What is one of the tools that is particularly useful in reducing system nervousness in an MRP system?a.) time fencesb.) time phasingc.) closed loop systemd.) lot sizing
Answers
Time fences is one of the tools that are particularly useful in reducing system nervousness in an MRP system.
What is an MRP system?
Based on demand and the bill of materials, a material requirements planning (MRP) system determines the required raw materials, components, and subassemblies as well as when to assemble the finished goods, thereby speeding up the manufacturing production process (BOM).
Three goals are meant to be accomplished by an MRP system at once: To make sure that products can be delivered to customers and that raw materials are available for manufacture. Keep stock levels of products and materials as low as feasible. Plan your production processes, delivery dates, and purchasing procedures.
Calculating the materials and parts required to make a product is done using a system called material requirements planning (MRP). Three main parts make up this process: listing the materials and components already in use, determining which more are required, and scheduling their manufacture or acquisition.
To learn more about an MRP system, use the link given
https://brainly.com/question/28583775
#SPJ4
Related Questions
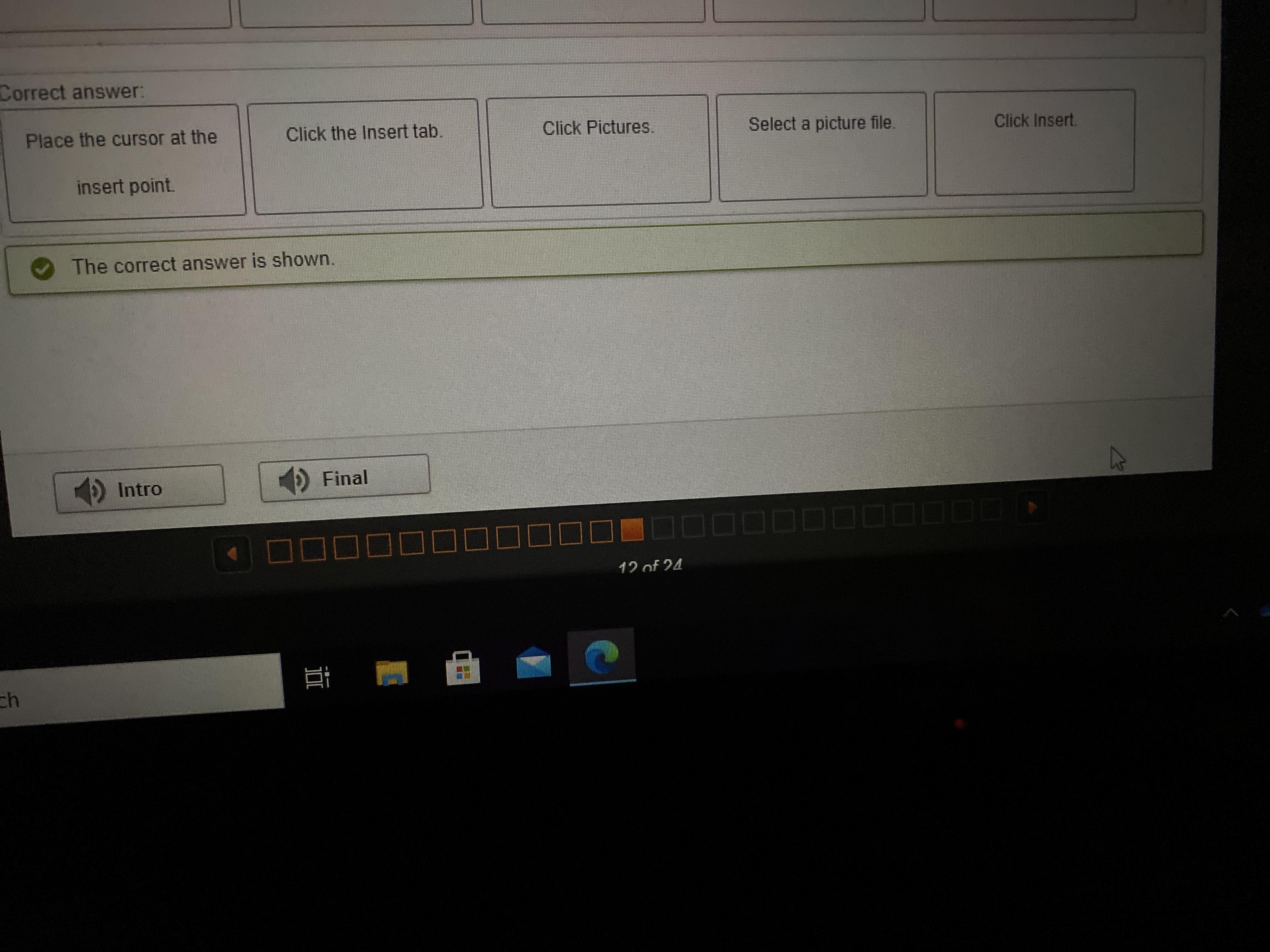
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
If the system has a mechanical advantage of 5 and the load of 350N.What effort is needed to lift the weight? Provide your answer in newtons
Answers
Answer:
Effort = 70 N
Explanation:
A machine is a device that can be used to overcome a load by the application of a minimal effort. For a practical machine, mechanical advantage (MA) is the ratio of the load (L) overcome to the effort (E) applied.
