which important property within an rbac custom role definition should we configure to ensure we can use the role within our own subscription?
Answers
To ensure the usability of a custom role within your own subscription in Azure RBAC (Role-Based Access Control), it is crucial to configure the "Assignable Scopes" property correctly.
The "Assignable Scopes" property determines the scope within which the role can be assigned. When defining a custom role, you need to specify the appropriate scope that aligns with your subscription. The scope can be set to the subscription level or a specific resource group. By configuring the "Assignable Scopes" property to include your subscription or the desired resource group, you ensure that the role can be assigned and used within that scope. This restriction prevents the role from being assigned outside of the specified scope, providing more granular control over access management within your own subscription.
Learn more about Configure here ; brainly.com/question/30278472
#SPJ11
Related Questions
How does decryption work?
Answers
Answer:
Decryption is the process of reversing an encryption. i.e The process which convert encrypted data into its original form
When configuring Group Policy to deploy applications, the applications must be mapped to which of the following locations?
a. UNC path
b. drive letter
c. shared folder
d. full install path
Answers
a. UNC path. When configuring Group Policy to deploy applications, the applications must be mapped to a UNC (Universal Naming Convention) path.\
A UNC path is a standardized way of specifying the location of a shared network resource. It consists of a server name and a shared folder name, identified by a double backslash (\) followed by the server name and the shared folder name. By specifying the UNC path of the application, Group Policy can distribute and install the application to the target computers on the network. This allows for centralized application management and deployment across multiple computers in an organization.
To learn more about Naming click on the link below:
brainly.com/question/14601830
#SPJ11
A Card class has been defined with the following data fields. Notice that the rank of a Card only includes the values from Ace - 10 (face cards have been removed):
class Card {
private int rank; // values Ace (1) to 10
private int suit; // club - 0, diamond - 1, heart - 2, spade - 3
public Card(int rank, int suit) {
this.rank = rank;
this.suit = suit;
}
}
A deck of cards has been defined with the following array:
Card[] cards = new Card[40];
Which of the following for loops will populate cards so there is a Card object of each suit and rank (e.g: an ace of clubs, and ace of diamonds, an ace of hearts, an ace of spades, a 1 of clubs, etc)?
Note: This question is best answered after completion of the programming practice activity for this section.
a
int index = 0;
for (int suit = 1; suit < = 10; suit++) {
for (int rank = 0; rank < = 3; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
b
int index = 0;
for (int suit = 0; suit < = 4; suit++) {
for (int rank = 0; rank < = 10; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
c
int index = 0;
for (int rank = 1; rank <= 10; rank++) {
for (int suit = 0; suit <= 3; suit++) {
cards[index] = new Card (rank, suit);
index++;
}
d
int index = 0;
for (int suit = 0; suit < = 3; suit++) {
for (int rank = 1; rank < 10; rank++) {
cards[index] = new Card (rank, suit);
index++;
}
}
Answers
Answer: b
Explanation: i did this one!!!!!!!!!!
HOW TO USE THIS IN A STORY CAN ANYONE HELP PICK % WORD FROM THE PAGE AN MAKE A STORY WHY DO I LIKE SUMMER ?????////
get 60 piont if you if you help meeeeeeeeeeee
ASAPPPPPPPPPPPPPPPPPPPPPP
The sunshine
Light mornings
Long light nights
BBQs in the garden
The smell of sun cream
Pretty wildflowers
Cloudless blue skies
Going to the beach
Feeling the warm sun on your face
Summer clothes
Sunglasses
Picnics in the park
Long walks
Sitting out on a warm evening
Eating fresh tasty salads
Drinking sangria
Orange glowy sunsets
Fresh air
Exploring new places
Ice cream (or Dairy Free alternative)
Summer playlists
Road trips
Eating fresh strawberries
Ice cold drinks on a hot day
The smell of freshly cut grass
Not having to wear a jacket when out
Autumn is just around the corner
Holidays at home or abroad
Salty sea breezes
Summer always seems to make people happier
Answers
Answer:
Picnic in the Park
Explanation:
Parks are my favorite spots to chill or go for a stroll. Parks make walking in a neighborhood more fun and offer space for common sports, promoting physical activity. They have hiking trails and other amenities to get people moving. Every place, in my opinion, needs some green space where people can get away from the crowds. I live near a park, so if the weather is good, I usually go there once or twice a week. Therefor, my favorite summer activity is going to the park.
Select the correct answer.
