you select a text frame on your page and choose object > arrange > send to back. however, it still appears on top of the graphics. what might be the reason?
Answers
The reason behind the text frame still appearing on the top of the graphics is The objects are on two different layers.
What does an InDesign text frame do?The sections in the InDesign document where text is placed are called text frames. Select the text tool from the Tools panel, then drag a rectangular shape into the page to create a text frame. The text frame can be sized and moved as needed.
What distinguishes a text frame from a graphic frame?When you choose an image to utilize File > Place, click (or drag), and place it on a blank area of your page, InDesign makes a graphic frame around the image. Frames for text You can convert another type of frame, which I'll talk about in a bit, but the only way to create an empty text frame is to drag with the Type tool.
To know more about the text frames visit:
https://brainly.com/question/14751990
#SPJ4
Related Questions
(ii) Explain briefly about B-MAC protocol. In what scenario it is best?
Answers
B-MAC is a MAC (Medium Access Control) protocol, which is used in the Wireless Sensor Network (WSN) to provide energy-efficient communication. It is specifically designed for sensor nodes with low-power batteries.
(ii)
The B-MAC protocol is based on the CSMA (Carrier Sense Multiple Access) method, in which the nodes access the channel after checking its availability.
Following are the essential features of the B-MAC protocol:
Energy Efficient Communication Low Latency Duty CyclingThe B-MAC protocol is most suitable for scenarios where energy-efficient communication is required. It is ideal for wireless sensor networks where the devices need to operate on low power batteries for extended periods of time.
It is also beneficial for applications where low latency communication is required, such as monitoring critical infrastructures like dams, bridges, and railway tracks.
Moreover, the B-MAC protocol is suitable for applications that need to communicate infrequently, and the devices can sleep for longer duration to save energy.
To learn more about MAC: https://brainly.com/question/13267309
#SPJ11
When the S and R inputs are both 0, both outputs go to a logical 1. This is called a ___________ for the flip-flop.
Answers
When the S and R inputs are both 0, both outputs go to a logical 1. This is called a **set-up condition** for the flip-flop.
In digital electronics, a set-up condition is a state in which a flip-flop's inputs are arranged to produce a particular output. In the case of an SR flip-flop, when both the S and R inputs are set to 0, the flip-flop enters a set-up condition, which causes both the Q and Q' outputs to go to a logical 1 state. This is an unstable condition, and the flip-flop will remain in this state until one of the inputs changes. If both inputs are then changed to 1 at the same time, it will cause the flip-flop to enter an invalid state, known as a "race" condition. Therefore, care must be taken when using SR flip-flops to ensure that set-up and race conditions are avoided, and the circuit operates correctly.
Learn more about S and R inputs here:
https://brainly.com/question/30247845
#SPJ11
steps in how to locate information on a website
Answers
Answer:
here you go!
Explanation:
1. Choose a website that you may have already heard of before (Wikipedia, Britannica)
2. You can go on that website and search for the specific thing you want
3. If nothing pops up you can just find a different website, but be careful for bots/hackers
4. Go on said website and look up for the specific thing u need to look up.
5. Once you find it (if you do) Read it thoroughly (it'll help later on)
6. Then go and check multiple websites
7. If the websites say similar things as the original website then it's probably a goof bout' of infomation
8. If the websites all have different opinions It's safe to say don't use that information.
Hope this helps!!!!
describe how to construct the period period dataset in words. how does the code block above accomplish this? please write your answer in this markdown box. add comments to the code block above.next we use statsmodels to fit a discrete time hazard model to explore the effects of the risk rating on the hazard of reincarceration. we will leave the baseline hazard fully flexible.
Answers
The code block above creates a dataset that records the time of reincarceration for each individual in the dataset. It does this by creating a 'time' column that stores the time since the individual was released from prison and a 'status' column that records whether the individual has been reincarcerated.
