Work made for hire. If an employer asks an independent designer to create an illustration, the copyright to that artwork is owned by the employer. true or false?
Answers
Answer:
False
Explanation:
On the basis of the designer being "independent", the artworks copyright remains with the designer. Being independent requires contractual transfer of copyright in the event that its created for another person.
Related Questions
Can someone tell me how to get rid of the the orange with blue and orange on the status bar
Please and thank you
Picture above

Answers
Answer:
Explanation:
i'm not sure how tho
Question # 2 Multiple Choice Do you think it is acceptable to copy and paste material from a web page into a term paper?
Yes, because information on the internet is free for everyone to use.
Yes, because information on the internet is free for everyone to use.
Yes, if you paste of where you got it from but do not quote it.
Yes, if you paste of where you got it from but do not quote it.
No, because you should not pass other people’s work off as your own.
No, because you should not pass other people’s work off as your own.
No, because you can get sued by the owner of the material.
Answers
Do you think it is acceptable to copy and paste material from a web page into a term paper: No, because you should not pass other people’s work off as your own.
What is plagiarism?Plagiarism simply refers to an act of representing or using an author's literary work, thoughts, ideas, language, or expressions without their consent, permission, acknowledgement or authorization.
This ultimately implies that, plagiarism is an illegal act that involves using another author's intellectual work or copyrighted items word for word without getting an authorization and permission from the original author.
In this context, we can reasonably infer and logically deduce that it is very wrong to copy and paste material from a web source into a term paper without an accurate citation or reference to the original author.
Read more on plagiarism here: brainly.com/question/397668
#SPJ1
Answer:
C. No, because you should not pass other people’s work off as your own.
Explanation:
Three differences between Selecting and Highlighting
Answers
Answer:
highlighting is selecting a text & it turns into a color
selecting is just going over the text with a cursor
Explanation:
Answer:
Selecting an item is simply choosing something. Highlighting is to note important information. Highlighting only takes important details, selecting chooses objects.
you have a table for a membership database that contains the following fields: MemberLatName, MemberFirstName, Street, City, State, ZipCode and intiation fee. there are 75,000records in the table. what indexes would you create for the table, and why would you create these indexes?
Answers
A unique lookup table called an index is used to speed performance
What is lookup function?
Use the lookup and reference function LOOKUP when you need to search a single row or column and find a value from the same position in another row or column. As an example, let's say you have the part number for a car part but don't know how much it costs.
We employ we lookup since?
Use VLOOKUP when you need to search by row in a table or a range. For instance, you could use the employee ID to look up a person's name or the part number to check the price of a car part.
To know more about speed visit:-
https://brainly.com/question/17661499
#SPJ1
5.19 LAB: Countdown until matching digits
PYTHON: Write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.

Answers
Using the knowledge of computational language in python it is possible to write a code that write a program that takes in an integer in the range 11-100 as input. The output is a countdown starting from the integer, and stopping when both output digits are identical.
Writting the code:n = int(input())
if 20 <= n <= 98:
while n % 11 != 0:
print(n)
n -= 1
print(n)
else:
print("Input must be 20-98")
See more about python at brainly.com/question/18502436
#SPJ1

Why is it important to state the insights from your graphic when using the McCandless method?
Answers
When using the McCandless method, it is essential to state the insights from the graphic because it helps ensure effective communication and enhances the understanding of the data being presented.
By explicitly stating the insights derived from the graphic, the audience can grasp the key takeaways without having to interpret the visualization solely based on their own observations.
This ensures that the intended message is conveyed accurately and reduces the chances of misinterpretation or confusion.
Additionally, stating insights provides context and adds meaning to the graphic.
A visualization alone may be visually appealing, but without the accompanying insights, it may be challenging to comprehend the purpose or significance of the displayed data.
Insights serve as a bridge between the visual representation and the underlying information, guiding the audience towards the intended understanding.
Moreover, insights help highlight patterns, trends, or relationships that may not be immediately apparent from the graphic alone.
They act as a guide for the audience, drawing attention to the important aspects of the data and providing a narrative that connects the visual elements.
