What are two characteristics of the application layer of the TCP/IP model? (Choose two.)the creation and maintenance of dialogue between source and destination applicationsclosest to the end user
Answers
The application layer of the TCP/IP model is responsible for providing network services to end-user applications. This layer interacts directly with users and plays a crucial role in communication between networked devices.
Two characteristics of the application layer in the TCP/IP model are:
The creation and maintenance of dialogue between source and destination applications: The application layer manages communication between applications by establishing, maintaining, and terminating connections. It ensures that data is exchanged reliably and accurately between the source and destination devices.Closest to the end user: The application layer is the highest layer in the TCP/IP model, which means it is the closest to the end user. This layer is where users interact with network applications, such as email, web browsing, and file sharing. It translates user inputs into network commands and processes data received from the network for the user.In summary, the application layer of the TCP/IP model is responsible for managing communication between network applications and is the layer closest to the end user. It creates and maintains dialogue between source and destination applications, ensuring reliable and accurate data exchange.
To learn more about TCP/IP, visit:
https://brainly.com/question/27742993
#SPJ11
Related Questions
an online b2b transaction uses a(n) _____ network to exchange information on the web.
Answers
An online b2b transaction uses an electronic network to exchange information on the web. In a B2B (business-to-business) transaction, companies communicate and exchange information with each other through electronic means.
The network used can be a combination of various technologies such as the internet, intranet, extranet, and virtual private networks (VPN). These networks allow businesses to securely communicate and share data with their partners and suppliers in a cost-effective and efficient manner. Additionally, these networks can also facilitate the automation of various business processes, including procurement, sales, and inventory management.
An online b2b transaction relies on an electronic network, which can be a combination of various technologies, to facilitate the exchange of information between businesses. EDI networks facilitate this process by enabling the structured transmission of data between organizations, allowing them to share information such as purchase orders, invoices, and shipping notices efficiently and securely.
To know more about electronic network visit:
https://brainly.com/question/8808445
#SPJ11
statements are used for creating tables, relationships, and other structures. a. ddl b. dml c. tcl d. dcl
Answers
A. DDL (Data Definition Language) statements are used for creating tables, relationships, and other structures. DDL is a subset of SQL (Structured Query Language) that is used to define and manage the structures and constraints of a database. Common DDL statements include CREATE (to create a new database or table), ALTER (to modify the structure of an existing database or table), and DROP (to delete a database or table).
DML (Data Manipulation Language) statements are used to manipulate data in a database, such as SELECT, INSERT, UPDATE, and DELETE.
TCL (Transaction Control Language) statements are used to manage the transactions in a database, such as COMMIT, ROLLBACK, and SAVEPOINT.
DCL (Data Control Language) statements are used to manage user access to a database, such as GRANT and REVOKE.
Learn more about Data Definition Languag here:
https://brainly.com/question/30407588
#SPJ11
The statement used for creating tables, relationships, and other structures is DDL, which stands for Data Definition Language. The correct answer is option a.
DDL statements are used to define the database schema, which includes creating, altering, and dropping database objects such as tables, views, indexes, constraints, and sequences. Some examples of DDL statements are CREATE, ALTER, and DROP.
DML (Data Manipulation Language) statements are used for inserting, updating, and deleting data from a database. Examples of DML statements are INSERT, UPDATE, and DELETE.
TCL (Transaction Control Language) statements are used to manage transactions within a database. Some examples of TCL statements are COMMIT, ROLLBACK, and SAVEPOINT.
DCL (Data Control Language) statements are used to control access to data within a database. Examples of DCL statements are GRANT and REVOKE.
Therefore option a is the correct answer.
Learn more about the database:
https://brainly.com/question/24027204
#SPJ11
Contrast the ways that Maggie walker and Sarah “madam C.J” Breedlove walker supported the black community through their work
Answers
Although Madam C.J. Walker assisted the community by developing hair and beauty products for black women, Maggie Walker supported the community by starting a bank and offering financial services.