What is Dataset?A dataset is a collection of data, usually presented in tabular form. It may include data from a variety of sources, such as a database, text files, spreadsheets, and more. A dataset can be used for a wide range of tasks, such as data analysis, machine learning, and predictive modeling.
To know more about Dataset
https://brainly.com/question/518894
#SPJ4
write a statement that calls the recursive function backwards alphabet() with input starting letter. sample output with input: 'f' f e d c b a
Answers
Using the knowledge in computational language in python it is possible to write a code that write a statement that calls the recursive function backwards alphabet() with input starting letter.
Writting the code:def backwards_alphabet(n):
if ord(n) == 97:
return n
else:
return n + backwards_alphabet(ord(n-1))
See more about python at brainly.com/question/12975450
#SPJ1

User inserts 10 numbers. Write a program that will show if there are more positive or negative numbers among the entered numbers.
Answers
Here is a basic program that I wrote. This will check how many positive/negative numbers are in the table and then prints the amount..
Using Python
# list of numbers
list1 = [10, -21, 4, -45, 66, -93, 1]
pos_count, neg_count = 0, 0
# iterating each number in list
for num in list1:
# checking condition
if num >= 0:
pos_count += 1
else:
neg_count += 1
print("Positive numbers: ", pos_count)
print("Negative numbers: ", neg_count)
Question 5 (5 points)
(01.03 MC)
When programming dictionaries in Python?
Answers
When programming dictionaries in Python, you should use curly braces {} to enclose the key-value pairs. The key-value pairs are separated by a colon, and each pair is separated by a comma.
In Python, dictionaries are an important data type that allow you to store key-value pairs. To create a dictionary, you use curly braces {} to enclose the key-value pairs. Each key-value pair is separated by a colon, and each pair is separated by a comma.
For example, here is how you would create a dictionary that stores the names of students and their corresponding grades:
```python
grades = {'Alice': 90, 'Bob': 85, 'Charlie': 80}
```
In this example, 'Alice', 'Bob', and 'Charlie' are the keys, and 90, 85, and 80 are the values.
You can access the values in a dictionary by referencing the key. For example, to get the grade for 'Alice', you would write:
```python
grades['Alice']
```
This would return the value 90.
You can also add new key-value pairs to a dictionary or modify existing ones by assigning a value to a key:
```python
grades['David'] = 95
grades['Charlie'] = 82
```
In this example, we added a new key-value pair for 'David' with a value of 95, and we modified the value for 'Charlie' to be 82.
Overall, dictionaries are a powerful tool in Python that allow you to store and manipulate key-value pairs.
Learn more about Python: https://brainly.com/question/30427047
#SPJ11
what are the characteristics of review site
Answers
- Web 2.0 techniques: Review sites may use Web 2.0 techniques to gather reviews from site users or may employ professional writers to author reviews on the topic of concern for the site
- Self-selection bias: Most review sites make little or no attempt to restrict postings, or to verify the information in the reviews. Critics point out that positive reviews are sometimes written by the businesses or individuals being reviewed, while negative reviews may be written by competitors, disgruntled employees, or anyone with a grudge against the business being reviewed. Some merchants also offer incentives for customers to review their products favorably, which skews reviews in their favor
- Reviewer characteristics: Understanding online reviewer characteristics has become important, as such an understanding can help to identify the characteristics of trustworthy reviews. Some of the characteristics that have been studied include valence, rationality, and source
- Content characteristics: The content characteristics of online consumer reviews can make them more useful to readers. Some of the content characteristics that have been studied include the tone of the review, the level of detail, and the relevance of the review to the reader's needs
- Successful owner responses: Successful owner responses to reviews can help to improve the reputation of a business. Some of the characteristics of successful owner responses include being prompt, personalized, and professional
Monica is teaching herself to paint. What web resource would be the most helpful
Answers
Answer:
Video Tutorial
Explanation:
The others don’t make sense.
Answer: video tutorial
Java Coding help please this is from a beginner's class(PLEASE HELP)
Prior to completing a challenge, insert a COMMENT with the appropriate number.