Terrence has five columns of numbers in a spreadsheet. He's entered formulas at the end of each column to calculate the average of the
numbers. One of the averages seems implausibly incorrect. Which TWO of the following might be causing this?
The spreadsheet software isn't working correctly.
Terrence made a mistake while entering the formula.
Terrence should have entered the numbers in rows rather than columns.
Terrence entered one or more numbers incorrectly.
A formula can calculate an average only if there's also a formula to calculate the sum.
Answers
Terence made a mistake while entering the formula.
Terence entered one or more numbers incorrectly.
Despite how well you might take care of your computer, problems can always arise. when troubleshooting problems you encounter, at what point should you engage a professional for assistance? why? at what point might you consider purchasing a new computer?
Answers
If troubleshooting problems is the one you encounter, the best thing to do is for one to get a professional to help one to see if the problem with the hardware is one that is within the computer chassis.
What is troubleshooting?Troubleshooting is known to be a form of systematic method that is often used in problem-solving that is known to help one to see and also correct issues that are linked with complex machines, electronics, computers and software systems.
Hence, If troubleshooting problems is the one you encounter, the best thing to do is for one to get a professional to help one to see if the problem with the hardware is one that is within the computer chassis.
Learn more about troubleshooting from
https://brainly.com/question/9572941
#SPJ1
What disease has presented new and more difficult problems to the public health system in recent years because of the development of drug-resistant strains of the bacteria
Answers
One disease that has presented new and more difficult problems to the public health system in recent years due to the development of drug-resistant strains of the bacteria is tuberculosis (TB).
TB is caused by the bacterium Mycobacterium tuberculosis and primarily affects the lungs. The emergence of drug-resistant TB, poses significant challenges for its control and treatment. These drug-resistant strains are resistant to the standard first-line antibiotics used to treat TB, making treatment more complex, expensive, and less effective. The spread of drug-resistant TB strains requires specialized diagnostic tests, longer treatment durations, and potentially more toxic medications. This situation highlights the importance of public health efforts to prevent the development and spread of drug-resistant bacteria through strategies such as appropriate antibiotic use, infection control measures, and surveillance programs.
Learn more about tuberculosis here;
https://brainly.com/question/29481832
#SPJ11
why is technology important to a beauty salon?
Answers
Only 2 people answer this
Answers
Answer:
2
Explanation:
The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called:________
Answers
The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called Potential GDP.
What is meant by GDP?GDP is known to be the term hat looks into or one that measures the monetary worth of final goods and services and it is one which is said to be bought by the final user.
What is Potential GDP?Potential GDP is known to be called full-employment GDP and this is said to be the maximum rate or quantity that an economy is known to be able to make or produce given full employment of its former levels of labor, physical capital, and others.
Hence, The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called Potential GDP.
Learn more about Potential GDP from
https://brainly.com/question/13824314
#SPJ1
Evaluate and select theΣdifferences between WPA and WPA2. (Select two)ANSWERSELECT ALL THAT APPLYWPA2 supports an encryption algorithm based on the Advanced Encryption Standard (AES) rather than the version of RC4 "patched" with the Temporal Key Integrity Protocol (TKIP).WPA2 is much more secure than WEP, where WPA is not. WPA2 is a security protocol developed by the Wi-Fi Alliance for use in securing wireless networks.WPA2 requires you to enter alonger password than WPA.
Answers
WPA2 should be used whenever possible since it is more secure than WPA (Wi-Fi Protected Access), which it replaced. WEP, WPA, and WPA2 are just a few of the security protocols that wireless routers can support to secure wireless networks. This analysis shows that WPA2 is the most secure of the three.
WPA
Protected Access over WiFi
a security standard created by the Wi-Fi Alliance in 2003 to take the role of the WEP protocol and be used to secure wireless networks.
WPA utilizes the same weak RC4 stream cipher that WEP does as a band-aid fix, but adds more security via TKIP.
Somewhat. better than WEP, worse than WPA2.
WPA2
Protected Access over WiFi 2
a security standard created by the Wi-Fi Alliance in 2004 to take the role of the WEP and WPA protocols for use in safeguarding wireless networks.
WPA2 employs the AES standard rather than the RC4 stream cipher, in contrast to WEP and WPA. WPA's TKIP is replaced by CCMP.
When Wi-Fi Protected Setup (WPS) is turned off, WPA2 is advised over WEP and WPA because it is more secure. Over WPA3, it is not advised.
