The following mediums of advertising are part of the purchase funnel: Online Video, Search, Display, and Social TV Commercials, Billboards, and Newspaper
Answers
The mediums of advertising mentioned, such as online video, search, display, and social, are typically used in the awareness and consideration stages of the purchase funnel.
These mediums help to introduce the brand, generate interest, and drive website traffic. TV commercials, billboards, and newspaper ads are more traditional mediums that can also be effective in generating awareness and consideration.
However, they may not provide as much targeted reach as digital mediums. Overall, using a combination of these mediums can be a great way to reach consumers at different stages of the purchase funnel and increase the likelihood of conversion.
You can learn more about advertising at: brainly.com/question/3163475
#SPJ11
Related Questions
Deliberately providing controlled unclassified information (CUI) to the media describes which type of unauthorized disclosure
Answers
Deliberately providing controlled unclassified information (CUI) to the media describes unauthorized disclosure or media leak.
In other words, it refers to the intentional sharing of CUI information with the public without authorization.What is unauthorized disclosure?Unauthorized disclosure refers to the sharing or revealing of classified or unclassified information in violation of established policy and protocols. It can happen deliberately or accidentally. Unauthorized disclosures can be classified into two categories - intentional or unintentional.
Intentional unauthorized disclosure involves the deliberate and willful disclosure of classified or unclassified information without authorization. It can happen through leaks to the media, sharing sensitive information with unauthorized personnel, and other related activities.
Unintentional unauthorized disclosure, on the other hand, refers to the inadvertent sharing of classified or unclassified information. It could happen due to human error, mishandling of classified information, or other related reasons.
Deliberately providing controlled unclassified information (CUI) to the media describes unauthorized disclosure or media leak.
To know more about unclassified information visit:
brainly.com/question/30371123
#SPJ11
write a paragraph on plastic and pollution within 100 words
Answers
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
Most importantly, plastic pollution harms the Marine life. The plastic litter in the water is mistaken for food by the aquatic animals. They eat it and die eventually. For instance, a dolphin died due to a plastic ring stuck in its mouth. It couldn’t open its mouth due to that and died of starvation. Thus, we see how innocent animals are dying because of plastic pollution.
In short, we see how plastic pollution is ruining everyone’s life on earth. We must take major steps to prevent it. We must use alternatives like cloth bags and paper bags instead of plastic bags. If we are purchasing plastic, we must reuse it. We must avoid drinking bottled water which contributes largely to plastic pollution. The government must put a plastic ban on the use of plastic. All this can prevent plastic pollution to a large extent.
Answer:
Plastic is everywhere nowadays. People are using it endlessly just for their comfort. However, no one realizes how it is harming our planet. We need to become aware of the consequences so that we can stop plastic pollution. Kids should be taught from their childhood to avoid using plastic. Similarly, adults must check each other on the same. In addition, the government must take stringent measures to stop plastic pollution before it gets too late.
Uprise of Plastic Pollution
Plastic has become one of the most used substances. It is seen everywhere these days, from supermarkets to common households. Why is that? Why is the use of plastic on the rise instead of diminishing? The main reason is that plastic is very cheap. It costs lesser than other alternatives like paper and cloth. This is why it is so common.
Secondly, it is very easy to use. Plastic can be used for almost anything either liquid or solid. Moreover, it comes in different forms which we can easily mold.
Furthermore, we see that plastic is a non-biodegradable material. It does not leave the face of the Earth. We cannot dissolve plastic in land or water, it remains forever. Thus, more and more use of plastic means more plastic which won’t get dissolved. Thus, the uprise of plastic pollution is happening at a very rapid rate.
suppose the net capital outflow from zenovia is negative. this implies that:____
Answers
If the net capital outflow from Zenovia is negative, this implies that Zenovia is experiencing a net capital inflow, meaning more investments are coming into the country than leaving it.
