accounting records and reports.
The worksheet is used in accounting as a tool to help prepare the financial statements. It is a document that is used to summarize all the financial information for a specific period of time, such as a month or a quarter. The worksheet contains columns for each account and allows the user to enter data and information into each column.
To know more about worksheet visit:
https://brainly.com/question/31917702
#SPJ11
FILL IN THE BLANK. This type of software allows students to record, sort, mathematically analyze and represent numerical data in tabular and/or graphical forms. ___
Answers
Spreadsheets software is a type of software allows students to record, sort, mathematically analyze and represent numerical data in tabular and/or graphical forms.
Why do people use spreadsheets?One tool for storing, modifying, and analyzing data is a spreadsheet. A spreadsheet's data is arranged in a series of rows and columns, where it can be searched, sorted, calculated, and used in a number of charts and graphs.
Therefore, A program known as a spreadsheet, also referred to as a tabular form, is used to arrange data into rows and columns. This information can then be arranged, sorted, calculated (using formulas and functions), analyzed, or graphically represented to illustrate.
Learn more about Spreadsheets from
https://brainly.com/question/26919847
#SPJ1
In an online shopping application, the primary case type PurchaseOrder has two child case types: Payment and Packaging. In processing PurchaseOrder case PO-11, Payment case Pay-37 and Packaging case Pac-56 are created. Which statement about the processing of PO-11, Pay-37, and Pac-56 is correct?
A. PO-11 has to be resolved before either Pay-37 and Pac-56 is resolved.
B. Pac-56 has to be resolved before Pay-37 is resolved.
C. Both Pay-37 and Pac-56 have to be resolved before PO-11 can be resolved.
D. PO-11 can be resolved when either Pay-37 or Pac-56 is resolved.
Answers
Answer:
The answer is "Option C".
Explanation:
The principal instance type PurchaseOrder has two types of instance children in an online purchasing application: Pay and Packing. Pay case Pay-37 and packing instance Pac-56 are designed to Sales Orders case PO-11 execution. All statements regarding PO-11, Pay-37, and Pac-56 should be settled before PO-11 may be addressed. Both Pay-37 and Pac-56.
A numbering system such as identifiers for control and sub accounts is superior to the text based system of names, because .................
it is cheaper to implement.
it results in fewer errors and avoids duplication, making it easier to generate unique identifiers.
it is required by the Accounting Principles Board.
is understood better as it has been a long comvention and was used even before the advent of computer based accounting systems.
Answers
A numbering system such as identifiers for control and sub accounts is superior to the text-based system of names because it results in fewer errors and avoids duplication, making it easier to generate unique identifiers.
Implementing a numbering system for control and sub accounts offers several advantages over a text-based system. Firstly, it reduces the likelihood of errors and duplication. With numbers, it is easier to ensure uniqueness and avoid confusion compared to relying on names, which may be subjective, ambiguous, or prone to spelling mistakes.
Secondly, a numbering system simplifies the process of generating unique identifiers. By following a consistent numerical pattern, it becomes easier to assign and manage account codes. This promotes efficiency and accuracy in accounting processes, such as record-keeping, analysis, and reporting.
While a numbering system is not necessarily required by the Accounting Principles Board, it is widely adopted and recommended in the field of accounting. The convention of using numerical identifiers predates computer-based accounting systems and has stood the test of time due to its practicality and effectiveness. Therefore, the use of a numbering system for control and sub accounts is considered superior to a text-based system, as it offers cost-effectiveness, minimizes errors and duplication, and aligns with longstanding accounting practices
To know more about unique identifiers,visit:
https://brainly.com/question/14439455
#SPJ11
What is the typical educational requirement for a non-entry level software programmer? high school diploma technical certificate bachelor’s degree master’s degree
Answers
Answer: technical certificate
Explanation: i just took the test and i got it right
A bachelor's degree in computer science, information technology, or computer engineering is usually required for a career as a computer programmer. Option C is correct.
What education do you need to be a non-entry level software programmer?Computer programmers create computer programs by creating code in a variety of programming languages. They run new programs through their paces and look for flaws. A bachelor's degree is often required for computer programmers, however some firms may recruit programmers with an associate degree.