To know more about WPA:
https://brainly.com/question/29889030
#SPJ4
anaconda is an installation program that's used by fedora, rhel, and other distributions. which of the following does anaconda perform? (select three.
Answers
Identifies the computer's hardware, Creates a file system and Provides a user interface with guided installation steps does anaconda perform.
What a user interface means?The user interface of a device is the point of interaction and communication between humans and computers. Desktop monitors, keyboards, mice, and other pointing devices may fall under this category. It also describes how a user interacts with a website or program.
The user interface is the point of interaction and communication between people and computers on a gadget, website, or app. Desktop graphics, keyboards, mice, and display screens are a few examples of this.
Thus, the options are written.
For more information about user interface, click here:
https://brainly.com/question/15704118
#SPJ1
define a class named creditcardpayment that is derived from payment. this class should contain instance variables (member variables) for the name on the card, expiration date, and credit card number. include appropriate constructor(s) and accessor/mutator methods for all instance variables. finally, redefine thepaymentdetails method to include all credit card information in the printout. override tostring() method with contents of credit payment details (should still call paymentdetails()).
Answers
To create a CreditCardPayment class, derive it from Payment and add instance variables for name on card, expiration date, and credit card number, along with appropriate constructors and accessor/mutator methods. Override the toString() method to display all credit card information.
To create the CreditCardPayment class, we can inherit from the Payment class and add the required instance variables, such as the name on the card, expiration date, and credit card number. We will also need to include constructors and accessor/mutator methods for these variables to ensure proper encapsulation.
Additionally, we can override the toString() method to display all the credit card information, while still calling the paymentDetails() method to display the transaction details. This will provide a complete overview of the payment and the associated credit card information.
For more questions like Circle click the link below:
https://brainly.com/question/19341222
#SPJ11
A separate device driver is typically present for each I/O device
A) False
B) True
Answers
A separate device driver is typically present for each I/O device. The answer is: B) True
A separate device driver is typically present for each I/O (input/output) device because each device has its own unique set of functions and operations, which requires a specific driver to communicate effectively with the computer's operating system.
The device driver is a software component that enables the operating system to communicate with the specific hardware device, and it is responsible for controlling the device's functions and operations. Each device driver is designed to work with a specific hardware device, and it provides a standardized interface that the operating system can use to interact with the device. This allows the operating system to manage and control multiple hardware devices simultaneously, each with its own device driver.
Learn more about operating system here:
https://brainly.com/question/24760752
#SPJ11
Staying at home and working using computers and telecommunications equipment is called
Answers
Answer:
telecommuting
Explanation:
12r3393938
ILL GIVE BRAINLIEST TO FIRST ANSWER David is adopting an iOS app from a non-retina screen to a retina screen. The app currently works at a pixel density of 150DPI, what density should it be on a retina screen to maintain its apparent size?
Answers
Answer: what density should it be on a retina screen to maintain its apparent size?
Discuss the importance of using appropriate tools in conducting activity in farming?
Answers
Answer:
Farm tools can be very helpful to a farmer - just like all tools they improve the efficacy of the work the farmer does, making them more productive. It all depends on the tool and the job it is matched to. There is a gap between the tools that are being sold by various and sundry purveyors and the actual need of the farmer. So far, I have found that bigger is not always better vis-a-vis big tractors and the like. We have more recently purchased lighter tractors on our farm as they work better on wet ground which is what we are dealing with in our most recent wet Springs.
Which network protocol is used to handle delivery of information
Answers
Answer:
TCP
Explanation:
TCP stands for Transmission Control Protocol a communications standard that enables application programs and computing devices to exchange messages over a network. It is designed to send packets across the internet and ensure the successful delivery of data and messages over networks.
Which tool would you use to make chart in Excel?
Answers
The Chart Tools Design tab in Microsoft Office Excel is the tool to make chart 1 resemble chart 2. The Excel program's features are essential elements that make organizing numbers and data formulas simpler and faster.
The user can choose from a variety of interchangeable charts in Microsoft Office Excel. Diagrams of the sort. The following are a few Excel charts: The charts in columns. The graphs in line. These bar graphs. Charts of the region. And a few of others. Alternate charts You may easily switch a chart's formats by using the Chart Tools Design tab. The Excel feature that may change Chart 1 into Chart 2 is the data labels. Charts use graphics to represent data components. Charts can include the following: The data label has to be made visible in order for chart 1 to resemble chart 2. The instrument that can convert Chart 1 into Chart 2 is the data lab.
