What are the two access modes that are used when opening a file for input and output when pickling? (choose two.)
Answers
The two access modes that are used when opening a file for input and output when pickling are "rb" and "wb". The two access modes that are used when opening a file for input and output when pickling are "rb" and "wb".
1. "rb" stands for read binary mode. This mode is used when opening a file for reading or inputting data. It allows the program to read the file in binary format.
2. "wb" stands for write binary mode. This mode is used when opening a file for writing or outputting data. It allows the program to write data to the file in binary format.
In summary, "rb" is used for input or reading, while "wb" is used for output or writing when pickling.
To know more about modes visit:
https://brainly.com/question/28566521
#SPJ11
Related Questions
According to the video, which tasks do Police Patrol Officers perform? Select all that apply.
providing legal advice
helping lost children
cleaning up hazardous materials
O supervising workers in prisons
enforcing traffic laws
o completing paperwork
Answers
Answer:
The answer is B, E, and F
Explanation:
Based on the video, the tasks do Police Patrol Officers perform are:
Helping lost children. Enforcing traffic laws. Completing paperwork..What is the work of police in patrol?Due to advances in technology and the society, work, etc., the reason of patrol is known to be the same as always. They serve to:
The protection of property and lives.The prevention and also detecting crime.Carrying out other services.Learn more about Police from
https://brainly.com/question/26085524
T/F. Filters can be used to narrow the list of citing references
Answers
Answer: False
Explanation:
False. Filters are used to narrow down search results, but they cannot be used to narrow the list of citing references. The list of citing references refers to the articles that have cited a particular article and is typically provided by a citation database or search engine. This list cannot be filtered in the same way as search results because it is based on a specific article and its cited references. However, citation databases and search engines may provide tools to sort and analyze the list of citing references based on various criteria, such as the publication year or journal name.
PLEASE HURRY!!!!! Part of a program that does not work correctly
O Loop
O Mouse
O All programs are perfect
O Bug
Answers
Answer:
bug
Explanation:
A bug computer definition is referred to as a failure or a flaw in the software program. A Bug produces an incorrect or undesired result that deviates from the expected result or behavior.
define application software
Answers
Answer: An application software is a type of software that the user interacts with, while a system software is a type of software that the system interacts with.
Hope this helped you :)
What is the primary objective of the HIPAA security Rule?
Answers
The primary objective of the HIPAA (Health Insurance Portability and Accountability Act) Security Rule is to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI).
The HIPAA Security Rule sets standards for safeguarding sensitive health information in electronic form. Its main goal is to ensure that covered entities, such as healthcare providers, health plans, and healthcare clearinghouses, implement appropriate security measures to protect the privacy and security of individuals' health information. The Security Rule establishes specific administrative, physical, and technical safeguards that organizations must implement to secure ePHI against unauthorized access, use, and disclosure.
By adhering to the HIPAA Security Rule, covered entities are expected to implement comprehensive security programs, conduct regular risk assessments, develop policies and procedures, provide employee training, and employ security measures such as access controls, encryption, and audit controls. Ultimately, the Security Rule aims to enhance the overall security posture of the healthcare industry and safeguard individuals' sensitive health information in electronic form.
learn more about "Security":- https://brainly.com/question/28004913
#SPJ11
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
Which is an example of a natural separation of visitors from employees?
Bollard
Fencing
Security guard
Desk
A ) bollard. B)fencing c)security guard d)desk
Answers
Answer:
d) desk
Explanation:
srry if this is wrong ;
Brainstorming is a group process designed to stimulate the discovery of new solutions to problems. Can you brainstorm effectively in a remote or hybrid environment? Discuss how you can run a virtual brainstorming session successfully and give examples of available tools/software that will support your session.
Answers
Brainstorming is a group process that aims to stimulate the discovery of new solutions to problems. It typically involves a group of individuals coming together to generate ideas and share perspectives. While traditionally conducted in-person, brainstorming can also be effectively done in a remote or hybrid environment.
To run a successful virtual brainstorming session, you can follow these steps:
1. Set clear objectives: Clearly define the problem or challenge that needs brainstorming. Ensure that all participants have a clear understanding of the goal.
2. Select the right participants: Choose individuals who have diverse perspectives and expertise relevant to the problem at hand. Consider inviting team members from different departments or even external stakeholders.
3. Prepare in advance: Share any necessary background information or materials with the participants prior to the session. This will allow them to come prepared with ideas and insights.