For more questions on effective communication
https://brainly.com/question/26152499
#SPJ8
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
Which virus is also known as hybrid virus ?
Answers
Answer:
A multipartite virus
Explanation:
Analyze the characteristics of Hypertext Transfer Protocol (HTTP) to determine which statements accurately describe the protocol. (Select two)
A. HTTP is a stateless protocol, and the default port is 80.
B. HTTP offers a secure means of uploading files.
C. HTTP was developed by Netscape to address problems with the lack of security in previous protocols.
D. HTTP communications are not secured.
Answers
The default port for HTTP is 80, and communications over HTTP are not encrypted.
What are HTTP's (Hyper Text Transfer Protocol) fundamental features?Basic HTTP (Hyper Text Transfer Protocol) Characteristics It is the protocol that enables communication between web browsers and servers. It is a protocol for requests and answers. By default, it connects to the secure TCP connections on port 80.
How does the HTTP protocol function? What is it?The protocol is still used often today to access the Internet. How is HTTP implemented? Through the transmission of hypertext messages between clients and servers, HTTP provides users with a method of interacting with web resources like HTML files.
To know more HTTP visit :-
https://brainly.com/question/10663873
#SPJ4
Classify the characteristics as abstract classes or interfaces.
A. Uses the implements keyboard
B. Cannot have subclasses
C. Does not allow static and final variables
D. Can have subclasses
E. Uses the extends keyboard
F. Allows static and final variables

Answers
how would you feel if the next version of windows becomes SaaS, and why?
Answers
If the next version of Windows becomes SaaS, SaaS or Software as a Service is a software delivery model in which software is hosted on the cloud and provided to users over the internet.
Moving Windows to a SaaS model means that Microsoft will continue to deliver updates and new features through a subscription-based service rather than through major new versions of the operating system.
This approach has its own advantages and challenges.
Benefits of the SaaS model for Windows:
Continuous Updates: Users receive regular updates and new features, ensuring they always have access to the latest improvements and security patches.
Flexibility: Subscriptions offer different tiers and plans so users can choose the features they need and customize their experience.
Lower upfront costs: A subscription model could reduce the upfront cost of purchasing Windows, making Windows more accessible to a wider audience.
Improved security: Continuous updates can help address vulnerabilities and security threats more rapidly, enhancing overall system security.
Challenges and concerns with a SaaS model for Windows:
Dependency on internet connectivity: Users would need a stable internet connection to receive updates and access features, which may not be ideal for those in areas with limited or unreliable internet access.
Privacy and data concerns: Users might have concerns about data collection, privacy, and the potential for their usage patterns to be monitored in a subscription-based model.
Cost considerations: While a subscription model may provide flexibility, some users may find it less cost-effective in the long run compared to purchasing a traditional license for Windows.
Compatibility issues: Continuous updates could introduce compatibility challenges for legacy software and hardware that may not be updated or supported in the new model.
Whether you view Windows' migration to a SaaS model as a positive or negative is ultimately determined by your personal perspective and specific implementations by Microsoft.
Cost: SaaS is a subscription-based model, which means users have to pay recurring fees to use the software.
They have to rely on the provider to update, maintain, and improve the software.To sum up, I would feel hesitant about using SaaS if the next version of Windows becomes SaaS.
For more questions on Software as a Service:
https://brainly.com/question/23864885
#SPJ8
How do I fix my mistake in the code, do not give me a bs answer like “I don’t know sorry” if you do not know just move on because I will report it like I have before.

Answers
The problem lies within your if statement. You're using a single equals sign when you should be using two.
if (operation == 1)
Two equal signs is a comparison operator. It checks to see if one value equals another value. In your case, its checking if operation equals 1. But, this only solves half the problem. Operation is a string and you need to compare it to a string.
if (operation == "1")
I hope this helps!
Of the following hard drives, which one is fastest?
a. SATA 6 Gb/s SSD
b. SATA 6 Gb/s 10,000-RPM drive
c. M.2 SSD using a SATA3 interface
d. PCIe NVMe SSD card
Answers
Answer:
D. PCIe NVMe SSD card
Explanation:
PCIe NVMe SSD cards are ludicrously fast even compared to some modern SSD drives today. Some can even average up to 8 GB/s while moving/copying files, though, the price tag is pretty high compared to some other SSD / HDD drives.
