Which of the following is an example of how high student loan debt can
impact a person's life decisions?
Answers
Student loan debt is the debt owed by the students to a financial institution. The person has to choose public transportation over a personal vehicle as they cannot afford a downpayment.
What is the impact of the student loan?Students loan are the debt that is incurred by the students for educational purposes and affects the quality of the life of a person as they need to save money to pay the debt.
The student owing money cannot afford to buy their vehicle because of the downpayment and will choose to use public transportation over buying a car to save money.
Therefore, high student loans will lead to the use of public transportation instead of buying cars.
Learn more about loans here:
https://brainly.com/question/27205887
#SPJ1
Related Questions
This program extends the earlier "Online shopping cart" program. (Consider first saving your earlier program).
(1) Extend the ItemToPurchase struct to contain a new data member. (2 pt)
char itemDescription[ ] - set to "none" in MakeItemBlank()
Implement the following related functions for the ItemToPurchase struct.
PrintItemDescription()
Has an ItemToPurchase parameter.
(2) Create three new files:
ShoppingCart.h - struct definition and related function declarations
ShoppingCart.c - related function definitions
main.c - main() function (Note: main()'s functionality differs from the warm up)
Build the ShoppingCart struct with the following data members and related functions. Note: Some can be function stubs (empty functions) initially, to be completed in later steps.
Data members (3 pts)
char customerName [ ]
char currentDate [ ]
ItemToPurchase cartItems [ ] - has a maximum of 10 slots (can hold up to 10 items of any quantity)
int cartSize - the number of filled slots in array cartItems [ ] (number of items in cart of any quantity)
Related functions
AddItem()
Adds an item to cartItems array. Has parameters of type ItemToPurchase and ShoppingCart. Returns ShoppingCart object.
RemoveItem()
Removes item from cartItems array (does not just set quantity to 0; removed item will not take up a slot in array). Has a char[ ](an item's name) and a ShoppingCart parameter. Returns ShoppingCart object.
If item name cannot be found, output this message: Item not found in cart. Nothing removed.
ModifyItem()
Modifies an item's description, price, and/or quantity. Has parameters of type ItemToPurchase and ShoppingCart. Returns ShoppingCart object.
GetNumItemsInCart() (2 pts)
Returns quantity of all items in cart. Has a ShoppingCart parameter.
GetCostOfCart() (2 pts)
Determines and returns the total cost of items in cart. Has a ShoppingCart parameter.
PrintTotal()
Outputs total of objects in cart. Has a ShoppingCart parameter.
If cart is empty, output this message: SHOPPING CART IS EMPTY
PrintDescriptions()
Outputs each item's description. Has a ShoppingCart parameter.
(3) In main(), prompt the user for a customer's name and today's date. Output the name and date. Create an object of type ShoppingCart. (1 pt)
(4) Implement the PrintMenu() function in main.c to print the following menu of options to manipulate the shopping cart. (1 pt)
(5) Implement the ExecuteMenu() function in main.c that takes 2 parameters: a character representing the user's choice and a shopping cart. ExecuteMenu() performs the menu options (described below) according to the user's choice, and returns the shopping cart. (1 pt)
(6) In main(), call PrintMenu() and prompt for the user's choice of menu options. Each option is represented by a single character.
If an invalid character is entered, continue to prompt for a valid choice. When a valid option is entered, execute the option by calling ExecuteMenu() and overwrite the shopping cart with the returned shopping cart. Then, print the menu and prompt for a new option. Continue until the user enters 'q'. Hint: Implement Quit before implementing other options. (1 pt)
(7) Implement the "Output shopping cart" menu option in ExecuteMenu(). (3 pts)
8) Implement the "Output item's description" menu option in ExecuteMenu(). (2 pts)
(9) Implement "Add item to cart" menu option in ExecuteMenu(). (3 pts)
(10) Implement the "Remove item from cart" menu option in ExecuteMenu(). (4 pts)
(11) Implement "Change item quantity" menu option in ExecuteMenu(). Hint: Make new ItemToPurchase object before using ModifyItem() function. (5 pts)
Answers
Answer:
To create an online shopping cart. You need to do the following:
Update the ItemToPurchase struct to include a new data member called itemDescription.
Create three new files: ShoppingCart.h, ShoppingCart.c, and main.c.
Build the ShoppingCart struct with the following data members: customerName, currentDate, cartItems (which can hold up to 10 items of any quantity), and cartSize.
