host-attached storage is . a. a special purpose storage system that is accessed remotely over a data network b. accessed via local i/o ports c. not suitable for hard disks d. not suitable for use in raid arrays
Answers
Network-attached storage was designed to improve user collaboration and data sharing. Distributed teams that require remote can benefit from it.
What is direct-attached storage?
A type of storage known as direct-attached storage (DAS) is connected to a computer directly, bypassing a network. Local I/O ports are used to access host-attached storage. These ports employ a variety of technology. Network-attached storage (NAS), often known as IDE or ATA, allows several users and a variety of client devices to access data from a centralised disc capacity. A typical Ethernet connection is used by users on a local area network (LAN) to access the shared storage. most desktop PCs employ a bus architecture. With this configuration, there can be two drivers per bus.
To learn more about LAN from given link
brainly.com/question/13247301
#SPJ4
Related Questions
What are some text effects found in WordArt gallery? Check all that apply
Bevel
Glitter
Reflection
Shadow
Shine
Soft edges
Answers
Depending on the version of Microsoft Word or Office, the text effects seen in the WordArt collection may change. Keep in mind that the text effects "Glitter" and "Shine" are not frequently used ones in the WordArt gallery.
What text effects can be seen in the WordArt gallery?Each style in the WordArt exhibition was produced by combining several text effects found in Word. You can change the text effects or use different text effects after adding WordArt to the text. Glow, reflection, 3D, morphing, shadow, and bevel are a some of the effects.
What kinds of text effects are there?Choose either text or WordArt. Go to Home > Text Effects. Click the desired effect. Point to Outline, Shadow, and Other for further options.
To know more about Microsoft visit:-
https://brainly.com/question/26695071
#SPJ1
Logan is creating a program using an integrated development environment which of the following is not a function of an IDE
A. a place for coders to write out code
B. a place for coders to test code
C. a place where code is converted to binary code
D. a place where code is downloaded for free
Answers
when implemented correctly, continuous deployment (cdsix )'s components keep each team member, team, and agile release train on schedule. which of the following two best describes a cd component? (select two) a) maintain manual deployment b) deploy to staging every third iteration c) maintain a staging environment that emulates production d) development and test environments should be separate from production e) automate testing features and non-functional requirements see all questions back skip question course content course content overview q
Answers
A) Maintain Manual Deployment
B) Automate testing features and non-functional requirements
What is Automate testing features ?Automated Testing is a type of software testing that uses specialized tools to execute tests, compare the results to expected outcomes and generate detailed reports of the results. Automated testing is used to improve the efficiency and accuracy of software testing, ensuring that tests are run quickly and consistently. It is especially advantageous for tests that need to be repeated frequently or that involve a large number of input values. Automated testing typically involves a combination of unit tests, integration tests, system tests, and acceptance tests. Automated testing tools can also be used to check for compliance with coding standards and to detect security vulnerabilities. Automated testing is highly recommended for any software development project, as it can help save time, reduce costs, and improve the overall quality of the product.
To learn more about Automate testing features
https://brainly.com/question/29023352
#SPJ1
anybody know how to code?
Use an algorithm to help the Python Turtle get to the finish line in 10 steps by using only the 3 commands below:
- Turn Left
- Turn Right
- Move #
Answer:
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.

Answers
▪︎An onscreen camera for drawing virtual images is called "turtle" in python language.
\(\hookrightarrow\)The codes we will be using in the following algorithm are :
▪︎Turtle.left
▪︎Turtle.right
▪︎Turtle.move #upward
\(\hookrightarrow\) An algorithm to help the python turtle reach the finish line :
Turtle.leftTurtle.leftTurtle.leftTurtle.move#upwardTurtle.move#upwardTurtle.move#upwardTurtle.rightTurtle.rightTurtle.move#upwardTurtle.leftThe internet service that allows users to navigate among many pages is.
Answers
Answer:
The world wide web
Explanation:
The world wide web is a hypertext information system that links internet documents and allows users to navigate through the Web, by using a computer mouse to click on “links” that go to other web pages.
Is MOOC's potentially harmful to copyright? Why or why not ?
