What is a possible indication of a malicious code attack in progress.
Answers
A possible indication of a malicious code attack in progressThere are various indications that a malicious code attack is in progress. In computer security, it's always critical to be aware of the latest cyber risks and attacks, as well as the most effective defense mechanisms against them.
The following are some of the possible signs of a malicious code attack in progress:Sudden network slowdowns: When a network experiences a sudden slowdown, it may be due to a malicious attack. It might occur as a result of hackers carrying out a DDoS (Distributed Denial of Service) attack on your network, rendering it unresponsive to legitimate traffic.A sudden increase in network traffic: When there's a sudden surge in traffic on a network, it may be a sign of a malicious attack.
Hackers can also utilize botnets to drive traffic to their target, overwhelming the system and slowing it down.Unusual system crashes: When a system crashes in an unusual manner, it's critical to investigate the cause. Malicious code can cause system crashes in unexpected ways, which can lead to the loss of vital data and other issues. A sudden change in system behavior: Changes in system behavior can be caused by malicious code.
To know more about code visit:
https://brainly.com/question/15301012
#SPJ11
Related Questions
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
Consider the following methods 0 /* Precondition: a and > public static int methodonerint , int b) int loop Count = 0; forint 101 b1 ++) loopCount++; return loopCount: - Precondition and b 0 / public static int method tvorint a, int b) int loopCount = 0; int i = 0; while ( L a ) loopCount : return loop Count; Which of the following best describes the conditions under which methodone and method to return the same value? A) When a and b are both even When a and b are both odd When a is even and b is odd When a b is equal to zero E) When a tb is equal to one
Answers
To answer this question, we need to analyze the code of both methods. Method one has a for loop that counts the number of iterations from b to 100 inclusive, loop Count and then returns that count. Method two has a while loop that counts the number of iterations from 0 to a-1, and then returns that count.
Let's start by considering the case when a and b are both even. In this case, the for loop of method one will iterate from b to 100 inclusive for an even number of times. For example, if a = 10 and b = 6, the for loop will iterate 48 times. On the other hand, the while loop of method two will iterate from 0 to a-1 for an odd number of times. For example, if a = 10, the while loop will iterate 9 times.
Now let's consider the case when a and b are both odd. In this case, the for loop of method one will iterate from b to 100 inclusive for an odd number of times. For example, if a = 11 and b = 7, the for loop will iterate 47 times. The while loop of method two will iterate from 0 to a-1 for an even number of times. For example, if a = 11, the while loop will iterate 10 times.
Next, let's consider the case when a is even and b is odd. In this case, the for loop of method one will iterate from b to 100 inclusive for an odd number of times, just like in the previous case. For example, if a = 10 and b = 7, the for loop will iterate 47 times. The while loop of method two will iterate from 0 to a-1 for an even number of times, just like in the first case. For example, if a = 10, the while loop will iterate 9 times.
To know more about loop Count visit:-
https://brainly.com/question/13144925
#SPJ11
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
How does a cell phone change the
incoming signals from a caller into sound that
you can hear
Answers
Answer:
they send electrical signals to the buzzer. The buzzer changes those electrical signals into sound. You hear the buzzer sound and know that someone is calling you.
Explanation:
Answer: Cell phone or any electric device you can say changes the electric signal to radio waves at transmitting end which is converted back to electric signal and perceived as sound waves at receiving end
Explanation:
4. (10 marks) The Model View Controller (MVC) pattern is used in web development to structure an application. (a) (4 marks) Describe the job of the Controller in this pattern and how it interacts with
Answers
The Model View Controller (MVC) pattern is used in web development to structure an application. The main idea behind MVC is to create three interconnected components namely Model, View and Controller that differentiate application logic and user interface.
The job of the controller in the MVC pattern is to accept input from the user and after that perform appropriate validation. Once the data has been confirmed by the controller, it is sent to the model where it can be processed. After the processing is done, the model returns data back to the controller. The controller will then send the data to the view for display to the user.