Answers
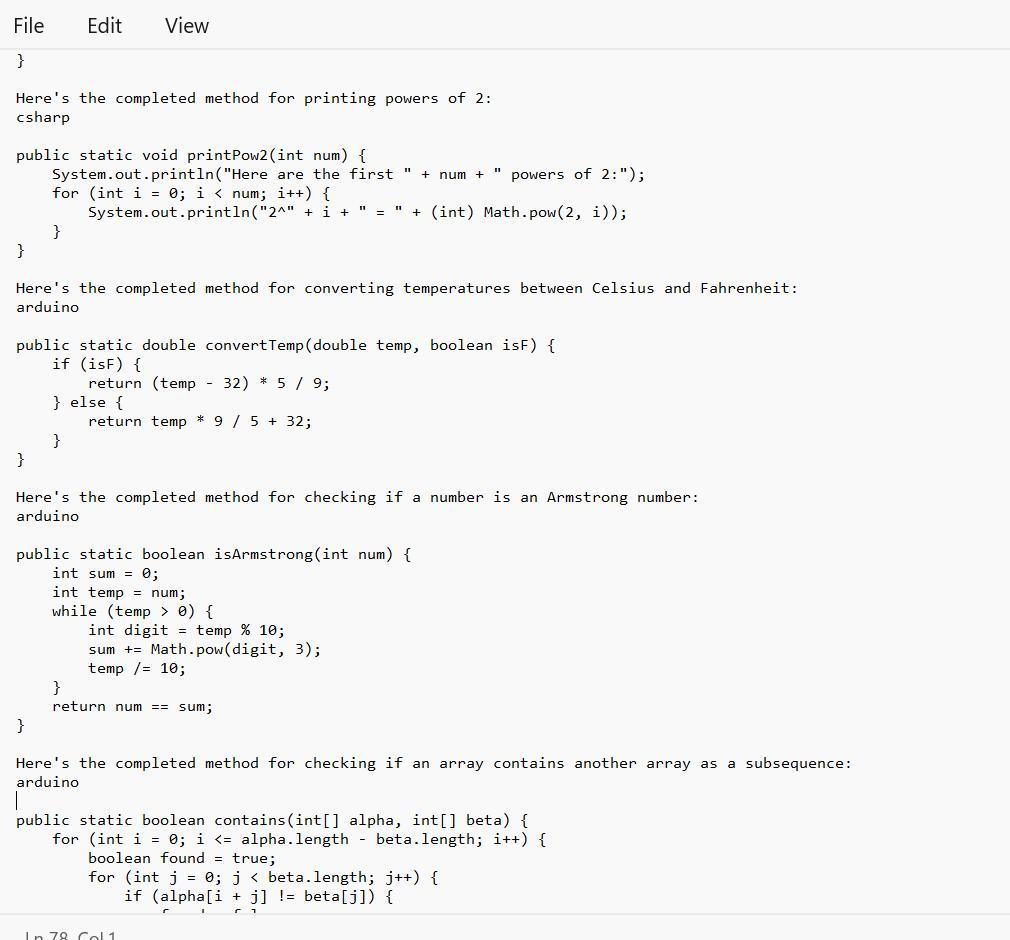
Given in the images are the completed method that one can be able to use for a linear search on an array:
What is the Java Coding?The given text provides several programming code that bear completing the work of different styles.
Note tnat Each system has a specific set of conditions that need to be met in order to give the anticipated affair.
Therefore, code range from simple codes similar as performing a direct hunt on an array or publishing a board with a given size and pattern, to more complex codes similar as checking if one array contains another array in a successive and ordered manner.