Implement the AddItem, RemoveItem, ModifyItem, GetNumItemsInCart, GetCostOfCart, PrintTotal, and PrintDescriptions functions for the ShoppingCart struct.
In the main function, prompt the user for a customer's name and today's date, and create an object of type ShoppingCart.
Implement a menu of options to manipulate the shopping cart in the PrintMenu function in main.c.
Implement the ExecuteMenu function in main.c to perform the menu options according to the user's choice.
Implement the "Output shopping cart" menu option in ExecuteMenu.
Implement the "Output item's description" menu option in ExecuteMenu.
Implement the "Add item to cart" menu option in ExecuteMenu.
Implement the "Remove item from cart" menu option in ExecuteMenu.
Implement the "Change item quantity" menu option in ExecuteMenu.
Note: Each step has a point value assigned to it, and some steps have hints provided.
BADM-Provide a reflection of at least 500 words (or 2 pages double spaced) of how the knowledge, skills, or theories of this course have been applied, or could be applied, in a practical manner to your current work environment. If you are not currently working, share times when you have or could observe these theories and knowledge could be applied to an employment opportunity in your field of study.
Required:
Provide a 500 word (or 2 pages double spaced) minimum reflection.
Answers
Answer:
WooW We Have To All This Which Class can you Please tell
Is the product function is given as Q=L+L³ find marginal product function.
Answers
To find the marginal product function, we need to differentiate the given production function with respect to the variable of interest, which in this case is labor (L).
Given the production function Q = L + L³, we will differentiate it with respect to L:
dQ/dL = 1 + 3L²
The derivative dQ/dL represents the marginal product of labor (MPL), which is the additional output produced by each additional unit of labor.
Therefore, the marginal product function for the given production function Q = L + L³ is MPL = 1 + 3L².
Kindly Heart and 5 Star this answer and especially don't forgot to BRAINLIEST, thanks!im trying to call the keys in a dictionary I have called "planet_dict". in order for them to be included in the for loop, the values of the keys have to be within a range of
273 <= x <= 373
I understand how to do this with certain values, but idk how to call them from a dictionary.

Answers
You can do something like this. My code iterates through the dictionary keys and then we use that key to get a value. We check if the value is between 273 and 373 and if it is, it's a water planet. My code is just a general idea of what to do. Instead of printing, you could add the key to a list and then print the contents of the list.

Plz answer this question for me quick for a Brainly

Answers
which bird is the symbol of peace ?
dove
What do the cookies saved on your computer do?
They track your browsing habits.
They track your online preferences.
They prevent you from visiting some websites.
They track any pirated files on your system.
They store and maintain your personal information.
Answers
what is a cell selector
Answers
Answer:
it's files contain each buttons configuration information and the size and number of buttons in the configuration.
Answer:
Cell selector files contain each button's configuration information and the size and number of buttons in the configuration. If mr_cellcelector is not defined, the cells in the attached cell library are loaded. If neither condition is met, a dialog is opened for selecting a cell library.
Explanation:
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
what are reserved words with a programming language
Answers
This is a syntactic definition, and a reserved word may have no user-defined meaning. Often found in programming languages and macros, reserved words are terms or phrases appropriated for special use that may not be utilized in the creation of variable names. For example "print" is a reserved word because it is a function in many languages to show text on the screen
Which is an example of a demand account
Answers
Answer: savings account investment account credit account checking account Checking account is an example of a demand account.
What is number of maximum number of virtual processors for each of the
following Hyper-V client?
Answer by a number such as 16.
1. Windows 7
2. Windows 8
3. Open SUSE 12.1
Answers
The number of maximum number of virtual processors for each of the
following Hyper-V client are:
Windows 7 - 4 virtual processorsWindows 8 - 32 virtual processorsOpen SUSE 12.1 - 64 virtual processorsWhat is the virtual processors?Hyper-V is a hypervisor-located virtualization platform that allows diversified virtual machines to gossip a single physical apparatus. One of the key advantages of virtualization is the skill to allocate virtual processors for each virtual system, which allows the computer software for basic operation running inside the virtual tool.
The maximum number of in essence processors that can be filling a place a virtual machine depends on various factors, containing the capabilities of the physical main part of computer and the version of the computer software for basic operation running inside the virtual machine.
Learn more about virtual processors from
https://brainly.com/question/30628655
#SPJ1
why is NAND gate known as universal gate? expain
Answers
It's universal because it can be used to implement any gate, so you can use it as the only type of gate in a logic circuit.