The controller is responsible for managing the flow of the application. When the user sends a request to the application, the request is managed by the controller. The controller communicates with the model to obtain data to return to the user. The controller is responsible for choosing the appropriate view for displaying the data to the user.The controller also manages the user input, which is obtained through the view.
When a user sends a request to the application, the request is handled by the controller, which determines which action to take and what response to provide.The controller is responsible for the business logic of the application. It manages the flow of the application by interacting with both the model and view. The controller is the core of the application, and it determines the behavior of the application.
To learn more about MVC :
https://brainly.com/question/30755991
#SPJ11
Implement a Full Adder using:
A. A 4x1 MUX for the Sum output, and another 4x1 MUX for the Carry Out. B. A 2x1 MUX for the Sum output, and another 2x1 MUX for the Carry Out.
Answers
To implement a Full Adder using a 4x1 MUX for the Sum output and another 4x1 MUX for the Carry Out, we can utilize the MUXes to select the appropriate output based on the input conditions.
To implement a Full Adder using a 2x1 MUX for the Sum output and another 2x1 MUX for the Carry Out, we can use the MUXes to choose the correct output based on the input conditions.
A Full Adder is a combinational logic circuit that performs the addition of three binary inputs: two operands (A and B) and a carry-in (Cin). It produces two outputs: the sum (Sum) and the carry-out (Cout). In this explanation, we will explore two different implementations of the Full Adder using multiplexers (MUXes) for the Sum and Carry Out outputs.
A. Using a 4x1 MUX for the Sum output and another 4x1 MUX for the Carry Out, we can select the appropriate output based on the input conditions. The inputs of the MUXes are determined by the operands
A Full Adder is a combinational logic circuit that performs the addition of three binary inputs: two operands (A and B) and a carry-in (Cin). It produces two outputs: the sum (Sum) and the carry-out (Cout). In this explanation, we will explore two different implementations of the Full Adder using multiplexers (MUXes) for the Sum and Carry Out outputs.
and the carry-in. The selection lines of the MUXes are based on the values of the operands and the carry-in. By properly configuring the MUXes, we can obtain the Sum and Carry Out outputs of the Full Adder.
B. Alternatively, we can implement the Full Adder using a 2x1 MUX for the Sum output and another 2x1 MUX for the Carry Out. Similar to the previous approach, the MUXes are used to select the appropriate output based on the input conditions. The inputs and selection lines of the MUXes are determined by the operands and the carry-in. By configuring the MUXes correctly, we can obtain the desired Sum and Carry Out outputs.
Both implementations utilize multiplexers to choose the appropriate output based on the input conditions of the Full Adder. The specific configuration and wiring of the MUXes will depend on the desired logic and functionality of the Full Adder circuit.
Learn more about Full Adder
brainly.com/question/33355855
#SPJ11
A friend function has what level of access to a class's
attributes and methods?
Answers
A friend function has full access to the private and protected attributes and methods of a class.
A friend function in C++ is a function that is not a member of a class but is granted special access privileges to the private and protected members of that class. It is declared as a friend of the class within the class definition.
As a result, a friend function can directly access and manipulate the private and protected attributes and methods of the class. It can read and modify their values without any restrictions, effectively bypassing the usual access controls imposed by encapsulation.
This feature can be useful in certain scenarios where external functions need to work closely with the internals of a class. However, it is important to use friend functions judiciously, as they can potentially break encapsulation and compromise the integrity of the class if misused.
Learn more about friend functions and their access level here: brainly.com/question/31565859
#SPJ11
What is the result of the arithmetic operation? 5**2 =
Answers
Answer:
25
Explanation:
5^2
The result of the arithmetic operation 5**2 will be 25, as it indicate two as a power of five.
What is arithmetic operators?It is a mathematical operator that works with both groups and numbers. In AHDL, the prefix and the binary plus (+) and minus (-) symbols are supported arithmetic operators in Boolean statements.
The addition, subtraction, multiplication, division, exponentiation, and modulus operations are carried out via the arithmetic operators.
The term "arithmetic operation" refers to a function that can add, subtract, multiply, or divide numbers.
