you are preparing to give a presentation at a client's location using your mobile device and a large screen tv. you have successfully connected to the company's guest wi-fi network, and you tap the screen mirroring option on your device but cannot locate an available tv, monitor, or projector. the previous presenter finished her presentation a few minutes earlier and had no issues using the tv. Which of the following is the most likely reason for this behavior?
a. The mobile device is on a different Wi-Fi network than the TV.
b. The large screen TV is connected to the wrong network segment.
c. The brightness control on the large screen TV has been set too low.
d. The mobile device does not support display mirroring.
Answers
a. The mobile device is on a different Wi-Fi network than the TV.- the following is the most likely reason for this behavior.
What exactly is a WiFi network?Instead of using cables, a wireless or WiFi network connects your devices, including computers, printers, and cellphones, to the Internet and one another. Within a given range in all directions, any wirelessly enabled device, such as a laptop or tablet, may pick up the WiFi signal.
What are WiFi's three different varieties, and why is it named WiFi?There are just three options for wireless in your house or place of business: G, N, or AC. Wi-Fi was the new technology's WECA moniker. (Wi-Fi is not an acronym for "wireless fidelity"; it was coined by a marketing company for WECA and selected for its catchy sound and similarity to "hi-fi" [high-fidelity].
To know more about WiFi Network visit
brainly.com/question/14015791
#SPJ4
Related Questions
Briefly explain the risks we face in augmented reality,iot and AI
Answers
Augmented Reality (AR), Internet of Things (IoT), and Artificial Intelligence (AI) are all cutting-edge technologies that offer many benefits, but they also come with certain risks. Some of the main risks associated with these technologies include:
Augmented Reality: One of the main risks associated with AR is that it can distract users from their real-world surroundings, potentially leading to accidents or injuries. Additionally, AR can also be used to spread misinformation or to manipulate people's perceptions of the world.
Internet of Things: The IoT is vulnerable to cyber attacks, as the interconnected nature of these devices makes them an attractive target for hackers. A security breach of an IoT device can lead to the loss of sensitive information or to unauthorized control of the device.
Artificial Intelligence: AI systems can be trained on biased data, which can lead to biased decisions, particularly in sensitive areas such as criminal justice or hiring. Additionally, AI can be used to automate certain tasks, which can displace jobs, and its usage can be used for malicious intent like spreading misinformation, hacking and surveillance.
It's important to keep in mind that these are not exhaustive lists, and there are other risks associated with these technologies. It is crucial to be aware of these risks and to take the appropriate measures to mitigate them.
Look at the following Polygon class:
public class Polygon
{
private int numSides;
public Polygon()
{
numSides = 0;
}
public void setNumSides(int sides)
{
numSides = sides;
}
public int getNumSides()
{
return numSides;
}
}
Write a public class named Triangle that is a subclass of the Polygon class. The Triangle class should have the following members:
a private int field named base
a private int field named height
a constructor that assigns 3 to the numSides field and assigns 0 to the base and height fields
a public void method named setBase that accepts an int argument. The argument's value should be assigned to the base field
a public void method named setHeight that accepts an int argument. The argument's value should be assigned to the height field
a public method named getBase that returns the value of the base field
a public method named getHeight that returns the value of the height field
a public method named getArea that returns the area of the triangle as a double.
Use the following formula to calculate the area: Area = (height * base) / 2.0
Answers
Answer: This is the complete program for this with the highest level of explanation.
This program is written in the Java programming language.
