Read-only memory chips are used to
A. record high scores and later, "save slots" for longer games
B. Translate input from players into visual output
C. Store data that cannot be modified
D. Secure game code so that it can't be copied or pirated
pls help ill mark branliest!!!
Answers
Answer:
C
Explanation:
Think of memory, you can remeber things. A memory chip is meant to "remember" things!
Related Questions
A data analyst is working with the penguins data. The variable species includes three penguin species: Adelie, Chinstrap, and Gentoo. The analyst wants to create a data frame that only includes the Adelie species. The analyst receives an error message when they run the following code:
penguins %>%
filter(species <- "Adelie")
How can the analyst change the second line of code to correct the error?
# filter(species == "Adelie")
// The code chunk is filter(species == "Adelie"). The filter function is used to specify the part of the data to be viewed. Two equal signs in an argument mean "exactly equal to." Using this operator instead of the assignment operator <- calls only the data about Adelie penguins to the dataset.
Answers
By correcting the code to use the equality comparison operator (==), the analyst can create a data frame that only includes the Adelie species from the penguins data.
The analyst can change the second line of code to correct the error by using the equality comparison operator (==) instead of the assignment operator (<-). The correct code would be:
```R
penguins %>% filter(species == "Adelie")
```
In the original code, the assignment operator (<-) is being used instead of the equality comparison operator (==). The assignment operator is used to assign a value to a variable, while the equality comparison operator is used to check if two values are equal. By using the equality comparison operator (==), the analyst can compare the values in the "species" column with the string "Adelie" and filter the data frame accordingly.
By correcting the code to use the equality comparison operator (==), the analyst can create a data frame that only includes the Adelie species from the penguins data. This will help the analyst focus on analyzing and working with the specific subset of data they require.
To know more about comparison operator follow the link:
https://brainly.com/question/29557207
#SPJ11
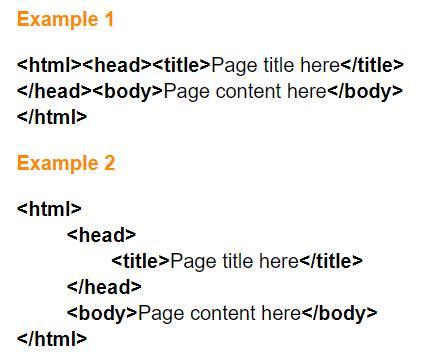
Choose all items that are true about the two example of HTML shown on the right.
Example 1 will display differently than example 2 in a web browser.
They are styled differently, but will look the same in a web browser.
Example 2 is easier to analyze and repair.
The styling in example 2 is required by modern web browsers.
Answers
Answer:
2
Explanation:
Answer:
B and C
Explanation:
what will be the output for;
for i in range(1,6):
if i==3:
print('hello')
break
else:
print(i)
print('done')
Answers
The output for; for i in range(1,6): if i==3: print('hello') break else: print(i) print('done') the output for the given Python program is 001020340.
What is range () in Python?
The python range() function creates a collection of numbers on the fly, like 0, 1, 2, 3, 4. This is very useful, since the numbers can be used to index into collections such as string. The range() function can be called in a few different way.
The given program is as:i =0while i < 5print(i)i +=1if i==3 :breakelse:print(0)It will give the following as result 001020340Hence, the answer is 001020340.
Read more bout the python :
https://brainly.com/question/26497128
#SPJ1
why do many experts recommand longer time horizonal if you are doing high risk investment
Answers
Answer:In general, the longer your time horizon, the better you can handle fluctuations in value and take more risk in order to reap greater rewards.
Explanation:
how do I get the bot token for discord? (scripting etc)
Answers
Answer:
1 Open your App on the Developer Portal.
2 Go to the Bot settings from the side menu.
3 Press the Reset Token button located under the Build-a-Bot section.
4 A pop-up window will show up asking you to confirm.
5 Your new token will now show up under the Build-A-Bot section. Make sure to copy and paste it into your code right away. Be sure to follow good token management security practices!