Learn more about Tools Design tab here:
https://brainly.com/question/26067434
#SPJ4
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
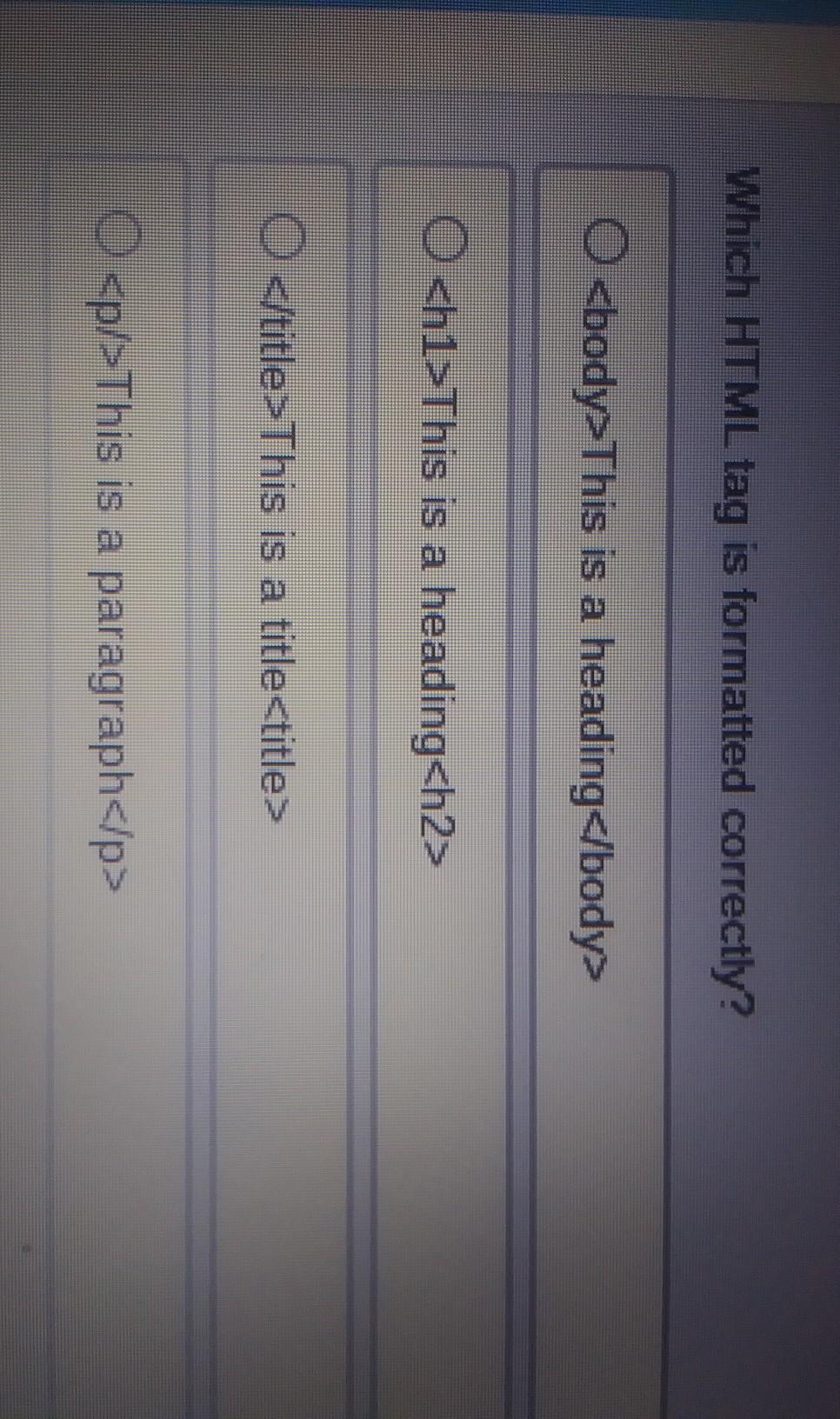
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
A film producer is having difficulty with distribution. After major and minor theaters show no interest in the film, what would the logical next move be for him to take?
release the soundtrack on compact disc
make a sequel
give up
pursue Internet distribution
Answers
Answer:
pursue internet distribution
Explanation:
Answer:
B: pursue internet distribution
Explanation:
edg2021

What mathematical functions can be solved while using python?
Answers
Answer:
Once the script is loaded into a Python code, it gives the ability to solve problems of: Nonlinear equations Differential and algebraic equations
Explanation:
Once the script is loaded into a Python code, it gives the ability to solve problems of: Nonlinear equations Differential and algebraic equations
If you type =5*3 into a cell, what do you expect the answer will be?
