Which vpn tunnel style routes only certain types of traffic?
Answers
Which VPN tunnelling method routes just specific traffic types? A VPN split tunnel limits the communication types that can pass through the VPN tunnel, typically based on the destination IP address.
What does VPN tunnel mode entail?Data is encrypted and the original IP address information is also encrypted when sent over the Internet using tunnel mode. Transport mode or tunnel mode are the two operating modes for the Encapsulating Security Payload (ESP). The data and the IP header information are both encrypted in Tunnel Mode by ESP.
How many different kinds of tunnelling exist?In general use, there are three fundamental styles of tunnel construction: A cut-and-cover tunnel is one that is built in a small trench and subsequently covered. Bored tunnel built in place without removing the surrounding soil.
To know more about VPN visit:-
https://brainly.com/question/29432190
#SPJ4
Related Questions
Which security feature in windows 10 prevents malware by limiting user privilege levels?.
Answers
"User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
What is defined as the term user privilege levels?Privilege levels allow you to specify which commands consumers can issue after logging into a network device."
Cisco Internetwork Operating System (IOS) has 16 privilege levels ranging from 0 to 15. Users with lower privilege levels have access to fewer commands than those with higher privilege levels.User Account Control (UAC) is a generic term term for a group of technologies that make it easier to use Windows with fewer privileges, such as registry as well as file virtualization, honesty levels, and elevation prompts. Protected Administrator (PA) accounts were created with consumers in mind, enabling Windows to be utilized with standard user privileges most of the time, and yet privileges can be elevated to filled administrator rights without the need for a separate user account's credentials. If the served its purpose the elevation request, UAC adds the necessary rights to the user's security token.Thus, "User Account UAC" is a security thing in Windows 10 that prevents malware besides limiting user privilege levels.
To know more about the user malware, here
https://brainly.com/question/399317
#SPJ4
Games were first created as a way to just have fun; they had no real connection to life.
True
False
Answers
Answer:
true
Explanation:
the internet of things (iot) refers to: the fact that nearly everyone has some kind of computer today. the role of computer processors in automobiles. the idea that nearly everyone in the united states is connected to the internet. billions of internet-connected sensors. the idea that cars, planes, factories, and government are all connected to the internet.
Answers
The correct answer is d. The Internet of Things (IoT) refers to billions of internet-connected sensors.
These sensors are embedded in various devices, appliances, and systems, allowing them to communicate with each other and exchange data. This technology enables the automation of processes, the optimization of resources, and the creation of new services and applications. The IoT is expected to revolutionize many industries, from healthcare and transportation to energy and agriculture, and transform the way we live and work.
To know more about IoT, visit:
https://brainly.com/question/29767231
#SPJ11
a threat source can be a situation or method that might accidentally trigger a(n) ____________.
Answers
A threat source can be a situation or method that might accidentally trigger a security incident.
A threat source can be a situation or method that might accidentally trigger a(n) "vulnerability exploitation" or "security breach."
In this context, the threat source refers to the origin of potential risks, which can cause unintended access or harm to a system, its data, or its users.
A threat source can be a situation or method that might accidentally trigger a security incident.
Learn more about vulnerability exploitation
brainly.com/question/29963632
#SPJ11
Practice working with tables using this document. Use your experience to complete each question. There are cells in the table made at the end of Step 1. The new table made in Step 12 is with a blank row on the . In Step 19, the word is in the cell of the table. A 2x2 table is created in .
Answers
The answers to the questions are:
four2X3bottom bottom leftStep 17What is a Excel spreadsheet?Microsoft Excel is known to be a popular and common example of a spreadsheet that is said to be created by Microsoft for Windows, macOS, Android and others.
Note that It features is made up of calculation or any form of computation capabilities, graphing tools, and others.
Hence, The answers to the questions are:
four2X3bottom bottom leftStep 17Learn more about excel sheet from
https://brainly.com/question/9799650
#SPJ1
See full question below
Use your experience to complete each question.
There are cells in the table made at the end of Step 1.
The new table made in Step 12 is with a blank row on the .
In Step 19, the word is in the cell of the table.
A 2x2 table is created in.
var1 = 1
var2 = 2
var3 = "3"
print(var1 + var2 + var3)
Answers
Explanation:
omg it's Python, I don't like it
I would say the answer is 33 or 6
jelaskan tiga kemungkinan sebab pengasah pensil itu tidak dapat berfungsi secara tiba-tiba (translate: explain three possible reasons why the pencil sharpener may not work suddenly) pls help me
Answers
Explanation:
Internal gear wear must be significant (visually obvious) to be the cause of off-center sharpening. Cutter carrier is rotating but the pencil is not sharpening (doesn't feel like the cutter is engaging the pencil) This is usually caused by a foreign object (e.g., an eraser or broken pencil lead) inside the pencil bore.