The name of this file is Triangle.java
public class Triangle extends Polygon {
// private fields to store the dimensions of the triangle
private int base;
private int height;
// constructor to initialize the fields and set the number of sides
public Triangle() {
// call the setNumSides method inherited from Polygon to set the number of sides to 3
setNumSides(3);
// initialize base and height to 0
base = 0;
height = 0;
}
// setter method for the base field
public void setBase(int b) {
base = b;
}
// setter method for the height field
public void setHeight(int h) {
height = h;
}
// getter method for the base field
public int getBase() {
return base;
}
// getter method for the height field
public int getHeight() {
return height;
}
// method to calculate and return the area of the triangle
public double getArea() {
// calculate the area using the formula (base * height) / 2.0
return 0.5 * base * height;
}
}
The name of this file is Polygon.java
public class Polygon {
private int numSides;
public Polygon() {
numSides = 0;
}
public void setNumSides(int sides) {
if (sides == 3) {
numSides = sides;
} else {
System.out.println("Error: Invalid number of sides for a triangle");
}
}
public int getNumSides() {
return numSides;
}
}
The name of this file is Main.java
import java.util.Scanner;
public class Main {
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
// Create a new Polygon object and set its number of sides to 3
Polygon polygon = new Polygon();
polygon.setNumSides(3);
// Print out the number of sides of the polygon
System.out.println("Number of sides: " + polygon.getNumSides());
// Obtain input from user for the base and height of a triangle
System.out.print("Enter the base of the triangle: ");
int base = scanner.nextInt();
System.out.print("Enter the height of the triangle: ");
int height = scanner.nextInt();
// Create a new Triangle object and set its base and height
Triangle triangle = new Triangle();
triangle.setBase(base);
triangle.setHeight(height);
// Calculate the area of the triangle and print it out
double area = triangle.getArea();
System.out.println("Area of the triangle: " + area);
}
}
This will be the output generated by this program.
Number of sides: 3
Enter the base of the triangle: 10
Enter the height of the triangle: 15
Area of the triangle: 75.0
Step 2/2
This is the complete explanation for this program.
This Triangle class is a subclass of the Polygon class, which means it inherits all of the methods and variables of the Polygon class.
This Triangle class has two private instance variables: base and height. These variables are used to store the dimensions of the triangle.
This Triangle class has a constructor that initializes the number of sides to 3 and sets the base and height variables to 0.
This Triangle class has four public methods:
a. This set Base method, which sets the value of the base variable to the given value.
b. This set Height method, which sets the value of the height variable to the given value.
c. This get Base method, which returns the value of the base variable.
d. The get Height method, which returns the value of the height variable.
Explanation:
This triangle class has a public get Area method that calculates the area of the triangle using the formula (base * height) / 2.0 and returns the result as a double.
Final answer
This is the image of the output generated by this code.
This is the image of the final output.
This is the complete summary of the entire program.
This program defines two classes: Polygon and Triangle. The Polygon class has one private instance variable, num Sides, and three public methods: Polygon(), set Num Sides(int sides), and get Num Sides (). The Triangle class is a subclass of the Polygon class and features two private instance variables, base and height, as well as six public methods: Triangle (), set Base(int base), set Height(int height), get Base (), get Height (), and get Area ().
The Main class is used to build a Triangle class object and to gather user input for the triangle's base and height. The set Base and set Height methods are used to set the values of the base and height instance variables, respectively.
Answer:
public class Triangle extends Polygon {
private int base;
private int height;
public Triangle() {
setNumSides(3);
base = 0;
height = 0;
}
public void setBase(int baseValue) {
base = baseValue;
}
public void setHeight(int heightValue) {
height = heightValue;
}
public int getBase() {
return base;
}
public int getHeight() {
return height;
}
public double getArea() {
double area = (height * base) / 2.0;
return area;
}
}
Hope This Helps
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Consider the following classes.
public class Dog
{
/* code */
}
public class Dachshund extends Dog
{
/* code */
}
Assuming that each class has a default constructor, which of the following are valid declarations?
I. Dog sadie = new Dachshund();
II. Dachshund aldo = new Dachshund();
III. Dachshund doug = new Dog();
Group of answer choices
I only
II only
III only
I and II only
II and III only
Answers
Assuming that each class has a default constructor, Only I and II are valid declarations.
What is default constructor?In object-oriented programming, a constructor is a special method that is called when an object is created. It initializes the object's data members and prepares the object for use.
Dog sadie = new Dachshund();
This is valid because Dachshund is a subclass of Dog, so a Dachshund object can be assigned to a Dog variable.
Dachshund aldo = new Dachshund();
This is also valid because it creates a Dachshund object and assigns it to a Dachshund variable.
Dachshund doug = new Dog();
This is not valid because a Dog object cannot be assigned to a Dachshund variable. While a Dachshund is a Dog, a Dog is not necessarily a Dachshund.
Thus, only I and II are valid declarations.
For more details regarding default constructor, visit:
https://brainly.com/question/31053149
#SPJ3
Complete the procedure for creating and sending an email message by selecting the correct term from each drop-
down menu.
