Which company specializes in working behind the scenes to meet advertiser’s cpm guarantees by tagging users to create consumer profiles, but is not an ad network?
Answers
Browser, software that enables a computer user to search for and see information on the Internet.
Web browsers interpret HTML elements in downloaded documents and format the displayed data in accordance with a set of style rules. A website is a collection of publicly accessible, interconnected Web pages that use the same domain name. Individuals, groups, businesses, and organizations can construct and maintain websites for a variety of objectives. OTS is a possible exposure of an advertising message to one audience member. Also known as a marketing impression. engaging with consumers. Any advertiser who invests in digital interactivity should be prepared to maintain contact with their target audiences.
Learn more about software here-
https://brainly.com/question/29946531
#SPJ4
Related Questions
a loop will always be executed at least once. question 2 options: a) posttest b) user-controlled c) pretest d) conditional
Answers
A posttest loop will always be executed at least once.
What does a Python posttest loop do?
A posttest loop is one in which the block is to be iterated through until the required condition is satisfied, and then the result is tested.A loop that executes an after-each-iteration condition testOne or more times the loop is executed. 2. Loops following tests • Verifying the halting condition after the loop's body has been executed. •What exactly are the pre- and post-test loops?
Both loops can be be divided into pre-test and post-test loops for further classification. An end condition is checked in a pre-test loop before each repetition, whereas a post-test loop checks the end condition after each repetition.Because the for loop is a pretest loop, each iteration begins with an evaluation of the test expression.Learn more about posttest loop
brainly.com/question/28099182
#SPJ4
outline 4 IDE features that makes software development much faster and more convenient than other alternatives.
Answers
Answer:
IDEs can let you code without internet.
Explanation:
1. you can code without wifi.
2. it combines common developer tools into 1 GUI (grafic user interface).
3. it gives a warning about memory leaks.
4. it can correct synaxes.
Hope This Helps! :)
here have a good day
Answers
offers a simple, secure, and automated way to migrate your nas data from any source-destination to any target destination, in the cloud or on your premises.
Answers
Our solution offers a simple, secure, and automated way to migrate your NAS data from any source-destination to any target destination, whether in the cloud or on your premises.
To know more about migrate data from source to destination
https://brainly.com/question/30144789?
#SPJ4
A NAS data migration service offers a simple, secure, and automated way to migrate your NAS data from any source destination to any target destination, whether it's in the cloud or on your premises.
This allows for efficient data transfer and storage management to meet your specific needs. Data refers to any information or set of information that can be stored, processed, and analyzed by a computer. It can take many different forms, such as text, numbers, images, audio, and video. Data is essential for businesses, governments, researchers, and individuals to make informed decisions and to gain insights into various phenomena.
Data can be collected through various sources, such as surveys, sensors, and social media, and it can be stored and organized using databases or file systems. Once data is collected, it can be processed and analyzed using various tools and techniques, such as statistical analysis and machine learning, to derive meaningful insights and predictions.
In today's digital age, data is an increasingly valuable asset, and there are many ethical and legal concerns around its collection, use, and sharing. With the rise of big data and artificial intelligence, data is poised to play an even greater role in shaping the world around us.
Learn more about Data here:
https://brainly.com/question/21927058
#SPJ11
What is Communication
Answers
Give an example of computing circumstances that would favor first-fit allocation over best-fit. Explain your answer.
Answers
In computing, many processes may need to use the CPU and the CPU would have to make the decision on which process it would allocate its resources to.
First ft memory allocation is a method where the CPU allocates its resources to a process first to a memory location that has free space that is equal to or more than its size
Best ft memory allocation is a method where the CPU allocates its resources to the best available process with space with the smallest free partition that is considered adequate and it is slower than first fit.
One example of computing circumstances that would favor first-fit allocation over best-fit is when a memory partition is allocated to a process that has similar memory space.
Read more here:
https://brainly.com/question/14120703
Made from zinc and copper, brass has been manufactured for thousands of years. It is used in weapons, pipes, musical instruments, and many other important ways. Which of these words best describes brass?.
