What does it mean that encryption is a deterministic process?
Answers
Encryption is a deterministic process, which means that when you apply the same encryption algorithm and key to identical plaintext data, you will consistently get the same encrypted output.
When we say that encryption is a deterministic process, it means that for a given set of input data, the output of the encryption process will always be the same. In other words, if you encrypt the same data using the same encryption algorithm and key, you will always get the same encrypted output.
This is important in cryptography because it ensures that the encrypted data can be reliably decrypted by the intended recipient, as they will know exactly what encryption process was used to create it.
Overall, encryption is a complex process that involves transforming data into a form that is unreadable without the appropriate decryption key, and the deterministic nature of this process helps to ensure its reliability and security.
Visit here to learn more about Encryption:
brainly.com/question/4280766
#SPJ11
Related Questions
what are the main components of a magnetic hard disk? describe each component.
Answers
The main components of a magnetic hard disk are: the platters, the read/write heads, the spindle motor, and the actuator arm.
The main components are as described below:
1. Platters: Platters are the circular discs coated with a magnetic material, where the data is stored. Multiple platters can be stacked in a hard disk to increase storage capacity.
2. Read/Write Heads: These components read and write data on the magnetic surface of the platters. The heads float on a thin layer of air, maintaining a small gap between them and the platter surface to prevent physical contact.
3. Spindle Motor: The spindle motor rotates the platters at a constant speed, typically between 5,400 and 7,200 RPM for most consumer hard drives. This rotation enables the read/write heads to access data stored on the platters.
4. Actuator Arm: The actuator arm is a mechanical component that moves the read/write heads across the platters' surfaces, allowing them to access different tracks and sectors where the data is stored.
These components work together to store, retrieve, and manage the data on a magnetic hard disk.
To learn more about hard disk; https://brainly.com/question/29608399
#SPJ11
What best describes the difference between plagiarism and fair use?
a Plagiarism is copying material without crediting the source, while fair use is a limited, nonprofit use.
b Plagiarism is copying material for profit, while fair use is a limited, non-profit use.
c Plagiarism is any copying of material without credit to the source, while fair use is unlimited nonprofit use.
d Plagiarism allows for unlimited, nonprofit use, while fair use is copying material for profit.
Answers
Answer:
What best describes the difference between plagiarism and fair use?
Explanation:
b Plagiarism is copying material for profit, while fair use is a limited, non-profit use.
Answer:
Its A Not B!!!!!
Plagiarism is copying material without crediting the source, while fair use is a limited, nonprofit use.
Explanation:
Which data format type will increase the cell width instead of overlapping into empty cells?
a. number
b. general
c. text
d. date
Answers
Number is a data format type that will widen the cell rather than encroaching into empty ones.
How can I adjust a cell's size without altering the entire column?Combine several cells. One choice is to merge multiple cells if you want to increase the size of a cell without changing the row or column as a whole. By combining two or more cells into one that spans several rows or columns, you can merge cells.
How can I make Excel's cell sizes larger?Under the Home tab, in the Cells group, select Format. Simply choose Default Width from the Cell Size menu. Click OK after entering a new value in the Standard column width box.
To know more about data format type visit:-
https://brainly.com/question/30019805
#SPJ4
Which phrase is the best definition of sparklines in Excel 2016?
A. a type of graphic that users can insert into a worksheet
B. a type of mini chart that users can insert into a worksheet
C. a simple image that is displayed in Excel
B. a link to an outside source that is referenced in a worksheet
Answers
Answer:
The correct answer is:
B. a type of mini chart that users can insert into a worksheet
Explanation:
Microsoft excel is a spreadsheet software that is used for calculations and making payrolls.
Excel provides many visual features to display the data in graphical form. One of them is Spark lines.
Spark lines are used to show trends and variations in the collected data. Spark lines are just like mini charts.
