what is the wavelength for a tv channel that broadcasts at 54.0 mhz ?
Express your answer to three significant figures and include the appropriate units.
Answers
The wavelength for a TV channel that broadcasts at 54.0 MHz is 5.56 m.
Wavelength is the distance between one point on a wave and the same point on the next wave, and is typically measured in meters. It can also be described as the distance that a wave travels in one cycle or oscillation. A wave's wavelength determines its frequency, which is the number of waves that pass a given point per second (measured in hertz).Frequency and wavelength are inversely proportional; as one increases, the other decreases. Higher frequencies have shorter wavelengths and lower frequencies have longer wavelengths. The formula for calculating wavelength is given asλ = c / fWhere:λ = Wavelength (in meters)c = Speed of light (3.00 x 10^8 m/s)f = Frequency (in hertz)Given:Frequency (f) = 54.0 MHz = 54.0 x 10^6 HzSpeed of light (c) = 3.00 x 10^8 m/s. Using the above formula, we can calculate the wavelength (λ) as follows:λ = c / f= (3.00 x 10^8 m/s) / (54.0 x 10^6 Hz)= 5.56 m (rounded to three significant figures).
Therefore, the wavelength for a TV channel that broadcasts at 54.0 MHz is 5.56 m.
To know more about Wavelength, click here:
https://brainly.com/question/12924624
#SPJ11
Related Questions
How to Fix a Padding to Disable Msie And Chrome Friendly Error Page?
Answers
Answer:
A "Padding to Disable MSIE and Chrome Friendly Error Page" error typically occurs when a website or application is using padding or extra spaces in the HTTP response headers, which can cause the browser to display a friendly error page instead of the intended content. To fix this error, you can remove any extra spaces or padding in the response headers. Here are a few ways you can do this:
Use a tool such as Fiddler or Wireshark to inspect the response headers and remove any extra spaces or padding.
Check your server-side code for any spaces or line breaks that may be added to the response headers. This could be caused by a library or framework that is being used.
Check for any middleware or plugins that may be adding spaces or padding to the response headers. Disabling or removing these may fix the issue.
Check for any load balancer or reverse proxy that may be adding spaces or padding to the response headers.
Check for any Content Security Policy that may be causing the issue and adjust it accordingly
It's important to note that this is a generic solution and the exact cause of the error will vary. The best way to fix this error is by identifying the root cause of the problem and addressing it accordingly.
e. What is computer memory? Why does a computer need primary memory?
Answers
Computer memory refers to the storage space in a computer where we can temporarily or permanently store data and instructions. There are two categories: primary memory and secondary memory.
Why a computer needs primary memory?A computer needs primary memory because it allows it to access and process the data and instructions it needs quickly.
The computer's operating system uses primary storage to manage memory allocation and determine which stores data and instructions in primary memory and which should move to secondary memory.
It is also sufficient for storing the data and instructions that the computer is currently using and enables programs to run efficiently.
What's the size of this struct? struct record4 int a; int c; float e; char b; char d; A 16 B 20 C 14 D 24
Answers
The size of the struct `record4` is **D) 24 bytes**.
To calculate the size of a struct, we add up the sizes of its individual members, taking into account padding and alignment.
In this case, we have:
- `int a` (4 bytes)
- `int c` (4 bytes)
- `float e` (4 bytes)
- `char b` (1 byte)
- `char d` (1 byte)
When calculating the size, the compiler may add padding bytes to ensure proper alignment. In this case, to align the `float e` member, the compiler may add 2 bytes of padding after `int c` and `char b`.
So, the total size of the struct becomes:
4 (int a) + 4 (int c) + 4 (float e) + 1 (char b) + 1 (char d) + 2 (padding) = **16 bytes**.
It's important to note that the size of a struct can vary depending on the compiler and its specific padding and alignment rules. To ensure consistency, it's good practice to use compiler-specific directives, such as `#pragma pack`, to control the padding and alignment of structs when necessary.
learn more about struct here:
https://brainly.com/question/31414222
#SPJ11
Project stem 2.3 code practice question 2
Answers
Answer:
"Write a program that accepts two decimal numbers as input and outputs their sum."
a = float(input("Enter an integer: "))
b = float(input("Enter an integer: "))
print(a + b)
Explanation:
We are just entering an integer and having the code float the variable down to our print function thats why we have added the "float" variable
Glad to help!