4. Choose appropriate tools/software: There are various tools available to support virtual brainstorming sessions.
5. Facilitate the session: As the facilitator, ensure that all participants have equal opportunities to contribute. Encourage an open and supportive atmosphere where all ideas are welcomed.
6. Capture and organize ideas: Use the chosen tool/software to capture and document all ideas generated during the session. Categorize and prioritize them for further evaluation.
By following these steps and utilizing the appropriate tools/software, you can effectively run a virtual brainstorming session and facilitate the discovery of new solutions to problems.
Learn more about Brainstorming
https://brainly.com/question/1606124
#SPJ11
Which of the following activities is not permissible for IT professionals while on the job? Check all of the boxes that apply.
working on a side job while at work for one’s primary job
viewing s3xual content on a company computer
sending coworkers an e-mail joke containing suggestive humor
downloading music from a file-sharing service
Answers
The activities that is not permissible for IT professionals while on the job are option A, B, C and D.
Working on a side job while at work for one’s primary jobViewing s3xual content on a company computerSending coworkers an e-mail joke containing suggestive humorDownloading music from a file-sharing service What values underpin the IT industry?In the workplace, employees are frequently required to uphold professionalism, also the issue of accountability, as well as integrity. This entails managing private information responsibly, ensuring a secure workplace, and abstaining from illegal behavior like taking bribes.
IT specialists are the people that often design, test, as well as install, maintain, and that of repair hardware and software for businesses.
Therefore, Employees have a responsibility to comprehend a user's capabilities and needs in order to supply the goods and services that best satisfy those needs, subject, of course, to financial and logistical limitations. The public expects professionals to contribute significantly to society and to behave responsibly.
Learn more about IT professionals from
https://brainly.com/question/17496239
#SPJ1
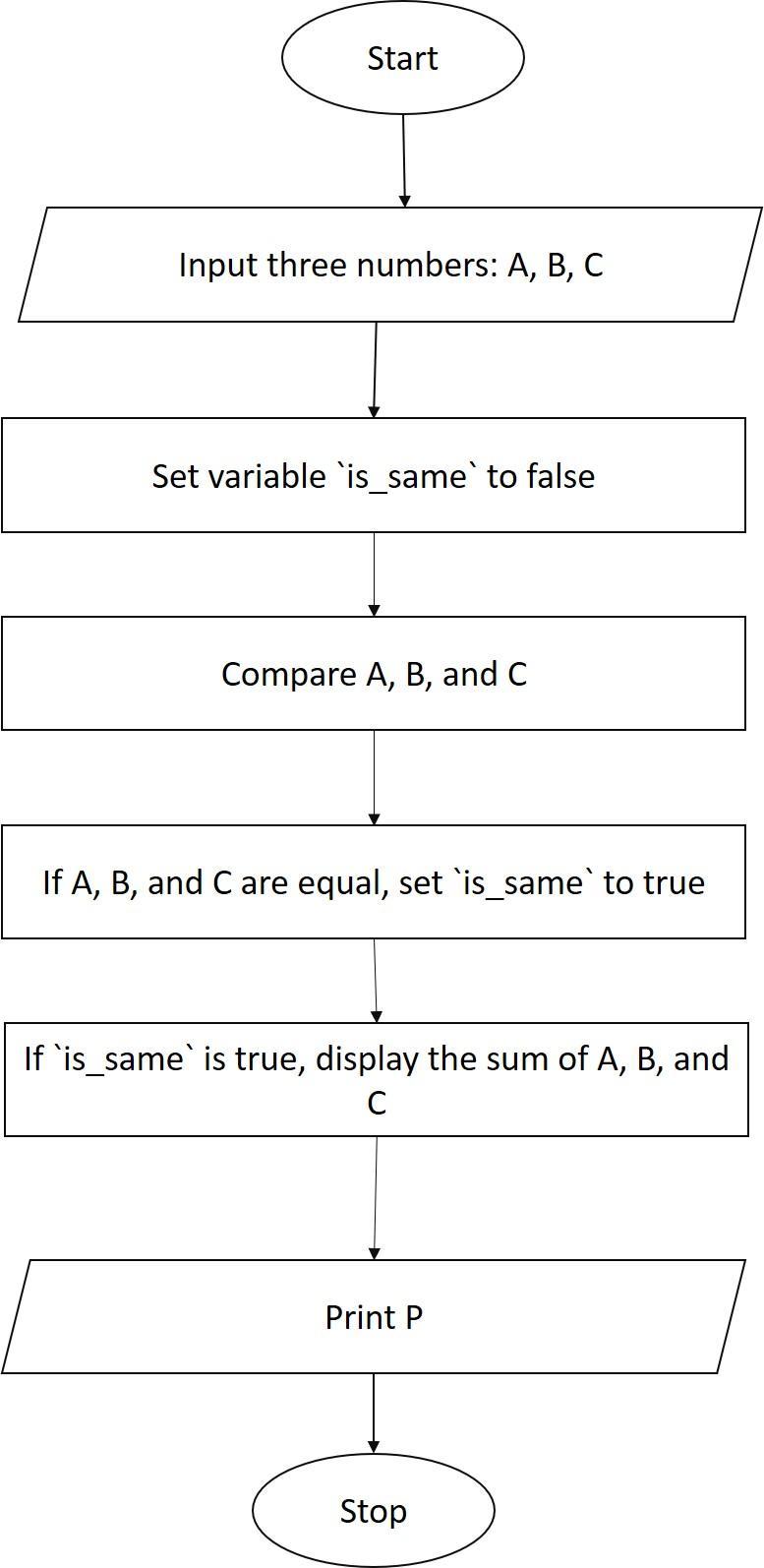
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
Richard wants to share his handwritten class notes with Nick via email. In this scenario, which of the following can help Richard convert the notes into digital images so that he can share them via email? a. Bar coding device b. Digital printing software c. Document scanner d. Radio frequency identification tag
Answers
Answer: Document Scanner
Explanation: Cos then he can easily add the paper notes to his computer and email the client.
You are one of the IT administrators for your company. Your coworker says that when she boots her computer it displays a message saying that one of her programs had an error while loading and is not working.
To fix this issue, you would like to see if Windows can provide a log file that may give you a hint to what is failing at boot time
