For this assignment, we are building on the previous assignment and developing a function that we will use for our final project. Add this function to your code from assignment 1 and update the docstring. Make a copy of assignment_1 and name it assignment_2. When updating the docstring be sure to add a short description of this assignment just above the description of assignment 1. Hand in only one program, please. Be sure to update the docstring to include the functionality that you are adding in this assignment.
Temperature Conversions
Implement the function:
convert_units(celsius_value, units)
that accepts two arguments, a float (celsius_value) and an int (units).
The function will return the supplied temperature, converted as follows:
- If units = 0, return temperature in Celsius (no change)
- if units = 1, return temperature in Fahrenheit
- if units = 2, return temperature in Kelvin
Prompt the user for the Celsius temperature and units in main(), the unit-test code. If the user enters an invalid units value (something other tn 0, 1,or 2 be sure to tell the user and then end the program. In the real world, you would also want to figure out valid values for celsius_value. Don't worry about prompting the user to reenter the units, just tell them to run the program again. When we learn about loops, we will prompt again when invalid input is presented.
Note that the function must only return a float (floating point number), not a string. This float is the result of the conversion done by the convert_units() function. Your convert_units() function performs the computation based on the arguments passed, the main() function will handle all input/output. The main() function contains the unit-test code.
Formulas:
T(°F) = T(°C) × 9/5 + 32
T(°k) = T(°C) + 273.15
Unit Test
Unit testing is a testing method by which individual units of source code are tested to determine if they are ready to use. In the main() function, add code that asks the user to input the temperature in Celsius, and then the program should print the temperature converted to the temperature requested by the user, using f-strings. This code in the main function is called a "unit test" because its only purpose is to test an individual unit of your code. In this case, you want to test the function convert_units.
As happens frequently in the English language we are using the word unit in two completely different contexts. The term unit test is a test designed to test just one function or a related group of functions. The word units in converts_units if referring to units used in the measurement of temperature.
The unit test code will be removed from main() in the next assignment, it will be replaced by the unit test code for Lab Assignment 3. Be sure to include at least four sample runs of your program! One for each of the three valid conversions and one responding to an invalid request. The validation of the input will be done by convert_unit, not main(). convert_units will be used later in the project.
Again, the requirements:
You function signature must exactly match: convert_units(celsius_value, units)
Your convert_units function must accept unit values of 0, 1, or 2.
Your convert_units function will return an error code to the calling function (main()) for any other values and the calling function will notify the user of the error.
Your convert_units() function should be able to accept and convert any Celsius value
Your convert_units() function should return a float value (not a string) based on what value was passed to the units parameter
Your convert_units() function should not print anything.
You must use f-strings to incorporate numbers into the output.
Don't forget the
if __name__ == "__main__" logic as described in the modules.
Can someone please help me its due on april 23. and the code needs to be in python.
Answers
Answer:
def convert_units(celsius_value, units):
if units == 0:
return celsius_value
elif units == 1:
return celsius_value * 9/5 + 32
elif units == 2:
return celsius_value + 273.15
else:
return -1 # error code for invalid units input
if __name__ == "__main__":
celsius = float(input("Enter temperature in Celsius: "))
unit = int(input("Enter desired unit of conversion (0 for Celsius, 1 for Fahrenheit, 2 for Kelvin): "))
converted_temp = convert_units(celsius, unit)
if converted_temp == -1:
print("Invalid units input. Please enter 0, 1, or 2.")
else:
print(f"The temperature in {['Celsius', 'Fahrenheit', 'Kelvin'][unit]} is {converted_temp:.2f}.")
Explanation:
In the code, we define the convert_units function that takes in a Celsius temperature value (celsius_value) and an integer representing the desired unit of conversion (units). We use a conditional statement to check which conversion is requested and return the temperature value in that unit. If an invalid unit is provided, we return -1 as an error code.
In the if __name__ == "__main__" block, we prompt the user to enter the temperature in Celsius and the desired unit of conversion. We then call the convert_units function with these inputs and store the result in converted_temp. We check if the result is -1 (i.e. an invalid unit was provided) and notify the user of the error. Otherwise, we use an f-string to print the converted temperature with two decimal places and the corresponding unit.
Here are four sample runs of the program:
Enter temperature in Celsius: 25
Enter desired unit of conversion (0 for Celsius, 1 for Fahrenheit, 2 for Kelvin): 1
The temperature in Fahrenheit is 77.00.