Several applications might be installed on a computer but it really only needs one ____________________ to function.
Answers
Several applications might be installed on a computer but it really only needs one operating system (OS) to function. An operating system is software that manages computer hardware resources and provides common services for computer programs.
The OS is responsible for managing the computer's memory, processing power, input/output devices, and network connectivity.
Without an operating system, it would be impossible for any application to function on a computer. The OS provides a layer of abstraction between the hardware and software, allowing applications to interact with the hardware resources in a standardized and controlled manner.
Additionally, the OS provides a user interface that enables users to interact with the computer and its applications. The OS manages files and directories on the computer, providing a file system that allows users to store and access their data.
In summary, the operating system is the backbone of any computer system, providing the necessary services for other applications to run smoothly and interact with the computer's hardware resources.
Learn more about applications here:
https://brainly.com/question/31164894
#SPJ11
given two numbers x and y. write a pseudo code to determine the difference between x and y. if x-y is negative, compute r=x+y; if x-y is zero, compute r=2x+2y; and if x-y is positive, compute r=x*y. print out the values of x, y and r
Answers
The pseudo code below determines the difference between two numbers, x and y, and computes the value of r based on the result. It prints out the values of x, y, and r accordingly, considering whether the difference x-y is negative, zero, or positive.
Input x, y
Compute diff = x - y
If diff < 0, then
r = x + y
Else if diff = 0, then
r = 2x + 2y
Else,
r = x * y
Print x, y, r
The pseudo code begins by taking the input of two numbers, x and y. It then calculates the difference between x and y and stores it in the variable 'diff.' The code proceeds with conditional statements to determine the value of r based on the value of 'diff.'
If the difference (diff) is found to be less than zero, it implies that x-y is negative. In this case, the code executes the statement to compute r as the sum of x and y. If the difference (diff) is zero, it means that x-y equals zero. The code then calculates r as twice the sum of x and y. Finally, if the difference (diff) is positive, the code computes r as the product of x and y. After determining the appropriate value for r based on the conditions, the code prints out the values of x, y, and r.
Learn more about input here: https://brainly.com/question/21512822
#SPJ11
Approximately how many tweets are posted on Twitter each day? 500 500 thousand 500 million 500 billion
Answers
Answer:
around 500 million
Explanation:
which of the following should be the primary goal of a lenovo service technician?
Answers
The primary goal of a Lenovo service technician is to provide effective and efficient technical support and solutions to Lenovo customers. This includes diagnosing and resolving hardware or software issues, ensuring customer satisfaction, and maintaining the functionality and performance of Lenovo products.
The primary goal of a Lenovo service technician is to deliver exceptional customer service and technical support. They should strive to provide effective solutions to any hardware or software problems faced by Lenovo customers. This involves diagnosing the issues accurately, troubleshooting the components, and implementing appropriate repairs or replacements.
A service technician should prioritize customer satisfaction by addressing customer concerns promptly and professionally. They should possess strong communication skills to clearly explain technical concepts and provide guidance to customers in resolving their problems.
Furthermore, a Lenovo service technician should focus on maintaining the functionality and performance of Lenovo products. This includes performing regular maintenance tasks, such as software updates, hardware inspections, and system optimizations, to ensure optimal performance and reliability.
Overall, the primary goal of a Lenovo service technician is to deliver top-notch technical support, resolve customer issues efficiently, and ensure customer satisfaction while upholding the functionality and performance of Lenovo products.
Learn more about software here: https://brainly.com/question/985406
#SPJ11
name any two web browsers?
Answers
Explanation:
Chrome
Opera
That's all i can get for u
Answer:
Microsoft Edge and Internet Explorer
Explanation:
Adjust the code you wrote for the last problem to allow for sponsored Olympic events. Add an amount of prize money for Olympians who won an event as a sponsored athlete.
