if there is a sticker and i remove the sticker from the item and ask what will they do on it is that illegal?
Answers
No, it is not illegal. However, depending on the item, the removal of the sticker may void any manufacturer's warranty.
Why remove the sticker from the item is illegal?Removing a sticker from an item is illegal because it is a form of theft. By removing the sticker, you are taking something that does not belong to you and not paying for it, which is a violation of the law. Additionally, it is possible that the sticker contains valuable information, such as serial numbers and barcodes, which can be used to track the item. Removing the sticker can interfere with the ability to track the item, which could lead to legal issues. Furthermore, some stickers may be part of an item's design, and their removal could damage the item or devalue it. Lastly, some stickers may be part of a product's certification, and their removal could make the item unsafe or inoperable. For all these reasons, removing the sticker from an item is illegal.
To learn more about removing a sticker refer to:
https://brainly.com/question/29673738
#SPJ4
Related Questions
you notice that the data in column e is an example of boolean data. why did you come to this conclusion?
Answers
I came to the conclusion that the data in column E is an example of boolean data because it consists of only two possible values, typically represented as "true" or "false" or "1" or "0".
Boolean data is used to represent logical values and can be used in logical expressions and conditions.
By noticing that the data in column E only has two possible values, it is clear that it is an example of boolean data. This type of data is commonly used in programming and computer science to represent logical values and make decisions based on those values.
Learn more about Boolean data: https://brainly.com/question/15328429
#SPJ11
Write a program that reads the content of a text file. the program should create a dictionary in which the keys are individual words found in the file and the values are the amount of times the word appears in the file. For example, if the word 'the' appears in the file 128 times, the dictionary would contain an element with the key as 'the' and the value as 128. Write in Python
Answers
This software opens the file filename.txt, reads the text inside, and then uses the split() method to separate the text into individual words. After that, it loops and produces a new empty dictionary called freq dict.
How can I construct a Python program to count the number of times a word appears in a text file?To calculate the frequency of each word in a sentence, create a Python program. In Python: counts = dict in def word count(str) () split() for word in words with words = str: If a word is counted, then counts[word] += 1. and if counts[word] = 1 then return counts The swift brown fox leaps over the slothful hound, print(word count('.
# Use the command open('filename.txt', 'r') as file to open and read the file's contents:
file.read content ()
# Separate the text into its component words.
Language is content.
split()
# Construct a blank dictionary by changing freq dict to.
# Determine the frequency of every word in words:
If word appears in freq dict, then freq dict[word] +=
if not, freq dict[word] =
# Use the freq dict.items() function to display the frequency count for each word individually:
print(word, count) (word, count)
To know more about software visit:-
https://brainly.com/question/985406
#SPJ1
In this module you learned about making decisions. You learned about the syntax and rules used to develop programs containing decisions and how the logic can make your programs more robust.
Draw a flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it.
There are NO LOOPS, NO Functions(other than the random number generator) and NO MODULES at this point. Everything at this point is in sequence(Line-By-Line). You can add comments at the beginning of each block to explain what the code is doing..
Declare the variables and data types used
import random (Generate random integers using Python randint() - AskPython )
You want to add the code so the player can enter their name, then display a welcome message using their name.
You also want to display a message that describes what the program will do.
The program should allow the player to guess the number that was randomly generated.
Display a message indicating whether the player’s guess was too high, or too low.
When your program ends, thank the person for playing and display "Game Over"
Complete the Python code using IDLE Editor.
Complete the flowchart. Upload the exported PDF to the Blackboard assignment area by clicking on the Browse My Computer button below the text editor.
Answers
A flowchart for a program that shows the logic for a program that generates a random number and the player tries to guess it, and declares the variables and data types used, imports random (Generate random integers using Python randint() - AskPython), and displays a message that describes what the program will do.
Let's see the solution step-by-step:
Step 1: Importing the random module and declaring variables import randomplayer = input("Enter your name:")# Declare variables and data types usedrandom_number = random.randint(1,100)guess = 0print(f"\nWelcome {player}, let's play a game!")print("I am thinking of a number between 1 and 100. Can you guess it?")
