state 10 differences between video conferencing and teleconferencing
Answers
Teleconferencing is voice-only or audio and video communication, while video conferencing supports the conference by providing both video and voice, so you can fully see the person when you are listening to the communicator,
Teleconferencing is capable of transmitting the data during the conference, either using traditional PBX systems or VoIP, while video conferencing offers VoIP services. The formal requires less bandwidth, while the latter is highly dependent on network bandwidth.
Related Questions
What is the output of the following snippet?
my_list =
[[0, 1, 2, 3] for i in range (2) ]
print (my_list [2] [0])
Answers
Answer:
Explanation is being shown in the file that takes you to the link
How do I make the text and heading different colors?
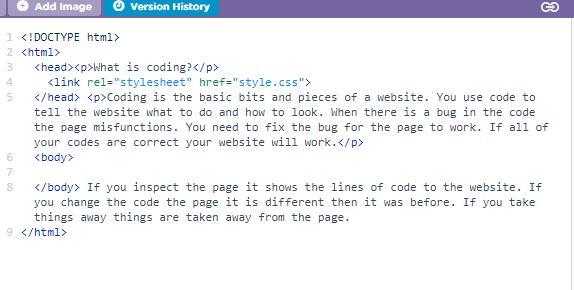
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
Nathan notices his computer System is slowing down when he tries to copy documents to it he also gets a prompt I warned him that the system is running low on storage space which hardware device should he consider upgrading in order to increase the system storage space?
Answers
Answer:Hard drive or Solid State drive
Explanation:
I need help i am suppose to write a multimedia pressintation and i dont know what to do
Here is a pick you get 30 points and a brainliest
Answers
Creating a multimedia presentation can be an exciting and effective way to convey information. Here are some steps and suggestions to help you get started:
Determine ind compelling.Outline your content: Create an outline or structure for your presentation. Decide on the main points you want to cover and the order in which you will present them.Collect and organize your materials: Gather relevant information, images, videos, audio clips, and any other multimedia elements that support your presentation. Make sure to keep them organized for easy access.Choose a multimedia presentation software: your slides or multimedia components based on your outline. Keep your visuals engaging, use legible fonts, and limit the amount of text on each slide. Utilize images, charts, videos, and other media to enhance your content.Add transitions and animations: Use transitions and animations to create smooth transitions between slides or multimedia elements. Be mindful not to overuse them and keep the focus on your content.Practice and rehearse: Rehearse your presentation to become comfortable with the flow and timing. Pay attention to your speaking pace and practice delivering your content confidently.Seek feedback: Share your presentation with a friend, family member, or teacher to get feedback on your content, design, and delivery. Incorporate their suggestions to improve your presentation further.
learn more about multimedia here :
https://brainly.com/question/29426867
#SPJ11
.............. 1010111 needs to be transferred w.ith odd parity and the answer is
A. 01010111
B.11010111
C.10101110
D.10101111
Answers
Answer:
A. 01010111
Explanation:
This is because in odd parity, the number on the far left (the 8th number) would always be a 0
Which variable name is the best to hold the area of a rectangle?
1A
area
AREA
a
Answers
A variable name that is the best to hold the area of a rectangle is known as the area. Thus, the correct option for this question is D.
What is the formula for calculating the area of the rectangle?The formula for calculating the area of the rectangle is as follows:
Area of the rectangle = Length × Width.
It is only calculated when both the parameters are known in a numerical.
The Area is considered the variable name through which the area of the rectangle best holds in any numerical problem. This is because the area of the rectangle may be changed when the length and breadth parameters have deviated very minutely.
Therefore, a variable name that is the best to hold the area of a rectangle is known as the area. Thus, the correct option for this question is D.
Learn more about the Area of the rectangle:
brainly.com/question/25292087
#SPJ1
In the game Badland, how do you get to the next level?
A.
If you get close enough to the exit pipe, it sucks you up and spits you out in the next level.
B.
If you shoot enough enemies, you automatically advance to the next level.
C.
If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
D.
If you answer enough puzzles correctly, you advance to the next level.