How did Madam C.J. Walker support the African-American community?Her political and philanthropic influence grew along with her money. Walker gave to the YMCA, covered the Tuskegee Institute tuition for six African Americans, and participated in the fight against lynching by giving $5,000 to the NAACP's programmes.
What was the Walker approach she promoted in her goods?The name of her initial line of goods was "Madam Walker's Amazing Hair Grower." The "Walker Way" was her own strategy for selling goods. She employed "The Walker Way" by selling door to door.
To know more about beauty products visit:-
https://brainly.com/question/26455031
#SPJ1
Which of the following is not a common integrated I/O port?FireWireRJ-45UEFIUSB
Answers
UEFI is not a common integrated I/O port.
UEFI (Unified Extensible Firmware Interface) is a type of firmware that is used to boot up a computer system. It is not an I/O (input/output) port or a physical connector used to connect peripherals to a computer.
FireWire, RJ-45, and USB are all common integrated I/O ports. FireWire (also known as IEEE 1394) is a high-speed serial bus interface that is used for connecting devices such as digital cameras and external hard drives to a computer. RJ-45 is a type of Ethernet port that is used for connecting a computer to a local area network (LAN) via an Ethernet cable.
USB (Universal Serial Bus) is a standard interface for connecting a wide range of peripherals to a computer, such as keyboards, mice, printers, and external storage devices.
Learn more about UEFI here:
https://brainly.com/question/14353510
#SPJ11
Write a program that takes three numbers as input from the user, and prints the largest.
Answers
Answer:
I'll be using python:
__________________________
a=int(input("Enter a number :"))
b=int(input("Enter another number :"))
c=int(input("Enter last number :"))
lis=[a,b,c]
sort=sorted(lis)
print("The largest number is:", sort[1])
___________________________
Which command compiles the Java source code file Welcome.java?Select one:A. java Welcome.javaB. javac WelcomeC. compile Welcome.javaD. cd Welcome.javaE. javac Welcome.java
Answers
The command that compiles the Java source code file Welcome.java is option E: javac Welcome.java.
The javac command is the Java compiler command used to compile Java source code files (.java files) into bytecode (.class files) that can be executed by the Java Virtual Machine (JVM). In this case, running "javac Welcome.java" will compile the Welcome.java file, assuming the file is in the current directory. Once the compilation is successful, it generates a corresponding bytecode file (Welcome.class) that can be executed using the "java" command followed by the class name (e.g., "java Welcome"). Therefore, option E (javac Welcome.java) is the correct command to compile the Java source code file Welcome.java.
To know more about Java s click here,
https://brainly.com/question/33208576
#SPJ11
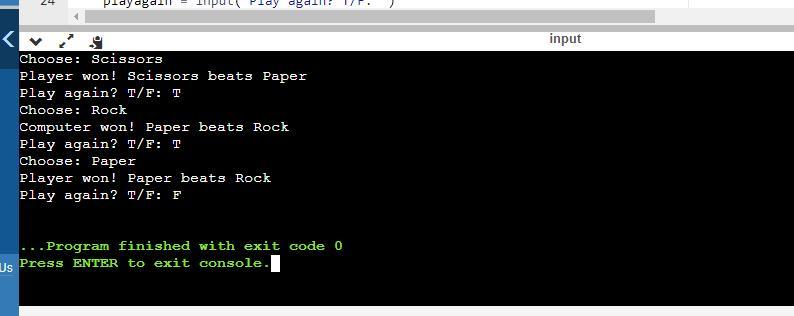
"write a program to play and score the paper-rock-scissor game. each of two users types in either p, r, or s. the program then announces the winner as well the basis for determining the winner: paper covers rock, rock breaks scissors, scissors cut paper, or nobody wins. be sure to allow the users to use lowercase as well uppercase letters. your program should include a loop that lets the user play again until the user says she or he is done."
Answers
The program is an illustration of conditional statements.
Conditional statements are used to execute instructions, if and only if certain condition or conditions are met.
