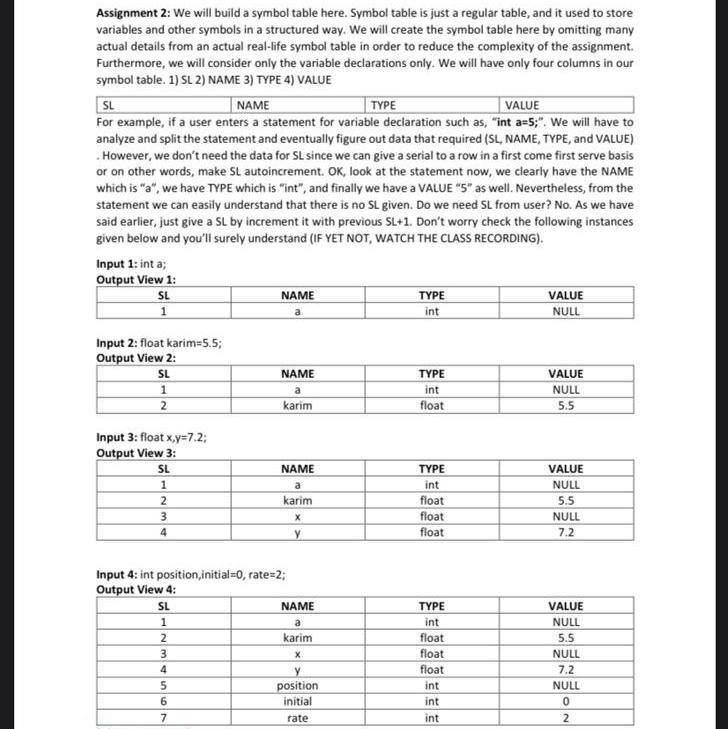
In a TCP connection, the initial sequence number at the client site is 2,171. The client opens the connection, sends only one segment carrying 1,000 bytes of data, and closes the connection. What is the value of the sequence number in each of the following segments sent by the client?
a. The SYN segment?
b. The data segment?
c. The FIN segment?
explain for full credit
Answers
Answer:
a. 2171
b. 2172
c .3172
Explanation:
a . As we know that sequence number is 32 bits has a two responsibility
When the SYN flag is set to the value 1 then that is the number of a initial list. That sequence number +1 is then the sequence number of the real initial data bit.When the SYN flag is set to the value 0 then for the current session is equals to the average sequence number of this section's initial data Bit.Initially the sequence number at the client site is 2,171 that is equals to the he SYN segment i.e 2171.
b The data segment is determined by the following formula
\(=sequence \ number\ in\ the\ client site\ +\ 1\)
\(=2,171 +1\)
\(=2172\)
c As mention in the question there are 1,000 bytes of data,
so FIN segment can be determined by the
\(=2171+1000+1\)
\(=3172\)
Related Questions
Help me with this…… please

Answers
Answer:
2. The texture is being use to look sturdy
3. some repetition are being repeated for example the blocks
4. No it because of the words
5. The words at the bottom
It my opinion so it might not be correct
What feature allows a person to key on the new lines without tapping the return or enter key
Answers
The feature that allows a person to key on new lines without tapping the return or enter key is called word wrap
How to determine the featureWhen the current line is full with text, word wrap automatically shifts the pointer to a new line, removing the need to manually press the return or enter key.
In apps like word processors, text editors, and messaging services, it makes sure that text flows naturally within the available space.
This function allows for continued typing without the interruption of line breaks, which is very helpful when writing large paragraphs or dealing with a little amount of screen space.
Learn more about word wrap at: https://brainly.com/question/26721412
#SPJ1
If you take parent controls off a iphone does the parent controler get a notification?
Answers
It depends on how the parental controls were set up on the iPhone.
What is the parent controller about?If the parental controls were set up using Apple's Screen Time feature, then the parent will receive a notification on their device when the child turns off Screen Time or makes changes to the Screen Time settings. This notification will include information about which settings were changed and at what time.
However, if the parental controls were set up using a third-party app or service, it's possible that the parent may not receive a notification when the controls are removed. It's important to check the specific app or service's settings and documentation to see if this is the case.
Learn more about parent controller from
https://brainly.com/question/14481481
#SPJ1
Which of the following scenarios following to the category of internal computer crimes
Answers
Wheres the Scenarios?
Explanation:
Answer:
The four primary categories of computer crimes are internal computer crimes, telecommunications crimes, computer manipulation crimes, and traditional theft.
Explanation:
How are the aims of science and technology different?
Answers
Answer:
goal of technology is to create products that solve problems and improve human life.