Individuals who want to work as computer programmers must have a degree in computer science, information technology, mathematics, or a related field.
A bachelor's degree in computer and information technology or a related discipline, such as mathematics, is often required for computer programmers. Some firms, however, hire people with different degrees or experience in specialized programming languages.
Therefore, option C is correct.
Learn more about the bachelor’s degree, refer to:
https://brainly.com/question/5709442
#SPJ2
Case 20-4 Customized Software
Answers
Custom software development is the process of creating, deploying, and maintaining software particularly for a set of users, tasks, or organizations.
Give an illustration of bespoke software.specialized qualities and skills: A developer creates a bespoke software product specifically to meet the requirements of the commissioning company. For instance, only JPMorgan Chase or one of its specific divisions would use a software a programmer created for the bank.
The definition of "custom software"Software that has been specially developed for a certain business or user is referred to as software applications (sometimes referred to as bespoke software or tailor-made software).
To know more about software visit:-
brainly.com/question/985406
#SPJ4
what is a defult? pls help if you wouldn't mind
Answers
Answer:
a beginner or a novice
Explanation:
Which of the following is an example of a database?
A. the names and ages of children
B. the title of a book
C. a word that rhymes with bat
D. the name of the most recent U. S. president
Answers
Answer:
the names and ages of children
a technician wishes to deploy windows 10 pro to multiple pcs through the remote network installation process. the technician begins by connecting the new pcs to the network and booting them up. however, the deployment fails because the target pcs are unable to communicate with the deployment server. what is the possible cause?
Answers
Answer:
There are several possible causes for the deployment failure in this scenario:
Network connectivity issues: One possible cause is that there are network connectivity issues preventing the target PCs from communicating with the deployment server. The technician should check the network cables and switches, as well as the network settings on the target PCs and the deployment server, to ensure that they are properly configured and functioning correctly.Firewall or security software: Another possible cause is that the firewall or security software on the target PCs or the deployment server is blocking the communication. The technician should check the firewall settings and any security software on both the target PCs and the deployment server, and ensure that they are properly configured to allow communication.Incorrect deployment server configuration: It is also possible that the deployment server is not properly configured for the deployment. The technician should check the deployment server settings and ensure that it is set up correctly for the remote installation process.Hardware or software issues: Finally, hardware or software issues on the target PCs or the deployment server could also cause the deployment failure. The technician should check for any hardware or software issues on both the target PCs and the deployment server, and resolve any issues that are found.By identifying and addressing the root cause of the communication failure, the technician should be able to successfully deploy Windows 10 Pro to the target PCs through the remote network installation process.
Explanation:
A technician wishes to deploy Windows 10 Pro to multiple pcs through the remote network installation process. The possible cause is the NIC cards on the new PCs are not PXE-enabled.
What is a deployment failing?Network connectivity problems: One potential reason is that the target PCs are unable to connect to the deployment server due to network connectivity problems. The network cables, switches, target PCs, and deployment server settings should all be examined by the expert to make sure everything is configured and working properly.
Firewall or security software: The firewall or security software on the target computers or the deployment server could also be the issue. On both the target PCs and the deployment server, the technician should examine the firewall configurations and any security software to make sure they are set up correctly to allow communication.
Therefore, a technician wants to use the remote network installation technique to distribute Windows 10 Pro to several computers. The new PCs' NIC cards not supporting PXE could be the issue.
To learn more about technician, refer to the link:
https://brainly.com/question/13194741
#SPJ2
Justify the following statement: “Some Americans’ sedentary lifestyles contribute to their poor health.”
Answers
Answer:
Since the average American will spend 24 hours watching television per week, it is safe to say that they suffer from a lack of movement and exercise. This, in turn, will lead more Americans to be overweight and more likely to suffer from serious health problems! :)
Explanation:
1. write a statement that accesses the contents of the field quantity in an array variable named $_post.
Answers
You can extract the contents of the "quantity" field in the $_POST array variable by implementing the subsequent code.
