logical errors are mistakes that cause the program to produce erroneous results. group of answer choices true false
Answers
It is true Logical mistakes are mistakes that result in the programme producing inaccurate results. This is a group of computer language commands that work together to do a certain task. Application software describes programmed that help users use computers.
What exactly is software?A software programmed is a collection of executable instructions, often used to provide instructions to a computer system on how to carry out a certain operation or solve a particular issue.
An example of a syntax error
A syntax error is a particular kind of error that often results from errors in a software program's source code, such as:
word spelling.
typographical mistakes
Inaccurate labelling
Spacing
What is a mistake of logic?
A logical mistake is a form of error that often results in inaccurate results from the software programmed and causes a runtime error.
Learn more about logical error from here:
https://brainly.com/question/28957248
#SPJ4
Related Questions
impact of science in the world
Answers
Answer:
scientific impact reflection that finding all publication has on science or on society
Explanation:
such impact can be short term or long term and it is important not be imprise 1 over the other to great extent
For each scenario, select the best solution to try from the drop-down menu. A computer will not connect to the network. An IP address is being used by more than 1 computer. A router does not appear to be working at all. Some network files have become damaged.

Answers
Answer:
1) Check the switches, routers, and hubs.
2) Try logging off and on again.
3) Make sure everything is plugged in and turned on.
4) Restore files from backup versions.
Explanation:
Hope this helped!! :D
When might you need to freeze a user instead of deactivating? (User Setup)
Answers
You might need to freeze a user instead of deactivating when you want to temporarily restrict the user's access without deleting their account.
Freezing a user account is a useful option when you want to restrict access to an account temporarily. This may be necessary for a variety of reasons, such as a user taking a leave of absence or a temporary suspension due to a policy violation.
By freezing the account, the user's data and settings are retained, and the account can be reactivated when needed without requiring the user to create a new account.
On the other hand, deactivating a user account is more permanent and can result in the loss of data and settings. Therefore, if you need to restrict a user's access temporarily, it is best to freeze their account instead of deactivating it.
For more questions like User click the link below:
https://brainly.com/question/30630974
#SPJ11
1. when is it a good idea to use lossless compression
Answers
Hope this helped please brainiest
what kind of electronic communication might commonly be affected by citizen journalism?
pls explain I need 3 explanations
Answers
Answer: Don't got three explanations don't know a lot but here.
Explanation:
"Citizen journalists cover crisis events using camera cell phones and digital cameras and then either publish their accounts on the Web, or exchange images and accounts through informal networks. The result can be news in real-time that is more local and informative."
there are methods that help measure application blank information by the degree to which the information differentiates between high- and low-performing individuals. this scoring methodology is called a(n
Answers
Answer: Weighted application blank
Explanation:
Which of the following steps must be performed first to round the decimal 0.135 to the hundredths place?
Answers
First, keep in mind that 0.135 is divided into two pieces. The fractional component to the right of the decimal point and the integer part to the left of the decimal point:
Part of an integer: 0
135th fractional part
To round 0.135 to the closest hundredth is to round the numbers such that the fractional element has just two digits. Recall that you can only round a number if it is up to 5. Hence, the hundredth place of the above decimal will be 1.4.
What is a decimal?The decimal numeral system is the most widely used system for representing both integer and non-integer values. It is the Hindu-Arabic numeral system's expansion to non-integer numbers. Decimal notation is the method of representing numbers in the decimal system.
To convert a number from integer to percent, multiply it by 100 and then add a percent sign%. To convert a decimal to a percentage, multiply the decimal number by 100 and add %. To convert from decimal to percent, shift the decimal point two positions to the right and then add a percent sign.
Learn more about decimals:
https://brainly.com/question/1827193
#SPJ1
Pedestrians have ______.
A. to get out of your way when you’re driving
B. no right to use the Highway Transportation System
C. a right to use the Highway Transport System
D. to be on the sidewalk or crosswalk at all times
Answers
Answer:
c
Explanation:
I think c is correct answer if I answer wrong
Pedestrians have a right to use the Highway Transport System. Hence, option C is correct.
What is Highway Transport System?A system of highways used for the movement of cars. Type of transit, means of transportation, or transportation system. A structure that houses the equipment necessary for transporting people or goods.
A transportation system can be defined as the combination of factors and how they interact to produce the need for travel within a given area and the delivery of transportation services to satisfy this need. This concept is inclusive and flexible enough to be applied in various contexts.