Take for instance: If b = 5, print "ab"
The above print statement will only be executed, if the value of b is 5
The paper-rock-scissor program in Python where comments are used to explain each line is as follows,
#This imports the random module
import random
#This is used to control the repetition of the game
playagain ="T"
#The following is repeated until the user chooses not to play again
while(playagain == "T"):
#This generates a random choice for the computer
computer = random.choice(['Rock', 'Paper', 'Scissors'])
#This gets input for the player
player = input('Choose: ')
#If the player and computer choose the selection
if player == computer:
#Then, it's a tie
print('A tie - Both players chose '+player)
#If the player wins
elif (player.lower() == "Rock".lower() and computer.lower() == "Scissors".lower()) or (player.lower() == "Paper".lower() and computer.lower() == "Rock".lower()) or (player == "Scissors" and computer.lower() == "Paper".lower()):
#This prints "player won" and the reason
print('Player won! '+player +' beats '+computer)
#If otherwise,
else:
#This prints "computer won" and the reason
print('Computer won! '+computer+' beats '+player)
#This asks if the player wants to play again
playagain = input("Play again? T/F: ")
At the end of each round,
The program displays the winnerOr prints a tie, if there's a tieSee attachment for sample run
Read more about conditional statements at:
https://brainly.com/question/22078945
You are the digital forensics investigator for a law firm. The firm acquired a new client, a young woman who was fired from her job for inappropriate files discovered on her computer. She swears she never accessed the files. What questions should you ask and how should you proceed? Write a one- to two-page report describing the computer the client used, who else had access to it, and any other relevant facts that should be investigated
Answers
As a digital forensics investigator, the first step would be to gather as much information about the client's computer network as possible.
This would include the make and model of the computer, the operating system, and any installed software. It would also be important to know if any anti-virus or anti-malware software was installed and if it was up-to-date.
Next, I would ask the client about who else had access to the computer. This could include family members, roommates, or coworkers who may have used the computer. It would also be important to know if the computer was ever left unattended or unlocked.
In terms of the files in question, I would ask the client if she had ever seen them before or if she recognized the content. It would also be important to know when the files were created or modified and if there was any evidence of them being downloaded from the internet.
Based on the information gathered, the next step would be to conduct a forensic examination of the client's computer. This would involve creating a forensic image of the hard drive and analyzing the data for any evidence of the inappropriate files. It would also be important to look for any evidence of malware or hacking that may have been used to plant the files on the computer.
Once the examination is complete, a detailed report should be provided to the law firm outlining the findings and any potential evidence that may be relevant to the case. This report would also include any recommendations for further investigation or actions that should be taken.
To know more about network visit
https://brainly.com/question/26875099
#SPJ11
what technology can collect information to make decisions, reach conclusions, and combine information in new ways?
Answers
The technology that can collect information to make decisions, reach conclusions, and combine the information in a new way is known as Artificial Intelligence.
Artificial Intelligence is a realistic computing process that simulates human intelligence.
Artificial Intelligence can perform several functions, including speech detection, machine intuition, etc.
Artificial Intelligence is categorized into four including:
Reactive machines,Limited memory, Theory of mind,Self-awareness.Hence, in this case, it is concluded that the correct answer is Artificial Intelligence.
Learn more here: https://brainly.com/question/22826064
The following for loop is an infinite loop:
for(int j = 0; j < 1000;) i++;
True or false
Answers
True, this is an infinite loop because the condition for the loop to terminate (j < 1000) is never met. The variable being incremented is i, not j, so j remains at 0 and the loop continues to run indefinitely.
A loop is a programming construct that allows a set of instructions to be executed repeatedly until a certain condition is met. Loops are commonly used in computer programming to iterate through data structures or to automate repetitive tasks. There are two main types of loops: the for loop and the while loop.
A for loop is used to iterate through a sequence of values a fixed number of times. It consists of an initialization statement, a condition statement, and an update statement.
A while loop is used to execute a block of code repeatedly as long as a certain condition is true. It consists of a condition statement that is evaluated before each iteration of the loop.
Loops are an essential part of programming and are used in a wide range of applications, from simple scripts to complex algorithms.