Learn more about Java Coding from
https://brainly.com/question/18554491
#SPJ1
See text below
1) Complete the method: public static int simpleSearch(int[] nums, int value), that performs a linear (sequential) search on the array parameter, and returns the index of the first occurrence the of value parameter. Return -1 if value doesn't exist in nums.
simpleSearch(new int[] {8, 6, 7, 4, 3, 6, 5), 7) >>> 2
//2 is index of the value 7
2) Complete the method: public static void squareBoard(int num), that prints an num by num board with a '#' character in every position.
squareBoard(2) >>>
3) Complete the method: public static void checkerBoard(int num), that prints an num by num board with a '# character in every position in a 'checkerboard' fashion.
checker Board(3) >>>
4) Complete the method: public static void printPow2(int num), that prints num powers of 2 (including O), given the supplied number. Use String concatenation to print like this:
//with a call of printPow2(4):
Here are the first 4 powers of 2:
2^8 = 1
2^1 = 2
2^2 = 4
238
5) Complete the method: public static double convertTemp/double temp, boolean isF), that performs a Celsius to Fahrenheit conversion (and vice versa) when called. The parameter isF will be supplied as true if temp is in Fahrenheit.
6) Complete the method: public static boolean isArmstrong(int num), that returns true if the supplied number is an "Armstrong number". An Armstrong number is a number for which the sum of the cubes of its digits is equal to the number itself. Modulus and integer division will help.
IsArmstrong (371) >>> true //3*3*3+7*7*7+ 1*1*1 == 371
7) Difficulty level HIGH: Complete the method: public static boolean contains(int[] alpha, int[] beta). that returns true if the sequence of elements in beta appear anywhere in alpha. They must appear consecutively and in the same order. You'll need nested loops for this.
contains(new int[] {1, 2, 1, 2, 3), new int[] {1, 2, 3}) >>> true
contains (new int[] 1, 2, 1, 2, 3, 1), new intf (1, 1, 3, 1)) >>> false


according to _______, "responding within 24 hours is a good rule of thumb," in regard to handling negative reviews on social media.
Answers
According to experts in the field of social media management and customer service, responding within 24 hours is a good rule of thumb when handling negative reviews on social media. This is because social media users tend to expect a prompt response to their comments, questions, and concerns, especially when they are voicing a complaint or expressing dissatisfaction with a product or service.
By responding quickly and professionally to negative reviews, companies can demonstrate that they take customer feedback seriously and are committed to providing a high level of customer service.
However, it is also important to remember that responding quickly does not mean responding impulsively or defensively. It is important to take the time to read and fully understand the negative review, empathize with the customer's perspective, and formulate a thoughtful, constructive response. This can involve acknowledging the customer's concern, apologizing for any inconvenience or frustration they may have experienced, and offering a potential solution or next steps.
By taking a customer-centric approach to social media management, companies can not only address negative reviews in a timely and effective manner but also build stronger relationships with their customers over time. This can help to improve brand reputation, increase customer loyalty, and ultimately drive business growth and success.
To know more about management visit:
https://brainly.com/question/32216947
#SPJ11
assume that you have compiled a program named calc average and that there is a file named my data.txt, which contains the necessary input data that will be processed by the program. what would be the command that you need to enter at the command prompt to execute the program, with input redirected from the my data.txt file?
Answers
The command to execute the program "calc average" with input redirected from the "my data.txt" file would be:
./calc_average < my_data.txt
The "<" operator redirects the contents of the "my_data.txt" file as the input for the "calc_average" program.
What is meant by command?
Command can be described as direct with special authority or prerogative; order. A command is a directive to a computer program to perform a specific task, in computing, a command is a directive to a computer program to perform a specific task. It may be issued via a command-line interface, such as a shell, or as input to a network service as part of a network protocol, or as an event in a graphical user interface triggered by the user selecting an option in a menu.. Command may be issued via a command-line interface, such as a shell, or as input to a network service as part of a network protocol, or as an event in a graphical user interface triggered by the user selecting an option in a menu.