It’s been a brutally cold and snowy winter. None of your friends have wanted to play soccer. But
now that spring has arrived, another season of the league can begin. Your challenge is to write a
program that models a soccer league and keeps track of the season’s statistics.
There are 4 teams in the league. Matchups are determined at random. 2 games are played every
Tuesday, which allows every team to participate weekly. There is no set number of games per
season. The season continues until winter arrives.
The league is very temperature-sensitive. Defenses are sluggish on hot days. Hotter days allow for
the possibility of more goals during a game.
If the temperature is freezing, no games are played that week. If there are 3 consecutive weeks of freezing temperatures, then winter has arrived and the season is over.
Teams class
Each team has a name.
The program should also keep track of each team’s win-total, loss-total, tie-total, total goals scored, and total goals allowed.
Create an array of teams that the scheduler will manage.
Print each team’s statistics when the season ends.
Games class
In a game, it’s important to note each team’s name, each team’s score, and the temperature that day.
Number each game with integer ID number.
This number increases as each game is played.
Keep track of every game played this season.
This class stores an ArrayList of all games as a field.
Your program should determine scores at random. The maximum number of goals any one team can score should increase proportionally with the temperature.
But make sure these numbers are somewhat reasonable.
When the season ends, print the statistics of each game.
Print the hottest temperature and average temperature for the season.
Scheduler class
Accept user input through a Scanner. While the application is running, ask the user to input a temperature. (Do while)
The program should not crash because of user input. If it’s warm enough to play, schedule 2 games.
Opponents are chosen at random.
Make sure teams aren’t scheduled to play against themselves.
If there are 3 consecutive weeks of freezing temperatures, the season is over.
A test class with a main is to be written
Also take into account if there are no games at all
Answers
Below is an example of a program that models a soccer league and keeps track of the season's statistics in Java:
What is the Games class?java
import java.util.ArrayList;
import java.util.Random;
import java.util.Scanner;
class Team {
private String name;
private int winTotal;
private int lossTotal;
private int tieTotal;
private int goalsScored;
private int goalsAllowed;
// Constructor
public Team(String name) {
this.name = name;
this.winTotal = 0;
this.lossTotal = 0;
this.tieTotal = 0;
this.goalsScored = 0;
this.goalsAllowed = 0;
}
// Getters and Setters
public String getName() {
return name;
}
public int getWinTotal() {
return winTotal;
}
public int getLossTotal() {
return lossTotal;
}
public int getTieTotal() {
return tieTotal;
}
public int getGoalsScored() {
return goalsScored;
}
public int getGoalsAllowed() {
return goalsAllowed;
}
public void incrementWinTotal() {
winTotal++;
}
public void incrementLossTotal() {
lossTotal++;
}
public void incrementTieTotal() {
tieTotal++;
}
public void incrementGoalsScored(int goals) {
goalsScored += goals;
}
public void incrementGoalsAllowed(int goals) {
goalsAllowed += goals;
}
}
class Game {
private int gameId;
private String team1;
private String team2;
private int team1Score;
private int team2Score;
private int temperature;
// Constructor
public Game(int gameId, String team1, String team2, int temperature) {
this.gameId = gameId;
this.team1 = team1;
this.team2 = team2;
this.team1Score = 0;
this.team2Score = 0;
this.temperature = temperature;
}
// Getters and Setters
public int getGameId() {
return gameId;
}
public String getTeam1() {
return team1;
}
public String getTeam2() {
return team2;
}
public int getTeam1Score() {
return team1Score;
}
public int getTeam2Score() {
return team2Score;
}
public int getTemperature() {
return temperature;
}
public void setTeam1Score(int team1Score) {
this.team1Score = team1Score;
}
public void setTeam2Score(int team2Score) {
this.team2Score = team2Score;
}
}
class Scheduler {
private ArrayList<Team> teams;
private ArrayList<Game> games;
private int consecutiveFreezingWeeks;
// Constructor
public Scheduler(ArrayList<Team> teams) {
this.teams = teams;
this.games = new ArrayList<>();
this.consecutiveFreezingWeeks = 0;
}
// Schedule games based on temperature
public void scheduleGames(int temperature) {
if (temperature <= 32) {
consecutiveFreezingWeeks++;
System.out.println("No games played this week. Temperature is below freezing.");
} else {
consecutiveFreezingWeeks = 0;
int maxGoals = 0;
// Calculate max goals based on temperature
if (temperature <= 50) {
maxGoals = 3;
} else if (temperature <= 70) {
maxGoals = 5;
Read more about Games class here:
https://brainly.com/question/24541084
#SPJ1
Write a Python 3 script in PyCharm that will simulate the game of "Rock, Paper, Scissors": Display a header and the simple rules of RPS Prompt player_1 for their move To make sure player_2 can't see what player_1's move was, insert: print('*** NO CHEATING ***\n\n' * 20) Prompt player_2 for their move Design and develop an IF-ELSE structure to play the game IF player_1's move equivalent to player_2's move, "It's a tie" "rock" beats "scissors" "scissors" beats "paper" "paper" beats "rock" Make sure you test for valid input!!