1. On the Home tab, click the
button
2. In the To field, type the email address of each recipient
3. In the Subject field, type a relevant subject line for the email,
4. In the message body area, type your message content and click
Answers
Answer:
1. Compose
4. Send
Explanation:
PROCEDURE FOR CREATING AND SENDING AN EMAIL MESSAGE
1. On the Home tab, click the compose button
2. In the To field, type the email address of each recipient
3. In the Subject field, type a relevant subject line for the email,
4. In the message body area, type your message content and click send.
Answer:
New Email
Send
Explanation:
Write a usability report of 2000 words for Clikcasnap.com
The report should be presented using an industrial usability report template and cover the following contents:
an executive summary to highlight key findings and recommendations;
a context of use analysis;
a detailed usability evaluation using cognitive walkthrough;
a detailed app navigation evaluation covering screen-level and overall navigation using think aloud;
design recommendations for all the issues identified.
Answers
The usability evaluation of Clikcasnap.com was conducted using a cognitive walkthrough and think aloud protocol to identify usability issues in the web application.
The analysis revealed several usability issues related to information architecture, navigation, and user interface design, which negatively impact the user experience.
The key recommendations include improving the navigation and information architecture, simplifying the user interface, and optimizing the search functionality to enhance the usability and user experience of the website.
Context of Use Analysis:
Clikcasnap.com is a web application that allows users to find, book, and pay for photography services online. The website is primarily aimed at individual consumers who want to hire a photographer for events, such as weddings, birthdays, and corporate events.
The users are expected to have basic computer skills and internet knowledge. The website caters to a diverse audience, including people of different ages, genders, and cultural backgrounds.
The website is designed to be used on desktops, laptops, and mobile devices, with a responsive design that adapts to the screen size of the device.
The context of use analysis revealed that the website has a clear purpose, but the navigation and user interface design are confusing and cluttered, which makes it challenging for users to find the information they need.
The website's primary task is to help users find photographers, but the information architecture does not support this task efficiently, leading to a poor user experience.
Detailed Usability Evaluation using Cognitive Walkthrough:
The usability evaluation of Clikcasnap.com using cognitive walkthrough identified the following usability issues:
1. Poor Information Architecture: The website's information architecture is poorly organized, making it challenging for users to find the information they need. The website lacks a clear and intuitive hierarchy that guides users to the content they need. The website's navigation structure is confusing, with too many options that overlap and are not well-organized.
2. Inconsistent Design: The website has an inconsistent design, with different layouts, fonts, and colors used across different pages. This inconsistency leads to confusion and hampers the user experience.
3. Cluttered User Interface: The user interface design is cluttered, with too many elements on the screen, making it challenging for users to focus on the task at hand.
4. Poor Search Functionality: The search functionality on the website is limited and does not provide users with relevant results.
5. Inefficient Navigation: The navigation on the website is inefficient, with too many clicks required to reach the desired content. Users often have to navigate through multiple pages to find the information they need.
Detailed App Navigation Evaluation covering Screen-level and Overall Navigation using Think Aloud:
The navigation evaluation of Clikcasnap.com using the think-aloud protocol identified the following usability issues:
1. Confusing Navigation: The navigation structure is confusing and does not follow a clear hierarchy. Users often find it challenging to navigate to the desired content, resulting in frustration.
2. Overlapping Content: The content on the website overlaps, with too many links and options that make it difficult to distinguish between different sections.
3. Inconsistent Layout: The layout of the website is inconsistent, with different pages having different layouts, fonts, and colors.
4. Unclear Labels: The labels on the website are often unclear, making it difficult for users to understand the purpose of each link.
Usability evaluation of Clikcasnap.com using cognitive walkthrough and think aloud protocols revealed several issues related to information architecture, navigation, and user interface design, requiring design recommendations to enhance the user experience.
For more questions on usability, visit:
https://brainly.com/question/24289772
#SPJ11
Explain working principle of computer.
Answers
Explanation:
The working principle of the computer system. Computers do the work primarily in the machine and we can not see, a control center that converts the information data input to output. This control center, called the central processing unit (CPU), How Computers Work is a very complex system.
hope it is helpful to you



HELPPPPP 20 POINTS CORRECT ANSWER GETS BRAINLIEST
sorry wrong amount of points ;-;

Answers
Answer:
C
Explanation:
Answer:
it will be B or D not sure but IMA go with B
who is know as father of computer
Answers
Answer:
Babbage is sometimes referred to as "father of computing." The International Charles Babbage Society (later the Charles Babbage Institute) took his name to honor his intellectual contributions and their relation to modern computers.