Explanation:
The words science and technology can and often are used interchangeably. But the goal of science is the pursuit of knowledge for its own sake while the goal of technology is to create products that solve problems and improve human life.
Write a function named cube that accepts a number as an argument and returns the cube of that number. Write Python statement(s) that passes 3 to this function and prints returned value.
Answers
def cube(num):
return num*num*num
for the number 3:
def cube():
return 3*3*3
Which development approach was used in the article, "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet"? Predictive, adaptive or Hybrid
Answers
The sequential and predetermined plan known as the waterfall model is referred to as the predictive approach.
What is the development approachThe process entails collecting initial requirements, crafting a thorough strategy, and implementing it sequentially, with minimal flexibility for modifications after commencing development.
An approach that is adaptable, also referred to as agile or iterative, prioritizes flexibility and cooperation. This acknowledges that needs and preferences can evolve with time, and stresses the importance of being flexible and reactive to those alterations.
Learn more about development approach from
https://brainly.com/question/4326945
#SPJ1
The development approach that was used in the article "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet" is Hybrid approach. (Option C)
How is this so?The article "Protecting American Soldiers: The Development, Testing, and Fielding of the Enhanced Combat Helmet" utilizes a hybrid development approach,combining aspects of both predictive and adaptive methods.
Predictive development involves predefined planning and execution, suitable for stable projects,while adaptive methods allow for flexibility in adapting to changing requirements and environments.
Learn more about development approach at:
https://brainly.com/question/4326945
#SPJ1
How is LUA different from Python?
Give an example.
Answers
This is the answer I couldn't write it here since brainly said it contained some bad word whatever.
Answer:
good old brainly think stuff is bad word even tho it is not had to use txt file since brainly think code or rblx is bad word
1. What is virtual memory?
The use of non-volatile storage, such as disk to store processes or data from physical memory
A part of physical memory that's used for virtualisation
Some part of physical memory that a process though it had been allocated in the past
O Future physical memory that a process could be allocated
Answers
Answer:
The use of non-volatile storage, such as disk to store processes or data from physical memory.
Explanation:
Virtual memory is used by operating systems in order to allow the execution of processes that are larger than the available physical memory by using disk space as an extension of the physical memory. Note that virtual memory is far slower than physical memory.
Input a list of employee names and salaries and store them in parallel arrays. End the input with a sentinel value. The salaries should be floating point numbers Salaries should be input in even hundreds. For example, a salary of 36,510 should be input as 36.5 and a salary of 69,030 should be entered as 69.0. Find the average of all the salaries of the employees. Then find the names and salaries of any employee who's salary is within 5,000 of the average. So if the average is 30,000 and an employee earns 33,000, his/her name would be found. Display the following using proper labels. Save your file using the naming format LASTNAME_FIRSTNAME_M08 FE. Turn in your file by clicking on the Start Here button in the upper right corner of your screen. 1.Display the names and salaries of all the employees. 2. Display the average of all the salaries 3. Display all employees that are within 5,000 range of the average.
Answers
Using the knowledge in computational language in JAVA it is possible to write the code being Input a list of employee names and salaries and store them in parallel arrays
Writting the code in JAVA:
BEGIN
DECLARE
employeeNames[100] As String
employeeSalaries[100] as float
name as String
salary, totalSalary as float
averageSalary as float
count as integer
x as integer
rangeMin, rangeMax as float
INITIALIZE
count = 0;
totalSalary =0
DISPLAY “Enter employee name. (Enter * to quit.)”
READ name
//Read Employee data
WHILE name != “*” AND count < 100
employeeNames [count] = name
DISPLAY“Enter salary for “ + name + “.”
READ salary
employeeSalaries[count] = salary
totalSalary = totalSalary + salary
count = count + 1
DISPLAY “Enter employee name. (Enter * to quit.)”
READ name
END WHILE
//Calculate average salary with mix , max range
averageSalary = totalSalary / count
rangeMin = averageSalary - 5
rangeMax = averageSalary + 5
DISPLAY “The following employees have a salary within $5,000 of the mean salary of “ + averageSalary + “.”
For (x = 0; x < count; x++)
IF (employeeSalaries[x] >= rangeMin OR employeeSalaries[x] <= rangeMax )
DISPLAY employeeNames[x] + “\t” + employeeSalaries[x]
END IF
END FOR
END
See more about JAVA at brainly.com/question/12978370
#SPJ1

8. Which of the following is an output device
a. CD
b. Hard Drive
C joystick
D printer
Answers
You work at a print shop that produces marketing materials, and your manager asks you to install a new printer. The printer comes with two options for drivers. One uses PCL, and the other uses Postscript. Which driver is the best option and why
Answers
Since you work at a print shop that produces marketing materials, and your manager asks you to install a new printer. The drivers that is best is PCL, because it can be used in the office to print physical document while the Postcript can only be used for online document or pdf and since it is office job, PCL is the best.
