Jacob holds a Computer Hacking Forensic Investigator (CHFI) certification. Which of the following responsibilities should Jacob have the ability to perform?
1 Measure ethical hacking
2 Identify intruder footprints
3 Develop cybersecurity law
4 Manage risk mitigation
Which of the following positions is suitable for a person who holds a Certified Information Systems Security Professional (CISSP) certification?
1 Chief Information Security Officer
2 Security or Network Architect
3 All of positions would be suitable
4 Director of Security
Which of the following cybersecurity frameworks strive to improve the infrastructure of an organization’s cybersecurity practices by providing standard methods and processes for combatting attacks?
1 SAFETY Framework
2 NIST Framework
3 Organization of Cybersecurity 27005
4 Payment Card Industry Data Security Standard (PCI DSS)
Answers
Answer:
the answers too the questions are B. identify intruder footprints,
D. Director of security, and B. Nist framework
Explanation:
Answer:
the answers too the questions are B. identify intruder footprints,
B. Nist framework D. Director of security,
Related Questions
When Eliza was first written (in 1966), some people thought it seemed human. Did Eliza seem human to you? Why or why not?

Answers
Answer:
yes she is a real person she had a son named Phil and her husband was alexander Hamilton he died in a duel with the vice president Aaron burr
there son died in a duel two so Eliza was just alone in the world with out her some and husband she ran a orphanage and saw all of the kids and it reminded her of Alex
Explanation:
Answer:
yeah shes human i refuse to think shes not
Explanation:
Which is the best approach to debugging?
A.
Don’t worry about it at all until after the program is written.
B.
Be sure the program will work perfectly before writing it.
C.
Anticipate errors before they happen, and find and fix errors that happen.
D.
Use an HTML encoder.
Answers
What is the name given to the parts of a computer that you can actually
touch?
Software
Computer Parts
Computer Case
Hardware
Answers
Answer:
Hardware
Explanation:
Hardware, is the parts of the computer that you can physically touch. Examples include, the keyboard and mouse.
Hope this helps. <3
Hardware is the name given to the parts of a computer that you can actually touch.
What is Hardware?
The physical components of a computer, such as its chassis, CPU, RAM, monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers, and motherboard, are referred to as computer hardware.
Software, on the other hand, is a collection of instructions that may be stored and executed by hardware. Software is referred to as "soft" because it is flexible, but hardware is referred to as "hard" because it is rigid in terms of modifications.
Software often instructs hardware to carry out any command or instruction. A useful computer system is one that combines hardware and software, while there are also systems that use simply hardware.
Therefore, Hardware is the name given to the parts of a computer that you can actually touch.
To learn more about Hardware, refer to the link:
https://brainly.com/question/15232088
#SPJ5
ANSWER ASAP GIVING BRAINIEST FIVE STAR AND HEART!
THIS IS 6TH GRADE TECHNOLOGY!
Please answer the following essay question:
What is the difference between a function and a formula? List an example of each.
Answer in paragraph form using 5-7 complete sentences.
Answers
Answer : A Formula is a method, statement, or procedure for achieving something, especially reconciling different aims or positions. A function is an activity or purpose natural to or intended for a person or thing. The difference between the two is a function is a piece of code that executes a predefined calculation, while a formula is something you create yourself.
Answer:
A Formula is a method, statement, or procedure for achieving something, especially reconciling different aims or positions. A function is an activity or purpose natural to or intended for a person or thing. The difference between the two is a function is a piece of code that executes a predefined calculation, while a formula is something you create yourself.
Explanation:
how do I start a private conversation?
Answers
Name 10 reasons why computers are better than other electronic devices? :)
Answers
windows 93 it is a website THE QUESTION IS WHAT IS THE FIRST THING THAT POPS UP WHEN YOU OPEN THE WEBSITE?
Answers
Answer:
A black screen with green text in the top left corner
Explanation:
Write the importance of software in computer . In 6 points
Answers
Answer:
Software is a set of instructions, data or programs used to operate computers and execute important tasks but can also help you work more efficiently.
Uses of Software
Uses of Software in Office.Uses of Software in Business.Uses of Software for Play Game.Uses of Software in Shop.Uses of Software for Entertainment.Explanation:
If computers can only understand binary code, how is it possible to create a program in Logo or Tynker?
by overriding the binary mechanism
by teaching the computer how to understand the new code
by using a translator to convert the block instructions to binary
by adding memory to the system
Answers
By using a translator to convert the block instructions to binary it is possible to create a program in Logo or Tynker. Thus option C is correct.
What is a binary code?
Because each bit only has a number of either one or 0, it cannot have any other number. The central processing unit (CPU) plus RAM of computers may store binary code, which is composed of digitized 1s and 0s, to gather.
Computers must use binary circuits for dependability considerations. The expressive potential of the binary circuits for use in Logo or Tynker is maximized by the incorporation of binary numbers in computers.
Featuring a range of interesting projects and modules, they are an excellent method to learn programming in general, including Python and Javascript in addition. Therefore, option C is the correct option.
Learn more about binary code, Here:
https://brainly.com/question/28222245
#SPJ2
Why is it recommended to develop a study plan? A. It tells you when your teacher is planning on giving the test. B. It helps you organize what you will study and when you will study to ensure you have enough time. C. It provides all of the information that your teacher will put on the test. D. It tells your Learning Coach when to help you study for your test.
Answers
Answer:
B. It helps you organize what you will study and when you will study to ensure you have enough time.
Plz answer correctly plz

Answers
Answer:
2.Counter
3. Accumulator
2counter
When the prompt function is used in JavaScript, _____ appears.
A.
an error message
B.
a pop-up box
C.
a data warning
D.
a password request
Answers
Answer:
B
Explanation:
instructs the browser to display a dialog with an optional message prompting the user to input some text, and to wait until the user either submits the text or cancels the dialog
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Which methods can be used to run a query? Check all that apply
On the Create tab, in the Queries group, click Run.
In query Design view, on the Design tab, click Run
Switch to Datasheet view before any other commands
Close the Show Table dialog box in the Datasheet view
On the Create tab, in the Queries group, click Create Query
Answers
Answer:
- In query Design view, on the Design tab, click Run
Explanation:
In Microsoft Acess computer program queries are used in order to preview and or modify data; mostly spreadsheet data.
For example, a query could be used to filter out the scores of students above 70% in an Exam. To run a query, the user should enable Design view, while on the Design tab, click on Run. At this point preferes query actions such as delete, copy etc could be executed.
Hope this helps
what is the meaning of the phrase "the risk for the sake of the profit?"
Answers
Answer:
Doing a risk in order to achieve the profit.
Explanation:
PLEASE HELP!!! What is one game you think would be hard for computers to play? (AI)
Answers
Answer:
I would say the game "Go" because it requires intuition to play.
Explanation:
Answer:
I dont play much games but probaly a game you need to think outside of the box for
Explanation:
robots arent creative
What is the purpose of the PC troubleshooting process? Select two answers. BRAINLIEST to who gets it right

Answers
Answer:
identify...
solve...
Explanation:
Troubleshooting is a form of problem solving, often applied to repair failed products or processes on a machine or a system.
Answer:
Identify Problems and Fix Broken Components
Explanation:
"Critical troubleshooting will automatically fix things like corrupt settings that keep critical services from running, make adjustments to work with your hardware, or make other specific changes required for Windows to operate with the hardware, apps, and settings you've selected." Cited from Microsoft Support's Website
Which involves more human input, basic algorithms, or machine learning?
Answers
Answer:
Machine learning
Explanation:
Machine learning involves more human input. Check more about machine learning below.
Does machine learning needs human input?Note that as long as AI technology is invoke and there are new applications that are made for AI to learn, AI will need to have human input.
Therefore, Machine learning involves more human input as AI. needs to learn more about humans so as to function well.
Learn more about human input from
https://brainly.com/question/24953880
#SPJ2
why would you use a custom filter?
Answers
Answer:By specifying conditions, you can create custom filters that narrow down the data in the exact way that you want. You do this by building a filter. If you've ever queried data in a database, this will look familiar to you. Point to either Number Filters or Text Filters in the list.
Explanation:
In 1 to 2 sentences, describe how to create a list with bullets
Answers
Answer:
To create a bulleted list:
Select the text you want to format as a list.
On the Home tab, click the drop-down arrow next to the Bullets command. A menu of bullet styles will appear.
Move the mouse over the various bullet styles. ...
The text will be formatted as a bulleted list.
Explanation:
~Hope this helps
Answer:
the person above is correct i got 100% give him brainly Est
Explanation:
Quick, answer this please! What happens if you answer bot questions with low points? Like they say they would give you 10+ points but they only have 5 points? I am afraid I might get h a c k e d
Answers
Answer:
Hello! I haven't been h a c k e d yet so I'm pretty sure its safe.
Explanation:
Lol fortnite really going UwU and anime
First buff cat aka. Meowscles
Then Anime girl aka. Lexa
But tbh i like anime more but meowscles is one of my favortite skins, and lexa is also one of my favorite skins
Answers
Answer:
epic
Explanation:
Answer:
le epic
Explanation:
PLEASE HELP ME Write a 150-word paragraph about five of the zaniest and/or most novel ways you’ve found online that people earn incomes. Keep in mind that the sites should not be corporate sites. We are looking for unique niches. Have fun. We think you will be surprised when you see what people are willing to pay for online.
Answers
Answer: Disney and video games winning ratings can produced a vast amount of money, making into a job, that anyone could create for example becoming an actor or becoming a gamer.
we could go over the amount of time disney and other companies spent.
what are some basic commands to remember in terminal? windows 10
please help if you know
Answers
Answer:
If you just need a few, maybe this can help.
Explanation:
Cat - The cat command means 'Concatenate'. It prints the contents of a file or files to stdout. It's frequently used in Linux commands.
Touch - Using the 'Touch' command, you can create a file, or possibly just modify or generate a timestamp.
Move - The 'mv' command stands for 'Move'. As the name says, we can use this command to move files and directories from one place to another.
Chsh - The chsh command changes a user's login shell attribute. If you want to change the shell of another user, execute the command with root permissions.
Sudo - 'Sudo', or 'super user do', is a command that allows you to elevate your user privileges while executing the command to administrator privileges.
Most files in Windows are associated with a specific program that is assigned to open the file by default. At times, remembering these associations can become confusing. You can remind yourself by entering the command assoc to display a full list of filename extensions and program associations. You can also extend the command to change file associations. For example, assoc .txt= will change the file association for text files to whatever program you enter after the equal sign. The assoc command itself will reveal both the extension names and program names, which will help you properly use this command.
In Windows 10, you can view a more user-friendly interface that also lets you change file type associations on the spot. Head to Settings (Windows + I) > Apps > Default apps > Choose default app by file type
2.Cipher
Deleting files on a mechanical hard drive doesn't really delete them at all. Instead, it marks the files as no longer accessible and the space they took up as free. The files remain recoverable until the system overwrites them with new data, which can take some time. The cipher command, however, lets you wipe a directory on an NTFS-formatted volume by writing random data to it. To wipe your C drive, for example, you'd use the cipher /w:d command, which will wipe free space on the drive. The command does not overwrite undeleted data, so you will not wipe out the files you need by running this command.
When you run the cipher command by itself, it returns the encryption state of the current directory and the files it contains. Use cipher /e: to encrypt a file, cipher /c: to retrieve information about encrypted files, and cipher /d: to decrypt the selected file. Most of these commands are redundant with the Windows encryption tool BitLocker.
3.file Compare
You can use this command to identify differences in text between two files. It's particularly useful for writers and programmers trying to find small changes between two versions of a file. Simply type fc and then the directory path and file name of the two files you want to compare.
You can also extend the command in several ways. Typing /b compares only binary output, /c disregards the case of text in the comparison, and /l only compares ASCII text.
So, for example, you could use the following:
fc /l "C:\Program Files (x86)
The above command compares ASCII text in two Word documents.
4.Ipconfig
This command relays the IP address that your computer is currently using. However, if you're behind a router (like most computers today), you'll instead receive the local network address of the router.
Still, ipconfig is useful because of its extensions. ipconfig /release followed by ipconfig /renew can force your Windows PC into asking for a new IP address, which is useful if your computer claims one isn't available. You can also use ipconfig /flushdns to refresh your DNS address. These commands are great if the Windows network troubleshooter chokes, which does happen on occasion.
5.Netstat
Entering the command netstat -an will provide you with a list of currently open ports and related IP addresses. This command will also tell you what state the port is in; listening, established, or closed.
This is a great command for when you're trying to troubleshoot devices connected to your PC or when you fear a Trojan infected your system and you're trying to locate a malicious connection.
6.Ping
Sometimes, you need to know whether or not packets are making it to a specific networked device. That's where ping comes in handy.
Typing ping followed by an IP address or web domain will send a series of test packets to the specified address. If they arrive and are returned, you know the device is capable of communicating with your PC; if it fails, you know that there's something blocking communication between the device and your computer. This can help you decide if the root of the issue is an improper configuration or a failure of network hardware.
7.PathPing
This is a more advanced version of ping that's useful if there are multiple routers between your PC and the device you're testing. Like ping, you use this command by typing pathping followed by the IP address, but unlike ping, pathping also relays some information about the route the test packets take.
Name the video game character (first), and I will give you brainliest.

Answers
The character is........
Baller
Answer:Baller
Explanation:
it became a meme
Part 1: Compare the Websites
You are conducting research for a project about elephant sanctuaries. Compare the two websites using the 5 W’s criteria for reliability and validity. For each website, complete the 5 W’s Checklist.
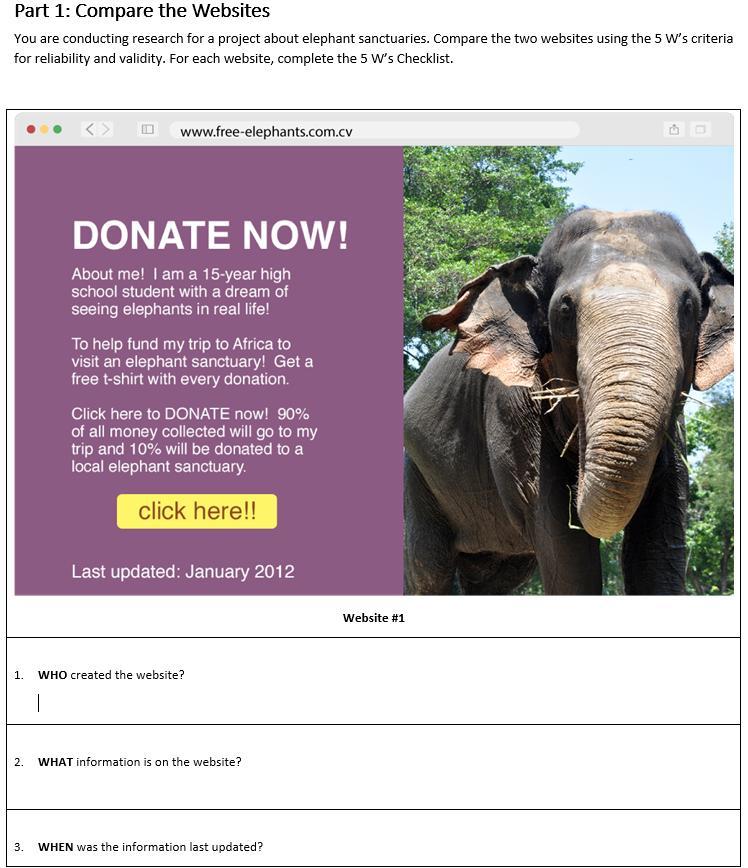




Answers
Answer:
WHO: a 15-year old high school student
WHAT: information about donating to a local elephant sanctuary and a trip
WHEN: January 2012
WHERE: www.free-elephants.com.cv
WHY: To help fund the student's trip to Africa to visit an elephant sanctuary
who: a 15-year-old high school student
what: information about donating to a local elephant sanctuary and a trip
when: January 2012
where: www.free-elephants.com.cv
why: To help fund the student's trip to Africa to visit an elephant sanctuary
You can find this out on Brainly! Recycling one glass jar saves enough energy to watch television for _ hours It's one of the fun facts!
Answers
Recycling one glass jar saves enough energy to watch television for 3 hours.
How do you code things to make shapes out of them and add color
Answers
Answer:
go to KhanAcademy and search "Coloring with code" and it should be the first thing at the top
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!