Visit a shoot location for any video or film and observe the ongoing activities. Based on your observation, answer the following questions. If you’re unable to visit an actual shoot location, you can perform online or offline resources to answer the questions below.
What was the approximate size of the crew on the shoot? (Alternatively, what is the average crew size on a film shoot?)
What is the role of the director?
What is the role of a cameraman or cinematographer?
What is the role of the light technicians and assistants?
What does the makeup man do?
Was there a stylist on the shoot? What did he or she do?
Answers
Finding actual sites to act as the imaginary locations mentioned in a film's screenplay is known as location scouting. The correct setting aids the story and contributes to the creation of a believable world in films.
What does filming on location entail?Location filming is simply shooting outside of a studio in the actual location where the story takes place. A soundstage is a space or building that is soundproof and utilized for the creation of movies and television shows.
How can I locate my shooting location?For assistance, get in touch with the film commission or your local government office. They can aid in locating potential shooting sites for your movie. For a list of locations that are offered to filmmakers, you may also check out location-scouting websites.
to know more about shooting here:
brainly.com/question/10922117
#SPJ1
Related Questions
the wireless technology that can be used to transmit data between 2 different network
Answers
Answer:
most probably that's wifi.
_ clouds are more suitable for organizations that want to offer standard applications over the Web, such as e-mail, with little involvement by IT managers.
a.
Public
b.
Private
c.
Community
d.
Hybrid
Answers
The main answer to your question is option A, public clouds. Public clouds are managed by third-party providers and offer standard applications over the Web, making them a more suitable option for organizations that want to offer services such as e-mail without involving IT managers. This is because the provider takes care of maintenance, security, and upgrades, leaving IT managers with little involvement.
Public clouds are a type of cloud computing model where the infrastructure and services are provided by a third-party provider over the Internet. They are accessible to anyone who wants to use them and are usually offered on a pay-per-use basis. Public clouds are ideal for organizations that want to offer standard applications, such as e-mail, with little involvement by IT managers.
In a public cloud, the provider is responsible for managing the infrastructure, including maintenance, security, and upgrades. This makes it a more cost-effective solution for organizations that don't have the resources or expertise to manage their own IT infrastructure. Additionally, public clouds offer scalability and flexibility, allowing organizations to easily add or reduce resources as needed.
In contrast, private clouds are typically used by organizations that want more control over their IT infrastructure. Community clouds are shared by several organizations with similar needs, while hybrid clouds combine the features of both public and private clouds.
Learn more about standard applications:
https://brainly.com/question/29563268
#SPJ11
what should you wear while installing a circuit board in a computer?
Answers
When installing a circuit board in a computer, you should wear appropriate attire to minimize the risk of electrostatic discharge (ESD) damage. ESD can cause harm to sensitive electronic components on the circuit board.
1. Wear an ESD wrist strap: An ESD wrist strap is a crucial tool to prevent static discharge while handling circuit boards. It connects to your wrist and has a grounding cord that attaches to a grounded surface, allowing any static charge to safely dissipate.
2. Avoid wearing synthetic fabrics: Synthetic materials, such as polyester and nylon, can generate static electricity. Instead, opt for natural fiber clothing, such as cotton, which is less prone to creating static.
3. Wear closed-toe shoes: Closed-toe shoes help protect your feet from any dropped components or tools. Additionally, rubber-soled shoes can help reduce the buildup of static electricity.
4. Avoid wearing jewelry or accessories: Metal jewelry can conduct electricity and increase the risk of ESD. It's best to remove any rings, bracelets, necklaces, or watches before working on a circuit board.
5. Keep a clean workspace: Make sure your work area is clean and free of any materials that can generate static electricity, such as plastic bags or foam.
In summary, when installing a circuit board in a computer, wear an ESD wrist strap, natural fiber clothing, closed-toe shoes, and avoid wearing jewelry or accessories. This will minimize the risk of electrostatic discharge damage to the delicate components on the board.
More on circuit board : https://brainly.com/question/28655795
#SPJ11
a class that takes data pertaining to a business event and translates the data for appropriate presentation to the user would be a(n):
Answers
A class that takes data pertaining to a business event and translates the data for appropriate presentation to the user would be a data visualization class.
This class would use various techniques and tools to convert raw data into meaningful visual representations, such as charts, graphs, and tables, which can be easily understood by the user. The class may also involve methods for data analysis and interpretation to help users make informed decisions based on the data presented.