Answers
Answer:
Fair-use exceptions to traditional copyright protection face challenges as well, given a MOOC's potential for global reach. Nonetheless, fair use and MOOCs are not mutually exclusive ideas. MOOCs remain an experiment...
testing whether a computer boots up the first time is an example of ____
Answers
"Initial system testing" or "Power-on self-test (POST)" would be an appropriate term for testing whether a computer boots up the first time.
Testing whether a computer boots up the first time is an example of the Power-On Self-Test (POST) process that runs automatically when a computer is powered on. The POST is a built-in diagnostic program that checks the system's hardware components such as the motherboard, processor, memory, storage, and input/output devices to ensure they are functioning correctly. If any issue is found during the POST, the computer will alert the user through a series of beeps, error messages or a black screen. The POST is an essential process to ensure the system is functional before the operating system starts up.
Learn more about Initial system testing here.
https://brainly.com/question/28201596
#SPJ11
Hey can y’all help me with this thanks

Answers
Answer:The answer is 144
Explanation:First you subtract the two numbers which would be 8-2=6
Then you multiply the 6 by how many numbers there are: 6x2=12
then you multiply 12 by itself: 12x12=144
try pinging between pc1 and pc4. although the access ports are assigned to the appropriate vlans, were the pings successful? explain.
Answers
The pings between PC1 and PC4 were not successful because they are in different VLANs and need a Layer 3 device (router) to communicate between them.
Pings between PC1 and PC4 were not successful because they belong to different VLANs. VLANs provide logical separation within a network, and by default, devices within different VLANs cannot communicate directly. A Layer 3 device, such as a router, is required to facilitate communication between VLANs. Access ports, which are assigned to specific VLANs, can only forward traffic within their assigned VLAN. To establish successful communication between PC1 and PC4, a router or Layer 3 switch should be configured to enable inter-VLAN routing, allowing traffic to be routed between the VLANs and facilitating successful pings between the two devices.
learn more about device here:
https://brainly.com/question/11599959
#SPJ11
Three short term goals?
Answers
eat well
get good sleep
go outside more
Explanation:
its just mine
As a Manager, you will find it difficult to operate on daily basis without a computer in your office and even at home. Evalauate this statement
Answers
As a manager, operating on a daily basis without a computer in both the office and at home would indeed pose significant challenges. Computers have become an essential tool in modern management practices, enabling efficient communication, data analysis, decision-making, and productivity enhancement.
In the office, a computer allows managers to access critical information, collaborate with team members, and utilize various software applications for tasks such as project management, financial analysis, and report generation. It provides a centralized platform for managing emails, scheduling meetings, and accessing company systems and databases.
Outside the office, a computer at home provides flexibility and convenience for remote work and staying connected. It enables managers to respond to urgent emails, review documents, and engage in virtual meetings. It also allows them to stay informed about industry trends, access online resources for professional development, and maintain a work-life balance through effective time management.
Without a computer, managers would face limitations in accessing and analyzing data, communicating efficiently, coordinating tasks, and making informed decisions. Their productivity and effectiveness may be compromised, and they may struggle to keep up with the demands of a fast-paced, technology-driven business environment.
In conclusion, a computer is an indispensable tool for managers, facilitating their daily operations, communication, and decision-making. Its absence would significantly impede their ability to perform their responsibilities effectively both in the office and at home.
To learn more about Computers, visit:
https://brainly.com/question/32329557
#SPJ11
soo I have a problem I have these Bluetooth headphones when I turn them on it tells me it's connected but when I try to listen to something on my computer it brings out no sound does anyone know a way to fix that
Answers
Answer:
troubleshoot it or maybe your volume is off. what type of headphones are they? if they are airpods then i dont think they can connect to devices that arent made by apple
Explanation:
Answer:
Enable Bluetooth Support Service
Set your default playback device
Check your volume levels
Update your Audio Driver
Run your Troubleshooting tool
Check audio problems in Device Manager
Explanation:
Try these
"Which problem does the Spanning Tree Protocol prevent?"
A) Broadcast storms
B) Routing loops
C) MAC address table overflow
D) Network congestion.