What's the full meaning of COBOL,FORTRAN,PL1,dBASE,ALGOL,RRG,APL,LISP,PROLOG,PASCAL in high level programming
Answers
Answer:
this doesn't scare me
Explanation:
COBOL(Common Business-Oriented Language) is a high-level programming language for business applications. It was the first popular language designed to be operating system-agnostic and is still in use in many financial and business applications today
FORTRON(FORmula TRANslation) general-purpose, compiled imperative programming language that is especially suited to numeric computation and scientific computing.
(Programming Language One) procedural, imperative computer programming language developed and published by IBM
dBASE( arbitrary name) was one of the first database management systems for microcomputers
... look mister I got tons of anime to watch
A security administrator is investigating a report that a user is receiving suspicious emails. The user's machine has an old functioning modem installed. Which of the following security concerns need to be identified and mitigated? (Select TWO).
a) Vishing
b) Whaling
c) Spear phishing
d) Pharming
e) War dialing
f) Hoaxing
Answers
Answer:
Spear Phishing and War Dialing
Explanation:
So let's tackle these one at a time.
Vishing is simply any type of message (i.e., email, text, phone call, etc.) that appears to be from a trusted source but is not.
Whaling is simply a spear phishing attack of a high-value target such as a CEO or someone with high-level access at a company.
Spear phishing is simply a targeted phishing attack, usually towards a specific person or group of people. (Phishing attack is simply a social attack to try and gain unauthorized access to a resource).
Pharming is an attack that attempts to redirect website traffic to a fake site.
War dialing is a technique to automatically scan a list of numbers in an area in attempt to search for exposed modems, computers, board systems, or fax machines, in order to breach the network.
Hoaxing is simply a social attack that describes a serious threat in attempts to retrieve unauthorized access or money from a victim. (Think microsoft tech support scams)
Now that we have defined these things, let's identify the possible threats that need to be reported.
(a) Vishing? The sec admin report doesn't mention the source of the message so we cannot associate this one
(b) Whaling? The sec admin report says a user, implying someone not high up in the company, but doesn't say it's not someone high up. This is possible.
(c) Spear phishing? The sec admin report says a user, implying that only this user is being targeted so this is definitely valid.
(d) Pharming? The sec admin report says nothing about site redirection.
(e) War dialing? The sec admin report doesn't say anything about unauthorized scanning; however, it mentions the user has an old functioning modem, so this is possible.
(f) Hoaxing? The sec admin report doesn't mention a pop up in the email or the content of the email so we are uncertain.
Thus with these considerations, the two threats that are identified and need mitigation are Spear phishing and War Dialing/Whaling. Note that we aren't positive of the war dialing or whaling, but a case could be made for either; however, given the modem information, the question seems to indicate war dialing.
which of the following is a part of the database requirements step? database deployment logical modeling database implementation all of the above none of the above
Answers
Conceptual modelling is a phase in the database deployment, logical modelling, and implementation processes.
A conceptual model is a representation of an application that the creators hope consumers will comprehend. Users form an image of how the programme functions in their brains by using it and maybe reading its documentation. The model that users create in their thoughts should ideally resemble the one that the creators intended.
A logical data model defines the organisation of data pieces and the connections between them. The information on how the data will be used is independent of the physical database. A template for the utilised data is provided by the logical data model. The logical data model expands on the concepts of conceptual data modelling by incorporating more details.
Learn more about Logical here:
https://brainly.com/question/14617992
#SPJ4
Explain the derived data types in C language with examples each
Answers
Answer:
Array, pointers, struct, and union are the derived data types.
How could this code be simplified

Answers
Answer:
D
Explanation:
by using for loop because its repeating alot and stuff yk
Physical education is the body's ability to function effectively and efficiently without excessive farigue. TRUE/FALSE
CAN YOU PLEASSSSSSSEEEEEEE
ANSWER THIS
Answers
Answer: True
Explanation:
AP computer science principles:
QUESTION: Every computer has how many bits that it uses when doing numeric floating point decimals?