Step 2: Starting the game with while loop. The game will continue until the player guesses the number. The player has to guess the number, and the program should give feedback if the guess is too high or too low, using if statements.while guess != random_number: guess = int(input("\nTake a guess: ")) if guess > random_number: print("Too high, try again!") elif guess < random_number: print("Too low, try again!")
Step 3: Printing the output If the player guesses the number, the program will end with a message thanking the person for playing and displaying "Game Over".print("\nCongratulations, you guessed the number!")print(f"Thank you for playing, {player}!")print("Game Over")
Step 4: FlowchartPlease see the attached file for the flowchart.
To learn more about flowchart:
https://brainly.com/question/31697061
#SPJ11
The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called:________
Answers
The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called Potential GDP.
What is meant by GDP?GDP is known to be the term hat looks into or one that measures the monetary worth of final goods and services and it is one which is said to be bought by the final user.
What is Potential GDP?Potential GDP is known to be called full-employment GDP and this is said to be the maximum rate or quantity that an economy is known to be able to make or produce given full employment of its former levels of labor, physical capital, and others.
Hence, The maximum quantity that an economy can produce, given its existing levels of labor, physical capital, technology, and institutions, is called Potential GDP.
Learn more about Potential GDP from
https://brainly.com/question/13824314
#SPJ1
Discuss the Autonomous Robots and Additive Manufacturing contribution to Smart Systems. Why are these two technologies are important for the Smart Systems? Explain the technologies with an example.
Answers
Additive manufacturing, also known as 3D printing, revolutionizes traditional manufacturing methods by constructing objects layer by layer. It enables rapid prototyping, customization, and on-demand production. For instance, in a smart healthcare system, additive manufacturing can be employed to produce personalized medical implants, such as customized prosthetics or dental implants, based on patient-specific requirements, resulting in improved patient outcomes and reduced lead times. Both technologies contribute to the advancement of Smart Systems by optimizing processes, enhancing productivity, and enabling customization in various industries.
saved what is the order of growth of the worst case running time of the put operation for the book's binary search with n keys, when the key being inserted is already in the symbol table? question 1 options: logarithmic constant linear quadratic
Answers
The order of growth of the worst-case running time for the put operation in a binary search with n keys, when the key being inserted is already in the symbol table, is logarithmic. This is because the algorithm only needs to traverse the height of the binary search tree, which is proportional to log(n) in the worst case.
The order of growth of the worst case running time of the put operation for the book's binary search with n keys, when the key being inserted is already in the symbol table, is constant. This is because the put operation will simply update the value associated with the existing key, rather than searching for the correct position to insert the key. Therefore, the time complexity of the put operation remains the same regardless of the number of keys in the symbol table.
Learn more about logarithmic here:-
https://brainly.com/question/30085872
#SPJ11
In one paragraph, explain how understanding social media influencing tactics has impacted the way you see social media posts in your daily life.
Answers
Answer:
Social media influencing tactics has impacted the way I see social media posts in your daily life in the sense that if influences what posts I see and what posts I interact with.
Explanation:
Some examples of social media influencing tactics include ads, videos, social media influencers and so on.
When for example, and ad pops up on my social network and I click on it, similar ads of different products would appear later on my social network. In this way, my interaction with that ad has brought up similar ads to my attention. Likewise interaction with videos and social media influencers. When i interact with one video or social media influencer, a similar video or social media influencer is brought up to my attention in my feed.
Social media refers to the media that is online and includes popular media and social apps , and many more. People can create hare and exchange information regarding topics, ideas, and trends.
There are many aspects of social media and some help in influencing society at large. Such as mass campaigns for political elections. Some of the tactics that we can use in unsocial media include creative content, video subscription, sharing comments.Social media posts encourage you to comment, like, and subscribe and are done to show follows. Can impact the mentality of society and changes a person's behavior.Learn more about the understanding social media influencing tactics has impacted.
brainly.com/question/20708829.
How can you ensure that your internet search is happening over a secure network connection?.
Answers
A person can you ensure that your internet search is happening over a secure network connection by the use of:
By Renaming your Routers and Networks.The use of a strong passwords.Do Turn on encryption.The use of multiple firewalls.What is secure network connection?A secure connection is known to be a kind of a connection that is known to be one that is often encrypted by the use of a single or a lot of security protocols to make sure that the security of data that is known to be passing between two or more nodes.