Answers
Answer:
'''
Rock, Paper, Scissors:
The Rules:
If player1's move equivalent to player2's move, "It's a tie".
"rock" beats "scissors", "scissors" beats "paper", and "paper" beats "rock"
'''
player_1 = input("Player 1's move: ")
print('*** NO CHEATING ***' * 20)
player_2 = input("Player 2's move: ")
if player_1 or player_2 not in ["rock", "paper", "scissors"]:
print("Invalid input!")
if player_1 == player_2:
print("It's a tie")
else:
if player_1 == "rock":
if player_2 == "scissors":
print("Player 1 won")
elif player_2 == "paper":
print("Player 2 won")
elif player_1 == "scissors":
if player_2 == "paper":
print("Player 1 won")
elif player_2 == "rock":
print("Player 2 won")
elif player_1 == "paper":
if player_2 == "rock":
print("Player 1 won")
elif player_2 == "scissors":
print("Player 2 won")
Explanation:
In the comment part, put the header and the rules of the game
Ask the user to enter the player1's move
Print the asterisks
Ask the user to enter the player2's move
If any of the input is not "rock", "paper", "scissors", state that the input is invalid
Check the inputs. If they are equal, print that it is a tie. Otherwise:
If player1's move is rock. Check player2's move. If it is "scissors", player1 wins. If it is "paper", player2 wins
If player1's move is scissors. Check player2's move. If it is "paper", player1 wins. If it is "rock", player2 wins
If player1's move is paper. Check player2's move. If it is "rock", player1 wins. If it is "scissors", player2 wins
Create a class Car, which contains Three data members i.e. carName (of string type), ignition (of bool type), and currentSpeed (of integer type)
A no-argument constructor to initialize all data members with default values
A parameterized constructor to initialize all data members with user-defined values
Three setter functions to set values for all data members individually
Three getter function to get value of all data members individually
A member function setSpeed( ) // takes integer argument for setting speed
Derive a class named Convertible that contains
A data member top (of Boolean type)
A no-argument constructor to assign default value as “false” to top
A four argument constructor to assign values to all data-members i.e. carName, ignition, currentSpeed and top.
A setter to set the top data member up
A function named show() that displays all data member values of invoking object
Write a main() function that instantiates objects of Convertible class and test the functionality of all its member functions.
Answers
Answer:
Copy paste it.
Explanation:
#include <iostream>
#include <string>
using namespace std;
//Create a class Car, which contains • Three data members i.e. carName (of string type), ignition (of bool type), and //currentSpeed (of integer type)
class Car
{
public:
string carName;
bool ignition;
int currentSpeed;
//A no-argument constructor to initialize all data members with default values
//default value of string is "",bool is false,int is 0
Car()
{
carName="";
ignition=false;
currentSpeed=0;
}
//A parameterized constructor to initialize all data members with user-defined values
Car(string name,bool i,int speed)
{
carName=name;
ignition=i;
currentSpeed=speed;
}
//Three setter functions to set values for all data members individually
// Three getter function to get value of all data members individually
void setCarName(string s)
{
carName=s;
}
void setIgnition(bool ig)
{
ignition=ig;
}
void setCurrentSpeed(int speed)
{
currentSpeed=speed;
}
string getCarName()
{
return carName;
}
bool getIgnition()
{
return ignition;
}
int getCurrentSpeed()
{
return currentSpeed;
}
//A member function setSpeed( ) // takes integer argument for setting speed
void setSpeed(int sp1)
{
currentSpeed=sp1;
}
};
//Derive a class named Convertible
class Convertible:public Car
{
//A data member top (of Boolean type)
public:
bool top;
public:
//A no-argument constructor to assign default value as “false” to top
Convertible()
{
top=false;
}
//A four argument constructor to assign values to all data-members i.e. carName, ignition,
//currentSpeed and top.
