#include
#include
#include
using namespace std
int main()
{
x;
Stack< int, vector<> > iStack;
for (x = 2; x < 8; x += 2)
{
cout << "Pushing " << << endl;
.push(x);
}
cout << "The size of the stack is ";
cout << iStack.() << endl;
for (x = 2; x < 8; x += 2)
{
cout << "Popping " << iStack.() << endl;
iStack.pop();
}
Answers
It seems that the code snippet you provided is incomplete and contains some errors. I assume that you are trying to use a stack data structure from the `<stack>` library in C++.
Here's an updated version of the code with corrections and explanations:
```cpp
#include <iostream>
#include <stack>
#include <vector>
int main() {
int x;
std::stack<int, std::vector<int>> iStack;
for (x = 2; x < 8; x += 2) {
std::cout << "Pushing " << x << std::endl;
iStack.push(x);
}
std::cout << "The size of the stack is " << iStack.size() << std::endl;
for (x = 2; x < 8; x += 2) {
std::cout << "Popping " << iStack.top() << std::endl;
iStack.pop();
}
return 0;
}
```
Explanation:
- The `<iostream>` library is included for input/output operations.
- The `<stack>` library is included for using the stack data structure.
- The `<vector>` library is included for providing the underlying container for the stack.
- `std::stack<int, std::vector<int>> iStack;` declares a stack `iStack` that holds integers, using a `vector` as the underlying container.
- The first loop `for (x = 2; x < 8; x += 2)` pushes even numbers (2, 4, 6) onto the stack using `iStack.push(x)`.
- The second loop `for (x = 2; x < 8; x += 2)` pops the elements from the stack using `iStack.top()` to access the top element and `iStack.pop()` to remove it.
- The size of the stack is printed using `iStack.size()`.
- `std::cout` is used for outputting the messages to the console.
Make sure to include the necessary header files (`<iostream>`, `<stack>`, `<vector>`) and compile the code using a C++ compiler.
To know more about header files, click here:
https://brainly.com/question/30770919
#SPJ11
Related Questions
Which element is represented by the electron configuration in example B? Example B: 1s22s22p63s23p64s1 Aluminum Cesium Potassium Arsenic
Answers
Answer:
Potassium
Explanation:
potassium because all of the others are being used and potassium is not being used in example b
Answer:
It is potassium.
Explanation:
I just took the quiz and it was right.
how graphical representation of spreadsheet data can be helpful in business
Answers
Answer: Business graphs are visual aids used to analyze data. They can make comparing multiple sets of data much easier, as sometimes trends and relationships are easily identified on the chart or graph. They also help to show the audience the data in a way that is easy to understand and remember.
Explanation:
An array named Ages holds 10 different ages. Write pseudo-code to increase each age in the array by one. The Ages array should be initialised as follows:
Answers
Answer:
Ages = [12, 15, 20, 18, 25, 30, 40, 32, 28, 50]
for i = 0 to 9 do
Ages[i] = Ages[i] + 1
end for
Explanation:
The above code initializes the Ages array with 10 different ages. The for loop iterates through the array, and for each element, it increases its value by 1. The loop starts at index 0 and goes up to index 9, which are the indices of the 10 elements in the array. After the loop completes, the Ages array will contain the original ages increased by 1.
Question # 1 Multiple Select Which of the following shows the assignment of a string to a variable? Select 3 options. answer = "23" answer = (23) answer = '23' answer 23 answer = input("How old are you?")
Answers
Answer:
answer = input("How old are you?")
Explanation:
Answer is a variable The Input function takes a string
Answer:
answer = input("How old are you? ")answer = '23'answer = "23"Explanation: Correct on Edg 2020/2021.
what is not an example of a job skill
Answers
Being dishonest, irresponsible and unpunctual.Answer:
Explanation:
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
what are the difference among the whole note, half note and quarter note ? (this is music)
Answers
Answer:
The second note in is called the half note and held for two counts — half a whole note. Notice it has a stem attached to it. ... The quarter note is the third note; it looks like a filled-in half note, with the same stem attached. You hold it for one full count, which is a quarter of a whole note.
