Let G be a weighted undirected graph with all edge weights being distinct, and let (u,v) be the edge of G with the maximum weight. Then (u,v) will never belong to any minimum spanning tree. True False In a weighted undirected graph G=(1,5) with only positive edge weights, breadth-first search from a vertex s correctly finds single- source shortest paths from s. True False Depth-first search will take O(V + E) time on a graph G = (V, E) represented as an adjacency matrix. . True False
Answers
True.
This statement is true. If (u,v) has the maximum weight in the graph, then any minimum spanning tree must include all edges of smaller weights than (u,v), and therefore cannot include (u,v).
True.
This statement is true. In a weighted undirected graph G with only positive edge weights, breadth-first search from a vertex s can be used to correctly find single-source shortest paths from s, as long as there are no negative-weight cycles in the graph. Since all edge weights are positive, BFS will always visit nodes in increasing order of distance from the starting node, ensuring that the shortest path is found without being affected by negative edge weights.
False.
This statement is false. Depth-first search can take up to O(V^2) time on a graph G = (V,E) represented as an adjacency matrix. This is because each iteration of the DFS loop may check every vertex in the graph for adjacency to the current vertex, leading to a worst-case runtime of O(V^2). A more efficient representation for DFS would be to use an adjacency list, which would give a runtime of O(V + E).
Learn more about spanning tree here:
https://brainly.com/question/13148966
#SPJ11
Related Questions
I’m buying a prebuilt pc once I get it and set it up, what do I need to install on it?
Answers
Project: Programming as a Team
You know the advantages of working in a team. sharing the workload diverse knowledge sets diverse perspectives and ideas In this project, you are going to plan and write a program with a team of your fellow students. Objectives Decompose a project into assignments for members of a team. Your Programming Goal Your team is going to write a program as part of a team. Your teacher may require you to come up with your own goal. If not, use the following goal. You have been asked by a math teacher to write a program to process a pair of points. The program will find the distance between the points, the midpoint of the two points, and the slope between them. Your Task Plan your program. Meet with your team to plan the program. Assign a task to each member of the team. Record each person's name and their task. Write the program. Test your program. Be sure to test each function of your program. Evaluate the performance of each member of the team. Describe what each member did and how it worked. Record the project in a Word (or other word-processing) document, as described below. Your Document's Sections Part 1: Names Your name Your partners' names Part 2: Goal Describe the goal of your program Part 3: Team Tasks Give each person's name and their assigned task Part 4: The Program Copy and paste the program your team wrote Part 5: The Output Copy and paste the output; make sure you test each type of output Part 6: Team Evaluation Evaluate the performance of each member of your team Use this rubric to evaluate your project before you submit it.
Answers
Answer:
doma de su ermosa sonaer somaer domado tí domaer dona somee don comer dore ligeramente somaer domado domado amer no donar coja ER domaed voy yo comer dore domE ⚡doma cose conmigo está domaer di fi somaer dona
The advantages of working in a team are:
Better at problem solving.Fast and Increased potential for innovative ideas and growth.What is Teamwork?This is known to be a kind of collaborative work that is done when two or more people act as a group so that they can achieve a common goal.
Note that The advantages of working in a team are better at problem solving as more people can handle complex issues together and fast.
Learn more about from
https://brainly.com/question/3951300
#SPJ2
3
Select the correct answer.
What is the output of the following HTML code?
Please click here to visit our website.
OA.
Please click here to visit our website
ОВ.
Please click here to visit our website
Oc.
Please click here to visit our website
OD.
Please click here to visit our website
OE.
Please click here to visit our website
Reset
Next

Answers
Answer: use this
Explanation:


Answer:
The answer is D
Explanation:
I took test

______ is a machine learning technique that helps in detecting the outliers in data
Answers
Outlier Detection is a machine learning technique that helps in detecting the outliers in data. It is used to identify data points that are significantly different from the majority of the data.
Finding and analysing data points that differ considerably from the bulk of the other data points in a dataset is the process of outlier detection. Outliers are data points that are significantly larger or smaller than the other data points in the dataset. They can significantly affect machine learning models and statistical analysis.
It can be used to detect anomalies in financial data, medical data, manufacturing data, or any other type of data.
For such more question on Detection:
https://brainly.com/question/12854520
#SPJ11
How to fix error "this challenge page was accidentally cached by an intermediary and is no longer available"?