A programming tool known as an operator performs a function on one or more inputs, such as arithmetic operators.
For numerical values, the double asterisk (**) is used as an exponentiation operator. It enables the programmer to enter many arguments and parameters when used in a function definition.
Thus, answer is 25.
For more details regarding arithmetic operators, visit:
https://brainly.com/question/25834626
#SPJ6
1/3 pts rtial Question 2 Question 11 Complete the line of code to test if all bits 2, 5, 8, 13 and 15 of num1 are set to 1. Use hex for constant operands. if ((numl operator ex mask) == ex value) ... & operator: Ox5092 mask: values Ox5092 Answer 1: & Answer 2: Ox5092 Answer 3: Ox5092
Answers
`python
result = ((num1 & 0x5092) == 0x5092)
```The variable `result` will be `True` if all the specified bits are set to 1 in `num1`, and `False` otherwise.
Does `num1` have all the bits 2, 5, 8, 13, and 15 set to 1?if ((num1 & 0x5092) == 0x5092)
In order to test if specific bits are set to 1 in `num1`, the `&` (bitwise AND) operator is used with a mask value of `0x5092`. The mask has the bit positions 2, 5, 8, 13, and 15 set to 1, while all other bits are set to 0.
The `&` operator performs a bitwise AND operation between `num1` and the mask. If the result of this operation is equal to the value `0x5092`, it indicates that all the specified bits in `num1` are set to 1.
So, the complete line of code to test this condition is:
```python
if ((num1 & 0x5092) == 0x5092):
```
This line checks if the bitwise AND operation of `num1` and `0x5092` equals `0x5092`, which implies that bits 2, 5, 8, 13, and 15 are all set to 1 in `num1`.
Learn more about variable
brainly.com/question/15078630
#SPJ11
most of the early development of computers was funded by_________
Answers
Most of the early development of computers was funded by Government.
What were the Benefits of this funding?
The growth of the US computing sector has been greatly influenced by government sponsorship of research. Federal research funding has helped speed up the commercialization of technology created in industrial labs and given a testing ground for novel computing concepts, systems, and architectures. This influence can be seen in a number of ways, including:
(1) the development of novel goods, services, businesses, and billion-dollar industries based on federally funded research;
(2) the improvement of university computer science and electrical engineering research capabilities;
(3) the development of the human capital that has propelled the computing revolution; and
(4) the improvement of federal agencies' capacity to carry out their public missions.
To know more about such Fundings, Check out:
https://brainly.com/question/27550874
#SPJ4
.
What is wrong with the following code? publicstatic char grade(int score) { if (score >= 9) { return 'A'; } else if (score >= 8) { return 'B'; } else if (score >= 6) { return 'C'; } else if (score > 4) { return 'D'; } else if (score < 4) { return 'F'; } }
Answers
Answer:
c) No return statement for all possible logic paths
The question is inside the screenshot

Answers
Answer:
second choice
Some one help pls will mark brainless !!!!!