Stay up and Stay Blessed!
in the table below, select the correct answer. the horizontal analysis of the net sales and accounts receivable would most likely tell you what?
Answers
The horizontal analysis of the net sales and accounts receivable would most likely tell you about the trend or changes in sales revenue and the amounts owed by customers over a period of time.
Horizontal analysis, also known as trend analysis, involves comparing financial data over multiple periods to identify patterns, trends, and changes in performance. In this case, analyzing the net sales would help identify the growth or decline in sales revenue over time, providing insights into the company's sales performance. Analyzing accounts receivable would reveal the changes in the amounts owed by customers, indicating the effectiveness of the company's credit and collection policies, as well as the liquidity of the company.
Therefore, the horizontal analysis of net sales and accounts receivable would provide valuable information about the financial performance, sales trends, and customer payment behavior of the company.
You can learn more about horizontal analysis at
https://brainly.com/question/25806750
#SPJ11
ways you will use to reach all pupils who are living at a
disadvantaged area
Answers
Answer:
?
im confused
Explanation:
program that shows if it's an integer or not
Answers
47. Which of these examples demonstrates good netiquette?
Typing a comment on a video detailing how boring and poorly made it is.
A-Sending an email without a salutation or a signature.
B-Posting a blog article about how stuck-up your peers are.
C-Being straightforward and truthful in all electronic communications.
Answers
Answer:
typing it, on a video detailing how boring and poorly made it is
Explanation:
this is an example of good netiquette because they are criticizing the video game and what good netiquette is is making a comment relevant to the original message. the original message being the video game
Define bit, nibble, byte, binary
Answers
Answer: , a group of 4 bits is called a nibble
Explanation:
________ deals with more objective, rational, and technical knowledge.
Answers
Explicit knowledge deals with more objective, rational, and technical knowledge.
Explicit knowledge is knowledge that can be readily verbalized, codified, stored and accessed. Hence, explicit knowledge can be easily transmitted to others.
Explicit knowledge is the most basic form of knowledge since it can be easily accessed. Examples of explicit knowledge is company data sheets, research reports. Explicit knowledge deals with more objective, rational, and technical knowledge.
Find out more at: https://brainly.com/question/16980038
what's the valency of carbon , electron configuration 2,4?
Answers
Answer:
4 is the valency of carbon
because it has 4 valence electrons
hope it helps
A ______ is a set of step-by-step instructions to complete a task so that users can be sure to complete the task correctly.
Answers
Answer:
Algorithm
Explanation:
An algorithm a process or set of instructions that is created to solve a problem.
Can you solve this challenging activity?

Answers
Answer:
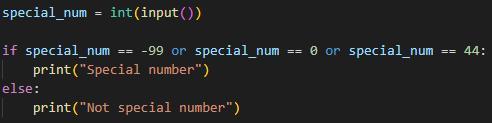
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
a group of windows pcs in a new subnet has been added to an ethernet network. when testing the connectivity, a technician finds that these pcs can access local network resources but not the internet resources. to troubleshoot the problem, the technician wants to initially confirm the ip address and dns configurations on the pcs, and also verify connectivity to the local router. which three windows cli commands and utilities will provide the necessary information? (choose three.)
Answers
The Three windows cli commands and utilities that will provide the necessary information are ping, ipconfig and nslookup.
The ipconfig and nslookup commands will make the initial IP address and DNS configuration information availabe to the technicians while determining whether the DHCP is assigning correct information to the PCs. The ping utility on the other hand would be used in verifying whether, or not, the connectivity to the default gateway (router) using the configured default gateway address, or using the known correct default gateway address if these are found to be different.