A. 5*3
B. 15
C. E3
D. 8
Answers
Answer:
I think 15
what do you mean by cell
Explanation:
Answer:
15
Explanation:
right on edge
what method is used to access subsets of information? group of answer choices filtering conditional formatting logging sorting
Answers
The technique is used to access subsets of information is called "filtering."
Explain the term filtering?A filter is indeed a program or portion of code used in computer applications that checks each output or input request for a set of qualifying criteria before processing or forwarding it.
Using software or hardware that screen and/or restrict access to problematic emails, websites, executables, and other questionable objects is a technique known as content filtering. Content-based filtering, sometimes referred to as information filtering, is frequently used by businesses as a component of the internet firewalls. Content filtering, a typical security solution, enables businesses to carry out corporate regulations that govern the use of information systems, such as screening and preventing employee access to social networking platforms.Filtering software can check content for anything offensive or illegal, including social media, hate sites, and illegal content.Thus, filtering is the technique is used to access subsets of information.
To know more about the filtering, here
https://brainly.com/question/13129235
#SPJ4
Software as a Service refers to
software that you put on your computer.
software you can access using any device.
a server.
a web browser.
Answers
Answer:a,b,d,e
Explanation: The other top ones are right but it's a multiple choice answer
Type the program's output.
#include
using namespace std;
int main()
{
int numCats;
numCats = 6;
if (numCats > 8) {
cout << "a" << endl;
}
else {
cout << "f" << endl;
}
cout << "k" << endl;
return 0;
}
Answers
The program's output is "f" followed by "k" on a new line.
The program starts by declaring an integer variable named numCats and assigning it a value of 6. Then, it checks if numCats is greater than 8 using an if statement. Since numCats is not greater than 8, the code inside the if block is not executed. Instead, the code inside the else block is executed which prints "f" to the console followed by an endline character.
After the if-else statement, the program prints "k" to the console followed by an endline character. Finally, the main function returns 0, indicating successful program execution.
Therefore, the program outputs "f" and "k".
Know more about program outputs here:
https://brainly.com/question/19088371
#SPJ11
what is the answer of this Q?

Answers
Answer:
Because of refraction.
Explanation:
Light coming from fish passes through two medium, one is water and another is air. As the density of medium is changing from high to low, the light bends away from the normal. So to the human eyes, the fish appears to be above its actual position.
Light rays reflected from the fish are refracted at the surface of the water, but the eyes and brain trace the light rays back into the water as thought they had not refracted, but traveled away from the fish in a straight line. This effect creates a "virtual" image of the fish that appears at a shallower depth.
why wont my chromebook stay charging while im using it
Answers
Answer:
Explanation:
Well, it is probly because your chromebook is broken or the carger and/or is it working when you are not using it?
Which term describes the process of training a machine to do simple, repetitive
tasks, and adapt or correct its performance based on changing conditions at
speed and scale?
Intelligent Automation
O Robotic Process Automation
O Machine Learning
O Personal Automation
O I don't know this yet.
Answers
Robotic Process Automation (RPA) is the term that describes the process of training a machine to do simple, repetitive tasks and adapt its performance based on changing conditions at speed and scale.
Robotic Process Automation (RPA) refers to the use of software robots or "bots" to automate repetitive tasks within business processes. RPA involves training these bots to perform simple, rule-based tasks that were previously carried out by humans.
These bots can interact with various software applications, mimic human actions, and adapt their performance based on changing conditions. RPA allows organizations to automate routine and mundane tasks, increase efficiency, reduce errors, and achieve scalability.
While RPA focuses on process automation, it does not necessarily involve advanced cognitive capabilities like machine learning. RPA is widely used in various industries and sectors to streamline operations and optimize resource utilization.
Learn more about RPA here: brainly.com/question/28914209
#SPJ11
Reggie is having trouble signing into his email account at work. He picks up the phone to call someone in IT, and then checks the phone list to see who to call. Which IT area should Reggie call
Answers
The IT area that Reggie should call is called; Information Security
What are the functions of an Information Technology Department?The IT department that Reggie should call is called Information Security department.
This is because Information security protects sensitive information from unauthorized activities such as inspection, modification, recording, and any disruption or destruction.
The aim of this department is to make sure that the safety and privacy of critical data such as customer account details, financial data or intellectual property are safe.
Read more about information technology at; https://brainly.com/question/25920220