Sample Run 1
Enter Gold Medals Won: 1
For how many dollars was your event sponsored?: 5000
Your prize money is: 80000
Sample Run 2
Enter Gold Medals Won: 2
For how many dollars was your event sponsored?: 25000
Your prize money is: 175000
Sample Run 3
Enter Gold Medals Won: 3
For how many dollars was your event sponsored?: 15000
Your prize money is: 240000
Sample Run 4
Enter Gold Medals Won: 4
For how many dollars was your event sponsored?: 1
Your prize money is: 300001
The Get_Winnings(m, s) function should take two parameters — a string for the number of gold medals and an integer for the sponsored dollar amount. It will return either an integer for the money won or a string Invalid, if the amount is invalid. Olympians can win more than one medal per day.
Answers
The code wrote for the last problem to allow for sponsored Olympic events is given below:
What is code?Code is a set of instructions, written using a programming language, that tell a computer what tasks to perform. It is a set of commands and instructions that allow a computer to perform specific tasks. Code can be used to create software applications, websites, games, and even mobile applications.
def Get_Winnings(m, s):
"""
Calculate the prize money for an Olympic event sponsored by a given dollar amount.
Parameters:
m (string): The number of gold medals won.
s (int): The amount of money sponsored for the event.
Returns:
int: The prize money won by the athlete.
string: "Invalid" if the sponsored amount is invalid.
"""
if s <= 0:
return "Invalid"
else:
medal_value = s * 8 # Each gold medal is worth 8x the sponsored amount
winnings = int(m) * medal_value
return winnings
To learn more about code
https://brainly.com/question/29330362
#SPJ1
What 5 factors determine the seriousness of a gunshot wound?
Answers
Bullet size, velocity, form, spin, distance from muzzle to target, and tissue type are just a few of the many factors that can cause gunshot wound.
The four main components of extremities are bones, vessels, nerves, and soft tissues. As a result, gunshot wound can result in massive bleeding, fractures, loss of nerve function, and soft tissue damage. The Mangled Extremity Severity Score (MESS) is used to categorize injury severity and assesses age, shock, limb ischemia, and the severity of skeletal and/or soft tissue injuries. [Management options include everything from minor wound care to amputation of a limb, depending on the severity of the injury.
The most significant factors in managing extremities injuries are vital sign stability and vascular evaluation. Those with uncontrollable bleeding require rapid surgical surgery, same like other traumatic situations. Tourniquets or direct clamping of visible vessels may be used to temporarily decrease active bleeding if surgical intervention is not immediately available and direct pressure is ineffective at controlling bleeding. People who have obvious vascular damage require rapid surgical intervention as well. Active bleeding, expanding or pulsatile hematomas, bruits and thrills, absent distal pulses, and symptoms of extremities ischemia are examples of hard signs.
To know more about wound:
https://brainly.com/question/13137853
#SPJ4
A company has enlisted the help of TDojo Consulting Co. to assist them in designing an AWS disaster recovery solution for their on-premises bare metal servers and SQL databases. The implementation has to be robust, fast, and simple to use. It should also prevent any type of data loss from occurring. The company would like to keep track of the status of the migration. Which tool should the team adopt for the DR solution
Answers
Answer: CloudEndure Disaster Recovery
Explanation:
The tool that the team should adopt for the DR solution is the CloudEndure Disaster Recovery.
CloudEndure Disaster Recovery is the tool that helps in minimizing downtime and data loss through the provision of a fast and a reliable recovery of the servers into the AWS Cloud.
It also allows the user recover the environment from an unexpected infrastructure, data corruption, or malicious attacks.
the organizing category of competent workplace communication is accomplished through discussion of schedules.true or false?
Answers
The statement "the organizing category of competent workplace communication is accomplished through discussion of schedules" is false.
The organizing category of competent workplace communication is achieved through efficient and effective planning and implementation of communication strategies. The main objective is to communicate and collaborate to achieve a common goal.