What Microsoft tool/console would most likely give you the ability to create such a log file?
Answers
Answer:
MSConfig
Explanation:
It's meant to troubleshoot programs having issues when starting up.
MSConfig is the Microsoft tool/console would most likely give you the ability to create such a log file.
What is IT administrators?An IT administrator, often known as a system administrator, is in responsible of setting up and ensuring the reliable operation of client computer systems, servers, and data security measures. The organization's internal IT structure is constantly kept up to date by the administrator.
The duties involved in managing or putting together a business or other organization: My top salesmen shouldn't be wasting their entire day on office work.
Given the amount of schooling required, systems administrators have a better earning potential than other IT fields. The demand for systems administration jobs is expected to rise by 36% over the next ten years.
Thus, it is MSConfig.
For more information about IT administrators, click here:
https://brainly.com/question/29230350
#SPJ2
The _____ role in active directory is used to ensure that all sids in a domain are unique.
Answers
The RID (Relative Identifier) Master role in Active Directory is used to ensure that all SIDs (Security Identifiers) in a domain are unique.
In Active Directory, each object (such as users, groups, and computers) is assigned a unique SID. The SID is a security principal's unique identifier and is used to control access to resources in the domain. The RID Master role is responsible for assigning a unique RID to each object created in the domain.
The RID consists of three parts: the domain SID, the RID Pool, and the RID. The domain SID is the same for all objects in the domain, the RID Pool is a range of RIDs assigned to the domain, and the RID is a unique number from the RID Pool assigned to each object.
The RID Master ensures that each object created in the domain is assigned a unique RID from the RID Pool. This prevents any conflicts or duplication of SIDs within the domain.
In conclusion, the RID Master role in Active Directory plays a crucial role in ensuring that all SIDs in a domain are unique. By assigning a unique RID to each object created, it helps maintain the security and integrity of the domain.
Learn more about Active Directory visit:
https://brainly.com/question/32696453
#SPJ11
Assignment 4: Evens and Odds
Need help on this

Answers
Answer:
any even number plus 1 is odd
Which option is NOT a command group on the Picture Tools contextual tab when an image is selected in the Word document?
Adjust
Color
Picture Styles
Arrange
Answers
Answer:
Color
Explanation:
I got you:)
Answer:
color
Explanation:
How is new operator different than malloc? (2 marks)
What is the difference between function overloading and operator
overloading? (2 marks)
Answers
Difference between new operator and malloc: Memory Allocation, Type Safety, Constructor Invocation, Return Type, Error Handling:.
Memory Allocation: The new operator is used in C++ to dynamically allocate memory for objects, while malloc is a function in C used for dynamic memory allocation.