For instance, people are transported to airports and ship docks using buses and cars. Transportation systems are a part of the larger technological, social, and environmental systems in our world.
Thus, option C is correct.
For more details about Highway Transport System, click here:
https://brainly.com/question/1071443
#SPJ2
How does a file reader know where one data item begins and another starts in a data file?
Python recognizes the end of one data item and the beginning of the next because they are separated by ___.
Answers
The way that a file reader know where one data item begins and another starts in a data file is option A: Every line in a text file has a hidden EOL (end of line) set of characters.
Python recognizes the end of one data item and the beginning of the next because they are separated by a comma-separated sequence.
What is the process of retrieving data from a file called?When the data held in them cannot be accessed normally, data recovery in computing is the process of restoring deleted, inaccessible, lost, corrupted, damaged, or formatted data from secondary storage, portable media, or files.
One line is read from the file and returned as a string using the readline function. The newline character is present at the end of the string readline returns.
An ordered group of items is known as a list, and each value is given an index. The components of a list are referred to as its elements.
Therefore, the location of the subsequent item to be read from a file is indicated by the read position of that file. The read position is initially set to the file's beginning.
Learn more about Python from
https://brainly.com/question/26497128
#SPJ1
See options below
How does a file reader know where one line starts and another ends?
Every line in a text file has a hidden EOL (end of line) set of characters.
Python knows how many characters to expect in a line.
The last item in a line of data does not have a comma after it.
Every line starts with a BOL (beginning of line) character.
Need help quick!!
Select all that apply.
Select each of the tasks you may perform using database software.
•finding the average of four numbers
•finding patterns in a large set of data
•retrieving data that matches a certain criteria
•connecting tables
•creating a pie graph
•updating information in more than one place at the same time
•analyzing data in order to make better decisions
•validating the data entered and check for inconsistencies
•finding answers to queries
•arranging data in a certain order
•calculating a percentage
Answers
Answer:
•retrieving data that matches a certain criteria
•connecting tables
•updating information in more than one place at the same time
•analyzing data in order to make better decisions
•validating the data entered and check for inconsistencies
•finding answers to queries
•arranging data in a certain order
given a double variable named x that has been declared and given a value, let's use a binary search technique to assign an estimate of its square root to another double variable, root that has also been declared. let's assume that x's value is greater than 1.0 -- that will simplify things a bit. here's the general idea: since x>1, we know its square root must be between 1 and x itself. so declare two other variables of type double (a and b say) and initialize them to 1 and x respectively. so we know the square root must be between a and b. our strategy is to change a and b and make them closer and closer to each other but alway make sure that the root we're looking for is between them. (such a condition that must always hold is called an invariant.) to do this we will have a loop that at each step finds the midpoint of a and b. it then squares this midpoint value and if the square of the midpoint is less than x we know that the root of x must be bigger than this midpoint: so we assign the midpoint to a (making a bigger and shrinking our a and b interval by half!)-- and we still can be sure that the root is between a and b. of course if the midpoint's square is greater than x we do the oppo we assign b the value of midpoint. but when to stop the loop? in this exercise, just stop when the interval between a and b is less than 0.00001 and assign root the midpoint of a and b then. we call this a binary search also because at each stage we cut the interval under consideration in half. efficient as this method is, old isaac newton discovered an algorithm that is even more efficient and that's what the library function sqrt uses.
Answers
In this coding exercise, a binary search technique is used to estimate the square root of a double variable named x.
Two double variables named a and b are declared and initialized to 1 and x respectively, and a loop is used to find the midpoint of a and b at each step. If the square of the midpoint is less than x, the midpoint is assigned to a, making a bigger and shrinking the interval by half. If the square of the midpoint is greater than x, the midpoint is assigned to b. The loop stops when the interval between a and b is less than 0.00001, and the root is assigned the midpoint of a and b. This technique is called a binary search because the interval under consideration is cut in half at each stage. However, the library function sqrt uses a more efficient algorithm discovered by Isaac Newton.
To get a similar answer on binary search:
https://brainly.com/question/12946457
#SPJ11
Shannon needs to select text from multiple locations which are not next to each other in her document. Which of the following keys should she press while selecting the different text areas to complete her non-contiguous selection?
Ctrl
Alt
Shift
Tab
Answers
What are the basic parts of sewing machine?
Answers
Answer:
1. Spool Pin
Thread usually comes on a spool. That is the wooden thread holder you buy in the store. The spool pin holds the spool of thread for you making it easier for you to thread your machine and keep the thread coming as you want it to. Read about the spool pin felt.