Answers
Answer: Routing loops. The Spanning Tree Protocol (STP) prevents the problem protocol generates a single spanning tree for the whole network. Ensures that there is no loop in the topology .However it does not meet today’s requirements.
inter-AS routing loops since it contains the subnet reachability data from AS. There are many various reasons the BGP router always choose the loop-free route with shortest AS –path length. Among them include, the router may contain one path or more to catch any one prefix.
When this happens, BGP can apply some elimination rules to catch the one route. However, a longer loop-free path is sometimes likely preferred than shorter AS–path length due to economic-driven reasons.
Learn more about Routing loops here
https://brainly.com/question/9257367
#SPJ11
when the parser parse's the current token stored in nexttoken then it calls the lexical analyzer's getnexttoken method how many times?
Answers
When the parser parses the current token stored in nextToken, then it calls the lexical analyzer's getNextToken method once.
The parser takes in a sequence of tokens and produces a syntax tree for them. In addition, parsers can validate whether the sequence of tokens satisfies a specific grammar or not. Lexical analysis is the process of converting a sequence of characters (such as in a computer program) into a sequence of tokens (strings with an identified meaning). A parser examines the sequence of tokens generated by the lexical analyzer and constructs a syntax tree based on it.The getNextToken method in the lexical analyzer class reads the next token from the input and returns it. When the parser encounters a particular token, it calls the getNextToken function, which reads the next token and returns it to the parser, which then processes it.In conclusion, when the parser parses the current token stored in nextToken, then it calls the lexical analyzer's getNextToken method once.
Learn more about parser here:
https://brainly.com/question/16979044
#SPJ11
In Cyclic coding, the dataword is 1011010 and the divisor 10011, what is the dividend at the sender A) 101101000 B) 1010110000 C) 10110100000 D) 10110101000 To correct 3 errors, the Hamming distance between each pair of codewords should be at least A) 4 B) 5 C) 6 D) 7
Answers
In cyclic coding, the message is treated as a series of digits, each of which is a coefficient of a polynomial. These digits are represented by the coefficients of a polynomial in the form of binary numbers. The polynomial is divided by a given polynomial, and the remainder obtained is the codeword.
The polynomial division is accomplished by using XOR (exclusive OR) subtraction of polynomials.
Dataword and Divisor in Cyclic coding:
The given dataword is 1011010, and the divisor is 10011. To get the dividend at the sender, follow the steps mentioned below:
Step 1: Multiply the dataword by 2^m, where m is the degree of the divisor. In this case, m is 4, so the dataword is multiplied by 2^4.
1011010 is the dataword, and 2^4 is the divisor.
1011010 00000 is the result of the multiplication.
Step 2: Divide the resulting number by the divisor. Perform this division using the modulo-2 method.
101101000 is the dividend that the sender has to send.
Hamming distance:
The minimum Hamming distance is the smallest number of bit positions at which any two encoded messages differ. The formula to find the minimum Hamming distance between the codewords is d min = minimum weight of all nonzero codewords.
If there are two codewords: 1100 and 0101. They differ at two positions. So, their Hamming distance is 2. To correct 3 errors, the Hamming distance between each pair of codewords should be at least 4.
To know more about polynomial visit:
https://brainly.com/question/11536910
#SPJ11
what is the full form for OMR?
Answers
Answer:
The full form of OMR is Optical Mark Recognition
Which composer below was not part of the classical period?
A. Beethoven B. Bach
C. Mozart
Answers
Explanation:
B. Bach
Thanks for your point
what is presentation software in bussiness used for
Answers
Answer:
Presentation software is a category of application software that is specifically designed to allow users to create a presentation of ideas by stringing together text, images and audio/video.
Explanation:
Answer:
Presentation software is a category of application software that is specifically designed to allow users to create a presentation of ideas by stringing together text, images and audio/video.
Explanation:
FILL THE BLANK. after bingeing on cakes and cookies, bonnie practices self-induced vomiting to avoid gaining weight. based on this information, you would expect to notice ________ as a sign of her purging behavior.
Answers
Based on this information, you would expect to notice signs of "dental erosion" as a result of Bonnie's purging behavior.