Answers
In the game Badland, the way a person get to the next level is option C: If you reach the end of the maze, you hear the sound of a bell and are taken to the next level.
What is the story of BADLAND game?
The story occurs throughout the span of two distinct days, at various times during each day's dawn, noon, dusk, and night. Giant egg-shaped robots start to emerge from the water and background and take over the forest as your character is soaring through this already quite scary environment.
Over 30 million people have played the side-scrolling action-adventure game BADLAND, which has won numerous awards. The physics-based gameplay in BADLAND has been hailed for being novel, as have the game's cunningly inventive stages and breathtakingly moody sounds and visuals.
Therefore, in playing this game, the player's controller in Badland is a mobile device's touchscreen. The player's Clone will be raised aloft and briefly become airborne by tapping anywhere on the screen.ult for In the game Badland, the way a person get to the next level.
Learn more about game from
https://brainly.com/question/908343
#SPJ1
The creation of OSHA provided this important right to workers:
a) The right to equal employment opportunities. b) The right to privacy. c) The right to pension benefits. d) The right to a safe and healthful workplace.
Answers
The creation of OSHA provided this important right to workers: d) The right to a safe and healthful workplace.
What is OSHA?OSHA is simply an abbreviation for occupational safety and health administration that was created under the Occupational Safety and Health Act, so as to develop work-safety standards for workers and providing precautionary measures against all workplace hazards.
Generally, OSHA is an agency of the federal government which is saddled with the following responsibilities of developing work-safety standards for employees and providing precautionary measures against all workplace hazards.
In this context, we can infer and logically deduce that the creation of OSHA provided this important right to workers the right to a safe and healthful workplace.
Read more on OSHA here: brainly.com/question/17199752
#SPJ1
What occurs when distributed database experiences a network error and nodes cannot communicate?
Consistent records
Network partition
Inconsistent transactions
A developer wishes to link to a database with a utility created in C. Which MySQL component does the developer use for the link?
Workbench
Command-line
API
Data warehouses should be refreshed periodically. To start all data should be …….
Extracted to a temporary database.
Restructured for optimization.
Integrated the data into a uniform structure.
Answers
When a distributed database experiences a network error and nodes cannot communicate, a network partition occurs. To link to a database with a utility created in C, the developer should use the MySQL API. To refresh a data warehouse, all data should be extracted to a temporary database.
A network partition disrupts communication between nodes, leading to potential inconsistencies in the distributed database. The correct option is network partition. MySQL API provides a way to connect and interact with the database using C programming. The correct option is API.
To refresh a data warehouse, data is first extracted to a temporary database, then transformed and loaded into the warehouse to ensure consistency and optimization. The correct option is extracted to a temporary database.
Learn more about MySQL visit:
https://brainly.com/question/32267222
#SPJ11
Which situations make use of interactive multimedia and which do not? Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister. Roy is going through a tutorial on his laptop that explains a do-it-yourself project. Jaden is listening to a presentation on early music in his class. Fred is answering an online quiz that requires him to select correct answers. Linear Multimedia Kristen is watching an educational film on her tablet. Non-linear Multimedia
Answers
The situation that make use of interactive multimedia is Roy is going through a tutorial on his laptop that explains a do-it-yourself project, and that do not is Amelia is exploring a shopping website looking for clothes or accessories she could give to her sister.
What is an interactive multimedia?Interactive multimedia is a type of interaction in which the user can operate, control, and change the text, image, and picture, and function in a phone or computer.
Thus, the correct options are A and B.
Learn more about interactive multimedia
https://brainly.com/question/26090715
#SPJ1
How do u set up a Wi-Fi network on Android
Answers
Answer:
These are some way I know

Kelsan Informatics has its client computers connected to a router through which the clients can access the organization's servers in the DMZ. The DMZ is connected to a NAT router that is connected to the Internet. In addition to providing access to the Internet, the NAT router also offers additional capabilities, such as traffic throttling, intrusion prevention, and malware filtering.
What is the term for this type of NAT router?
a. Next Generation Firewall
b. Last mile technology
c. Demarcation point
d. Point-to-Point Protocol over Ethernet (PPPoE)
Answers
Next Generation Firewall is the term for this type of NAT router. Hence option a is correct.