What is PCL printer?PCL use depends on the device. This indicates that certain printed data, typically graphical data like fill areas, underlines, or fonts, is created by the drivers for this language by using the printer hardware. As a result, the print job can be processed by the computer fast and effectively. The production and processing of page data must then be finished by the printer.
Note that If you typically print from "Office" programs in general, use the PCL driver. If you wish to print PDFs more quickly or use professional DTP and graphics tools for the majority of your printing, pick the PostScript driver.
Learn more about printer driver from
https://brainly.com/question/14230829
#SPJ1
Information needed comes from one source or method true or false?
Answers
Answer: This is in fact false.
how do i work this out? does anyone do programming?
Answers
Analyze and write a comparison of C's malloc and free functions with C++'s new and delete operators. Use safety as the primary consideration in the comparison
Answers
Answer:
The C's malloc and free functions and the C++'s new and delete operators execute similar operations but in different ways and return results.
Explanation:
- The new and delete operators return a fully typed pointer while the malloc and free functions return a void pointer.
-The new and delete operators do not return a null value on failure but the malloc/free functions do.
- The new/delete operator memory is allocated from free store while the malloc/free functions allocate from heap.
- The new/delete operators can add a new memory allocator to help with low memory but the malloc/free functions can't.
- The compiler calculates the size of the new/delete operator array while the malloc/free functions manually calculate array size as specified.
1. Utilizing Microsoft VISIO, you are to leverage the content within the prescribed narrative to develop an Entity Relationship Diagram (ERD). Make use of the 'Crow's Foot Database Notation' template available within VISIO.
1.1. You will be constructing the entities [Tables] found within the schemas associated with the first letter of your last name.
Student Last Name
A -F
K-0
P -T
U-7
Schema
1 and 2 as identified in 6.4.1.1.
1 and 3 as identified in 6.4.1.1.
1 and 4 as identified in 6.4.1.1.
1 and 5 as identified in 6.4.1.1.
1 and 6 as identified in 6.4.1.1.
1.2. Your ERD must include the following items:
• All entities must be shown with their appropriate attributes and attribute values (variable type and length where applicable)
•All Primary keys and Foreign Keys must be properly marked
Differentiate between standard entities and intersection entities, utilize rounded corners on tables for
Answers
To create an Entity Relationship Diagram (ERD) using Microsoft Visio, here is what you need to do.
Steps for creating ERD using VisioOpen Microsoft Visio and select the 'Crow's Foot Database Notation' template.Identify the schemas associated with the first letter of your last name. For example, if your last name starts with A-F, choose Schema 1 and Schema 2.Construct the entities (tables) within the chosen schemas based on the provided narrative.Include all necessary attributes and their values for each entity, specifying variable type and length where applicable.Properly mark the Primary Keys and Foreign Keys within the entities.Differentiate between standard entities and intersection entities by using rounded corners on tables.By following these steps, you can create an ERD using Microsoft Visio, representing the entities, attributes, relationships, and key identifiers of the database schema associated with your given criteria.
Learn more about Microsoft Visio:
https://brainly.com/question/29340759
#SPJ1
To behave ethically means
that you do what is right
that you need not obey the law
that you are above the law
that you behave morally
that you stick to the law
. Select 3 options.
Answers
Answer:
1) You do what is right
2)You behave morally
3)You stick to the law
To help insure that an HTML document renders well in many web browsers it is important to included which at top of file
Answers
Answer:
<!DOCTYPE html>
Explanation:
This tells the browseer that the code is HTML5 format
Identify a Web page with an active rollover image and where it is located and describe the image
Answers
The Web was initially just text, which was incredibly boring. Thankfully, it didn't take long for the option to include photographs (as well as other more intriguing sorts of material) inside web pages.
What does a website rollover image mean?Rollovers are graphic elements that improve the aesthetics of a website and convey navigational information. As an indication that the picture is a link and can take the visitor to another part of the website, the Rollover changes when the user's mouse moves over the image.
What does HTML rollover mean?When a user rolls their mouse pointer over a graphical picture, rollover is a JavaScript technique used by Web developers to create the desired effect. The term "rollover" can also refer to a button on a website that enables user and website interaction.
to know more about rollover here:
brainly.com/question/28902915
#SPJ1
The digital world is exciting, but like everything else, it has its pluses and minuses. Describe one advantage and one disadvantage of living in a digital world.