Self-induced vomiting can lead to the exposure of stomach acid to the teeth, which can erode the enamel and cause dental problems. This is a common consequence of purging behaviors in individuals with eating disorders. It is important to note that purging behaviors can have serious physical and psychological effects and should be addressed with appropriate support and treatment.
Learn more about dental erosion here;
https://brainly.com/question/32269821
#SPJ11
Take one action in the next two days to build your network. You can join a club, talk to new people, or serve someone. Write about this action and submit this as your work for the lesson. icon Assignment
Answers
Making connections is crucial since it increases your versatility.You have a support system of people you can turn to when things get tough so they can help you find solutions or in any other way.
What are the advantages of joining a new club?
Support Network - Joining a club or organization can help you develop a support network in addition to helping you make new acquaintances and meet people.Your teammates and friends will be there for you not only during practice but also amid personal difficulties. Working collaboratively inside a group, between groups, between communities, or between villages is known as network building.One method of creating a network is by forming a group. Attending events and conferences and developing connections with other attendees and industry speakers is one of the finest methods to build a strong network.In fact, the framework of many networking events and conferences encourages networking and connection opportunities. Personal networking is the process of establishing connections with organizations or individuals that share our interests.Relationship growth often takes place at one of the three levels listed below:Networks for professionals.Neighborhood networks.Personal networks. Reaching out is part of an active communication process that will help you learn more about the other person's interests, needs, viewpoints, and contacts.It is a life skill that needs to be actively handled in order to preserve or, more importantly, to advance a prosperous profession. various network types.PAN (personal area network), LAN (local area network), MAN (metropolitan area network), and WAN (wide area network) are the different types of networks.To learn more about network refer
https://brainly.com/question/28041042
#SPJ1
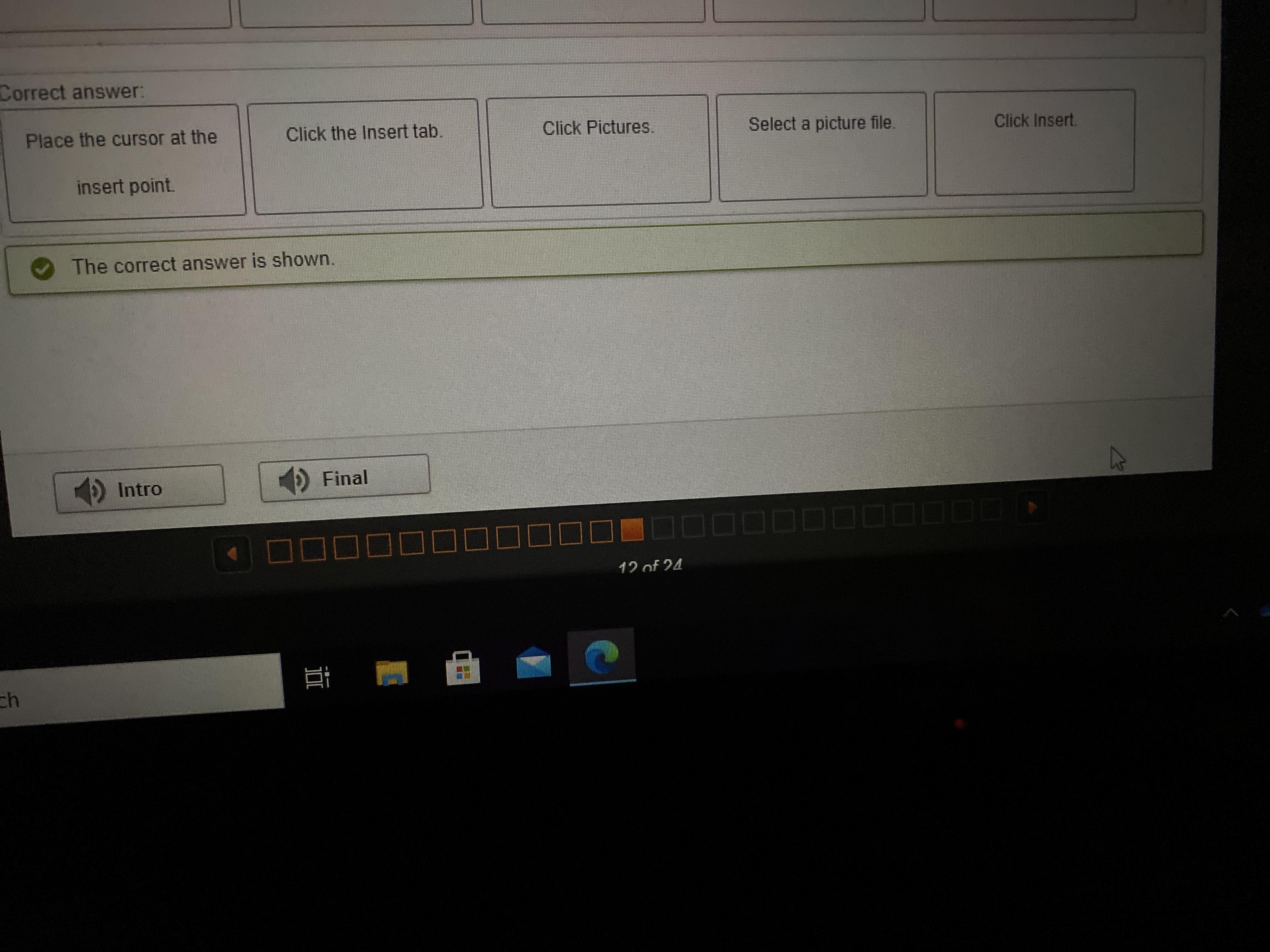
Describing How to Insert a Picture in a Document
What are the correct steps for inserting a picture into a Word 2016 document?
Click Insert.
Click Pictures.
Select a picture file.
Click the Insert tab.
Place the cursor at the
insert point.
Helllpppp
Answers
Answer:
Explanation:
Right answer
Python String Functions: Create a new Python Program called StringPractice. Prompt the user to input their name, then complete the following:
Length
