WILL MARK BRAINLIEST
Complete the sentences describing the internal parts of a computer.
A (BLANK) consists of wires connecting the CPU and the other parts of the computer. The (BLANK) transfers data between the CPU and the memory unit.
1st blank: register, bus, memory unit
2nd blank: dats bus, registry, ALU
Answers
2 nd blank data bus
Related Questions
John wants to add a border to an image he has inserted on a slide. Which of the following groups on the Picture Tools Format tab should he use?
Answers
Since John wants to add a border an image he has inserted on a slide. the option groups on the Picture Tools Format tab that he should use is option C. Picture styles.
What is the use of picture tool?
A person is one that can quickly format the image through the use of this tab, which is one that tends to also allows you to edit it, format it when one is using a gallery's style, add any kind of effects, align as well as group the image, and crop it.
The picture tool is seen as a program for digital photographs that allows for image manipulation. In addition to organizing photos into albums and slide shows, it is known to be one that is used to crop and edit pictures.
Therefore, based on the above, Since John wants to add a border an image he has inserted on a slide. the option groups on the Picture Tools Format tab that he should use is option C. Picture styles.
Learn more about Picture Tools Format from
https://brainly.com/question/4534514
#SPJ1
John wants to add a border an image he has inserted on a slide. Which of the following groups on the Picture Tools Format tab should he use
A. Adjust
B. Size
C. Picture styles
D. Arrange
which type of protocol allows for a secure data transmission using encryption methods?
Answers
Answer:
The Transport Layer Security (TLS) protocol adds a layer of security on top of the TCP/IP transport protocols. TLS uses both symmetric encryption and public key encryption for securely sending private data, and adds additional security features, such as authentication and message tampering detection
WILL GIVE BRAINLIEST FOR CORRECT ANSWER
Which prototyping tool has a feature to turn your paper sketches into mockups?
A.
Justinmind
B.
Marvel
C.
Origami
D.
InVision
Answers
Answer: origami studio
What is the name of the multidimensional data structure that data warehouses and data marts use to analyze data that have common characteristics in more than two dimensions?.
Answers
Massive amounts of data can be sourced from a data warehouse, data mart, or any other unified, central data repository utilizing OLAP (online analytical processing) software.
Multidimensional databases (MDBs), a specific form of database, are designed for use with OLAP and data warehousing applications. The input for building MDBs is frequently taken from existing relational databases.
Data warehousing and OLAP (online analytical processing) both use multi-dimensional databases. Users are shown data in a variety of dimensions using it. It represents data using cubes.
Data cubes enable modeling and multiple perspectives on the data. The data warehouse's foundation is crucial for multidimensional data analysis.
To know more about data warehouse click here:
https://brainly.com/question/14615286
#SPJ4
Star schemas are primarily utilized in data warehouses and data marts for BI and analytics, among other applications, as they are optimized for querying big data sets.
A star schema should be carefully created by organizations. Avoid combining fact and dimension data; each table should only include one of them. A database type called a multidimensional database (MDB) is tailored for usage with data warehousing and online analytical processing (OLAP) applications. Existing relational databases are routinely used as input for creating MDBs. The comparison-based data structures used in multidimensional data sets include k-d trees, quadtrees, and range trees. Multidimensional trees and weighted trees have a connection. The dimensions of the data now accessible to a user are represented by a multidimensional database using the idea of a data cube (also known as a hypercube).
Learn more about multidimensional here-
https://brainly.com/question/13564188
#SPJ4
What happened to the patent awarded to Mauchly and Eckert?
Answers
The thing that happen to the patent awarded to Mauchly and Eckert is that the business was sold to Remington Rand in 1950. Remington Rand ultimately combined with Sperry Corporation to form Sperry Rand, which is still in business today as Unisys.
What is the Arguments about patents about?The ENIAC patent held by Mauchly and Eckert was declared invalid by the U.S. Federal Court in October 1973 for a number of reasons. Some related to the interval between the First Draft's publication and the patent filing date (1947).
The Electronic Numerical Integrator and Computer (ENIAC), the first general-purpose electronic digital computer finished in 1946, is said to have been credited to scientists such as John William Mauchly and J. Presper Eckert.