Explanation:
3.5 code practice
grade = str(input("What year of high school are you in?: "))
if ("grade ==Freshman"):
print("You are in grade: 9")
elif ("grade == Sophomore"):
print("You are in grade: 10")
elif ("grade == Junior"):
print("You are in grade: 11")
elif ("grade == Senior"):
print("You are in grade: 12")
else:
print("Not in High School")
It keeps printing your are in grade 9. Why?
Answers
The fixed code is shown below. input() function already returns string that's why you don't have to convert string again. Also the syntax in if-else scope is wrong.
grade = input("What year of high school are you in?: ")
if(grade.lower()=="freshman"):
print("You are in Grade 9.")
elif(grade.lower()=="sophomore"):
print("You are in Grade 10.")
elif(grade.lower()=="junior"):
print("You are in Grade 11.")
elif(grade.lower()=="senior"):
print("You are in Grade 12.")
else:
print("Wrong input!")
Please helpppppppppppppppppp please I’m stuck!

Answers
do u know thw muffin man
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
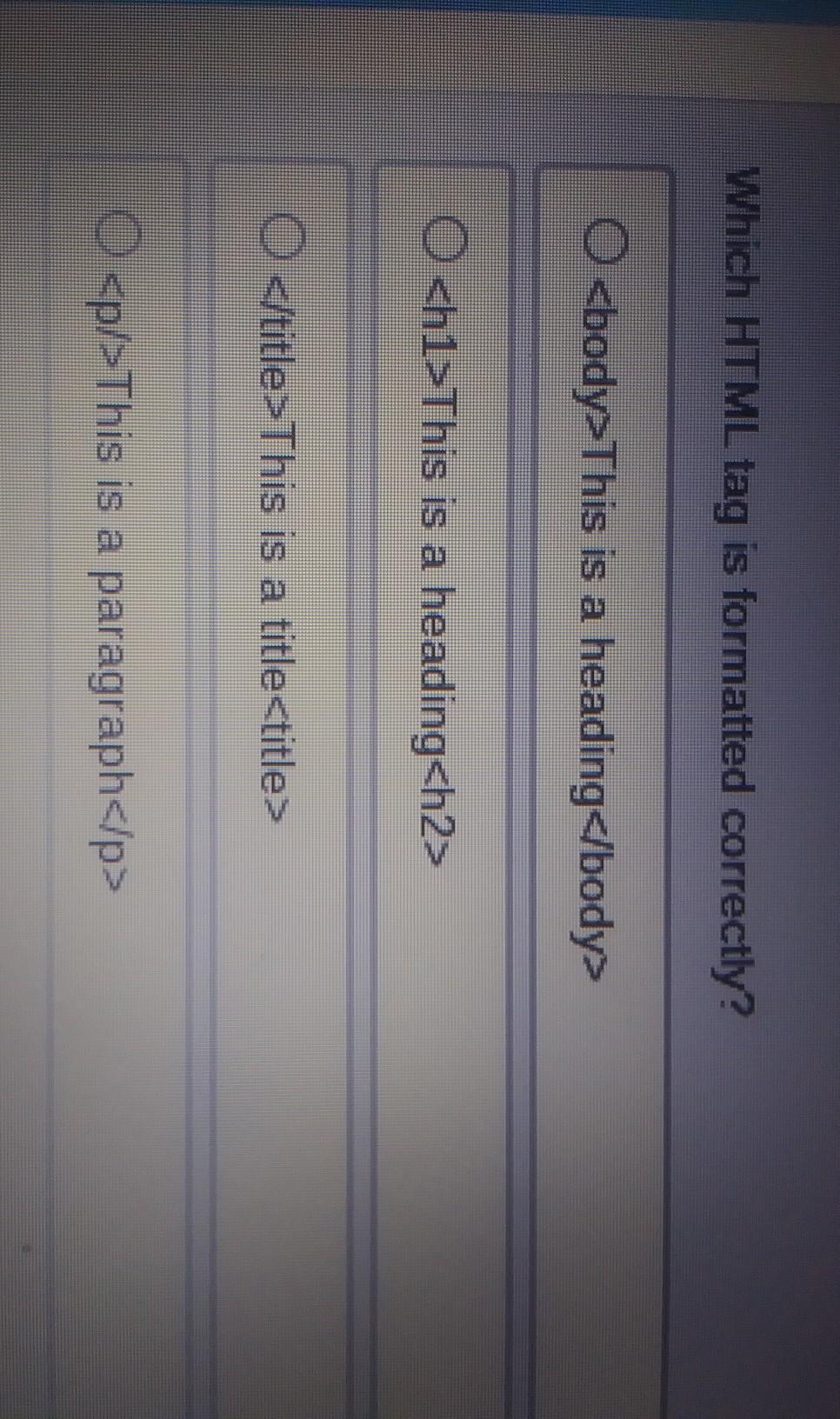
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
Which arrangement is most common for printed texts?

Answers
Headings in a sans-serif font and text in a serif font
What are fonts ?
A collection of typography or text characters in a certain style and size that may be printed or displayed is referred to as a font.
There are four major font types:
- serif
- sans serif
- script
- monospaced
Therefore, headings in a sans-serif font and text in a serif font.
You can learn more about fonts from the given link
https://brainly.in/question/22063729
#SPJ13
with a two-phase commit strategy for synchronizing distributed data, committing a transaction is faster than if the originating location were able to work alone. T/F
Answers
The statement "With a two-phase commit strategy for synchronizing distributed data, committing a transaction is faster than if the originating location were able to work alone" is False.
A two-phase commit strategy is used to ensure data consistency across distributed systems, but it introduces additional communication and coordination overhead. This can result in a slower transaction commitment process compared to a single-node system where the originating location works alone.
The two-phase commit protocol involves two phases: the prepare phase and the commit phase. In the preparation phase, all participants in the distributed transaction agree to commit or abort the transaction. If all participants vote to commit, then the commit phase is initiated, and the transaction is committed at all locations. However, if any participant votes to abort or if a failure occurs during the process, the transaction is aborted.
The two-phase commit protocol adds coordination and communication overhead, which can introduce delays compared to a single location working alone. The purpose of this protocol is to provide a reliable and consistent outcome for distributed transactions, ensuring that all participants reach a consensus on the transaction's outcome.
Learn more about the communication:
https://brainly.com/question/28153246
#SPJ11
What information can you gather from a Whois search?
Passive or active?
Answers
A Whois search is an active search that gathers information about a domain name or IP address.
The information that can be gathered using a Whois search includes the name and contact information of the domain owner, the domain registration and expiration dates, the domain registrar, and the DNS servers associated with the domain. This information can be helpful for identifying the owner of a website, determining the legitimacy of a domain, and resolving issues related to domain ownership or registration.
A Whois search is an active tool, as it sends queries to Whois servers to obtain information about a domain name. However, some registrars and domain privacy services may restrict the amount of information available through Whois searches.
To learn more about Whois database visit : https://brainly.com/question/14704109
#SPJ11
System software consists of programs that support day-to-day business functions and provide users with the information they require. _________________________
Answers
System software refers to the programs that support everyday business functions and provide users with the information they need. It is primarily responsible for managing the computer's hardware components and allowing the application software to communicate with them.
The three main types of system software are operating systems, device drivers, and utility software.
Operating System (OS): It's a type of system software that controls and manages computer hardware, software resources, and offers common services for application software. It also manages memory allocation, file management, process management, security, and other critical system activities. Some popular examples of operating systems are Windows, MacOS, and Linux.Device Drivers: They are software programs that enable the operating system to communicate with various hardware devices like printers, scanners, keyboards, and monitors. Without device drivers, an operating system cannot work with hardware, and it's useless. Device drivers can either come with the operating system, or users may need to install them separately.Utility Software: It's a type of system software that provides additional capabilities to the operating system and the user. These programs perform various tasks like disk management, backup, data compression, antivirus scanning, and system maintenance. Examples of utility software are antivirus programs, file managers, and disk defragmenters.System software is a crucial component of a computer system. It's responsible for managing hardware, enabling communication between application software and hardware, and providing additional capabilities to the user. The main types of system software are operating systems, device drivers, and utility software.
To learn more about System software, visit:
https://brainly.com/question/30914363
#SPJ11
1. by default, web servers listen for http requests at port . a. 110 b. 80 c. 443 d. 53 2. which of the following is a parameter that can be configured for a rule in windows firewall with advanced security? (choose all that apply.) a. remote port b. protocol c. source ip address d. program 3. the diagnose/repair function of windows firewall with advanced security allows users to troubleshoot which of the following components? (choose all that apply.) a. network adapter b. shared folders c. web browser d. internet connections 4. the main mode and quick mode nodes under the security associations node in windows firewall with advanced security are related to the protocol. a. ipsec b. icmp c. https d. http 5. by default, the remote desktop protocol is blocked by windows firewall with advanced security in windows 10. true or false
Answers
Question 1.
By default, web servers listen for http requests at port b) 80.
Question 2.
The following are parameters that can be configured for a rule in Windows Firewall with Advanced Security: remote port, protocol, source IP address, and program.
Question 3.
The diagnose/repair function of Windows Firewall with Advanced Security allows users to troubleshoot the a) network adapter and d) internet connections.
Question 4.
The main mode and quick mode nodes under the security associations node in Windows Firewall with Advanced Security are related to the a) IPsec protocol.
Question 5.
False, by default, Remote Desktop Protocol is not blocked by Windows Firewall with Advanced Security in Windows 10.
What are the features of HTML?HTML (Hypertext Markup Language) has the following features:
Text Markup: HTML is a markup language that is used to format text with unique features, such as headings, fonts, and colors. HTML is used to make it simple for search engines to scan your website or blog.Web Standards: HTML is a coding language that is used to build websites that are compliant with web standards, such as CSS and JavaScript. HTML is one of the basic elements of web design and must be used in conjunction with other technologies such as CSS and JavaScript for best results.Dynamic Web Design: HTML provides the foundation for creating dynamic websites, which are websites that are interactive and engage with their audiences. HTML is the foundation for creating content that can be seen and interacted with by users across a variety of devices.Learn more about HTML at
https://brainly.com/question/17959015
#SPJ11
how many 2/8 pound patties can she make from 7/8 of a pound of hamburger
Answers
Answer:
3/8
Explanation:
Because 2 can't go into 7, the next best thing is 6, so 2x3 is 6 with 1/8 left over~~~~~hope this helps :) pls brainlist
1 Choose whether each of the following statements is true or false:
A An environment is monitored so that it can be controlled.
B
An environment that is controlled must be monitored.
C
A sensor is used to monitor a system.
D
A sensor must be recording data continuously.
E
An actuator is used to control an environment or a system.
F
If a sensor detects a problem in a controlled environment, it must send a signal to the
actuator to correct the problem.
Answers
The answer response are:
A. An environment is monitored so that it can be controlled. -True
B. An environment that is controlled must be monitored.- False
C.A sensor is used to monitor a system.- True
D. A sensor must be recording data continuously.-False
E. An actuator is used to control an environment or a system.-True
F. If a sensor detects a problem in a controlled environment, it must send a signal to the actuator to correct the problem.- True
What is the environment about?A. An environment is monitored so that it can be controlled - This statement is true. Monitoring an environment involves collecting data about its conditions and parameters, which is then used to control it. By monitoring the environment, the control system can adjust it to maintain desired conditions.
B. An environment that is controlled must be monitored - This statement is false. It is possible to control an environment without monitoring it. For example, a control system could be programmed to make certain changes based on a set schedule, without monitoring the environment to see if it needs adjustment.
C. A sensor is used to monitor a system - This statement is true. Sensors are devices that collect data about an environment or system, which is used to monitor it. They provide information about temperature, humidity, pressure, and other physical conditions that can be used to control the environment.
Learn more about sensor from
https://brainly.com/question/28068549
#SPJ1
If you want to create a new line within a cell, press the ____ keys to move the insertion point to the next line within the cell.
Answers
If you want to create a new line within a cell, press the ALT + ENTER keys to move the insertion point to the next line within the cell.
What is a cell in a spreadsheet?A cell in a spreadsheet is a rectangular box formed by the intersection of horizontal lines and vertical lines where it divides the spreadsheet into rows and columns. The cells are identified by the reference or cell name or cell address. Columns will be named by the alphabet and rows will be named by the numbers.To learn more about Cell in spreadsheet refer to:
https://brainly.com/question/26728357
#SPJ2
When you right-click a picture in a word processing program, which actions can you choose to perform on that image?
You can choose to
an image when you right-click the picture in the word processing program. You can also choose to
an image when you right-click the picture in the word processing program
Answers
Answer:
Lots to choose from such as "copy" or "crop"

Write 4 types of viruses , explain them briefly.
Answers
I can help with two.
Web Scripting Virus, A sneaky virus that targets popular websites. What this virus does is overwrite code on a website and insert links that can install malicious software on your device. Web scripting viruses can steal your cookies and use the information to post on your behalf on the infected website.
FILE INFECTOR, targeting executable files (.exe), file infector viruses slow down programs and damage system files when a user runs them.
anyone pls answer this!!!!!!thanks ^-^

Answers
Answer:
True
False
False
False
Explanation:
HTML isnt a scripting a scripting language it's a markup language
There are 6 levels of HTML
An empty tag only has a starting tag
who invited talbulating machine
Answers
Answer:
Herman Hollerith
brainliest please?
Explanation:
Herman Hollerith was an American businessman, inventor, and statistician who developed an electromechanical tabulating machine for punched cards to assist in summarizing information and, later, in accounting
Answer:
HERMAN HOLLERITH
(born February 29, 1860, Buffalo, New York, U.S.—died November 17, 1929, Washington, D.C.)
American inventor of a tabulating machine that was an important precursor of the electronic computer.
During the 1880s the engineer Herman Hollerith devised a set of machines for compiling data from the United States Census called as the talbulating machine
Explanation:
brainliest plz
What is another way to ensure maximum protection and prevent the accidental deletion of a preserved version?
Answers
Another way to ensure maximum protection and prevent the accidental deletion of a preserved version is by implementing a backup and recovery system. This system creates regular backups of the preserved version, allowing for easy restoration in case of accidental deletion or loss.
Here are the steps to set up a backup and recovery system:
1. Choose a reliable backup solution: Research and select a backup solution that meets your needs. Look for features like automatic backups, versioning, and secure storage. 2. Schedule regular backups: Set up a schedule for automatic backups. Depending on the frequency of changes to the preserved version, you can opt for daily, weekly, or monthly backups.
3. Store backups securely: Ensure that the backups are stored in a secure location, preferably off-site or on cloud storage. This protects against physical damage or loss. 4. Test the backup process: Periodically test the backup and recovery system to ensure it is working correctly. This involves restoring a backup version and verifying its integrity.
5. Implement access controls: Restrict access to the preserved version and the backup system to authorized personnel only. This reduces the risk of accidental deletion or unauthorized modifications. By implementing a backup and recovery system with regular backups, secure storage, and access controls, you can ensure maximum protection and prevent the accidental deletion of a preserved version.
To know more about recovery visit:
https://brainly.com/question/33225786
#SPJ11
some portion of cache system a represented below. the system is byte-addressable and the block size is one word (4 bytes). the tag and line number are represented with a binary numbers. the contents of words in the block are represented with hexadecimal. tag line number word within block 00 01 10 11 10 1000 0100 1001 0110 1101 2016 6116 c116 2116 10 1000 0100 1001 0110 1110 3216 7216 c216 d216 10 1000 0100 1001 0110 1111 4216 8216 4116 a216 10 1000 0100 1101 0111 0000 e216 9216 5216 b216 1. what is the size of the main memory of this system?
Answers
To determine the size of the main memory in this cache system, we need to first look at the tag and line number bit sizes. From the given table, we can see that the tag is 2 bits and the line number is also 2 bits. This means that the cache has 4 lines (2^2).
Next, we need to determine the block size which is given as one word or 4 bytes. Therefore, each block in the cache consists of 4 words or 16 bytes (4 bytes/word x 4 words/block).
Since each line in the cache consists of one block, the size of each line is 16 bytes. And since there are 4 lines in the cache, the total size of the cache is 64 bytes (16 bytes/line x 4 lines).
However, the size of the main memory is not provided in the given information. Without additional information, we cannot determine the size of the main memory in this system.
To know more about cache system visit:
https://brainly.com/question/32266160
#SPJ11
1. Computer Hardware can consist of a
A. monitor, mouse, applications, games
B. keyboard, mouse, operating system
C. monitor, keyboard, CPU and mouse
D. monitor, operating system, applications
Answers
Answer:
C. monitor, keyboard, CPU and mouse.
Explanation:
Computer hardware refers to the physical components of a computer system that can be touched and seen. Some of the major hardware components of a computer include:
Monitor: A display screen that shows the output of the computer.
Keyboard: An input device used for typing and entering data into the computer.
CPU (Central Processing Unit): The "brain" of the computer that processes instructions and performs calculations.
Mouse: An input device used for navigating and interacting with the computer.
Option A is incorrect because a monitor and a mouse are hardware components, but applications and games are software components that run on the hardware. Option B is incorrect because an operating system is software, not hardware. Option D is incorrect because applications and an operating system are software components, not hardware.
Having sound enhances your App, do you agree with this? Explain.
Answers
Answer:
Yes, it does.
Explanation:
I mean, having some sort of audio feedback is obviously useful for a user.
(If it's a media-content-viewer, of course you need sound)
We should discuss some cases here:
1. In case it's a game, sound enhances the experience of the virtual world, by creating what is called an "ambience", or the acoustical surroundings of the environment since you can perceive stuff without the need to look at it.
2. Other apps: It makes the app seem more friendly and comfortable to use, especially if partnered with an animation
In programming && is considered an arithmetic operator. True/False.
Answers
In programming && is considered an arithmetic operator---- False. The double ampersand operator && is considered a logical operator rather than an arithmetic operator when used in programming.
Which logical operator is it?A type of operator that is utilized in programming to carry out logical operations on one or more Boolean values or expressions is known as a logical operator. Based on the evaluation's outcome, these operators are used to evaluate conditions and direct program execution.
The three primary logical operators are:
The AND (&&) operator evaluates to true in programming when both of its operands are true, and to false otherwise.
The OR (||) operator, on the other hand, evaluates to true only if both of its operands are false, and to true only if at least one of its operands is true.
The WRONG operator negates its operand's value. These operators are used to control a program's flow and evaluate logical expressions.
For logical AND operations on two Boolean values or phrases, programmers use the logical operator && (double ampersand). It returns true if both operands are true; If not, it will return false. It is not regarded as an operator in mathematics.
Mathematical operations like addition, subtraction, multiplication, division, and modulus are carried out with the help of arithmetic operators. +, -, *, /, and % are some common arithmetic operators used in programming languages.
Therefore, the assertion that the programming operator && is an arithmetic operator is incorrect because it is a logical operator. Arithmetic operators are used to perform mathematical operations on numerical values, whereas logical operators are used to evaluate logical expressions and control program flow.
Learn more about logical operator:
brainly.com/question/13382096
#SPJ4
when you save a microsoft office file to onedrive, where are you saving it?
Answers
Answer:
You're saving it to your personal OneDrive folder and uploading it to the OneDrive servers.
Explanation:
(True or False) When you set styles in the Pages Properties dialog box, they will overwrite styles in an external style sheet?
Answers
Answer:
That will be True.
Explanation:
similar to home electricity use, the cloud allows organizations to dynamically increase and decrease programmatically so that they only pay for the resources that they actually use. this is because cloud use is ____.
Answers
Depending on the intended meaning, the sentence might have a number of different ends, making it incomplete. Here are some potential resolutions:
"This is because cloud utilization is elastic." Elasticity is the capacity of a system to scale up or down rapidly and automatically in response to variations in demand. Cloud service providers offer elastic computing resources that can be deployed and deprovisioned on-demand and programmatically, such as virtual machines, containers, and storage. As a result, businesses may scale up or down their apps and services as necessary without having to buy and maintain their own physical infrastructure. The resources they use can be metered and invoiced by the hour or by the minute, and they only pay for what they use. This is because using the cloud.
learn more about Cloud here:
https://brainly.com/question/29531817
#SPJ4