Therefore, based on the above scenario, A person can you ensure that your internet search is happening over a secure network connection by the use of:
By Renaming your Routers and Networks.The use of a strong passwords.Do Turn on encryption.The use of multiple firewalls.Learn more about internet search from
https://brainly.com/question/20850124
#SPJ1
The ______ is designed to store audio data on computers and/or digital music players.
A. waveform
B. audio file format
C. sample rate
D. bandwidth
Answers
Answer:
audio file formats of computer
) what is a denial of service attack? a) it is an attack when the perpetrator is inserting malicious query in input such that it is passed to and executed by an application program. 30) b) it is an attack when the perpetrator uses software to guess company's addresses, send employees blank e-mails, and add unreturned messages to spammer e-mail list. c) it is an attack when the perpetrator is inputting so much data that the input buffer overflows. the overflow contains code that takes control of the company's computer. d) it is an attacked when the perpetrator sends hundreds of messages from randomly generated false addresses, overloading an internet service provider's e-mail server.
Answers
Sends messages involving products of companies previously sued under the CAN-SPAM Act. Thus, option B is correct.
What is CAN-SPAM Act?This act is an act of Controlling the Assault of Non-Solicited Marketing And Other things. It is an attack when the perpetrator uses software to guess company's addresses, send employees blank e-mails, and add unreturned messages to spammer e-mail list.
It is the law that establish the rules for the commercial message and the commercial e-mails, gives recipients right to have the business stops emailing them, and they outline the penalties incurred for those person who has violated the law.
Therefore, Sends messages involving products of companies previously sued under the CAN-SPAM Act. Thus, option B is correct.
Learn more about CAN-SPAM Act on:
https://brainly.com/question/3747672
#SPJ1
About how many computer languages are in use?
Answers
Answer:
2,000
Explanation:
which of the following characteristics relates to a common gateway interface (cgi) script?
Answers
A common gateway interface (CGI) script interacts with web servers, executes on the server, handles form submissions, communicates using standard input and output, and provides dynamic content.
What are the characteristics of a common gateway interface (CGI) script?A common gateway interface (CGI) script has the following characteristics:
Interacts with web servers: CGI scripts are programs or scripts that interact with web servers to generate dynamic content. When a CGI script is invoked, it receives input from the web server, processes it, and produces output that is sent back to the server for further processing and eventual delivery to the client's web browser.Executes on the server: CGI scripts execute on the web server, not on the client's computer. They are typically written in scripting languages like Perl, Python, or Ruby, although other programming languages can also be used.Handles form submissions: One common use of CGI scripts is handling form submissions. When a user submits a form on a web page, the data entered in the form is sent to the CGI script, which can process the data, validate it, store it in a database, or perform other actions based on the form's content.Communicates using standard input and output: CGI scripts communicate with the web server using standard input (stdin) and output (stdout). The web server passes input to the CGI script through environment variables and the standard input stream. The script processes the input, generates the desired output, and sends it back to the web server through the standard output stream.Provides dynamic content: CGI scripts are often used to generate dynamic content for web pages. They can retrieve data from databases, interact with external APIs, perform calculations, and dynamically generate HTML, XML, or other formats to be returned to the client's browser.Overall, a CGI script is a program or script that executes on a web server, interacts with the server through standard input and output, handles form submissions, and generates dynamic content for web pages.
Learn more about gateway interface
brainly.com/question/31721184
#SPJ11
What parts of the computer does it not need to function?
Answers
When you insert a Quick table, you cannot format it true or false
Answers
Answer:
True
Explanation:
Format the table the way you want — e.g. borders, shading, row height, alignment, emphasis, font size, etc. for the heading row and the table rows. You can use manual formatting, or one of the built-in table designs
match the following

Answers
Answer:
can't understand.... what's your question???!!
What are three things you can create with spreadsheet software?