In this situation, foreign investors are investing more in Zenovia's assets than Zenovian investors are investing in foreign assets. Here's a step-by-step explanation:
1. Net capital outflow (NCO) is the difference between the total amount of capital leaving a country and the total amount of capital entering the country. A positive NCO means more capital is leaving than entering, while a negative NCO means more capital is entering than leaving.
2. When there is a negative NCO, it indicates that foreign investments in Zenovia are greater than Zenovian investments in foreign countries. This could be due to a variety of factors, such as favorable interest rates, strong economic growth, or political stability in Zenovia.
3. As a result of the negative NCO, Zenovia will experience an increase in its financial capital, which can lead to greater economic growth and development.
4. A negative NCO can also have an impact on Zenovia's currency, as foreign investors must purchase Zenovian currency to invest in its assets. This demand for the currency can lead to an appreciation of its value.
5. In summary, a negative net capital outflow from Zenovia implies that the country is experiencing a net capital inflow, with more foreign investments coming in than Zenovian investments going out. This can lead to various economic benefits, including increased financial capital and currency appreciation.
Know more about the net capital inflow click here:
https://brainly.com/question/14292127
#SPJ11
PLZZZZZZZZZZZZZZZ HELP ME OUT!!!!! I SICK AND TIRED OF PEOPLE SKIPING MY QUESTION WHICH IS DUE TODAY!!!!
Directions
Read the dilemma below and then complete the Feelings & Options steps.
"Missing Out"
Text:
For months, Aida and her three closest friends had been waiting for a new movie to come out. The movie was based on one of their favorite books, and they promised they would see it all together and then go out for pizza. On the movie's opening weekend, Aida had a last-minute emergency and wasn't able to go. The others decided to go anyway because they had really been looking forward to it. That night they posted constantly about their fun and new inside jokes. Aida wanted to keep connected, but seeing the constant posts bummed her out. She felt like no one even cared that she had missed out on their plans.
Identify: Who are the different people involved in the scenario? What dilemma or challenge are they facing?
Answers
Answer:
One friend being nice and the other being rude, thats a dillema.
Explanation:
Because its logical
Does anyone know 7.1.3: Firework karel?
Answers
Answer:
Yess its from freelancer
Play a role of an IT employee and explain how you will solve
business problems and provide decision support for a school by
establishing a database.
Write it clearly. thank you!
Answers
As an IT employee, I would solve business problems and provide decision support for the school by establishing a database. A database would help in organizing and managing various school-related data effectively, enabling informed decision-making and streamlining processes.
To establish a database for the school, I would follow the following steps:
Requirement Gathering: I would meet with key stakeholders, such as school administrators, teachers, and staff, to understand their data management needs and identify the specific problems they are facing. This could include areas such as student records, attendance, academic performance, curriculum management, financial data, and more.Database Design: Based on the requirements gathered, I would design the database schema, which includes defining the tables, fields, and relationships between them. This step involves careful consideration of data normalization techniques to ensure efficient data storage and retrieval.Database Implementation: Using appropriate database management software, such as MySQL, Oracle, or Microsoft SQL Server, I would create the database and tables as per the design. I would also establish necessary security measures, such as user access controls and data encryption, to protect sensitive information.Data Migration and Integration: If the school already has existing data in different formats (e.g., spreadsheets, paper-based records), I would develop a strategy to migrate and integrate that data into the new database. This process may involve data cleansing, transformation, and validation to ensure accuracy and consistency.Application Development: Depending on the school's requirements, I may develop customized software applications or use existing solutions to interact with the database. These applications could include student information systems, attendance trackers, gradebook systems, or financial management tools. Integration with other existing systems, such as learning management systems or communication platforms, may also be considered.Training and Support: I would provide training sessions and documentation to school staff, ensuring they understand how to use the database effectively and efficiently. Ongoing support and maintenance would be provided to address any issues or evolving needs that may arise.By establishing a database for the school, we can centralize and organize various data sets, enabling efficient data management and decision-making processes. The database would improve data accuracy, accessibility, and integrity, leading to better insights and informed decision support for school administrators, teachers, and staff. It would streamline administrative tasks, enhance collaboration among different departments, and ultimately contribute to an improved overall school management system.