So,
From the given options the best option is: B. a type of mini chart that users can insert into a worksheet
Hence,
The correct answer is:
B. a type of mini chart that users can insert into a worksheet
A contact list is a place where you can store a specific contact with other associated information such as a phone number, email address, birthday, etc. Write a program that first takes in word pairs that consist of a name and a phone number (both strings), separated by a comma. That list is followed by a name, and your program should output the phone number associated with that name. Assume the search name is always in the list. Ex: if the input is: joe,123-5432 linda,983-4123 frank,867-5309 frank the output is: 867-5309.
Answers
Using the knowledge in computational language in python it is possible to write a code that first takes in word pairs that consist of a name and a phone number (both strings), separated by a comma.
Writting the code:# Store name numbers pairs inputs in a list splitted on whitespaces
namesAndNumbersListInpWithComma = input().split(" ")
# Input the name on next line
nameOn2ndLineToLookfor = input()
# Dictionary to map the names to numbers
mappedDictOfNameandCorrsNums = {}
# Go over namesAndNumbersListInpWithComma list
for indxOfProgLoop in range(0, len(namesAndNumbersListInpWithComma)):
# Get name and number from each item (like get 'Joe', and '123-5432' from 'Joe,123-5432')
# Split on comma and then get the first item of list
nameToBeMappedInDict = namesAndNumbersListInpWithComma[indxOfProgLoop].split(",")[0]
# Split on comma and then get the second item of list
numToBeMappedInDict = namesAndNumbersListInpWithComma[indxOfProgLoop].split(",")[1]
# Store name and corresponding number into dictionary 'mappedDictOfNameandCorrsNums'
mappedDictOfNameandCorrsNums[nameToBeMappedInDict] = numToBeMappedInDict
# Print the asked number with no whitespaces at the start or end by using the mapped dictionary
print((mappedDictOfNameandCorrsNums[nameOn2ndLineToLookfor]).strip())
See more about python at brainly.com/question/12975450
#SPJ1

What is ABC computer?
Answers
Answer: The Atanasoff–Berry computer was the first automatic electronic digital computer. Limited by the technology of the day, and execution, the device has remained somewhat obscure. The ABC's priority is debated among historians of computer technology, because it was neither programmable, nor Turing-complete.
Explanation:
Identify the authors of the books Becca Nelson ordered. Perform the search using the customer name.
a)
The SQL statement with the traditional approach
Query:
SELECT a.lname, a.fname, b.title FROM books b, orders o, orderitems i, customers c, bookauthor t, author a
WHERE c.customer# = o.customer#
AND firstname = 'BECCA'
AND lastname = 'NELSON'
AND o.order# = i.order#
AND i.isbn = b.isbn
AND b.isbn = t.isbn
AND t.authorid = a.authorid;
Sample Output:
Answers
The SQL statement with the traditional approach:
Query:
SELECT a.lname, a.fname, b.title
FROM books b, orders o, orderitems i, customers c, bookauthor t, author a
WHERE c.customer# = o.customer#
AND c.firstname = 'BECCA'
AND c.lastname = 'NELSON'
AND o.order# = i.order#
AND i.isbn = b.isbn
AND b.isbn = t.isbn
AND t.authorid = a.authorid;
Sample Output:
This search will show the author's last name, first name, and the title of each book that Becca Nelson has ordered.
To know more about SQL, click here:
https://brainly.com/question/20264930
#SPJ11
what does the box mean when texting
Answers
Answer:
This means that your device's operating system did not recognise part of the message.
Explanation:
Martha is developing a software program in C++ and has a question about how to implement a particular feature. She performs an online search and finds a link to a site written by a programmer with posts about tips and tricks in using the C++ language. What kind of resource did she find? a forum a blog a tutorial an online help site
Answers
Answer:
A blog
Explanation:
A blog is a regularly updated website or web page, typically one run by an individual or small group, that is organised by posts.
Answer:
Martha found a blog
if you were setting up a performance max for store goals campaign, which of these manual inputs would you need to provide?
Answers
To set up a performance max for a store goals campaign, you need to provide ad creatives, target audiences, budget, bidding strategies, and duration.