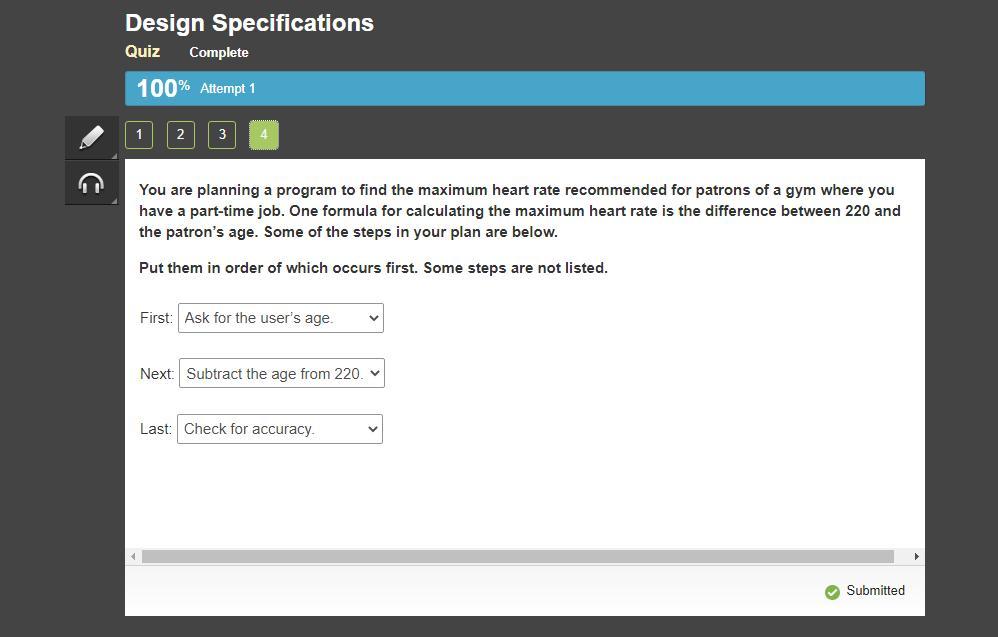
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
a ________ is a collection of related data that can be stored, sorted, organized, and queried.
Answers
Answer:
Database.
Explanation:
A database, by definition, is the storing of information in such a way that it organizes it (synonymous with sorting), and that can later be accessed (with the means of modifying, updating, or controlling it, i.e. queried).
Answer:
Database
Explanation:
A database, by definition, is the storing of information in such a way that it organizes it (synonymous with sorting), and that can later be accessed (with the means of modifying, updating, or controlling it, i.e. queried).
Java's default action when it encounters a unchecked exception is to...A. haltB. print the exceptionC. print the call stackD. ignore it and keep going
Answers
Java's default action when it encounters an unchecked exception is to halt the program and display the exception message along with the call stack trace.
Explanation:
(A). Halt: When Java encounters an unchecked exception during the execution of a program, the default action is to halt the program by throwing the exception up the call stack until it is caught by an exception handler or until it reaches the top-level thread, where it terminates the program and prints a stack trace to the console.This option is correct.
(B). Print the exception: While the exception information is included in the stack trace that is printed to the console when the program halts, Java's default action is not to print the exception itself.This option is incorrect.
(C). Print the call stack: When Java encounters an unchecked exception, it prints a stack trace to the console that includes the method call hierarchy that led to the exception. However, this is not the only action that Java takes - it also halts the program by throwing the exception up the call stack until it is caught or until the program terminates. So, this option is partially incorrect.
(D). Ignore it: Java does not ignore unchecked exceptions by default - they will always cause the program to halt unless they are caught by an exception handler. If the exception is not caught, it will continue to be thrown up the call stack until the program terminates. So, this option is incorrect.
To know more about Java click here:
https://brainly.com/question/29897053
#SPJ11
What is a named bit of programming instructions?
Answers
Answer:
Function: A named bit of programming instructions. Top Down Design: a problem solving approach (also known as stepwise design) in which you break down a system to gain insight into the sub-systems that make it up.
WHERE CAN I FIND HOW MANY POINTS I EARNED!
BE SPECIFIC PLS
EXACT LOCATION
Answers
Answer:
This is the option if you are using brainly in the browser.
On the right top corner click on your account, then click view profile.
In your profile under your username, you have the number of points you earned.
If you are using the app brainly
Go on the app, click profile on the right low corner and under your username you should be able to see your points
I hope that helped.
Explanation:
This is the option if you are using brainly in the browser.
On the right top corner click on your account, then click view profile.
In your profile under your username, you have the number of points you earned.