i.e MA = \(\frac{Load}{Effort}\)
In the given question, MA = 5 and the load = 350 N. So that;
5 = \(\frac{350}{E}\)
E = \(\frac{350}{5}\)
= 70
The effort applied to the machine is 70 N.
Which of the following organizations works to increase diversity in their field?
Screen Actors Guild
Directors Guild of America
Writers Guild
Dance/USA
Answers
Answer:
screen actors guild
Answer:
Dance/USA
Explanation:
Paavtc Unit 1: Performing Arts Test said it's this one
A ________ examines each part of a message and determines whether to let that part pass.
Answers
Answer:
packet-filtering
Explanation:
A packet-filtering firewall examines each part of a message and determines whether to let that part pass.
can someone please give me some ideas of hooks about negative affects about social media?
Answers
I'm sure you have heard of social media, But have you heard it start's to get out of hands because kids get addicted?
1)Causes kids to be addicted
Answer well to be honest it just gives people something to do but if your on it to long you start to get addicted to that. and my parents try to get them off of it and people could post something that you don't want to. i may be 17 but i still choose not to have social media
BASIC program that prints the value of sin(30)
Answers
Answer:
The value of sin 30° is 1/2. In terms of radian sin 30° is written as sin π/6. Trigonometric functions are very important, for various studies such as it is useful to study Wave motion, Movement of light, the study velocity of harmonic oscillators, and other applications. Most common trigonometric functions are the sine function, cosine function, and tangent function.
sin 30° = 1/2 = 0.5
Explanation:
What are some commands found in the Sort Options dialog box? Check all that apply.
Answers
The Sort Options dialog box contains a number of functions, including Add Level, Delete Level, Copy Level, and Move Up or Down.
What does the sort command's option do?In Linux, the sort command is used to print a file's output in a specific order. This command organizes your data—the content of the file or the output of any program—in the form that you specify, making it easier for us to read the data quickly.
What are kind and its various forms?The sorting procedure places the data in ascending and descending order. Data structures support a number of sorting techniques, including bucket sort, heap sort, fast sort, radix sort, and bubble sort.
To know more about Sort Options visit:
https://brainly.com/question/15133582
#SPJ1
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
3. Under audience, in the mobile overview report, what percentage of sessions came from mobile devices?
Answers
Under audience, in the mobile overview report, the percentage of sessions that came from mobile devices is 65%.
What is the percentage?In the analytics report by a popular internet-providing organization, it was reported that the percentage of sessions that account for the usage of mobile devices in accessing the internet is 65%.
This is more than half of the devices used so mobile devices are a major source for accessing the internet.
Learn more about mobile devices here:
https://brainly.com/question/23433108
#SPJ1
I NEED HELP!! What is the portrait mode?

Answers
Answer:
A its achromatically save your file
The correct answer is E. It applies vertical dimensions to your document.
Explanation:
The portrait mode is a function in programs such as Microsoft Word that allow users to change the orientation of pages. Indeed, by selecting "portrait mode" the pages of the document will be vertical. This is the opposite of "landscape mode" that makes the pages in a document to be horizontally orientated. Additionally, these two functions are relevant for the user because it allows him/her to decide the orientation of pages and therefore the distribution of text, images, graphs, etc. According to this, the portrait mode is the function that "applies vertical dimensions to your document".
A protocol is a set of _____, especially in the formatting of data.
Answers
Answer:
instructions.
Explanation:
I think it’s instructions because it could also be a set of rules or instructions. But it it’s either a set of rules or instructions because, a protocol is pretty much a set of instructions which tell you what to do. Kind of like how the laws are supposed to help keep people civilized and also to help ensure that as many people as possible are being stopped when they do something bad.
How would you describe the game Space Invaders?
A.
a modern-day shooter-style game created in the year 2000
B.
a classic type of shooter game created in the 1970s
C.
an educational game about space
D.
a modern, puzzle-style game
Answers
One can describe the game Space Invaders as: "a classic type of shooter game created in the 1970s" (Option B).
What is space invaders?Space Invaders is a stationary shooter in which the player moves a laser gun across the bottom of the screen and fires at aliens above. The aliens begin in five rows of eleven, moving left and right as a group, changing lower whenever they hit a screen boundary.
Prior to Space Invaders, music and sound effects were essentially afterthoughts in game design, serving as supplemental features that had little bearing on gameplay. Space Invaders was the first game to have ongoing music that played as the player moved.
Given the intentionality of the low-pixel feel of the above-named, game, one can rightly say that is is a classic type of shooter game.
Learn more about Space Invaders:
https://brainly.com/question/10941943
#SPJ1
System Reliability Theory: Models, Statistical Methods, and
Applications by M. Rausand, A. Barros, and A. Hoyland.
QUESTION: List some technical items for which you consider it
beneficial to use the p
Answers
It is beneficial to use the p-model (also known as the power law model) in System Reliability Theory for the following technical items:
Electronic Components: The p-model is useful for analyzing the failure rates of electronic components, such as integrated circuits and transistors. It captures the phenomenon of "burn-in" failures commonly observed in the early life of electronic devices.
Mechanical Systems: The p-model is applicable to mechanical systems, including rotating machinery, pumps, and engines. It helps in characterizing the wear-out phase, where failure rates increase over time due to aging and degradation.
Structural Components: For infrastructure and civil engineering applications, the p-model can be used to estimate failure rates of structural components, such as bridges, dams, and buildings. It provides insights into the long-term performance and deterioration of these systems.
Reliability Growth Analysis: The p-model is beneficial for studying the reliability growth of complex systems during the development and testing phases. It helps identify areas where improvements can be made to enhance system reliability.
The p-model is a versatile tool in System Reliability Theory due to its ability to capture various failure characteristics observed in different technical items. Electronic components often exhibit a high initial failure rate, which decreases over time. The p-model accurately represents this behavior, allowing engineers to optimize burn-in procedures and predict failure rates during the operational phase.
In mechanical systems, wear-out failures are prevalent, where failure rates increase with system age. The p-model accommodates this behavior, enabling engineers to estimate the system's remaining useful life and plan maintenance activities accordingly.
For structural components, long-term reliability analysis is essential. The p-model facilitates the assessment of aging effects and deterioration processes, enabling proactive maintenance strategies and ensuring the safety and longevity of infrastructure.
Moreover, during the development of complex systems, reliability growth analysis is crucial. The p-model can assist in tracking reliability improvements over time, identifying failure modes that require attention, and optimizing the allocation of resources for reliability enhancement.
The p-model is a valuable tool for analyzing the reliability of various technical items across different domains. Its versatility lies in its ability to capture different failure characteristics, including burn-in failures in electronic components, wear-out failures in mechanical systems, aging effects in structural components, and reliability growth in complex systems. By applying the p-model, engineers and researchers can gain valuable insights into failure rates, remaining useful life, system performance, and optimization strategies. This aids in designing robust systems, planning maintenance activities, improving reliability, and ensuring the safety and longevity of critical infrastructure
To know more about Reliability ,visit:
https://brainly.com/question/14266917
#SPJ11
code a statement that tests if the database named testdb exists.
Answers
To test if the database named `testdb` exists, the following statement in SQL can be used:```SHOW DATABASES LIKE 'testdb'```This statement searches for the `testdb` database in the list of databases available and returns a result if it exists. If the database exists, the output will include the name of the database, otherwise, no result will be returned.
The `LIKE` keyword is used to perform a pattern match search for the specified database name.The statement returns a list of databases whose names match the specified pattern. In this case, we are using `testdb` as the pattern to find the database with this name.
The `SHOW` keyword is used to display information about the database, in this case, the list of databases matching the pattern provided.To test if the `testdb` database exists, we can use the SQL statement `SHOW DATABASES LIKE 'testdb'`. This statement searches for the `testdb` database in the list of databases available and returns a result if it exists. If the database exists, the output will include the name of the database, otherwise, no result will be returned. The `LIKE` keyword is used to perform a pattern match search for the specified database name. The statement returns a list of databases whose names match the specified pattern. The `SHOW` keyword is used to display information about the database, in this case, the list of databases matching the pattern provided.
To Know more about database visit:
brainly.com/question/30163202
#SPJ11
Before a new email application could be released to the public, it was released for a few days to some account holders of a website. The project team then collected feedback from this limited number of users and later made the email application available for public use. What type of testing did the project team use?
The project team used __ testing for the email application.
Answers
Answer:
closed
Explanation:
closed beta testing
Answer:
beta
Explanation:
SRFRAME RKMATE - people from nearby provinces come to buy livestock direct from raisers themselves.
Answers
Answer:
Farmers market.
Explanation:
Farmers market is a type of market (marketplace) where people from nearby provinces come to buy livestock direct from raisers themselves.
This ultimately implies that, the consumers go to farmers market to buy farm produce such as vegetables, fruits and livestock directly from the farmers.
Additionally, farmers market is devoid of middlemen such as wholesalers or retailers in the transactional process.
What is the keyboard shortcut for the Undo command?
Choose the answer.
CTRL+X
CTRL+Z
CTRL+U
CTRL+V
Answers
Answer:
CTRL+Z is Undo
Explanation:
CTRL+X: Cut
CTRL+Z: Undo
CTRL+U: Underline
CTRL+V: Paste
A Trojan is a malicious program that uses a computer network to replicate.
a. True
b. False
Answers
False. A Trojan is a type of malware that fools users into downloading and installing it on their computers by disguising itself as a trustworthy software or file. A Trojan may carry out a range of destructive actionn.
Is a Trojan a malicious application that spreads itself across a computer network?Trojan horses are spoofs, or malicious software that pose as something pleasant but are actually malicious. The fact that Trojan horse programmes do not replicate themselves makes them extremely different from real viruses. Trojans include malicious code that, when activated, results in data loss or even theft.
What do computer Trojans do?Malware that poses as trustworthy programmes or software is known as a Trojan Horse (Trojan). Attackers enter the network once inside.
To know more about malware visit:-
https://brainly.com/question/14276107
#SPJ1
95.5% completequestionan incident involving a data breach is under investigation at a major video game software company. the incident involves the unauthorized transfer of a sensitive file to an outside source (a leak). during the investigation, something occurs where neither the dlp team or employees can find the concerning file that was once found on the network. verify the data loss prevention (dlp) terminology that describes what has occurred to the file in question.
Answers
the terminology that describes what has occurred to the file in question is "data loss". the file in question was once present on the network but is now missing and cannot be located by the DLP team or employees. This constitutes a loss of data, as the sensitive file has been compromised and is no longer under the control of the company. it can be further explained that data loss prevention is a critical component of cybersecurity, as it aims to protect sensitive information from unauthorized access, use, disclosure, or destruction.
When a data breach occurs, it is important to quickly identify and respond to the incident to mitigate the damage and prevent further loss. In this case, the missing file represents a significant data loss, and the company should take immediate steps to investigate the incident, determine the extent of the damage, and implement measures to prevent similar incidents in the future. The DLP terminology that describes what has occurred to the file in question is "False Negative."
In the context of Data Loss Prevention (DLP), a False Negative refers to a situation where the DLP system fails to detect and prevent the unauthorized transfer of sensitive information, such as the file in this case. The DLP team and employees are unable to find the concerning file on the network, which indicates that the DLP system did not properly identify the file as sensitive or properly block its transfer to an outside source. In summary, the term "False Negative" in DLP terminology accurately describes the incident where the concerning file was not detected and prevented from being transferred to an unauthorized outside source.