2. Bobbin Binder Spindle
A bobbin is a little cylinder that may come with or without flanges. It holds the thread that is wound around it. The spindle is where the bobbin is placed during winding.
3. Bobbin Winder Stopper
The bobbin is only so large. It cannot always hold the amount of thread you want to put on it. This part stops the bobbin from collecting thread when it has reached full capacity.
4. Stitch Width Dial
On many newer sewing machines, you get a variety of stitch options to use. The purpose of this part is to control the zig-zag stitch option while you are busy concentrating on your sewing.
5. Pattern Selector Dial
This little dial allows you to select one stitch pattern out of the many that come built into your sewing machine. You just turn the dial to get the pattern that you want on your clothes and other fabrics you want to mend or create.
6. Hand Wheel
This is the manual needle control which raises or lowers the needle. It is usually located at the right-hand side of the machine. It shouldn’t be that hard to turn.
7. Stitch Length Dial
More recent sewing machines may have this part attached to them. Its purpose is to control the length of your selected stitch. This helps you stay in control of your sewing duties and make sure you get what you want and need.
8. Reverse Stitch Lever
Once you push this lever, you get to sew in the opposite direction. This function makes your sewing a little easier and faster to do because you can go forward or in reverse when you need to.
9. Power Switch
You already know what this switch does. The key to using it is to make sure you turned your sewing machine off before you walk away. Also, it should be located at the right side of your machine.
10. Bobbin Winder Thread Guide
When you activate this part on your sewing machine, you are guiding the thread towards the bobbin/ This makes winding your thread up a little easier and should prevent twists, tangles or caught thread.
11. Thread Tension Dial
Tension is important when you do your sewing. Too loose can cause you problems and too much tension could snap your thread and make sewing more time consuming as you have to re-thread the machine. This little part simply controls the tension on the thread so be careful when you use it.
12. Thread Take-Up Lever
Your top thread passes through this part as you do your sewing. The lever moves up and down with your needle so do not be alarmed that it is constantly moving.
13. Needle Clamp Screw
Needles do not stay in place by themselves. It would be nice if they did. You need this part to hold your needle where it is supposed to be. It also makes sure your needle is secure as it moves.
14. Presser Foot
This is the part that holds your fabric so it doe snot slip all over the place while you are working. Controlling your fabric is important while you do your sewing.
15. Bobbin Cover
Your sewing machine parts do need some protection to keep them in top working order and to help then last you for years. This is the job of the bobbin cover. It protects the bobbin as it covers it.
16. Bobbin Cover Release Button
Also, you need access to your bobbin when it its filled with thread or there is a problem. This release button helps you to remove the bobbin cover so you have complete access to your bobbin.
17. Feed Dog
It is an interesting name, but it has a very straightforward function., This part feeds your fabric through the sewing machine while you are sewing. This helps you concentrate on other sewing needs as you work.
18. Needle
Another self-explanatory label that tells you everything you need to know. The needle is an integral part of the sewing machine and without it, the other parts cannot do their job.
19. Needle Plate
This part is located right under the needle and an under the presser foot. Its job is to help move the fabric forward as you sew. It may help help push the fabric back when you use the reverse mode on your sewing machine.
Explanation:
how does a salesos user get daily or weekly scoops emailed directly to them? (select all that apply)
Answers
A salesOS user can get daily or weekly scoops emailed directly to them through the following steps:
1. Login to your salesOS account using your credentials.
2. Navigate to the settings or preferences section of your account.
3. Look for the "Email Notifications" or a similar option.
4. Enable the option to receive daily or weekly scoops via email.
5. Save the changes to update your preferences.
Once you have completed these steps, you will start receiving the scoops directly in your email inbox on a daily or weekly basis, depending on your preference selection.
For more such questions scoops,Click on
https://brainly.com/question/33871487
#SPJ8
The ________ selection control structure provides only one alternative path of execution.
Answers
The if-else selection control structure provides only one alternative path of execution.
The if-else structure is a fundamental control structure in programming that allows for conditional execution of code. It consists of an if statement followed by an optional else statement. When the condition specified in the if statement evaluates to true, the code within the if block is executed. If the condition is false, the code within the else block (if present) is executed.
In this context, the if-else structure provides only one alternative path of execution because it either executes the if block or the else block, but not both. The decision on which block to execute is based on the evaluation of the condition. If the condition is true, the if block is executed, and if it's false, the else block (if present) is executed. This structure is useful for implementing simple binary choices in code, where only one of two possible actions needs to be taken based on a condition.