Type Safety: The new operator ensures type safety by automatically determining the size of the object based on its data type, while malloc requires manual specification of the size in bytes.
Constructor Invocation: When using new, the constructor of the object is called to initialize its state, whereas malloc does not invoke any constructor. This allows new to handle complex objects with constructors and destructors, while malloc is suitable for allocating raw memory.
Return Type: The new operator returns a pointer to the allocated object, automatically casting it to the appropriate type. malloc returns a void* pointer, requiring explicit casting to the desired type.
Error Handling: If the new operator fails to allocate memory, it throws an exception (std::bad_alloc), whereas malloc returns NULL if it fails to allocate memory.
Difference between function overloading and operator overloading:
Function Overloading: It allows multiple functions with the same name but different parameters in a class or namespace. The compiler differentiates between these functions based on the number, types, or order of the parameters. Function overloading provides flexibility and code reusability by allowing similar operations to be performed on different data types or with different argument combinations.
Operator Overloading: It enables operators such as +, -, *, /, etc., to be redefined for custom types. It allows objects of a class to behave like built-in types with respect to operators. Operator overloading is achieved by defining member functions or global functions with the operator keyword followed by the operator symbol. It provides a concise and intuitive way to work with objects, enabling natural syntax for custom operations.
In summary, function overloading is used to define multiple functions with the same name but different parameters, while operator overloading allows custom types to redefine the behavior of operators.
Learn more about operator from
https://brainly.com/question/29673343
#SPJ11
What is the difference between weak AI and strong AI?
Answers
Explanation:Strong AI has a complex algorithm that helps it act in different situations, while all the actions in weak AIs are pre-programmed by a human. Strong AI-powered machines have a mind of their own. They can process and make independent decisions, while weak AI-based machines can only simulate human behavior.
How to set encapsulation angular component.
Answers
Answer: anyone know?
Explanation:
What evolution has cryptography grown since sample passwords? Name 5.
Answers
Answer:
Encrypting Company Devices. ...
Securing Email Communications. ...
Protecting Sensitive Company Data. ...
Encrypting Databases. ...
Securing a Website.
Explanation:
you would like to enable an ospfv3 routing process on a single interface and begin to use route ipv6 traffic. which command(s) would you use?
Answers
To enable an OSPFv3 routing process on a single interface and start using it to route IPv6 traffic, the command you'd use is the following:ipv6 ospf process-number area.
area-id interface interface-id [cost cost] [priority priority] [instance instance-id] [transmit-delay seconds] [hello-interval seconds] [dead-interval seconds] [retransmit-interval seconds] [authentication {ipsec | md5} authentication-key] [bfd {enable | disable}] [bfd minimum-interval milliseconds] [bfd multiplier number] [ttl-security hops] [prefix-suppression] [shutdown]Where process-number is the OSPFv3 process ID, area-id is the OSPFv3 area ID, and interface-id is the ID of the interface on which OSPFv3 should be enabled. The rest of the options are used to configure the OSPFv3 interface in various ways, such as specifying the cost of the interface, setting the priority of the interface, setting the transmit delay, hello interval, and dead interval timers, and setting authentication options.
Learn more about OSPFv3 here:
https://brainly.com/question/13487130
#SPJ11
How fast or slow a video sequence is
A. Time aperature
B. Length
C. Frame rate
D. Continuous
E. None of these
Answers
Answer:
C. Frame rate
Explanation:
hope this helps
How do I reset my brainly password?
I can't just go into my account settings and change it that why it didn't work when I did that.
And guys I'm really struggling, please don't just try to take the 25 points for nothing I really need help iv'e tried almost everything
Answers
Answer:
MARK AS BRAINLIEST! LOOK AT PICTURE!

To obtain your first driver's license, you must successfully complete several activities. First, you must produce the appropriate identification. Then, you must pass a written exam. Finally, you must pass the road exam. At each of these steps, 10 percent, 15 percent and 40 percent of driver's license hopefuls fail to fulfil the step's requirements. You are only allowed to take the written exam if your identification is approved, and you are only allowed to take toe road test if you have passed the written exam. Each step takes 5, 3 and 20 minutes respectively (staff members administering written exams need only to set up the applicant at a computer). Currently the DMV staffs 4 people to process the license applications, 2 to administer the written exams and 5 to judge the road exam. DMV staff are rostered to work 8 hours per day. (i) Draw a flow diagram for this process (ii) Where is the bottleneck, according to the current staffing plan? (iii) What is the maximum capacity of the process (expressed in applicants presenting for assessment and newly-licensed drivers each day)? Show your workings. (iv) How many staff should the DMV roster at each step if it has a target to produce 100 newly-licensed drivers per day while maintaining an average staff utilisation factor of 85%? Show your workings.