To know more about "data loss" visit:
https://brainly.com/question/31595444
#SPJ11
To get information about a result set like the number of columns and names of the columns, you can use the methods of the
Statement object
ResultSet object
Connection object
ResultSetMetaData object
Answers
To get information about a result set like the number of columns and names of the columns, you can use the methods of the
ResultSetMetaData objectWhat is ResultSetMetaData object?Obtaining critical data concerning the result set- column specifics and their names- can conveniently be achieved using relevant methods housed within the ResultSetMetaData object.
This interface, implemented in Java, serves as an efficient means to obtain metadata outlining the structure of the result set inclusive of the number of columns present, the individual identifiers associated with each one, pertinent details regarding types of data contained within said columns among other vital components therein found.
Learn more about ResultSetMetaData at
https://brainly.com/question/13103023
#SPJ1
Chapter 21 discusses four aspects of the speaking situation you should take into account when planning the graphics you'll use in an oral presentation including the length of the presentation, the size and layout of the room, and the available equipment. What is the last aspect?
Answers
Answer:
The answer is "audience aptitude and experience "
Explanation:
The presentation is the ability to provide a variety of audiences with successful and stimulating interactions. The main objective of an oral presentation is to talk formally to a live audience about a particular subject. You have to write an oral speech that engages the audience and fulfills your goals.
In this type of presentation, the Listener-centric concept is effective as the productivity of a speaker is enhanced by creating and presenting the speech throughout the proper manner.
Is it always beneficial to have a comprehensive troubleshooting plan covering all possible test cases from a given category?
No, a troubleshooting plan covering all possible test cases from a given category could involve extra work, be redundant, and prove unproductive for improving the product.
Yes, a troubleshooting plan needs to include all possible test cases, for a given category to meet industry standards
No, a troubleshooting plan does not need to include any test cases from other categories
Yes, it is always beneficial to have a troubleshooting plan that covers all test cases from a given category.
Answers
Yes, it is always beneficial to have a troubleshooting plan that covers all test cases from a given category. The correct option is D.
What is test case?A test case is a description of the inputs, execution circumstances, testing process, and anticipated results that comprise a single test to be conducted in software engineering.
The testing work that must be done throughout the project life-cycle to ensure a successful implementation is mapped out in the test plan.
A well-crafted test strategy forces your business to consider the needs, plan for what will be needed in terms of resources, and list the risks associated.
Having a troubleshooting strategy that addresses every test case from a certain category is always advantageous.
Thus, the correct option is D.
For more details regarding test cases, visit:
https://brainly.com/question/22148292
#SPJ1
10. Which of the following is NOT a determining factor in which side of the digital divide a
citizen is on?
(A) Education
(B) Socioeconomic status
(C) Location
(D) Gender
Answers
An option which is not a determining factor in which side of the digital divide a citizen is on is: (D) Gender.
What is the digital divide?The digital divide simply refers to a terminology which is used to describe the gap (vacuum) which typically exist between the group of people (the information rich and the information poor) who have unrestricted access to digital technology and those who are unable to access it.
This ultimately implies that, a digital divide is mostly influenced by the fact that legislation allow communications firms to charge end users (customers) per website for access. Additionally, some parents are fond of limiting the amount of time their children spend using computing devices or the Internet.
In conclusion, geographical location, socioeconomic status, and education are all determining factors which affect the side of the digital divide that a citizen would be on.
Read more on digital divide here: https://brainly.com/question/14896873
#SPJ1
why is it important to put specific conditionals first?
Answers
Answer:
i dunno
Explanation:
Answer:
Explanation:
First conditional is used to talk about actions/events in the future which are likely to happen or have a real possibility of happening. If it rains tomorrow, I'll stay at home.
¿Podría decir que la Tecnología cumple como medio y herramienta para
satisfacer necesidades? Justifique su respuesta.
Answers
Answer:
gggaghqjgfdttedfvqtffqgfq graffiti qtrdgg
consider an extensible hash table that uses 4-bit hash keys and stores two records per bucket. simulate the insertion, into an initially empty hash table, of records with (hash values of) keys 1111, 1110, 1101,..., 0001, 0000, in that order.
which combination of i (the number of bits used to index the bucket array) and a set of of keys belong to one bucket at some time during the sequence of insertions?
Answers
To be able to simulate the insertion of records into any form of an extensible hash table which is said to make use of 4-bit hash keys as well as stores two records per bucket, we need to start with a free hash table
What is the combination?The number of bits i is one that is often used to index the bucket array and it is one that is known to be initially 1, and then it tends to doubles all of the time the hash table is reorganized.