Answers
Answer:
An interactive whiteboard is an electronic device that helps students learn English in a more stimulating way. It is very useful in the classroom because it can engage students and provide them with interactive opportunities. You can write on it with a special pen or even with your finger. You can also run presentation software on the interactive whiteboard. It is useful for teachers to make grammar or vocabulary presentations and save them for using again. After students complete an exercise, they can see the correct answers on the board. Teachers can also download resources such as gap-fill exercises, multiple-choice quizzes or games for their students to do in class. All the students have to do is to come to the board and drag and drop their answers into the gaps with their fingers. This involves them directly in work in front of the board, which most of them love. In summary, an interactive whiteboard is beneficial for both teachers and students in the classroom.
Performing sequential operations on tuples without creating an entire temporary table of all tuples is called 1) pipelining 2) streaming 3) buffering 4) optimizing TOSHIBA
Answers
Performing sequential operations on tuples without creating an entire temporary table of all tuples is called streaming.
What is the term for executing sequential operations on tuples without creating a temporary table?The main answer is "streaming," which refers to the process of performing sequential operations on tuples without the need to create an entire temporary table. In streaming, tuples are processed one by one or in small batches, allowing for efficient use of system resources and avoiding the overhead of creating and storing intermediate tables.
This approach is particularly beneficial when dealing with large datasets or when real-time processing is required. By leveraging streaming techniques, applications can process data in a continuous and efficient manner, enabling faster and more scalable data processing pipelines.
Streaming is an important concept in data processing, particularly when dealing with large datasets or real-time processing scenarios. It allows sequential operations to be performed on tuples without the need to create temporary tables, which can consume a significant amount of system resources.
By processing tuples one by one or in small batches, streaming minimizes memory usage and improves overall performance. Streaming is widely used in various domains such as data analytics, ETL (Extract, Transform, Load) processes, and event-driven architectures.
Understanding and implementing streaming techniques can greatly enhance the efficiency and scalability of data processing pipelines.
Learn more about sequential operations
brainly.com/question/31960074
#SPJ11
Choose the term that makes the sentence true.
When you enlarge a raster image, the painting program uses ___
to add the needed pixels.
Answers
When you enlarge a raster image, the painting program uses interpolation to add the needed pixels.
What is Interpolation?Interpolation is a technique used by painting programs to add pixels to an image when it is enlarged, by estimating the color values of the new pixels based on the color values of existing pixels.
Hence, it can be seen that when making an image edit and you want to make an enlargement of a raster image, there is the use of interpolation to add the needed pixelation.
Read more about interpolation here:
https://brainly.com/question/18768845
#SPJ1
Which of the following statements is
TRUE?
A. You must be connected to the Internet to compile
programs.
B. Not all compilers look the same.
C. All machines have a built in compiler.
D. All compilers contain a file browser.
Answers
Answer: B / Not all compilers look the same.
Explanation: Depending on the language you are programming in, would determine which compiler you use.
Does anyone know the answer for 4.2 Code Practice: Question 1 on edhesive
Answers
Answer:
Question 1
sum=0
count=0
while(sum<=100):
x=int(input("Enter a nmber"))
sum=sum+x
count=count+1
print("Sum: "+str(sum))
print("Numbers Entered: "+str(count))
Question 2
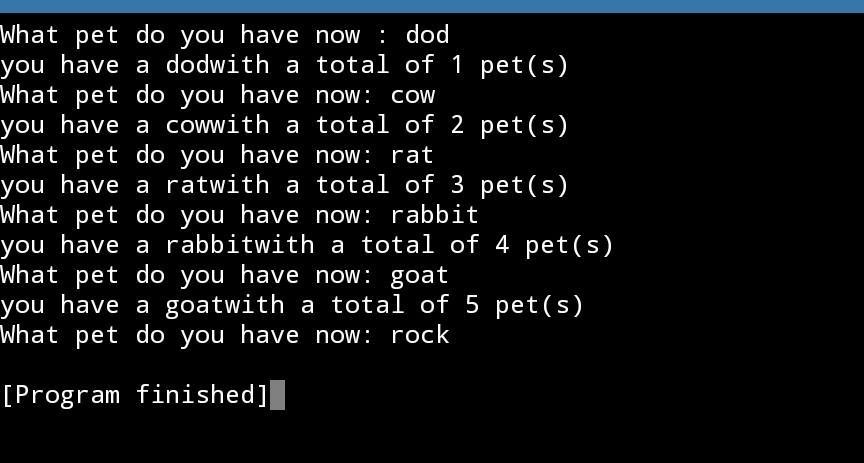
count = 0
pet = (input("What pet do you have? "))
while(pet != "rock"):
count = count +1
print("You have a " + pet +" with a total of " + str(count) + " pet(s)")
pet = (input("What pet do you have? "))
Explanation:
The required program written in python 3 which continues to request user to input a pet name until a rock is entered is as follows :
pet = input('What pet do you have now : ')
#request an input from the user and store in the variable pet
total = 0
#initialize the total number of pets owned to 0
while (pet != 'rock'):
#while loop ensures that program runs until a rock is inputted by the user
total +=1
#adds one to the total after each loop
print('you have a ' + str(pet) + 'with a total of ' + str(total) + ' pet(s)')
#displays the formatted string using the total and pet variables which continues to update
pet = input('What pet do you have now: ')
#requests user to input pet name again as long as rock has not been supplied.