Here's the complete question:
A group of Windows PCs in a new subnet has been added to an Ethernet network. When testing the connectivity, a technician finds that these PCs can access local network resources but not the Internet resources. To troubleshoot the problem, the technician wants to initially confirm the IP address and DNS configurations on the PCs, and also verify connectivity to the local router. Which three Windows CLI commands and utilities will provide the necessary information? (Choose three.)
a. netsh interface ipv6 show neighbor
b. arp -a
c. tracert
d. ping
e. ipconfig
f. nslookup
g. telnet
Learn more on Windows CLI command from:
https://brainly.com/question/13263568?referrer=searchResults
#SPJ4
When first designing an app, all of the folldwing are important EXCEPT
A. debugging
B. determining how a user would interact with the app.
C. determining the purpose of the app
D. identifying the target audience
Answers
Answer:
B
Explanation:
Determining how the user could interact with the app varies person to person, the others are essential to creating apps though.
the security kernel is external to the trusted computing base (tcb) because for it to effectively provide security it needs to be outside of the environment so that it cannot be tampered with. true false
Answers
False. The security kernel is not external to the Trusted Computing Base (TCB). In fact, the security kernel is a fundamental component of the TCB. The TCB encompasses all the hardware, software, and firmware components that are essential for enforcing security policies and protecting the system against unauthorized access and malicious activities.
The security kernel refers to the core part of the operating system or security architecture that implements and enforces the security mechanisms and controls. It is responsible for managing access control, authentication, secure communication, and other critical security functions.
The security kernel is typically a part of the TCB and resides within the trusted computing environment. It must be highly trusted and undergo rigorous security evaluation and testing to ensure its integrity and reliability. By being part of the TCB, the security kernel can effectively provide security measures within the trusted environment and protect it from tampering or unauthorized modifications.
Learn more about firmware here:
https://brainly.com/question/28945238
#SPJ11
In stranger things 3 hopper said" to turn back the clock" which is a spoiler for season 4. (Something's gonna reset the clocks and all of what happens will begin again)
Answers
What is the result of the following code fragment?
BigInteger a = new BigInteger ("10");
BigInteger b = new BigInteger ("25");
a.multiply(b);
a.add(b);
System.out.println(a);
A. 10
B. 35
C. 250
D. 275
Answers
Answer:
D
Explanation:
I don't know the language, but it is clear what is going on.
It looks like you are defining a value for a in both commands.
a.multiply(b); looks like you take the value in a (which is 10) multiply it by 25 and put the result back in a. So so far we have 10 * 25 = 250
Note the next command
a.add(b)
looks like you take the current value in a(which is now 250)
and put the value of b (which has not been changed. It is still 25) and put that in a (which is 250).
The result is 250 + 25 = 275
The answer is D. Since I only understand the logic, if this answer is wrong, I wish you'd leave a note.
analiza esta frase: algunas personas sueñan con grandes logros mientras que otros se quedan despiertos y actuan

Answers
Answer:
Para lograr tus sueños y objetivos se debe trabajar duro, hacer lo posible por hacerlos realidad, no quedarse con solo la idea de tu sueño.
Explanation:
Which command is a full-featured command-line Registry editor?
a. Regsrv32
b. Regedt32
c. Regedit
d. Reg
Answers
The Windows Registry is a hierarchical database that stores configuration settings and options for the operating system, hardware, software, and user preferences.The correct answer is c. Regedit.
Regedit is a full-featured command-line Registry editor. It is a powerful tool provided by Microsoft Windows that allows users to view, modify, and manage the Windows Registry. The Windows Registry is a hierarchical database that stores configuration settings and options for the operating system, hardware, software, and user preferences. Regedit provides a graphical user interface (GUI) that enables users to navigate through the registry and make changes to its keys and values. It allows users to create, delete, modify, and export registry keys and values. Regsrv32, on the other hand, is a command-line utility used to register and unregister dynamic-link libraries (DLLs) in Windows. Regedt32 is an older version of the Registry editor that was used in earlier versions of Windows, but it has been replaced by Regedit in modern versions. The command "Reg" is a command-line utility used to query, add, modify, and delete registry keys and values, but it does not provide the full set of features available in Regedit.
Learn more about database here:
https://brainly.com/question/30163202
#SPJ11
what is the minimum number of paths that would need to be broken to prevent computing device a from connecting with computing device e?
Answers
The minimum number of paths that would need to be broken to prevent computing device a from connecting with computing device E is 3 .
What is computing device?Computing device refers to, as appropriate, a student-owned computing device used as part of the Bring-Your-Own-Device (BYOD) Program or an Ontario Tech owned computing device that was loaned to the student. This Software Use Agreement ("Agreement"), as it may be updated from time to time by the University, must be accepted without modification in order to use the Software, which is a privilege, not a right.
You ("User") and the University are the parties to this Agreement. You confirm that, as a User, you have read, comprehended, and agree to be bound by the terms and conditions contained in this Agreement by clicking "I agree" below.