Convertible(string n,bool i,int s,bool t):Car(n,i,s)
{
carName=n;
ignition=i;
currentSpeed=s;
top=t;
}
// A setter to set the top data member up
void setTop(bool t)
{
top=t;
}
//A function named show() that displays all data member values of invoking object
void show()
{
cout<<"Car name is:"<<carName<<endl;
cout<<"Ignition is: "<<ignition<<endl;
cout<<"Current Speed is :"<<currentSpeed<<endl;
cout<<"Top is:"<<top<<endl;
}
};
//main function
int main()
{
//creating object for Convertible class
Convertible c1("Audi",true,100,true);
c1.show();
c1.setCarName("Benz");
c1.setIgnition(true);
c1.setCurrentSpeed(80);
c1.setTop(true);
c1.show();
cout<<"Car Name is: "<<c1.getCarName()<<endl;
cout<<"Ignition is:"<<c1.getIgnition()<<endl;
cout<<"Current Speed is:"<<c1.getCurrentSpeed()<<endl;
return 0;
}
The Boolean operators include which of the following?
A. and, or, not
B. to, for, from
C. a, an, the
D. is, are, not
Answers
Answer:
The answer is A. and, or, not
Explanation:
Using a Boolean search can help narrow your results. A Boolean search is a query that uses the Boolean operators AND, OR, and NOT, along with quotation marks, to limit the number of results. For example, searching the terms Alexander the Great AND conquests will provide results about Alexander, great, and their conquests.
Let K(x, y) denote the statement "x knows y" and D denote the domain of all people. Express the following English sentences as a quantified proposition using the definitions above:
1. Everybody knows somebody.
2. There is somebody that no one knows.
3. There is no one who knows everybody
Answers
Answer:
Given: K(x,y) denotes statement:
"x knows y"
D denote domain of all people.
Explanation:
1. Everybody knows somebody.
Solution:
∀x∈D ∃y∈D : K(x, y)
∀ means for all. Here it is used for Everybody.
∃ means there exists some. Here it represents Somebody.
∈ means belongs to . Both x and y belongs to the domain D of all people.
2. There is somebody that no one knows.
Solution:
∀x∈D ∃y∈D : ¬K(x, y)
∀ means for all. ∃ means there exists some. ∈ means belongs to both x and y belongs to the domain D of all people.¬ this is negation sign which means not K(x,y). So the negation of everybody knows somebody can be expressed as there is somebody that no one knows.
3. There is no one who knows everybody
Solution:
This can be represented in both the ways below.
∀ y∈D ∃ x∈D : K(x, y)
∀ means for all. ∃ means there exists some. ∈ means belongs to both x and y belongs to the domain D of all people.
∀x∈D ∀y∈D : ¬K(x, y)
∀ means for all. The negation shows that there is no one who knows everybody.
In Python, an equal symbol (=) is used to concatenate two or more strings.
True
False
Answers
In Python, an equal sign is used to assign a variable. Ex: my_money = 27
To concatenate, you would simply use a +. Ex: amount_for_babysitting = 10
my_money + amount_for_babysitting
LANGUAGE IS PYTHON PLEASE HELP.
Write a while loop that repeats while user_num ≥ 1. In each loop iteration, divide user_num by 2, then print user_num.
Sample output with input: 20
10.0
5.0
2.5
1.25
0.625
Answers
What is an automatic update and when should you use it
Answers
Automatic updates allow users to keep their software programs updated without having to check for and install available updates manually. The software automatically checks for available updates, and if found, the updates are downloaded and installed without user intervention.