Answer: Charles Babbage
Before inserting a preformatted table of contents, what must you do first?
apply heading styles to text
update the table of contents
navigate to the Review tab and the Table of Contents grouping
navigate to the Insert Table of Contents dialog box
Answers
Answer: apply heading styles to text.
Explanation:
Assume a 2^20 byte memory:
a) What are the lowest and highest addresses if memory is byte-addressable?
b) What are the lowest and highest addresses if memory is word-addressable, assuming a 16-bit word?
c) What are the lowest and highest addresses if memory is word-addressable, assuming a 32-bit word?
Answers
a) Lowest address: 0, Highest address: (2^20) - 1. b) Lowest address: 0, Highest address: ((2^20) / 2) - 1. c) Lowest address: 0, Highest address: ((2^20) / 4) - 1.
a) If memory is byte-addressable, the lowest address would be 0 and the highest address would be (2^20) - 1.
This is because each byte in the memory requires a unique address, and since there are 2^20 bytes in total, the highest address would be one less than the total number of bytes.
b) If memory is word-addressable with a 16-bit word, each word would consist of 2 bytes.
Therefore, the lowest address would be 0 (representing the first word), and the highest address would be ((2^20) / 2) - 1.
This is because the total number of words is equal to the total number of bytes divided by 2.
Subtracting 1 gives us the highest address, as the addresses are zero-based.
c) If memory is word-addressable with a 32-bit word, each word would consist of 4 bytes.
In this case, the lowest address would still be 0 (representing the first word), and the highest address would be ((2^20) / 4) - 1.
Similar to the previous case, the total number of words is equal to the total number of bytes divided by 4.
Subtracting 1 gives us the highest address.
For more questions on address
https://brainly.com/question/30273425
#SPJ8
What is your biggest concern when it comes to purchasing a used phone or laptop?
Answers
Answer:
quality
Explanation:
if i know about the phone or laptop quality and quantity then i can know which is important if i buy.
i can give you example by laptop. For example i want to get buy laptop. i should know about the quantity and quality. then if i choose quantity i can buy so many laptops if they are more than 3 laptops and i get it in low price. then i take it and i try to open the laptops for some other thing to do but they cant opened so it means it has lowest quality.
and if i choose the quality. may be i can't buy more than 1 laptops but the qulaity of the laptops is high so when i open the laptop it opened
Notequality is the superiority or the quality level of a things.
quantity is the abundance or the quantity level of a thing
Let's say set1 contains the following values: 1, 2, 3. set2 contains 3, 4, 5. Please name the difference between set1 and set2:
a. 4,5
b. 3
c. None of the above / below.
d. 1,2,3,4,5
e. 1,2
Answers
Answer:
c
Explanation:
None of the above /below
initial tokens (initial state) of your system should reflect at least 2
scooters and 2 commuters.
Answers
The initial tokens (initial state) of the system would reflect at least 2 scooters and 2 commuters. The tokens would include:
Scooter1: This token would represent the first E-Scooter in the system, and would have properties such as current location, battery level, and whether it is currently in use or not.Scooter2: This token would represent the second E-Scooter in the system, and would have properties similar to Scooter1.Commuter1: This token would represent the first registered commuter in the system, and would have properties such as name, registered payment details, and current ride information (if any).Commuter2: This token would represent the second registered commuter in the system, and would have properties similar to Commuter1.What are the tokens about?The system would have transition functions that would allow for the reservation and release of scooters, computation of ride fees, and automatic debit of fees from the commuter's registered payment details.
Therefore, To increase the complexity, the system could include additional tokens such as additional scooters and commuters, as well as more advanced features such as real-time tracking of scooters and commuters, integration with a mapping system, and the ability for commuters to rate their ride and leave feedback.
Learn more about tokens from
https://brainly.com/question/29034547
#SPJ1
See full question below
Scenario: You are tasked with the development of an E-Scooter ride-share system. It allows registered commuters to approach an idle E-Scooter and reserve it, following which they use the E-Scooter to commute a certain distance (that is not known prior to use). Finally, after the commuter reaches their destination, they end the ride, which prompts an automatic
computation of the ride fees. which is automatically debited using the
commuters registered payment details.