Learn more about Computing device
https://brainly.com/question/4774474
#SPJ4
Write an algorithm to find addition, subtraction, and multiplication of 2 numbers
Answers
Answer:
AdditionStep 1: Input the two numbers, a and b.
Step 2: Output a + b.
Step 3: Output a - b.
Step 4: Output a * b.
Step 5: If b = 0 output “undefined”.
Step 6: Else output a / b.
subtractionStep 1 If ( a < b ) then there will be no answer .
step 2f ( a = b ) then all the numbers greater than a are the answer so there will be infinite solutions possible.
Step 3 If ( a > b ) Suppose x is an answer to our equation. Then x divides (a – b).
derek sets up a series of virtual machines that are automatically created in a completely isolated environment. once created, the systems are used to run potentially malicious software and files. the actions taken by those files and programs are recorded and then reported. what technique is derek using?
Answers
Derek uses sandboxing technique. Sandboxing is the cybersecurity practice of running, observing, analyzing, and programming code in a safe, isolated environment on a network that mimics the end user's operating environment.
Why is it called sandbox?Sandboxes are designed to prevent threats from entering a network and are commonly used to examine untested or untrusted code. The term sandbox comes from the idea of a children's sandbox, where sand and toys are stored in small containers or walled areas for children to play safely. The sandbox approach gives each software application a "sandbox". This is a controlled and restricted environment for running and executing code.
What are sandbox examples?specific example of using sandboxes to isolate code execution: Web browser. Trusted web browsers can run in a sandbox. Second, if a website exploits a vulnerability in that web browser, the damage is limited to the sandbox and is minimal.
To learn more about technique visit:
https://brainly.com/question/14300582
#SPJ4
For extra depth of perspective, you should consider using a gradient. (pg. 219)
O True
O False
Answers
Answer:
true
Explanation:
2. What is ICT ? Explain its use in health and banking.
Answers
Answer:ICT stands for Information and Communication Technology. It is an umbrella term that refers to the use of digital technologies for managing, processing, and transmitting information. ICT includes a wide range of technologies such as computers, software, the internet, mobile devices, and other digital tools.
ICT has revolutionized many industries, including healthcare and banking. In healthcare, ICT is used to improve patient care, increase efficiency, and reduce costs. For example, electronic health records (EHRs) enable healthcare providers to access and share patient information easily and securely, leading to better coordinated care. Telemedicine, which involves using video conferencing and other digital technologies to provide remote healthcare services, has also become more popular due to the COVID-19 pandemic. It allows patients to receive medical consultations, diagnosis, and treatment without visiting a physical healthcare facility.
In banking, ICT has enabled the development of online banking, mobile banking, and other digital financial services. Online banking allows customers to access their accounts, transfer funds, pay bills, and manage their finances from anywhere, at any time. Mobile banking offers even greater convenience by allowing customers to access their accounts using their smartphones. The use of biometric authentication, such as fingerprint recognition and facial recognition, has also improved the security of banking transactions.
In summary, ICT has had a profound impact on healthcare and banking, improving efficiency, reducing costs, and increasing convenience for users. As technology continues to advance, we can expect to see even more innovative applications of ICT in these and other industries.
Regenerate response
Explanation:
Write a program that reports whether or not someone is eligible to run for president in the U.S. You should do the following in your program:
Ask the user for their age, and store it in a variable
Ask the user if they are a citizen of the U.S.
Ask the user how long they’ve been a resident in the U.S.
Use an if/else statement with the proper comparison operator to print You are eligible to run for president! if they have the following credentials:
They are at least 35 years old
They were born in the U.S.
They have been a resident for at least 14 years
Answers
Answer:
Not sure which language are you using, so I'm using python.
# getting the information
age = input("What is your age?")
citizen = input ("Are you are US citizen? (Y/ N)")
duration = input ("How many years have you been staying in the US?")
# print the line if one fits all requirements
if (age >= 35 || citizen == Y || duration >= 14) :
print ("You are eligible to run for president!")
else :
return
"please help i have exam
Discuss three phases of social media marketing maturity.