Answers
Brass has been manufactured for thousands of years and has a wide range of uses, including in weapons, pipes, musical instruments, and many other important applications.
It is known for its strength, durability, and corrosion resistance, as well as its ability to be molded, shaped, and worked into a variety of different forms.
What is Brass?
Brass is a metallic alloy. An alloy is a mixture of two or more elements, at least one of which is a metal. Alloys are typically made by combining different metals in specific proportions to create materials with specific properties and characteristics. Brass is an example of an alloy that is made from the metals zinc and copper.
To learn more about corrosion resistance, visit: https://brainly.com/question/13926854
#SPJ4
someone help me please and thank you

Answers
The Creative Commons license allows creators to specify how others can use their work.
It offers options for attribution, non-commercial use, share-alike, and no-derivative works to protect intellectual property and encourage collaboration. See further explanation below.
What is the rationale for the above response?Attribution: Someone might want to use this part of the Creative Commons license because it ensures that they receive credit for their work. This is important for creators who want recognition for their efforts and to be acknowledged for their intellectual property. By requiring attribution, creators can also prevent others from taking credit for their work.
Non-Commercial: Someone might want to use this part of the Creative Commons license to prevent others from using their work for commercial purposes. This may be important for creators who do not want their work to be used in advertisements or to be sold for profit. By limiting commercial use, creators can maintain control over their work and ensure that it is being used in accordance with their values.
Share-Alike: Someone might want to use this part of the Creative Commons license to encourage collaboration and innovation. By requiring users to share any new versions of the work under the same license, creators can ensure that their work remains open and accessible to others. This can promote creativity and encourage others to build upon existing work.
No Derivative Works: Someone might want to use this part of the Creative Commons license to protect the integrity of their work. By prohibiting changes to the work, creators can maintain control over how their work is presented and ensure that it is not altered in a way that they do not approve of. This can be important for creators who are concerned about how their work is being used and want to maintain control over its message.
Learn more about Creative Commons at:
https://brainly.com/question/29247019
#SPJ1
please help me very important
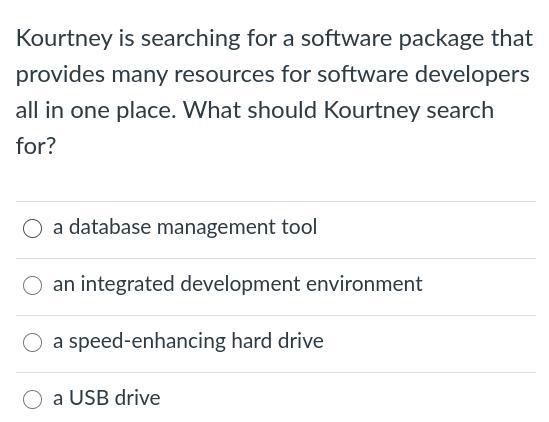
Answers
Answer:
C, Or D.
Explanation:
Because A speed enhancing hard drive Can store any type of quick file if you just click on it will load fast. Same thing goes for a hard drive but you have to transfer the file
differenticate between half and full deplex modes of transmission in three points
Answers
Answer:
In simplex mode, the signal is sent in one direction. In half duplex mode, the signal is sent in both directions, but one at a time. In full duplex mode, the signal is sent in both directions at the same time.In simplex mode, only one device can transmit the signal. In half duplex mode, both devices can transmit the signal, but one at a time. In full duplex mode, both devices can transmit the signal at the same time.Full duplex performs better than half duplex, and half duplex in turn performs better than simplex.Hope it helps!
Read the following scenario:
A musical production is in development. The production will air live on television, and the performers are scheduled to rehearse the day before the event. As equipment is being set up, one of the grips discovers that a gel kit is missing. Which is the most likely course of action in this scenario?
The grip will work with the lighting designer to re-set the lights.
The grip will consult with the gaffer who will track down the missing kit.
The grip will double-check the equipment with the gaffer who, if the kit is still missing, will coordinate with the best boy to track it down.
The grip will review the inventory to make sure the kit was included in the equipment, then consult with the best boy.