Therefore, We have to simulate the insertion of records and this can be done via the use of keys 1111, 1110, 1101,..., 0001, 0000, in the right order.
Learn more about combination from
#SPJ1
what is one way that advertisers exert control over media outlets
Answers
One way that advertisers exert control over media outlets is through advertising revenue and the influence it holds over media organizations.
Advertisers can use their financial power to shape the content and agenda of media outlets to align with their interests.
Advertisers play a significant role in supporting media outlets financially through advertising purchases. The revenue generated from advertisements is crucial for the sustainability of media organizations. Advertisers understand this dependence and can leverage their financial influence to exert control over the content and direction of media outlets.
By strategically allocating their advertising budgets, advertisers can shape the editorial decisions made by media outlets. They may request specific content, tone, or messaging that aligns with their brand image or objectives. Media organizations, in turn, may feel compelled to meet the expectations of their advertisers to maintain their financial support.
Advertisers may also use their economic power to pressure media outlets into avoiding certain topics or viewpoints that could be detrimental to their interests. They can threaten to withdraw advertising support or direct their spending to alternative platforms that are more compliant with their preferences.
In this way, advertisers have the ability to influence media outlets by leveraging their financial resources, thus exerting control over the content, agenda, and overall editorial direction of the media.
To learn more about outlets visit:
brainly.com/question/14514615
#SPJ11
A laptop user has traveled to visit a client and forgot his power adapter. Before going to lunch with the client, he wants to conserve battery power, but he wants to enable the fastest possible startup when he gets back, with his applications already open. Which power mode will conserve battery life but enable the fastest startup?
Answers
Answer:
Sleep mode
Explanation:
Sleep mode pauses all actions on the computer, all open processes are put in memory and the computer goes to a low-power state. This means when he comes back from lunch, that user's laptop will immediately resume all the applications and processes, all the while using very little power.
Hope this helps <3
Cocaine-related deaths are often a result of...
a) Cardiac arrest
b)
A traffic crash
c)
Cancer
Answers
Answer: a) Cardiac arrest
Explanation:
Describe in words or with pseudo code how you would write your own least squares solver, similar to 1east_equares. Note that while you can do this by looping through a range of parameter values, I'll also accept simply using a built in optimizer to do the minimisation.
Answers
Pseudocode for a least squares solver using a built-in optimizer:
python
import optimizer_library
# Define the objective function
def objective_function(params):
# Calculate predicted values using the model and current parameter values
predicted_values = model(params)
# Calculate residuals by subtracting observed values from predicted values
residuals = observed_values - predicted_values
# Calculate the sum of squared residuals
sum_squared_residuals = sum(residuals**2)
return sum_squared_residuals
# Define the model
def model(params):
# Define the equation or model based on the parameter values
return predicted_values
# Set initial parameter values
initial_params = [initial_values]
# Create an optimization problem
problem = optimizer_library.Problem()
# Set the objective function
problem.setObjective(objective_function)
# Set the initial parameter values
problem.setInitialParams(initial_params)
# Solve the optimization problem
optimal_params = optimizer_library.solve(problem)
# Retrieve the optimal parameter values
final_params = optimal_params.getValues()
Define your objective function: Start by defining the objective function that you want to minimize. In the case of least squares, the objective function is typically the sum of squared residuals between the predicted values and the observed values.
Define your model: Determine the model or equation that you want to fit to the data. This could be a linear model, polynomial model, or any other model that best represents the relationship between the independent variables and the dependent variable.
Set up the optimization problem: Create an optimization problem where the goal is to minimize the objective function. You can use a built-in optimizer or optimization library to solve the problem. This library should have methods to define the objective function and handle constraints, if any.
Specify initial parameter values: Choose initial parameter values for your model. These initial values will be used as a starting point for the optimization algorithm.
Solve the optimization problem: Use the optimizer to solve the optimization problem. Provide the objective function, initial parameter values, and any other necessary information to the optimizer. The optimizer will iteratively adjust the parameter values to minimize the objective function.
Retrieve the optimal parameter values: Once the optimization is complete, retrieve the optimal parameter values obtained from the solver.
To know more about Pseudocode
https://brainly.com/question/17102236
#SPJ11