Learn more about command, in here https://brainly.com/question/30319932
#SPJ4
The use of+=, -=, and *= are all examples of what type of operators? a. overloaded mathematic operators b. augmented assignment operators c. extended arithmetic operators d. protracted assignment operators
Answers
Augmented assignment operators are +=, -=, and *=. Arithmetic can be performed on a variable and the results can then be assigned back to the original variable using augmented assignment operators.
What does the *= operator mean?The *= operator initially multiplies the expression's value by the variable or property's value, which is on the right side of the operator (on the left-hand side of the operator). After then, the operator assigns the operation's outcome to the variable or property.
What does an augmented assignment operator look like?A statement where an operator takes a variable as one of its inputs and then assigns the result back to the same variable is typically replaced by an augmented assignment. A straightforward illustration is x += 1, which is expanded to x = x + 1.
to know more about operators here:
brainly.com/question/29949119
#SPJ1
Your boss has approved your project team’s recommendations to increase productivity (select a specific organization that is applicable to you, if desired). Many of your recommendations will result in significant change to the organization. You have been tasked to lead the change effort.
As part of your plan you want to build momentum by generating short-term wins. What is not a characteristic of a short-term win?
Answers
Answer:
A. Visible to senior leadership, but not lower levels of the organization.
Explanation:
John Kotter explained that short-term wins are clear, real, unambiguous, tangible, and visible to all. Short-term wins involve goals that do not take a long time before they are completed and this makes the results clearly seen by all.
So when I plan to build momentum by generating short-term wins, the results should be visible to all in the organization and not just to senior leadership.
which of the following type of attack uses password cracking software to generate every possible combination of letters, numerals, and symbols.
a. entropy
b. m assive
c. dictionary
d. brute force
Answers
Brute force attack uses password cracking software to generate every possible combination of letters, numerals, and symbols in order to find the correct password. It systematically tries all possible combinations until the correct one is discovered. This method is time-consuming and resource-intensive but is effective against weak and poorly chosen passwords.
A brute force attack involves systematically attempting every possible combination of characters until the correct password is found. It does not rely on any specific patterns or known information about the target. This method is typically employed when there is no prior knowledge or specific clues about the password. Brute force attacks can be very time-consuming and resource-intensive, especially for longer and more complex passwords, as the number of possible combinations increases exponentially. However, they can be successful against weak passwords that lack complexity or length. Advanced password cracking software and high-performance computing systems may be utilized to speed up the process.
Learn more about software here:
https://brainly.com/question/985406
#SPJ11
What is the predicate ___ for the following query and its result?
?- ____(f(a,b),F,A).
A = 2
F = f
A. args/3
B. assert/1
C. atom/1
D. clause/2
E. call/1
F. findall/3
G. functor/3
H. ground/1
I. op/3
J. retract/1
K. var/1
L. =, \=
M. ==, \==
Answers
The predicate for the given query is G. functor/3.
The query is:
?- functor(f(a,b),F,A).
The result is:
A = 2
F = f
Explanation:
The functor/3 predicate has three arguments: Term, Functor, and Arity. In this query, Term is f(a,b), Functor is F, and Arity is A. functor/3 extracts the functor (function symbol) and arity (number of arguments) of a given term. In this case, f is the functor and 2 is the arity (since f has two arguments: a and b). Therefore, the values of F and A are f and 2, respectively.
To know more about Functor:
https://brainly.com/question/27958883
#SPJ11
The selling and administrative expense budget of Ohio Corporation is based on budgeted unit sales, which are 4,600 units for March. The variable selling and administrative expense is $7.30 per unit. The budgeted fixed selling and administrative expense is $51,980 per month, which includes depreciation (a noncash expense) of $6,440 per month. The remainder of the fixed selling and administrative expense represents current cash flows. The total cash disbursements for selling and administrative expenses on the March selling and administrative expense budget should be:
Answers
The total cash disbursements for selling and administrative expenses on the March budget should amount to $79,120.
What is the total cash disbursement for selling and administrative expenses on the March budget, considering variable and fixed expenses?To calculate the total cash disbursements for selling and administrative expenses on the March budget, we need to consider both the variable and fixed expenses.