Related Questions
let Xi; i=1,2....,n from distribution with p.d.f , f(x) = ϑx^ϑ-1, 0
Answers
Answer:
User is very angry...................
..
> var direction = []; directions.push("walk to corner");//1 directions.push("turn right");//2 directions.push("walk one block");//3 directions.push("turn left");//4 directions.push("walk to gray house");//5 directions.push("go down the strairs");//6 directions.push("knock on the pink door");//7 console.log(directions); "knock on the pink (7) ["walk to corner", "turn right", "walk one block", "turn left", "walk to the gray house", "go down the astairs" door",]
is dis code correct
Answers
Answer:
no it's not correct.........
Using "subTotal" and "taxRate", what is the formula to determine the total bill including taxes (grandTotal)?
Answers
Answer:
The formula to determine the total bill including taxes, i.e. grand Total =
"subTotal" + ("taxRate" * "subTotal").
Another formula is:
"grandTotal" = ("subTotal" * 1 +"taxRate")
Explanation:
The above stated formulas produce the same outcome. The first formula computes the tax amount and adds it to the subtotal before arriving at the grand total. The second formula goes straight to compute the total bill without showing the tax amount. It applies the tax factor (1 + "taxRate") to the "subTotal." All two formulas are valid. However, I prefer the second formula to the first, as it is very straight forward.
what are the steps involved in adding headers and footers to a Microsoft word document.
Answers
hey!!
your ans is here...
steps :
1.Click on insert tab.
2.Click on the header button or footer button.
suppose u have click on header..
3. A list of various header styles appears. Now u can select the required style.
Thanks
Hope it helps u.. mark as brainlist..Help pls.
Write python 10 calculations using a variety of operations. Have a real-life purpose for each calculation.
First, use Pseudocode and then implement it in Python.
For example, one calculation could be determining the number of gallons of gas needed for a trip based on the miles per gallon consumed by a car.
Answers
A python program that calculates the number of gallons of gas needed for a trip based on the miles per gallon consumed by a car is given below:
The Programdef printWelcome():
print ('Welcome to the Miles per Gallon program')
def getMiles():
miles = float(input('Enter the miles you have drove: '))
return miles
def getGallons():
gallons = float(input('Enter the gallons of gas you used: '))
return gallons
def printMpg(milespergallon):
print ('Your MPG is: ', str(milespergallon))
def calcMpg(miles, gallons):
mpg = miles / gallons
return mpg
def rateMpg(mpg):
if mpg < 12:
print ("Poor mpg")
elif mpg < 19:
print ("Fair mpg")
elif mpg < 26:
print ("Good mpg")
else:
print ("Excellent mpg")
if __name__ == '__main__':
printWelcome()
print('\n')
miles = getMiles()
if miles <= 0:
print('The number of miles cannot be negative or zero. Enter a positive number')
miles = getMiles()
gallons = getGallons()
if gallons <= 0:
print('The gallons of gas used has to be positive')
gallons = getGallons()
print('\n')
mpg = calcMpg(miles, gallons)
printMpg(mpg)
print('\n')
rateMpg(mpg)
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
fine the average of 5,2,3
Answers
Answer:
3 1/3
Explanation:
If you can answer theses ill give u a brainliest (i think thats how u spell it) but only if u get it right u will get one NOT A SCAM!!
Question: In which logical operator at least one condition has to be true?
O or
O None of the above
O not
O and
Question: In which logical operator both conditions must be true?
O and
O or
O not
O None of the above
Answers
Answer:
or / and
Explanation:
i took the quiz at unitek college
Answer:
1. or
2. and
Explanation:
25)What are HITs?
A. Heuristic Identity Tables
B. Human Interactivity Tests
C. Help and Information Tools
D. Higher Instruction Transducers
E. Human Intelligence Tasks
Answers
Answer:
A. Heuristic Identity Tables
Explanation:
Write a program to print the prime numbers from 500 to 700. The program should also print the count of prime numbers between 500 and 700. A number is called a prime number if it has exactly two positive divisors, 1 and the number itself. For example, the number 5 is prime as it has only two divisors: 1 and 5.
Answers
primes = 0
for x in range(500, 701):
count = 1
for w in range(2, x+1):
if x % w == 0:
count += 1
if count < 3:
print(x, end=" ")
primes += 1
print("\nThere are {} prime numbers between 500 and 700".format(primes))
I hope this helps!
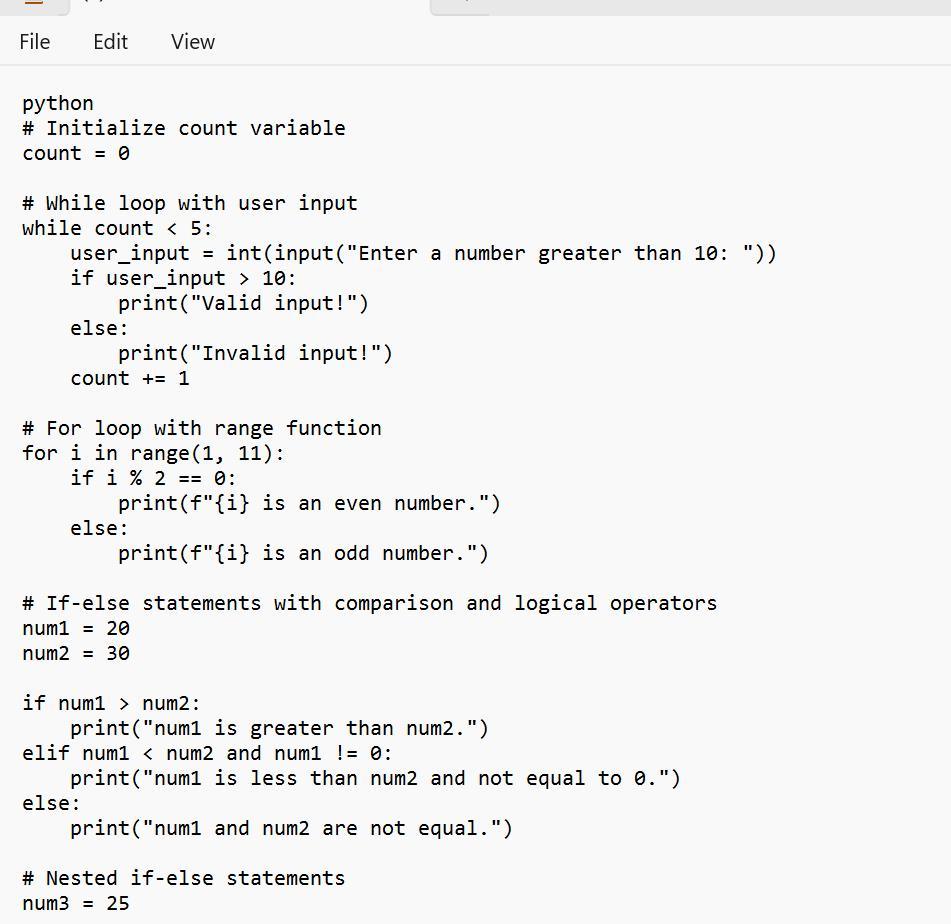
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

Parallel Computing and Distributed Computing
Sequential computing has been great, but computer scientists need every speed and storage advantage they can get. Clever computer scientists have found even more efficient ways to use computer hardware for certain types of problems.
parallel Computing
Parallel computing is the use of a computer that performs multiple instructions at the same time. The programs used for parallel computing must be designed so they can be broken down into smaller independent parts that each processor can work on.
Parallel computing uses multiple computing cores. A computing core is one processor in the CPU. Parallel computers will have many different processors in their CPUs instead of just one.
Speedup in Parallel Computing
The advantage of a parallel computing solution over a sequential computing solution can be measured in speedup. Speedup is the amount of time used to perform a task with sequential computation divided by the amount of time used to perform the same task with parallel computation.
For example, imagine that you run a program on a sequential computer and it takes 10 minutes to complete. Next, you run the same program on a parallel computer and it takes 5 minutes to complete. You would divide the 10 by the 5 and come up with a speedup of 2. This means your program is two times faster on a parallel computer.
Distributed Computing
Many computer problems are so complex that they take an extremely long time to run on one computer. Distributed computing is the use of multiple computers to solve a problem. Distributed computing is like parallel computing but with many different computers; parallel computing is the use of one computer with many different processors.
QUESTION:
A program takes 10 minutes to compute sequentially and has a speedup of 2 on a parallel computer, meaning it takes how many minutes. ??
Answers
Answer:
5 minutes
Explanation:
It is there in the section on Speedup in Parallel Computing
For example, imagine that you run a program on a sequential computer and it takes 10 minutes to complete. Next, you run the same program on a parallel computer and it takes 5 minutes to complete. You would divide the 10 by the 5 and come up with a speedup of 2
https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
The data component of an information system is:Group of answer choicesthe input to the information system.the output of the information system.a series of integrated files containing relevant facts.a set of facts that have been analyzed by the process componen
Answers
Answer:
The input to the information system.
Explanation:
An information system interacts with its environment by receiving data in its raw forms and information in a usable format.
Information system can be defined as a set of components or computer systems, which is used to collect, store, and process data, as well as dissemination of information, knowledge, and distribution of digital products.
Generally, it is an integral part of human life because individuals, organizations, and institutions rely on information systems in order to perform their duties, functions or tasks and to manage their operations effectively. For example, all organizations make use of information systems for supply chain management, process financial accounts, manage their workforce, and as a marketing channels to reach their customers or potential customers.
Additionally, an information system comprises of five (5) main components;
1. Hardware.
2. Software.
3. Database.
4. Human resources.
5. Telecommunications.
Hence, the information system relies on the data it receives from its environment, processes this data into formats that are usable by the end users.
Therefore, the data component such as hardware and software of an information system is the input to the information system.
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
Valiant is an NGO that has very strong opinions against the government. It has faced a number of legal notices and its IP address has been blocked numerous times for voicing out dissent on online forums and social media. Valiant has requested your help as a network analyst to find a way around this problem so that it won't receive any more legal notices due to IP address tracking. Which of the following methods will you use in this scenario?
1. Proxy server
2. Firewall
3. IDS
4. IPS
Answers
In this situation, firewall techniques will you employ.
The firewall's definition ?The monitoring and filtering of incoming and outgoing network traffic by a firewall, a network security tool, is done in accordance with the security policies that have already been defined by the company. Essentially, a firewall is the wall that separates a private internal network from the public Internet.
What are the three types of firewalls?There are four main kinds of firewalls, depending on how they work. a packet-filtering firewall. Firewalls that use packet filtering are the most traditional and fundamental. Routers at the circuit level. Stateful Check Firewalls. Applied-Level Gateways (Proxy Firewalls).
To know more about firewall techniques visit :-
https://brainly.com/question/13055134
#SPJ1
An electronics technician who enjoys working "at the bench" would most likely want to work
Answers
Answer: for a manufacturer
Explanation:
The options include:
A. for a manufacturer.
B. as a microwave technician.
C. as a central office technician.
D. for a TV or radio station.
An electronics technician who enjoys working "at the bench" would most likely want to work with a manufacturer.
In this case, if the person wants to work at the bench since he or she enjoys it, then the person should work for a manufacturer.
Write a function, named series_of_letters, that takes a reference to a vector of chars and returns nothing. The function should modify the vector to contain a series of letters increasing from the smallest letter (by ASCII value) in the vector. Note, the vector should not change in size, and the initial contents of the vector (excepting the smallest letter) do not matter.
Answers
Answer:
Follows are the code to this question:
#include <iostream>//defining header file
#include <vector>//defining header file
#include <algorithm>//defining header file
#include <iterator>//defining header file
using namespace std;//use namespace
void series_of_letters(vector<char> &d)//defining a method series_of_letters that accept a vector array
{
char f = *min_element(d.begin(), d.end()); //defining a character array that holds parameter address
int k = 0;//defining integer vaiable
std::transform(d.begin(), d.end(), d.begin(), [&f, &k](char c) -> char//use namespace that uses transform method
{
return (char)(f + k++);//return transform values
});
}
int main() //defining main method
{
vector<char> x{ 'h', 'a', 'd' };//defining vector array x that holds character value
series_of_letters(x);//calling series_of_letters method
std::copy(x.begin(),x.end(),//use namespace to copy and print values
std::ostream_iterator<char>(std::cout, " "));//print values
}
Output:
a b c
Explanation:
In the above code, a method "series_of_letters" is defined that accepts a vector array in its parameter, it uses a variable "d" that is a reference type, inside the method a char variable "f" is defined that uses the "min_element" method for holds ita value and use the transform method to convert its value.