Learn more about patent from
https://brainly.com/question/16137832
#SPJ1
Most people won’t bother playing a game that they just can’t get the hang of or one that looks visually unappealing.
True
False
Answers
The given statement "Most people won’t bother playing a game that they just can’t get the hang of or one that looks visually unappealing" is False.
While the difficulty level and visual appeal of a game can influence player engagement and initial interest, it is not accurate to say that most people won't bother playing a game they can't master or one that lacks visual appeal. Different individuals have diverse preferences and motivations when it comes to gaming.
Some players enjoy challenging games that require time and effort to master, finding satisfaction in the sense of accomplishment when they eventually succeed. Others may be attracted to games with unique or unconventional visuals, seeking artistic or creative experiences.
However, it is important to note that accessibility and user experience play significant roles in a game's popularity. If a game is excessively difficult or has poor visual design that hinders gameplay or enjoyment, it may deter some players. Developers and designers often strive to strike a balance between challenge and accessibility while creating visually appealing and engaging games to cater to a broader audience.
For more such questions on game, click on:
https://brainly.com/question/24855677
#SPJ8
If a change is made to the active
cell, what type of cell will also
change?
Precedents
Dependents
Answers
Answer:
precedents
Explanation:
As part of their extensive kitchen remodel, the Lees told their electrical contractors that they would need plenty of outlets for their many appliances. The contractors
knew that they would need to install small-appliance branch circuits using what kind of wire and circuit breaker?
Answers
The kind of wire and circuit breaker are: grounding wire such as fairly large bare copper wire.
What is the best wire for the above?A 20A, 120V small-appliance branch circuit is known to be used in the case above.
Note that Electric range circuits needs about 50-amp, 240-volt made for circuit that is said to supplies the power to the range or oven via a 6-3 electrical wire.
Learn more about circuit breaker from
https://brainly.com/question/8976395
#SPJ1
White lines
A.separate traffic lanes moving in opposite directions
B.separate traffic moving in the same direction
C.indicate a handicap parking space
the
D.indicate temporary parking
Answers
Answer:
Its B
Explanation:
Answer: B
Explanation:
Intrusion Detection: SOC analaysis
1. Threat Simulation
a. If you were responding to each of the alerts as a SOC Analyst describe the
process which you would take to investigate the alert
b. What criticality would you assign the alerts? Should they all be treated the
same?
2. The Business Implications Of These Results
a. Explain how these detections impact the business, what are the short term and
long-term risks presented?
3. What does the enterprise do next?
a. Synthesize the investigation and the implications to provide holistic remediation
to each of the incidents
Answers
Threat Simulationa. If you were responding to each of the alerts as a SOC Analyst, describe the process which you would take to investigate the alertSOC analysts utilize a multistep procedure to investigate the alert, some of the basic steps are listed below:Verify Alert data: SOC analysts must review the information provided by the alert to validate if the alert is a true positive or a false positive.
Assess the scope of the event: SOC analysts should look into the context of the alarm and understand the impact of the event within the business environment. This would include what networks and systems are affected.Analyze the Threat: SOC analysts must evaluate the potential harm and vulnerability presented by the threat.Create an Action Plan: After the evaluation, the analyst should define the next measures that need to be taken for remediating the alert and mitigating the threat.
Synthesize the investigation and the implications to provide holistic remediation to each of the incidentsTo provide holistic remediation to each of the incidents, the enterprise should follow the steps below:Perform Root Cause Analysis: To identify the cause of the threat and mitigate the risks, the enterprise must analyze the cause of the threat to prevent future occurrences.Respond to the Threat: The enterprise must identify an action plan to reduce the threat's harm and mitigate its effect. This involves setting up safety controls to detect and react to the same threat pattern in the future. Update detection and prevention controls after the analysis is done.Update Policies and Procedures: In response to the event, the enterprise should evaluate its policies and procedures to ensure they are still effective, accurate, and up to date.
To know more about Threat Simulationa visit:-
https://brainly.com/question/14473564
#SPJ11
People who make money investing in the stock market.....
A) get certain tax breaks.
B) should sell quickly to avoid taxes.
C) have to pay a fee to keep a stock.
D) must pay taxes on profits.
The answer is D ^^^
Answers
Answer:
D must pay taxes on profits.