Variable selling and administrative expense per unit: $7.30
Budgeted unit sales for March: 4,600 units
Variable expense for March: $7.30 per unit * 4,600 units = $33,580
Fixed selling and administrative expense (excluding depreciation): $51,980 - $6,440 = $45,540
Total cash disbursements for March selling and administrative expenses: Variable expense + Fixed expense
Total cash disbursements = $33,580 + $45,540 = $79,120
Therefore, the total cash disbursements for selling and administrative expenses on the March budget should be $79,120.
Learn more about disbursements
brainly.com/question/31214335
#SPJ11
Which of the following is hardware or software that monitors and controls network traffic to prevent security breaches?
O trojan horse
O firewall
O anti-malware
O keylogger
Need answer now!!!!!
Answers
Answer:
Firewall
Explanation:
A trojan horse and keylogger are types of malware. While an anti-malware software may come with a firewall built in, the firewall is still the thing monitoring network traffic.
a DVD looks just like a CD, but it holds less information true or false
Answers
Answer:
False
Explanation:
A DVD can hold more information because it is basically a double sided CD where it gets information on both sides whereas on a CD, you only read one side. On CDs, people can put stuff like stickers or whatever on one side while the important side is uncovered.
a) Show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent by using series of logical equivalence. (3 marks)
b) Determine whether (p∧q)→(p∨q) is a tautology. (4 marks)
c) With the aid of a truth table, convert the expression (¬p→q)∧(¬q∨r) into Disjunction Normal Form (DNF) (5 marks)
Answers
a) To show that ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent, we can use a series of logical equivalences:
¬(p∨(¬p∧q)) (De Morgan's Law)
≡ ¬p∧¬(¬p∧q) (De Morgan's Law)
≡ ¬p∧(p∨¬q) (Double Negation)
≡ (¬p∧p)∨(¬p∧¬q) (Distributive Law)
≡ False∨(¬p∧¬q) (Negation Law)
≡ ¬p∧¬q (Identity Law)
Therefore, ¬(p∨(¬p∧q)) and ¬p∧¬q are logically equivalent.
b) To determine whether (p∧q)→(p∨q) is a tautology, we can construct a truth table:
p | q | (p∧q) | (p∨q) | (p∧q)→(p∨q)
-----------------------------------
T | T | T | T | T
T | F | F | T | T
F | T | F | T | T
F | F | F | F | T
Since the last column of the truth table always evaluates to true, (p∧q)→(p∨q) is a tautology.
c) Truth table for the expression (¬p→q)∧(¬q∨r):
p | q | r | ¬p | ¬p→q | ¬q | ¬q∨r | (¬p→q)∧(¬q∨r)
--------------------------------------------------
T | T | T | F | T | F | T | T
T | T | F | F | T | F | F | F
T | F | T | F | F | T | T | F
T | F | F | F | F | T | T | F
F | T | T | T | T | F | T | T
F | T | F | T | T | F | F | F
F | F | T | T | T | T | T | T
F | F | F | T | T | T | T | T
Converting the truth table into Disjunction Normal Form (DNF):
(¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r)
Therefore, the expression (¬p→q)∧(¬q∨r) in Disjunction Normal Form (DNF) is (¬p∧¬q∧r)∨(¬p∧q∧¬r)∨(p∧¬q∧r)∨(p∧¬q∧¬r)∨(p∧q∧r).
To know more about DNF, visit
https://brainly.com/question/31326308
#SPJ11
BLANK refer to system maintenance activities such as backups and file management.
Remote desktop service
Network management services
Network encryption
BLANK provide features to prevent unauthorized access to the network.