Task 2.
The initial tokens (initial state) of your system should reflect at least 2
scooters and 2 commuters. More generally → Please ensure a level of
complexity similar to the CPN model example given in the lecture.
Write a program that repeatedly takes integers from the user as long as he
wants to input. The program then, shows a summary of the inputs. The summary
should include: 1) minimum of the inputs, 2) maximum of the inputs, 3) total Even
inputs , 4) total Odd inputs, 5) Average of Even numbers, 6) Average of Odd
numbers, and 7) the total Average
Answers
Answer:
Written in Python:
evens = 0
odds = 0
oddtotal = 0
eventotal = 0
total = 0
mylst = []
tryag = "Y"
while tryag == "Y" or tryag == "y":
num = int(input("Input: "))
mylst.append(num)
tryag = input("Another Input (Y/y): ")
mylst.sort()
print("Minimum: "+str(mylst[0]))
print("Maximum: "+str(mylst[-1]))
for i in mylst:
total = total + i
if i%2 == 0:
evens = evens + 1
eventotal = eventotal + i
else:
odds = odds + 1
oddtotal = oddtotal + i
print("Evens: "+str(evens))
print("Odds: "+str(odds))
print("Even Average: "+str(eventotal/evens))
print("Odd Average: "+str(oddtotal/odds))
print("Total Average: "+str(total/(evens+odds)))
Explanation:
The following lines initializes useful variables to 0
evens = 0
odds = 0
oddtotal = 0
eventotal = 0
total = 0
This declares an empty list
mylst = []
tryag = "Y"
This is repeated until user stops the loop by entering strings other than y or Y
while tryag == "Y" or tryag == "y":
This prompts user for input
num = int(input("Input: "))
User input is appended to the list
mylst.append(num)
This prompts user to try again the loop
tryag = input("Another Input (Y/y): ")
This sorts the list from small to large
mylst.sort()
This prints 1. The minimum
print("Minimum: "+str(mylst[0]))
This prints 2. The maximum
print("Maximum: "+str(mylst[-1]))
The following iterates through the list
for i in mylst:
This calculates the total
total = total + i
This checks for even entry
if i%2 == 0:
This counts the number of even entries
evens = evens + 1
This sums the even entries
eventotal = eventotal + i
else:
This counts the number of odd entries
odds = odds + 1
This sums the odd entries
oddtotal = oddtotal + i
This prints 3. Sum of Even entries
print("Evens: "+str(evens))
This prints 4. Sum of Odd entries
print("Odds: "+str(odds))
This prints 5. Average of Even entries
print("Even Average: "+str(eventotal/evens))
This prints 6. Average of Odd entries
print("Odd Average: "+str(oddtotal/odds))
This prints 7. Total Average
print("Total Average: "+str(total/(evens+odds)))
When the U.S. dollar goes up against the British Pound, it could be a result of _____.
poor government relations
an increase in the trade deficit
speculation on Wall Street
trouble in the Leadership of the US Department of Treasury
Answers
Answer:When the US dollar goes up against the British Pound, it can be a result of B. an increase in the trade deficit.
Trade deficit refers to the fact that a particular country is importing far more than it is exporting - therefore it is losing money. As a result of that, the currency of that country can change - foreign money can rise, whereas domestic currency can plummet.
Answer:
When the U.S. dollar goes up against the British Pound, it could be a result of an increase in the trade deficit.
Explanation:
hope this helps
how would you feel if the next version of windows becomes SaaS, and why?
Answers
If the next version of Windows becomes SaaS, SaaS or Software as a Service is a software delivery model in which software is hosted on the cloud and provided to users over the internet.
Moving Windows to a SaaS model means that Microsoft will continue to deliver updates and new features through a subscription-based service rather than through major new versions of the operating system.
This approach has its own advantages and challenges.
Benefits of the SaaS model for Windows:
Continuous Updates: Users receive regular updates and new features, ensuring they always have access to the latest improvements and security patches.
Flexibility: Subscriptions offer different tiers and plans so users can choose the features they need and customize their experience.
Lower upfront costs: A subscription model could reduce the upfront cost of purchasing Windows, making Windows more accessible to a wider audience.
Improved security: Continuous updates can help address vulnerabilities and security threats more rapidly, enhancing overall system security.