Answers
The steps listed below will help you fix it: Click Date & Area in the Control Panel before selecting Timeline. Click On “ options after selecting the Internet tab. Change the destination to time.windows.com & select the option labelled "Synchronize with just an Internet service given id."
What is meant by "Internet service"?
Internet Connections refers to the package we offer you that allows you to use the World wide web and specific goods, whether through a television, desktop computer, or another device. Those solutions may be supplied through either digital or analogue infrastructure.
What function does internet access serve?
ISPs are businesses that link people and organizations to the Internet and offer them services. ISPs may also offer email addresses, software packages (such browsers), and then a website page or webpage. ISPs have the ability to both host and construct webpages for businesses.
To know more about "Internet service" visit:
https://brainly.com/question/14298989
#SPJ4
when flynn added a date field to a pivottable, excel grouped the date values into quarters, months, and years. what can flynn do if he does not want to group the pivottable this way?
Answers
If Flynn does not want to group the Pivot Table, then he can
Regroup the dates to show quarters only.Ungroup the dates.What is a Pivot Table?
The individual items in a larger table are aggregated into one or more discrete categories in a pivot table, which is a table of grouped data. This summary may comprise sums, averages, or other statistics, which the pivot table aggregates using a selected aggregation function applied to the aggregated information. If you need to track sums of long rows or columns of information that you can quickly compare to one another, pivot tables can be quite helpful.
Large volumes of data can be easily summarized interactively using pivot tables. A pivot table can be used to answer unexpected inquiries about your data and conduct an in-depth analysis of numerical data. A pivot table is particularly useful for Querying massive volumes of data in a variety of user-friendly ways.
To learn more about a pivot table, use the link given
https://brainly.com/question/29526863
#SPJ4
what is a soft ware?
Answers
Software is a collection of instructions and data that tell a computer how to work. This is in contrast to physical hardware, from which the system is built and actually performs the work. In computer science and software engineering, computer software is all information processed by computer systems, including programs and data. Computer software includes computer programs, libraries and related non-executable data, such as online documentation or digital media. Computer hardware and software require each other and neither can be realistically used on its own.
Answer:
it is like some data
Explanation:
what is database management?
Answers
Answer:
Database management is the process of organizing, storing, retrieving, and protecting data using a database management system (DBMS). The DBMS is a software application that enables users to interact with the database and manage data efficiently.
Database management involves designing the database schema, creating tables and fields, defining relationships between tables, and ensuring data integrity by enforcing constraints and validation rules. It also involves querying the database using SQL or other programming languages, updating or deleting data, and creating reports or visualizations of data.
How does net neutrality protect your information? Do they connect everyone into something?
Answers
Answer:
Net neutrality law focuses on regulating and/or preventing three main practices:
Blocking: ISPs cannot block or prevent access to any lawful content on the web.
Paid prioritization: Providers cannot prioritize companies or consumers who pay a premium for a “fast lane” and keep those who don’t pay in a “slow lane.”
Throttling: Providers cannot limit your bandwidth or slow your connection based on your internet activities.
Without net neutrality or other laws protecting equal content, ISPs could, in theory, block certain websites and favor others. For example, your internet provider could theoretically make Netflix slower in order to push you towards its cable TV service.
Or, Xfinity could allow their subscribers to stream Peacock content (which they own through NBCUniversal) for free, while charging subscribers for watching Netflix. With net neutrality, you would have free and equal access to both Peacock and Netflix.
Another example would be your ISP slowing your connection every time you try to game over Twitch, but speeding it back up again when you’re not gaming, a practice known as throttling.
Explanation:
Answer: Net neutrality rules prevent this by requiring ISPs to connect users to all lawful content on the internet equally, without giving preferential treatment to certain sites or services. In the absence of net neutrality, companies can buy priority access to ISP customers.
question 26 options: a (very small) computer for embedded applications is designed to have a maximum main memory of 8,192 cells. each cell holds 16 bits. how many address bits does the memory address register of this computer need?
Answers
13 address bits are needed for the main memory of 8192 cells.
How to calculate the address bits?
Step 1 is to determine the address's bit length (n bits)
Step 2: Determine how many memory locations there are (bits)
To calculate the address bits we need to know which power of the cells is raised to 2. so 13 address bits because 2 ^ 13 = 8192 cells
What are the address bits?