Security services
File replication services
Printing services
Answers
Network management services
Second answer:
Security services
which component of the oracle cloud infrastucre identiy and access management service can be used for controlling access to resources for authentuicated pricakpls
Answers
Oracle Cloud Infrastructure Identity and Access Management (IAM) service component that can be utilized for controlling access to resources for authenticated principals is called policy.What is Oracle Cloud Infrastructure Identity and Access Management (IAM) service?Oracle Cloud Infrastructure Identity and Access Management (IAM) service allows managing users, groups, compartments, and policies in Oracle Cloud Infrastructure (OCI).
It offers a centralized, cloud-based way to authorize and authenticate applications and services to access your cloud resources. It provides the following features:Identity ManagementAccess ManagementIntegration and Federation PolicyComponents of Oracle Cloud Infrastructure Identity and Access Management (IAM) ServiceThere are three components of Oracle Cloud Infrastructure Identity and Access Management (IAM) Service:UsersGroupsPoliciesThe Policies component of the Oracle Cloud Infrastructure Identity and Access Management (IAM) Service is utilized for controlling access to resources for authenticated principals.Explanation:The Policies component of the Oracle Cloud Infrastructure Identity and Access Management (IAM) Service is utilized for controlling access to resources for authenticated principals. You can utilize policies to enforce compliance, to grant or restrict access to resources, to organize users, and to support auditing and monitoring activities.In Oracle Cloud Infrastructure (OCI), policies allow you to specify who can access a resource and what actions they can perform on that resource. Policies use groups and compartments to simplify administration and policy management. A policy consists of one or more policy statements, each of which specifies one or more resource types, actions, and who can access that resource and how.
Policy statements are written in Oracle Cloud Infrastructure's policy language and are applied to IAM users, groups, and compartments.Policies are composed of policy statements. Each policy statement defines one or more resource types, actions, and who can perform those actions. A policy statement can be applied to an IAM user, group, or compartment. Policies make it easy to centralize and enforce permissions across multiple services and resources.
To know more about Identity and Access Management (IAM) service visit :
https://brainly.com/question/32200175
#SPJ11
which devices is not found in the CPU
Answers
The devices that is not found in the CPU is printer. The correct option is D.
What is CPU?A central processing unit, sometimes known as a CPU, is a piece of electronic equipment that executes commands from software, enabling a computer or other device to carry out its functions.
The part of a computer that obtains and executes instructions is called the central processing unit (CPU).
A CAD system's CPU can be thought of as its brain. It is made up of a control unit, a number of registers, and an arithmetic and logic unit (ALU). The term "processor" is frequently used to refer to the CPU.
The size, speed, sophistication, and price of a printer varies. It is a device that receives text and graphic output from a computer and transmits the information to paper.
Thus, the correct option is D.
For more details regarding CPU, visit:
https://brainly.com/question/16254036
#SPJ6
Your question seems incomplete, the missing options are:
a. ALU
b. Control Unit
c. Instruction register
d. Printer
What has happened to the audience in the digital era of third and fourth screens?
Answers
The audience in the digital era of third and fourth screens has become more fragmented and harder to reach.
With the rise of smartphones and tablets, people are no longer just consuming content on traditional TV screens or computers. This has led to a fragmentation of the audience across multiple platforms and devices, making it harder for content creators and advertisers to reach them. Additionally, the ability to personalize and target content has made it more difficult to capture the attention of the audience, who now have an abundance of choices and the ability to quickly switch to other content.
As a result, the audience has become more elusive and harder to engage, and content creators and
must adapt to this new reality.
Learn more about audience here:
https://brainly.com/question/30435704
#SPJ11
A security administrator is conducting a penetration test on a network. She connects a notebook system to a mirror port on a network switch. She then uses a packet sniffer to monitor network traffic to try and determine which operating systems are running on network hosts. Which process did the administrator use in the penetration test in this scenario
Answers
Answer:
Active fingerprinting
Explanation:
Right now, I'm banned, I'm trying to see where it says the time until I'm unbanned, but I can't find it. Does anyone know where it is?
Answers
Answer:
Well it may be on your profile but other than that it will take you 1 month to get your account unbanned
Answer:
It should be next to your username. It depends on how long the administrators wanna ban you. It can be from 15 minutes to 48 hours.