Learn more about database visit:
https://brainly.com/question/29412324
#SPJ11
write short note on social and emotional interaction
Answers
Social and emotional interaction refers to the way individuals interact with others and their ability to manage their own emotions in social situations. This involves skills such as communication, empathy, and understanding social cues.
Social and emotional interaction skills are critical for individuals to navigate social situations successfully and form strong relationships. Effective communication, empathizing with others, and understanding social cues can enhance one's ability to connect with others and foster positive interactions. Being able to regulate one's emotions in social situations is also crucial for managing stress, building resilience, and maintaining mental health. These skills can be improved through practice, such as engaging in social activities, seeking feedback, and learning from experience. Education and therapy can also provide valuable tools and strategies for developing social and emotional interaction skills and promoting healthy relationships and emotional wellbeing.
Learn more about mental health here;
https://brainly.com/question/31708532
#SPJ11
Explain why this scenario could put an organization in jeopardy of losing some of its workforce.
Situation: The IT manager decides to add a new software application to replace an older albeit less efficient software application.
Answers
Answer:
Not educating its employees on the new software.
Consider the following code segment. int x = 1;while ( /* missing code */{System.out.print ( x + "" "");x = x + 2;
Answers
To complete the code segment, one needs to add a condition to the while loop. The condition will determine when the loop should continue iterating and when it should stop. This would result in the output: 1 3 5 7 9.
Based on the provided code snippet, it appears that the intention is to print the value of x and update its value by adding 2 in each iteration of the loop.
If one want to print the value of x until it reaches a certain threshold, such as 10, the missing code in the while loop condition could be:
while (x <= 10) {
System.out.print(x + " ");
x = x + 2;
}
With this code, the loop will continue executing as long as x is less than or equal to 10. In each iteration, it will print the current value of x, followed by a space, and then update x by adding 2. The loop will terminate when x exceeds 10.
This would result in the output: 1 3 5 7 9.
Leran more about the code segment here
https://brainly.com/question/28343520
#SPJ4
describe the vulnerability and discuss the likelihood of the vulnerability being exploited involved in accessing a website with an unsigned public key
Answers
Users should exercise caution when accessing websites with unsigned public keys and verify the authenticity of the website and its SSL/TLS certificate before entering any sensitive information.
Accessing a website with an unsigned public key can expose the user to a security vulnerability, as it makes it easier for attackers to intercept and manipulate the communication between the user and the website. A public key is a crucial component of the SSL/TLS encryption protocol that is used to establish secure connections between users and websites. When a website uses an unsigned public key, it means that the authenticity of the public key has not been verified by a trusted third party, such as a certificate authority.
The vulnerability arises because an attacker can intercept the user's connection request and replace the website's unsigned public key with a fake public key that they control. This allows the attacker to establish a man-in-the-middle attack, where they can intercept and manipulate the communication between the user and the website. This can enable the attacker to steal sensitive information, such as login credentials, credit card details, or personal information, or to install malware on the user's device.
The likelihood of the vulnerability being exploited depends on various factors, such as the sophistication of the attacker, the sensitivity of the information being transmitted, and the value of the target. While the use of unsigned public keys is relatively rare, it can still pose a significant risk to users who access such websites. It is essential for website owners to ensure that their public keys are signed by a trusted certificate authority and that they use up-to-date SSL/TLS encryption protocols to establish secure connections with their users.
Learn more about Users here
https://brainly.com/question/27960093
#SPJ11
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
what are the answers for theses question?




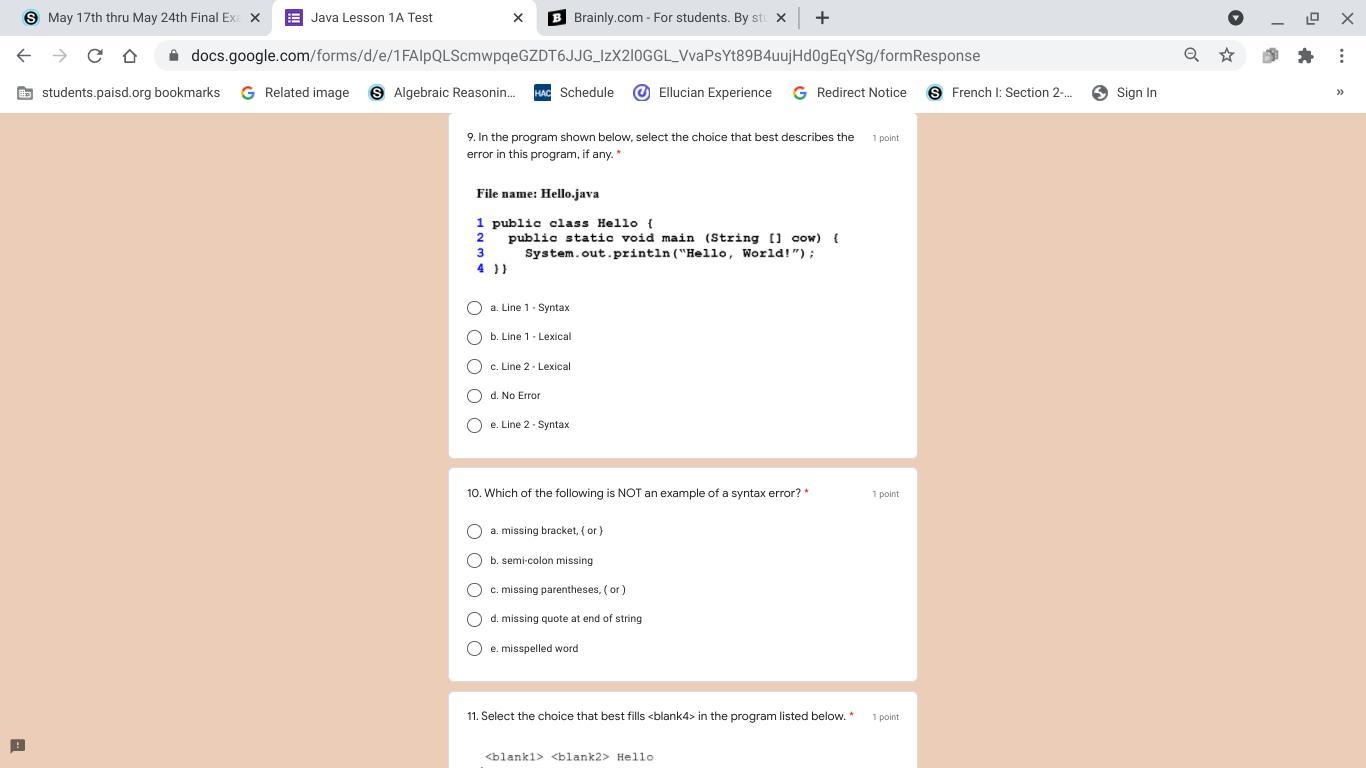
Answers
Answer: me no comprende coding
Explanation:
sorry
folder names should _____.
Answers
Only letters, numbers, and underscores—not spaces, punctuation, or amusing characters—should be used in folder names.
What does a computer folder do?A region on the computer known as a folder that houses other folders and files aids in keeping the computer organized. A folder can house files, which can hold data utilized by the operating system or other computer programs.
What do subfolders and folders do?Additionally, folders may include other folders, which may themselves contain additional folders or files. Folders are also referred to as file directories or simply directories due to the way they arrange and store data within the file system of the storage medium. There is no restriction on how many folders or subfolders can be made.
To learn more about folders visit:
brainly.com/question/14472897
#SPJ1
Which term refers to a system or application that acts as a go-between for clients' requests for network services
Answers
A The term that refers to a system or application that acts as a go-between for clients' requests for network services is "Proxy."
What is a proxy?A proxy is a server that serves as a link between clients and the internet. It intercepts traffic passing between the two. In addition, it can also be employed to offer anonymity.
Proxies are frequently utilized to filter content requests, log internet usage, and provide caching services.A proxy server has several advantages. They can provide security and privacy, as well as save bandwidth and improve network performance.
Learn more about proxy at;
https://brainly.com/question/4272568
#SPJ11
How do I get rid of system requirements not met go to Settings to learn more?
Answers
The correct answer is The "System requirements not met" watermark on the desktop informs users that they have installed Windows 11 on unsupported hardware.
A device (such as a computer, smartphone, tablet, or other mobile device) with internet connectivity and the capability to save and reproduce these Transaction Terms and any notices we provide you when using our Services is considered to have met the minimum system requirements (such as payment notifications). What standards are these? functions provided by the system, such as timing restrictions, limitations on the development process, standards, etc., such as dependability, reaction time, and storage needs. limitations on system representations, device capabilities, etc. Functional requirements, data requirements, quality requirements, and limitations are some major categories of system requirements. Consumers are frequently given them in great detail.
To learn more about System requirements click on the link below:
brainly.com/question/30664333
#SPJ4
Write an algorithm to find addition, subtraction, and multiplication of 2 numbers
Answers
Answer:
AdditionStep 1: Input the two numbers, a and b.
Step 2: Output a + b.
Step 3: Output a - b.
Step 4: Output a * b.
Step 5: If b = 0 output “undefined”.
Step 6: Else output a / b.
subtractionStep 1 If ( a < b ) then there will be no answer .
step 2f ( a = b ) then all the numbers greater than a are the answer so there will be infinite solutions possible.
Step 3 If ( a > b ) Suppose x is an answer to our equation. Then x divides (a – b).
Continuing with the same data set. Use Microsoft Excel or Tableau or one of the other visualization tools and create 3 visuals(graphs/charts): First chart should at-least use 2 data columns Second chart should at-least use 3 data columns Third chart should also use at-least 3 data columns These charts should show the legends correctly. Take screens shots and explain the dependencies that you have shown in these visuals in your report to submit.
Answers
Visuals using Microsoft Excel or Tableau and explain the dependencies you can show in the visuals. If you have specific data and requirements, please provide them, and I'll assist you in creating the visuals and explaining their dependencies in a report format.
For the first chart, you can create a bar chart that compares data from two columns. For example, you could compare the sales figures of two different products over a specific time period. The x-axis can represent the time period, and the y-axis can represent the sales figures. The legend can show the two products, distinguishing them by different colors or patterns. In the second chart, you can create a line chart that displays data from three columns. For instance, you could plot the temperature, humidity, and rainfall data over different months. The x-axis can represent the months, while the y-axis can represent the respective measurements.
Learn more about Microsoft Excel here:
https://brainly.com/question/32584761
#SPJ11
Internal combustion engines use hot expanding gasses to produce the engine's power. Technician A says that some engines use spark to ignite the gasses. Technician B says some engines use compression to ignite the gasses. Who is correct?
Answers
Answer:
Explanation:
Both are right.
Engines are divided into:
1) Internal combustion engines
2) Diesels
round 74,361 to the nearest 10
Answers
Answer:
74,400 i think
Explanation:
X = 10
y =
20
х» у
print("if statement")
print("else statement")
Answers
Answer:
"else statement"
Explanation:
Given
The above code segment
Required
The output of the program
Analyzing the program line by line, we have:
x = 10 ----> Initialize x to 10
y = 20 ----> Initialize y to 20
if x > y ----> check if x is greater than y
print("if statement") ----> Execute this line if the condition is true
The condition is false because 10 is less than 20, so: the statement will not be executed. Automatically, the else condition will be executed
else
print("else statement")
"else statement" without the quotes will be printed because the if condition is false
Custom-built mini-programs that can execute a complicated series of commands in a tool like microsoft word or excel are called.
Answers
Custom-built mini-programs that can execute a complicated series of commands in a tool like Microsoft word or excel are called macros.
What is a macro program?Macros are known to be a type of programs that functions by automating some commonly used processes or tasks that are found in the Excel.
Note that Custom-built mini-programs that can execute a complicated series of commands in a tool like Microsoft word or excel are called macros as a often records day to day operations through the use of keystrokes or a mouse.
Learn more about mini-programs from
https://brainly.com/question/24833629
#SPJ1
The method of encoding information to memory is called ___________. a. retention b. reviewal c. processing d. rehearsal please select the best answer from the choices provided a b c d
Answers
The method of encoding information to memory is called Rehearsal.
What is encoding?Encoding is the process of transforming data into a specific format that can be used by other systems or applications. It is used to reduce the size of data, improve data security, and make it easier to store and transfer data. Encoding is used in various areas like communication, data storage, and data processing. It is used to transform information into a format that can be read and understood by both machines and humans. It is also used to encode passwords, images, videos, and audio files. Encoding is an essential process that helps make data more secure, efficient, and reliable.
To learn more about encoding
https://brainly.com/question/24613164
#SPJ4
"Occasionally, visualization of an immobilization device appears
on the final image. What would you do if this is the case?
Answers
If an immobilization device appears on the final image during visualization, there are a few steps you can take to address this issue:Assess the impact,Retake the image,Communicate with the patient,Document the incident and supervisor.
1. Assess the impact: Determine if the presence of the immobilization device on the final image affects the diagnostic quality or interpretation of the image. If it does not affect the results, no further action may be necessary.
2. Retake the image: If the immobilization device obstructs the area of interest or hinders accurate interpretation, it may be necessary to retake the image.
Ensure that the patient is properly repositioned and the immobilization device is appropriately adjusted or removed before retaking the image.
3. Communicate with the patient: Explain to the patient the reason for retaking the image and reassure them that it is a necessary step to obtain accurate diagnostic information. Address any concerns or questions they may have regarding the retake.
4. Document the incident: Make a note in the patient's medical record documenting the presence of the immobilization device on the initial image and the steps taken to address the issue.
5. Consult with a radiologist or supervisor: If you are unsure about the appropriate course of action or need guidance, consult with a radiologist or supervisor for further instructions.
Remember to always prioritize patient care and follow established protocols and guidelines in your specific healthcare facility.
For more such questions visualization,Click on
https://brainly.com/question/29916784
#SPJ8
True or false. Genomics is an old science that is being replaced with computer technology
Answers
Answer:
False
Explanation:
The correct answer is false. Genomics is a relatively new technology compared to other biotechnologies from the past and it started around the 1970s when Frederick Sanger developed the first sequencing technique to sequence the entire genome. There were many discoveries prior to this such as the discovery of the structure of DNA and its bases. The Human Genome Project was launched in 1990 with the goal to sequence the entire human genome and was completed in 2003. Since then there have been many advancements in DNA sequencing technologies such as next-generation sequencing (NGS).
I hoped this helped <33
HISTORIA DE LAS PRINCIPALES CUENTAS CONTABLES Y DE LOS DOS ESTADOS FINANCIEROS
MENCIONAR LAS CUENTAS Y SUB CUENTAS EN CADA CASO.
Answers
Answer:
Sorry bud, i dont speak spanish, especially not ALL CAPS SPANISH.
Explanation:
this is your question in english:
HISTORY OF THE MAIN ACCOUNTS AND THE TWO FINANCIAL STATEMENTS.
MENTION THE ACCOUNTS AND SUB ACCOUNTS IN EACH CASE.
replacing sensitive personal information with fake data is called
Answers
Replacing sensitive personal information with fake data is called data masking.
Data masking is a technique used to protect personal information by replacing sensitive data with fictitious data. This method is used to prevent data breaches and to protect the privacy of individuals.
Sensitive personal information includes details such as social security numbers, credit card information, health records, and any other information that can be used to identify an individual. Data masking involves scrambling the original data and replacing it with a different set of data that cannot be traced back to the original information.