OPTIONS:
A- a finite number
B- an approximate number
C- an indefinite number
D- an infinite number
Answers
Note that in Computer Science principles, the number of bits that a computer has when doing numeric floating point decimals is: "a Finite number" (Option A)
What is Decimal Floating Point?Both a description and operations on decimal floating-point numbers are referred to as decimal floating-point arithmetic. Working directly with decimal fractions allows you to avoid rounding mistakes that are common when converting between decimal fractions and binary fractions.
The benefit of decimal floating-point representation over decimal fixed-point and integer representation is that it can accommodate a significantly broader range of values.
Learn more about Floating Points:
https://brainly.com/question/22237704
#SPJ1
Assume we need to implement the following sequence of Instructions with
forwarding by using a 5 stages pipeline.
sub x12, x11, x13
and x8 x12, x15
or x9,x16.x12
For clock cycle 5, what are the control values of A and B (the two outputs of
"Forwarding unit") respectively?
(The control values for the forwarding multiplexors
are shown in the following table)
MUX Control Source
A/B - 00
ID/EX
W/B - 10
EX/MEM
Answers
Answer:
0 0 1 0
Explanation:
sub X12, X11, X13 and x8, X12, X15 or X9, x16, x12 For clock cycle 5, what are the control values of A and B.
QUESTION 5 OF 30
Burnout can happen quickly when
working with multiple sysadmins
working overtime
working as the sole sysadmin
Answers
Answer:
Burnout can happen quickly when working with multiple sysadmins, working overtime, or working as the sole sysadmin.
Explanation:
You are a software engineering consultant and have been called in by the vice-president for finance of a corporation that manufactures tires and sells them via its large chain of retail outlets. She wants your organization to build a product that will monitor the company's stock, starting with the purchasing of the raw materials and keeping track of the tires as they are manufactured, distributed to the individual stores, and sold to customers.
a) What criteria would you use in selecting a life-cycle model for the project?
b) Which team structure you would like to prefer? Give sound reasoning.
Answers
The criteria that I would use in selecting a life is the use of scale of the product, also the vagueness of the different requirements, as well as time given and all of the possible risks.
The team structure that I would like to prefer is the use of the agile model.
Why use the agile model?Iterative and incremental development are combined in the agile methodology. The product is broken down into smaller components using the agile methodology, and each component is supplied to the user in an interactive way.
These product components are then separated into time jobs before being implemented. The organization can build the product swiftly thanks to this model. The agile model reduces the resources needed for product development.
Therefore, As a result, criteria can be changed quickly to meet the demands of the customer, the company is able to create a product with all the required features.
Learn more about agile model from
https://brainly.com/question/23661838
#SPJ1
Write the SQL queries that accomplish the following tasks in the HAFH Realty Company Property Management Database:
Answers
The complete question is:
Write the SQL queries that accomplish the following tasks in the HAFH Realty Company Property Management Database:
a. Display the SMemberID and SMemberName for all staff members.
b. Display the CCID, CCName, and CCIndustry for all corporate clients.
c. Display the BuildingID, BNoOfFloors, and the manager’s MFName and MLName for all buildings.
d. Display the MFName, MLName, MSalary, MBDate, and number of buildings that the manager manages for all managers with a salary less than $55,000.
e. Display the BuildingID and AptNo, for all apartments leased by the corporate client WindyCT.
f. Display the InsID and InsName for all inspectors whose next inspection is scheduled after 1-JAN-2014. Do not display the same information more than once.
g. Display the SMemberID and SMemberName of staff members cleaning apartments rented by corporate clients whose corporate location is Chicago. Do not display the same information more than once.
h. Display the CCName of the client and the CCName of the client who referred it, for every client referred by a client in the music industry.
i. Display the BuildingID, AptNo, and ANoOfBedrooms for all apartments that are not leased.
Also a schema of the HAFH database is attached.
Answer:
Using SQL's SELECT, FROM, WHERE syntax, find below the queries for each question.
a.
SELECT SMemberID , SMemberName
FROM staffmember
b.