Challenges and concerns with a SaaS model for Windows:
Dependency on internet connectivity: Users would need a stable internet connection to receive updates and access features, which may not be ideal for those in areas with limited or unreliable internet access.
Privacy and data concerns: Users might have concerns about data collection, privacy, and the potential for their usage patterns to be monitored in a subscription-based model.
Cost considerations: While a subscription model may provide flexibility, some users may find it less cost-effective in the long run compared to purchasing a traditional license for Windows.
Compatibility issues: Continuous updates could introduce compatibility challenges for legacy software and hardware that may not be updated or supported in the new model.
Whether you view Windows' migration to a SaaS model as a positive or negative is ultimately determined by your personal perspective and specific implementations by Microsoft.
Cost: SaaS is a subscription-based model, which means users have to pay recurring fees to use the software.
They have to rely on the provider to update, maintain, and improve the software.To sum up, I would feel hesitant about using SaaS if the next version of Windows becomes SaaS.
For more questions on Software as a Service:
https://brainly.com/question/23864885
#SPJ8
Draw the resulting image on the grub below using the following rules: it
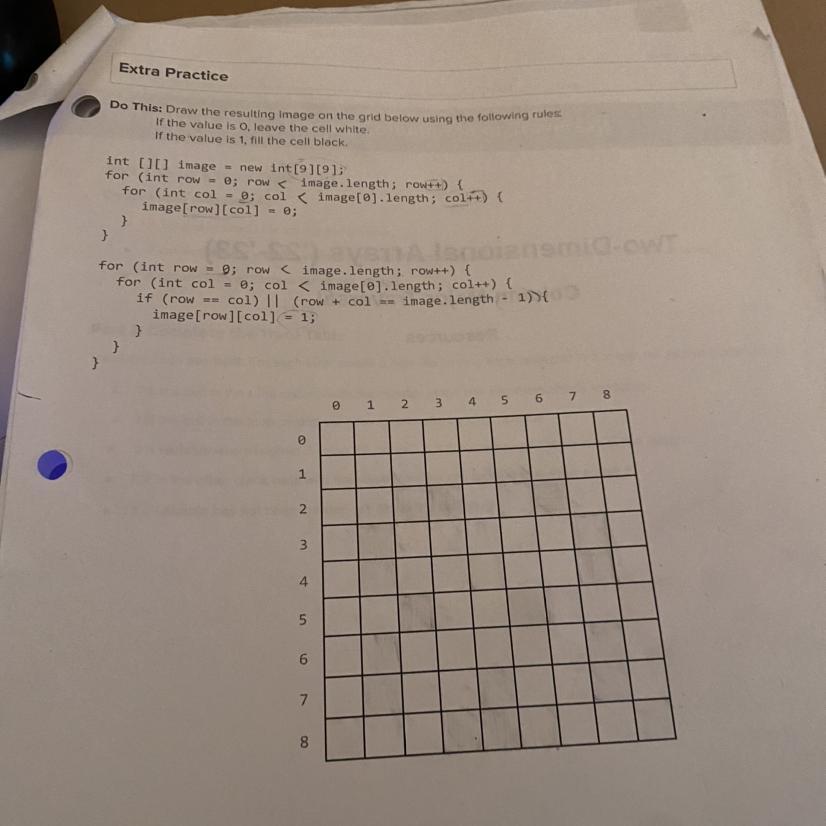
Answers
Explanation:
I just answered this.
I cannot draw here.
but it will mark all dots, where row number = column number.
and all dots, where row number + column number = 8.
this will create a giant X.
the 2 lines go from (0, 8) to (8, 0), and from (0, 0) to (8, 8) with (4, 4) being the central intersection point.
Which tasks fall under WBS?
Kevin’s WBS for a project
Project manager Kevin has made a project plan for a software development project. a) Kevin calls a meeting with his team members to further discuss project requirements.
In the meeting they decide to b) break down deliverables into subdeliverables with detailed explanations.
After listing the tasks and milestones, the project team c) decides to enter the duration for each task. The entire list of tasks follows a logical sequence which aids in scheduling.
Answers
Answer:
Amongst them are a risk management plan, quality plan, procurement plan, communications plan, staffing plan, and a work breakdown schedule plan. The work breakdown schedule includes the start and completion dates for all tasks, activities, and deliverables defined in the WBS.