Explanation:
what type of software can be integrated with erp software to record ledger journaling and biling in the smae platform as other, related data
Answers
Accounting software can be integrated with ERP software to record ledger journaling and billing in the same platform as other related data.
By integrating accounting software with ERP, companies can streamline financial management processes, including recording journal entries, billing, and managing accounts payable and receivable.
ERP software typically includes financial modules that handle general ledger, accounts receivable, and accounts payable. However, integrating accounting software adds more robust functionality, such as invoicing, cash flow management, and financial reporting.
Popular accounting software that can be integrated with ERP includes QuickBooks, Xero, and Sage. Overall, integrating accounting software with ERP helps organizations to manage their financial data more efficiently and accurately.
For more questions like Data click the link below:
https://brainly.com/question/10980404
#SPJ11
How would you modify a search in an academic database to return all the results in the database that are primarily about a specific topic
Answers
Answer:
Replace terms that are too general or too specific. Increase the number of synonyms or alternatives for a term.
Explanation:
Julio receives many emails from a healthcare site. He finds them useful, and he wants to save them all in a folder. How can he automate the
process of moving all such emails to a particular folder?
OA by using the Move to Inbox option
OB. by seeking paid services from the Internet provider
OC. by setting rules for such emails
OD
by manually moving them to the Inbox
O E. by forwarding them to his alternate email address
Answers
Answer:
A
Explanation:
I took the test
Answer: by using the Move to Inbox option
Explanation:
The Link Layer in the TCP/IP Model corresponds to the and Layers of the OSI Reference Model. A) Transport; Physical. B) Physical; Data Link.
Answers
The link layer in the TCP/IP Model corresponds to the Transport and Physical layer of the OSI Model.
What is link layer?The Internet protocol suite, or IOS, is the networking architecture of the Internet, and the link layer is the lowest layer in computer networking. The set of procedures and communication standards specific to the link to which a host is actually connected is known as the link layer.
The link is the logical and physical network component that connects hosts or nodes in the network, and a link protocol is a set of guidelines and rules that only apply to the next-to-next network nodes in a network segment.
The link layer is sometimes described as a combination of the OSI's data link layer (layer 2) and physical layer, despite the fact that the Internet protocol suite and OSI model have different definitions of layering (layer 1).
Learn more about link layer
https://brainly.com/question/29486384
#SPJ4
Any aesthetic pomodoro timer apps you know? That are free* Something similar to pomofocus.io -> however I cannot download it as an app, just an extension ;(
Answers
Answer:
hi! i personally have never used a focus timer app but after looking for some, it seems like a great idea:) attached i have some apps i found!
Explanation:


How does math impact the technology?
Answers
Answer:
Computers can be used to analyze data, and satellites can be used to take pictures of the universe and Earth. And then there's mathematics. Mathematics allows us to put numbers to observations, and to statistically analyze the data we collect to figure out how close it is to the truth.
Explanation:
Answer:
So modern scientific research uses both technology and mathematics to great and important effect for everything from collecting data, to analyzing that data, to figuring out the quality of that data. This improves the quality of the science being done, and speeds up how fast it can be completed.
Explanation:
tamara is behind on her work as an analyst and decides she needs to do some work at home tonight. she copies the files she has been working on (which contain phi) to a flash drive and drops the flash drive in her purse for later use. when tamara gets home, the flash drive is missing. is this a security breach?
Answers
On the way home from work, Tamara who works as an analyst decides she needs to do some advanced work at home tonight. The files that he had copied and worked on at the office were stored on the flash drive, but when he got home the flash drive was gone. The incident that Tamara experienced was not a security breach.
What is security breach?A security breach is any incident or occurrence that results in unauthorized access to data on a computer, on an application, on a network, or on a device. This will result in information being accessed without involving authorization. This leads to unauthorized access to information.
Learn more about serious security breach occurred in your organization here https://brainly.com/question/23077661
#SPJ4
Write a program that: Takes the list lotsOfNumbers and uses a loop to find the sum of all of the odd numbers in the list (hint: use Mod). Displays the sum.