Answers
The three phases of social media marketing maturity are: 1. Foundation Phase 2. Growth Phase 3. Optimization Phase
1. Foundation Phase: In this phase, businesses establish their presence on social media platforms and focus on building a solid foundation for their marketing efforts. They create social media accounts, develop a consistent brand voice, and start engaging with their audience. The primary goal is to increase brand awareness and establish a basic level of social media presence.
2. Growth Phase: During this phase, businesses expand their social media strategies and start leveraging the full potential of social media marketing. They focus on growing their audience, increasing engagement, and driving traffic to their website or physical stores. This phase involves implementing more advanced strategies such as content marketing, influencer partnerships, and targeted advertising campaigns.
3. Optimization Phase: In the optimization phase, businesses refine their social media strategies based on data-driven insights and continuous improvement. They use analytics tools to measure the effectiveness of their campaigns, identify areas for improvement, and optimize their social media content and advertising strategies. This phase emphasizes the importance of data analysis, testing, and ongoing optimization to achieve better results and maximize return on investment.
The three phases of social media marketing maturity represent a progression from establishing a basic presence to achieving strategic growth and continuous optimization. As businesses advance through these phases, they develop a deeper understanding of their target audience, refine their messaging, and refine their tactics to drive meaningful results from their social media marketing efforts.
To learn more about website click here: brainly.com/question/32113821
#SPJ11
Which of the following algorithms are used in symmetric encryption? (Select three.)
ElGamal
Blowfish
DiffieHellman
3DES
AES
Answers
In symmetric encryption, three algorithms that are commonly used are Blowfish, 3DES, and AES.
1. Blowfish: This is a symmetric block cipher created by Bruce Schneier in 1993. It provides a good encryption rate and has a variable key length, making it a flexible and secure option for encryption. Blowfish is well-suited for applications where the key does not change frequently, such as file encryption.
2. 3DES (Triple Data Encryption Standard): Developed as an improvement to the original Data Encryption Standard (DES), 3DES uses the DES algorithm three times in a row with different keys. This provides a stronger level of encryption compared to the original DES, which had a relatively small key size and was vulnerable to brute-force attacks.
3. AES (Advanced Encryption Standard): AES is a widely used symmetric encryption algorithm that was established as the encryption standard by the U.S. National Institute of Standards and Technology (NIST) in 2001. AES provides strong encryption with key sizes of 128, 192, and 256 bits, making it suitable for various applications, including securing communications and sensitive data.
In summary, Blowfish, 3DES, and AES are three algorithms commonly used for symmetric encryption, providing various levels of security and flexibility. ElGamal and Diffie-Hellman, on the other hand, are examples of asymmetric encryption algorithms and thus not relevant to symmetric encryption.
know more about Blowfish here:
https://brainly.com/question/31683644
#SPJ11
In the data view of SPSS, each row shows the values of the same
variable, while each column shows the values of the same
observation (consumer, survey respondent, salesperson, etc).
True
False
Answers
False. In the data view of SPSS (Statistical Package for the Social Sciences), each row represents a separate observation (e.g., individual, respondent, case) in the dataset, while each column represents a variable.
Typically, a dataset in SPSS consists of multiple variables that capture different aspects of the observations. For example, if you have survey data on consumer preferences, each row would represent a different respondent, and each column would represent a different variable, such as age, gender, income, and product preference.
By organizing the data in this way, SPSS allows for easy analysis and manipulation of the dataset. Researchers can apply various statistical procedures, run tests, generate descriptive statistics, and explore relationships between variables.
It's essential to understand the structure of the data view in SPSS to correctly input, manage, and analyze data. Remember, each row represents a different observation, and each column represents a different variable.
This organization facilitates data analysis and ensures accurate interpretation of results.
For more such questions on SPSS,click on
https://brainly.com/question/30929074
#SPJ8
What are the data items in the list called?
Question 9 options:
data
items
values
elements
Answers
A list's elements are its data items. Each entry in the list has an index that indicates its specific location inside the list.
What do the items in a list go by?An ordered group of values is a list. The components of a list are referred to as its elements or items. The terms element and item will both refer to the same object.
A list is what?An ordered data structure called a list has elements that are delimited by square brackets and separated by commas. For example, the lists 1 and 2 below each only have one type of data. Here, list1 is made up of integers, whereas list2 is made up of texts. Lists can also store mixed data types, as shown in the list3 here.
To know more about data visit:-
https://brainly.com/question/13650923
#SPJ4