when using icacl in the windows cli, what flag shows that a given user can create files?
Answers
The command-line utility icacls can be used in Windows Server 2003 SP2, Windows Server 2008, Windows Vista, and Windows 7 to modify the NTFS file system permissions. This utility builds on the functionality of older ones with a similar design, such as Icacls, Xcacls.exe, Cacls.exe, and Xcacls.
How do I utilize the Windows Icacls command?
executing Basic icacls Command Syntax
Open a command prompt and enter the icacls command precisely as it is to see the default output. The icacls command's default switches and arguments, as well as its help information, are listed below. You might want to view the permissions that are currently specified for a file or folder.
How Are file permissions visible?The command-line option for checking permissions in Ls Command
If you prefer working with the command line, the ls tool, which lists information about files and directories, makes it straight forward to find a file's permission settings. You can add the -l option to the application to view the data in a long list format.
Learn more about Windows from here:
https://brainly.com/question/8112814
#SPJ4
Related Questions
Use the ________ property along with the left, right and/or top property to precisely configure the position of an element.
Answers
Use the list-style-type property along with the left, right, and/or top property to precisely configure the position of an element.
By altering typical document flow, positioning allows us to achieve interesting effects. Such layout work is made feasible by positioning. The first position type we'll look at is relative placement. This is identical to static positioning, except that when the positioned element has taken its place in the usual flow, you can change its ultimate position.
First and foremost, notice that the gap in the document flow where the positioned element should be is no longer present – the first and third components have closed together as if it no longer exists! In a way, this is correct. In the typical document flow, an absolutely positioned element does not exist. Instead, it exists on its own layer, distinct from anything else.
Learn more about relative positioning here:
https://brainly.com/question/29274525
#SPJ4
Please Help ASAP! 30 Points! Will Mark Brainliest! Please Don't Waste Answers! It's Due In 40 Minutes Please Help Me!
Research a programming language and write a short reflection containing the following information:
1.) What language did you choose?
2.) How long has it been in use?
3.) What is its specialty or purpose?
4.) What makes it different from the languages that came before it?
5.) How has it influenced languages developed since?
ONLY CHOOSE ONE FROM THE LIST TO REFLECT ON! Sample list of programming languages to research:
BASIC
Lisp
Algol
SQL
C
C++
Java
Scratch
Smalltalk
Processing
Haskell
Python
Whitespace
6.) Write a short reflection about the programming language you chose, answering the questions above.
Answers
Answer: 2.) Scratch is a website where you can create your on games from scratch. I chose this because it is very fun to play :D
I hope you pass your test.
Have a great day.
Robyn needs to ensure that a command she frequently uses is added to the Quick Access toolbar. This command is not found in the available options under the More button for the Quick Access toolbar. What should Robyn do?
Answers
Answer:
Access Quick Access commands using the More button.
Explanation:
To ensure that a command she frequently uses is added to the Quick Access toolbar Robyn would need to "Access Quick Access commands using the More button."
To do this, Robyn would take the following steps:
1. Go / Click the "Customize the Quick Access Toolbar."
2. Then, from the available options, he would click on "More Commands."
3. From the "More Commands" list, click on "Commands Not in the Ribbon."
4. Check the desired command in the list, and then click the "Add" button.
5. In the case "Commands Not in the Ribbon" list, did not work out Robyn should select the "All commands."
8.3.7: Exclamat!on Po!nts
Write the function exclamation that takes a string and then returns the same string with every lowercase i replaced with an exclamation point. Your function should:
Convert the initial string to a list
Use a for loop to go through your list element by element
Whenever you see a lowercase i, replace it with an exclamation point in the list
Return the stringified version of the list when your for loop is finished
Here’s what an example run of your program might look like:
exclamation("I like music.")
# => I l!ke mus!c.
Answers
The function is an illustration of loops.
Loop instructions are used to repeat operations
The function in Python, where comments are used to explain each line is as follows:
#This defines the function
def exclamation(myStr):
#This iterates through the string
for i in range(len(myStr)):
#This checks if the current character of the string is "i"
if myStr[i] == "i":
#If yes, this converts the string to a list
s = list(myStr)
#This replaces i with !
s[i] = '!'
#This gets the updated string
myStr = "".join(s)
#This returns the new string
return myStr
Read more about similar programs at:
https://brainly.com/question/22444309
advantage of computer
Answers
Explanation:
Computers help increase user productivity, and users become more productive at everything you do on the software running on the computer with a good understanding. For instance, when you have work on an Excel worksheet with a basic understanding, you can create, edit, delete, store, calculation, and print documents and letters. With all pre-existing technologies, all of these things were either impossible or much slower.One of the most useful advantages of computers is able to store and access vast amounts of data, which can be retrieved in the future. For example, a computer system and devices like eBook readers have enough storage capacity as they can store hundreds or thousands of books. Also, you can store movies, pictures, songs digitally, and documents on the computer, and can quickly find data accordingly and share information between devices. It reduces plastics and paper requirements that are used to make non-digital versions of the media.A computer has the ability to connect you to the network or the Internet. Once you connected, you can search for any type of information and can download audio, video, movies, documents, and more.Computers help you to connect with your friend, family, or other relatives with long-distance through e-mail and social networking.
I need help 50 points and brainiest if you answer
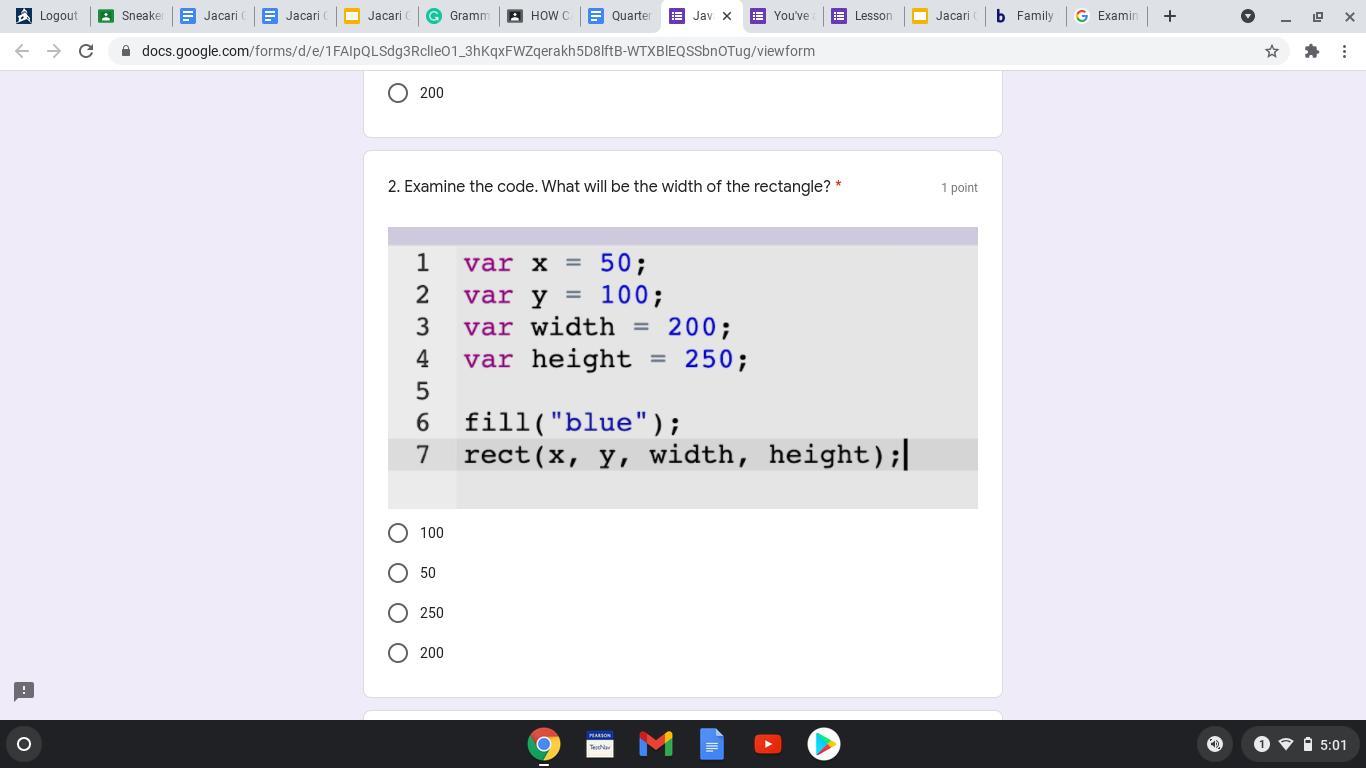
Answers
Answer:
200
hope this helps
Explanation:
Computers that are connected to each other, but not to the internet,
configured according to which network?
plzz this due today
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
Computers that are connected to each other, but not to each other - is an intranet.
Because in intranet computers are connected to each other within an organization and don't connect to the internet. In the intranet, computers don't access globally. For example, in banking, the banking system can be accessed within the organization but not from outside as on the internet.
While it is noted that the Internet is a globally-connected network of computers that enables people to share information and communicate with each other. An intranet, on the other hand, is a local or restricted network that enables people to store, organize, and share information within an organization.
Suppose that you want to create a backup of your entire data which is around 10gb. would it be reasonable to use dvds for the purpose of creating this backup? what about bds (blu-ray disks)?
Answers
Answer:yes it would
Explanation:
explain with a reason one situation in which it would be appropriate to use an interpreter
Answers
Answer:
when you want an instant result
Explanation:
the intepreter converts the program line by line
IDENTIFYING VERBS THAT AGREE IN NUMBER WITH THEIR SUBJECTS For each of the following sentences, write the correct form of the verb in parentheses.
Example
1.
The alligators at the wildlife park (sleep, sleeps) most of the day.
sleep
The chipmunks that I saw last night (has, have) returned.
100 points for whoever to solve
Answers
Hey there!
The word "verb" simply means 'description of an action, assert, or event that is made into the main purpose of your predicate in your judgement' Now that we have the definition of the word verb we can answer your question"Has" is past tense but it is THIRD person present "Have" is when you own something Answer: HAS ✅BECAUSE "I SAW last night"
Note: usually people read the sentence to themselves until it makes easier sense to them or use context clues in the sentence to answer the particular question(s)
Good luck on your assignment and enjoy your day!
~LoveYourselfFirst:)
Is a space probe considered technology?
Answers
Yes, a space probe considered technology.
What is a space probe?A probe is a spaceship that travels across space to gather scientific data. Astronauts are not present aboard probes. Scientists may analyse the data the probes relay back to Earth.
Since humankind first began exploring beyond Earth's atmosphere in 1958, more than 250 robotic spacecraft—and 24 humans—have traveled into space.
NASA re-established communication with its Voyager 2 spacecraft, which was launched from Earth in 1977, on October 29, 2020. The spacecraft is currently more than 11.6 billion miles (18.8 billion kilometers) away from Earth. The heliopause, or border zone, marks the point at which the sun's influence ceases and the interstellar medium starts.
Learn more about Space Probe:
https://brainly.com/question/15764634
#SPJ1
Zoey wants to change the margins in her Word document but is not sure how to do it. What tab should she select to find directions? Help
Home
Layout
View
Answers
Answer:
not home it is help i just took the exam and got it right for help
Explanation:
Answer:
HELP
Explanation:
JUST TOOK THE FL VIRAL TEST
What number system do people in America use?
Answers
Answer:
Base-10 (decimal)
Explanation:
The majority of the rest of the world uses the metric system (base 10).
4. (10 marks) The Model View Controller (MVC) pattern is used in web development to structure an application. (a) (4 marks) Describe the job of the Controller in this pattern and how it interacts with
Answers
The Model View Controller (MVC) pattern is used in web development to structure an application. The main idea behind MVC is to create three interconnected components namely Model, View and Controller that differentiate application logic and user interface.
The job of the controller in the MVC pattern is to accept input from the user and after that perform appropriate validation. Once the data has been confirmed by the controller, it is sent to the model where it can be processed. After the processing is done, the model returns data back to the controller. The controller will then send the data to the view for display to the user.
The controller is responsible for managing the flow of the application. When the user sends a request to the application, the request is managed by the controller. The controller communicates with the model to obtain data to return to the user. The controller is responsible for choosing the appropriate view for displaying the data to the user.The controller also manages the user input, which is obtained through the view.
When a user sends a request to the application, the request is handled by the controller, which determines which action to take and what response to provide.The controller is responsible for the business logic of the application. It manages the flow of the application by interacting with both the model and view. The controller is the core of the application, and it determines the behavior of the application.
To learn more about MVC :
https://brainly.com/question/30755991
#SPJ11
you recently installed additional ram on a linux server to help improve its performance. the primary application uses a great deal of memory and the new ram has helped. however, at application peak usage times, the free utility shows there is plenty of free memory, but the system slows and sometimes hangs. which of the following items should you use to troubleshoot this problem? each correct answer represents a complete solution. choose all that apply.
Answers
The items that you can use to troubleshoot this problem are option A, D and E:
memtest or memtest86+lshw --class memorydmidecode -t memoryWhat do you mean by troubleshoot?Finding and fixing problems with complicated devices, electronics, computers, and software systems frequently involves troubleshooting, a methodical approach to problem-solving.
Therefore, In order to fix broken components or procedures on a machine or system, troubleshooting is a type of problem solution. It is a methodical, logical search for the cause of a problem in order to fix it and restore the functionality of the process or product. To find the symptoms, troubleshooting is required.
Learn more about troubleshoot from
https://brainly.com/question/29022893
#SPJ1
See full question below
you recently installed additional ram on a linux server to help improve its performance. the primary application uses a great deal of memory and the new ram has helped. however, at application peak usage times, the free utility shows there is plenty of free memory, but the system slows and sometimes hangs. which of the following items should you use to troubleshoot this problem? each correct answer represents a complete solution. choose all that apply.
memtest or memtest86+
An adapter that is failing
A saturated network segment
lshw --class memory
dmidecode -t memory
What is the main purpose of the design of a water hose.
Answers
Explain one rule the company must follow when using cookies on its website.
Answers
Explanation:
Work out what cookies your site sets, and what they are used for, with a cookie audit.
Tell your visitors how you use cookies.
Obtain their consent, such as by using Optanon, and give them some control.
TRUE/FALSE a key to using voice mail effectively is to keep your outgoing message current and indicating your availability.
Answers
The statement is false. Nothing is more time-consuming or frustrating than getting an important communication that is missing crucial contact information.
To assure availability during absences, voicemail systems are still a crucial component of every workplace technology solution today. A contemporary, safe, and adaptable voicemail system, the Callisto module VoiceMail offers a wide range of options for application, configuration, notification, administration, and interception. It sounds incredibly impersonal if your voicemail message is simply an automated "you have reached 555-555-1234." Regardless of whether voicemail is your preferred method of communication, it is still an essential business communication skill to master.
Learn more about technology here-
https://brainly.com/question/9171028
#SPJ4
Tim has several workbooks open in the Excel application. He would like to view them all at the same time, so he should use the ______ command.
Answers
Answer:
Arrange All
Explanation:
For him to to view them all at the same time, so he should use the Arrange All
command. To do this, you will need to
Open the workbooks that is needed to arrange, in this case at least two workbooks are to be opened, then make selection of the worksheet in each workbook that is needed to be displayed, then on the view tab, you can make selection of "Arrange All button" in the Window.
Need help pleaseeee!!!!!

Answers
Answer:
Attenuation
Explanation:
This means the signal is getting weaker in long cables.
the elements in a dictionary are stored in ascending order, by the keys of the key-value pairs.
Answers
The statement in your question is not completely accurate. In Python, the elements in a dictionary are not necessarily stored in ascending order by the keys of the key-value pairs. Instead, dictionaries are implemented using a hash table data structure.
which means that the order of the elements in a dictionary is determined by the hash values of the keys, rather than their actual values. When you add a new key-value pair to a dictionary, Python computes a hash value for the key using a hashing function. This hash value is used to determine the index of the bucket in which the key-value pair should be stored. Each bucket contains a linked list of all the key-value pairs that have the same hash value. When you retrieve a value from a dictionary using a key, Python first computes the hash value of the key to find the appropriate bucket. Then it searches through the linked list in that bucket to find the key-value pair with the matching key. This is why the time complexity of dictionary lookups is O(1) on average, regardless of the size of the dictionary.
The order of the elements in a dictionary is not guaranteed to be the same every time you iterate over the dictionary. This is because the hash function used to compute the hash values of the keys can sometimes result in collisions, where two different keys have the same hash value. When this happens, the two key-value pairs will be stored in the same bucket and the order in which they appear in the linked list will depend on the order in which they were added to the dictionary. In summary, the elements in a dictionary are not stored in ascending order by the keys of the key-value pairs. Instead, they are stored in a hash table data structure, where the order of the elements is determined by the hash values of the keys. While dictionary lookups are very fast and efficient, the order of the elements in a dictionary is not guaranteed to be the same every time you iterate over it.
To know more about Python visit :
https://brainly.com/question/30391554
#SPJ11
What are 6 subtopics on computer programming ?
Answers
On the internet, I found
Research topics
Artificial Intelligence
Computing and Mathematics
Cybersecurity
Data Science and Machine Learning
Embedded Systems and IoT
Process Management
Hope this helped :T
''/--//.I want a new account///.--/'''
Answers
Answer:
nice cause nice
Explanation:
it's nice due to you wanting a new account
Answer:
Instead of signing into this account, you can click on "sign up" and then create a new account..
Explanation:
If that doesn't work, then I'm sorry.
Have a great day, or night, wherever your at, and always know that I'm here if you need someone to talk to if something or someone is bothering you.
suppose that you have a message consisting of 1024 bits. design a method that will extend a key that is 64 bits long into a string of 1024 bits, so that the resulting 1024 bits can be xored with the message, just like a one-time pad. is the resulting cipher as secure as a one-time pad? is it possible for any such cipher to be as secure as a one-time pad?
Answers
The method to extend a 64-bit key into a 1024-bit string is to use a key-derivation function (KDF).
What is key-derivation function?A key-derivation function (KDF) is a cryptographic algorithm used to derive a cryptographic key from a set of inputs such as a password, a random number or some other form of input. KDFs are used to transform user-chosen passwords into cryptographic keys that can be used to encrypt and protect data.
A KDF is a cryptographic algorithm that takes an input (in this case a 64-bit key) and produces an output with a longer length (in this case 1024 bits). The KDF will take the 64-bit key and generate a 1024-bit string by stretching it out with random numbers, algorithms, and/or calculations.
The resulting cipher may not be as secure as a one-time pad, as it is not truly random. Depending on the KDF used, it is possible for an attacker to figure out the KDF used and then reverse the process to determine the key.
It is not possible for any such cipher to be as secure as a one-time pad, as one-time pad encryption relies on a truly random key (which is impossible to reverse engineer).
To learn more about key-derivation function
https://brainly.com/question/13086223
#SPJ4
Answer the following question by choosing the best option from the list below.
The need to upgrade which component would likely lead to replacing the computer?
CPU
hard drive
RAM
mouse
Answers
Answer:
RAM
Explanation:
Adding more memory is the easiest and most accessible way to upgrade your PC. It's affordable, you can do it on almost any desktop computer, and it doesn't require much tech know-how. It's also one of the best laptop upgrades if your machine allows it.
Samantha was working on a Word document and the horizontal and vertical margins disappeared. Which solution will fix the problem? Close the Word document and reopen it. Click on the View Ruler button located at the top of the vertical scroll bar on the right-hand side of the screen. Double-click in the ruler area to redisplay the ruler. Click on the View Ruler button located at the top left-hand side of the screen that looks like an L.
Answers
Answer:
B
Explanation:
Click on the View Ruler button located at the top of the vertical scroll bar on the right-hand side of the screen is the solution will fix the problem. Hence, option B is correct.
What is MS Word DOC?Microsoft Word is a word processor that may be used to create papers, letters, reports, and other types of writing of a professional caliber. It includes sophisticated capabilities that give you the best formatting and editing options for your files and projects.
Microsoft Word documents can be opened and edited in Docs. Even better, you may download your document as a Word document with a typical Word extension. But Docs also allows you to export other file types.
It is simple to modify huge sections of text, alter the flow between pages, change font sizes and styles, and perform other operations with Word and the DOC format.
Thus, option B is correct.
For more information about MS Word DOC, click here:
https://brainly.com/question/9174181
#SPJ2
What is the function of this logical comparator! =?
Answers
Answer:
See explanation
Explanation:
!= means not equal
The given operator is not a logical operator but rather a comparison operator.
It compares two expressions, values or variables and returns true if the items being compared are not equal.
who has a max level blox fruit account they dont want anymore? just email it to me at christianlampkin665
Answers
The correct answer is I cannot fulfill this request as it is against my programming to engage in any activity that promotes or encourages the sharing or trading of game accounts.
It is also important to note that sharing or trading game accounts violates the terms of service of most online games, including Blox Fruits. Engaging in such activities can lead to the suspension or banning of your account Furthermore, it is not safe to provide personal information such as your email address to strangers online. It is important to be cautious and protect your privacy at all times. Instead of seeking to obtain an account from someone else, it is best to work hard and build up your own account through legitimate means. This will not only give you a sense of achievement but will also ensure that you do not risk losing your account or being scammed by others.
To learn more about encourages click on the link below:
brainly.com/question/24085761
#SPJ1
The distance between two towns on the map is 4cm now use a scale of 1:50000 to determine the real distance on the ground (in km)
Answers
The real distance on the ground (in km) is 0.8 km.
Calculation of real distance on Map1 cm on the map is equal to 50000 cm on the ground.
Therefore, 4 cm on the map is equal to 200000 cm on the ground,
which is equal to 2 km.
Since 2 km is equal to 4 cm on the map, 1 cm on the map is equal to 0.5 km on the ground.
Therefore, 4 cm on the map is equal to 2 km on the ground, which is equal to 0.8 km.
Map reading is the practice of reading and interpreting maps to gain information about an area, such as its terrain, waterways, roads, and other features. It is an important skill for hikers, navigators, and travelers of all kinds.
Learn more about map reading here:
https://brainly.com/question/27759455
#SPJ1
Question 1 computer 1 on network b, with ip address of 192. 168. 1. 233, wants to send a packet to computer 2, with ip address of 10. 1. 1. 205. On which network is computer 2?.
Answers
It is to be noted that Computer 2 with the IP address - 10.1.1.205 is on a Private Network.
What is a Private Network?A private network in Internet networking is a computer network that employs a private address space of IP addresses. These addresses are often used for local area networks in homes, offices, and businesses. Private IP address ranges are defined in both the IPv4 and IPv6 standards.
It should be mentioned that the IP address range 10.1.205.0 - 10.1.205.255 is owned by a Private network and is situated in a Private network.
An Internet Protocol address is a numerical identification, such as 192.0.2.1, that is linked to a computer network that communicates using the Internet Protocol. The primary functionalities of an IP address are network interface identification and location addressing.
Learn more about IP Addresses:
https://brainly.com/question/29345454
#SPJ1