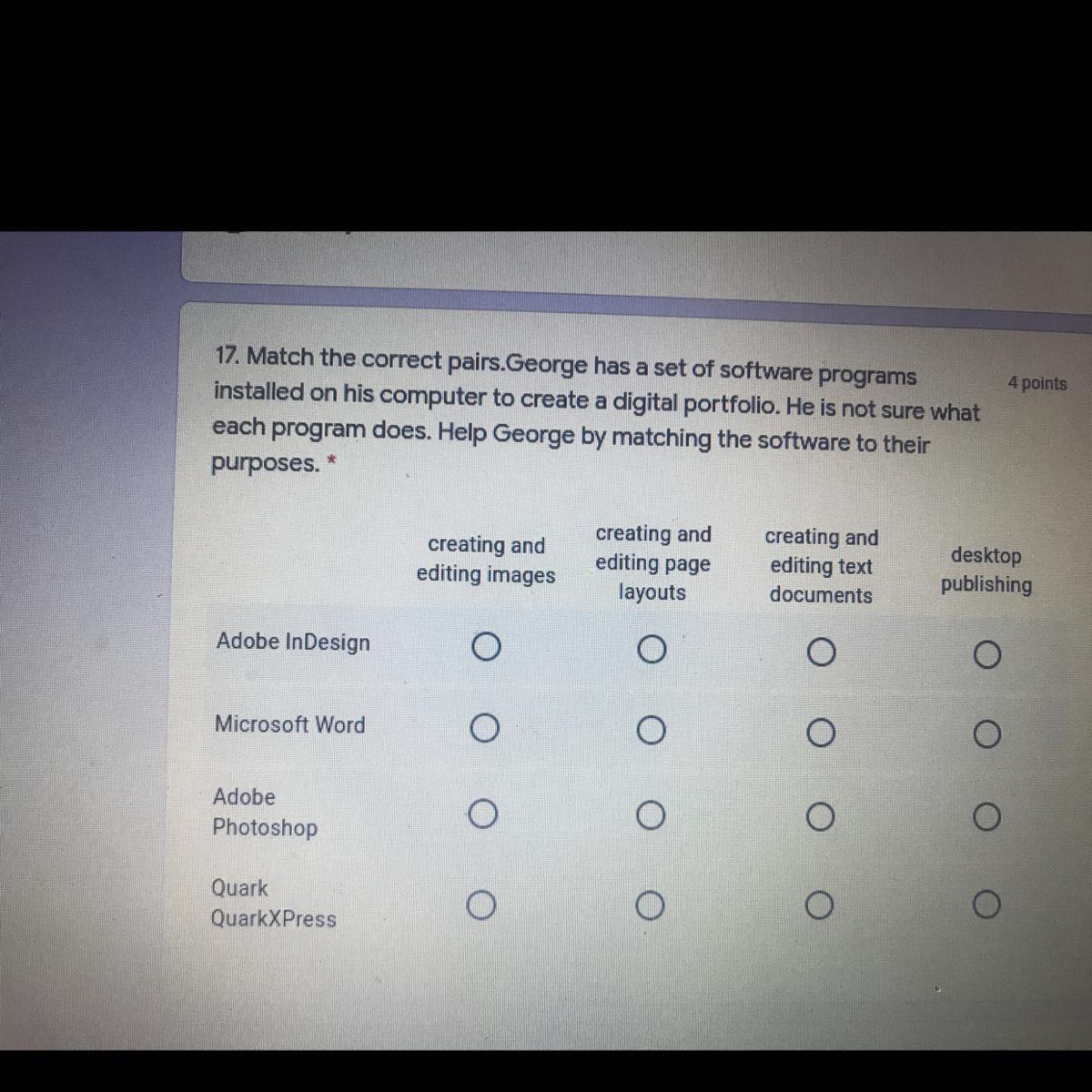
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail? Analysis report Resources document Scope Scope creep
Answers
Answer:
The given option "Resource document" is the correct answer.
Explanation:
Whenever it applies to chronology as either the documentation a resource records collection of specific documents should indeed be regarded as a component of this kind of record. The resource component encompasses a series of proclamations provided by the researcher including its memorandum, and therefore is willing to take responsibility for each other by the very same body is nonetheless accountable again for the file.The remaining three options do not apply to something like the specified scenario. And the latter is the correct one.
Answer:
Resource document
Explanation:
To select nonadjacent items, select the first item as usual, press and hold down the ____ key, and then while holding down the key, select the additional items.
Answers
Answer:
CTRL key
Explanation:
To select nonadjacent items in a spreadsheet, hold down the control key.
typically wlans involve multiple access points connected to various switches in the network. this type of infrastructure mode is known as a(n) ____.
Answers
Typically wlans involve multiple access points connected to various switches in the network. This type of infrastructure mode is known as a(n) distributed infrastructure mode.
In a distributed infrastructure mode, multiple access points are strategically placed throughout the network coverage area. Each access point is connected to a switch or wired network infrastructure.
This setup allows for broader coverage and seamless roaming for wireless devices within the network.