The organization of competent workplace communication has several categories which are vital for communication:
Structuring the messageUnderstanding the audienceSharing informationSetting objectives and desired outcomesEnsuring feedback and follow-upCommunication is not just about sharing information but also understanding the audience and their requirements
Learn more about workplace communication at
https://brainly.com/question/30348456
#SPJ11
Which of the following is used to regularly update an operating system? App Extension OS Patch
Answers
Answer:
patch
Explanation:
patch, by definition, is an update meant to fix security flaws.
app, extension, and os dont update
To regularly update an operating system is Patch.
What is Patch?Unlike different news apps, the Patch app allows users to subscribe to a personalized newsfeed from considerable cities and towns across the U.S. Following a smooth launch before this year, the app already includes over 233,000 downloads and averages a 4.5-star rating on both the Apple and Android app stores.In 2013, Patch was spun out of AOL as a joint experience with Hale Global. In January 2014, the latest owners reported layoffs of 400 journalists and other workers. In February 2016, The Wall Street Journal documented that Patch had 23 million users, which was advantageous and developing into new territories.The birth management patch may be a good alternative for someone who's sexually active, considers less than 198 pounds (90 kilograms), and discovers it hard to determine to take a pill every day or who keeps trouble ingesting pills. In some cases, medical or other circumstances make the use of the patch less practical or riskier.
To learn more about Patch, refer to:
https://brainly.com/question/20652851
#SPJ2
To _______ you worksheet, click (save button hard drive). The Save As dialog box opens.
Answers
To save your worksheet, click the "Save" button.
The "Save As" dialog box opens if it's the first time you're saving the worksheet, or if you want to save the worksheet with a different name or in a different location.
To save your worksheet in Microsoft Excel, you can use the "Save" button or the keyboard shortcut "Ctrl + S".
This will save the worksheet using its current file name and location. If this is the first time you are saving the worksheet, Excel will prompt you to choose a location and file name for the worksheet using the "Save As" dialog box.
The "Save As" dialog box allows you to choose a location on your computer or network to save the worksheet and also gives you the option to change the file name.
The worksheet, such as a CSV file, PDF, or XPS.
Excel will automatically add the appropriate file extension based on the file type you choose.
In addition to the "Save As" dialog box, Excel also provides other options for saving your worksheet.
To save a copy of the worksheet in a different location or with a different file name using the "Save a Copy" option.
You can also save the worksheet as a template or save it to your OneDrive or SharePoint account if you have those services available.
Saving your worksheet regularly is important to ensure that you do not lose any work in case of a power outage or system crash.
It is a good practice to save your worksheet frequently while you are working on it, especially if you are making significant changes or additions.
For similar questions on worksheet
https://brainly.com/question/30463017
#SPJ11
addition to the application software/systems you listed in question 2; fidelity needs an information technology (it) infrastructure.
Answers
In addition to the application software and systems listed in question 2, Fidelity needs an Information Technology (IT) infrastructure. IT infrastructure refers to the hardware, software, and network resources that support an organization's IT services and processes. This includes computer systems, servers, storage devices, networks, security devices, and more.
An IT infrastructure provides a foundation for an organization's IT services, ensuring that the hardware and software components work together efficiently.Fidelity needs an IT infrastructure to support its application software and systems. The infrastructure should provide a reliable and secure platform for the software and systems to run on, as well as provide a scalable solution that can grow as the company expands. The infrastructure should also be able to handle the high volume of data that Fidelity generates and stores. This will require a robust storage system and fast network connections between servers and storage devices.
Finally, Fidelity needs to ensure that its IT infrastructure is reliable and secure. This will require regular maintenance and updates to keep the infrastructure running smoothly and to patch any security vulnerabilities. Overall, a reliable and secure IT infrastructure is critical to Fidelity's success, and the company should invest in building a robust infrastructure that can support its growing business needs.
To know more about software visit:-
https://brainly.com/question/32393976
#SPJ11
Question # 4
Multiple Choice
Which of the following led to the development of the computer?
Enigma machine
morse code
sonar
telephone
Answers
Answer:
Explanatio Morse code
Please help, thanks! (simple question) I'm doing a project and need to ask two people what they think is the highest contributor to global warming. my phone is dead. What do you think is one of the greatest contributors to global warming? I have to make an app about the two things.