• Print: “The length of your name is: [insert length here]”
Equals
• Test to see if the user typed in your name. If so, print an appropriate message
Really appreciate the help.
Answers
#Swap this value by your name. Mine is Hamza :)
my_name = "Hamza"
#Get input from user.
inp = input("What's your name?: ")
#Print the length of his/her name.
print("The length of your name is",len(inp),"characters.")
#Check if the input matches with my name?
#Using lower() method due to the case insensitive. Much important!!
if(inp.lower()==my_name.lower()):
print("My name is",my_name,"too! Nice to meet you then.")
how to enabled hardware assisted virtualization and data execution protection in the bios?
Answers
To make sure virtualization is enabled, check the BIOS settings. Navigate to Windows Features > Switch them on or off (you can search for it) If Hyper-V is running, turn it off. Reboot the computer.
How can I make the BIOS enable data execution protection?To access advanced system settings, select System and Security > System. Click Settings under the Performance heading on the Advanced tab. The Data Execution Prevention tab should be selected. Only turn on DEP for Windows apps and services that are absolutely necessary.
How do you make the BIOS enable virtualization?Press F10 as soon as the machine starts up to access BIOS Setup. Choose the Configuration tab with the arrow keys, then click Virtualization Technology. Choose Enable. To save the adjustments and exit BIOS, press f10.
To know more about BIOS visit:-
https://brainly.com/question/3364065
#SPJ4
what should you do if you want to change the rights first assigned to a user?
Answers
If you want to change the rights first assigned to a user, you can modify their user account settings.
If you want to change the rights first assigned to a user, you should follow these steps:
1. Identify the user whose rights you want to change.
2. Access the system, application, or platform where the user's rights are managed.
3. Locate the user management or permissions settings section within the system.
4. Find the specific user in the list of users and select them.
5. Modify the rights or permissions assigned to the user according to your desired changes.
6. Save or apply the changes made to the user's rights.
7. Inform the user about the changes in their rights, if necessary.
By following these steps, you can successfully change the rights first assigned to a user.
To learn more about permissions settings visit : https://brainly.com/question/21962698
#SPJ11
Collaboration, listening, and negotiating are considered __________ skills.
interpersonal
mathematical
personal
verbal
VERBAL IS NOT THE ANSWER SOMEONE HELP
Answers
Answer:
interpersonal
Explanation:
Interpersonal skills are the types of skills that enhance the individuals' social interaction and communication means with others whereby there is the establishment of social rules and references.