Learn more about if-else selection here:
brainly.com/question/13438284
#SPJ11
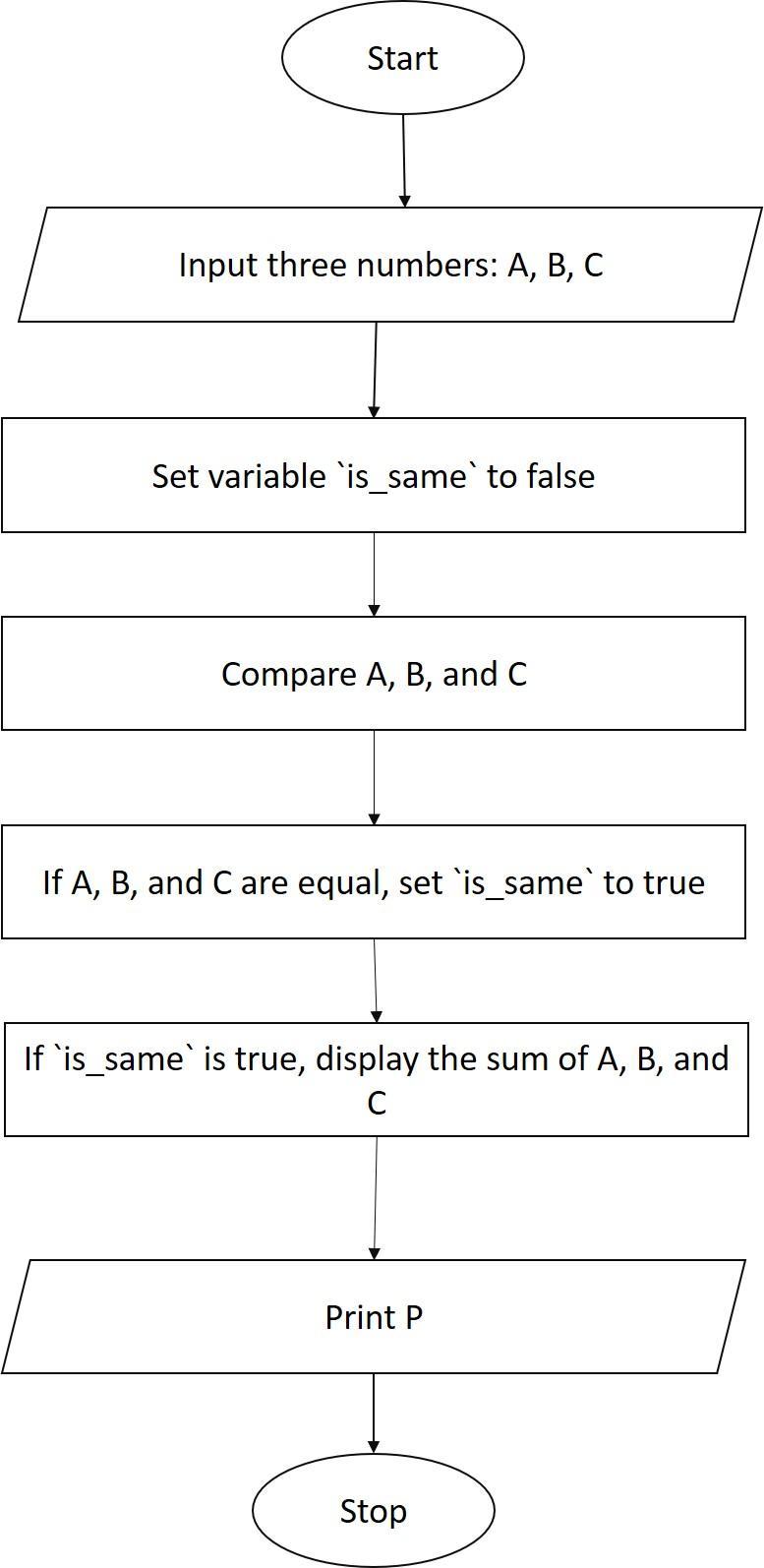
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
[15 points] 3.2 Lesson Practice (holy marry mother of joseph)
![[15 points] 3.2 Lesson Practice (holy marry mother of joseph)](https://i5t5.c14.e2-1.dev/h-images-qa/contents/attachments/OxLqD49puudaWhoX2hXqxFvMqVivfCCT.png)
Answers
HELP PLEASE
Which app would require two people to know the same language but not require either to speak aloud in order to communicate?