Inside the main method, a vector array "x" is defined that holds character value, which is passed into the "series_of_letters" to call the method and it also uses the namespace to print its values.
A software approach to mutual exclusion is Lamport's bakery algorithm,so called because it is based on the practice in bakeries and other shops in which every customer receives a numbered ticket on arrival, allowing each to be served in turn.The algorithm is as:

Answers
Answer:
I am sorry
Explanation:
I don't answers
follow me
During a user’s onboarding process, many designers focus on a gradual release of information. This process is called what?
Answers
progressive disclosure
Which of the factors below is NOT a cause of online disinhibition?
O Anonymity
O Lack of nonverbal cues
Lack of tone of voice
Smartphones

Answers
Answer:
Lack of tone of voice
Explanation:
Remember, online disinhibition refers to the tendency of people to feel open in communication via the internet than on face to face conversations.
A lack of tone voice isn't categorized as a direct cause of online disinhibition because an individual can actually express himself using his tone of voice online. However, online disinhibition is caused by people's desire to be anonymous; their use of smartphones, and a lack of nonverbal cues.
write a valid HTML + Python page that will count numbered from 1 to 1,000,000?
Answers
Answer:
I remember before the corona virus we used to do math at school
which of the following file formats cannot be imported using Get & Transform
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
In this question, the given options are:
A.) Access Data table
B.)CVS
C.)HTML
D.)MP3
The correct option to this question is D- MP3.
Because all other options can be imported using the Get statement and can be further transformed into meaningful information. But MP3 can not be imported using the GET statement and for further Transformation.
As you know that the GET statement is used to get data from the file and do further processing and transformation.
Which statement about a modular power supply is true?
Answers
The true statement about a modular power supply is A. Modular power supplies allow for the customization and flexibility of cable management.
Modular power supplies provide the advantage of customizable cable management. They feature detachable cables that can be individually connected to the power supply unit (PSU) as per the specific requirements of the computer system.
This modular design enables users to connect only the necessary cables, reducing cable clutter inside the system and improving airflow.
With a modular power supply, users can select and attach the cables they need for their specific hardware configuration, eliminating unused cables and improving the overall aesthetic appearance of the system. This customization and flexibility make cable management easier and more efficient.
Additionally, modular power supplies simplify upgrades and replacements as individual cables can be easily detached and replaced without the need to replace the entire PSU.
This enhances convenience and reduces the hassle involved in maintaining and managing the power supply unit.
Therefore, option A is the correct statement about modular power supplies.
For more questions on PSU, click on:
https://brainly.com/question/30226311
#SPJ8
I think this is the question:
Which statement about a modular power supply is true?
A. Modular power supplies allow for the customization and flexibility of cable management.
B. Modular power supplies are less efficient than non-modular power supplies.
C. Modular power supplies are only compatible with specific computer models.
D. Modular power supplies require additional adapters for installation.
Describe a cellular network, its principle
components and how it works.
Answers
A cellular network is a contact network with a wireless last connection. The network is divided into cells, which are served by at least one fixed-location transceiver station each. These base stations provide network coverage to the cell, which can be used to send voice, data, and other types of information. It's often referred to as a mobile network.
The principal components of the cellular network will be explained below as follows-
BTS (Base Transceiver Station) - It is the most important part of a cell since it links subscribers to the cellular network for data transmission and reception. It employs a network of antennas that are dispersed across the cell.
BSC (Basic Station Controller) - It is a portion that interfaces between Basic Station Controllers and is connected to Basic Station Controllers via cable or microwave links, as well as routing calls between Basic Station Controllers and the MSC (Mobile Switching Center).
MSC (Mobile Switching Center) - The supervisor of a cellular network is linked to several Basic Station Controllers and routes cells between them. It also connects the cellular network to other networks such as the PSTN through fiber optics, microwave, or copper cable.
A cellular network works when the SIM card is organized into geographical cells, each of which has an antenna that transmits to all mobile phones in the city, cellular networks operate by knowing the exact location, which comes from the SIM card. A transmitter generates an electrical signal, which is converted by the transmit antenna into an electromagnetic wave, which is then radiated, and the RF wave is then converted back into an electrical signal. In cellular network networks, four multiple access schemes are used, ranging from the first analog cellular technologies to the most modern cellular technologies.
Describe the legend of Steve Job
Answers
Answer: Steve Jobs was a real person and not a legendary figure. However, his life and work have become the stuff of legend, and he is widely considered to be one of the most influential figures in the history of technology.
Jobs co-founded Apple Inc. in 1976 with Steve Wozniak and helped to create some of the most iconic products in the history of computing, including the Macintosh computer, the iPod, and the iPhone.
He was known for his visionary leadership style, his focus on design and user experience, and his ability to anticipate and shape consumer trends. Steve passed away in 2011, but his legacy still passes on till this day.
Read the following statement and state whether True or False.
A. Fateh Burj is located in Mohall (Punjab).__________
8. Pongal is celebrated in West Bengal.__________
C. Chand minar is also known as the Tower of Moon'.________
D. Rabindra Nath Tagore stared the 'Shanti Niketan' school.__________
E The national sport of India is football.________
Answers
Answer:
A. false
8. false
c. true
d. true
e false
Answer:
A. False
B. False
C. True
D. True
E. False
100 point question, with Brainliest and ratings promised if a correct answer is recieved.
Irrelevant answers will be blocked, reported, deleted and points extracted.
I have an Ipad Mini 4, and a friend of mine recently changed its' password ( they knew what the old password was ). Today, when I tried to login to it, my friend claimed they forgot the password but they could remember a few distinct details :
- It had the numbers 2,6,9,8,4, and 2 ( not all of them, but these are the only possible numbers used )
- It's a six digit password
- It definitely isn't 269842
- It definitely has a double 6 or a double 9
I have already tried 26642 and 29942 and my Ipad is currently locked. I cannot guarantee a recent backup, so I cannot reset it as I have very important files on it and lots of memories. It was purchased for me by someone very dear to me. My question is, what are the password combinations?
I have already asked this before and recieved combinations, however none of them have been correct so far.
Help is very much appreciated. Thank you for your time!
Answers
Based on the information provided, we can start generating possible six-digit password combinations by considering the following:
The password contains one or more of the numbers 2, 6, 9, 8, and 4.
The password has a double 6 or a double 9.
The password does not include 269842.
One approach to generating the password combinations is to create a list of all possible combinations of the five relevant numbers and then add the double 6 and double 9 combinations to the list. Then, we can eliminate any combinations that include 269842.
Using this method, we can generate the following list of possible password combinations:
669846
969846
669842
969842
628496
928496
628492
928492
624896
924896
624892
924892
648296
948296
648292
948292
Note that this list includes all possible combinations of the relevant numbers with a double 6 or a double 9. However, it is still possible that the password is something completely different.
Select the correct answer from each drop-down menu.
Tanya wants to include an instructional video with all its controls on her office website. The dimensions of the video are as follows:
width="260"
height="200"
What code should Tanya use to insert the video?
To insert the video, Tanya should add the following code:
✓="video/mp4">

Answers
The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
How to explain the informationTanya can use the following code to insert the video with all its controls on her office website:
<video width="260" height="200" controls>
<source src="video.mp4" type="video/mp4">
<source src="video.ogg" type="video/ogg">
Your browser does not support the video tag.
</video>
The width and height attributes specify the dimensions of the video player. The controls attribute specifies that the video player should display all its controls. The source elements specify the location of the video files.
The first source element specifies the location of the MP4 file, and the second source element specifies the location of the Ogg file. The browser will use the first file that it supports. If the browser does not support any of the files, the text between the video and </video> tags will be displayed.
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
1. In your own words, describe the purpose of a for a loop.
Now think of one website, app, or machine that you use that you think uses a for loop
Answers
A for loop is typically used in situations where the number of cycles for the loop is known before hand. One thing that uses for loops is video rendering software, it uses it to render each file and allocate each rendered file to its specified destination.
Answer:
calc
Explanation:
On a system with paging, a process cannot access memory that it does not own. Why? How could the operating system allow access to other memory?
Answers
Answer:
Because the page is not in its page tableThe operating system could allow access to other memory by allowing entries for non-process memory to be added to the process page tableExplanation:
On a system with paging, a process cannot access memory that it does not own because the page is not in its page table also the operating system controls the contents of the table,therefore it limits a process of accessing to only the physical pages allocated to the process.
The operating system could allow access to other memory by allowing entries for non-process memory to be added to the process page table.that way two processes that needs to exchange data can efficiently do that . i.e creating a very efficient inter-process communication