SELECT CCID, CCName, CCIndustry
FROM corpclient
c.
SELECT b.BuildingID, b.BNoOfFloors, m.MFName, m.MLName
FROM building b, manager m
WHERE b.ManagerID = m.ManagerID
d.
SELECT m.MFName, m.MLName, m.MSalary, m.MBDate, count(*) as buildings
FROM building b, manager m
WHERE m.MSalary<55000
AND b.ManagerID = m.ManagerID
GROUP BY m.ManagerID
e.
SELECT b.BuildingID, a.AptNo
FROM building b, apartment a, corpclient c
WHERE c.CCName = "WindyCT"
AND c.CCID = a.CCID
AND a.BuildingID = b.BuildingID
f.
SELECT DISTINCT i.InsID, i.InsName
FROM inspector i, inspecting x
WHERE i.InsID = x.InsID
AND x.DateNext > "2014-01-01"
g.
SELECT DISTINCT s.SMemberID, s.SMemberName
FROM staffmember s, cleaning c, apartment a, corpclient cc
WHERE s.SmemberID = c.SmemberID
AND c.AptNo = a.AptNo
AND a.CCID = cc.CCID
AND cc.CCLocation = "Chicago"
h.
SELECT cc1.CCName, cc2.CCName
FROM corpclient cc1, corpclient cc2
WHERE cc1.CCIDReferencedBy = cc2.CCID
AND cc2.CCIndustry = "Music"
i.
SELECT a.BuildingID, a.AptNo, a.ANoOfBedrooms
FROM apartment a
WHERE a.CCID NOT IN (SELECT c.CCID FROM corpclient c)

While setting up annetwork segment you want to check the functionality cable before putting connectors on them. You also want to meaure the termination point or damange in cable which tool used
Answers
A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
What is network Segementation?Segmentation works by regulating the network's traffic flow. The term "network segmentation" should not be confused with "microsegmentation," which limits east-west communication at the workload level in order to lower an organization's network attack surface.
Despite having some uses, microsegmentation should not be confused with standard network segmentation.
A network is divided into several zones via network segmentation, and each zone or segment is independently managed. To regulate what traffic is allowed to pass through the segment and what is not, traffic protocols must be used.
Dedicated hardware is used to create network segments that are walled off from one another and only permit users with the proper credentials to access the system.
Therefore, A network is divided into several parts (subnets) using network segmentation, which creates smaller, independent networks for each segment.
To learn more about network, refer to the link:
https://brainly.com/question/15088389
#SPJ1
Which components often account for most of the downloaded bytes on a web page?
O Fonts
O JavaScript
O Articles
O Images
Answers
Frequently, the majority of the downloaded bytes from a web page come from its image components.
An image can be embedded on a web page using the HTML element. Images are linked to online sites; they are not actually placed into web pages. The linked picture has a holding area thanks to the tag. The tag has no ending tag, is empty, and just includes attributes.
Adding images to your website is a simple method to enhance user experience. Visual information makes up 90% of the information that we take in and have sent to our brains. Images may aid in drawing attention to your site and directing visitors' lines of sight.
We utilise the element to add a basic picture to a web page.
Learn more about Web page here:
https://brainly.com/question/29526483
#SPJ4
can u please answer this logos?