Performance Max is a machine learning-based tool that optimizes your advertisements across G0ogle's inventory for maximum performance. Store visits, sales, and lead generation are among the available objectives. With Store Visits as the key aim, Performance Max for Store Goals Campaign is a strategy that aims to help you get the most out of your business data by automatically choosing the best products to advertise and where to advertise them.
Ad creatives refer to the content you use to advertise your store goals campaign, such as images, videos, and text. Target audiences refer to the people you want to reach with your campaign, such as gender, age, or location. Budget refers to the amount of money you are willing to spend on your campaign. Bidding strategies refer to the way you want to bid on impressions or clicks for your ads. Finally, duration refers to how long you want your campaign to run.
Learn more about the store goals campaign https://brainly.com/question/30066196
#SPJ11
Nadia has inserted an image into a Word document and now would like to resize the image to fit the document befter. What is the quickest way to do this? keyboard shortcut sizing handles context menu sizing dialog box
Answers
Answer:
To resize the document, Nadia needs to press
Command +>/ Ctrl+> to increase the size of the frame and its contents by 1%.
Or press Command +</ Ctrl+< to decrease the size of the frame and its contents by 1%
Question 5 of 10
If you pay the balance of your credit card bill before the due date, how much
do you pay?
OA. The full amount that you owe
B. The minimum payment on your bill
C. The full amount you owe, plus a service fee
D. The full amount you owe, plus interest for the past month
SUBMIT
Answers
Answer:
b
explination.
By paying the credit card dues early, you will have an advantage over the others as the credit card issuer will report a lower balance to the credit bureaus. This will reflect in your credit report and you can have an edge over the others for a lower credit utilization ratio.
In a day, a car passes n
kilometers. How many days does it take to travel a route of length m
kilometers?
The program receives as input in the first line a natural number n
and in the second line a non-negative integer m
. Python code
Answers
#Calculate days.
def calculateDay(m, n):
assert isinstance(m, int) and m >= 0, "m should be a natural number."
assert isinstance(n, int) and n > 0, "n shouldn't be negative."
return m/n
#Main function
def Main():
m, n = input().split()
print(f'Result: {calculateDay(int(m),int(n)):.2f} days.')
#Point.
if(__name__ == "__main__"):
Main()

1. What are the biggest risks when using the public Internet as a Wide Area Network (WAN) or transport for remote access to your organization’s IT infrastructure?
Answers
Answer:
The problems or risk when using a WiFi is that, hackers often have the ability to position themselves between the user and the end point connection. and once these hackers gains access to your information and privacy, u might lose important documents or contents.
It is of utmost importance that when an end user is using a public WiFi as a WAN, he/she must ensure to browse with VPN turned on, and the sharing options turned off.
Explanation:
Solution
One of the biggest risk with public WiFi is the ability or capacity for hackers to position themselves between you (user) and the point of connection. so instead of communicating directly with the hotpot, at several times you end up sending your information to the hacker.
The hacker also have access or privileges to every information you send out such as credit card information, emails and so on. once the hacker gains access to that information, you run into trouble.
As an end user when making use of public WiFi to ensure to browse with VPN (Virtual private Network) on and turned off sharing options
write a program to input a number.Find the sum of digits and number of digits
Answers
omg a computer program
i love it
okay so i will assume taht you want the program to be in python
here we go
a = int(input("Enter a number ")
b = int(input("Enter another number ")
sum = a + b
def Digits(sum):
count = 0
while sum != 0:
sum //= 0
count += 1
return count
print(f"Sum is {sum} \nnumber of digits are {Digits(sum)}")
Answer:
#Sum of Digits
a = int(input("Enter a number: "))
sumofdigits = sum(int(dig) for dig in str(number))
print("Sum of digits: ", sumofdigits)
# Number of digits
count = 0
print ("Total number of digits : ",len(str(abs(a))))
Explanation:
It is pretty self-explanatory however, I will tell it to you anyways. So, the sum of digits iterates to each digit and adds them up. For the number of digits, it uses in-built functions (length, string and absolute)
which output will be displayed by the following program?
print(Grade List)
print(100)
print(93)
print(82)
print(Total)
print(100+93+82)
Answers
Answer:SyntaxError: unexpected data type
Explanation:I just took the test and i tried the code in python
:) good luck on the test!!