Answers
a(n) member function may only be called from a function that is a member of the same class.
Answers
The given statement "A member function may only be called from a function that is a member of the same class." is true.
This means that member functions are exclusive to the class they belong to, and they can only be accessed or executed by other functions within the same class. This ensures that the encapsulation and organization of the class are maintained, promoting good programming practices.
In object-oriented programming, a class is a blueprint for creating objects that encapsulate data and behaviors.
A class can contain member functions, which are functions that are defined inside the class and can access the class's data members.
When a member function is defined in a class, it is implicitly associated with the class, and can only be called from within the class or by an object of that class.
This is because a member function is designed to operate on the data members of the class, and needs access to them in order to perform its intended function.
Attempting to call a member function from outside the class, or from a function that is not a member of the same class, will result in a compilation error. This is because the function does not have access to the class's data members, and therefore cannot perform its intended function.
In order to call a member function, it must be called from within the same class or by an object of that class. This ensures that the function has access to the class's data members and can operate on them as intended.
This is because the function is designed to operate on the data members of the class, and needs access to them in order to perform its intended function.
The complete question is "True or false: A member function may only be called from a function that is a member of the same class"
Learn more about member function:
https://brainly.com/question/30009557
#SPJ11
In a ____ attack, an attacker monitors (or sniffs) packets from the network, modifies them, and inserts them back into the network. Group of answer choices sniff-in-the-middle man-in-the-middle server-in-the-middle zombie-in-the-middle
Answers
The attack you are referring to is called a "man-in-the-middle" attack. In this type of attack, an attacker intercepts and monitors packets that are being transmitted across a network.
They can then modify the packets or even insert their own packets into the network, allowing them to eavesdrop on communications or steal sensitive information. The attacker typically accomplishes this by placing themselves between two parties who are communicating with each other, such as between a user and a website or between two servers. They then intercept the traffic that is passing between them, allowing them to see and modify the data before it reaches its intended destination.
To protect against man-in-the-middle attacks, it is important to use encryption and other security measures to secure your network traffic. This can include using strong passwords, implementing firewalls, and using encryption protocols like SSL/TLS. Additionally, it is important to be aware of the risks and to monitor your network for suspicious activity, such as unusual traffic patterns or unexpected packet modifications.
In summary, man-in-the-middle attacks are a serious threat to network security, and it is important to take steps to protect against them. By using strong encryption, implementing security best practices, and staying vigilant for suspicious activity, you can help to keep your network safe from these types of attacks.
In a man-in-the-middle attack, an attacker monitors (or sniffs) packets from the network, modifies them, and inserts them back into the network.
Step-by-step explanation:
1. The attacker intercepts the communication between two parties (e.g., between a user and a website).
2. The attacker then monitors or "sniffs" the packets being exchanged between the two parties.
3. The attacker modifies the packets to manipulate the information or inject malicious content.
4. The modified packets are then inserted back into the network, with the two parties being unaware of the attacker's interference.
In this scenario, the man-in-the-middle attack involves intercepting, modifying, and retransmitting the packets to the original sender and recipient.
To know more about man-in-the-middle attacks visit:
https://brainly.com/question/13014110
#SPJ11
True or False: A ruler is used to measure units of length, inches, feet
and yards.
Answers
Answer:
True
Explanation:
Rulers are used to measure relatively small increments including centimeters, inches, feet and even yards (yardsticks).
discuss how the accessibility of television has changed over time
Answers
Answer:
Back then, television was seen as a rare and insane device. Now, in 2020, many people have access to television because it is not a new thing anymore and many people own it.
Explanation:
The development of online capabilities created the ________, an information- and communication-based electronic exchange environment occupied by sophisticated computer and telecommunication technologies and digital offerings.
Answers
It should be noted that development of online capabilities created the marketspace, where an information- and communication-based electronic exchange is been done.
