Those that work in the Printing Technology pathway are typically
-self-employed, and work indoors.
-self-employed, and work outdoors.
-not self-employed, and work outdoors.
-not self-employed, and work indoors.
Answers
Answer: self-employed, and work indoors.
Related Questions
The code below run a full-stepping sequence for a unipolar stepper motor? while(1) 1 const char steps ) = [0x08. OxOC, Ox04, 0x06. OxO2, Ox03, 0x01. 0x09); PTC->PDOR - steps [i++ & 7] << 3: delayMs(5): 1 True False
Answers
The provided code runs a full-stepping sequence for a unipolar stepper motor by continuously updating the PTC register with values from an array and introducing a 5 millisecond delay between steps. The statement "True" is correct.
The code "while(1) const char steps) = [0x08, 0x0C, 0x04, 0x06, 0x02, 0x03, 0x01, 0x09]; PTC->PDOR = steps[i++ & 7] << 3; delayMs(5);" runs a full-stepping sequence for a unipolar stepper motor. It continuously loops while shifting through the array of steps values and updating the PTC register with the corresponding value.
The "delayMs(5)" function introduces a delay of 5 milliseconds between each step. The statement "1" is always true, indicating an infinite loop. Therefore, the statement "True" is correct, while the statement "False" is incorrect.
Learn more about array of steps here:
https://brainly.com/question/31678821
#SPJ11
.What are two types of cloud-enabled services for mobile devices? (Choose two.)
1. Locator apps
2. Remote backup
3. passcode configuration
4. screen app locking
Answers
The two types of cloud-enabled services for mobile devices are remote backup and locator apps. These apps can also remotely lock or erase data from the device for security purposes.
Remote backup allows users to backup their mobile device data such as contacts, photos, and messages to the cloud, which can be accessed from any device with internet access. This ensures that users can recover their data in case their device is lost, stolen, or damaged.
Cloud-enabled services have become essential for mobile device users as they provide numerous benefits such as data backup, synchronization, and remote access. There are different types of cloud-enabled services available for mobile devices, but two of the most common ones are remote backup and locator apps. Remote backup is a service that allows users to backup their mobile device data to the cloud, which can be accessed from any device with internet access. This data includes contacts, photos, messages, and other important files. The data is encrypted and stored securely in the cloud, ensuring that it is safe from any kind of security breach. In case of a lost, stolen, or damaged device, users can easily recover their data by logging into their cloud account from another device.
To know more about cloud-enabled services visit :-
https://brainly.com/question/30227796
#SPJ11
agree and tell why becoming a priest/nun is an honorable job PLEASE ASAP
Answers
la révolution industrielle rédaction
Answers
The Industrial Revolution began in the 18th century in Great Britain. It was only the first stepping-stone to the modern economic growth that is still growing to this day. With this new bustling economic power force Britain was able to become one of the strongest nations. While the nation was changing so was the way that literature was written. The Industrial Revolution led to a variety of new social concerns such as politics and economic issues. With the shift away from nature toward this new mechanical world there came a need to remind the people of the natural world. This is where Romanticism came into play; it was a way to bring back the urban society that was slowly disappearing into cities.
The Agricultural Revolution: Between 1750 and 1900 Europe’s population was dramatically increasing, so it became necessary to change the way that food was being produced, in order to make way for this change. The Enclosure Movement and the Norfolk Crop Rotation were instilled before the Industrial Revolution; they were both involved in the separation of land, and the latter dealt more with developing different sections to plant different crops in order to reduce the draining of the land. The fact that more land was being used and there weren’t enough workers it became necessary to create power-driven machines to replace manual labor.
Socioeconomic changes: Prior to the Industrial Revolution, the European economy was based on agriculture. From the aristocrats to the farmers, they were linked by land and crops. The wealthy landowners would rent land to the farmers who would in turn grow and sell crops. This exchange was an enormous part of how the economy ran. With the changes that came with the Industrial revolution, people began leaving their farms and working in the cities. The new technologies forced people into the factories and a capitalistic sense of living began. The revolution moved economic power away from the aristocratic population and into the bourgeoisie (the middle class).
The working conditions in the factories during the Industrial Revolution were unsafe, unsanitary and inhumane. The workers, men, women, and children alike, spent endless hours in the factories working. The average hours of the work day were between 12 and 14, but this was never set in stone. In “Chapters in the Life of a Dundee Factory Boy”, Frank Forrest said about the hours “In reality there were no regular hours, masters and managers did with us as they liked. The clocks in the factories were often put forward in the morning and back at night. Though this was known amongst the hands, we were afraid to speak, and a workman then was afraid to carry a watch” (Forrest, 1950). The factory owners were in charge of feeding their workers, and this was not a priority to them. Workers were often forced to eat while working, and dust and dirt contaminated their food. The workers ate oat cakes for breakfast and dinner. They were rarely given anything else, despite the long hours. Although the food was often unfit for consumption, the workers ate it due to severe hunger.