Answers
Answer:
The digital world is exciting, but like everything else, it has its pluses and minuses. Advantage: Digital technology makes it easy to stay in touch with friends, family, and work remotely, even if you are in another part of the world. [ Disadvantage: Data Security. ]
Define the Database
Answers
the focus of these problems will be working with information extracted from a municipal government data feed containing bids submitted for auction of property. all materials for this assignment can be found in the supporting materials section below. the data set is provided in two comma-separated files: ebid monthly sales.csv (larger set of 12,023 bids) ebid monthly sales dec 2016.csv (smaller set of 76 bids) this assignment is designed to explore sorting algorithms by implementing both a selection sort and quicksort of a vector of bids loaded from a csv file.
Answers
Two other file extensions that include data are CSV and Excel, or.xls.The distinction is that the data is in text format and is separated from one another by commas in CSV, or comma-separated values.
An Excel file is it an Excel file? Two other file extensions that include data are CSV and Excel, or.xls.The distinction is that the data is in text format and is separated from one another by commas in CSV, or comma-separated values.Information is tabular and is organized in rows and columns in Excel or xls. A text file with a specific format called a CSV (comma-separated values) file allows data to be saved in a way that is organized into tables.A text file that contains information that is separated by commas is known as a CSV file.Derived from an Excel spreadsheet.The File tab will appear when your Excel document is open.Tab-delimited text or CSV should be selected as the File Format (Comma delimited).To learn more about CSV file refer
https://brainly.com/question/29808893
#SPJ4
A loss of __________ is the unauthorized disclosure of information.
a) authenticity
b) integrity
c) confidentiality
d) reliability
Answers
Answer:
I believe its confidentiality
Explanation:
confidentiality means the state of being kept secret or private
A loss of confidentiality is the unauthorized disclosure of information. The correct option is c).
What is confidentiality?Confidentiality is a set of rules or a promise that limits access to specific information. There aren't enough boundaries in confidential information. One shouldn't give your information to random people, but you also shouldn't give it to people close to you because not everyone is trustworthy.
One should only give out one's information when it is absolutely necessary, which is if you are. Unless there is a compelling reason not to, request consent to share information.
Unless it is going to hurt you or another person, a counselor will keep all of the information you give them confidential. When a detective keeps all crime-related clues and information confidential and hidden from civilians.
Therefore, the correct option is c) confidentiality.
To learn more about confidentiality, refer to the link:
https://brainly.com/question/15144094
#SPJ5
I have to do this shape-up and have this on notepad but I don't know what my next move should be to be able to run it.
This is the Specifications for the shape up • Add a 2-tier navigation menu. The main menu and Stress Relief submenu should include the links shown above. In addition, a Healthy Diets submenu should be included with the links “Why a Healthy Diet?”, “Plan Your Meals”, “Count Your Calories”, and “Calculate Your BMI”. Be sure all the links refer to the correct pages. (The “What is Stress?” link should refer to the index.html page in the stress folder, and the “Why a Healthy Diet?” link should refer to the index.html page in the diet folder).
• Format the navigation menu so the background color is steelblue, so the link for the page that’s currently displayed (in this case, Home) has black text, and so the link that the mouse is hovering over or has the focus (in this case, Meditation) has a lightsteelblue background.
• Remove the links from the h3 headings in the section, since these pages can now be accessed from the menu.
• Modify the logo in the header so it’s a link that displays the home page. • Format the list in the sidebar so there’s no space to the left of the list items. In addition, remove the underlines from the links in the list items.





Answers
Using the knowledge in computational language in html it is possible to write a code that enhance the home page you worked on in so it includes a two-tier horizontal navigation menu and an image link.