The Javascript Code
$quantity = $_POST['quantity'];
The value of the "quantity" field in the $_POST array is being assigned to the variable $quantity through this code. This presupposes that the field labeled as "quantity" has been transmitted via a form utilizing the POST technique.
Thus, it can be seen that the statement that accesses the contents of the field quantity in an array variable named $_post is given.
Read more about javascript here:
https://brainly.com/question/16698901
#SPJ1
4.14 lab: grocery shopping list (linked list: inserting at the end of a list) given main() in the shoppinglist class, define an insertatend() method in the itemnode class that adds an element to the end of a linked list. do not print the dummy head node. ex. if the input is: 4 kale lettuce carrots peanuts where 4 is the number of items to be inserted; kale, lettuce, carrots, peanuts are the names of the items to be added at the end of the list. the output is: kale lettuce carrots peanuts
Answers
Using the codes in computational language in python it is possible to write a code that given main() in the shoppinglist class, define an insertatend() method in the itemnode class that adds an element to the end of a linked list.
Writting the code:public class ItemNode {
private String item;
private ItemNode nextNodeRef; // Reference to the next node
public ItemNode() {
item = "";
nextNodeRef = null;
}
// Constructor
public ItemNode(String itemInit) {
this.item = itemInit;
this.nextNodeRef = null;
}
// Constructor
public ItemNode(String itemInit, ItemNode nextLoc) {
this.item = itemInit;
this.nextNodeRef = nextLoc;
}
// Insert node after this node.
public void insertAfter(ItemNode nodeLoc) {
ItemNode tmpNext;
tmpNext = this.nextNodeRef;
this.nextNodeRef = nodeLoc;
nodeLoc.nextNodeRef = tmpNext;
}
// TODO: Define insertAtEnd() method that inserts a node
// to the end of the linked list
public void insertAtEnd(ItemNode head, ItemNode nodeLoc){
ItemNode temp = head;
// Iterate till the last node
while(temp.nextNodeRef!=null){
temp = temp.nextNodeRef;
}
// Insert after the last node
temp.nextNodeRef = nodeLoc;
}
// Get location pointed by nextNodeRef
public ItemNode getNext() {
return this.nextNodeRef;
}
public void printNodeData() {
System.out.println(this.item);
}
}
See more about python at brainly.com/question/29225072
#SPJ1

Which Application program saves data automatically as it is entered?
MS Word
PowerPoint
MS Access
MS Excel
Answers
The Application program that saves data automatically as it is entered MS Access. The correct option is C.
What is MS Access?Microsoft Access is a database management system that includes a graphical user interface, the relational Access Database Engine, and software-development tools.
It is a component of the Microsoft 365 software package and is available as a standalone product or as part of the Professional and higher editions.
Data kept in Access may be found and reported on with ease. Make interactive data entry forms. a variety of data sources can be imported, transformed, and exported.
Access is often more effective at managing data because it makes it easier to keep it structured, searchable, and accessible to several users at once.
MS Access is an application tool that automatically saves data as it is entered.
Thus, the correct option is C.
For more details regarding MS access, visit:
https://brainly.com/question/17135884
#SPJ2
What is the missing line?
import csv
_____
myReader = csv.reader(inFile)
for item in myReader:
print(item)
inFile = open("fruit.txt","r")
inFile = reader("fruit.txt","open")
inFile = reader("fruit.txt","r")
inFile = open("fruit.txt","read")
Answers
Based on the code written above, the missing line is option C: inFile = reader("fruit.txt","r")
What does line encoding mean?The code used to transmit data from a digital signal via a transmission line is called a line code. This coding method was chosen to prevent signal overlap and distortion like inter-symbol interference.
A group of instructions used to alter data such that a certain input yields a specific output is known as a program in computer coding.
Digital data is transformed into digital signals through the process of line coding. Using this method, we turn a series of bits into a digital signal. Digital data are encoded into a digital signal at the sender side, and they are reproduced at the receiver side by decoding the digital signal.