The distributed infrastructure mode enables the creation of a single logical network where wireless clients can connect to any access point within the coverage area and maintain connectivity as they move.
The access points work together to provide a unified wireless network, allowing users to seamlessly roam between different access points without experiencing disruptions in connectivity.
To learn more about network: https://brainly.com/question/8118353
#SPJ11
what is an example of an absolute cell reference
Answers
Answer:
Absolute cell referencing uses dollar sign with the row number and column name. When any formula with absolute referencing is copied, the cell addresses used remain the same.
Explanation:
A Question 1 (3 points) Retake question Listen ▶ Lyrics, melodies and underlying musical notes all refer to the.... sound recording copyright music copyright master recording mechanical license
Answers
Lyrics, melodies, and underlying musical notes all refer to the music copyright.
Copyright is the legal right that belongs to an artist, publisher, or producer to be the sole user of a literary, musical, dramatic, or artistic work. Copyright laws grant creators of original works exclusive rights to the use, distribution, and display of their works. Copyright infringement happens when someone uses a creative work without the owner's permission.
In the context of music, the term "copyright" refers to the protection provided to original songs and music compositions. Lyrics and musical notes that make up a song are both protected by copyright. This means that anyone who wishes to use, record, or reproduce the song or composition must first acquire the necessary rights or licenses.
The mechanical license, master recording, and sound recording copyright are all related to the music industry and refer to different types of licenses and rights granted to music producers, artists, and copyright owners.
The mechanical license is granted to anyone who wants to create a cover or new version of a song. The master recording refers to the final version of a song that is used for commercial purposes, and the sound recording copyright refers to the protection provided to the sound recording of a song or musical composition.
To learn about copyright here:
https://brainly.com/question/357686
#SPJ11
The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that companies which process, store, or transmit credit and debit card information maintain a secure environment. TRUE FALSE
Answers
The given statement "The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that companies which process, store, or transmit credit and debit card information maintain a secure environment." is TRUE.
PCI DSS is a set of standards created by major card brands such as Visa, MasterCard, Discover, and American Express. It was established in 2004 to safeguard sensitive information and reduce fraud and data breaches in the payment card industry. The standard applies to all organizations that accept credit card payments, including merchants, financial institutions, and payment service providers, and is designed to ensure that they maintain a secure environment for the processing, storage, and transmission of cardholder data.
PCI DSS requires companies to implement a variety of security controls, including firewalls, encryption, and access control measures, and to undergo regular security audits to maintain compliance. The standard consists of six main goals and 12 requirements that provide specific guidance for protecting cardholder data. In summary, the Payment Card Industry Data Security Standard is a set of requirements that aims to ensure the security of payment card information, which is TRUE.
Learn more about Master card here,suppose that you have a mastercard and a visa and you typically use the mastercard because it gives you airmile points f...
https://brainly.com/question/29341193
#SPJ11
for linux files, the default permission is 666, and the default umask is 022. when a new file is created, it will be assigned 644 (rw-r--r--) permissions. if the umask is set to 027, what permissions will be assigned for newly created files?
Answers
If the umask is set to 027, 640 (rw-r——-) permissions will be given to newly created files in Linux files.
What are Linux files?
A partition or a disk drive's structured collection of files is referred to as a Linux file system.
A memory segment known as a partition houses a particular set of data.
Different memory divisions may exist in our machine.
Typically, a file system is present on every partition. In contrast, the Linux/Unix operating system organizes files into a tree-like structure beginning with the root directory, as illustrated in the image below.
The root directory serves as the starting point for the whole Linux/Unix file system hierarchy.
So, in the given situation, for newly created files, 640 (rw-r——-) permissions will be assigned if the umask is set to 027.
Therefore, if the umask is set to 027, 640 (rw-r——-) permissions will be given to newly created files in Linux files.
Know more about Linux files here:
https://brainly.com/question/25480553
#SPJ4
What is a microsoft protocol used to synchronize microsoft exchange e-mail, contacts, and calendars that has become widely used across a range of mobile os platforms and hardware vendors, including apple and android devices
Answers
DKIM is a widely used technique for email authentication that includes a digital signature in sent messages.