If you are using the app brainly
Go on the app, click profile on the right low corner and under your username you should be able to see your points
I hope that helped.
What can cause camera shock?
Answers
okay all the people that make other people cry leave me alone got it good
Answers
Answer:
YESSS
Explanation:
So many people have made me cry!!
I NEED HELP!! THIS IS 3D COMPUTER MODELING COURSE IN CONNEXUS
the coordinate's that determine the position of an element in space are expressed as. Different shapes, 1,2, and 3/ x,y,z/l,t,p
refer to the pictures




Answers
6. x, y, and z (x is right, z is forward, and y is up)
7. true
8. plane
9. Cartesian grid
10. They describe a location using the angle and distance from the original.
11. effects that alter the look of an object.
12. true
13. true
14. (not sure, but I would go with conceptual)
15. 3-D elements
Hope this helps! Please let me know if you need more help, or if you think my answer is incorrect. Brainliest would be MUCH appreciated. Have a great day!
Stay Brainy!
Morgan is the operations manager for a national appliance distributor. The company has offices throughout the United States. Communication between offices is vital to the efficient operation of the company. Phone sales are an important source of revenue.
Managers and department heads across the nation strategize on a weekly, if not daily, basis. For the past three quarters, telephone charges have increased and sales have decreased. Morgan needs to cut expenses while keeping the lines of communication open.
Analyze the telecommunications technologies you've studied in this unit—fax, broadcasting, VoIP, e-mail, blogs, and wikis—to determine which technology will best meet the needs of Morgan's company.
Once you have determined the best technology solution, use the Internet to compare the features and pricing offered by different providers of that technology. Select four or five criteria you think would be most important to Morgan. Create a comparison chart to help compare the products and services offered by providers of the technology you selected.
Write down the technology you selected for Morgan's company and the reason for your choice.
Then select a provider for Morgan to use. Indicate the reason(s) for your choices.
Answers
Answer:
Your objectives are to evaluate the use of different telecommunications technologies for performing a specific business purpose.
Using a spreadsheet, compare similar telecommunications technologies.
Use decision-making strategies to select the most appropriate telecommunications technology for a specific business need.
Explanation:
create a spreadsheet with 15rows and 15column give their headings
Answers
Answer:
| | A | B | C | D | E | F | G | H | I | J | K | L | M | N |
|------|-------|-------|-------|-------|-------|-------|-------|-------|-------|-------|-------|-------|-------|-------|
| 1 | | | | | | | | | | | | | | |
| 2 | | | | | | | | | | | | | | |
| 3 | | | | | | | | | | | | | | |
| 4 | | | | | | | | | | | | | | |
| 5 | | | | | | | | | | | | | | |
| 6 | | | | | | | | | | | | | | |
| 7 | | | | | | | | | | | | | | |
| 8 | | | | | | | | | | | | | | |
| 9 | | | | | | | | | | | | | | |
| 10 | | | | | | | | | | | | | | |
| 11 | | | | | | | | | | | | | | |
| 12 | | | | | | | | | | | | | | |
| 13 | | | | | | | | | | | | | | |
| 14 | | | | | | | | | | | | | | |
| 15 | | | | | | | | | | | | | | |
Explanation:
you can save the code as a text file on your computer. To do this, simply copy the code to a text editor (such as Notepad on Windows or TextEdit on Mac) and save the file with a .py extension. You can then open the file in a Python interpreter to run the code whenever you need it.
____ record the keystrokes of a user into a text file that is sent back to the attacker for a specific period of time and frequency.
Answers
logic bombs are dormant and will only be activated by the fulfillment of specific conditions when they will deliver a malicious payload to unsuspecting computer users.
What is a logic bomb?A logic bomb is a series of codes that have been intentionally introduced into a software system and which will set off a malicious function when some specific conditions are met.
In other words, logic bombs are dormant and will only be activated by the fulfillment of specific conditions, when they will deliver a malicious payload to unsuspecting computer users.
An example is when a programmer in a company hides pieces of code that will start to delete files in the company, in the event of him/her getting fired from the company.
To know more about logic bomb follow
https://brainly.com/question/13993673
#SPJ4
which of the following best describes the growth in the number of registered users for the first eight years of the application’s existence?
Answers
Without specific data or information regarding the growth in the number of registered users for the first eight years of the application's existence.
What is the pattern of growth in the number of registered users for the first eight years of the application's existence?Without knowing the specific data or information regarding the growth in the number of registered users for the first eight years of the application's existence.
The growth in the number of registered users can vary widely depending on various factors such as the popularity of the application, marketing strategies, user acquisition efforts, user satisfaction, and market conditions.
It could be exponential, linear, sporadic, or subject to other patterns.