An index in memory is the main storage address. The address of a single byte is a 32-bit address. An address can be found on 32 of the bus's wires (there are many more bus wires for timing and control). Addresses like 0x2000, which appear to be a 16-bit pattern, are occasionally brought up in conversation.
Hence 13 address bits are needed for the main memory
To know more about address bits please follow the link
https://brainly.com/question/13267271
#SPJ4
Can someone help me I am coding.
Answers
Answer:
i will help u
Explanation:
what did you want
3. QUESTIONS 3.1. What is the difference between GPS and GIS? ( 0.5pt) 3.2 What is the minimum number of satellites you need to get in your GPS receiver to get a relatively accurate location? (0.5 pt) 3.3 What sre the three pieces of geographic information collected by a basic GPS receiver? (0.5 pt) 1. 2. 3. 3.4 While DEMs and LiDAR both produce models of terrain, there are differences in the models. In what ways are they different? (1 pt)
Answers
GPS is a satellite-based positioning system used for determining accurate location and navigation, while GIS is a system for capturing, managing, analyzing, and visualizing geographic data.
What are the differences between GPS and GIS in terms of their functionality and purpose?3.1. GPS is a satellite-based positioning system, while GIS is a system for capturing, managing, analyzing, and displaying geographic data.
3.2. A minimum of four satellites is needed for a GPS receiver to obtain a relatively accurate location.
3.3. The three pieces of geographic information collected by a basic GPS receiver are latitude, longitude, and altitude.
3.4. DEMs provide a digital representation of terrain elevation, while LiDAR uses laser scanning to generate a detailed 3D model of the Earth's surface.
Learn more about satellite-based
brainly.com/question/1913365
#SPJ11
As an IT technician for your company, you are in the process of setting up several servers in your network. During the process, one of the servers is misconfigured and is, therefore, having trouble synchronizing information with the other servers.
Answers
the errors simple yet effective.
Resolved -The United States Federal Government should ban the collection of personal data through biometric recognition technology.
I need to write a public forum debate case negating this resolution
Answers
Sure, here's a possible case negating the resolution:
Introduction:
Thank you, Mr./Madam Chair, and esteemed opponents. We, the negating team, believe that the United States Federal Government should not ban the collection of personal data through biometric recognition technology. While we acknowledge the concerns raised by the affirming team, we argue that biometric recognition technology has several benefits that outweigh its potential drawbacks.
Contention 1: Biometric recognition technology enhances security and public safety.
Biometric recognition technology enables law enforcement agencies to identify and track criminals, terrorists, and other threats more accurately and efficiently. For instance, facial recognition technology has helped the police to identify suspects in cases of kidnapping, robbery, and terrorism. A study by the National Institute of Standards and Technology (NIST) found that some facial recognition algorithms have a high accuracy rate of up to 99%, especially for high-quality images. Biometric recognition technology can also enhance security in sensitive areas such as airports, government buildings, and military installations, by verifying the identity of individuals before granting access.
Contention 2: Biometric recognition technology facilitates convenience and efficiency.
Biometric recognition technology can also facilitate convenient and efficient transactions and services, both in the public and private sectors. For example, many smartphones, laptops, and other devices now have fingerprint or face recognition features that allow users to unlock their devices, make payments, and access apps without having to remember passwords. This technology can also streamline and speed up processes such as voting, banking, and healthcare by eliminating the need for paper-based forms and identity verification procedures.
Contention 3: Biometric recognition technology is subject to regulation and oversight.
Contrary to the affirming team's claims, biometric recognition technology is not a lawless Wild West. The technology is already subject to several regulations and oversight mechanisms, such as the Privacy Act, the Electronic Communications Privacy Act, and the Fair Information Practice Principles. Additionally, several states, including Illinois and Texas, have passed biometric privacy laws that impose restrictions on how private entities can collect and use biometric data. The federal government can build on these existing regulations and frameworks to ensure that biometric recognition technology is used ethically and responsibly.
Conclusion:
In conclusion, we urge the judges and the audience to consider the benefits of biometric recognition technology, such as enhancing security, convenience, and efficiency, and the existing regulations and oversight mechanisms that can mitigate its potential risks. We believe that a balanced approach that recognizes both the benefits and challenges of this technology is the way forward, rather than an outright ban that would deprive society of its potential benefits. Thank you.