Hope it helps you my dear:)
Drag each tile to the correct box. Match each decimal number to an equivalent number in a different number system. 6910 22810 4210 2710
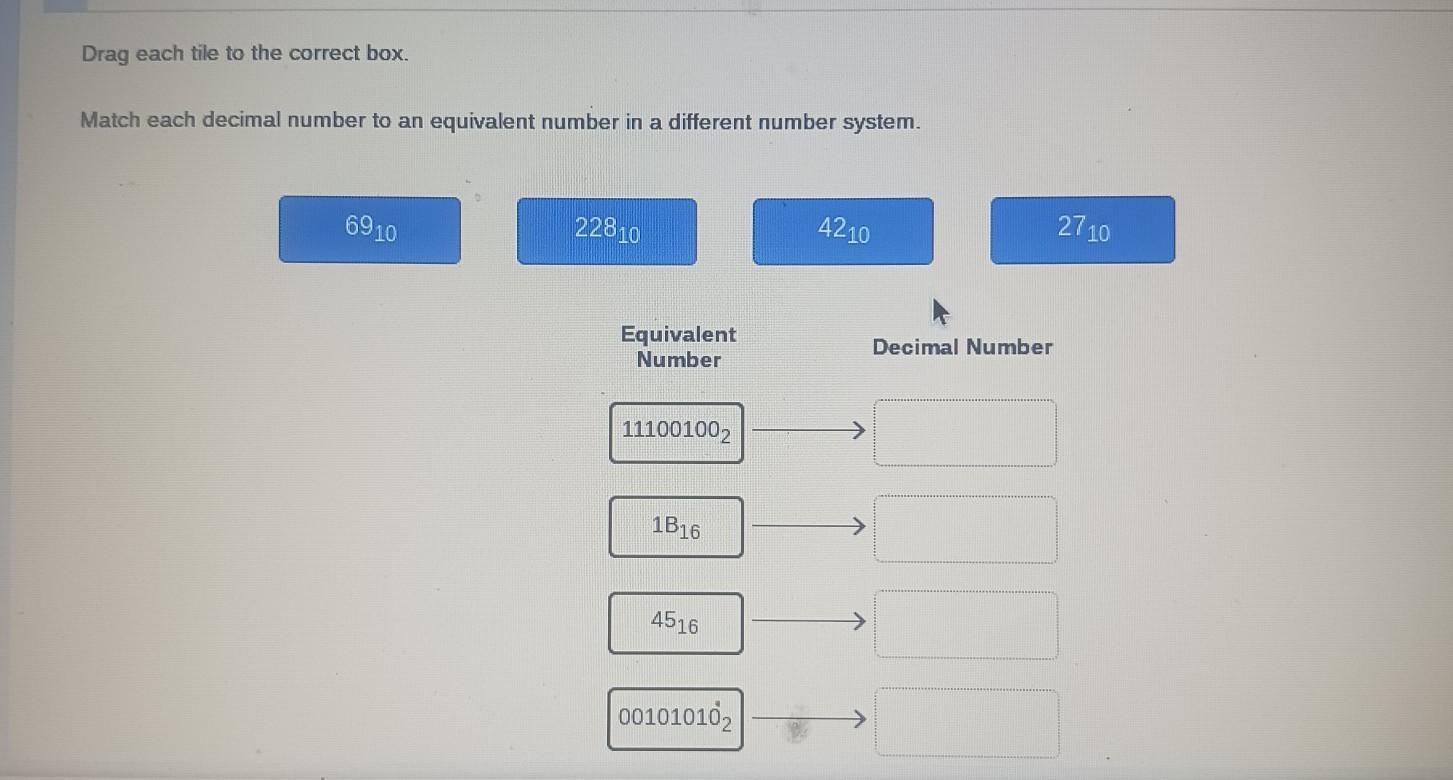
Answers
Explanation:
you can do that with calculator only

Which of the following is true about Needs Met rating tasks? Select all that apply.
True
False
Every result has both Needs Met and Page Quality sliders.
True
False
Same as... duplicate results will sometimes be pre-identified for you.
True
False
You should always assign the Needs Met rating before assigning the Page Quality rating.
True
False
Some results do not have an obvious link to a landing page.
Answers
match the cell reference to its definition
Answers
Answer:
which cell reference:-|
Answer:
absolute reference: the cell remains constant when copied or moved.
mixed reference: the cell has a combination of two other types of cell references.
relative reference: the cell changed based on the position of rows and columns.
A company is looking for an employee to assign passwords to all of its
computers to prevent sensitive information from being stolen. Which
computer field most likely includes this job?
A. Network systems administration
B. Information security analysis
C. Computer support
D. Applications development
Answers
A computer field which most likely include assigning passwords to all of its computers to prevent sensitive information from being stolen is: B. Information security analysis.
What is information security?Information security can be defined as a preventive practice which is typically used to protect an information system (IS) that use, store or transmit information, from potential theft by thieves, attack, damage, or unauthorized access, especially through the use of a body of technologies, frameworks, passwords, encryption, processes and network engineers.
In Cyber security, a computer career field that deals with assigning or allocating passwords to all the computers on a network in order to prevent sensitive information from being stolen is generally referred to as information security analysis.
Read more on security here: brainly.com/question/14286078
#SPJ1
Answer:
B. Information security analysis
Explanation:
which type of files removed by Disk Cleanup took up the most space?