It involves social communication activities such as collaboration, listening, and negotiation.
Hence, in this case, the correct answer is "INTERPERSONAL SKILLS.
Answer:
A. is correct
Explanation:
TASK 1 – Work out the cost.
The cost of the trip for each student is a share of the cost of a coach plus the cost of entry to the theme park.
The total cost of the coach will be $550. The entry cost to the park is $30 for each student. The national park gives one free ticket for every ten that are bought, which must be taken into consideration.
Set up a program that:
• stores the cost of the coach
• stores the cost of an entry ticket
• inputs the estimated number of students taking part, this must be validated on entry and an
unsuitable entry rejected
• calculates and outputs the recommended cost per student to ensure the trip does not make a loss.
Write an algorithm to complete Task 1, using either pseudocode, programming statements or a
flowchart. [5]
Answers
Answer:
please check the question again
Explanation:
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

In order to perform a calculation in a spreadsheet, you need to use a:
A) Variable
B) Formula
C) Table
D) None of the above
Answers
Answer:
B formula
Explanation:
took this last year
write a program that removes all non-alpha characters from the given input. ex: if the input is: -hello, 1 world$!
Answers
Here's a Python program that removes all non-alpha characters from the given input```python input_string = "-hello, 1 world$!" output_string = "" for char in input_string: if char.isalpha(): output_string += char print(output_string) When you run this program, it will output the following string.
helloworld This program starts by defining an input string variable that contains the text we want to remove non-alpha characters from. We also define an empty output string variable to hold the final result. we loop through each character in the input string using a for loop. For each character, we use the `isalpha()` method to check if it's an alphabetic character.
If it is, we append it to the output string using the `+=` operator. After looping through all the characters in the input string, we print out the output string that contains only the alphabetic characters. The `isalpha()` method is a built-in Python function that returns `True` if a character is an alphabetic character and `False` otherwise. In our program, we use this method to check each character in the input string and only add it to the output string if it is alphabetic. The `+=` operator is a shorthand way of concatenating strings. In our program, we use it to append each alphabetic character to the output string as we loop through the input string. Overall, this program is a simple way to remove non-alpha characters from a given input string. To write a program that removes all non-alpha characters from the given input, such as "-hello, 1 world$!", follow these Define the input string. Create an empty string called "result". Iterate through each character in the input string. Check if the character is an alphabetical character If it is, add it to the "result" string. Print the "result" string. Here's a sample Python program using the above explanation`python # Step 1: Define the input string input_string = "-hello, 1 world$!"# Step 2: Create an empty string called "result" result = "" # Step 3: Iterate through each character in the input strinfor char in input_string:# Step 4: Check if the character is an alphabetical character if char.isalpha(): # Step 5: If it is, add it to the "result" string result += char Print the "result" strin print(result) Running this program with the input "-hello, 1 world$!" would result in the output "helloworld".
To know more about removes visit:
https://brainly.com/question/30455239
#SPJ11
A data set includes data from 500 random tornadoes. The display from technology available below results from using the tornado lengths (miles) to test the claim that the mean tornado length is greater than 2.2 miles. Use a 0.05 significance level. Identify the null and alternative hypothesis, test statistic, P-value, and state the final conclusion that addresses the original claim. LOADING... Click the icon to view the display from technology. What are the null and alternative hypotheses
Answers
Answer:
The answer is:
\(H_0:\mu=2.2\\H_1:\mu> 2.2\)
Explanation:
\(H_0:\mu=2.2\\H_1:\mu> 2.2\)
The test value of statistic t= \(\frac{\bar x-\mu}{\frac{s}{\sqrt{n}}}\)
\(=\frac{2.31688-2.2}{0.206915}\\\\=0.56\)
The value of P = P(T>0.56)
=1-P(T<0.56)
=1-0.712
=0.288
Since the P value exceeds its mean value (0.288>0.05), the null assumption must not be rejected. Don't ignore H0. This assertion, it mean length of the tornado is greater than 2.2 miles also isn't backed by enough evidence.