A language learning app
A language translation app
An electronic notepad app
A speech-to-text app
Answers
A language translation app
--------------------------------------------------------------------------------------
A language learning app, like Duolingo, would only require one person, since it person vs computer
An electronic notepad app, i dont think that has anything to do with language?
A speech to text app would defeat the whole purpose of not speaking aloud, so thats not correct.
The only one that makes sense is a language translation app, like iTranslate, which allows people to speak to it, but ONLY if they want, because they can type the words they want to translate.
Hope this helps! Please let me know if you need more help, or if you think my answer is incorrect. Brainliest would be MUCH appreciated. Have a great day!
Stay Brainy!
−\(WishWolf\)
Answer:
A language translation app
Explanation:
Which of the following behaviors does not harm a company if your employment is terminated?
A. getting a copy of word-processing software before leaving
B. selling trade secrets to competing companies or to your future employer
C. creating a username and password so you can access company information after you have left
D. notifying your employer of all accounts you have access to, and requesting that they change all passwords before you leave
Answers
Answer:
Notifying your employer of all accounts you have access to, and requesting that they change all passwords before you leave.
Answer:
its D
Explanation:
took the test
a cpu handless all the instruction that it recieces from hard ware and software which are available on the computer true or false
Answers
Answer:
True
Explanation:
The CPU controls the computer like a brain controls a body. And yes it takes instruction from hardware and software and runs it.
Question 1 (5 points) When you are at a job interview, you should use effective communication strategies, like formal language. What is formal language and why do we use it? Formal language helps create the impression that the speaker is an expert on the topic. It suggests to audience members that the speaker's points deserve respectful consideration, and it presents the ideas of the speech in the most polished possible way.. Formal language is archaic and derived from Shakespeare to help us sound fancy in order to ensure that an employer can see that we are versatile Formal language is our ability to speak more than just one language. If we are bilingual, we have a better chance at being hired.
Answers
This prompt is about formal oanguage and styles of communication. See the explanation below.
What is formal language and why do we use it ?Formal language refers to a style of communication that follows specific grammatical and linguistic conventions, typically associated with academic, professional, or formal settings. It is characterized by the use of proper grammar, syntax, and vocabulary, and avoids slang or colloquial expressions.
We use formal language in job interviews to convey professionalism, competence, and respect for the setting and the interviewer. It also helps to convey our ideas in a clear and concise manner, without the distractions of informal language.
Contrary to the notion that formal language is archaic or derived from Shakespeare, it is a contemporary and widely used mode of communication in formal settings. It is not related to bilingualism, which refers to the ability to speak two languages fluently.
Learn more about formal language:
https://brainly.com/question/24222916
#SPJ1
Write a memo to the vice president, outlining the steps an employee might have taken to create an e-mail message and make it appear to come from another employee's account. Be sure to include some SMTP commands the culprit might have used.
Answers
Answer:
Following are the memo to the vice president:
Explanation:
In this question, the president claims, that he got a threatening e-mail from the Maui worker. HR acknowledged that all of the workers should always be dismissed, in its protection, that worker claims that he did not send the message but he does not recognize why the message implies him return address. Here is a note for the vice president, who explains how an employee could have produced an email and made it look to be from another worker's account. That stuff we want will be progressively explained as follows:
a) The manipulating and e-mail used only by spammers and attackers were called this technique. In the SMTP server, it sends messages, that you can set up to send your spammer to the email addresses. Instead of a mail confirmation, I d the forger requires the receiver to see the next employee I d email. that recipient doesn't understand who sent the message.
b) The e-mail Systems information allowing for accessible transfer is used by the intruder or forger. It must use an attacker order to verify communication with the SMTP server command:
telnet smpt.server.name 25
Its name of the SMTP server is smpt.domain.name, and the port is 25.
c) when the last stage is successful as well as a link created, this order to imitate an email account only with command can be entered:
MAIL from: Email-id
It creates a problem for the worker that sends the e-mail with the same id
d) Hacker sets the email of the receiver to:
RCPT to: boss email-id
It sets the beneficiary as the e-mail above.
e) By entering an order, you can create the email data:
DATA It may also adjust the date by using command and Any date we would like to use.
Date: (date you would like)
We should settle on the following:
Subject: (your topic)
f) We press Insert after the topic is written. In this body can then be e-mail forms. It produces the text.
g) its email forged is forwarded.
PLEASE HELP!!! THIS IS DUE TODAY!! WILL MARK BRAINLIEST!!