Therefore, an output of the program written is attached below.
Learn more on python programs :https://brainly.com/question/18685986
Which of these plays an important role in keeping attack traffic off your systems and helps to protect users? check all that apply
Answers
Answer:
Antivirus software
Antimalaware measures
The things which play an important role in keeping attack traffic off your systems and helping to protect users are antimalware measures and Antivirus software. The correct options are a and b.
What are antimalware measures and antivirus software?Antimalware can assist in the prevention of malware assaults by checking all incoming data and preventing malware from being installed and infecting a computer.
When the operating system is unable to communicate with a mouse, the solution is to update the mouse device driver. This is because the mouse driver is frequently and always required to assist the motherboard in interacting with the device.
It is also a software that works between the Operating System and the Mouse because it can effectively and efficiently translate the signals to the motherboard appropriately or ways, which is why Microsoft's generic driver is used.
Therefore, the correct options are a and b.
To learn more about antimalware measures, refer to the link:
https://brainly.com/question/27994271
#SPJ2
The question is incomplete. Your most probably complete question is given below:
Antimalware measures
Antivirus software
Digital attack surfaces
cybersecurity
A conditional statement will select the block of statements that will execute based on the given condition. The result of the program depends on the condition. If the condition provided proves to be true, the result is 1; if it proves to be false, the result is 0.
Answers
The statement "A conditional statement will select the block of statements that will execute based on the given condition. The result of the program depends on the condition. If the condition provided proves to be true, the result is 1; if it proves to be false, the result is 0" is true because a conditional statement is a programming statement that allows the program to make decisions based on the value of a variable or expression.
The conditional statement will first evaluate the condition, and if the condition is true, then the block of statements that follows the condition will be executed. If the condition is false, then the block of statements will not be executed.
The result of the program will depend on the value of the condition. If the condition is true, then the result of the program will be 1. If the condition is false, then the result of the program will be 0.
Here is an example of a conditional statement:
if (age >= 18) {
print("You are an adult.");
} else {
print("You are not an adult.");
}
In this example, the condition is age >= 18. If the value of the age variable is greater than or equal to 18, then the block of statements that follows the condition will be executed. The block of statements prints the text You are an adult.. If the value of the age variable is less than 18, then the block of statements will not be executed.
Conditional statements are a powerful tool that can be used to control the flow of a program. They can be used to make decisions, to branch the program into different paths, and to repeat blocks of code.
To learn more about conditional statement visit: https://brainly.com/question/27839142
#SPJ11
30 pts!
Explain how Moore's law presumes everyone will have access to the Internet.
Answers
Answer:
Moore's law predicts that this trend will continue into the foreseeable future.
Explanation:
Moore's Law refers to Moore's perception that the number of transistors on a microchip doubles every two years, though the cost of computers is halved.
Which of the following will NOT correctly increment the value by one of a previously initialized integer variable named counter?
counter + 1;
counter++;
counter = counter + 1;
counter += 1;
All of the above will correctly increment the value by one.