A technician wants to move a file called widget.txt from the current directory to /home/fred,
Which of the following commands would the technician use?
ed widget.ext /home/fred
move widget.xt/home/fred
my widget.ext /home/fred
Op widget.txt /home/fred
Answers
The command that the technician will use to carry out the moving of the file is; Option C; mv widget.txt /home/fred
Linux CommandsIn Linux, If we want to move files, we make use of the "mv" command which is quite similar to the cp command. The only difference being that with mv command, the file is physically moved from one place to another, whereas with cp, it is being duplicated.
Since the technician wants to move the filled called widget.txt from the current directory to /home/fred, then he will make use of the "mv" command.
Read more about LINUX at; https://brainly.com/question/25480553
What does the acronym SMART stand for
Answers
Specific, Measurable, Achievable, Relevant, Time-bound
List and briefly describe the major types of system in organization?
Answers
1. operational-level systems
2. management-level systems
3. strategic-level systems
1. operational-level systems = support operational activities by keeping track of the elementary activities and transactions of the organization, such as assigning employees to tasks and recording the number of hours they work, or placing a purchase order. Operational activities are short-term in nature.
2. management-level systems = Management-level systems serve the monitoring, controlling, decision-making, and administrative activities of middle managers. Management-level systems typically provide periodic reports rather than instant information on operations.
3. strategic-level systems = Strategic-level systems (SLS) are information systems at the strategic level of an organization designed to address unstructured decision-making.
The major types of systems in the organization are:
Operational Level systemManagement Level systemStrategic Level systemThe classification of information systems based on organization levels is determined by the specialties and interests in some functional areas.
Operational-level systems assist operational managers by tracking the organization's basic operations and transactions, as well as the movement of materials in a factory. The primary function of systems at this level is to respond to routine inquiries and to record the movement of transactions via the organization. In general, information must be easily accessible, up to date, and accurate.
Management-level systems support middle managers' observing, regulating decision-making, and administrative operations. The primary question tackled by such systems is:
Are things running smoothly?Management-level systems usually give regular reports rather than real-time operational data.
Strategic-level systems assist senior management in addressing strategic challenges and long-drawn patterns, both inside the organization and in the external world. Their primary focus is harmonizing external adjustments in the environment with current organizational capacity.
Therefore, from the above explanation, we can conclude that we've fully understood the types of systems in the organization of information systems.
Learn more about information systems here:
https://brainly.com/question/13299592?referrer=searchResults
Considering the following part of the database to keep track of students and their marks for the courses that they follow.
Student(sid, sname, year)
Registered(sid, cid, mark, grade)
Course(cid, cname, no_credit, deptid)
Which of the following sequence of operations would list the names of students who have not registered for any course?
Answers
To list the names of students who have not registered for any course, we can use the following sequence of operations:
Retrieve all student IDs (sid) from the Student table.Retrieve all student IDs (sid) from the Registered table.Perform a LEFT JOIN between the two sets of student IDs, filtering out the matching records.Retrieve the names (sname) of the students from the resulting set.How can we list the names of students who have not registered for any course?To obtain the names of students who have not registered for any course, we need to compare the student IDs between the Student and Registered tables.
By performing a LEFT JOIN and filtering out the matching records, we will be left with the students who have not registered for any course. Finally, we can retrieve their names from the resulting set to list them.
Read more about sequence of operations
brainly.com/question/550188
#SPJ1
The following diagram shows a close-up of the surface of a CD. Which of the following would allow for more data to be stored on a CD?

Answers
The overlapping pits making more room for data to be stored on a CD.
How is data stored on a CD?A CD is burned by merely laying a pattern of pits and lands across the polycarbonate layer. On the other hand, the burning process must be exceedingly precise because the data must be precisely encoded on such a small scale. The data on a CD is written (burned) using a CD burner. It includes a "Write Laser," a moving laser that looks a lot like a CD player. The Write Laser, which is more potent than the "Read Laser," can change the surface of the CD rather than just reflecting the laser light off of it. The Write Laser bounces a light beam over the surface of the CD during the burning process, creating a series of pits in accordance with the data (binary values).
Learn more about Compact disk here:
brainly.com/question/14555020
#SPJ1
The role of ICT In government.
Answers
Answer:Communication between a government and its citizens can happen in real-time since messages are delivered instantaneously.