The output for the given program will be SyntaxError: invalid syntax.
What is invalid syntax?Invalid syntax simply implies that the code one wrote cannot be interpreted as valid Python instructions. "Syntax" called to the rules and structures of a language, both spoken a s well as written.
Python creates syntax errors when it transforms source code to byte code. They usually implies that something is wrong with the program's syntax.
For illustration: The message is redundant when the colon at the end of a def statement is removed. SyntaxError: insufficient syntax.
Here are some examples of Python syntax errors: x, y = myfunction Otherwise, return x + y: print("Hello!") if mark is greater than 50 print("You succeeded!") If you arrive, print("Hi!") print("Bye!") else If flag is set, print("Flag is set!")
Thus, as per the given program, it is not showing proper format of the language so it will be showing SyntaxError.
For more details regarding programming, visit:
https://brainly.com/question/11023419
#SPJ5
you client wants a wireless access point with greater scalability than the one the isp has provided. best practice would be to disable the wireless and routing capabilities of the isp modem/router. what mode would we setup the isp modem router to? this question is beyond the scope of the lab but a very important one. do a little research if necessary to get this right, you will use this knowledge in the future
Answers
The wireless access point can then be connected to the modem/router through the LAN ports, allowing it to provide wireless connectivity throughout the home or office. This is the best practice for setting up an ISP modem/router when a client requires a wireless access point with greater scalability than the one provided by the ISP.
In order to provide greater scalability to a client who requires a wireless access point, it is recommended to disable the wireless and routing capabilities of the ISP modem/router. In order to accomplish this, it is necessary to set the ISP modem/router to bridge mode. Bridge mode is a network configuration that allows a device to work as a bridge, which helps in forwarding traffic between two networks. When a modem is in bridge mode, the modem is configured to pass-through the traffic directly to the connected device in order to enable them to carry out their tasks. This information can be useful in the future, particularly when setting up a network or troubleshooting issues related to network connectivity.
Learn more about Internet Service Provider : https://brainly.com/question/28342757
#SPJ11
which functions are performed by server-side code??
Answers
Answer:
The answer is explained below
Explanation:
Server side code is a code built using the .NET framework so as to communicate with databases which are permanent. Server side code is used to store and retrieve data on databases, processing data and sending requested data to clients.
This type of code is used mostly for web applications inn which the code is being run on the server providing a customized interface for users.
This processing activity involves pre-cooking.
Answers
Answer:
what processing activity ? xd
Explanation:
Answer:
no
Explanation:
When your grounded and the only thing you can get on is a computer........................oh wellllllllllllllllllllllllllllllllllllllll
Answers
Answer:
I feel your pain
i mean u could log into ur snap and ig but i mean sure why not???
Who has a stronger Air Force? USA or Russia?
-You get it right, then you get brainliest, and make sure you go check out my other questions so you can brainliest next time I post
-Friend me for question #4
Answers
Answer:
BOTH USA & RUSSIA
Explanation:
BOTH USA AND RUSSIA USA IS #1 and RUSSIA IS #2
What are enterprise messaging solutions most often used by business teams
for?
A. Cataloging and printing shipping labels for product deliveries
B. Sorting through and deleting a large number of company emails
C. Working on projects and communicating with each other to stay
updated
D. Distributing and tracking the use of computers in the workspace
Answers
Answer:
C. Working on projects and communicating with each other to stay updated
Explanation:
Working on projects and communicating with each other to stay
updated. Therefore, the correct answer is option C.
An corporate Messaging System (EMS) is a system that allows "program-to-program" messaging across corporate applications and systems.
Company messaging is typically used to integrate several company systems. It is a software interface that allows one programme to send loosely connected asynchronous data (messages) and store it in a message queue until the receiving programme can process it.
Typically, enterprise messaging falls under two categories:
Enterprise Messaging is classified into two types: promotional and transactional.
Bulk SMS messages are used to market a company's products and services. Bulk uploads, templates, phonebooks, scheduling messages, viewing delivery reports, and importing text and excel files are all common capabilities.Transactional SMSs: The SMS is typically sent by the sender's name (brand name) and is available 24 hours a day, seven days a week.Advantages of deploying an EMS:
Secure Messaging - The secure transmission of critical information and files to smartphones or feature phones.Notifications, reminders, and alerts are delivered globally.Two-way interactive SMS is commonly used for appointment confirmation, business process automation, surveys, and voting campaigns.Campaign Control/Management - Marketing programmes can be readily managed and measured in terms of performance.Delivery Assurance - Access to detailed message delivery can be gained.Customer preferences can be used to create customised messaging programmes using intelligent analytics and reporting.Therefore, the correct answer is option C.
Learn more about the enterprise messaging solutions here:
https://brainly.com/question/32271386.
#SPJ3
Select the correct answer.
Which of these components is utilized in use case diagrams?
A.
classes
B.
components
C.
flow
D.
actors
Answers
Answer:
B.components
Explanation:
how is the incorrect verb tense formatted. Taylor TAKE out the trash this morning. A in a different font face. B in a different font size. C in a different font D in italics . plz help quick and thx sorry not trying to be rude
Answers
Answer:
cant really tell cause you didnt use the original font and stuff. ig maybe A (different font size)
Explanation:
Do know who is in my dp?
Answers
Answer:
wut dat mean i dont understand
Explanation:
Answer:
Interested.... :-):-):-):-):-):-)
The task where verified data is coded or converted into machine
Answers
Input-this step is defined as the task of coding and converting the verify data into the machine breedable form so that it can be processed through software or an application.
Which of the following is hardware or software that monitors and controls network traffic to prevent security breaches?
O trojan horse
O firewall
O anti-malware
O keylogger
Need answer now!!!!!
Answers
Answer:
Firewall
Explanation:
A trojan horse and keylogger are types of malware. While an anti-malware software may come with a firewall built in, the firewall is still the thing monitoring network traffic.
What are you NOT allowed to do when building digital logic circuits? (Multiple correct answers are possible. Wrong answers will deduct points.)Connect multiple inputs of different gates.Connect multiple inputs of the same gate.Connect multiple outputs of different gates.Connect an output of a logic gate to two inputs of different gates.Connect an output of a logic gate to twelve inputs of different gates.
Answers
When building digital logic circuits, you should not:
a. Connect multiple outputs of different gates.
d. Connect an output of a logic gate to twelve inputs of different gates.
What is a digital logic circuit?
Digital systems are built using digital logic circuitry. These logic circuits are a collection of logic gates that demonstrate the logical equality of two separate sets of binary numbers.
Before producing any form of output, every logic circuit needs at least one input. Inputs and outputs of digital logic are frequently binary.
Therefore, the correct options are a and d.
To learn more about the digital logic circuit, refer to the link:
https://brainly.com/question/30388552
#SPJ1
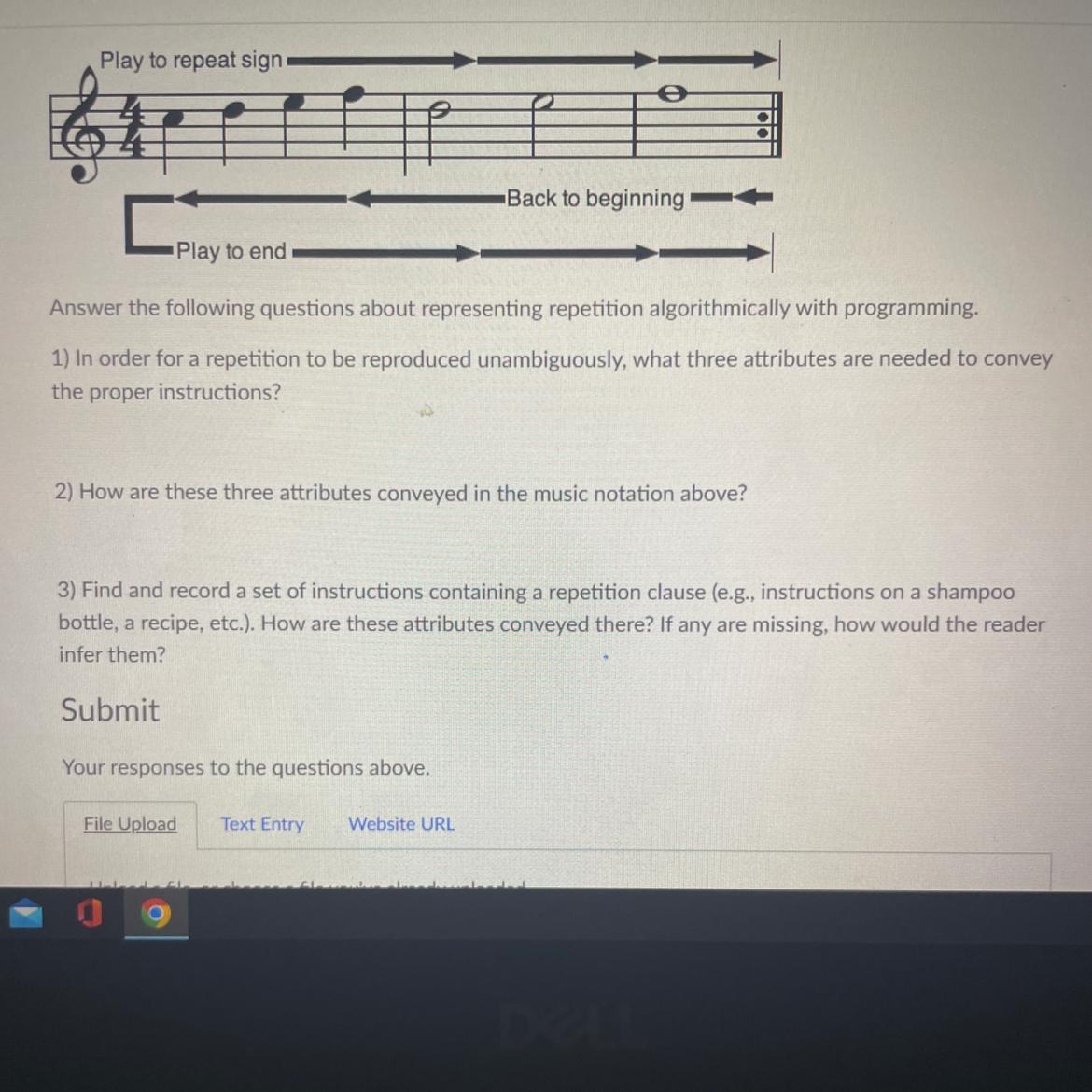
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
Q: what is the addressing mode for the following instruction: (B139), BL Immediate mode Register Mode Indirect mode Direct mode O Indexed Addressing Mode MOV* 2 points
Answers
The addressing mode for the instruction (B139) is immediate mode.
Immediate mode is an addressing mode in which the operand value is directly specified in the instruction itself. In this mode, the instruction contains a constant value or an immediate data that is used as the operand. The value is typically specified using a numeric or symbolic representation. In the given instruction (B139), the value "B139" is directly specified as the operand, indicating an immediate mode addressing.
Immediate mode is commonly used when the operand value is known at compile time or when there is a need to perform immediate calculations or comparisons. It allows for efficient and concise coding by eliminating the need for extra memory accesses or register usage. However, it also has limitations as the immediate value is fixed and cannot be modified during program execution.
In the context of assembly language programming, understanding different addressing modes is essential for effective program design and optimization. Each addressing mode offers unique benefits and trade-offs in terms of code efficiency, memory usage, and flexibility. By choosing the appropriate addressing mode, programmers can tailor their instructions to efficiently manipulate data and perform desired operations.
To learn more about programming click here:
brainly.com/question/14368396
#SPJ11