Answers
Answer:
The grip will double-check the equipment with the gaffer who, if the kit is still missing, will coordinate with the best boy to track it down.
Explanation:
100% right on edge 2021
in what ways do researchers attempt to control extraneous variables?
Answers
In experimental research, extraneous variables are factors that can potentially influence the dependent variable but are not of interest to the researcher. These variables can impact the validity of the study, making it difficult to identify the true effects of the independent variable.
To control extraneous variables, researchers employ various strategies such as randomization, standardization, and matching. One of the primary methods for controlling extraneous variables is through randomization. This involves randomly assigning participants to groups so that extraneous variables are equally distributed among the groups. This method ensures that any effects observed are due to the independent variable and not any confounding variables.
This involves using standard procedures for measuring and manipulating variables to minimize any potential biases.Matching is another technique that researchers use to control extraneous variables. This involves selecting participants based on certain characteristics such as age, gender, or education level so that they are similar across groups.
To know more about factors visit:
https://brainly.com/question/31931315
#SPJ11
python fundamentals 2.4 code practice question 1
write the code to input a number and print the square root. use the absolute value function to make sure that if the user enters a negative number, the program does not crash.
sample run: -16
sample output : 4.0
Answers
Answer:
import math
inputNumber = float(input('Please input a number'))
inputNumber = abs(inputNumber)
print(math.sqrt(inputNumber))
Explanation:
hey GSPAULING! lets do some PYTHON and PYTHON is epic because its logo has those python looking things. theres one thats blue and one thats yellow you know what im talking about right? ANYWAYS LETS WRITE SOME CODE
First how do we start?We need an input statement right?inputNumber = int(input('Please input a number'))
ok so the line above which starts with "input" is the first line of our code, it's gonna ask the user for a number and the number will become the variable called "inputNumber" and it will be an integer type of variable, right?
and now the absolute value function is: abs()
so lets incorporate that in the next line
inputNumber = abs(inputNumber)
so now the negative numbers are going to be turned into positive numbers.
ok but now lets not forget to import the math module, you should actually put this line at the very beginning:
import math
ok now we can find the square root of the inputNumber variable and print it:
print(math.sqrt(inputNumber))
so the final program will be as follows:
import math
inputNumber = float(input('Please input a number'))
inputNumber = abs(inputNumber)
print(math.sqrt(inputNumber))
Which of the following problems associated with storing data in a list is avoided by storing data in a relational database?
A) Maintaining the data may require changing the same data value in many locations.
B) Inconsistency when a data item is used multiple times
C) Inability to store partial data
D) Duplication of data items
E) All of the above
E) All of the above
Answers
Storing data in a relational database avoids all the mentioned problems associated with storing data in a list. Thus, Option E, All of the above, is correct.
What is a relational database?A relational database is a data storage structure that uses multiple tables to store data. Each table contains rows and columns, with each row representing a unique record and each column representing a unique field.
Relational databases are the most prevalent type of database used in industry because they are effective at storing and managing structured data, which is data that can be easily organized into tables with distinct columns and rows.
They are made up of multiple tables that are related to one another in some way. Relational databases use a structured query language (SQL) to communicate with the database. SQL is a standard language that is used to access, manipulate, and query relational databases.
Option E is correct.
Learn more about relational database https://brainly.com/question/13262352
#SPJ11
If the start index is __________ the end index, the slicing expression will return an empty string.
Answers
Answer:
"Greater than."
Explanation:
The designated end of a string cannot be reached from the start. For example, if you had a list labeled 'colors' (colors = [1,2,3,4]) and then you tried to bring back that list using colors[1:0], you will recieve an empty string. However, if the starting is lower than the final index, then your program will run. For example, if you use colors[0:1], you will be given the output: [1].
what command must be entered to configure an ip address of 192.168.10.3 and subnet mask of 255.255.255.0 for a switch?
Answers
IP address 192.168.99.2 255.255.255.0 is the command must be entered to configure an IP address of 192.168.10.3 and a subnet mask of 255.255.255.0 for a switch.