Two examples of good digital citizenship, and provide your reasoning as to why they are good.
Answers
Answer:
1. Respecting rules and cookies while browsing a website.
2. Being kind and properly following the requirements the owner asks you to follow. Reporting any sort of comment or image that is hurtful/harmful.
Explanation:
1. By the rules and cookies for a website, you ensure the safety of your device and are not putting any information at risk.
2. Cyberbullying is a huge issue and you can reduce cyberbullying with the simple steps of being kind and respecting others.
Conclusion:
These rules are examples of good digital citizenship and following them will benefit you and your peers greatly.
Example 1. Learning to type, use a mouse, and other computer skills.
Explanation: This is a good example of digital citizenship because by learning these skills it allows you to actively engage with others digitally and even give them pointers with their own learning.
Example 2. Avoiding harassment or hateful speech while conversing with others online.
Explanation: This is a good example of digital citizenship because by avoiding harassment or hateful speech you are contributing to making the digital world a safer place for everyone.
hopefully this deserves brainliest :)
how to create an e mail account
Answers
Answer:
Go into setting; go to accounts; look for create account or add account; it will then come up with a tab asking what you want to create the for ( choose Email) it will ask who you want to create it for (yourself or Bussiness), you choose whichever you want and then fill in your information.
Hope this helps....
Explanation:
When using the BF-76 plugin compressor, what is the optimal ratio setting for Parallel Compression to achieve an aggressive parallel path?
Answers
The optimal ratio setting for parallel compression with the BF-76 plugin compressor will depend on the specific material being processed and the desired effect.
However, to achieve an aggressive parallel path, you may want to use a high ratio of compression on the parallel path.
Typically, parallel compression involves mixing an uncompressed signal with a heavily compressed signal to achieve the desired dynamic range and tonal characteristics.
To create an aggressive parallel path, you may want to use a higher ratio of compression on the parallel path, such as 10:1 or higher, to heavily compress the signal being sent to the parallel path.
It is important to note that the exact optimal settings for parallel compression will vary depending on the specific material being processed and the desired effect.
Therefore, it is recommended to experiment with different ratio settings and adjust other parameters such as threshold, attack, and release to find the optimal settings for your specific application.
To learn more about compression, click here:
https://brainly.com/question/30060592
#SPJ11
Describe the command structure of Cisco IOS software,
Answers
Cisco IOS software uses a hierarchical command structure. Commands are organized into different modes, and each mode has a set of commands associated with it. Modes are typically accessed by entering a command at the router prompt. For example, the enable mode can be accessed by entering the enable command at the router prompt.
What is Cisco IOS?
The Internetworking Operating System (IOS) is a series of proprietary network operating systems used on numerous Cisco Systems router and network switch models. The system consists of a collection of routing, switching, internetworking, and telephony capabilities that are incorporated into a multitasking operating system. Although the IOS code base includes a cooperative multitasking kernel, most IOS capabilities have been ported to other kernels for usage in Cisco products, such as Linux and QNX. IOS is not supported by all Cisco networking products. Some Cisco Catalyst switches that run IOS XE and Cisco ASR routers that run IOS XE or IOS XR, both of which are Linux-based operating systems, are exceptions. Cisco Nexus switches and Cisco MDS switches both run NX-OS, a Linux-based operating system, in data centre environments.
To learn more about Cisco IOS
https://brainly.com/question/28270325
#SPJ13
Why do you think they added the wait .5 seconds block?
Answers
Answer:
Satisfaction
Explanation:
People enjoy the sensation of the computer doing something and the feeling that the program is advanced.
A(n) ____ tells the compiler or interpreter that the character that follows it has a special purpose.
Answers
The answer that tells the compiler or interpreter that the character that follows it has a special purpose is called; An Escape Character
Computer CharactersThe correct answer here is called ''Escape Character". This is because In computing and even in telecommunications, an escape character is a type of character that reinforces another interpretation on the next set of characters in a character sequence. An escape character is usually a peculiar case of using metacharacters.
From the definition above, we can see that the escape character tells the compiler or interpreter that the character that follows it has a special purpose.
Read more Computer characters at; https://brainly.com/question/6962696
state the difference between token and identifier
(computer)
Answers
The three most important factors that affect the distribution of resources are:
Answers
Answer:
The main factors that affect distribution of population are natural resources, climatic conditions, soils, cultural factors, age of human settlement, industrial development and means of transport and communication. The factors affecting distribution of population are described below one by one in a nutshell manner.
Explanation:
Hope it helps :)