The full code is:
import CSV
inFile = open('pets.txt', 'r')
myReader =
reader(inFile)
for item in myReader
print(item)
exit()
Learn more about code from
https://brainly.com/question/23865485
#SPJ1
the software development step that is particularly important for people who may be involved with the program in the future including users, operators, and programmers.
Answers
The step in software development that is particularly important for people who may be involved with the program in the future including users, operators, and programmers is the testing and debugging phase.
This is because it ensures that the program is working properly and any issues or errors are addressed before the program is released. Programmers play a crucial role in this phase as they are responsible for identifying and fixing any coding issues. Additionally, operators and users benefit from this phase as it results in a more stable and user-friendly program The software development step that is particularly important for people who may be involved with the program in the future, including users, operators, and programmers, is the "documentation" phase. In this phase, developers create clear and comprehensive documents to ensure the proper understanding, maintenance, and modification of the software by future team members.
To learn more about particularly click on the link below:
brainly.com/question/7500468
#SPJ11
While in the Current View command group for notes, which view options do you have available? Check all that apply.
Answers
Answer: A, B, C (is this for a Microsoft class?)
Explanation: Edge
Answer:
Icon
Note list
Last 7 days
Explanation:
Help!!! Photography class!! ASP
Which of the following represents aperture priority mode?
Select all that apply.
Α.
The photographer needs to select the value of aperture manually.
B.
The camera determines the value of aperture automatically.
С
The camera determines the value of shutter speed automatically.
D
The photographer needs to select the value of shutter speed manually.
Answers
Answer:
D.
Explanation:
Typically represented by a capital A (or sometimes Av, short for Aperture Value) on the camera mode dial, aperture priority allows the photographer to dial in this specific exposure setting—the ƒ-stop—and asks the camera to calculate the correct corresponding shutter speed in the instant before the shutter is released.
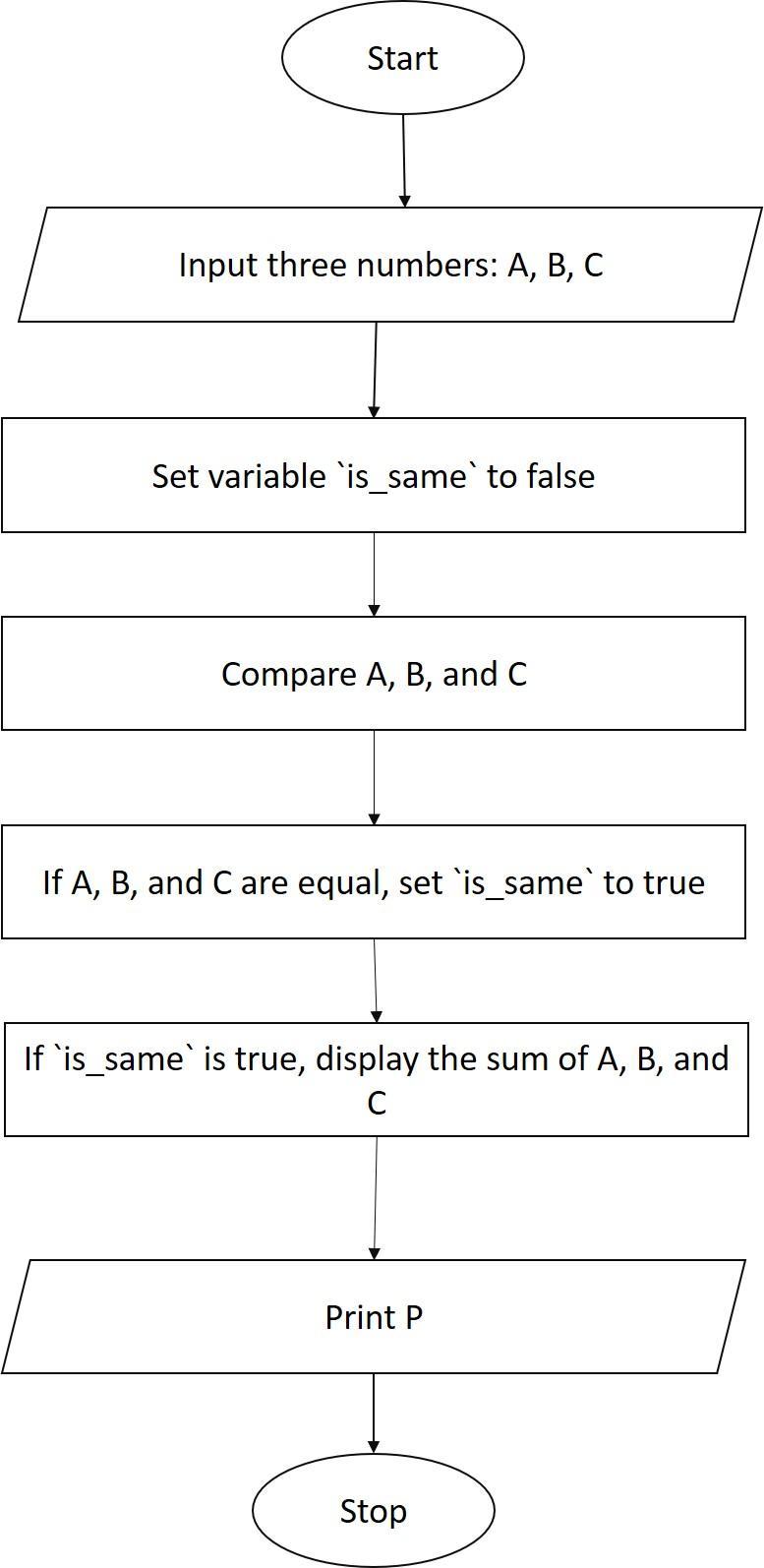
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
You have recently joined in an academic programme to learn more about
programming. You have learnt a few programmes. Your teacher has now given you a
number of tasks to complete.
a) Explain the concept of an algorithm and describe common algorithmic
techniques and solutions.