What is NAT ?NAT stand for network address translation. It is defined as a method that makes it possible for one distinct IP address to represent a whole network of machines. Most individuals do not use Network Address Translation (NAT), a sophisticated networking configuration.
Before uploading the data, there is a means to map several local private addresses to a public one. Both most household routers and organizations that need many devices to share a single IP address use NAT.
Thus, next generation firewall is the term for this type of NAT router. Hence option a is correct.
To learn more about NAT, refer to the link below:
https://brainly.com/question/28340750
#SPJ1
Where do high tides occur? (Select two.) WILLLL GIVVEEE BBRRAANNLLEESSTTTM PLSS AASSAAPP
only at the South Pole
on the side of Earth opposite the moon
on the side of the Earth facing the moon
only at the North Pole
at both the North and South Poles
Answers
Answer:
Maybe both?
Explanation:
High tides and low tides are caused by the Moon. The Moon's gravitational pull generates something called the tidal force. The tidal force causes Earth—and its water—to bulge out on the side closest to the Moon and the side farthest from the Moon. These bulges of water are high tides. (hope this helps)
Answer:
its the last one, it happens on the side of the earth facing the moon and also the opposite side
Q. Differentiate between language and package.
Answers
Answer:
Language is made up of syntactic norms and semantics since it is a resource which we use to develop computer programs and solve problems. The package, on the other hand, is a type of folder since it is a collections of linked and pre-defined classes. Furthermore, a package is designed for a certain set of tasks which has a limited computational capability. So, language has a set of rules and syntax for creating data encapsulation, whereas package has a chain of conditions for building menu action programs and applications.
In an online shopping application, the primary case type PurchaseOrder has two child case types: Payment and Packaging. In processing PurchaseOrder case PO-11, Payment case Pay-37 and Packaging case Pac-56 are created. Which statement about the processing of PO-11, Pay-37, and Pac-56 is correct?
A. PO-11 has to be resolved before either Pay-37 and Pac-56 is resolved.
B. Pac-56 has to be resolved before Pay-37 is resolved.
C. Both Pay-37 and Pac-56 have to be resolved before PO-11 can be resolved.
D. PO-11 can be resolved when either Pay-37 or Pac-56 is resolved.
Answers
Answer:
The answer is "Option C".
Explanation:
The principal instance type PurchaseOrder has two types of instance children in an online purchasing application: Pay and Packing. Pay case Pay-37 and packing instance Pac-56 are designed to Sales Orders case PO-11 execution. All statements regarding PO-11, Pay-37, and Pac-56 should be settled before PO-11 may be addressed. Both Pay-37 and Pac-56.
How many seconds long is the longest sound in the world?
Answers
How do you reset a g.mail password?
Answers
Answer:
put: forgot password to reset it
Answer:
Change your pass word
Open your Go ogle Account. You might need to sign in.
Under "Security," select Signing in to G oo gle.
Choose Password. You might need to sign in again.
Enter your new password, then select Change Password.
Create a program that allows the user to enter an unknown number of sales amounts for each of three car dealerships: Dealership 1, Dealership 2, and Dealership 3. The program should calculate the total sales. Display the total sales with a dollar sign and two decimal places. a. Create an IPO chart for the problem, and then desk-check the algorithm using 23000 and 15000 as the sales amounts for Dealership 1; 12000, 16000, 34000, and 10000 for Dealership 2; and 64000, 12000, and 70000 for Dealership 3. b. List the input, processing, and output items, as well as the algorithm, in a chart similar to the one shown earlier in Figure 8-16. Then code the algorithm into a program. c. Desk-check the program using the same data used to desk-check the algorithm. d. If necessary, create a new project named Intermediate19 Project, and save it in the Cpp8\Chap08 folder. Enter your C++ instructions into a source file named Intermediate19.cpp. Also enter appropriate comments and any additional instructions required by the compiler. e. Save and then run the program. Test the program using the same data used to desk-check the program.