Data visualization is the depiction of data using standard graphics like charts, plots, infographics, and even animations. These informational visual displays provide complicated data relationships and data-driven insights in a way that is simple to comprehend.
The graphic display of information and data is known as data visualization. Data visualization tools offer an easy approach to observe and analyze trends, outliers, and patterns in data by utilizing visual elements like charts, graphs, and maps.
To know more about data visualization , click here:
https://brainly.com/question/30328164
#SPJ11
you need to perform out-of-band management on a router. how should you connect to the router?
Answers
To perform out-of-band management on a router, you should connect to the router using a dedicated management interface or a separate communication channel that is distinct from the primary network connection.
Out-of-band management refers to the practice of managing network devices through a separate, dedicated pathway that is independent of the regular data network. This allows administrators to access and control the router even if the primary network is unavailable or experiencing issues. Typically, out-of-band management involves connecting to the router through a console port using a console cable and a terminal emulation program such as TeraTerm or PuTTY. The console port provides a direct, physical connection to the router's console interface, allowing administrators to configure, monitor, and troubleshoot the router's settings and operations. By using out-of-band management, administrators can have a reliable and secure means of accessing and managing network devices, even in situations where the primary network is down or compromised. It provides an alternative pathway for critical administrative tasks, ensuring continuous control and oversight of network infrastructure.
Learn more about Out-of-band management here:
https://brainly.com/question/31444492
#SPJ11
What are the ethic iue with a computer programmer creating a computer viru in order to tet the ecurity feature of window?
Answers
Below is a list of the three most important ethical issues related to cyber security: damage to privacy, allocating resources for cyber security, and openness and disclosure.
In a nutshell, ethical marketing is the process of advertising a product, service, or brand in a way that is consistent with your moral principles. This can involve speaking truthfully and forthright, as well as avoiding overstating things. Our top recommendations for raising standards and promoting an ethical workplace are listed below: construct a code, Engage your team and customers. the benefits of the code once more, Give people a good example by Inform your employees. advance your moral behaviour, the promotion of moral conduct, Observe your mistakes, Adjective. ethical. ethical e-thi-kl.: of or relating to ethics.
Learn more about ethical from
brainly.com/question/29552906
#SPJ4
Which correctly calls the add() function?
def add(a, b, c):
print(a + b + c)
add(2; 4; 6)
add(2 4 6)
add(2, 4, 6)
add(2 + 4 + 6)
Answers
The correct option is add(2, 4, 6) ,it is a correct function call to the add() function.
How to correctly call a function?The correct function call to the add() function is add(2, 4, 6). In this call, the function is invoked with three arguments: 2, 4, and 6, which are separated by commas.
This syntax follows the standard convention for passing multiple arguments to a function in many programming languages.
The semi-colon (;) is not used to separate arguments in a function call. It is a syntax error to write add(2; 4; 6) as shown in the second option.
Similarly, in the third option add(2 4 6), the absence of commas between the arguments is incorrect and would result in a syntax error.
The fourth option add(2 + 4 + 6) is also incorrect because it attempts to perform addition within the function call itself.
Instead, the individual values should be passed as separate arguments to the function, as shown in the correct function call example.
Learn more about function
brainly.com/question/31062578
#SPJ11
What is our collective responsibility to ensure information assurance referred to as?
A.
confidentiality
B.
infrastructure
C.
accountability
D.
nonrepudiation
Answers
Answer:
C
Explanation:
Answer: c
Explanation:
Please help me on this it’s due now

Answers
Using a vehicle like a car, truck, train, ship, or aircraft, goods transport is the movement of any kind of cargo or products.
What is Transporting Goods?There is a distinction between local and distant traffic. Local traffic is defined as the movement of products when the shipper and recipient are physically close to one another and the vehicle can make daily trips back to its starting place.
On the other hand, in long-distance traffic, the goods is moved over considerable distances.
Transport of goods, such as the distribution of industrial materials, the distribution of fuel and gas, the distribution of money, the distribution of food and beverages, the distribution of medical, health, and sanitation supplies, the distribution of primary needs.
Therefore, Using a vehicle like a car, truck, train, ship, or aircraft, goods transport is the movement of any kind of cargo or products.
To learn more about Transport, refer to the link:
https://brainly.com/question/29851765
#SPJ7
What layer of the OSI model does every transmission medium network function on?
A. the fifth layer
B. the second layer
C. the first layer
D. the seventh layer
Answers
Answer:
Hopefully i am correct! Sorry if i am not
Explanation:
Every transmission medium network function operates at the Physical Layer (Layer 1) of the OSI model.
The Physical Layer is responsible for the physical transmission of data over the communication channel, including the electrical, mechanical, and functional specifications of the network interface, such as voltage levels, data rates, and physical connectors.
Therefore, the correct answer is C. the first layer.
What is the purpose of a web server? What is the purpose of a web browser?
Answers
Answer: the purpose of a web browser is to help answer and needed questions, and to get to sites.
Explanation:
If you would like to give another user permissions on your mailbox or to particular folders within your mailbox, which role should you configure?
Assignee
Client
Delegate
Manager
Answers
Answer:
I think it's B, Delegate
Explanation:
Cause the other options didn't seem to fit as the answer.
I really don't know though.
A delegate is someone who has been granted permission by another user to access. The correct answer would be an option (C).
What is a mailbox?A computer-simulated mailbox that stores email messages. Mailboxes are saved on a disc as a message file or a message database.
A delegate is someone who has been granted permission by another user to access and manage their mailbox, including sending and responding to email messages on their behalf.
When you grant delegate access to another person, you are giving them the ability to access specific folders within your mailbox and perform specific actions, such as reading, sending, and deleting email messages.
Assignee, client, and manager are not terms typically used in the context of delegate access in email systems.
Thus, the correct answer would be option (C).
Learn more about the mailbox here:
https://brainly.com/question/28430685
#SPJ6
Question at position 5 a mathematician develops a program to solve systems of linear equations. When they use distributed computing techniques to run the program on two computers in parallel, they find a speedup of 2. In this case, what does a speedup of 2 indicate? a mathematician develops a program to solve systems of linear equations. When they use distributed computing techniques to run the program on two computers in parallel, they find a speedup of 2. In this case, what does a speedup of 2 indicate? the program completed in two minutes less time with two computers versus one computer. The program completed in half the time with two computers versus one computer. The program completed in twice as much time with two computers versus one computer. The program completed in two minutes more time with two computers versus one computer
Answers
A speedup of 2 means that the program completed in half the time with two computers versus one computer. Speedup is a measure of how much faster a program runs on multiple processors compared to a single processor, and a speedup of 2 indicates that the program runs twice as fast on two processors as it does on a single processor.
What does speedup of 2 indicateA speedup of 2 in this case indicates that the program completed in half the time with two computers versus one computer. Speedup is a measure of how much faster a program runs when executed on multiple processors compared to a single processor. A speedup of 2 means that the program runs twice as fast on two processors than on a single processor. In other words, if the program takes T time to complete on a single processor, it takes T/2 time to complete on two processors.
Learn more on processor here;
https://brainly.com/question/474553
#SPJ1
1. What is being decided when information is evaluated?
2. List and describe the two steps you can use to break down into its arguments
3. Why does confusing and uncertain need to be clarified?
4. What are some causes for confusion and uncertainty in an argument?
(Can someone help me out plz)
Answers
Answer:
1. Once you found information that matches the topic and requirements of your research, you should analyze or evaluate these information sources. Evaluating information encourages you to think critically about the reliability, validly, accurately, authority, timeliness, point of view or bias of information sources.
2. The first step of evaluating an argument is making an inference connection. The second step is asserting premise acceptability. 2 questions to ask is (1) Is this argument valid and (2) Is this argument sound or unsound.
Proportional spacing replaced what other kind of spacing? question 2 options: parallel spacing monospacing one-to-one spacing fixed spacing
Answers
According to the statement, Proportional spacing replaced monospacing.
Describe monospacing.A monospaced font is one in which each letter and character takes up the same amount of horizontal space. It is also known as a fixed-pitch, fixed-width, or non-proportional font. Variable-width fonts, in contrast, feature letters and spacing that are all the same width.
Monospace fonts have their uses.Practicality: On all screen sizes, monospaced typefaces are exceptionally simple to read. This means that your clients can quickly and easily locate what they're looking for on any device, greatly enhancing the user experience. Your users may become clients more frequently as a result.
To know more about monospace visit :
https://brainly.com/question/17824852
#SPJ4
what does a technician need in order to make changes to software installed on the computer of a customer?
Answers
A technician needs the customer's permission before making any changes to a computer.
What kind of work does a level one technician at a call center typically do?A level one technician's main duty is to obtain information from the customer. All of the data must be accurately entered into the work order by the level one technician.
Which of the following software launches first when you turn on your laptop?computing device. When a computer is turned on, an operating system, a specific program, must be started. By handling the intricate logistics of hardware management, the operating system's job is to make other computer applications more functional.