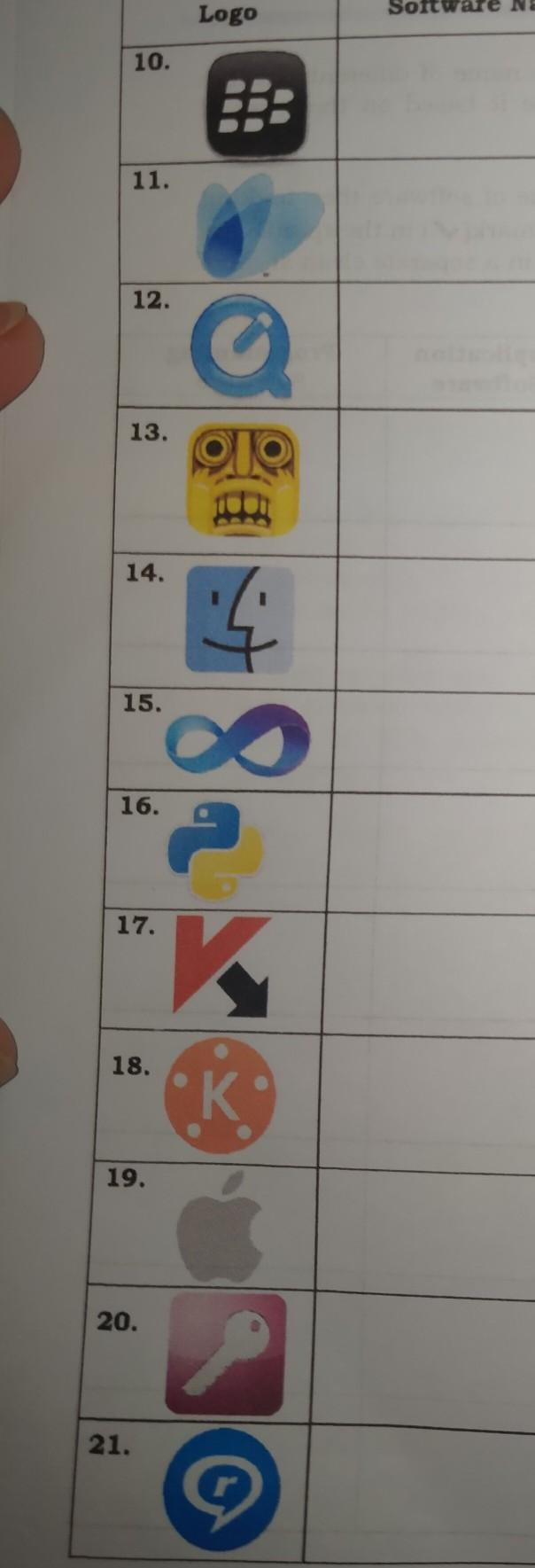
Answers
Answer:
19 is apple
I'm sorry I only know that, but I hope this helped you!!
if you want to learn how to perform an action, which feature of the excel window should you use
Answers
To learn how to perform an action on Excel Window, the feature you should use is the "Tell Me What To Do" Feature. It can be found on the top right corner above all the ribbons after "Help". This can be activated using the keyboard shortcut keys "Alt + Q".
What is Excel Window?Excel is a popular spreadsheet system that manages data into columns and rows that can be manipulated using formulas that allow the software to perform mathematical functions on the data.
It is software created by Microsoft that uses spreadsheets to organize numbers and data with formulas and functions. Excel analytics is ubiquitous around the world and is used by companies of all sizes for financial analysis
Learn more about Excel:
https://brainly.com/question/25879801
#SPJ1
Imani needs to copy text from one document into another document. She needs the pasted text to retain its original appearance. When she pastes the text, she should use which of the following settings?
Keep Text Only
Use Destination Theme
Merge Formatting
Keep Source Formatting
Answers
Answer:
Keep Text Only
Explanation:
Because why would it be any of the other ones so it would be that
Imani must transfer text from one paper to another. She ought to preserve the formatting from the original content when she pastes it. Hence, option D is correct.
What is a Document?A file produced by a software program is a computer document. Originally used to describe only word processing documents, the term "document" is now used to describe all saved files. Text, photos, music, video, and other sorts of data can all be found in documents.
An icon and a filename are used to identify documents. The filename gives the file a specific name, whereas the icon depicts the file type visually. The majority of filenames for documents also contain a file extension, which indicates the file type of the document. For instance, a Photoshop document might have a.PSD file extension, whereas a Microsoft Word document would have a.DOCX file extension.
To get more information about Document :
https://brainly.com/question/2901657
#SPJ6
Think of the silliest problem the problem solving process could help with.
Answers
Answer:
12 FISH ARE IN A BOWL. SOME BIG OTHERS LITTLE IF 5 BIG FISH ATE 2 SMALL FISH EACH HOW MANY FISH ARE LEFT IN THE BOWL ???
PLEASE MARK ME BRAINLIST IF YOU CAN'T ANSWER IT