What has made Microsoft famous?We teach and accredit developers and integrators of computer systems, and we offer consultancy, product, and solution support services. We also provide cloud-based solutions, which make use of pooled computing resources housed in central data centers to provide software, services, and content to consumers through the Internet.
Bill Gates called Microsoft America for a reason.Two childhood friends from Seattle, Bill Gates & Paul G. Allen, adapted the popular mainframe computer science language BASIC for use on the Altair, an early computer system (PC), in 1975. A short while later, Gates and Allen established Microsoft, naming it after the phrases software and microcomputer.
To know more about microsoft visit:
https://brainly.com/question/26695071
#SPJ4
Who is your favorite person from squid game?
Answers
Answer:
gi hun!
Explanation:
hes kinda...
Submit a report outlining the steps you will take to obtain digital evidence. In your report you must include the legal requirements, ethical considerations, and the digital sources you will be investigating in hopes of recovering data and collecting evidence to determine who was responsible for the data exfiltration.
For all assignments, remember the following important elements:
Proofread for spelling, grammar, and punctuation.
You may respond in bullet form for this project, but use standard written English. Do not use texting abbreviations or other similar shortcuts.
Answers
The steps you will take to obtain digital evidence.
One has to Respond First. Then a Search and Seizure is ordered.There is the Evidence Collection. There is the Securing of the Evidence. There is Data Acquisition stage.Then there is Data Analysis. Then there is Evidence Assessment. Then there is Documentation and Reporting.The last is expert witness testimony.What is Digital evidence?Digital evidence is known to be a kind of information that is often saved or transmitted in a method that uses binary form that can be relied on in case of court.
Note that it is one that can be found on a computer hard drive, a mobile device such as phone, among other means.
Hence, The steps you will take to obtain digital evidence.
One has to Respond First. Then a Search and Seizure is ordered.There is the Evidence Collection. There is the Securing of the Evidence. There is Data Acquisition stage.Then there is Data Analysis. Then there is Evidence Assessment. Then there is Documentation and Reporting.The last is expert witness testimony.Learn more about digital evidence from
https://brainly.com/question/18566188
#SPJ1
Which term was used to define the era of the Internet, when the web became a "platform" for user-generated input, as opposed to static web pages?
A. web 1.0
B. usernet
C. AOL
D. web 2.0
Answers
Hello, The answer to your question is:-
Option "Web 2.0"
Reference and proof:-
Web 2.0 refers to websites that emphasize user-generated content, ease of use, participatory culture and interoperability (i.e., compatible with other products, systems, and devices) for end users.
Hope it helps you...
Answered by Benjemin ☺️
✅
How do clinical information systems with decision support incorporate evidence-based information?.
Answers
Clinical Information systems helps in decision making by analyzing the data within the EHRs which reminders to assist the healthcare.
What is Clinical Information system?Clinical information system is the data which gives immediate information of the patients about their medical history, X-rays, laboratory reports etc.
CIS helps to support the evidence based information by analyzing the data within the EHRs which reminders to assist the healthcare.
It is also applicable cardiovascular disease (CVD) prevention also gives information on treatment, medication for changes in the health.
Learn more about Clinical information system here:
https://brainly.com/question/14700439
#SPJ1
How does a file reader know where one data item begins and another starts in a data file?
Python recognizes the end of one data item and the beginning of the next because they are separated by ___.
Answers
The way that a file reader know where one data item begins and another starts in a data file is option A: Every line in a text file has a hidden EOL (end of line) set of characters.
Python recognizes the end of one data item and the beginning of the next because they are separated by a comma-separated sequence.
What is the process of retrieving data from a file called?When the data held in them cannot be accessed normally, data recovery in computing is the process of restoring deleted, inaccessible, lost, corrupted, damaged, or formatted data from secondary storage, portable media, or files.
One line is read from the file and returned as a string using the readline function. The newline character is present at the end of the string readline returns.