Explanation:
Which of the following enables a DBMS to reduce data redundancy and inconsistency?
A) Ability to enforce referential integrity
B) Ability to couple program and data
C) Use of a data dictionary
D) Ability to create two-dimensional tables
E) Ability to minimize isolated files with repeated data
Answers
DBMS (Database Management System) reduces data redundancy and inconsistency through the following methods:1. Use of a data dictionary
The database dictionary stores the attributes of data elements and the associations between them, such as data types, default values, relationships, and constraints, enabling the DBMS to handle data consistently across the database.2. Ability to enforce referential integrityReferential integrity is a database concept that ensures that related tables in a relational database stay synchronized when records are inserted, deleted, or updated.
Referential integrity constraints assist in enforcing business rules that define how data should be related.3. Ability to minimize isolated files with repeated dataData redundancy can be minimized by using the DBMS to create two-dimensional tables, such as relational databases. Isolated files that include repeated data can be replaced by a relational database with tables for related data sets.
To know more about redundancy visit:
https://brainly.com/question/13266841
#SPJ11
a class that contains a pointer to another object of the same class is said to be a. a link pointer b.self-referential c. a traversal d. a collection
Answers
The correct option is a and B. A self-referential class is a class that contains a pointer to another object of the same class. This pointer is known as a link pointer.
A link pointer can be used for traversing the structure of the class and accessing each of the objects contained within. This type of class is commonly used for data structures such as linked lists and binary trees. Link pointers can be thought of as the building blocks of a data structure. A link pointer is a reference to another object, which can be traversed to access data contained within the class. By traversing the link pointer, each of the elements contained within the class can be accessed.
Link pointers can also be used to create collections of objects. These collections can then be accessed and manipulated using the link pointers. For example, a linked list could be created with a link pointer that contains a collection of objects that are linked together. Link pointers are a powerful tool in programming and can be used to create complex data structures. Link pointers can also be used to reduce the amount of code necessary to create and manipulate data structures.
You can learn more about the self-referential class at: brainly.com/question/13898701
#SPJ11
You want to develop a system that will allow employers to develop better punctuality habits for employees. The employer doesn’t want employees to come either too early or too late. Employees clock in their times. Your employer has told you that coming in 10 minutes late or early is within tolerable limits.
Develop a sliding scale that uses linguistic variables. This scale helps employers determine seven levels, starting from extremely early to extremely late and just-on-time right in the middle.
Answers
Answer:
To develop a system that will allow employers to develop better punctuality habits for employees, a sliding scale can be used that uses linguistic variables. This scale would help employers to determine seven levels for punctuality, starting from extremely early to extremely late and just-on-time right in the middle. The employer has stated that coming in 10 minutes early or late is within tolerable limits, so the scale could be set up with the following levels:
• Extremely Early: 0-5 minutes • Early: 6-10 minutes • On Time: 11-15 minutes • Late: 16-20 minutes • Very Late: 21-25 minutes • Extremely Late: 26-30 minutes • Unacceptable: 31+ minutes.
This scale will help employers to determine acceptable levels of punctuality for employees, and ensure that they are not coming in too early or too late.
Explanation:
see above
What is output by the following code? Select all that apply.
c = 2
while (c < 12):
print (c)
c = c + 3
Group of answer choices
3
4
6
7
9
2
10
5
12
8
1
11
Answers
Note that the output of the code given above is: 5.
What is the explanation of the above analogy?Given that the value of c is 2
2 < 12 (true statement)
c = c + 3
i.e, c = 2+3
Therefore, the answer is 5.
It is to be noted that in computer programming, computer code is a set of instructions or a set of rules expressed in a specific programming language (i.e., the source code). It is also the name given to the source code after it has been compiled and is ready to execute on a computer (i.e., the object code).
Learn more about codes:
https://brainly.com/question/28848004
#SPJ1