To know more about technician visit:-
https://brainly.com/question/14290207
#SPJ1
what consists of a series of tiny projects? waterfall methodology iterative development agile methodology all of these
Answers
Iterative development consists of a series of tiny projects.
What is project?
A project is any individual or team activity, maybe incorporating research or design, that is deliberately planned to attain a certain goal. A project is a temporary (rather than permanent) social structure (work system) that may be staffed by teams (inside or across organisations) to complete specific tasks under time limitations. When confronted with a problem, a need, a desire, or a cause of discomfort, a project is a specific and coordinated endeavour driven by a perceived opportunity.
Iterative development is a method of breaking down the software development of a large programme into smaller portions. Iterative development involves iteratively designing, developing, and testing feature code.
So, B is the right answer.
To learn more about project
https://brainly.com/question/508027
#SPJ4
When you have completed your document review in Print Preview, you have the option to save your document as a new file type. What file type can be created using Print?
A. .com
B. .jpeg
C. .exe
D. .pdf
Answers
which of these exemplifies an iterative process
A: you walk to school everyday with a friend
B: you do homework at a different time each day
C: sometimes you eat breakfast at school and something you eat at home
D: you write a research paper, review it, revise it, review it again, revise it again
Answers
Answer:
its D
Explanation:
took the test
Answer:
d
Explanation:
If you use your computer primarily for telnet into a remote computer, will you have a large long distance telephone bill?
Answers
If you use your computer primarily for telnet into a remote computer, a person will not have a large long distance telephone bill.
What is telnet used for?Telnet is known to be a kind of a network protocol that is said to be used to virtually look into a computer and to give a two-way, working hand in hand and text-based communication channel that exist between two machines.
Note that, If you use your computer primarily for telnet into a remote computer, a person will not have a large long distance telephone bill because it does not apply in any way.
Learn more about telnet from
https://brainly.com/question/23640188
#SPJ1
Create a letter of at least 250 words addressed to your newspaper editor that describes your storage options, and give at least three reasons why your option is the best choice.
Answers
Answer:
Following are the letter to this question:
Explanation:
Dear Raju:
For what journal is produced, I was composing to analyze the data collection possibilities. First of all, I should recognize how many documents you ’re expected to store: images, text files, news articles, and other records, even though going to weigh up the document is quite crucial to analyze that the best way to store this documents.
For hardware depositors, people will save the documents through memory chips, because this is a network interface with a huge variety of subject areas. In this single and the small device are use the massive quantities of data, that can be protected and many memory locations can be published and authored at the very same procedure.
And if you'd like to view the files previous with releases, its cloud computing provides storage solutions that can be extended to the length for just a little money. But you'll have to keep in mind that even strong internet access is often required. Its information would also have to be stored digitally and managed to make readable by the computer. Its objective of all these alternatives would be to make life simple and efficient to store and manage information. its standard disc repayments involve memory space, remotes, disc cages, and authority. Users will save equipment and tech assistance expenses with this alternative and you will always maintain its content online even though it is big files. Even so, to preserve your content, it should make a regular backup.
If you determine that option fits your needs, let me learn and I'll support you there.
Yours sincerely,
Dev
true or false? a supernode is a user computer selected by the software provider that has enough power to store the index of available music and provide search capabilities.
Answers
True. (A supernode is user computer selected by a software provider with sufficient power to store an index of available music and provide search functionality.)
What is a supernode?
In circuit theory, supernodes are theoretical building blocks that can be used to solve circuits. This is done by viewing the voltage source on the wire as a point source voltage relative to the other point voltages found at various nodes in the circuit relative to the ground node assigned zero or negative charge .
How do you recognize supernode?
Supernode are indicated by the dotted area. This is possible because if the total current out of node 2 is zero (0) and the total current out of node 3 is zero (0), the total current out of the combination will be zero.
To know more about Supernode visit here:
https://brainly.com/question/25664639
#SPJ4
8 grades, help please!!!!

Answers
Answer: can you take a clearer picture its really blurry then I can help Thx! :)
Explanation:
Hi am feeling really happy just passed a test after a lot of tries :-)
Answer this with your opinion don't search it up
What the best game on earth according to arts in like computer graphics?
Answers
Answer:
1. real life 2. (my actual answer) horizon zero dawn 3. chess
Explanation:
hope you have a great day. congratulations
6.6 Code Practice 2- Boat:
Use the code above to write a program that draws an image of a boat on water. Your program should create an image similar to the one below. Your image does not need to be exactly the same as the one above, but can have slight modifications (for example, your image can use a different color or different positioning of
objects).
(In edhesive please)
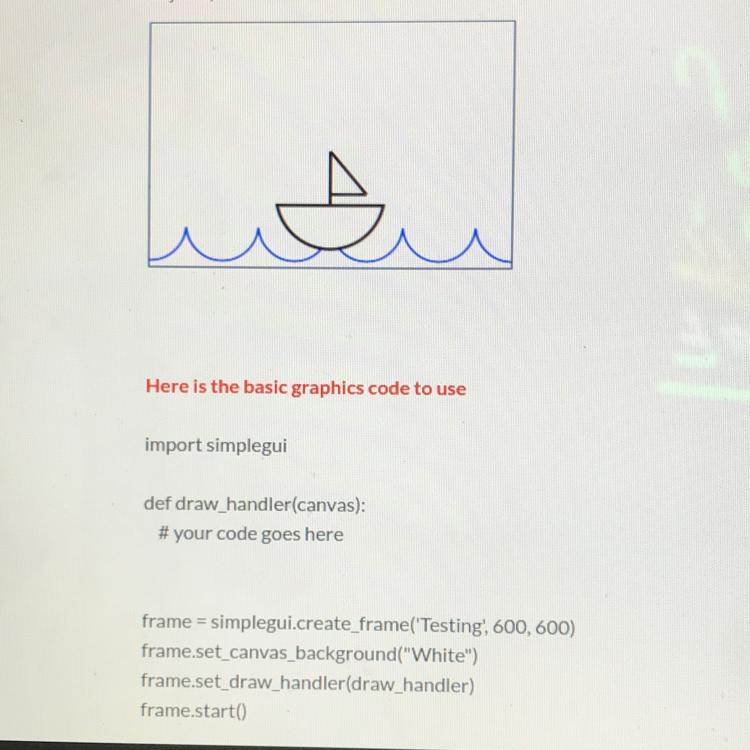
Answers
Answer:
import simplegui
def draw_handler(canvas):
canvas.draw_circle((0,550), 2, 100, "Blue")
canvas.draw_circle((100,550),2,100,"Blue")
canvas.draw_circle((200,550),2,100,"Blue")
canvas.draw_circle((300,550),2,100,"Blue")
canvas.draw_circle((400,550),2,100,"Blue")
canvas.draw_circle((500,550),2,100,"Blue")
canvas.draw_circle((600,550),2,100,"Blue")
canvas.draw_polygon([(0,550), (600,550), (600,500), (0,500)], 5, "White", "White")
canvas.draw_circle((300, 525), 2, 100, "Black")
canvas.draw_polygon([(250, 525), (350,525), (350, 475), (250, 475)], 5, "White", "White")
canvas.draw_line((250,525), (350,525), 5, "Black")
canvas.draw_line((300,525), (300, 500), 5, "Black")
canvas.draw_polygon([(300,500), (325, 500), (300,450)], 5, "Black")
frame = simplegui.create_frame('Testing', 600, 600)
frame.set_canvas_background("White")
frame.set_draw_handler(draw_handler)
frame.start()
Explanation:
Little jank but looks fine
smartphone users may be able to share the internet connection of their device via a cable, bluetooth, or wi-fi in a process known as select one: a. tethering. b. binding. c. hitchhiking. d. piggybacking.
Answers
Answer: the answer to that is A
Explanation:
The Russian artist Wassily Kandinsky believed that color could show emotions. Please fill in the emotions that he believed each color showed.
Answers
Answer:
Yellow could disturb, while blue might make people feel good. The warm colors - red, yellow, and orange - are usually considered lively colors that can sometimes be harsh. The cool colors - green, blue, and purple - are considered more peaceful and subdued.Kandinsky was especially fond of blue. He also discussed the neutrals, black, gray, and white. White is silence and quiet, and black is completely devoid of possibility. Gray can go either way.
In what year was the TED group created?
Answers
Answer:
1984
Explanation:
__ allow(s) users with mobility issues to control the computer with their voice.
Speech input software
Tracking devices
Head pointers
Text-to-speech
Answers
Answer:
Speech input device
Explanation:
I think this is the answer
Answer: speech input software
Explanation: got it right on edgen
Which of the following features of file managers could you use to move a file?

Answers
Answer:
copy and paste
Explanation:
you dont want to delete a file you dont want to see the details and you dont want to throw it away so copy and paste.