unlike sgml, xml can be used to design markup languages for different types of structured documents.
Answers
That statement is correct. Unlike SGML (Standard Generalized Markup Language), XML (eXtensible Markup Language) allows for the design of markup languages for different types of structured documents. XML is a more flexible and simplified markup language that was designed to be platform-independent and widely applicable.
XML provides a set of rules for encoding documents in a format that is both human-readable and machine-readable. It allows users to define their own custom markup languages by creating tags and defining the structure and semantics of the document. This flexibility makes XML suitable for a wide range of applications and document types, including web pages, data interchange, configuration files, and more.
In contrast, SGML is a more complex and less specialized markup language that served as the basis for XML. SGML requires more extensive markup declarations and is less user-friendly for designing markup languages for different document types. XML, with its simpler syntax and self-descriptive tags, has become widely adopted as a standard for representing structured data.
Learn more about flexible here
https://brainly.com/question/11833604
#SPJ11
Related Questions
The ethernet cable is also known as? *
Cat 5 cable
Wan cable
RD-45 cable
Sat 5 cable
Answers
Answer:
Cat 5 cable
Explanation:
The ethernet cable is also known as Cat 5 cable.
if you were creating a game for senior citizens, what type of demographic information would you include?
Answers
Answer: I would put reminders for dentures, or maybe reminders to take a walk or take meds.
Explanation: That's just what I would put
After months of hard work, the big day has finally arrived, and your software will be produced and distributed. Which phase of the software life cycle is this?
analysis
maintenance
implementation
testing
Answers
Answer:
implementation
Explanation:
implementation is the process of putting a decision or plan into effect or execution.
why is what you say in business as important as how you say it
Answers
Answer:
Because the things you say and how you say it can determine whether or not you sell an item, make a deal with another company and things of that nature. Hope this helps!!
Check My Work In a _____, one or more powerful servers control the network, and departmental servers control lower levels of processing and network devices
Answers
The term that describes this type of network architecture is "client-server network".
In a client-server network, one or more powerful servers act as the central hub and control the overall network. These servers provide services such as file sharing, email, and access to applications. Departmental servers, on the other hand, control lower levels of processing and network devices, and they are typically used to provide more specialized services to a specific department or group of users.
In this type of network architecture, the network is organized in a top-down manner. The powerful servers at the top level are responsible for managing and controlling the overall network, while the departmental servers at lower levels handle more specific tasks and control network devices.
To know more about Client-server visit:-
https://brainly.com/question/7500232
#SPJ11
are it applications an asset or an expense?
Answers
Applications can be considered both an asset and an expense, depending on the context.
Why do we consider Application as both an asset and an expense?
If you purchase or develop applications to use in your business operations, they can be considered an asset, specifically intangible assets. Intangible assets have value but are not physical objects. In this case, the applications would provide value to your business by streamlining processes, improving efficiency, or offering other benefits.
On the other hand, applications can also be an expense. When you pay for the development, maintenance, or subscription fees associated with applications, these costs are treated as expenses in your financial accounting. These expenses are necessary for the business to continue using the applications as part of its operations.
So, applications can be classified as both an asset and an expense, depending on the context in which they are being considered.
To know more about assets and expenses:
https://brainly.com/app/ask?q=asset+
#SPJ11
A segment of a track in a mass storage system
a. pixel
b. address
c. sector
d. flip-flop
Answers
The correct option is c. sector. The segment of a track in a mass storage system is represented by a sector.
How is a segment of a track represented in mass storage systems?In the context of a mass storage system, the segment of a track refers to a specific portion or subdivision of the track. The segment can contain a certain amount of data or information, and it plays a crucial role in organizing and managing data storage.
Among the given options, the term "sector" is the most appropriate choice to represent a segment of a track in a mass storage system.
A sector is a logical division of a track that serves as the smallest addressable unit for reading and writing data.