Learn more about loop here:
https://brainly.com/question/13918592
#SPJ11
The statement "The following for loop is an infinite loop: for(int j = 0; j < 1000;) i++" is true.
The given for loop is :
for(int j = 0; j < 1000;)
i++;
This loop is an infinite loop. This is because the loop lacks an increment for the variable 'j' in the loop definition.
An infinite loop occurs when the loop's termination condition is never met, causing the loop to run indefinitely. In this case, the loop will continue to run because the variable 'j' remains at 0 and never reaches 1000. To fix this, the loop should include an increment for 'j', like this: for(int j = 0; j < 1000; j++).
To learn more about infinite loops visit : https://brainly.com/question/13142062
#SPJ11
What does the following if statement do?
if (num1 == Math.abs(num1))
Answers
This statement checks if num1 is equal to the absolute value of num1
For instance,
num1 = 4 and the absolute value of num1 = 4. This would run the code inside the if statement but if num1 = -1 the absolute value of num1 = 1 and the if stamtent would be skipped because -1 does not equal 1
this code for: 14- 15 2- f1 = input('Enter The Function: ', 's') for example x^2-2 I hope that the 3- f = inline (1) ; 4- y = input('Enter The Interval: ');for example [ 21 answer to the 5- n = input('Enter the Bamber of iterations: '); question is 6- t = input ("Enter the Tolerance: '); 7- a = y(1) ; b = y(2); within 25 8- 2 = fialv = f(b) minutes, after 9- i ziv> 10- disp('The Foo: Not Found, wrong Enterval!') which the portal 11- break for receiving 12- else 13- i = 0; questions from while i <= n my university will c - (a+b)/21 16- if f(c) == 0 Il abs((b-a)/2) <= t be closed and I disp([' The Root = ' num2 stric)]) will get the 18- break 19- elseif sign ((c)) == sign (f (a)) lowest marks. 20- a = 21- else 22 b-CI 23- end 24- i =i+1; 25- end 26- if i>n 27- disp('The Root Not Found, need more iterations!'); a) N-r method b)bisection method c) fixed -point method
Answers
Based on the implementation, the code corresponds to the b) bisection method for finding the root of a function.
The provided code snippet seems to be implementing the bisection method to find the root of a function. The algorithm involves iterating through a specified number of iterations to narrow down the interval where the root exists. Here's a breakdown of the code:
The code prompts the user to enter the function as an input string.
It then initializes variables and takes user inputs for the interval and number of iterations.
The code enters a while loop that iterates until the number of iterations is reached or until the root is found.
Within each iteration, it calculates the midpoint of the interval using the bisection formula: c = (a + b) / 2.
It checks if the function evaluated at the midpoint is equal to 0. If so, it breaks the loop as the root is found.
If the function evaluated at the midpoint has the same sign as the function evaluated at the start point (a), it updates the start point (a) to the midpoint (c).
Otherwise, it updates the end point (b) to the midpoint (c).
The iteration counter (i) is incremented.
After the loop, it checks if the iteration counter has exceeded the specified number of iterations and displays a message if the root is not found within the given tolerance.
If the root is found, it displays the root value.
Know more about bisection method here:
https://brainly.com/question/30320227
#SPJ11
Pls help me pls I’m struggling

Answers
Answer:
Forward(30)
Explanation:
To turn right you have to say right(Angle) and then forward(steps) to go that many steps in that direction
Robin has four copies of her midterm paper saved to a single folder on her
Windows computer. She wants to move each of these four files into a
separate folder within the existing one. How can Robin perform this task for
each file?
A. Right click on the folder containing all four files, select "Copy."
Open the same folder, select "Paste." Enter the new folder's title.
B. Open the folder containing all four files, right-click in the folder
window, select "New" enter the new folder's title, click on one file,
drag it into the new folder.
C. Open the folder containing all four files, right-click on one file,
select "New Folder," enter the new folder's title, click on the same
file, drag it into the new folder.