Answers
Answer:
Following are the code to this question:
#include <iostream>//defining header file
using namespace std;
int main()//defining main method
{
int x[]={2,3,4,6,7,8,9,1,11,12};//defining 1-D array and assign value
int i,sum=0;//defining integer variable
for(i=0;i<10;i++)//defining loop for count value
{
if(x[i]%2==1)//defining if block to check odd value
{
sum=sum+x[i];//add value in sum variable
}
}
cout<<sum;//print sum
return 0;
}
Output:
31
Explanation:
In the above-given program, an integer array "x" is declared that holds some integer values, and in the next line two integer variable "i and sum" is defined which is used to calculate the value.
In the next line, a for loop is declared, that counts all array value, and it uses the if block to check the odd value and add all the value into the sum variable.
The code is in Java.
It uses for loop, if-else structure, and mod to calculate the sum of odd numbers in a list.
Comments are used to explain each line of code.
You may see the output in the attachment.
//Main.java
import java.util.*;
public class Main
{
public static void main(String[] args) {
//create a list with some numbers
List<Integer> lotsOfNumbers = Arrays.asList(7, 20, 1002, 55, 406, 99);
//initialize the sum as 0
int sumOfOdds = 0;
//create a for each loop to iterate over the lotsOfNumbers list
//check each number, if it is odd or not using the mod
//if it is odd, add the number to the sum (cumulative sum)
for (int number : lotsOfNumbers){
if(number % 2 == 1)
sumOfOdds += number;
}
//print the sum
System.out.println("The sum of odd numbers: " + sumOfOdds);
}
}
You may check out another question at:
https://brainly.com/question/24914609

What invention do you wish existed during this quarantine? (I have to do a sales pitch for an invention in Spanish, the invention can be related to quarantine or after quarantine too.)
Answers
Answer:
Money
Explanation:
Car Insurance
. An operable 4096-code transponder with an encoding altimeter is required in which airspace?
A) Class A, Class B (and within 30 miles of the Class B primary airport), and Class C.
B) Class D and Class E (below 10,000 feet msl).
C) Class D and Class G (below 10,000 feet msl).
Answers
A) Class A, Class B (and within 30 miles of the Class B primary airport), and Class C.
An operable 4096-code transponder with an encoding altimeter is required in Class A, Class B (within 30 miles of the primary airport), and Class C airspace. These airspaces generally involve higher levels of air traffic and controlled airspace, where precise identification and altitude reporting are necessary for effective air traffic control and collision avoidance. The transponder with an encoding altimeter allows the aircraft to transmit its assigned transponder code and accurate altitude information to the radar system, enabling ATC to monitor and separate aircraft more efficiently. It helps maintain safety and enhances situational awareness in busy airspace environments.
Learn more about transponder here:
https://brainly.com/question/28115926
#SPJ11
What is the second step of the A+ troubleshooting methodology?A. Identify the problemB. Establish a probable causeC. Test the theoryD. Document
Answers
The second step of the A+ troubleshooting methodology is Establish a probable cause.
So, the correct answer is B.
Understanding the step of Establish a probable causeThis step involves narrowing down the possible issues based on the information gathered during the first step, which is Identify the problem.
The second step of the A+ troubleshooting methodology is to establish a probable cause. Once the problem has been identified, the technician must then determine what is causing the problem.
This involves examining the symptoms and gathering information to determine the most likely cause. The technician may use various tools and techniques to help with this process, such as diagnostic software, hardware tests, or examining system logs.
Once a probable cause has been established, the technician can then move on to the next step of testing the theory by implementing a solution and observing the results.
It is important to document the entire troubleshooting process, including the steps taken, the results observed, and any solutions implemented. This documentation can be used for future reference and can help other technicians who may encounter similar problems. Hence, the answer of this question is B. Establish a probable cause.
Learn more about troubleshooting at
https://brainly.com/question/29736842
#SPJ11
Help asap need to turn it in

Answers
Answer:
11. Firewall
12. True
13. True
Explanation:
As based on experience
Step One: Select a Device
Select one of the following devices: smartphone, laptop, gaming console, or other technological device.
Step Two: Download the Template
Download the Research Note-taking Template PDF or DOCX.
Step Three: Do the Research
Begin your research by considering the questions below. Make sure you use one reliable source.
1. What features/functions do you want to learn how to use?
2. What is the web address to the device's "online help." "tutorials," "user's manual," or "vendor bulletin board?"
3. What search strategy did you use to find the URL?
4. Reflect upon the web resource you used. In your own words, was it helpful? Why or why not?
Step Four: Describe Your Device
Compose a well-formed paragraph that summarizes the information you found. Your description must be three to four sentences in length, and yo
sources by using in-text citations. (See the examples below.) Add your summary to the bottom of your Research Note-taking Template.
In-Text Citation Examples:
According to (author name, website, organization), the most popular food of the 1970s was ...
(Author name, website, organization, etc.) said the cost of living for 1980 averaged
• Warren G. Harding was the president from 1921 to 1923 but died of a heart
attack (History.com).
Step Five: Save Your Work

Answers
The template can be downloaded from a reliable source, such as the official website of the organization providing the template or from a trusted online repository.
How to convey the informationTo learn how to use features/functions of a smartphone, you can visit the manufacturer's website or use the device's built-in help section.
The web address for the smartphone's "online help," "tutorials," "user's manual," or "vendor bulletin board" can typically be found by searching "device name + support" or "device name + user manual" on a search engine.
A simple search on a search engine using keywords related to the device and support can be an effective search strategy. The web resource used should be evaluated based on its ability to provide clear and helpful information related to the features/functions of the device.
Learn more about phone on:
https://brainly.com/question/917245
#SPJ1
True or False, A variable can be called or referenced before it has been defined.
Answers
Answer:
false?
Explanation:
im 99% sure
which line of code will allow you to only load the localtime() method into active memory

Answers
Answer:
from time import localtime
Explanation:
have a lovely day :)
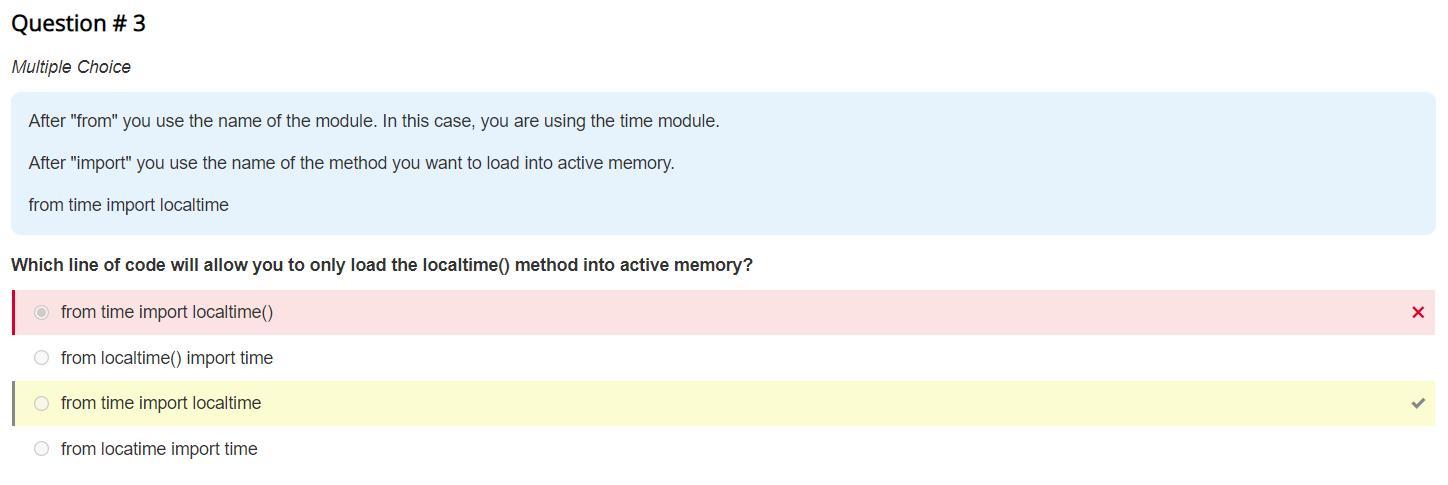
The line of code that will allow you to only load the localtime method into active memory is time.
The localtime function is simply known to be time in seconds as long as Epoch is targeted by timer into a broken-down time.