Answers
The type of files that can be removed by Disk Cleanup that took up the most space are:
Temporary Internet Files groupRecycle Bin filesDoes Disk Cleanup remove all files?Disk Cleanup is known to be a process that helps to free up space on any kind of hard disk, making an improved system performance.
Note that Disk Cleanup is one that searches your disk and then depicts temporary files, Internet cache files, as well as unnecessary program files that a person can be able to safely delete.
Therefore, based on the above, one can say that The type of files that can be removed by Disk Cleanup that took up the most space are:
Temporary Internet Files groupRecycle Bin filesLearn more about Disk Cleanup from
https://brainly.com/question/26328363
#SPJ1
only evansandre2007 and elizabetharnold84 can answer
Answers
Answer:
Explanation:
Okie dokie
Have a nice day
I have a channel called Moose In A Gaming Chair what should my first video be about?
Answers
Answer:
An introduction about your self and what your channel will be about.
Explanation:
please help me c code for binary file

Answers
Below is an example implementation of the Staff Information Module in C language using binary files. (see image attached)
First, let's define the structure of our staff record:
c
typedef struct {
char id[10];
char name[50];
char password[20];
char recovery[50];
char position[20];
} StaffRecord;
What is the c code for binary file about?We will use binary files to store the staff records. Each record will occupy a fixed size of bytes, so we need to calculate the size of our structure:
c
int RECORD_SIZE = sizeof(StaffRecord);
Now, let's define some functions to manipulate the staff records:
c
void addStaff() {
StaffRecord newStaff;
// Get input from user and populate the newStaff structure
// ...
FILE *fp = fopen("staff.dat", "ab");
fwrite(&newStaff, RECORD_SIZE, 1, fp);
fclose(fp);
}
void listStaff() {
StaffRecord staff;
FILE *fp = fopen("staff.dat", "rb");
while (fread(&staff, RECORD_SIZE, 1, fp) == 1) {
// Display the staff record
// ...
}
fclose(fp);
}
void findStaff(char *id) {
StaffRecord staff;
FILE *fp = fopen("staff.dat", "rb");
while (fread(&staff, RECORD_SIZE, 1, fp) == 1) {
if (strcmp(staff.id, id) == 0) {
// Display the staff record
// ...
break;
}
}
fclose(fp);
}
void updateStaff(char *id) {
StaffRecord staff;
FILE *fp = fopen("staff.dat", "rb+");
while (fread(&staff, RECORD_SIZE, 1, fp) == 1) {
if (strcmp(staff.id, id) == 0) {
// Update the staff record
// ...
fseek(fp, -RECORD_SIZE, SEEK_CUR);
fwrite(&staff, RECORD_SIZE, 1, fp);
break;
}
}
fclose(fp);
}
void deleteStaff(char *id) {
StaffRecord staff;
FILE *fp = fopen("staff.dat", "rb+");
FILE *temp = fopen("temp.dat", "wb");
while (fread(&staff, RECORD_SIZE, 1, fp) == 1) {
if (strcmp(staff.id, id) != 0) {
fwrite(&staff, RECORD_SIZE, 1, temp);
}
}
fclose(fp);
fclose(temp);
remove("staff.dat");
rename("temp.dat", "staff.dat");
}
In the above code, we have functions to add, list, find, update, and delete staff records. The functions use binary file operations to read and write the records.
To use the functions, we can create a simple menu-driven program:
c
int main() {
int choice;
char id[10];
do {
printf("\nStaff Information Module\n");
printf("1. Add Staff\n");
printf("2. List Staff\n");
printf("3. Find Staff\n");
printf("4. Update Staff\n");
printf("5. Delete Staff\n");
printf("6. Exit\n");
printf("Enter your choice: ");
scanf("%d", &choice);
switch (choice) {
case 1:
addStaff();
break;
case 2:
listStaff();
break;
case 3:
printf("Enter staff ID to find: ");
scanf("%s", id);
findStaff(id);
break;
case 4:
printf("Enter staff ID to update: ");
scanf("%s", id);
updateStaff(id);
break;
case 5:
printf("Enter staff ID to delete: ");
scanf("%s", id);
deleteStaff(id);
break;
case 6:
printf("Exiting...\n");
break;
default:
printf("Invalid choice. Please try again.\n");
}
} while (choice != 6);
return 0;
Read more about binary file here:
https://brainly.com/question/21375195
#SPJ1
See text below
please help me c code for binary file
design and build a console-based system using C language. The requirement is to develop a system that can be used to support the operation of a small M company. The system should contain a selection of modules from the following list:
Staff Information Module - to add staff login account and maintain staff login details.