The public forum debate case negating the resolution has been stated below.
What is the federal government?The national government of the United States is represented by the federal government. The public forum debate case negating the resolution is mentioned as follows:
Introduction:
The United States Federal Government, in our opinion, shouldn't outlaw the collection of personal information using biometric recognition technology, according to the opposing camp. We appreciate the issues stated by the affirmation team, but we contend that there are significant advantages to biometric recognition technology that exceed any possible disadvantages.
First claim: biometric identification technology improves safety and security.
Law enforcement organizations can more precisely and effectively identify and trace criminals, terrorists, and other dangers thanks to biometric identification technology. For example, face recognition technology has assisted law enforcement in locating suspects in kidnapping, robbery, and terrorist situations.
Second claim: Biometric recognition technology promotes efficiency and convenience.
Both in the public and private sectors, biometric recognition technology can enable simple and effective transactions and services. For instance, many modern smartphones, laptops, and other gadgets include face or fingerprint recognition capabilities that let users access apps, pay for items, and unlock their devices without having to remember a password.
Second claim: The use of biometric identification technology is governed and supervised.
The biometric identification technology is not a lawless Wild West, despite what the affirming team asserts. A number of laws and regulatory frameworks, including the Fair Information Practise Principles, the Electronic Communications Privacy Act, and the Privacy Act, already apply to the technology.
Conclusion:
Finally, we implore the judges and the audience to take into account the advantages of biometric recognition technology, such as improving security, ease, and effectiveness, as well as the current legislation and supervision frameworks that can reduce its potential threats.
Learn more about Federal Government here:
https://brainly.com/question/371257
#SPJ2
PLEASE HELP!! WILL MARK BRAINLIEST!!~~~Brody is concerned that he is going to exceed the quota set for his mailbox. Where should he go to access the Mailbox Cleanup tools?
Backstage view
Inbox
Deleted Items Folder
Outlook Web App
Answers
Answer:
d
Explanation:
Outlook Web App will provide access to the Mailbox Cleanup tools. The correct answer is D.
What is Outlook?On the Menus tab, you'll notice a Tools menu next to the Actions menu on the toolbar. Click Tools to open the Tools drop-down menu, which includes options such as Mailing All Folders, Cancel All, Com Add-Ins, Disable Items, Perspective Options, and so on.
These include any emails you send back and forth using replies.
The process of cleaning up is shown below.
Choose an email conversation that you want to clean up.Choose Delete > Clean Up Conversation by clicking the arrow next to it. You can also purge entire Folders.If prompted, choose Clean Up to confirm.
Access to the Mailbox Cleanup tools will be Outlook Web App. Then the correct option is D.
More about the Outlook link is given below.
https://brainly.com/question/17457799
#SPJ6
10
Select the correct answer.
What management function do managers perform first when an organization begins a project?
OA staffing
OB. organizing
O c.
directing
OD. controlling
O E. planning
Reset
Next
Answers
The first management function that managers perform when an organization begins a project is planning.
Planning is the first and most important step in project management. It involves defining the project's goals, objectives, scope, and requirements, as well as determining the resources needed, the timelines, and the risks associated with the project. Planning helps managers identify potential problems and develop solutions to ensure the project's success. It also helps them set realistic expectations and communicate them effectively to the team and stakeholders. Therefore, without proper planning, the project is likely to face significant delays, cost overruns, and quality issues.
To learn more about management functions click here:
https://brainly.com/question/15351742
#SPJ11
I copied my friend's homework... give me some excuses to get out of it!!
Answers
Answer:
Tell the teacher that you will pee in her coffee cup if they don't forget about what you did
Explanation:
Answer:
Explanation:
Depends on the homework, but
"We worked together on it and came to similar conclusions."
"We checked answers with each other when we finished to make sure we got the problems correct and did the problems correctly."
the computers in a local area network (lan) are usually connected to the network via a hardware component called a(n) .
Answers
Answer: Several hardware elements are needed to connect a device or computer to a local area network (LAN): a network interface controller (WNIC) or network interface card (NIC) (WNIC) a wired or wireless transmission method
Explanation:
What is a LAN ?
1) A local area network (LAN) is a collection of computers and ancillary devices that connect to
a server via a shared wired or wireless network within a certain geographical region.
2) A local area network can support just two or three users in a home office or thousands of
users in the headquarters of a company.