b)Create a flowchart from the following algorithm.
Step 1: Input VALUE1, VALUE2
Step 2: if (VALUE1 > VALUE2) then
MAX VALUE1
else
MAX VALUE2
endif
Step 3: Print “The largest value is”, MAX
Answers
The concept of an algorithm simply refers to the procedure that is used in problem-solving.
The description of the common algorithmic techniques and solutions are:
Brute-force or exhaustive search.Divide and Conquer.Greedy Algorithms.Dynamic Programming.Branch and Bound Algorithm.Randomized Algorithm.Backtracking.The sample flowchart:START
Input
VALUE1,VALUE2
is
VALUE1>VALUE2
If yes
MAX VALUE1
If no
MAX VALUE2
“The largest value is”, MAX
STOP
Read more about flowcharts here:
https://brainly.com/question/6532130
#SPJ1
What is a software routine that collects information about the devices operation?
Answers
Network management agent is a software routine that collects information about a device’s operations.
Network management is a process that monitors, configures, and manages network performance. As network complexity grows its ability to operate effectively depends upon the quality of network management. A network management agent is software that collects information from the network, network devices like routers and switches can also be used to access information.
Some benefits of effective network management include network visibility, performance optimization, and downtime detection. Network management is very important to ensure service delivery, reliability, and overall performance.
You can learn more about network management at
https://brainly.com/question/27961985
#SPJ4
Which of these is an opinion about cloud computing?
Businesses use the cloud to streamline operations
Resources on the cloud can be accessed by multiple users
Cloud storage is safer than storing it in local servers
Some have concerns about security and privacy in the cloud
Answers
"Some have concerns about security and privacy in the cloud" is an opinion about cloud computing.
The statement "Some have concerns about security and privacy in the cloud" is an opinion because it expresses a personal belief or judgement about the safety and privacy of cloud computing. While it is true that there are concerns about security and privacy in the cloud, it is not a fact that applies universally to all users and situations. Some users may find cloud storage to be just as safe or even safer than storing data in local servers, while others may have experienced security breaches or data loss in the cloud. Therefore, it is important to weigh the pros and cons of cloud computing and make an informed decision based on individual needs and circumstances.
Learn more about cloud computing: https://brainly.com/question/29846688
#SPJ11