What is IP address?The IP address of a device can be used to identify it on the internet or within a local network. The term "Internet Protocol," or IP, refers to the standards that specify how data is conveyed through a local or wide-area network or the internet.
IP addresses are essentially the identifier that allows information to be transmitted between devices on a network as they carry location information and make devices reachable for communication. On the internet, there needs to be a way to distinguish between computers, routers, and web pages. IP addresses, which are essential to how the internet functions, offer a way to do this.
An IP address is made up of a string of integers separated by commas. In order to represent IP addresses, four numbers are used; The range of each number in the set is 0 to 255. Therefore, the complete IP addressing range is 0.0.0.0 to 255.255.255.255.
To learn more about IP address visit:
https://brainly.com/question/16011753
#SPJ4
Select the correct answer.
Linda is making handouts for her upcoming presentation. She wants the handouts to be comprehensible to people who do not attend her
presentation. Which practice should Linda follow to achieve this goal?
OA.
OB.
OC.
OD.
provide a summary of the presentation
make the handouts more image-oriented
speak in detail about each topic
provide onlya printout of the slideshow
Can someone please help me with this class b4 I lose my mind
Amos: xoxo_11n
Answers
Answer:
OA
Explanation:
I took this quiz
What is an accessor in Java?
A
It's how Java accesses databases.
B
It's what Java classes use to get access to disk files.
C
It's a method that retrieves information from private class attributes.
D
It's a means of accessing the names of attributes in a class.
Answers
In microsoft access, when you have the field name firstname display as first name, you are changing what field property?.
Answers
In Microsoft access, when you have the field name firstname display as first name, you are changing the "Caption" property.
What is a field in access?
There are fields in every table in Access. The traits and behavior of data entered into a field are described by the field's properties.
The data type of a field controls the types of data that can be stored in that field, making it the most significant feature. A field might contain details about the employee, such as their name, the date they were hired, or their social security number.
To learn more about a field in access, use the link given
https://brainly.com/question/25266819
#SPJ4
html & css design and build websites by jon duckett
Answers
HTML and CSS are the fundamental building blocks of websites. Jon Duckett’s “HTML & CSS Design and Build Websites” is an excellent resource for both beginners and experienced developers.
The book is divided into three main sections. The first section introduces the basics of HTML and CSS. It covers topics such as text formatting, links, images, tables, forms, and CSS layout techniques. The second section goes into more detail about web design principles, including color, typography, and layout. The third section covers advanced topics such as responsive design and accessibility.
One of the great things about this book is that it uses real-world examples to demonstrate how to apply the concepts you learn. This makes it easy to see how you can use HTML and CSS to create beautiful and functional websites.
In conclusion, “HTML & CSS Design and Build Websites” is an excellent resource for anyone who wants to learn HTML and CSS. It is easy to read, visually appealing and provides practical examples that you can use to build your own websites. The book is also available in an online format, which makes it easy to access from anywhere.
To learn more about the website.
brainly.com/question/26959627
#SPJ11
15 points please help!!!!
David works at a company that provides financial solutions. He wants to create an interactive presentation for his company. Which interactive platforms can David use for this presentation?
David can use an interactive or a for his presentation.
Answers
Answer:
Powerpoint presentation
Explanation:
Powerpoint presentation is a part of Microsoft office that is established by Microsoft. PowerPoint. It is used to present the company visions, missions, key points in a short and in an attractive way by using the various designs, pictures, audio clips, etc
Here David wants to create an interactive presentation so he should use the powerpoint presentations so that he could present the company visions, objectives, etc
Imagine you're planning a wedding, and you need to transport all your wedding guests from the ceremony to the reception. A bus can carry 40 passengers. Please write a program to input the names of the bride(s) and groom(s), and how many guests are coming to the wedding. Then output the names of the couple, followed by how many buses are needed, and the number of extra people you could carry with those buses (empty seats)
Answers
To begin with, let's start by writing a program that can take in the necessary inputs and perform the calculations we need.
bride = input("Enter the name(s) of the bride(s): ")
groom = input("Enter the name(s) of the groom(s): ")
guests = int(input("Enter the number of guests attending the wedding: "))Next, we need to calculate how many buses we will need to transport all the guests. Since each bus can carry 40 passengers, we can divide the total number of guests by 40 and round up to the nearest integer to get the number of buses required. We can do this using the math.ceil() function, like so:
import math
buses_needed = math.ceil(guests/40)Finally, we need to calculate how many extra people we can carry with those buses. To do this, we can subtract the total number of guests from the number of buses times 40. If the result is positive, that means we have some extra seats on the buses that we can fill with additional guests. If the result is negative, that means we don't have enough buses to transport everyone. We can do this using a simple calculation, like so:
extra_seats = (buses_needed * 40) - guestsNow that we have all the necessary information, we can output it to the user using the print() function, like so:
print("Wedding details:")
print("Bride(s): " + bride)
print("Groom(s): " + groom)
print("Number of guests: " + str(guests))
print("Number of buses needed: " + str(buses_needed))
print("Extra seats: " + str(extra_seats))And that's it! With this program, you can easily calculate how many buses you need to transport your wedding guests and how many extra people you can carry with those buses. Good luck with your wedding planning!
For such more questions on Python
https://brainly.com/question/28675211
#SPJ11
From Edmentum/Plato
You may be familiar with rubrics used for grading at your school. Take the idea of a rubric and create your own grading or evaluation form based on what you think is important for employers to evaluate about their employees. You may use online resources to gain a better understanding of work-based evaluation forms and rubrics to support your answer
Answers
Answer:
Given below is an example of an evaluation form for a workplace. It consists of various parameters that an employer would ideally consider when evaluating an employee’s work performance during a specific period, such as six months or a year. While evaluating an employee, an employer could circle or make a check mark on the following scales:
5 (excellent)
4 (good)
3 (average)
2 (below average)
1 (poor)
Parameters Excellent Good Average Below Average Poor
Appearance/Grooming 5 4 3 2 1
Attendance 5 4 3 2 1
Communication Skills 5 4 3 2 1
Coordination 5 4 3 2 1
Initiative 5 4 3 2 1
Working in a group 5 4 3 2 1
Creativity 5 4 3 2 1
Problem-solving Ability 5 4 3 2 1
Punctuality 5 4 3 2 1
Overall Work Attitude 5 4 3 2 1
Explanation: edmentum answer
Which step creates a connection between a file and a program?
Answers
The step that creates a connection between a file and a program is to open the file. Thus, Option A is correct.
When a program needs to access a file, it first needs to establish a connection with the file by opening it. This involves identifying the file's location and obtaining permission to access it. Once the file is open, the program can then read its contents, process the information, and write to the file if needed.
After the program has finished working with the file, it should close the connection to release any system resources being used and ensure that any changes made to the file are saved. Opening and closing files correctly is an important aspect of programming and can help prevent errors and ensure data integrity.
Based on this explanation, Option a is correct.
The complete question:
Which step creates a connection between a file and a program?
a. Open the file.b. Read the file.c. Process the file.d. Close the file.Learn more about program https://brainly.com/question/16397886
#SPJ11
what type of fuzzer requires the user to give it predefined inputs? generation fuzzer mutation fuzzer protocol-based fuzzer
Answers
A generation fuzzer requires the user to give it predefined inputs.
In fuzz testing, there are three main types of fuzzers: generation fuzzers, mutation fuzzers, and protocol-based fuzzers. A generation fuzzer creates test data from scratch based on predefined inputs or rules specified by the user. This type of fuzzer is more suitable for situations where the input format is well-defined and understood. On the other hand, mutation fuzzers modify existing test data to create new test cases, while protocol-based fuzzers focus on testing communication protocols.
Among the three types of fuzzers mentioned, it is the generation fuzzer that requires predefined inputs from the user to generate test data.
To know more about fuzzer visit:
https://brainly.com/question/20314591
#SPJ11
HERES A RIDDLE!!
What is more useful when it’s broken??
Answers
Answer:
an egg
Explanation:
Select the correct answer.
If a user clicks on the hyperlink generated by the following code, where will the web browser redirect the user?
Click here to go to first table
A.
a web page called “table1”
B.
a website with the search tag “table1”
C.
an element on the same page with the id “table1”
D.
a paragraph on the same page with the text “table1”
Answers
Answer:
A.
Explanation:
The hyperlink will send you whatever the link was.
Consider the following method, which is intended to return true if at least one of the three strings s1, s2, or s3 contains the substring "art".; Otherwise, the method should return false.
public static boolean containsArt(String s1, String s2, String s3)
{
String all = s1 + s2 + s3;
return (all.indexOf("art") != -1);
}
Which of the following method calls demonstrates that the method does not work as intended?
Select one:
a. containsArt ("rattrap", "similar", "today")
b. containsArt ("start", "article", "Bart")
c. containsArt ("harm", "chortle", "crowbar")
d. containsArt ("matriculate", "carat", "arbitrary")
e. containsArt ("darkroom", "cartoon", "articulate")
a. containsArt ("rattrap", "similar", "today")
This is because the "art" is found as a combination of "similar" and "today". That is not as intended based upo
Answers
There are several ways to manipulate strings; this includes concatenating and iterating through strings.
The method call that does not work as intended is: (a) containsArt ("rattrap", "similar", "today")
From the question, we understand that the method would return true if any of s1, s2 and s3 contain the string "art"
From the list of given options, none of the strings in the method call (a) contains "art". i.e. "rattrap", "similar" and "today" do not contain "art"
But the method call would still return true.
When "rattrap", "similar" and "today" are concatenated on the first line of the method, the new string "rattrapsimilartoday" contains "art".
Hence, the method call that does not work as intended is: (a) containsArt ("rattrap", "similar", "today")
Read more about strings at:
https://brainly.com/question/16024994
There are several ways to manipulate strings; this includes concatenating and iterating through strings.
The method call that does not work as intended is: (a) containsArt ("rattrap", "similar", "today")
From the question, we understand that the method would return true if any of s1, s2 and s3 contain the string "art"
From the list of given options, none of the strings in the method call (a) contains "art". i.e. "rattrap", "similar" and "today" do not contain "art"
But the method call would still return true.
When "rattrap", "similar" and "today" are concatenated on the first line of the method, the new string "rattrapsimilartoday" contains "art".
Hence, the method call that does not work as intended is: (a) containsArt ("rattrap", "similar", "today")
Read more about strings at:
brainly.com/question/16024994
you are completing a network installation as part of a team. another group has cabled wall ports to a patch panel. is any additional infrastructure required?
Answers
No, additional infrastructure is not required if the wall ports have been properly cabled to a patch panel.
When wall ports are connected to a patch panel, it creates a centralized location for network connections. The patch panel acts as an intermediary between the wall ports and the networking equipment, such as switches or routers. It allows for easier management, organization, and maintenance of network connections.
By cabling the wall ports to a patch panel, the network installation team ensures that the physical connectivity is established correctly. Once the connections are made, the networking equipment can be connected to the patch panel, enabling communication between devices on the network. As long as the patch panel is properly installed and functioning, no additional infrastructure is required for the network installation.
You can learn more about patch panel at
https://brainly.com/question/31131663
#SPJ11
The library is purchasing Argus TL2530P All-In-One Thin clients. What does it mean that the thin clients are 802.3at compliant?
Answers
In this set up, the servers are workstations which perform computations or provide services such as print service, data storage, data computing service, etc. The servers are specialized workstations which have the hardware and software resources particular to the type of service they provide.
1. Server providing data storage will possess database applications.
2. Print server will have applications to provide print capability.
The clients, in this set up, are workstations or other technological devices which rely on the servers and their applications to perform the computations and provide the services and needed by the client.
The client has the user interface needed to access the applications on the server. The client itself does not performs any computations while the server is responsible and equipped to perform all the application-level functions.
Each server handles a smaller number of thin clients since all the processing is done at the server end. Each server handles more thick clients since less processing is done at the server end.
Learn more about server on:
https://brainly.com/question/29888289
#SPJ1