Writting the code:<!DOCTYPE html>
<html lang="en">
<head>
<style>
{
margin: 0;
padding: 0;
}
body
{
font-family: Arial, Helvetica, sans-serif;
font-size: 100%;
margin-left: 10px;
width: 900px;
margin: 0 auto;
border: 3px solid steelblue;
border-radius: 2px;
box-shadow: 2px 2px 3px 3px black;
background-color: #fffded;
}
a{ text-decoration:none;
}
a:link {color:maroon;}
a:visited{color:maroon;}
a:hover, a:focus{ color:steelblue;}
main p:first-child, a:hover, a:focus{color:maroon;}
main p:last-child,a:visited,a:focus,a:link{color:steelblue;}
header
{
padding-bottom: 1em;
border-bottom: 3px solid steelblue;
background-image: -moz-linear-gradient(
180deg, white 0%, lightsteelblue 100%);
background-image: -webkit-linear-gradient(
180deg, white 0%, lightsteelblue 100%);
background-image: -o-linear-gradient(
180deg, white 0%, lightsteelblue 100%);
background-image: linear-gradient(
180deg, white 0%, lightsteelblue 100%)
}
.quote
{
text-indent: 50px;
padding: .5em .5em .5em .5em;
}
header img
{
float:left;
margin-right:1em;
}
#div1 {
position: relative;
}
#div1 > a {
cursor:pointer;
list-style:none;
}
#div2 {
position: absolute;
top: 100%;
left: 0;
display:none;
height: 30px;
width: 200px;
background-color: white;
z-index: 20;
}
#div1:hover #div2 {
display:block;
}
#div3 {
position: relative;
}
#div3 > a {
cursor:pointer;
list-style:none;
}
#div4 {
position: absolute;
top: 100%;
left: 0;
display:none;
height: 30px;
width: 215px;
background-color: white;
z-index: 20;
}
</footer>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1

I am working on 8.8.6 "Totals of Lots of Rolls" in codeHS javascript and
I do not know what to do can someone help me?
Answers
Using the knowledge in computational language in JAVA it is possible to write a code that rolls a 6-sided die 100 times.
Writting the code:var counts = [0, 0, 0, 0, 0, 0, 0];
for (var i = 0; i < 100; i++) {
counts[Math.floor(1 + Math.random() * 6)]++;
}
console.log('You rolled ' + counts[1] + ' ones.');
console.log('You rolled ' + counts[2] + ' twos.');
console.log('You rolled ' + counts[3] + ' threes.');
console.log('You rolled ' + counts[4] + ' fours.');
console.log('You rolled ' + counts[5] + ' fives.');
console.log('You rolled ' + counts[6] + ' sixes.');
See more about JAVA at brainly.com/question/12975450
#SPJ1

Why does trust usually break down in a designer-client relationship?
A lack of service
B lack of privacy
C lack of communication
D lack of contract
Answers
Trust is usually broken down in a designer-client relationship due to a lack of service. Thus, the correct option for this question is A.
How do you end a client relationship?You would end a client relationship by staying calm, rational, and polite. Apart from this, reasons for terminating the relationship, but keep emotion and name-calling out of the conversation.
Follow-up with a phone call. You can start the process with an email, but you should follow up with a phone call in order to talk your client through the process and answer any questions.
But on contrary, one can build trust with clients by giving respect to them, Admit Mistakes and Correct Ethically, listening to them, listening to their words first followed by a systematic response, etc.
Therefore, trust is usually broken down in a designer-client relationship due to a lack of service. Thus, the correct option for this question is A.
To learn more about Client relationships, refer to the link:
https://brainly.com/question/25656282
#SPJ1
Which of these terms refers to a paper printout?
Answers
Answer:
A term that refers to a paper printout is a hardcopy output.
Explanation:
Any output that is available in paper form is typically referred to as a hard copy. It served as a word to set it apart from soft copy (which referred to any electronic form). It was talking about how the paper version appeared to be permanent; you couldn't update the data on a hard copy format without it being clear.
Data that was seen on a screen or saved to disk was considered soft copy, whereas data that was printed out was considered hard copy.
Thanks,
Eddie
What are Divine Laws? Explain the Golden Rule of Divine Laws. How Crime, Sin and Indiscipline are different from each other? Give examples of any State Law which is
(a) Similar to Divine Law (b) Opposite to Divine Law.
Answers
Answer:
Divine law comprises any body of law that is perceived as deriving from a transcendent source, such as the will of God or gods
Golden rule of Divine Laws:
Golden rule law is a modification of the literal rule. It states that if the literal rule produces an absurdity, then the court should look for another meaning of the words to avoid that absurd result.
The difference between sin and crime is that a sin is an opposed to god's will, and crime is opposed to the civil laws
To address cybercrime at the global level, law enforcement needs to operate
.
Answers
In order to address cybercrime on a worldwide scale, it is imperative that law enforcement agencies work together in a collaborative and cooperative manner across international borders.
What is the cybercrime?Cybercrime requires collaboration and synchronization among countries. Collaboration among law authorization organizations over different countries is basic for the effective request, trepidation, and conviction of cybercriminals.
In arrange to combat cybercrime in an compelling way, it is pivotal for law authorization to collaborate and trade insights, capability, as well as assets.
Learn more about cybercrime from
https://brainly.com/question/13109173
#SPJ1
whats difference between DCE AND DTE serial interface
Answers
DCE stands for data circuit-terminating, data communications, or data carrier equipment - this is a modem or more generally, a line adapter.
DTE stands for data terminal equipment which generally is a terminal or a computer.
Basically, these two are the different ends of a serial line.