It typically consists of a fixed number of bytes, such as 512 or 4096, and represents a discrete unit of data storage on a storage medium, such as a hard disk drive or solid-state drive.
Sectors are used extensively in mass storage systems for efficient data management.
They enable random access to specific parts of a track, allowing for rapid retrieval and modification of data. Operating systems and file systems use the concept of sectors to organize and address data stored on storage devices.
Overall, a sector is a fundamental component of mass storage systems, providing a logical and manageable unit for storing and accessing data on tracks. therefore the correct option is c. sector.
Learn more about segment
brainly.com/question/30694240
#SPJ11
How would you feel if the next version of windows become SaaS, and why
Answers
Any transition to a SaaS model would require careful consideration and addressing of these concerns to ensure it meets the diverse needs and expectations of Windows users.
I would have mixed feelings if the next version of Windows becomes a Software-as-a-Service (SaaS). While it can bring benefits such as regular updates and improved security, it also raises concerns about ongoing costs and potential loss of control over the operating system.
Transitioning Windows into a SaaS model would mean that instead of purchasing a one-time license for the operating system, users would pay a recurring subscription fee to access and use Windows. This approach offers some advantages. **Regular updates** would ensure users have the latest features and security patches, reducing the risk of vulnerabilities. Additionally, **compatibility** could be improved as developers could target a single version of the operating system, leading to a more streamlined experience.
However, there are also valid concerns associated with a SaaS model for Windows. One major consideration is the **cost**. While a subscription model may be suitable for some users, it may not be affordable or desirable for others, particularly those who prefer a one-time payment. Additionally, relying on a SaaS model could result in a loss of **control** for users. With a traditional Windows license, users have more autonomy over when and how they update their operating system. With a SaaS model, updates may be mandatory and potentially disruptive.
Furthermore, there are potential **privacy** and **data security** concerns with a SaaS-based Windows. Users might worry about their data being stored in the cloud or the need for an internet connection to access their operating system. These concerns would need to be addressed to ensure user trust and confidence.
In conclusion, while a SaaS version of Windows has its benefits in terms of regular updates and improved compatibility, the shift raises concerns about cost, loss of control, privacy, and data security. Any transition to a SaaS model would require careful consideration and addressing of these concerns to ensure it meets the diverse needs and expectations of Windows users.
Learn more about SaaS model here
https://brainly.com/question/31441174
#SPJ11
you are not sure if a certain word has an"e"at the end
Answers
Which expression can be used to find the surface area of the following square pyramid?
10

Answers
Answer:
100+40+40+40+40
Explanation:
hopes this help :)
Select the three type of undesirable software.
virus
firewall
peer-to-peer
nannyware
adware
malware
VPN
Answers
Virus, Adware, Malware
What file format would be required a coworker need to edit a layer in a photoshop file 
-png
-psd
-pdf
-jpeg
Answers
Using the flowchart below, what value when entered for Y will generate a mathematical error and prevent our flowchart from being completely executed? 3 0 1 None of these values will produce a mathematical error

Answers
Answer:
The answer is the last choice that is "None of these values will produce a mathematical error".
Explanation:
In this question, the above given choice correct because neither of the flowchart procedures could trigger a mathematical error. This error could not be induced by multiplication, addition and subtraction, and the only division by 15. It is the only divide by 0, that's why the above flowchart will produce a mathematical error.
Which statement about analog and digital images is true? With advances in technology, digital images look exactly like the analog images they represent. Sampling an analog image more frequently produces a digital image with a better representation. Analog images come from data that is measured at regular intervals. Digital images come from data that is measures continuously.
Answers
Answer:
Sampling an analog image more frequently produces a digital image with better representation.
Explanation:
Note that an image is a representation of two types of signals which contain color information that is arranged along the x and y spatial axis.
True, it is possible to convert analog image data into a digital image by means of sampling the analog display more frequently which leads a digital image with better representation.