Answers
As an AI language model, I cannot create or run programs. However, I can provide you with the algorithm and the pseudocode for the program you described:
Input:
Sales amounts for each of the three car dealerships
Processing:
Initialize total sales to 0
Loop through each dealership
Loop through each sales amount for the current dealership
Add the current sales amount to the total sales
Display the total sales with a dollar sign and two decimal places
Output:
Total sales
Pseudocode:
totalSales = 0
FOR each dealership
FOR each salesAmount in dealership
totalSales += salesAmount
END FOR
END FOR
DISPLAY "$" + totalSales with two decimal places
To desk-check the algorithm, we can use the given data:
Dealership 1: 23000, 15000
Dealership 2: 12000, 16000, 34000, 10000
Dealership 3: 64000, 12000, 70000
totalSales = 0
FOR each dealership
FOR each salesAmount in dealership
totalSales += salesAmount
END FOR
END FOR
DISPLAY "$" + totalSales with two decimal places
After running the algorithm with the given data, we should get a total sales of $230000.00.
To code the algorithm into a C++ program, we can use the following code:
#include <iostream>
#include <iomanip>
using namespace std;
int main() {
// Declare variables
double totalSales = 0;
double salesAmount;
char continueInput;
// Loop through each dealership
for (int dealership = 1; dealership <= 3; dealership++) {
cout << "Enter sales amounts for dealership " << dealership << ":\n";
// Loop through each sales amount for the current dealership
do {
cin >> salesAmount;
totalSales += salesAmount;
cout << "Enter another sales amount? (Y/N): ";
cin >> continueInput;
} while (toupper(continueInput) == 'Y');
}
// Display the total sales with a dollar sign and two decimal places
cout << fixed << setprecision(2);
cout << "Total sales: $" << totalSales << endl;
return 0;
}
To desk-check the program using the same data, we can run the program and input the following values when prompted:
Dealership 1: 23000, 15000
Dealership 2: 12000, 16000, 34000, 10000
Dealership 3: 64000, 12000, 70000
After running the program with the given data, we should get a total sales of $230000.00 displayed on the screen.
Learn more about algorithm here:
https://brainly.com/question/22984934
#SPJ11
you are the network administrator for a large organization. you are in charge of developing a plan to install 200 windows 10 computers in your company's data center. you decide to use wds. you are using a windows server 2012 r2 domain and have verified that your network meets the requirements for using wds. what command-line utility should you use to configure the wds server?
Answers
You should use the wdsutil command-line utility to configure the Windows Deployment Services (WDS).
Configuring the WDS serverAs the network administrator for a large organization, you are in charge of developing a plan to install 200 Windows 10 computers in your company's data center. You decide to use Windows Deployment Services (WDS) to automate the installation process. You are using a Windows Server 2012 R2 domain and have verified that your network meets the requirements for using WDS.
To configure the WDS server, you will use the wdsutil command-line utility. This utility will allow you to manage the WDS server and images, as well as perform other tasks such as starting and stopping the server.
Learn more about Windows at: https://brainly.com/question/14531631
#SPJ4
Social media marketers need the ability to do what?
Code in JavaScript
Collaborate across teams
Communicate with customers
Make a website useful
Answers
After making changes to a portal, what actions are required for the user to see the changes?A. Clear the browser's cache and cookiesB. Restart the server hosting the portalC. Log out of the portal and log back inD. Reload the portal page or refresh the browserE. Reboot the user's computer
Answers
Reload the portal page or refresh the browser. This will update the browser's cache with the latest changes made to the portal. Clearing the browser's cache and cookies may also be necessary if the changes are not visible after refreshing the page. Restarting the server or rebooting the user's computer are not necessary for the changes to be seen.
Saving the changes: If the portal has a "Save" or "Apply" button, the user may need to click on it to save the changes and make them visible to others.
Refreshing the page: The user may need to manually refresh the page in their web browser to reload the portal and see the updated content.
Clearing cache: If the portal uses caching mechanisms, the user may need to clear their browser's cache to ensure that the changes are retrieved from the server and not from the local cache.
Logging out and logging back in: In some cases, changes to the portal may only be visible after the user logs out of their account and then logs back in.
Waiting for server synchronization: If the portal is hosted on a server, the changes may need to be synchronized across multiple servers or databases, which may take some time before they become visible to all users.
It's important to note that the specific actions required for the user to see changes in a portal may vary depending on the portal's design and implementation, and it's always a good practice to follow any instructions or guidelines provided by the portal's administrators or developers.
learn more about Browser's Cache here:
https://brainly.com/question/17898582
#SPJ11
In raft survival ocean nomad I was traveling and now I can’t enter the island or go back home to my raft please help me.
Answers
Answer:
Get an island scanner
Explanation:
This may help
the web server software accepts ____ requests from web browsers connected to the internet.
Answers
The web server software accepts HTTP requests from web browsers connected to the internet.
HTTP (Hypertext Transfer Protocol) is the primary protocol that is used to transfer data from a web server to a web browser. When a user requests a web page by typing the URL into their browser or clicking a link, the web browser sends an HTTP request to the server, which then responds with an HTTP response. This exchange allows the user to receive and view the requested web page. Other protocols like HTTPS, FTP, and SMTP are also used for specific purposes in web communications, but HTTP is the most common protocol used to transfer data between web servers and browsers.
You can learn more about HTTP at
https://brainly.com/question/30984161
#SPJ11
a query sent to the ncic article file will search which of the ncic files
Answers
A query sent to the NCIC Article File will search the NCIC Article File itself.
The National Crime Information Center (NCIC) Article File is a database containing records of stolen articles, such as firearms, vehicles, boats, and other valuable items.
When a query is sent to this file, it searches within the NCIC Article File to locate any matching records. This allows law enforcement agencies to identify and recover stolen property and helps in the investigation of related crimes.
The NCIC database contains several files that can be searched, including the Article File. The Article File contains information about stolen articles, such as license plates, boats, firearms, and other valuable items. When a query is sent to the Article File, it searches for information about the requested stolen articles and returns any matching records to the requesting agency.
To learn more about National Crime Information Center (NCIC) visit : https://brainly.com/question/29346792
#SPJ11
Adjust the code you wrote for the last problem to allow for sponsored Olympic events. Add an amount of prize money for Olympians who won an event as a sponsored athlete.
The
Get_Winnings(m, s)
function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Here's my answer for question 1 please adjust it thanks!
def Get_Winnings(m):
if m == "1": return 75000
elif m == "2":
return 150000
elif m == "3":
return 225000
elif m == "4":
return 300000
elif m == "5":
return 375000
else:
return "Invalid"
MAIN
medals = input("Enter Gold Medals Won: ")
num = Get_Winnings(medals)
print("Your prize money is: " + str(num))
Answers
Answer:def Get_Winnings(m):
if m == "1": return 75000
elif m == "2":
return 150000
elif m == "3":
return 225000
elif m == "4":
return 300000
elif m == "5":
return 375000
else:
return "Invalid"
MAIN
medals = input("Enter Gold Medals Won: ")
num = Get_Winnings(medals)
print("Your prize money is: " + str(num))
exp: looking through this this anwser seemes without flaws and i dont follow
if you can provide what you are not understanding ican an help
what would be a reason for using a workstation rather than a personal computer? when you need to share resources when you need more powerful computational abilities when you need to serve applications and data to client computers when you need to access a network when you need to connect to a cloud computing platform
Answers
A reason for using a workstation rather than a personal computer is when you need more powerful computational abilities.
What is the workstation about?Workstations are typically designed with higher-end hardware components, such as faster processors, larger memory capacity, and more powerful graphics cards, than personal computers. This makes them better suited for complex tasks that require significant processing power, such as 3D modeling, video editing, scientific simulations, or software development.
Therefore, While personal computers can also be used for these tasks, they may not be able to handle them as efficiently or effectively as workstations. Additionally, workstations are often optimized for specific tasks and can be customized with specialized hardware and software to meet the specific needs of the user or the organization.
Learn more about workstation from
https://brainly.com/question/30206368
#SPJ1
What is the value of the variable result after these lines of code are executed? >>> a = 6 >>> b = 2 >>> c = 3 >>> result = a * b - a / c The value of the variable is .
Answers
The value of the variable result is 10.0
Following are the C++ language code that calculates the given expression value and prints its result value:
Program:#include <iostream>//header file
using namespace std;
int main()//main method
{
int a,b,c, result;//defining the integer variable
a = 6;//initilizing value 6 in a variable
b = 2;//initilizing value 2 in b variable
c = 3;//initilizing value 3 in c variable
result = a * b - a / c; //using the result variable that holds and calculate the result value
cout<<result;//print result value
return 0;
}
Output:
please find the attached file.
Program Explanation:
Defining the header file.Defining the "main method", inside the method four integer variable "a,b,c, and result" is declared.In the next line "a,b, and c" are declared initialized with the value that is "6, 2, and 3". Using the "result" variable that holds and calculates the result value, and prints its result value.
Find out more about the method here:
brainly.com/question/18881441

Which command can be used to modify the TCP/IP routing table? O. nslookup O tracertO routeO ipconfig O netstat
Answers
The "route" command can be used to modify the TCP/IP routing table.
The "route" command allows the user to view and modify the routing table, which is used to determine the path that network data takes as it travels from one device to another.
The route command can be used to add, delete, or change entries in the routing table, as well as to display the current contents of the table. For example, the "route add" command can be used to add a new entry to the routing table, while the "route delete" command can be used to remove an existing entry. The command can also be used to modify the metric value of a route which is used to determine the best path to a destination.
Learn more about command, here https://brainly.com/question/27742993
#SPJ4
The route (third O option) is the command can be use to modify the TCP/IP routing table.
What is TCP?TCP stand for Transmission Control Protocol defines as a standard which defines how to set up and preserve a network conversation by which applications could trade data. TCP runs with the Internet Protocol (IP), that defines how computers addressed packets of data to one another. Because of TCP works cant separate from IP, they also called as TCP/IP. There are four layers of the TCP/IP Model, they are Internet Layer, Host to Host Layer, Network Access Layer, and Application Layer. This layers are using one of the this 7 protocol: DHCP, FTP, HTTP, SMTP, Telnet, SNMP and SMPP.
Learn more about TCP here
https://brainly.com/question/17387945
#SPJ4
What is a recent innovation in edge computing enhanced by 5G?.
Answers
A recent innovation in edge computing enhanced by 5G is placing computing resources physically inside the network infrastructure.
5G is the fifth generation of mobile communications operating on the basis of telecommunication standards, following the existing 4G.
5G technologies must provide higher bandwidth than 4G technologies, which will ensure greater availability of mobile broadband, as well as the use of device-to-device modes (direct connection between subscribers).
It also allows ultra-reliable large-scale systems communication between devices, as well as less latency, higher speed, and less battery power consumption than 4G equipment.
Learn more about computers in https://brainly.com/question/24836371
address on the internet
Answers
A device on the internet or a local network can be identified by its IP address, which is a special address.The rules defining the format of data delivered over the internet or a local network are known as "Internet Protocol," or IP.
Which two kinds of Internet addresses are there?
picture of an address found online Internet Protocol (IP) addresses are used to connect your network with the Internet.IP addresses come in two varieties: static and dynamic.In order to help you choose between static and dynamic IP addresses, this article compares their main characteristics. Using one of the several IP lookup programs that are readily available online is the quickest approach to start learning someone's IP address.There are tools available to enter an IP address and search for its free public registry results on websites A network address and a host (or local) address are the components of an internet address.With this two-part address, a sender can identify both the network and a particular host on the network.Each network that connects to another Internet network receives a distinct, official network address. While IP addresses do identify your whereabouts, they do not provide as much detail as a home address.Additionally, IP addresses will never disclose your name, phone number, or any other specific personal details. "Internet protocol" is referred to as IP.For any device connected to your network, your router IP serves as an identification number.For the router to recognize it and send data packets to it, a device (such as a computer or smartphone) needs to have an IP address.Your internet is what it is because of the data packets.To learn more about IP address refer
https://brainly.com/question/21864346
#SPJ1