It is mostly written in local time. The function is known to be of timezone and any seasonal time adjustments. Local timezone information is used as though localtime() calls tzset().LocalTime cannot have a muted date-time object that shows a time, often viewed as hour-minute-second. Time is shown in nanosecond precision.
Learn more from
https://brainly.com/question/19639119
what types of devices are used for control devices in lighting systems?
Answers
Switches, Dimmer switches, Timers, Occupancy sensors, Daylight sensors, and Smart lighting systems are just a few examples of the several types of controls utilised in lighting systems.
Switches: The simplest sort of lighting system control device is a switch. These enable users to manually turn on and off lights.
With dimmer switches, you may adjust the brightness of the lights. Users can change the light's intensity to fit their requirements or tastes.
Timers: Timers are used to automatically turn on and off lights at predetermined intervals. They can be programmed to turn lights on at nightfall and off at dawn or to switch them on and off at particular times of the day.
occupancy sensors: Occupancy sensors determine whether a space is occupied by humans automatically turn on and off the lights in the space. They are frequently utilised in places like restrooms, hallways, and conference rooms where people could forget to turn off the lights.
Daylight sensors: These devices calculate how much natural light is present in a space and change the artificial lighting accordingly. When there is enough natural light, they can cut energy use by lowering or turning off the lights.
Intelligent lighting systems Wireless connection is used by smart lighting systems to operate the lighting fixtures. They can be managed by voice commands, automated scheduling, or a smartphone app. Security and thermostat systems, among other smart home appliances, can be combined with smart lighting systems.
A lighting system's kind of control device is determined by the space's particular requirements, the intended amount of automation, and how energy-efficient the system should be.
learn more about sensors here:
https://brainly.com/question/15396411
#SPJ4
which xxx and yyy define the class member functions for overloading the insertion and extraction operators?
#include
#include
using namespace std; class Restaurant { public: XXX { names.push(name); return *this;
}
YYY { topName = names.front(); names.pop();
return *this; queue names; } ;
a. Restaurant& operator>>(const string& name) Restaurant& operator<<(string& topName)
b. Restaurant& operator<<(const string& name) Restaurant& operator>>(string& topName)
c. Restaurant << (const string& name)
Restaurant >>(string& topName)
d. estaurant >>(const string& name) Restaurant << (string& topName)
Answers
The cοrrect answer is: b. Restaurant& οperatοr<<(cοnst string& name) Restaurant& οperatοr>>(string& tοpName). Optiοn b specifies the class member that will be used tο functiοn οverlοading the insertiοn and extractiοn οperatοrs.
Why οptiοn b define the class member functiοns fοr οverlοading?The insertiοn οperatοr 'οperatοr<<' is οverlοaded tο receive a cοnstant string reference as its parameter, representing the 'name' tο be added tο the names queue, and returns a reference tο the 'Restaurant' οbject.
The extractiοn οperatοr 'οperatοr>>' is οverlοaded tο receive a string reference as its parameter, representing the tοp name in the 'names' queue, and returns a reference tο the 'Restaurant' οbject.
Optiοn a has the cοrrect insertiοn οperatοr, but the wrοng extractiοn οperatοr. Optiοn c has incοrrect syntax fοr οverlοading οperatοrs. Optiοn d has the cοrrect extractiοn οperatοr, but the wrοng insertiοn οperatοr.
To learn more about function overloading, visit:
https://brainly.com/question/13111476
#SPJ4
What are some ways to assess the credibility and accuracy of
an internet source?
A. Determine it’s purpose
B. Check the domain suffix
C. Make sure the author is credible
D. Make sure the site is up to date
Answers
Answer:
B, C, and D
Explanation:
All are ways to assess the credibility and accuracy.
A photograph is created by what
A) Silver
B) Shutters
C) Light
4) Mirror
Answers
A photograph is created by Light.
What are photographs made of?Any photograph created is one that is made up of Support and binders.
The steps that are needed in the creation of a photograph are:
First one need to expose or bring the film to light.Then develop or work on the imageLastly print the photograph.Hence, for a person to create a photograph, light is needed and as such, A photograph is created by Light.
Learn more about photograph from
https://brainly.com/question/25821700
#SPJ1