During this time of economic change and population increase, the controversial issue of child labor came to industrial Britain. The mass of children, however, were not always treated as working slaves, but they were actually separated into two groups. The factories consisted of the “free labor children” and the “parish apprentice children.” The former being those children whose lives were more or less in the hands of their parents; they lived at home, but they worked in the factories during the days because they had to. It was work or die of starvation in this case, and their families counted on them to earn money. Fortunately these children weren’t subjected to extremely harsh working conditions because their parents had some say in the matter. Children who fell into the “parish apprentice” group were not as lucky; this group mainly consisted of orphans or children without families who could sufficiently care for them. Therefore, they fell into the hands of government officials, so at that point their lives as young children turned into those of slaves or victims with no one or nothing to stand up for them. So what was it exactly that ended this horror? Investments in machinery soon led to an increase in wages for adults, making it possible for child labor to end, along with some of the poverty that existed. The way that the Industrial Revolution occurred may have caused some controversial issues, but the boost in Britain’s economy certainly led toward the country becoming such a powerful nation.
Write a For loop that will display the numbers starting at 20, then 40, then 60, and continuing the sequence all the way to 200.
Answers
A For loop can be used. Here's an example For loop that accomplishes this:```for (let i = 20; i <= 200; i += 20) { console.log(i);}```
In the For loop, the variable i is initialized to 20. The loop then continues as long as i is less than or equal to 200. On each iteration of the loop, i is increased by 20 using the i += 20 syntax, which is a shorthand way of writing i = i + 20.
This ensures that the loop will display the numbers in increments of 20.Finally, the loop body displays the current value of i using console.log(i). This will output the numbers 20, 40, 60, and so on until 200 is reached.
Learn more about loops execute at;
https://brainly.com/question/14613605
#SPJ11
Python help!
Input a grade level (Freshman, Sophomore, Junior, or Senior) and print the corresponding grade number [9-12]. If it is not one of those grade levels, print Not in High School.
Hint: Since this lesson uses else-if statements, remember to use at least one else-if statement in your answer to receive full credit
Sample Run 1
What year of high school are you in? Freshman
Sample Output 1
You are in grade: 9
Sample Run 2
What year of high school are you in?
Kindergarten
Sample Output 2
Not in High School
Answers
Answer:
print("What year of high school are you in?")
grade = input()
grade = grade.lower()
if grade == "freshman":
print("You are in grade: 9")
elif grade == "sophomore":
print("You are in grade: 10")
elif grade == "junior":
print("You are in grade: 11")
elif grade == "senior":
print("You are in grade: 12")
else:
print("Not in high school")
Explanation:
The first line prints the question. "grade = input()" stores the answer the user will type in the terminal into the variable 'grade'.
grade.lower():
The third line lowercases the entire string ("FreshMan" would turn to "freshman"). Python is case-sensitive.
Then, test the string to see if it matches freshman, sophomore, junior, or senior. If the input string matches print the statement inside the if block. The last statement is the else. It prints if nothing else matches.
Using the drop-down menus, correctly match the name of the person with the computer-programming
innovation
In 1975,
founded Microsoft, which released Altair BASIC, the first
programming language for personal computers.
found the first computer bug in 1947, and invented the concept of a compiler in
1952
v led a team at IBM that developed FORTRAN and its compiler in 1957
developed C++ programming language, and published the reference guide
in 1987
released the Python programming language.
Answers
Answer:
1. Bill Gates and Paul Allen
2. Grace Murray Hopper
3. John Backus
4. Bjarne Stroustrup
5. Guido van Rossum
Whats wrong with this code? in terms of indentation.
#Travies Robinson
#11/23/2020
#Coding Fundamentals : Coding Logic : 03.05 Python Project favorite video game response
def main():
answer = input("Would you like to take a one question survey? (yes or no)")
if(answer == "yes"):
favGame = input("What is your favorite video game?")
print("Your favorite video game is the " + favGame + " amazing i've never played that
before.")
answer = input("What your favorite part of " + favGame + "?")
print("Interesting mabye i should try " + favGame + "."")
Country = input("What country are you living in right now?")
print("You are currently living in " + Country + ".")
Age = input("How old are you?")
print("Your age is " + Age + ".")
print("Thank you for answering the survey and have a great day!")
else:
print("Good-bye")
main()
Answers
Answer:
(yes or no)") I do not really think this would work but I really didn't deal with this when i hack. That would need to be seperate from the question. Like for example Question = input("your question")
if Question == ("yes")
print ("well done")
elif Question == ("no")
print ("try again")
Why is compression important for video
streaming?
Oto increase the number of frames per second
so that motion appears smooth
Oto watch video without waiting for it to
download
O to improve image quality
O to increase file size
DONE✔
Question
Answers
Compression, important for video streaming to watch video without waiting for it to download.
The technique of compressing a video file such that it takes up less space than the original file and is simpler to send across a network or the Internet is known as video compression.
Since compression makes it possible for video data to be transferred over the internet more effectively, it is crucial for video streaming. The video files are often huge, they would take an extended period to download or buffer before playback if they weren't compressed.
Learn more about video, here:
https://brainly.com/question/9940781
#SPJ1
Carlos currently manages an 802.11n wireless network. He has been asked to see if there is a way to increase the speed of the network without upgrading to another Wi-Fi standard. Which of the following would allow him to do this if supported by the current technologies in use?a. ANT+ b. IR c. channel bonding d. 802.11ac
Answers
Since Carlos currently manages an 802.11n wireless network the option that would allow him to do this if supported by the current technologies in use is option d. 802.11ac.
Why are wireless networks important?Computer networks can be wireless or wired, depending on how the network nodes communicate with one another.
Computer networks can be wireless or wired, depending on how the network nodes communicate with one another. Residential, commercial, and telecommunications network installations can all be connected wirelessly.
Hence, Carlos has been asked to investigate any potential alternatives to upgrading to a new Wi-Fi technology in order to increase the network's speed. To determine whether his current 802.11n network is capable of channel bonding
Learn more about wireless network from
https://brainly.com/question/26956118
#SPJ1
Answer: the answer is 802.11ac
Explanation:
a signal’s spectral representation gives _______________ information about it.
Answers
A signal’s spectral representation gives frequency-domain information about it.
1. A signal's spectral representation gives frequency-domain information about it.
2. The spectral representation of a signal provides insights into the frequency content and distribution of the signal, allowing analysis and understanding of its frequency components.
3. By analyzing a signal in the frequency domain, we can determine the presence of specific frequencies or frequency ranges, identify dominant frequencies, and detect harmonics or interference.
4. The spectral representation is often obtained through techniques such as Fourier analysis, which converts a signal from the time domain to the frequency domain.
5. This frequency-domain information is valuable for various applications, including signal processing, communication systems, audio and video processing, and analyzing the behavior of physical systems.
Learn more about frequency-domain:
https://brainly.com/question/31757761
#SPJ11
3) If you were hired to develop a marketing strategy for a new container designed to store leftover food, what internet marketing strategies would you use? Who would you target, and how would you target them?
Answers
If someone is hired to develop a marketing strategy for a new container designed to store leftover food, the internet marketing strategies would be the quality and quantity of the container. The food companies would be targeted.
What are marketing strategies?A company's overall plan for reaching out to potential customers and converting them into buyers of their goods or services is referred to as a marketing strategy.
Therefore, the quality and quantity of the container would be the internet marketing tactics if someone were hired to create a marketing plan for a new container made to keep leftover food. The food industry would be the target.
To learn more about marketing strategies, refer to the link:
https://brainly.com/question/29376574
#SPJ1
Linux operating systems should not be modified once the installation is complete.
Answers
Linux operating systems are designed to be highly customizable and flexible, allowing users to tailor their system to their specific needs. However, it is generally not recommended to modify the core components of the operating system once the installation is complete. This is because any modifications to the system can potentially introduce instability or security vulnerabilities, and can also make it more difficult to receive updates and support from the Linux community.
Instead, users should focus on installing additional software packages or customizing the user interface without making fundamental changes to the underlying operating system. It is also important to keep the system up-to-date with security patches and software updates, which can help to mitigate any potential vulnerabilities or issues. Overall, while Linux offers a high degree of flexibility, it is important to use caution when making modifications to ensure the stability and security of the system.
It's important to clarify that the statement "Linux operating systems should not be modified once the installation is complete" is not entirely accurate. In fact, Linux systems are designed to be flexible and customizable, allowing users to modify, update, and enhance them as needed. This can be done through package management systems, software updates, security patches, and system configuration adjustments, all of which contribute to the ongoing maintenance and improvement of a Linux operating system.
To know more about Linux operating systems visit:-
https://brainly.com/question/29798420
#SPJ11
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
in java, it is possible to write a method that will return:
Answers
Yes, Java allows you to return this. The following assertion is true. "return this; ". The current object is returned when this is returned from a method.
What is return this in Java?When referring to the current object in a function Object() or instance method, Java uses the "this" keyword. This allows you to refer to class members like constructors, variables, and methods.
Name and age are two private variables for the class Student. We read user data via a method called setValues(), assign them to these (instance) variables, and then return the current object.
public class Student {
private String name;
private int age;
public Student SetValues(){
Scanner sc = new Scanner(System.in);
System.out.println("Enter the name of the student: ");
String name = sc.nextLine();
System.out.println("Enter the age of the student: ");
int age = sc.nextInt();
this.name = name;
this.age = age;
return this;
}
public void display() {
System.out.println("name: "+name);
System.out.println("age: "+age);
}
public static void main(String args[]) {
Student obj = new Student();
obj = obj.SettingValues();
obj.display();
}
}
To learn more about java refer :
https://brainly.com/question/25458754
#SPJ4
HELPPPP PLEASE HURRY
Which of these is the best way to become an art director in the gaming industry? (Select all that apply).
work your way up from a low level position
create a brilliant game
assemble a great team
familiarize yourself with the top games
Answers
Answer:
c.) assemble a great team
Explanation:
How do I make the text and heading different colors?
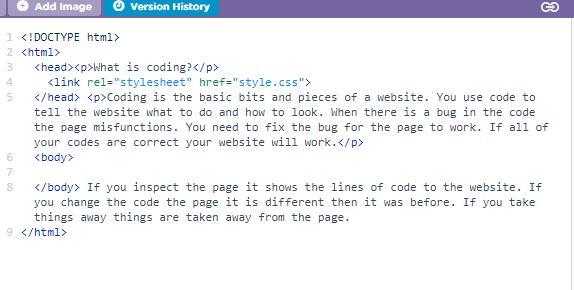
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
_____ what occurs when a distributed database experiences a network error and nodes cannot communicate
Answers
The database experiences a network error and nodes cannot communicate, it can lead to various issues ranging from service disruptions to data inconsistencies.
A distributed database experiences a network error and nodes cannot communicate, a partition or network split occurs. This situation impacts the system's consistency, availability, and partition tolerance, as outlined by the CAP theorem.
When a distributed database experiences a network error and nodes cannot communicate, it can lead to various issues. The extent of the impact on the database depends on the severity and duration of the network error.
To know more about algorithms visit:-
https://brainly.com/question/24452703
#SPJ11
A ______ is a set of step-by-step instructions to complete a task so that users can be sure to complete the task correctly.
Answers
Answer:
Algorithm
Explanation:
An algorithm a process or set of instructions that is created to solve a problem.
what is Mainframe computer
Answers
Answer:
A Mainframe computer, informally called an mainframe or big iron, is a computer used primarily by large organizations for critical applications, bulk data processing such as the census and industry and consumer statistics.
You will create a brief story that has a negative character arc and has at least two main characters (protagonist and antagonist). No one else will have a name besides your main characters (though you can specify things like ‘mom’ or ‘bestfriend’), and you will focus on these two characters. A minimum of 20 sentences will be required.
Answers
Answer:
Alex was an ambitious young man who had big dreams for himself. He had been working hard to reach his goals and was determined to make something of himself.
He had grown up in a small town and had always been the outsider. His parents had died when he was young and he had been raised by his aunt and uncle, who had never really given him the support he needed.
One day, Alex met a man who seemed to understand him. His name was John and he was a successful businessman. He told Alex that he could help him reach his goals and make something of himself.
Alex was eager to accept John's offer and quickly went to work for him. He soon found out that John was a ruthless businessman who only cared about making money. He didn't care who he hurt and was willing to do whatever it took to get what he wanted.
Alex found out that John was involved in some shady deals, but he was too scared to speak up. He was afraid of losing his job and not being able to reach his goals.
One day, John asked Alex to do something unethical and Alex refused. John was furious and fired Alex on the spot. Alex was devastated and felt like his dreams were shattered.
He went back to his small town and tried to start over, but he couldn't shake the feeling that he had failed. He had been so close to reaching his goals and now it seemed like it was all for nothing.
Still, Alex was determined to make something of himself and refused to give up. He worked hard and eventually got a job at a local company.
Although his new job was far from his dreams, Alex was grateful that he had something to fall back on. He was determined to make something of himself and refused to let John's betrayal define him.
Alex continued to work hard and eventually earned himself a promotion. He was back on track and things were starting to look up.
But then, one day, Alex received a call from John. He asked Alex to come back and work for him, but this time on his own terms. Alex was hesitant, but he knew he couldn't pass up this opportunity.
Alex went back to work for John, but this time he was much more cautious. He was determined to make something of himself and refused to let John take advantage of him again.
However, despite his best efforts, Alex soon found himself back in the same situation he was in before. He was once again stuck in a cycle of John's manipulation and lies. He had lost all control and was powerless to escape.
Alex had gone from having big dreams to feeling completely defeated. He had gone from being an ambitious young man to a victim of manipulation and lies. He had experienced a negative character arc, and it seemed like there was no way out.
Which girl is he baddest 1. Shawty 2.Lisa 3.Ashley
Answers
Answer:
. . . . . . . S H A W T Y.. . .. . .
When you turn on a computer, Windows starts and displays a ____ consisting of the time and date. Group of answer choices user name screen lock screen Start screen sign-in screen
Answers
Answer:
lock
Explanation:
When you turn on a computer, Windows starts and displays a(n) ____ screen, consisting of the time and date. a.access b.open c.lock d.homebase
✓ lock
When you turn on a computer, Windows starts and displays a lock screen consisting of the time and date. Hence, option B is correct.
What does lock screen do?To further secure your Android smartphone or tablet, you can configure a screen lock. Your smartphone will prompt you to enter a PIN, pattern, or password every time you power it on or wake up the screen. You can use a fingerprint to unlock various gadgets.
The lock screen feature's display of notifications related to a certain task is among its intriguing features. The user can specify whether they want notifications to come from all compatible applications or just the ones they specifically need.
On smartphones, the lock screen function also displays the time and date as well as any missed calls, text messages, or other notifications. Upon unlocking the device.
Thus, option B is correct.
For more information about lock screen, click here:
https://brainly.com/question/18442034
#SPJ6
describe the details of the process how the vm user program, vm kernel, the hypervisor, and hardware work together to execute the code and handle run-time conditions.
Answers
The process of how the VM user program, VM kernel, the hypervisor, and hardware work together to execute code and handle run-time conditions can be described in the following steps:
1. The VM user program starts by sending a request to the VM kernel to execute a certain code.
2. The VM kernel receives the request and translates it into instructions that the hardware can understand.
3. The VM kernel then sends the instructions to the hypervisor, which acts as an intermediary between the VM kernel and the hardware.
4. The hypervisor communicates with the hardware and instructs it to execute the code.
5. The hardware executes the code and sends the results back to the hypervisor.
6. The hypervisor then sends the results back to the VM kernel, which translates them back into a format that the VM user program can understand.
7. The VM kernel sends the results back to the VM user program, which can then use them to continue its operations.
Throughout this process, the VM kernel and the hypervisor work together to handle any run-time conditions that may arise, such as memory allocation or hardware errors. By working together in this way, the VM user program, VM kernel, hypervisor, and hardware are able to efficiently execute code and handle run-time conditions.
Learn more about VM user at
https://brainly.com/question/29892157
#SPJ11
listen to exam instructions which step in the penetration testing life cycle is accomplished using rootkits or trojan horse programs?
Answers
The "Exploitation" step of the penetration testing life cycle is often when rootkits or Trojan horse programs are used.
In the Exploitation phase, the tester uses vulnerabilities discovered in earlier parts of the testing process to try to gain unauthorized access to the target system or network. This can entail using tools like Trojan horse programs or rootkits to secretly access the system or to keep access after first entrance.
It's vital to remember that using such tools is typically not advised because they might be misused maliciously and destroy the target system or network.
Such tools should only be used in a penetration testing environment under rigorous control and only with the owner of the target system's express consent.
To know more about penetration testing kindly visit
https://brainly.com/question/29560410
#SPJ4
what happens when a logic error occurs? a. the program will end abnormally. b. the results of the program will be inaccurate. c. the program will continue executing until you cancel out of it.
Answers
Answer:
b. the results of the program will be inaccurate
Explanation:
Which operating system is used by most the supercomputer system in the world
Answers
Answer:
Linux
Explanation:
Linux runs all of the top 500 supercomputers
How do u set up a Wi-Fi network on Android
Answers
Answer:
These are some way I know

SOMEONE PLEASE HELP ME PLEASE!!!!!!!!

Answers
Answer:
Brainstorm and begin sketching new oven designs
Which of the following best describes today’s average gamer?
The average age is eighteen, and many more males play than females.
The average age is thirty, and only slightly more males play than females.
The average age is thirty, and many more males play than females.
The average age is eighteen, and only slightly more males play than females.