The statement which is true about analog and digital images is: B. Sampling an analog image more frequently produces a digital image with a better representation.
An analog image can be defined as a type of image in which the tone is represented by continuous variation. Some examples of an analog image are;
Photographs.Medical images.Television images.Paintings.A digital image can be defined as a type of image that comprises a matrix of pixels and is typically stored in binary form.
Digital image processing (DIP) is a sampling technique that is used to process (convert) an analog image into a digital image or for converting a digital image into an analog image. When continuously applied to an analog image, the intensity distribution and digital quality of the image is improved.
This ultimately implies that, a digital image with a better representation is produced when an analog image is sampled more frequently.
Find more information: https://brainly.com/question/8160034
Which fields in an IP packet header are examined by NetFlow to determine whether or not a given packet is part of a flow
Answers
NetFlow examines the source IP address, destination IP address, source port, destination port, and protocol field in the IP packet header to determine flow membership.
Flow membership refers to the classification of network packets into flows based on certain criteria. In the context of NetFlow, flow membership is determined by examining specific fields in the IP packet header, such as the source and destination IP addresses, source and destination ports, and the protocol field.
By analyzing these fields, NetFlow can group related packets that belong to the same flow, allowing for the monitoring and analysis of network traffic patterns, performance, and security.
Flow membership enables network administrators to gain insights into network behavior, identify anomalies, and optimize network performance and security measures.
Learn more about IP address here:
brainly.com/question/24930846
#SPJ4
!!Help please!!
Why is it a good idea to store numeric data in variables in a program?

Answers
Answer:
Pretty sure it's D
Explanation:
A variable in programming is a value that may vary depending on the conditions or information provided to the programme. The correct option is D.
What is a variable?A variable in programming is a value that may vary depending on the conditions or information provided to the programme. A programme is typically made up of instructions that tell the computer what to perform and data that the programme utilises while executing.
In any programming language, it is always a good idea to store numeric data in variables in a program because that makes it easier to reference and make changes to the data.
Hence, the correct option is D.
Learn more about Variables:
https://brainly.com/question/15776744
#SPJ2
you use the read csv() function to import the data from the .csv file. assume that the name of the data frame is flavors df and the .csv file is in the working directory. what code chunk lets you create the data frame?
Answers
The code chunk that lets you create the data frame is flavors_df <-read_csv("flavors_of_cacao.csv").
Here's the complete question:
you use the read csv() function to import the data from the .csv file. assume that the name of the data frame is flavors df and the .csv file is in the working directory. what code chunk lets you create the data frame?
A flavors_df <- "flavors_of_cacao.csv"(read_csv)
B flavors_df + read_csv("flavors_of_cacao.csv")
C flavors_df <-read_csv("flavors_of_cacao.csv")
D read_csv("flavors_of_cacao.csv") + flavors_df
What is a code chunk?
Code chunk refers to a runable piece of R programming language code that helps to reduce incidents of mismatch pertaining to the commentary in a paper and the results being discussed.
Learn more on code chunk rom:
https://brainly.com/question/28209816?referrer=searchResults
#SPJ4
what is computer? Write is features
Answers
Explanation:
A computer is an machine that accepts data as input,processes that data using programs, and outputs the processes the data as information.
the features are
1) speed
2) accuracy
3) versatility
4) multi tasking
5) reliability
anything you want to do in hootsuite can be found in the , with the main workspace in the ?
Answers
Everything on Hootsuite may be accessed in the Header or the Sidebar, with the primary workspace in the center. The sidebar has links to essential Hootsuite features such as Streams, Inbox, Planner, Analytics, and the App Directory.
What is a workspace?Workspaces are groups of windows on your desktop. You may set up numerous workspaces, which function similarly to virtual desktops.
Workspaces are intended to decrease clutter and make the desktop more navigable. Workspaces can help you arrange your tasks.
Learn more about Hootsuite:
https://brainly.com/question/19721837
#SPJ1
PLEASE HELP! WILL GIVE BRAINLIEST

Answers
Answer:
Explanation:find out
What does firewall do
Answers
Answer:
help
Explanation: to make people blocked on school computer
A company uses cell phones that do not have SIM cards and can only be managed by a specific
network provider. The company wants to buy 3G cell phones that have SIM cards so they can switch to
any chosen provider. What network type best suits the company's needs?
A. GSM
B. CDMA
C. PRL
D. LTE
Answers
Based on the company's requirement to switch to any chosen network provider, the network type that best suits their needs is GSM (Global System for Mobile Communications).
GSM is a widely adopted standard for mobile communication and is used by the majority of the world's cellular networks. One of the key advantages of GSM is its use of SIM cards (Subscriber Identity Module). SIM cards allow users to easily switch between different network providers by simply swapping out the SIM card in their device. This flexibility provides the company with the freedom to choose the network provider that offers the best coverage, pricing, and services for their specific needs.
On the other hand, CDMA (Code Division Multiple Access) is another network technology used in cellular communication. Unlike GSM, CDMA does not utilize SIM cards. CDMA phones are typically tied to specific network providers and do not offer the same level of flexibility when it comes to switching between providers. Therefore, CDMA is not the best network type for the company's requirement to have the ability to switch to any chosen provider.
PRL (Preferred Roaming List) is not a network type but rather a list that CDMA phones use to prioritize which networks to connect to when roaming. It is not directly relevant to the company's requirement.
LTE (Long-Term Evolution) is a 4G wireless communication standard that provides high-speed data transmission. While LTE is an advanced network technology, it does not specifically address the company's need for flexibility in switching network providers.
In summary, the network type that best suits the company's needs for switching to any chosen provider is GSM.
For more questions on network
https://brainly.com/question/28342757
#SPJ11
how can a network be certified as an effective network?
Answers
Performance, stability, security, and reliability tests can be used to certify a network's efficacy.
By evaluating a network's performance, stability, security, and dependability, its effectiveness can be confirmed. Performance testing entails evaluating the network's speed and capacity to make sure it satisfies user needs. , stability, security, and reliability tests can be used to certify a network's efficacy. Stability testing aids in finding any potential problems that might prevent the network from carrying out its intended duties. Through security testing, it is determined whether the network is safe from intrusions and malicious assaults. Last but not least, reliability testing makes sure the network is accessible and operating as it should. A network can only be certified as effective after passing each of these tests.
Learn more about network here:
brainly.com/question/29970297
#SPJ4
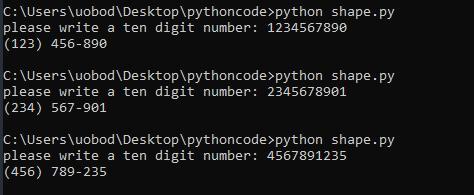
Write a program that takes a 10-digit phone number and adds a hyphen in the correct location. Using an input field for the user to enter the information. Also, use a string for instructions on how to enter the phone in the input field.
Answers
The python program will request for a ten digit number from the user and formulate a real phone number from it.
How to write a python program to form a real phone number?The program is written in python.
Therefore,
x = input("please write a ten digit number: ")
if len(x) == 10:
a = f"({x[0:3]})"
b = x[3:6]
c = x[7:]
print(a + " " + b + "-" + c)
Code explanation:The variable x is used to store the user's input.If the length of x is equals to 10, then we get the first three terms in bracket, the second three terms and the last 4 terms.Finally, we use delimiters to join the variables as required and print it out.learn more on python here: brainly.com/question/13462052
#SPJ1


look at all the snow is it a fragment or sentence
Answers
Answer: Sentence
Explanation: Because it has a subject (snow) and a predicate (look)
briefly explain the emerging trends in micro computer technology according to size
Answers
Answer:
Emerging trends in IT include big data analytics, virtual and augmented reality, 5G, and the internet of things. Computer science workers can learn about computer science current events and new technologies by joining a professional organization.Mar 3, 2022
Which method can be used to place an item at a specific index in a list?
a. append
b. add index
c. insert
Answers
To position an item at a given index in a list, use the insert method. adds a new item to a combo box or selection list before a particular item is selected.
Which procedure can be used to insert an item into a list at a given index?The extend() method appends a new data collection to a list while the insert() method appends a new item at the specified index, append() adds a new item to the end of a list, and append() adds a new item to the last index of a list.
What variety of inserts are there?There are two main categories of inserts: those held in place by external threads and those that rely on alternative holding mechanisms (such as knurling, grooves, and interference fits) in lieu of threads.
To know more about index visit :-
https://brainly.com/question/14297987
#SPJ4
why is concurrency control important? to ensure data integrity when updates occur to the database in a multiuser environment to ensure data integrity while reading data occurs to the database in a multiuser environment to ensure data integrity when updates occur to the database in a single-user environment to ensure data integrity while reading data occurs to the database in a single-user environment all above mentioed.
Answers
Mutual exclusion isolation is implemented using concurrency control. In the system, it guarantees serialization. When read-write operations are performed, it maintains data consistency and settles the dispute.
Why are concurrency and database integrity important?Data integrity is crucial because it ensures and secures the searchability and source-traceability of your data. When effective data accuracy and data protection are maintained, data performance and stability also improve. It's crucial to keep data accurate and complete while also preserving their integrity.
What exactly does the term "data integrity" mean to you?Data integrity is the consistency of the quality, correctness, and completeness of data across formats and throughout time. Data integrity preservation is an ongoing activity for your business.
To know more about concurrency control visit :-
https://brainly.com/question/14209825
#SPJ4
you are querying a database that contains data about music. each musical genre is given an id number. you are only interested in data related to the genre with id number 7. the genre ids are listed in the genre id column. you write the sql query below. add a where clause that will return only data about the genre with id number 7.
Answers
SELECT * FROM track WHERE album_ID = 7.
What is database?A collection of unique, compact pieces of information are called data. It can be utilized in many ways, including as text, numbers, media, bytes, etc. It may be kept on paper, in an electronic memory, etc.The word "data" comes from the Latin word "datum," which meaning "a single piece of information." It is the word datum's plural.Data is information that can be transformed into a form for swift movement and processing in computing. Data can be swapped out. The clause WHERE album_id = 7 will return only data about the album with ID number 7. The complete query is SELECT * FROM track WHERE album_ID = 7. The WHERE clause filters results that meet certain conditions. The WHERE clause includes the name of the column, an equal sign, and the value(s) in the column to include.To learn more about database, refer to
https://brainly.com/question/518894
#SPJ1
A customer has reported that when using a cable to connect an older laptop to a 100Mbps switch that the link light does not illuminate. When testing the same cable with a newer 1Gbps switch, it works fine. Which of the following is the MOST likely cause of the problem?
Answers
The cable is pinned as a crossover. Crossover cables move the wire from pin 1 at one end to pin 3 at the other connector, as the name implies.
What is Crossover cables ?An Ethernet cable used to directly connect computing devices is known as a crossover cable. The RJ45 crossover cable uses two separate wiring standards instead of just one, using the T568A wiring standard on one end and the T568B wiring standard on the other.The transmit signals at one end of the crossover wire are connected to the receive signals at the other end by purposefully crossed cabling. The transmit signals at one end of the crossover wire are connected to the receive signals at the other end by purposefully crossed cabling.A patch cable can be used in place of a crossover cable or vice versa, and the receive and transmit signals are automatically adjusted within the device to give a functional connection, thanks to the auto MDI-X functionality that is supported by many network devices today.To learn more about Crossover cables refer :
https://brainly.com/question/14325773
#SPJ4