Answers
counter + 1; will raise the value by one but it will not set the value of counter to itself + 1, therefore,
counter + 1; is the correct answer
smart tv has _____ intergrated with it
Answers
Answer:
an operating system
Explanation:
You have created a new storage space using a single 500 GB external USB 3.0 drive. The drive is becoming full, so you add another external 1 TB USB 2.0 drive to the storage pool. Now that you have two drives, you would like to create a volume with storage space resiliency set to two-way mirror. You create the new volume with two-way resiliency and a size limit of 1 TB. As you are copying files from the C: drive to this new volume, you receive a warning that you are running out of space. Only a few hundred megabytes have been copied; why might you be receiving the warning so quickly? What can you do about it?
Answers
Answer:
In the clarification section following, the definition including its query is mentioned.
Explanation:
I believe we possess 2 other discs except for the major memory card-a USB 500 GB USB 3.0 drive, just one TB USB 2.0 drive. So we're making a two-array mirrored storage space resilience kit. We get a warning when we duplicate files from either the C: drive towards this second adaptation that you should be running out of places. That was because these need to have a backup process around each other discs throughout the situation of a two-way mirror.This serves to protect the organization from disc failure and enhances the overall efficiency of the device. Thus, even when copying, even though only several 100 MB has also been cut and pasted to something like the disc, the disc intercepts that the information collected from either the 500 GB drive as well as the major disc must be stored there. And that is how the alert arrives that throughout the new trip, we're running out of space. So this is how they so easily get the alarm.
how can online presence help others?
Answers
Answer:
Online Presence helps others who might be naturally introverted, stuck in a precarious situation, or even by allowing someone company who desperately needs it.
Explanation:
Write a Python program to get the top three item prices in a shop. (15 points) Sample data: {'Apple': 0. 50, 'Banana': 0. 20, 'Mango': 0. 99, 'Coconut': 2. 99, 'Pineapple': 3. 99} Expected Output: Pineapple 3. 99 Coconut 2. 99 Mango 0. 99
Answers
To write a Python program to get the top three item prices in a shop. Here the code that represent the situation given:
def get_top_three_prices(items):
sorted_items = sorted(items.items(), key=lambda x: x[1], reverse=True)
top_three_items = sorted_items[:3]
for item, price in top_three_items:
print(item, price)
data = {'Apple': 0.50, 'Banana': 0.20, 'Mango': 0.99, 'Coconut': 2.99, 'Pineapple': 3.99}
get_top_three_prices(data)
How this codes work?In order to determine the top three of the price. The program need to do the following step :
Create a dictionary containing the item names and pricesStep Use the `sorted()` function with the `reverse` parameter set to `True` to sort the dictionary by price in descending orderStep Loop through the sorted dictionary and print the top three items and their prices. Here's the Python code to get the top three item prices in a shopAs per data given, by following this steps, the top three items and their prices in the given shop are Pineapple for 3.99, Coconut for 2.99, and Mango for 0.99.
Learn more about looping
https://brainly.com/question/31033657
#SPJ11
music sites through schools wifi 2020 What is one thing a person should do to stay safe when exercising? 100 pts.!
Answers
Answer:
They should stay away from others (keep workout short or at home)
always do The exercise right-properly
Explanation:
Answer:
they should stay at home and do workouts or they can start a fitness program in a safe area.
Write a program in Java that asks the user to enter four weighted assessment grades, calculate the average, then display the average with the message: "Student Pass" if the average is greater than or equal 60 or the message "Student Fail" otherwise. The details of the assessments and weights are as follow: Homeworks: 20% Labs: 15% Midterm: 25% Final: 40%
Answers
Answer:
Explanation:
In order to calculate the weighted average, the grade itself is multiplied by the percentage of the category and then these values are summed. This sum is then divided by the total percentage of the portfolio.
import java.util.Scanner;
class Main {
public static void main(String[] args) {
double sumOfWeights = 100;
Scanner in = new Scanner(System.in);
System.out.println("Please Enter Homework Grade: ");
double homework = in.nextDouble() * 20;
System.out.println("Please Enter Labs Grade: ");
double labs = in.nextDouble() * 15;
System.out.println("Please Enter Midterm Grade: ");
double midterm = in.nextDouble() * 25;
System.out.println("Please Enter Final Grade: ");
double finals = in.nextDouble() * 40;
double average = (homework + labs + midterm + finals) / sumOfWeights;
System.out.println("The Average of these Weighted Grades is " + average);
}
}