The digital market place serves as the environment occupied by sophisticated computer and telecommunication technologies and digital offerings.
What is a marketspace?marketspace can be regarded as a place where buying and selling takes place and this could be digital in nature.
Learn more about marketspace at;
https://brainly.com/question/11408596
the taskbar contains what
Answers
Answer:The taskbar is anchored to the bottom of the screen by default, but can be moved to any screen side, and contains the Start button, buttons for pinned and running applications, and a system tray area that contains notification icons and a clock.
Explanation:
3. Describe how you would properly dispose of the following materials so that you do not damage the environment. Write on each topic below.
CRT monitors
Scanners
Batteries
Ink/Toner
Hard Drives
Answers
Alkaline and zinc-carbon batteries may be securely disposed of in your domestic garbage in the majority of areas.
What is disposing of?Disposing of is the process of completely destroying any material completely.
It's critical to adhere to established practices for electronic device disposal, in addition, to securely protecting sensitive information on electronic devices.
The most effective method of preventing outsiders from obtaining your information is to physically destroy a gadget.
Your computer disc and other gadgets can be destroyed using specialized services that can burn, melt, dissolve, or pulverize them.
These techniques of sanitization are used in authorized incineration facilities or outsourced metal destruction facilities, and they are intended to totally destroy the media.
If you don't want to utilize a service, you may break your hard drive yourself by hammering nails or drilling holes in it.
Hence batteries may be securely disposed of in your domestic garbage in the majority of areas.
To learn more about the disposing of refer ;
https://brainly.com/question/15709251
#SPJ1
Please complete the following questions. It is important that you use complete sentences and present the questions and answers when you submit your work.
1.Give several reasons why Python is such a great programming language. Explain how Python is related to flowcharts.
2.Consider this program:
Cost1 = input("Please enter the first expense: ")
Cost2 = input("Please enter the second expense: ")
print("Your total for both expenses was", Cost1 + Cost2)
3.If the user inputs “10” for the first expense and “20” for the second expense, what will the interpreter show in the final line when this program is run? If this result in not what the programmer intended, how would you explain what went wrong?
4.You are writing a line of code that should ask the user to input the balance of their bank account in dollars and cents. The program will then perform a multiplication problem to tell the user how much interest they can earn. Identify three errors in your line of input code and explain why they are incorrect. Include the corrected line of code in your answer. Here is the code:
1num = input(What is your balance?)
5.What are some kinds of comments that might be useful for a programmer to include in a program?
If you were planning how to write a program, at what point would a flowchart be helpful? At what point would pseudocode be helpful? Explain your reasoning.
Answers
Answer:
ndnxnndjdjsnnznnzbzbbdbdhdhhdbdbdbbdhdjidieiei
Explanation:
bxbzbxncnxbbcnfnnfnfndndnndndnndndnndndndnndndndndnnddnndndndnhrjjsjdudjjdjd
Which of the following is one aspect of gaming that goes relatively unnoticed but
has a huge outcome on the realistic accuracy of the game *
A. Pixel size of screen
B. Frame Rate
C. Character Development
D. Use of Game Physics
Answers
Answer:
frame rate
Explanation:
true or false : ¨the computer is a tool of informatics but the focus¨
Answers
True. The computer is a tool of informatics that is used to process, store, and communicate information.
However, the focus of informatics is not just on the computer, but on how information is used and managed in various contexts. Informatics also includes the study of information systems, databases, and networks, as well as the social and ethical implications of information technology. So while the computer is a vital tool of informatics, it is not the sole focus of the field.
However, it is worth noting that the focus of informatics is not solely on computers or technology, but also on the people and organizations that use technology to manage and make sense of information.
Learn more about the role of computers in informatics here:https://brainly.com/question/28361043
#SPJ11
How do you interpret and analyze photographs? What method comes most
naturally to you when interpreting and analyzing photographic works? Identify and
discuss the methods and strategies that you use to interpret and analyze
photographs.
Answers
Answer:
You interpret and analyze photographs by observing detail.
Explanation: