in cryptography a key is a random data that is used as an additional input to a one-way function that hashes data such as passwords. t/f
Answers
A key is a string of characters that is used within an encryption algorithm to alter data so that it appears random, So the given statement is true.
What is key in an encryption algorithm?A random string of bits generated specifically to scramble and unscramble data is what an encryption key is. Encryption keys are generated using algorithms that ensure each key is unique and unpredictable. The longer the key is constructed in this manner, the more difficult it is to crack the encryption code.A hash function accepts as input a key that is associated with a datum or record and is used to identify it to the data storage and retrieval application. The keys can be of fixed length, such as an integer, or variable length, such as a name. In some cases, the datum itself is the key.Hash entries are frequently referred to as key-value pairs. This results in a data associative representation.To learn more about encryption refer to :
https://brainly.com/question/4280766
#SPJ4
Related Questions
(6-7) Question 1: Use a create table statement to create a new copy of the 1_employees table, with a new name of course. Then use an insert statement with a select clause to copy all the data from the 1_employees table to your new copy of the table. create table copy_of_employees as select EMPLOYEE_ID, FIRST_NAME, LAST_NAME, DEPT_CODE, HIRE_DATE, CREDIT_LIMIT, PHONE_NUMBER, MANAGER_ID from l_employees; INSERT INTO copy_of_employees SELECT * FROM l_employees; SELECT * FROM copy_of_employees;
Answers
Answer:
The SQL query is used to create a copy of a table like the 1_employee table in the SQL database.
Explanation:
create table copy_of_employees as select EMPLOYEE_ID, FIRST_NAME, LAST_NAME, DEPT_CODE, HIRE_DATE, CREDIT_LIMIT, PHONE_NUMBER, MANAGER_ID from l_employees;
INSERT INTO copy_of_employees SELECT * FROM l_employees;
SELECT * FROM copy_of_employees;
This SQL creates a table called copy_of_employees and copies the selected query of the 1_employees table and inserts it to the newly created table.
Which of the following is the correct binary representation of the number 2?
Answers
Answer:
10 i think
Explanation:
A stack is a ___________________ data structure.
Answers
Answer:
A stack is a base data structure.
Match List
Match the function to its purpose.
square root
an approximation of 7
greatest common divisor of two integers
:: sqrt()
#pi
::gcd(0)
Answers
square root:: sqrt()
an approximation of 7#pi
greatest common divisor of two integers::gcd(0)
why do you think errors in spreadsheet models go undetected? What can you do to minimize the risk of spreadsheet errors?
Answers
There are several reasons why errors in spreadsheet models go undetected. One reason is that people often rely too heavily on the accuracy of the formulas and functions built into the software, assuming that they are infallible.
To minimize the risk of spreadsheet errors, it is important to take a number of steps. These include thoroughly testing the spreadsheet model, ideally using an independent reviewer who can check for errors and inconsistencies.
There are several reasons why errors in spreadsheet models go undetected. One reason is that people often rely too heavily on the accuracy of the formulas and functions built into the software, assuming that they are infallible.
Additionally, spreadsheets can be complex, with many interdependent variables and calculations, which can make it difficult to identify errors. Another issue is that spreadsheet models are often developed by individuals who may not have adequate training or knowledge in proper spreadsheet design and use.
To minimize the risk of spreadsheet errors, it is important to take a number of steps. These include thoroughly testing the spreadsheet model, ideally using an independent reviewer who can check for errors and inconsistencies.
Additionally, it is important to follow best practices when designing spreadsheets, including using consistent formatting and naming conventions, clearly labeling inputs and outputs, and documenting all calculations and assumptions. Regularly reviewing and updating the spreadsheet model, and training users on proper spreadsheet use and best practices can also help to minimize the risk of errors.
Ultimately, a diligent approach to spreadsheet design and use, combined with robust testing and review processes, can help to reduce the likelihood of errors and ensure the accuracy and reliability of spreadsheet models.
For more such questions on spreadsheet, click on:
https://brainly.com/question/29510368
#SPJ11
Nicole is in a study group to prepare for a test on plant biology, a subject she knows a lot about. During their meetings, she always comes prepared, helps other students, does most of the talking, and handles all of the tasks. What does Nicole need to do to make the study group more effective?
Answers
Answer:
B
Explanation:
She did all of the work so the other students wherent able to do anything
The thing that Nicole needs to do to improve the study group is to involve others and give them tasks.
What is a Study Group?This refers to the collection of persons that forms a group with the aim of learning and revising together.
Hence, we can see that because Nicole does most of the tasks in the study group for the test on plant biology, she would have to involve the other students so they would handle some of the work.
Read more about study groups here:
https://brainly.com/question/23779014
#SPj2
Which core business etiquette is missing in Jane
Answers
Answer:
As the question does not provide any context about who Jane is and what she has done, I cannot provide a specific answer about which core business etiquette is missing in Jane. However, in general, some of the key core business etiquettes that are important to follow in a professional setting include:
Punctuality: Arriving on time for meetings and appointments is a sign of respect for others and their time.
Professionalism: Maintaining a professional demeanor, dressing appropriately, and using appropriate language and tone of voice are important in projecting a positive image and establishing credibility.
Communication: Effective communication skills such as active listening, clear speaking, and appropriate use of technology are essential for building relationships and achieving business goals.
Respect: Treating others with respect, including acknowledging their opinions and perspectives, is key to building positive relationships and fostering a positive work environment.
Business etiquette: Familiarity with and adherence to appropriate business etiquette, such as proper introductions, handshakes, and business card exchanges, can help establish a positive first impression and build relationships.
It is important to note that specific business etiquettes may vary depending on the cultural and social norms of the particular workplace or industry.
Which of the following areas of a PivotTable field list enables you to display average values?
VALUES AreaField buttonPivotTable Fields panePivotTable
Answers
The VALUES Area of a PivotTable field list enables you to display average values.
In a PivotTable, the VALUES Area is the area where you can choose the calculations or summary functions that you want to use for your data. By default, the VALUES Area will display the sum of the values for each category, but you can change this to display other summary functions, such as the average, count, or maximum value. To display average values in the VALUES Area, you would simply click on the drop-down arrow next to the field that you want to change, and then select "Average" from the list of options. This will change the summary function for that field to display the average value for each category.
Learn more about PivotTable here: https://brainly.com/question/27813971
#SPJ11
Which of the following policy guidelines specifies the restrictions on user access
regarding access to read, write, execute, or delete permissions on the system?
Least privilege
Accountability
Default use
Specific duties
Answers
The policy guidelines that specifies such restrictions on user access can be referred to as: A. Least privilege.
What is the Least Privilege Principle?
The least privilege principle can be described as a concept in information security and policy guidelines that gives a user minimum permission or levels of access that they are needed to execute a tasks.
Therefore, the policy guidelines that specifies such restrictions on user access can be referred to as: A. Least privilege.
Learn more about least privilege on:
https://brainly.com/question/4365850
T/F : cyberbullying is a person within the organization who is trusted to monitor, contribute, filter, and guide the social media presence of a company, individual, product, or brand.
Answers
Sending, uploading, or disseminating unfavorable, hurtful, or nasty content about someone else is considered cyberbullying.
What does about cyberbullying provide as an example?Constantly sending a classmate unpleasant messages via instant message is one example of "cyberbullying." uploading embarrassing photos of classmates without their consent, utilizing email to spread rumors about pupils at school.Sending, uploading, or disseminating unfavorable, hurtful, or nasty content about someone else is considered cyberbullying. It can involve disclosing sensitive or private information about another individual in a way that causes embarrassment or humiliation. Some forms of cyberbullying go too far and become illegal or criminal.Sending, uploading, or disseminating unfavorable, hurtful, or nasty content about someone else is considered cyberbullying. It can involve disclosing sensitive or private information about another individual in a way that causes embarrassment or humiliation.To learn more about cyberbullying refer to:
https://brainly.com/question/1460915
#SPJ1
Mission statement base on shoes company ? Help me
Answers
Here are 2 examples:
- Bringing comfortable walking, running, biking, and adventuring to the world.
- Transforming the way you live your life, two soles at a time.
A mission statement should be focused on what a company is about at its core roots. What's the driver for why the company does what it does? Often it is related to why a company is relevant in its industry.
Help please!, explain what is missing and what needs to be changed if anything.
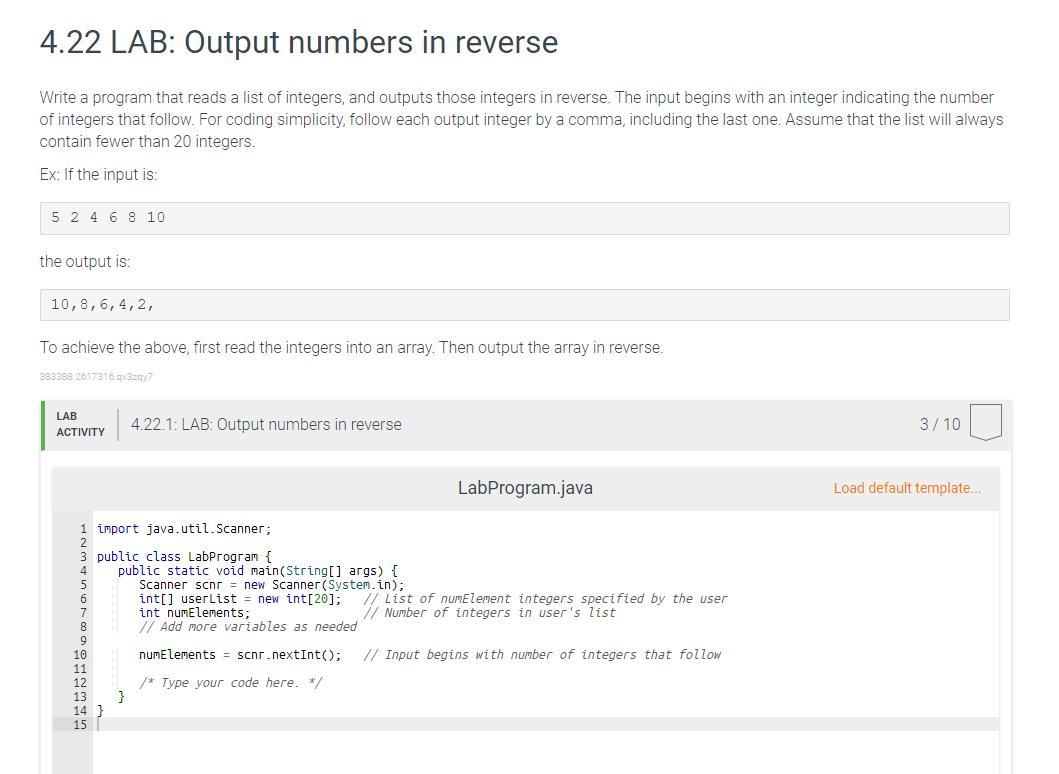
Answers
Using the computer language in JAVA to write a function code that output numbers in reverse
Writting the code in JAVA:import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int[] userList = new int[20];
int numElements;
numElements = scnr.nextInt();
for (int i = 0; i < numElements; ++i) {
userList[i] = scnr.nextInt();
}
for (int i = numElements - 1; i >= 0; --i) {
System.out.print(userList[i] + " ");
}
System.out.println();
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1


Explain the difference between storage devices and virtual storage
Answers
Answer:
Storage devices tend to be built in/physical pieces of storage such as an SD Card or Hard Drive. Virtual storage is more-so like Cloud storage, where the files are hosted elsewhere.
Explanation:
True and False(Total points: 10)
1. The CPU is responsible for moving the data between the peripheral devices that it controls
and its local buffer storage.
2. A linker is used to load the binary executable fle into memory, where it is eligible to run on a
CPU core.
3. When a process creates a new process, it must wait until its child has terminated.
4. TLS data are visible across function invocations but can not be accessed by other threads in the same
process.
5. The multilevel queue scheduling algorithm allows a process to move between queues.
6. The main disadvantage of mutex is that it requires busy waiting.
7. The resource-allocation-graph algorithm is applicable to a resource allocation system with multiple
instances of each resource type.
8. In virtual memory page replacement, increasing the number of frames always decreases the page-fault
rate.
9. DMA can release the CPU from the burden of transferring data between memory and disks, but it is
applicable only when the memory addresses are contiguous.
10. To improve I/O efficiency, I/O transfers between memory and mass storage are performed in units of
blocks, which is usually multiple of 512 bytes.
Answers
Answer:
1.T 2.f 3.t 4.f 5.f 6.f 7.t 8.t 9.f
2. T
3. F
4. T
5. T
6. F
7. T
8. F
9. F
10. T
JAVA HELP TEST An object is a member of the _______ ?
a class
b interface
c variable
d method
Answers
Which of these statements are true? Select 2 options.
A. The new line character is "\newline".
B. In a single program, you can read from one file and write to another.
C. Python can only be used with files having ".py" as an extension.
D. If you open a file in append mode, the program halts with an error if the file named does not exist.
E. If you open a file in append mode, Python creates a new file if the file named does not exist.
Answers
The appropriate choices are This is accurate; if you open a file in append mode and it doesn't exist, Python generates a new file with that name. You can also read from one file and write to another in a single programme.
Can a file be read in add mode?The pointer is added at the end of the file as information is added using the append mode. In the event that a file is missing, add mode generates it. The fundamental difference between the write and append modes is that an append operation doesn't change a file's contents.
Which of the following moves the file pointer to the file's beginning?The file pointer is moved to the file's beginning using the ios::beg function.
To know more about Python visit:-
https://brainly.com/question/30427047
#SPJ1
Do you think privacy policies are effective in social networking sites?
Answers
Answer:
When that information gets posted online, it is no longer private, and may end up falling into wrong hands. Even if you have put in place the highest possible security measures, some of your friends, colleagues and companies you interact with on social media, can end up leaking your personal information.
In my opinion, privacy policies are less effective in social networking sites When that fact receives published online, it's far now not private, and can become falling into incorrect hands.
What is the privacy in networking sites?Privacy and safety settings exist for a reason: Learn approximately and use the privateness and safety settings on social networks. They are there that will help you manipulate who sees what you put up and control your online revel in in a fine way.
Even when you have installed location the best viable safety measures, a number of your friends, colleagues and businesses you engage with on social media, can become leaking your private facts.
Read more about the social networking:
https://brainly.com/question/3653791
#SPJ2
1.what are the function of os
2.what is an is
3.explain the different between Windows os, Android os, and Los os
4.what is a letility software
Answers
Operating system, IS, Differences, Utility Software - Explore key concepts in computing, including operating systems, information systems, platform differences, and utility software functionalities.
How is this so?1. OS functions - manage hardware/software, provide interface, control access, schedule tasks, and facilitate communication between software/hardware.
2. IS - Information System collects, processes, stores, and disseminates information within an organization.
3. Differences - Windows for PCs, Android for mobile, iOS for Apple; user interface, applications, underlying technologies vary.
4. Utility software - enhances system management, optimization, and maintenance; includes antivirus, disk cleanup, file compression, and backup tools.
Learn more about Operating system at:
https://brainly.com/question/22811693
#SPJ1
Design a pda (pushdown automata) of the following:
a^n b^n c^m d^4m
Answers
Answer:
Explanation:
Here is the design of a Pushdown Automaton (PDA) for the language L = {a^n b^n c^m d^4m}:
1. The PDA has a stack to store symbols.
2. The initial state is q0 and the initial stack symbol is Z0.
3. The transitions are defined as follows:
- Transition from q0:
- Read 'a' from the input, push 'A' to the stack, and remain in q0.
- Read 'b' from the input, pop 'A' from the stack, and transition to q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q1:
- Read 'b' from the input, pop 'A' from the stack, and remain in q1.
- Read 'c' from the input, push 'C' to the stack, and transition to q2.
- Read 'd' from the input, push 'D' to the stack, and transition to q3.
- Transition from q2:
- Read 'c' from the input, push 'C' to the stack, and remain in q2.
- Read 'd' from the input, pop 'C' from the stack, and transition to q2.
- Read 'd' from the input, pop 'D' from the stack, and transition to q2.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
- Transition from q3:
- Read 'd' from the input, push 'D' to the stack, and remain in q3.
- Read end of input, pop 'Z0' from the stack, and transition to q4 (final state).
4. The PDA accepts the input string if it reaches the final state q4 with an empty stack.
Note: This PDA design assumes that n and m are positive integers. If n or m can be zero, some modifications to the transitions may be needed to handle those cases.
Why is it important to open the Map Custom Fields dialog box before importing/exporting a list of contacts? Check all that apply.
to remove fields as needed
to add new fields as needed
to move information to new fields
to make sure all the fields match
to rename the fields in both columns
Answers
Answer:
Except the last one, others are correct
Explanation:
Edg said that
Answer:
a b c d
Explanation:
What is the first step in finding a solution to a problem
Answers
assuming a 1-kb page size, what are the page numbers and offsets for the following address references (provided as decimal numbers)? (a) 21205 (b) 164250 (c) 121357 (d) 16479315 (e) 27253187
Answers
Note that the Page numbers and offsets for the following address references given a 1-kb page size are:
a) Address: 21205 → Page number: 20, Offset: 905
b) Address: 164250 → Page number: 161, Offset: 202
c) Address: 121357 → Page number: 119, Offset: 333
d) Address: 16479315 → Page number: 16093, Offset: 659
e) Address: 27253187 → Page number: 26708, Offset: 963.
What is an offset and an address reference?Note that an offset is a numerical value that represents the distance of a particular location within a file, block of memory, or other data structure from a reference point. It is often used to specify the location of a particular piece of data within a larger structure.
An address reference is a value that represents the location of a specific piece of data within a computer's memory.
To determine the page numbers and offsets for the given address references, you will need to divide the address by the page size. The page number will be the result of the division, and the offset will be the remainder.
Thus, for a:
Address: 21205 → Page number: 21205 / 1024 = 20,
Offset: 21205 % 1024 = 905
for b,
Address: 164250 → Page number: 164250 / 1024 = 161, Offset: 164250 % 1024 = 202
for c,
Address: 121357 → Page number: 121357 / 1024 = 119,
Offset: 121357 % 1024 = 333
for d,
Address: 16479315 => Page number: 16479315 / 1024 = 16093,
Offset: 16479315 % 1024 = 659
for e,
Address: 27253187 => Page number: 27253187 / 1024 = 26708,
Offset: 27253187 % 1024 = 963
In conclusion,
a) Address: 21205 → Page number: 20, Offset: 905
b) Address: 164250 → Page number: 161, Offset: 202
c) Address: 121357 → Page number: 119, Offset: 333
d) Address: 16479315 → Page number: 16093, Offset: 659
e) Address: 27253187 → Page number: 26708, Offset: 963.
Learn more about Address References:
https://brainly.com/question/2342795
#SPJ1
Choose the correct term to complete the sentence.
The media is usually repressed in
governments.

Answers
A dictator government has all power in the hands of one individual/group, suppressing opposition. The media is usually repressed in dictatorial government
What is the government?Dictatorships have limited to no respect for civil liberties, including press freedom. Media is tightly controlled and censored by the ruling authority. Governments may censor or control the media to maintain power and promote propaganda.
This includes restricting freedom of speech and mistreating journalists. Dictators control information flow to maintain power and prevent challenges, limiting transparency and public awareness.
Learn more about government from
https://brainly.com/question/1078669
#SPJ1
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
Thao tác trên mảng hai chiều với các yêu cầu sau đây: Khai báo mảng hai chiều; Nhập dữ liệu cho mảng hai chiều; Xuất theo dòng; Xuất theo cột; Nếu là ma trận vuông thì: Xuất đường chéo chính;Xuất đường chéo phụ
Answers
Answer:
THIS SERVER IS FOR THE PEOPLES WHO'S ON THE UNITED STATES ONLY . IF U WANT US TO ANSWER YOUR QUESTION TRANSLATE IT TO ENGLISHExplain how loops can be utilized in list processing. Please provide Python examples in your response.
Answers
Answer:
data = [0,1,2,3,4]
for i in range(4):
print(data[i])
i+=1
Explanation:
Loops can be utilized in a listing process by looping back to a list with a variable while the loop increases that variable to give a different response from the list.
Which of the following parts apply when delivering an indirect bad news message? Select all that apply.
Question 2 options:
Opening with a buffer statement
Being direct with news
Explaining the situation
Inserting stories and important anecdotes
Keeping details to a minimum
Providing alternatives
Answers
The parts that apply when delivering an indirect bad news message are:
Opening with a buffer statement
Explaining the situation
Keeping details to a minimum
Providing alternatives.
When delivering an indirect bad news message, the following parts apply:
Opening with a buffer statement: Start the message with a neutral or positive statement that prepares the recipient for the upcoming news. This helps soften the impact and reduces defensiveness.Explaining the situation: Provide a clear and concise explanation of the circumstances or reasons behind the bad news. This helps the recipient understand the context and rationale.Keeping details to a minimum: While it is important to provide necessary information, it is also crucial to avoid overwhelming the recipient with excessive details. Focus on the key points to maintain clarity and avoid confusion.Providing alternatives: Offer alternative solutions or options to mitigate the impact of the bad news. This shows empathy and provides the recipient with potential avenues for resolution or improvement.The parts that do not apply in delivering an indirect bad news message are:
Being direct with news: Indirect bad news messages typically involve delivering the news subtly rather than being direct.Inserting stories and important anecdotes: Including stories or anecdotes may not be suitable for an indirect bad news message as it can distract from the main message and dilute its impact.Therefore, the applicable parts for delivering an indirect bad news message are opening with a buffer statement, explaining the situation, keeping details to a minimum, and providing alternatives.
For more such question on bad news message
https://brainly.com/question/22473511
#SPJ8
What are other ways you could use the shake or compass code blocks in physical computing projects?
Answers
Answer:there are different ways of quick navigation between files and functions. ... You should use the menu 'Remove file from project' instead of deleting files. ... A Makefile generation tool for Code::Blocks IDE by Mirai Computing
Question 10 of 10
What information system would be most useful in determining what direction
to go in the next two years?
A. Decision support system
B. Transaction processing system
C. Executive information system
D. Management information system
SUBMIT
Answers
Answer: C. Executive information system
Explanation: The information system that would be most useful in determining what direction to go in the next two years is an Executive Information System (EIS). An EIS is designed to provide senior management with the information they need to make strategic decisions.
An Executive Information System (EIS) would be the most useful information system in determining what direction to go in the next two years. So, Option C is true.
Given that,
Most useful information about determining what direction to go in the next two years.
Since Executive Information System is specifically designed to provide senior executives with the necessary information and insights to support strategic decision-making.
It consolidates data from various sources, both internal and external, and presents it in a user-friendly format, such as dashboards or reports.
This enables executives to analyze trends, identify opportunities, and make informed decisions about the future direction of the organization.
EIS typically focuses on high-level, strategic information and is tailored to meet the specific needs of top-level executives.
So, the correct option is,
C. Executive information system
To learn more about Executive information systems visit:
https://brainly.com/question/16665679
#SPJ6
A sum amounts to ₹2400 at 15% simple interest per annum after 4 years fond the sum.
Answers
Answer: $1,500
Explanation:
The future value of value using simple interest is:
Future value = Value * ( 1 + rate * time)
2,400 = Value * (1 + 15% * 4)
2,400 = Value * 1.6
Value = 2,400 / 1.6
Value = $1,500