3) To enable network nodes to connect and share resources like printers or network storage,
homeowners and information technology (IT) administrators set up local area networks
(LANs).
A local area network (LAN) requires the following hardware elements in order to connect a computer or other device to it:
A NIC : Network Interface Card or WNIC : Wireless Network Interface Card Wired or wireless transmission medium.A device for making a network connection, such as a router, hub, switch, wireless access point (WAP), gateway, or bridgeTherefore, LAN are usually connected to network via a collection of :
Personal deviceNetwork deviceCablesInternet ConnectionYou can learn more about local area network ( LAN ) from the given link
https://brainly.in/question/12762201
Which of these is a biotic factor in a forest?
Will
O A. Climate
O O
O B. Terrain
O C. Trees
O D. Water
Answers
Answer: trees
Explanation:
Apply the default name for the rule (Gloria Vivaldi) and turn it on for current and future messages.
Answers
The steps to set up a rule with the default name "Gloria Vivaldi" in Microsoft Outlook is given below.
What are the steps needed?Open Microsoft Outlook.
Click on the "File" tab and select "Manage Rules & Alerts."
Click on the "New Rule" button to create a new rule.
In the "Rules Wizard" window, select "Apply rule on messages I receive" and click "Next."
Choose the conditions that you want to apply to the rule, such as specific senders or keywords in the subject line. Click "Next" after making your selections.
Choose the action that you want the rule to perform, such as moving the message to a specific folder or marking it as read.
Click "Next" after making your selections.
In the "Step 2: Edit the rule description" section, give your rule a name, such as "Gloria Vivaldi." You can also add any exceptions to the rule in this section. Click "Finish" when you're done.
The rule will be applied immediately to any incoming messages that meet the conditions you specified. You can also choose to run the rule on your existing messages by selecting the "Run Rules Now" option in the "Rules and Alerts" window.
Learn more about Microsoft on:
https://brainly.com/question/29576990
#SPJ1
Which of the following symbols would not be seen in the syntax for Java variables, methods, or arguments?
{}
()
??
[]
Answers
Answer:
??
Explanation:
?? is invalid syntax
When declaring or initializing variables names, and when writing methods, or arguments ?? is not used in Java .
() [] {} all these are used with variables , methods or arguments.
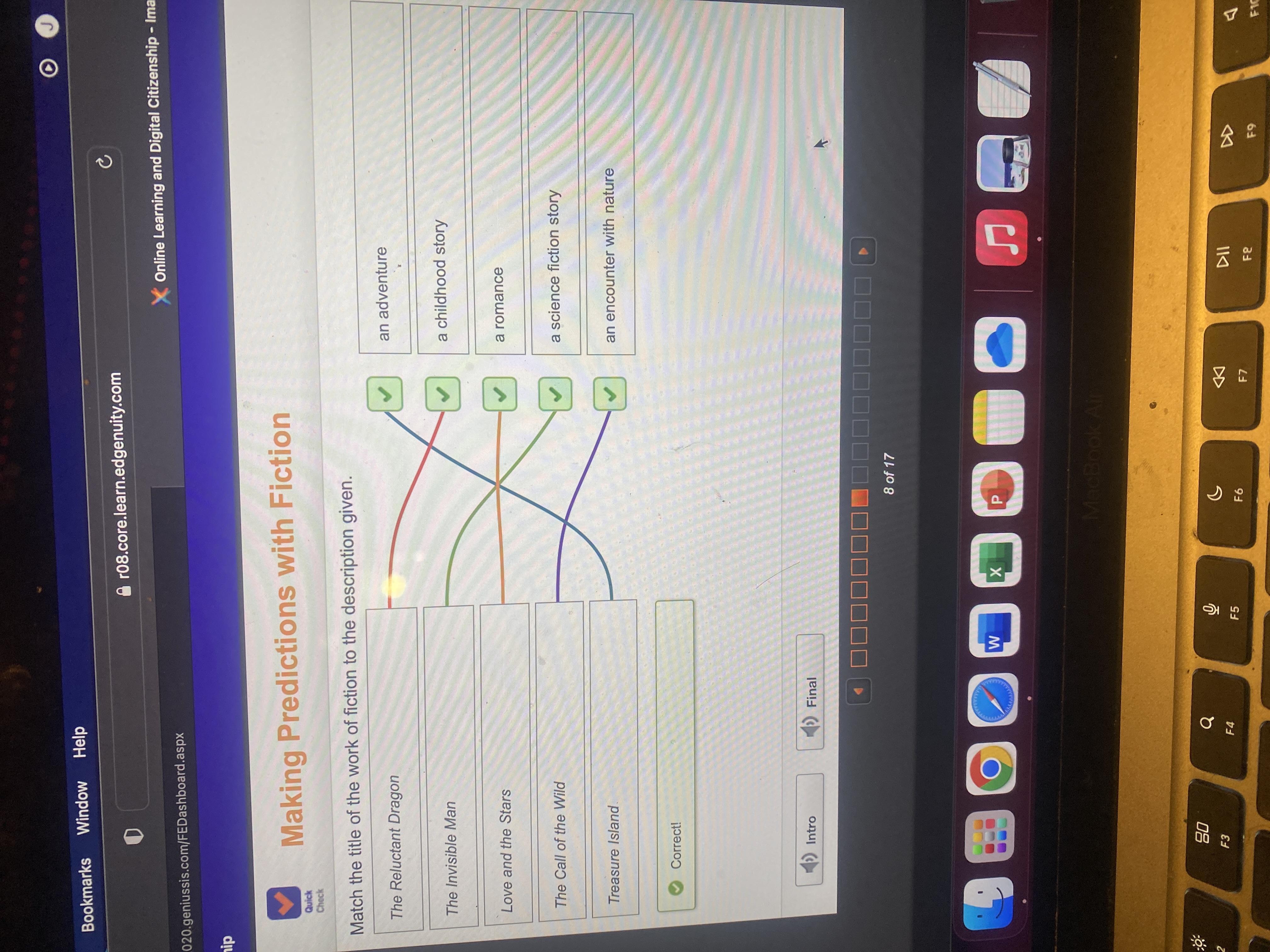
Match the title of the work of fiction to the description given.

Answers
Answer:
Explanation:
Let's get the ones that there is no dispute.
Love and the Stars Romance
The Invisible Man Science Fiction
Treasure Island An Adventure
Call of the Wild An encounter with Nature
Reluctant Dragon Childhood story.
Here's the problem.
Most ten year olds are children. They likely would like both Call of the Wild and the Reluctant Dragon as well as Treasure Island.
The Reluctant Dragon could be called science fiction.
Answer:
your welcomeee
Explanation:
Can someone help me with the 9. 5 minion translator in CMU CS Academy?
Answers
In the Minion Translator problem at CMU CS Academy, the task is to create a program that translates English text into Minionese, a language spoken by the Minions from the movie "Despicable Me."
To solve the problem, you need to write a function called translate that takes an English sentence as input and returns the corresponding translation in Minionese. Here's an example implementation:
def translate(english_sentence):
vowels = ['a', 'e', 'i', 'o', 'u']
translation = ""
for char in english_sentence:
if char.lower() in vowels:
translation += char + "p" + char.lower()
else:
translation += char
return translation
In this solution, we iterate over each character in the input English sentence. If the character is a vowel (either lowercase or uppercase), we append it to the translation string followed by "p" and the lowercase version of the vowel. Otherwise, we simply append the character as is.
To test your solution, you can call the translate function with different English sentences:
print(translate("banana")) # Outputs "bapAnapAp"
print(translate("Hello, world!")) # Outputs "Hepllo, wporlpld!"
Make sure to read the problem statement and follow the specific requirements outlined there.
Learn more about function here:
brainly.com/question/30721594
#SPJ11
How could you nonverbally express interest while speaking to a customer in person? Check all of the boxes that apply.
by crossing my arms
by making eye contact
by tapping my fingers on the table
by nodding my head
by smiling
by sitting far away from the speaker
by sitting up straight
Answers
Answer:
By smiling
By making eye contact
By nodding my head
By sitting up straight(This one is a maybe)
Explanation:
The body language I've listed is the most people use to nonverbally express interest while speaking to another person.
____storage provides a high-speed internet connection to a dedicated remote storage facility that contains banks of file servers to offer enormous amounts of storage.
Answers
Cloud storage provides a high-speed internet connection to a dedicated remote storage facility that contains banks of file servers to offer enormous amounts of storage.
Cloud storage allows users to store and access their data and files remotely over the internet. It eliminates the need for local storage infrastructure and provides scalability and flexibility in terms of storage capacity.
With cloud storage, data is stored across multiple servers and locations, ensuring redundancy and reliability. Users can access their files from any device with an internet connection, making it convenient for remote access and collaboration.
Cloud storage providers offer various plans and pricing options based on the amount of storage required. The infrastructure of cloud storage is typically managed and maintained by the provider, relieving users of the burden of hardware maintenance and upgrades.
Overall, cloud storage is a popular solution for individuals and businesses seeking secure, scalable, and high-capacity storage solutions accessible over the internet.
To learn more about Cloud storage visit : https://brainly.com/question/26972068
#SPJ11
A chatbot is a computer program designed to emulate human conversation. For this program, you will use if statements, user input, and random numbers to create a basic chatbot.
The Scenario
You have decided to design a fashion chatbot that helps people pick out their fashion preferences. Your bot can gauge what types of clothes and accessories the user might like.
Your chatbot should ask the user the following (minimum requirements for the grader) and then give answers depending on the answers the user inputs:
at least 6 questions
at least 3 if-elif-else statements
the use of the random module and randomly generated numbers
Based on these criteria, some responses will be based on what the user types and some will be based on random numbers.
For example, if the chatbot asks what is your favorite head accessory, your chatbot might respond I also think baseball hats are best. in response to a user input of baseball hats, or I love beanies! in response to a user input of beanies.
Additionally, you could also have a random number generated between, say, 1 and 3 and have a corresponding response depending on the number to randomly answer with That’s in right now. or Wow, so stylish!, and so on.
Note that in order to pass all of the test cases, your randomly generated numbers should not be dependent on user input (for example, you would not want to include a situation where if the user inputs a specific phrase, then a random number is generated). The randomly generated numbers should prompt a reply from the chatbot, and should do so separately from the user input statements that prompt a reply from the chatbot.
Answers
Based on the fact that you would use a ch.a tbot to emulate human conversation and we decide to design a fashion ch.a tbot that helps people pick out their fashion preferences, a program that would gauge what types of clothes and accessories the user might like is given below:
The Programimport random
good_responses = (["That's cool!", "Wow!", "That's great to hear!", "Tell me more"])
bad_responses = (["I'm sorry", "That is too bad!"])
first_name = input("What's your first name? ")
last_name = input("What's your last name? ")
print(f"Hello {first_name} {last_name}, nice to meet you!")
age = int(input(f"How old are you, {first_name}? "))
if age > 17:
print("Nice, you are considered an adult")
else:
print("You are young, our children's section is to aisle 10.")
color = input("What's your favorite color? ")
print(good_responses[random.randint(0,3)])
feeling = input(" What is your current mood (sad/happy) ")
if feeling == 'sad':
print(bad_responses[random.randint(0,1)])
else:
print ( good _ responses [ random . randint ( 0 , 3 ) ] )
print(f"It's been a nice ch. at time with you, { first _ name } ! " )
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
Need the answer ASAP!!!!!!!!
I’ll mark brainliest if correct
Drag each label to the correct location on the image. Match the correct component to the part on the flowchart
Procedure 1
subroutine
procedure 2
decision
input
End
Start

Answers
Answer:
i answerd this on a diffrent page
Explanation:
How large does a telsa coil need to be to transmit wireless electricity
Answers
The size of the largest operational Tesla Coil is measured to be 38ft or 12 meters. It transmits about 138kw of electricity.
What is a Tesla Coil?Nikola Tesla invented the Tesla coil, an electrical resonant transformer circuit, in 1891. It is used to generate high-voltage, low-current, high-frequency alternating current.
During his efforts to construct a "wireless" lighting system with gas discharge light bulbs that would shine in an oscillating electric field generated by a high voltage, high-frequency power source, Tesla devised the Tesla coil.
Tesla coils provide various health risks owing to high voltage radio frequency emission, including skin burns and nervous system and heart damage.
Learn more about Tesla Coil:
https://brainly.com/question/7295601
#SPJ1
who wants to play genshin?
Answers
Answer:
Sure! What server are you on tho?
Explanation:
Internal combustion engines use hot expanding gasses to produce the engine's power. Technician A says that some engines use spark to ignite the gasses. Technician B says some engines use compression to ignite the gasses. Who is correct?
Answers
Answer:
Explanation:
Both are right.
Engines are divided into:
1) Internal combustion engines
2) Diesels