Answers
The flow diagram for the given process is shown below. The bottleneck is the part of the process that limits the maximum capacity for driver license.
In the given process, the bottleneck is the road exam, where 40% of the driver's license applicants fail to fulfill the step's requirements.(iii) Maximum Capacity of the Process: The maximum capacity of the process can be calculated by finding the minimum of the capacities of each step. Capacity of the identification process = (1 - 0.10) × 480/5
= 86.4 applicants/dayCapacity of the written exam process
= (1 - 0.15) × 480/3
= 102.4
applicants/dayCapacity of the road exam process = (1 - 0.40) × 480/20
= 28.8 applicants/day
Therefore, the maximum capacity of the process is 28.8 applicants/day.Staff Required for 100 Newly-Licensed Drivers per Day: Let the staff required at the identification, written exam, and road exam steps be x, y, and z respectively. From the above calculations, we have the following capacities:86.4x + 102.4y + 28.8z = 100/0.85
To know more about driver visit:
https://brainly.com/question/30485503
#SPJ11
which two items do you need to access a shared resource? group of answer choices A. dns and ipconfig B. ipconfig and nslookup C. authentication and permissions D. name and ip address
Answers
The two items you need to access a shared resource are the d).name and IP address.
In computer networking, a name is a human-readable label that is assigned to a device or resource on a network, while an IP address is a unique numerical identifier that is used to locate and communicate with devices on a network. IP addresses, on the other hand, are used by computers and other devices on a network to identify and communicate with one another.
There are two main types of IP addresses: IPv4 and IPv6. IPv4 addresses are 32-bit numbers, while IPv6 addresses are 128-bit numbers. Each device on a network must have a unique IP address in order to communicate with other devices.
So the answer is d) Name and IP address.
Learn more about IP address: https://brainly.com/question/14219853
#SPJ11
what is a computer?
Answers
Answer:
A computer is an electronic machine designed to accept data as input , process the data, and give out required information/ result as output
EXPLANATION:
A computer is a device that accepts information (in the form of digitalized data) and manipulates it for some result
based on a program, software, or sequence of instructions on how the data is to be processed.
i hope this helped
what will disc paging in virtual memory do if the memory in ram is full?
Answers
Answer:
If your RAM is full, your computer is slow, and its hard drive light is constantly blinking, your computer is swapping to disk. ... If this is occurring, it's a clear side that your computer needs more RAM – or that you need to use less memory-hungry programs.
How to include quotation marks in a string javascript.
Answers
Explanation:
Try ' " and the beginning and " ' at the end.
It might be hard for some people to see the options so I’ma just;
A. What will happen if a certain condition is not met.
B. What color the ball is.
C. Whether the ball’s value is y-value is greater than 110.
D. The overall size of the ball used in the game.

Answers
I put the document in photos!
The question is - “According to the first paragraph of this document, did Hawaii agree to the annexation by the United States of America? Cite evidence for your claim?
Which type of chart is the least appropriate for depicting yearly rainfall totals for five cities for four years?.
Answers
The least appropriate type of chart for depicting yearly rainfall totals for five cities for four years would be a pie chart. Pie charts are best used to show percentages of a whole, not trends over time.
Instead, a line chart or a bar graph would be more appropriate for this type of data. A line chart can easily display changes in rainfall over time, while a bar graph can compare rainfall amounts between different cities. It is important to choose the appropriate chart type for the data being presented in order to accurately and effectively convey the information to the audience.
To know more about line chart visit:
brainly.com/question/29990229
#SPJ11
the use of technology to create product styles and designs is called a computer-assisted instruction. b robotics. c computer-aided design. d artificial intelligence.
Answers
The use of technology to create product styles and designs is called: C. computer-aided design.
What is Artificial Intelligence (AI)?In Computer technology, artificial Intelligence (AI) is also referred to as Machine learning (ML) and it can be defined as a subfield in computer science which typically focuses on the use of advanced computer algorithms and technology to develop a smart computer-controlled robot with the abilities to proffer solutions to very complex problems that are exclusively meant for humans or performed by using human intelligence.
Generally speaking, computer-aided design simply refers to the use of technology for the design and development of various product styles and designs.
Read more on Artificial Intelligence here: brainly.com/question/25523571
#SPJ4