An ordered group of items is known as a list, and each value is given an index. The components of a list are referred to as its elements.
Therefore, the location of the subsequent item to be read from a file is indicated by the read position of that file. The read position is initially set to the file's beginning.
Learn more about Python from
https://brainly.com/question/26497128
#SPJ1
See options below
How does a file reader know where one line starts and another ends?
Every line in a text file has a hidden EOL (end of line) set of characters.
Python knows how many characters to expect in a line.
The last item in a line of data does not have a comma after it.
Every line starts with a BOL (beginning of line) character.
Explain in your own words what a computer is. Expose in your answer the parts, operation, what it serves us for, etc. Why do we say that the computer is an electronic device?
Answers
Answer:
Explanation:
What is a computer?
A computer is an electronic device that manipulates information, or data. It has the ability to store, retrieve, and process data. You may already know that you can use a computer to type documents, send email, play games, and browse the Web. You can also use it to edit or create spreadsheets, presentations, and even videos. A computer has these basic parts: Monitor, keyboard, mouse and system unit
This programming language adds functionality to web pages.
JavaScript
SQL
Python
HTML
Answers
Among the programming languages listed, JavaScript is the language that adds functionality to web pages.
The correct answer to the given question is option A.
JavaScript is a client-side scripting language that enables interactivity and dynamic effects on web pages. It allows developers to create responsive and engaging web pages that can change in real-time based on user input or other events. It is widely used for front-end development along with HTML and CSS, and is supported by all modern web browsers.
SQL, on the other hand, is a database language used for managing and manipulating data in relational databases. It is not used for adding functionality to web pages, but rather for handling data on the server-side. Python is a general-purpose programming language that can be used for various applications, including web development, but it is not specifically designed for web pages. HTML, on the other hand, is a markup language used for creating the structure and content of web pages, but it does not add functionality.
In summary, JavaScript is the programming language that adds functionality to web pages, while SQL is used for database management, Python is a general-purpose programming language, and HTML is used for creating the structure and content of web pages.
For more such questions on JavaScript, click on:
https://brainly.com/question/16698901
#SPJ8
a hacker takes advantage of an open bluetooth connection to send a virus to a users smartphone. what kind of security breach has occured
Answers
A hacker taking advantage of an open Bluetooth connection to send a virus to a user's smartphone is an example of a security breach called "Bluejacking."
How does bluejacking occur?Bluejacking occurs when an attacker exploits vulnerabilities in the Bluetooth protocol to gain unauthorized access to a device. In this case, the hacker used the open Bluetooth connection to transmit a malicious payload (the virus) to the user's smartphone.
This security breach highlights the importance of securing Bluetooth connections, maintaining up-to-date software, and being cautious about connecting to unfamiliar devices.
Learn more about Hackers at
https://brainly.com/question/17881896
#SPJ11
The while statement is used to exit a program loop before the stopping condition is met. TRUE OR FALSE.
Answers
The statement "The while statement is used to exit a program loop before the stopping condition is met" is FALSE. A while statement is used to repeatedly execute a block of code as long as a specified condition remains true. The loop will only exit when the stopping condition is no longer true. If you want to exit a loop before the stopping condition is met, you can use a "break" statement within the loop.
A while statement is a control flow statement in programming that allows a block of code to be executed repeatedly as long as a specified condition is true.
The while loop evaluates the condition before executing the block of code. If the condition is true, the code block is executed, and then the condition is checked again. This process continues until the condition becomes false.
The stopping condition is the condition that, when evaluated as false, causes the loop to exit. It is typically defined based on certain criteria or calculations within the loop.
If the stopping condition is not met, the while loop continues to execute the code block. It does not exit the loop until the condition evaluates to false.
However, if there is a need to exit the loop before the stopping condition is met, you can use a "break" statement within the loop. The break statement allows you to terminate the loop prematurely and immediately move to the next statement after the loop.
By using the "break" statement, you can introduce additional conditions or logic within the loop to determine when to exit based on specific requirements or situations.
Learn more about while statement:
https://brainly.com/question/30479478
#SPJ11