O
D. Open the folder containing all four files, right-click in the folder
window, select "New Folder," enter the new folder's title, click on
one file, drag it into the new folder.
Answers
Answer:
d
Explanation:
i took the test
Which hardware component interprets and carries out the instructions contained in the software.
Answers
Answer:
Processor
A processor interprets and carries out basic instructions that operate a computer.
what is file management?can please help me
Answers
In science class, Patricia is giving a presentation on the different types of flowers in her community. As part of her presentation, she wants to show the basic structure and parts of a flower. What kind of visual aid should she use?
a line graph
a diagram
a pie chart
a map
Answers
Answer:
a diagram
Explanation:
Giving presentation is one of the methods of imparting information and knowledge about a certain topic. For this purpose the visual aids like images, videos, maps and diagrams are used for better dispersal of the information. A diagram is a visual representation of a certain topic that helps in the detailed analysis.
In the given excerpt, Patricia has used a diagram to highlight the basic structure and parts of the flower.
Answer:
b
Explanation:
edge 2021
Where do you stand on the controversial encryption issue? Should governments like the United States be allowed to have an escrowed key to all encrypted communications? Is unfettered encryption a good thing for cyberspace?
Answers
Where you stand on the controversial encryption issue depends on your point of view.
Some people believe that the government should have an escrowed key to all encrypted communications to prevent terrorism and other criminal activities. Others believe that unfettered encryption is a good thing for cyberspace and that the government should not be able to access private communications.
Encryption is a crucial part of cybersecurity and is used to protect sensitive information. It can also be used to prevent cyberattacks and data breaches. However, encryption can also be used by criminals to hide their activities and communications from law enforcement agencies and the government.
Encryption can make it difficult for the government to track down terrorists and other criminals. However, giving the government a backdoor to encrypted communications could also lead to abuse of power and violations of privacy rights.
Learn more about encryption at
https://brainly.com/question/31375565
#SPJ11
Which of the following best describes what happens when we take unstructured data and organize it into structured data?
A. When unstructured data is organized into structured data there is some loss of data, but the data is in a much more usable format.
B. When we extract the the data from an unstructured source and organize it into a structured data set, no data is lost, it is just in a more usable format.
C. When data is taken from an unstructured data source and organized into a structured set of data, some data is lost, but the data is now much more useful.
D. When unstructured data is reorganized into a structured format there is no loss of data, it just simply becomes more useful in the new format.
Answers
Answer:
When unstructured data is organized into structured data there is some loss of data, but the data is in a much more usable format
Explanation:
Explain why it is important for you to understand and describe the basic internal and external components of a computer in the
workplace. How might you use this information?
Answers
Users can adequately describe to your boss or consumer if they know the identity of an internal part of a computer, i.e. RAM, Processor, HDD, motherboard, etc and the further discussion can be defined as follows:
When any problems in a few of our computers are present user have to know the computer part names like keyboard, cursor, printer, scanner, microphone, cam, etc.Users can explain easily which inner or outside part of a computer is problematic if a problem has been found.Therefore, We can easily deal with it and solve issues if we know of various components at work in a computer.
Learn more:
brainly.com/question/12899825
How does decryption work?
Answers
Answer:
Decryption is the process of reversing an encryption. i.e The process which convert encrypted data into its original form
Payton bought a couple new dog toys for her puppy. The bone she bought cost $5.25 and the frisbee cost $6.75. About how much did the toys cost?
Answers
Answer:
$12
Explanation:
1 00
5.25
+ 6.75
-------
12.00
Order the steps for using the Rules Wizard to create an email rule.
Select the Home tab, and
click Rules button.
Click New Rule, and select Make any exceptions, and
a template.
name the rule.
Edit a description of the
rule by adding values.
Select Manage Rules and
Alerts
Answers
To use the Rules Wizard to create an email rule, you can follow these steps:
Select the Home tab and click the Rules button.Click New Rule and select a template.Edit a description of the rule by adding values and making any exceptions.Name the rule.Select Manage Rules and Alerts to save the rule.What is the email rule about?Below is the process in a more detailed form:
Open your email client and go to the Home tab.Click the Rules button, which is usually located in the Move section of the ribbon.In the Rules dialog box, click the New Rule button.In the Rules Wizard, choose a template that best fits your needs. You can also choose to create a custom rule by selecting "Start from a blank rule."Follow the prompts in the wizard to specify the conditions and actions for the rule. You can specify values and exceptions, such as the sender or recipient of the email, or the subject of the email.Give the rule a name and click Finish to save the rule.Therefore, To manage your rules, click the Manage Rules & Alerts button in the Rules dialog box. From here, you can edit or delete existing rules, or create new ones.
Learn more about email rule from
https://brainly.com/question/4783467
#SPJ1
(a) Willow has created a hangman program that uses a file to store the words the program can select from. A sample of this data is shown in Fig. 3.
Fig. 3
crime, bait, fright, victory, nymph, loose.
Show the stages of a bubble sort when applied to data shown in Fig. 3.
(b) A second sample of data is shown in Fig. 4.
Fig. 4.
amber, house, kick, moose, orange, range, tent, wind, zebra.
Show the stages of a binary search to find the word "zebra" when applied to the data shown in Fig. 4.
Answers
(a) A bubble sort applied to the data in Fig. 3 produces these stages:
Loose, crime, bait, fright, victory, nymph
Crime, loose, bait, fright, victory, nymph
Bait, crime, loose, fright, victory, nymph
Fright, bait, crime, loose, victory, nymph
Victory, fright, bait, crime, loose, nymph
Nymph, victory, fright, bait, crime, loose.
(b) When a binary search is conducted in order to find the word "zebra" in the data in Fig. 4, the following yield occurs:
The search begins by looking at the list's middle item, which is "orange".
Hope to explain the bubble sortSince "zebra" comes after "orange" alphabetically, the search continues amongst the second half of the list.
The centermost item on this narrowed down list proves to be "tent", from there, it is deduced that "zebra" must go after "tent" alphanumerically.
Likewise, the process is repeated for the reminder of the sequence.
Moving forward, the search encounters "wind" in its midst, again concluding that zebra has to appear subsequently.
Finally, when observing the midpoint of the remainder, "zebra" is pinpointed as the desired result.
Learn more about bubble sort on
https://brainly.com/question/30395481
#SPJ1
if you were giving a presentation there were 35 people in the room including yourself and you were to shake every person's hand in the room would you shake 35 hands. is it true or false?
Answers
Answer:
False, unless you were to shake your own hand.
Explanation:
(1) Consider the following relational schema and a set of functional dependencies valid in the schema.
R = (A, B, C, D)
F = {A → C, C → D}
Find the highest normal form valid for the relational schema. If the schema is not in BCNF, then decompose the schema into the smallest number of relational schemas where each one is in BCNF. Try to enforce as many functional dependencies as possible in the decomposed schemas. List all derivations of functional dependencies, minimal keys, the highest normal forms, and decompositions (if necessary).
(2) Consider the following relational schema and a set of functional dependencies valid in the schema.
R = (A, B, C, D, E)
F = {AB → C, C → D, D → E}
Find the highest normal form valid for the relational schema. If the schema is not in BCNF, then decompose the schema into the smallest number of relational schemas where each one is in BCNF. Try to enforce as many functional dependencies as possible in the decomposed schemas. List all derivations of functional dependencies, minimal keys, the highest normal forms, and decompositions (if necessary).
(3) Consider the following relational schema and a set of functional dependencies valid in the schema.
R = (A, B, C, D, E)
F = {A → BCD, D → E}
Find the highest normal form valid for the relational schema. If the schema is not in BCNF, then decompose the schema into the smallest number of relational schemas where each one is in BCNF. Try to enforce as many functional dependencies as possible in the decomposed schemas. List all derivations of functional dependencies, minimal keys, the highest normal forms, and decompositions (if necessary).
(4) Consider the following relational schema and a set of functional dependencies valid in the schema.
R = (A, B, C, D, E)
F = {A → BD, B → C} Find the highest normal form valid for the relational schema. If the schema is not in BCNF, then decompose the schema into the smallest number of relational schemas where each one is in BCNF. Try to enforce as many functional dependencies as possible in the decomposed schemas. List all derivations of functional dependencies, minimal keys, the highest normal forms, and decompositions (if necessary).
Answers
The objective is to analyze and normalize the schemas, determining the highest normal form and performing decomposition if necessary.
What is the objective of the given questions regarding relational schemas and functional dependencies?The given questions pertain to the process of normalizing relational schemas based on functional dependencies. Normalization is a technique used to eliminate data redundancy and ensure data integrity in databases. The goal is to decompose a schema into smaller schemas that adhere to specific normal forms.
In each question, a relational schema (R) and a set of functional dependencies (F) are provided. The task is to determine the highest normal form valid for the schema. If the schema is not in Boyce-Codd Normal Form (BCNF), it needs to be decomposed into smaller schemas that satisfy BCNF.
To solve these questions, you need to analyze the functional dependencies, identify minimal keys, and assess the normal forms of the schema. Based on the dependencies, you can determine the highest normal form and perform decomposition if required.
For each question, provide a step-by-step explanation of the normalization process, including derivations of functional dependencies, identification of minimal keys, determination of the highest normal form, and decomposition (if necessary).
The specific solutions to these questions would require a detailed analysis of the functional dependencies and applying normalization rules, which exceeds the word limit for the explanation.
Learn more about objective
brainly.com/question/12569661
#SPJ11
The bubble sort is an easy way to arrange data in ascending order but it cannot arrange data in descending order. group of answer choices true false
Answers
The answer to the question is false. Bubble sort is a simple sorting algorithm that arranges data in ascending order by repeatedly swapping adjacent elements if they are in the wrong order. However, it is also possible to modify the bubble sort algorithm to sort data in descending order.
To sort data in descending order using the bubble sort algorithm, we can modify the swapping condition. Instead of swapping adjacent elements if they are in the wrong order, we swap them if they are in the correct order. This way, the larger elements will "bubble" towards the beginning of the list, resulting in the data being sorted in descending order.
For example, consider the following array: [5, 3, 1, 4, 2]. Using the modified bubble sort algorithm for descending order, the array will be sorted as [5, 4, 3, 2, 1].
In summary, the statement that the bubble sort cannot arrange data in descending order is false. By modifying the swapping condition, we can use the bubble sort algorithm to sort data in both ascending and descending order.
Learn more about sorting algorithm: https://brainly.com/question/13098446
#SPJ11
Animations in an html5 page are created by defining ________________ properties for a specific css selector.
Answers
Animations in an HTML5 page are created by defining animation properties for a specific CSS selector. These animation properties include:
1. `animation-name`: This property specifies the name of the animation. It refers to the keyframes that define what happens during the animation.
2. `animation-duration`: This property sets the duration of the animation in seconds or milliseconds.
3. `animation-timing-function`: This property defines the timing function used for the animation. It determines how the animation progresses over time.
4. `animation-delay`: This property specifies the delay before the animation starts.
5. `animation-iteration-count`: This property sets the number of times the animation should repeat. You can specify a finite number or use `infinite` to make it repeat indefinitely.
To know more about Animations visit:
https://brainly.com/question/29996953
#SPJ11
What color line appears under a word that is spelled incorrectly in power point
Answers
Answer:a wavy red line
Explanation:
Hope this helps
Can I have brainliest pls
Answer:
ReD
Explanation:
BeCaUsE
What is the value of x after the following
int x = 5;
x++;
x++;
x+=x++;
A)14
B)10
C)13
D)15
Answers
Answer:
Option D: 15 is the right answer
Explanation:
Initially, the value of x is 5
Note- x++ is a post-increment operator which means the value is first used in the expression and then increment.
After executing the x++, the value of x is 6
similarly again executing the next line and right now the value of x is 7
At last the value of x is 15.