E-Government uses ICT for the development of more efficient and more economical government.
Explanation:
Software Security Integration involves which attributes? Select the correct option(s) and click submit. Estimation of Software Security Efforts & Software Security Budget Requirements Estimation of Software Security Efforts & Sign Off Criteria Definition Software Security Budget Requirements & Sign Off Criteria Definition Software Security Effort Estimation and Budget Requirements, Identification of teams to perform reviews & Defining Sign Off Criteria Submit
Answers
Software Security Integration concerns which attributes to Estimation of Software Security Efforts & Software Security Budget Requirements
What is software security requirements?
A security requirement is a statement of needed security functionality that provides one of many different security properties of software is being satisfied. Security requirements are emanated from industry standards, applicable laws, and a history of past exposures.
What is software safety courses?The types of security software for business websites contain computer antivirus, network security, SaaS security, content control system, e-commerce software, payment gateway software, content delivery network, bot comfort, and monitoring tool.
To learn more about security requirement, refer
https://brainly.com/question/2818423
#SPJ9
Write a program named Twitter that accepts a user’s message and determines whether it is short enough for a social networking service that does not accept messages of more than 140 characters.
If the message is more than 140 characters, output The message is too long. Otherwise output The message is okay.
Answers
Explanation:
It's a very easy one, Liev:
using System;
class Twitter
{
static void Main()
{
Console.WriteLine("Enter your message");
Console.WriteLine();
string message = Console.ReadLine();
Console.WriteLine();
if (message.Length <= 140)
{
Console.WriteLine("Yes, it's short enough for Twitter");
}
else
{
Console.WriteLine("Sorry, it's too long for Twitter");
}
Console.ReadKey();
}
}
how was this training content covered your task?
Answers
A way to use training content to cover our task is to incorporate relevant information and skills from the training into the task.
How can training content be used?By incorporating our relevance from training content into task, we can apply what they have learned in a practical setting. For example, if we receive training on effective communication skills, they can incorporate those skills into a task that involves communicating with others.
When an individual has received training on project management, they can use the techniques and tools learned during the training to manage a project effectively. Therefore, it can help to reinforce the learning and improve their performance.
Read more about training content
brainly.com/question/942454
#SPJ1
State three modules in HansaWorld and briefly describe what each is used for. (6)
2. With an example, explain what settings are used for. (3)
3. What is Personal Desktop and why is it good to use? Mention two ways in which an
entry can be deleted from the personal desktop. (6)
4. Describe how you invalidate a record in HansaWorld (3)
5. Briefly explain what specification, paste special and report windows are used for. (6)
6. How many reports can you have on the screen at once? How many reports does
HansaWorld have? (4)
7. Describe any two views of the Calendar and how you can open them (4)
8. Describe three (3) ways in which records can be attached to Mails. (6)
9. Describe the basic SALES PROCESS where there is no stock involved and how the
same is implemented in HansaWorld. (12)
Answers
1. We can see here that the three modules in HansaWorld and their brief descriptions:
AccountingInventoryCRM2. We can deduce that settings are actually used in HansaWorld for used for configuring the system to meet specific business requirements.
What is HansaWorld?It is important for us to understand what HansaWorld is all about. We can see here that HansaWorld is actually known to be an enterprise resource planning (ERP) system that provides integrated software solutions for businesses.
3. Personal Desktop is actually known to be a feature in HansaWorld. It allows users to create a personalized workspace within the system.
It can help users to increase their productivity and efficiency.
4. To actually invalidate a record in HansaWorld, there steps to take.
5. We can deduce here that specification, paste special and report windows help users to actually manage data and generate report.
6. There are factors that play in in determining the amount of reports generated.
7. The Calendar on HansaWorld is used to view upcoming events. There is the Day View and there is the Month View.
8. We can see that in attaching records, HansaWorld allows you to:
Drag and drop.Insert linkUse the Mail Merge FunctionLearn more about report on https://brainly.com/question/26177190
#SPJ1
New trends and tools are continuously emerging in the field of digital media. Discuss the advantages of these trends and tools for a digital media professional.
Answers
Answer:
There are multiple ways of being recognized and known, if new trends are emerging, people will try and get the most out of it so they can be recognized. Another reason is that people can try new things, it could be a new hobby, a new liking or just something they might want to share meaning it gets more attention
Explanation: