When packets arrive at their destination at different speeds, they sometimes arrive out of order. what does this cause?
a. jitter
b. latency
c. dropped packets
d. error rates
Answers
What cause based on the question is a. Jitter. Jitter is the variation in time between arriving data packets, caused by network congestion, or route changes. The longer the data packet is sent, the more jitter will affect the audio and network quality.
Standard jitter measurement in milliseconds (ms). If you receive a jitter higher than 15-20ms, it can increase latency and result in packet loss, causing a decrease in audio quality. Symptoms of jitter include:
Audio is intermittent Call pending or disconnectedStatic, intermittent, or garbled audioIf the test results show the Jitter rating is higher than 15-20ms, there is most likely a problem with the Internet Service Provider (ISP). If the test cannot be plugged directly into the modem, the ISP should be able to run the test. If they run into a jitter problem in the end, they should be able to solve it.
Learn more jitter https://brainly.com/question/13661659?
#SPJ4
Related Questions
Can you solve this challenging activity?

Answers
Answer:
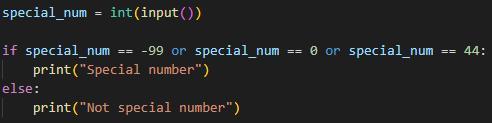
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
Cross peoples father chops just disappear with the advent of manufacturing today some manufacturing jobs are disappearing in favor of digital solutions what parallel can you draw between these two phenomena guns
Answers
Both the disappearance of manual labor jobs in manufacturing and the decline in the use of hand-chopped firewood can be seen as consequences of technological advancements and increased automation.
What is Automation?
Automation refers to the use of technology to perform tasks that would otherwise require human intervention. This can be achieved through the use of machines, software, or algorithms that are designed to perform specific tasks without the need for direct human involvement.
Automation has been widely adopted in industries such as manufacturing, transportation, and finance, as it allows for greater efficiency, speed, and cost savings. However, it can also result in job loss and the need for workers to acquire new skills to adapt to changing job markets.
To learn more about Automation, visit: https://brainly.com/question/28530316
#SPJ1
What does Spam mean in tech
Answers
Answer:
Spam is digital junk mail. They are unsolicited communications sent in bulk over the internet or through any electronic messaging system. For example, when you text someone "hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi hi" they will tell you "stop spamming!"
Answer:
Spam means Digit Junk Mail in tech context.
Explanation:
Spam is digital junk mail: unsolicited communications sent in bulk over the internet or through any electronic messaging system. It is unsolicited bulk messages, spamming is the act of sending these messages, and a person who engages the practice is a spammer. Most of the time, spamming is commercial in nature, and though the spam is bothersome, it isn’t necessarily malicious or fraudulent (though it can be).
What can you do to make a positive digital footprint for yourself? pls hurry due at 12:30 PM Group of answer choices Post only once a day. Adjust your privacy settings to control who sees your posts. Use only apps that make pictures and posts disappear. Share as much as you can with your best friends.
Answers
Answer:
Share as much as you can with your best friends.
Explanation:
Positive Digital footprint is a term that simply defines as a positive reputation or impression an internet user leave behind online or other online users' positive perception of such user, often in an online discussion group or social media website in general. This includes positive content such as comments, posts, and shares posted by the users or tagged by other users.
Hence, to make a positive digital footprint, a user should "share as much as s/he can with his/her best friends." This will make such users leave a positive digital footprint because often than not, it is always happy moments and subjects such users will be sharing.
/* howManyBits return the minimum number of bits required to represent x in
*
two's complement
*
Examples:
howManyBits (12) = 5
*
howManyBits (298) = 10
*
howManyBits (-5) = 4
howManyBits (0) = 1
*
howManyBits (-1) = 1
*
howManyBits (0x80000000) = 32
* Legal ops: ~ & ^ | + << >>
* Max ops: 90
* Rating: 4
*/
int howManyBits (int x) {
int n = 0;
X = X ^ (x >> 31);
n = n + ((!! (x >> (n + 16))) << 4);
n = n + ((!! (x >> (n + 8))) << 3);
n = n + (( !! (x >> (n + 4))) << 2);
n = n + ((!! (x >> (n + 2))) << 1);
n = n + ((!! (x >> (n + 1))));
n = n + (x >> n);
return n + 1;
}
Answers
The C function given in the question is an implementation of a function named howManyBits that takes an integer x as input and returns the minimum number of bits required to represent x in two's complement. The implementation takes advantage of bit-wise operations and relies on bit shifting and Logical operations to compute the number of bits required to represent the input value in two's complement.
The function first initializes a variable n to 0 and then sets x to be equal to the bit-wise exclusive OR of x and x right shifted by 31 bits. This is done to make sure that all the bits in x are positive, which is required to represent the value in two's complement notation.Next, the implementation uses a series of logical operations to compute the number of bits required to represent the input value. Specifically, it shifts x by n + 16, n + 8, n + 4, n + 2, and n + 1 bits and then uses the double exclamation mark operator to check if the result is non-zero. If the result is non-zero, the implementation adds the corresponding value to n.
Finally, the implementation shifts x by n bits, adds 1 to n, and then returns n.The implementation uses a total of 12 operations to compute the number of bits required to represent the input value. The maximum number of operations allowed is 90. Therefore, the implementation is quite efficient and works well for a variety of inputs, including positive and negative integers as well as zero.
To know more about Logical operations visit :
https://brainly.com/question/13382082
#SPJ11
The function howManyBits takes the input number x and returns the minimum number of bits required to represent x in two's complement.
How to explain the informationHere's a code example in Python that implements this logic:
import math
def howManyBits(x):
# Check if x is negative
is_negative = False
if x < 0:
is_negative = True
x = abs(x)
# Convert x to binary representation
binary = bin(x)[2:]
# Count the number of bits required
num_bits = len(binary)
# Add 1 additional bit if x is negative
if is_negative:
num_bits += 1
return num_bits
# Example usage
x = -10
bits_required = howManyBits(x)
print(bits_required) # Output: 5
Learn more about program on
https://brainly.com/question/26642771
#SPJ4
Next, Leah wants to add a content slide that allows her to insert a table.
Which tab should she click to complete this action? Home
What should Leah click to open a dialog box to select the slide she needs? New Slide down arrow
What should Leah do to access the notes pane of the slide she added? V Click Notes expander.
Multi media design
Answers
Answer:
1. Home
2. New slide down arrow
3. Click Note expander
Explanation:
Home tab should she click to complete this action.
The New Slide down arrow should Leah click to open a dialog box to select the slide she needs.
Click Notes expander should Leah do to access the notes pane of the slide she added.
What is a content slide?A collection of polished presentation templates is called the Presentations Content Slides. The site provides stunning infographics and PowerPoint illustrations that are laid out in a bullet point structure. Regardless on how many evaluation tools are provided, the main layout is one to three.
Select the button next to "New Slide" on the Home tab. Choose the layout visitors want and a new slide from the layouts collection.choose "New Slide" Make your layout selection in the New Slide dialogue box for any new slide. Study slide layouts in more detail.You can add extra information to presentations that doesn't show up on slides in the Notes pane.Learn more about content slide, here:
https://brainly.com/question/4214795
#SPJ6
If the Transaction file has the following 3 records:
Trans Key
D1
B1
A1
What will the value of Total be after execution of the program?
a) 9
b) 10
c) 8
d) 6
e) 7
Answers
It is to be noted that "If the Transaction file has the following 3 records:
Trans Key D1, B1, A1, the value of Total be after execution of the program will be 7 (Option E).
What is a transaction file?A transaction file is used to store data while a transaction is being processed. The file is then used to update the master file and audit transactions on a daily, weekly, or monthly basis. In a busy supermarket, for example, daily sales are logged on a transaction file and then utilized to update the stock file.
Master files are indestructible. Transaction files exist just for the duration of the transaction and are thereafter deleted. Here are some examples of transaction files:
Purchase orders, work cards, invoice dispatch notes, and so forth
Learn more about Transaction File:
https://brainly.com/question/14281365
#SPJ1
How do the existence of the intranet and extranet help businesses (List 5 benefits of intranet and 5 of the extranet).
Answers
Answer:
An intranet is a private - internal - business network that enables your employees to share information, collaborate, and improve their communications. An extranet enables your business to communicate and collaborate more effectively with selected business partners, suppliers and customers.
_______________________ determines how to structure a supply chain, including the product, selection of partners, the location and capacity of warehouse, transportation methods, and supporting management information systems.
Answers
Supply chain design determines how to structure a supply chain, including the product, selection of partners, the location and capacity of warehouses, transportation methods, and supporting management information systems.
Key aspects of supply chain design include:
Product Design: Determining the characteristics of the product and its packaging, which can impact transportation, storage, and handling requirements.
Partner Selection: Identifying and selecting suppliers, manufacturers, distributors, and other partners in the supply chain network based on their capabilities, reliability, and compatibility with the overall supply chain strategy.
Network Configuration: Determining the number, location, and capacity of warehouses, distribution centers, and production facilities to optimize inventory management, transportation costs, and responsiveness to customer demand.
Transportation Strategy: Selecting appropriate transportation modes, such as trucking, rail, air, or sea, and deciding on the routing and scheduling of shipments to ensure efficient and timely delivery.
Information Systems: Implementing management information systems, such as enterprise resource planning (ERP) systems, supply chain planning tools, and real-time tracking systems, to enable visibility, coordination, and decision-making across the supply chain.
Learn more about Supply chain here:
https://brainly.com/question/28165491
#SPJ11
The first computer available for commercial sale in the United States was made by Mauchly and Eckert in what year?
1974
1947
1940
1951
Answers
Answer:
1951
Explanation:
The people who perform jobs and tasks are part of which factor of production?
A.land
B.scarcity
C.capital
D.labor
Answers
The people who perform jobs and tasks are part of Labor.
What is Labor?The procedure by which the placenta and fetus depart the uterus is called labor. Vaginal delivery (via the birth canal) and cesarean delivery (surgery) are the two possible methods of delivery.
Continuous, increasing uterine contractions during labor help the cervix widen and efface (thin out). The fetus can now pass through the birth canal as a result.
Typically, two weeks before or after the anticipated birth date, labor begins. However, it is unknown what precisely starts labor.
Therefore, The people who perform jobs and tasks are part of Labor.
To learn more about Labor, refer to the link:
https://brainly.com/question/14348614
#SPJ2
how could the seven-segment display driver be designed using a 4-to-16 decoder and logic gates rather than multiplexers?
Answers
A digital combinational logic circuit known as a digital or binary decoder can change one kind of digital code into another.
A particular decoder called a BCD to 7-segment display decoder may change binary coded decimals into a format that can be easily viewed on a 7-segment display. Four binary weighted address inputs (A0 to A3) are decoded to produce sixteen mutually exclusive outputs (Y0 to Y15). The device has two inputs that are input enable (E0 and E1). The outputs are forced to be HIGH when either input is HIGH. In order to break down any combination of inputs into a set of terms that are all set to "0" except for one term, decoders are just a group of logic gates that are organized in a specified fashion.
Learn more about input here-
https://brainly.com/question/13014455
#SPJ4
why can’t the pm use the organization’s current information system for project monitoring and reporting?
Answers
PM needs to provide regular updates to stakeholders who require concise and actionable information. In such cases, the PM may have to invest in a dedicated system that is specifically designed for project monitoring and reporting.
There are several reasons why the project manager (PM) may not be able to use the organization’s current information system for project monitoring and reporting. These reasons are discussed below:Lack of Compatibility:One of the primary reasons why the PM may not be able to use the organization’s current information system is due to a lack of compatibility between the system and the project’s requirements.
The current system may not have the necessary features or functions to monitor and report on the project’s progress. As such, the PM may have to invest in a new system that is specifically designed for project monitoring and reporting.Cost:The cost of purchasing and implementing a new system can be a significant obstacle for many organizations. Even if the current system is not suitable for the project’s needs, the organization may be unwilling or unable to invest in a new system.
To know more about stakeholders visit:-
https://brainly.com/question/30241824
#SPJ11
d) Describe how instance variables of reference type are handled differently from variables of primitive type when passed as method arguments in Java. Outline the problem that this difference raises and explain the facility Java offers to overcome it. Explain the operation of a static method. How does it differ from an instance method?
Answers
Java is an object-oriented programming language that can handle variables of primitive and reference types.
In this context, Java treats variables of primitive types differently from instance variables of reference types when passed as method arguments in Java.
Primitive type variables are passed by value, while reference type variables are passed by reference. When a variable of primitive type is passed as a method argument, its value is copied, and the copied value is sent to the method. As a result, changes made to the value inside the method do not affect the original value of the variable in the calling code.
In contrast, when an instance variable of reference type is passed as a method argument, the reference to the object it points to is passed. As a result, changes made to the object inside the method affect the original object in the calling code.
The main problem with passing instance variables of reference type is that it can lead to unintended side effects and make the code harder to understand. Java offers the facility of copying the reference itself, not the object, through the use of the clone() method. This method returns a new object that is a copy of the original object, allowing changes to be made to the copy without affecting the original.
A static method is a method that belongs to a class rather than an instance of the class. It can be called without creating an instance of the class and is useful when we need to perform a specific operation that does not depend on the state of the instance variables.
On the other hand, an instance method is a method that belongs to an instance of a class and can only be called on an instance of the class. The operation of an instance method depends on the state of the instance variables.
Learn more about Java program: https://brainly.com/question/26789430
#SPJ11
What can handle work that is hard on a person and could cause repetitive injuries?
Answers
The robot which can handle work that is hard on a person and could cause repetitive injuries is a: Cobot.
Artificial intelligence (AI) is also referred to as machine learning and it can be defined as a branch of computer science which typically involves the process of using algorithms to build a smart computer-controlled robot or machine that is capable of performing and handling tasks that are exclusively designed to be performed by humans or with human intelligence.
A cobot is an intelligent robot that is designed and developed to perform and handle work that may be too hard (difficult) and hazardous for a person or could cause repetitive injuries to him or her.
Read more: https://brainly.com/question/21656851
1. What are the benefits of being skillful in making simple electric gadgets?
2. How can you be safe while working on a simple gadget project?
Answers
The benefits of being skillful in making simple electric gadgets is that due to your skill used in creating the gadget, it can help people to do their work more easily and fast.
One can be safe while working on a simple gadget project by wearing safety goggles or gloves if need be.
What are electronic gadgets?Electronic gadgets are known to be a kind of appliances that is said to function based on technology or the use of electronic technology.
Note that In simple gadget such as a calculator, it is known to be an electronic gadget that help one to calculate bigger amount easily and fast
Learn more about gadget from
https://brainly.com/question/1162014
All the rage these days, although not great for astronomical observatories or airports is 5G intemet. How energetic is this 30 GHz radiation? O A 1.99 x 10-23 O 8.199 1023 OC 1.99 x 10-32 O 0.1.99 x 1032 ) O E 1.99 J m I
Answers
The energy of 30 GHz radiation is about (A) \(1.99 * 10^{-23\) joules per photon, which is about 1000 times less energetic than visible light.
5G internet uses millimeter waves (MMWs) with frequencies ranging from 30 to 300 GHz. This type of radiation is non-ionizing, which means it doesn't have enough energy to remove electrons from atoms or molecules. The energy of MMWs is much lower than that of ionizing radiation, such as X-rays or gamma rays. The energy of 30 GHz radiation is about \(1.99 * 10^{-23\)joules per photon, which is about 1000 times less energetic than visible light.
Although MMWs are not harmful to humans, they are affected by obstacles and atmospheric conditions, which can cause signal attenuation and interference. This can be a challenge for 5G networks, which require a large number of small cell sites to provide seamless coverage in urban areas. MMWs are also absorbed by moisture in the atmosphere, which can limit their range and effectiveness.
Learn more about 5G :
https://brainly.com/question/29533919
#SPJ4
you can use tables for layout work. However, in XHTML, each form control should have its own ______ element
a. method
b. textarea
c. label
d. fieldset
Answers
Answer:
c. label
Explanation:
The database designer creates a(n) _______ when no suitable single-column or composite primary key exists.
natural key
master key
artificial key
foreign key
Answers
The database designer creates an artificial key when no suitable single-column or composite primary key exists.
So, the correct answer is C.
An artificial key, also known as a surrogate key, is a unique identifier that has no inherent meaning or relationship to the data it represents. It is used to ensure uniqueness in a table and simplify database management.
Unlike natural keys, which are derived from the data itself, artificial keys are system-generated and serve as a reference for linking records across tables.
They are essential in maintaining data integrity, and their use is often preferred when natural keys or composite keys cannot provide the necessary uniqueness for the primary key constraint.
Hence, the answer of the question is C.
Learn more about database at https://brainly.com/question/22920087
#SPJ11
matt, a senior technician, has installed a switch for the purpose of identifying devices on the lan. analyze which of the following addressing methods matt should follow so that the switch can quickly and efficiently direct the network traffic to its destination.
Answers
Since Matt, a senior technician, has installed a switch for the purpose of identifying devices on the lan. The addressing methods that Matt should follow so that the switch can quickly and efficiently direct the network traffic to its destination is option A: MAC address.
What is MAC address?This is seen as an exclusive identification code given to a network interface controller to be used as a network address in communications inside a network segment is called a media access control address. Ethernet, Wi-Fi, and Bluetooth are just a few of the IEEE 802 networking technologies that frequently employ this application.
Therefore, in context of the above question, If a switch's mac address table does not contain the destination mac address, it floods the frame to all ports other than the receiving port.
Learn more about MAC address from
https://brainly.com/question/13267309
#SPJ1
See full question below
Matt, a senior technician, has installed a switch for the purpose of identifying devices on the LAN. Analyze which of the following addressing methods Matt should follow so that the switch can quickly and efficiently direct the network traffic to its destination.
Transport layer ports
MAC address
IP address
Application layer domain
what does it mean that the right mouse button is context-sensitive?
Answers
Answer:
What does it mean that the right mouse button is "context-sensitive"? The menu items available will differ depending on the context of what you are right-clicking . You would like to add some frequently used buttons to the Quick Access Toolbar
Explanation:
which two groups represent major trading blocks in europe?
Answers
Major trading blocks play a significant role in facilitating trade and economic cooperation between countries. In Europe, two important groups represent such trading blocks.
The European Union (EU): The EU is a political and economic union consisting of 27 member countries. It promotes a single market, allowing for the free movement of goods, services, capital, and people between member states. The EU is considered one of the largest and most powerful trading blocks in the world.The European Free Trade Association (EFTA): The EFTA is a regional trade organization consisting of four member countries: Iceland, Liechtenstein, Norway, and Switzerland. While not part of the EU, these countries enjoy access to the European single market through bilateral agreements, promoting trade and economic cooperation with EU countries.In Europe, the European Union (EU) and the European Free Trade Association (EFTA) represent two major trading blocks that facilitate trade and economic cooperation among their member countries.
To learn more about European Union, visit:
https://brainly.com/question/3387326
#SPJ11
What is the output?
id_list = [13, 984, 231, 140]
for id in id_list:
if id != 231:
print(id, end=' ')
else:
print('Done')
Answers
The output of the given code in this problem is determined to be:
13 984 Done 140.
How to Determine the Output of a Code?The code iterates through each element in the id_list. If the element is not equal to 231, it prints the element followed by a space.
If the element is 231, it prints "Done". In this case, the elements 13, 984, and 140 are printed, and when the loop encounters 231, it prints "Done" instead.
Therefore, the output will be: 13 984 Done 140.
Learn more about Output of a Code on:
https://brainly.com/question/30772469
#SPJ4
what is meant by internet surveillance?....ONLY ANSWER IF YOU KNOW
Answers
Answer:
As a brief definition, Internet surveillance refers to your computer and online activity, online and offline data, and Internet traffic being monitored and logged by government agencies, ISPs, and – potentially – cybercriminals.
Explanation:
can I have brainliest
Answer: I LIKE EM BIG AND JUCIY
Explanation:
why was CDR the most developed country in nepal. Highlight any six reasons
Answers
Answer:
6 reasons are highlighted under explanation.
Explanation:
The 6 reasons why CDR region is the most developed in Nepal are as follows;
1) The capital city of Nepal which is named Kathmandu lies in the CDR region.
2) The residents of this CDR region are usually provided with adequate employment facilities.
3) Majority of the industries in Nepal were established in this CDR region.
4) Social facilities which include education and health care are adequately provided in this CDR region.
5) Due to the the many industries, employment facilities and social facilities, this region generates a great amount of the the trade of the country and therefore aids in increasing the size of the economy.
6) There are quite a lot of tourists and religious locations in this region which aids in bringing tourism to the country.
What is a font? A)
a typeface on a label
B) a typeface on a poster
C) a typeface on a computer or d) a typeface on a sign
Answers
Answer:
A is most likely the answer
Explanation:
Page orientation is determined in Microsoft Word from the __________ tab
Answers
Answer:
Page orientation is determined in Microsoft Word from the Page Layout tab.
Explanation:
The Page Layout Tab holds all the options that allow you to arrange your document pages just the way you want them. You can set margins, apply themes, control of page orientation and size, add sections and line breaks, display line numbers, and set paragraph indentation and lines.
your company purchases several windows 10 computers. you plan to deploy the computers using a dynamic deployment method, specifically provision packages. which tool should you use to create provisioning packages?
Answers
To create provisioning packages for deploying Windows 10 computers using a dynamic deployment method, you should use the Windows Configuration Designer tool.
Windows Configuration Designer (formerly known as Windows Imaging and Configuration Designer or Windows ICD) is a powerful graphical tool provided by Microsoft to create provisioning packages. It allows you to customize and configure various settings, policies, and applications to be applied during the deployment process.
Using Windows Configuration Designer, you can create provisioning packages that define the desired configurations for Windows 10 computers. These packages can include settings such as network configurations, security settings, regional preferences, installed applications, and more.
The tool provides an intuitive interface that guides you through the process of creating the provisioning package. You can select the desired configuration options, customize settings, and preview the changes before generating the package.
Once the provisioning package is created using Windows Configuration Designer, it can be applied during the deployment process to configure multiple Windows 10 computers with consistent settings and configurations. The provisioning package can be installed manually or through automated deployment methods like Windows Autopilot or System Center Configuration Manager (SCCM).
In summary, to create provisioning packages for deploying Windows 10 computers using a dynamic deployment method, you should use the Windows Configuration Designer tool. It enables you to customize settings and configurations, which can be applied during the deployment process to ensure consistent and efficient provisioning of Windows 10 computers.
Learn more about Designer here
https://brainly.com/question/32503684
#SPJ11
within a table, two or more attributes may be combined to create a unique identifier that is compositite key ______
Answers
Within a table, two or more attributes may be combined to create a unique identifier called a composite key. A composite key ensures that the combination of these attributes is distinct and can be used to uniquely identify a specific record in the table.
Yes, within a table, two or more attributes may be combined to create a unique identifier that is called a composite key. A composite key is used to uniquely identify a specific record within a table and is created by combining two or more attributes that, individually, may not be unique. The combination of these attributes creates a unique value that can be used to identify a record in the table. Composite keys are commonly used in database design to ensure data integrity and to help prevent duplicate records from being entered into the table.
Learn more about design https://brainly.com/question/14035075
#SPJ11
Call your function from Example 1 three times with different kinds of arguments: a value, a variable, and an expression. Identify which kind of argument is which.
Answers
Answer:
Example 1:
def function(num):
print(num*2)
Example 2:
function(5)
num = 2
function(num)
function(3-1)
Explanation:
Given:
See attachment for complete question
To start with Example (1)
def function(num):
print(num*2)
Note that; the above code segment which doubles the parameter, num could have been any other code
In Example (1), the parameter is num
For example (2):
We can call the function using:
#1. A value:
function(5)
In #1, the argument is 5; a value
#2. A Variable
num = 2
function(num)
In #2, the argument is num; a variable
#3. An Expression
function(3-1)
In #3, the argument is 3-1; an expression