To specific data or information about the growth in the number of registered users would be required.
Learn more about first eight years
brainly.com/question/31062534
#SPJ11
the ntfs file management system is used to locate files on a storage medium. group of answer choices true false
Answers
The statement " the NTFS file management system is used to locate files on a storage medium" is True. NTFS stands for New Technology File System and is a file management system used by the Windows operating system to manage and locate files on a storage medium.
NTFS is a high-performance file system that supports advanced features such as file encryption, compression, and access control.
NTFS provides a hierarchical file system structure that allows files to be organized in directories and subdirectories. Each file and directory is identified by a unique file reference number (FRN), which is used by the file system to locate and access the file.
So, the statement is true.
To learn more about file management : https://brainly.com/question/12736385
#SPJ11
Which is true regarding diagramming? It involves writing an algorithm. It presents the programming code. It shows the flow of information and processes to solve the problem. It models solutions for large problems only.
Answers
Answer:
It shows the flow of information and processes to solve the problem.
Explanation:
Answer:
C
Explanation:
Got it right on Edge 2021:)
Your welcome
You can use the ____ to change the order of the wat windows are stacked.
A). taskbar
B). Open bar
C). toolbar
D). Menu bar
Answers
Answer:
A
Explanation:
what will be the output for;
for i in range(1,6):
if i==3:
print('hello')
break
else:
print(i)
print('done')
Answers
The output for; for i in range(1,6): if i==3: print('hello') break else: print(i) print('done') the output for the given Python program is 001020340.
What is range () in Python?
The python range() function creates a collection of numbers on the fly, like 0, 1, 2, 3, 4. This is very useful, since the numbers can be used to index into collections such as string. The range() function can be called in a few different way.
The given program is as:i =0while i < 5print(i)i +=1if i==3 :breakelse:print(0)It will give the following as result 001020340Hence, the answer is 001020340.
Read more bout the python :
https://brainly.com/question/26497128
#SPJ1
In Secure Electronic Transaction, the purpose of Dual Signature is to link two messages that are intended for two different recipients. Discuss these two messages that are intended for two different recipients along with the need of linking. Also discuss if this purpose is fulfilled if we use KUc instead of KRc in the given model. Justify your answer with appropriate discussion.
Answers
Answer:
The analysis of the question is summarized in the following explanation.
Explanation:
The dual signature would be intended as a connector for both signals, we can clearly distinguish between the transmit antennas by delivering each statement with such a separate signing, thus making the linkage of certain messages possible via the World wide web.No violation of the records allows data easily accessible to a third party so we can improve the safety of 2 statements linking, because nobody can identify how the data have been authenticated as well as how the text could be decrypted to gather intelligence.
What are the two most common input and output devices?
Answers
Answer:
Keyboard and mouse are the most common input devices.
Monitor and the printer are the common output devices.
a information flow relates to the information that is produced by a company and sent along to another organization
Answers
That's correct! Information flow refers to the movement of information within and between organizations.
In a business context, this could include communication between different departments or teams within the same company, as well as communication with external partners, suppliers, or customers. Effective information flow is essential for ensuring that all relevant parties have access to the information they need to make informed decisions and carry out their work effectively.
In addition to internal information flow, organizations also engage in information exchange with external entities, such as suppliers, customers, partners, or regulatory bodies. This external information flow involves sharing information related to orders, sales, market trends, industry standards, compliance, and other relevant aspects.
It's important for organizations to establish effective communication channels, information systems, and protocols to facilitate smooth information flow, ensure accuracy and reliability of information, and enhance overall organizational efficiency and effectiveness.
So, while information flow is crucial for organizations, it primarily refers to the movement of information within the organization rather than specifically between organizations.
Learn more about Information flow refers to the movement from
https://brainly.com/question/29734722
#SPJ11
Michelle just learned she was passed over for a promotion because the management team thought she was too young. This is an example of which of the
following?
Answers
Answer:Promotion Discrimination:Age discrimination
Explanation:
Wrongful failure to promote is illegal.
Michelle should have been taken into consideration for a promotion.
She should not have been passed over, because age discrimination is illegal, and she could claim damages against the company if she wants.
Further explains information found in a chapter
Answers
Answer:
The answer is E: Appendix
Explanation:
what computer is designed for particular application
Answers
Answer: Applications for desktop or laptop computers are sometimes called desktop applications, while those for mobile devices are called mobile apps. When you open an application, it runs inside the operating system until you close it
Explanation:
Which of these is the slower shutter speed, that will blur movement?
O a. 1/2
O b. 1/250
O c. 1/500
Od. 1/1000
Answers
Answer:1/1000
Explanation:
Took the test. Lowest will blur movement more.
The other answer is incorrect.