Data masking is a crucial tool for companies and organizations that handle personal information. It ensures that sensitive data is not accessible to unauthorized individuals and helps protect individuals from identity theft and fraud. By masking personal information, companies can comply with privacy regulations and prevent costly data breaches.
In summary, data masking is the process of replacing sensitive personal information with fake data to protect the privacy and security of individuals. It is an essential tool for data protection and is widely used by organizations and companies around the world.
To learn more about the data:
https://brainly.com/question/29117029
#SPJ11
A group of statisticians at a local college has asked you to create a set of functions that compute the median and mode of a set of numbers, as defined in Section 5.4. Define these functions in a module named stats.py. Also include a function named mean, which computes the average of a set of numbers. Each function should expect a list of numbers as an argument and return a single number. Each function should return 0 if the list is empty. Include a main function that tests the three statistical functions. Ask users to enter the list of numbers, and then choose which function to apply to those numbers. After the single number is returned from the correct function, display to the user the list of numbers, the function selected and the answer in a format that is easy to understand.
Answers
Answer:
from functools import reduce
def mean(mylist):
score = reduce(lambda x,y: x + y, mylist)/ len(mylist)
return score
def median(mylist):
sorted(mylist)
list_len = len(mylist) % 2
i = round(len(mylist)/2)
x = len(mylist)//2
if list_len == 0:
median = (mylist[x] + mylist[x+1]) / 2
else:
median = mylist[i]
return median
def mode(mylist):
unique = set(mylist)
unique = list(unique)
collector = [mylist.count(key) for key in unique]
maxi = max(collector)
loc = collector.index(maxi)
return unique[loc]
def main():
scores = input( 'Enter list of numbers: ').split(",")
scores = [int(score) for score in scores]
operation = input('Enter operation: ')
operator = ['mean', 'median', 'mode']
for x in iter(list, 0):
if operation in operator:
break
print("Invalid operation: ")
operation = input('Enter operation')
index_loc = operator.index(operation)
if index_loc == 0:
return mean(scores)
elif index_loc == 1:
return median(scores)
#return np.median(scores) can be used of the defined function
elif index_loc == 2:
#return stats.mode(scores)[0] can be used of the defined function
return mode(scores)
print( main( ) )
Explanation:
The main python function calls conditionally three statistical functions namely mean, median and mode. It prompts for user input for a list of integer numbers and a function name name to return the corresponding result.
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
Which definition of intelligence is based on the Turing test?
Answers
Answer:
The Turing Test is a deceptively simple method of determining whether a machine can demonstrate human intelligence
Explanation:
Answer:
The correct answer would be Acting Humanly
Explanation:
My proof is in this test I took. (See The Picture Below)

What does disabled clipboard mean on Proctorio?
Answers
Proctorio disables the computer's clipboard by disabling its system's ability to paste and copy information. Copying and pasting text from or into the exam window as it is open is not permitted.
Describe a computer.A computer is indeed a piece of electrical equipment used to manipulate data or information. It will have the power to store, acquire, and process data. You probably are aware of the reality that you are able use a computer to play games, send emails, browse the web, and compose papers.
What word best sums up a computer?A computer is an item or equipment that follows instructions from a hardware or software program to carry out tasks, computations, and activities.
To know more about computer's visit:
https://brainly.com/question/20414679
#SPJ1
In Proctorio, 'disabled clipboard' means that the copy and paste feature has been turned off to maintain the integrity of exam processes. This restricts cheating by stopping students from pasting in outside information or sharing the test questions or answers.
Explanation:In the context of Proctorio, a tool used predominantly for online proctoring during exams, 'disabled clipboard' means that the copy-paste feature has been disabled. This is often done to maintain the integrity of the examination process, preventing students from copying and pasting information from outside sources into the test. It also restricts the capacity for sharing test questions or answers inappropriately.
It's important to note that these set measures can vary depending on the settings chosen by the instructor or institution administering the exam. Some may enable the clipboard, some may limit its usage, and others might disable it entirely.
Learn more about Disabled Clipboard here:https://brainly.com/question/32111024