Do the structure chart design of the Staff Information Module
Example:
Tickety
Input Ticket
Ticket
Output
3 level
Trequired
Kepri
1. MODULES.
module must involve a file with at least 6 data fields. You are encouraged to add in more data fields in order to enhance the application's logic and practicality.
Examples of data fields are listed below. You may add a few of your own. For counting purposes, date and time will each be taken as one field (even though they consist of 2 or more subfields)
Staff Information Module
o Staff ID, name, password, password recovery, position, etc.
o E.g.: ST0001, Jennifer Ng, 1234, numbers, Administrator, ...
2. CONCEPTS INCORPORATED.
Each module must incorporate the following 3 programming concepts and topics that have been covered in this course:
Structures
o Include as many useful fields as you feel is necessary
o Incorporate nested structure to show your understanding.
Use Text file
o You are expected to be able to process the files correctly
(i.e. retrieve/update records).
User-Defined Functions
o Enhance efficiency, readability and re-usability by using functions whenever appropriate.
o Include parameters where appropriate and minimize/eliminate the use of global variables.




As you know computer system stores all types of data as stream of binary digits (0 and 1). This also includes the numbers having fractional values, where placement of radix point is also incorporated along with the binary representation of the value. There are different approaches available in the literature to store the numbers having fractional part. One such method, called Floating-point notation is discussed in your week 03 lessons. The floating point representation need to incorporate three things:
• Sign
• Mantissa
• Exponent
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-
point notation.
B. Determine the smallest (lowest) negative value which can be
incorporated/represented using the 8-bit floating point notation.
C. Determine the largest (highest) positive value which can be
incorporated/represented using the 8- bit floating point notation.
Answers
Answer:
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-point notation.
First, let's convert -9/2 to a decimal number: -9/2 = -4.5
Now, let's encode -4.5 using the 8-bit floating-point notation. We'll use the following format for 8-bit floating-point representation:
1 bit for the sign (S), 3 bits for the exponent (E), and 4 bits for the mantissa (M): SEEE MMMM
Sign bit: Since the number is negative, the sign bit is 1: 1
Mantissa and exponent: Convert -4.5 into binary and normalize it:
-4.5 in binary is -100.1. Normalize it to get the mantissa and exponent: -1.001 * 2^2
Mantissa (M): 001 (ignoring the leading 1 and taking the next 4 bits)
Exponent (E): To store the exponent (2) in 3 bits with a bias of 3, add the bias to the exponent: 2 + 3 = 5. Now, convert 5 to binary: 101
Now, put the sign, exponent, and mantissa together: 1101 0010
So, the 8-bit floating-point representation of -9/2 (-4.5) is 1101 0010.
B. Determine the smallest (lowest) negative value which can be incorporated/represented using the 8-bit floating-point notation.
To get the smallest negative value, we'll set the sign bit to 1 (negative), use the smallest possible exponent (excluding subnormal numbers), and the smallest mantissa:
Sign bit: 1
Exponent: Smallest exponent is 001 (biased by 3, so the actual exponent is -2)
Mantissa: Smallest mantissa is 0000
The 8-bit representation is 1001 0000. Converting this to decimal:
-1 * 2^{-2} * 1.0000 which is -0.25.
The smallest (lowest) negative value that can be represented using the 8-bit floating-point notation is -0.25.
C. Determine the largest (highest) positive value which can be incorporated/represented using the 8-bit floating-point notation.
To get the largest positive value, we'll set the sign bit to 0 (positive), use the largest possible exponent (excluding infinity), and the largest mantissa:
Sign bit: 0
Exponent: Largest exponent is 110 (biased by 3, so the actual exponent is 3)
Mantissa: Largest mantissa is 1111
The 8-bit representation is 0110 1111. Converting this to decimal:
1 * 2^3 * 1.1111 which is approximately 1 * 8 * 1.9375 = 15.5.
The largest (highest) positive value that can be represented using the 8-bit floating-point notation is 15.5.
Explanation:
how to write a code that determines if a number is odd or even?
the code should start with a variable declaration
Answers
Answer:
//code in c++
#include <iostream>
using namespace std;
int main() {
int a;
cin>>a;
if(a%2==0){
cout<<"Even number";
}
else{
cout<<"Odd number";
}
return 0;
Explanation: