Find the error in the statement below.
if height_variable > 59;
print("You can ride this roller coaster.")
The opening parenthesis should be at the beginning of the second line.
The second line should not be indented.
The semi-colon should be a colon.
The > should be a <
Answers
Answer:
The semi-colon, should be a colon
Explanation:
The error in the statement below is a semi colon should be a colon.
What is error?Error is defined as a violation of a code of conduct due to ignorance or imprudence. A bug is a mistake in computer data. An mistake, flaw, failure, or fault in a computer program or system that results in it producing an inaccurate or unexpected result or behaving in an unexpected manner is known as a software bug.
The second line should begin with the opening parenthesis. There is no need to indent the second line. if the measurement tool or instrument is the same between the two operators. It's not required for two operators to produce results that are similar. There are three different sorts of faults: burst errors, multiple bit errors, and single bit errors.
Thus, the error in the statement below is a semi colon should be a colon.
To learn more about error, refer to the link below:
https://brainly.com/question/19575648
#SPJ5
Related Questions
a global information system (gis) is capable of supporting global decisions. what are the environmental factors that affect the complexity of such decisions?
Answers
Environmental factors that affect the complexity of decisions supported by a global information system (GIS) include scale, diversity of stakeholders, uncertainty, data quality, and resource constraints.
Environmental factors that affect the complexity of decisions in a global information system (GIS) are numerous. GIS, like any other information system, is subject to environmental influences that can affect its overall effectiveness. As a result, GIS systems must be built to consider a variety of environmental variables that may affect their efficiency.Global information systems (GIS) are essential in many areas of human activity. GIS systems are used to track and manage environmental factors, land use, health concerns, public security, and a variety of other variables in order to ensure that human activity is both effective and sustainable. Environmental variables may be understood as the various variables that influence the actions of humans and the natural environment that surrounds them.In order to be effective, GIS systems must account for these variables and determine how they affect the decision-making process. This may involve collecting and analyzing data on climate, geography, population density, resource availability, and a variety of other variables.
Learn more about variables here:
https://brainly.com/question/29699537
#SPJ11
The three greater-than signs, >>>, represent a _____.
A. prompt
B. file-path
C. file name
D. IDLE
Answers
Answer:
it's A. prompt
Explanation:
difference between sorting and filtering
Answers
Answer:
Essentially, sorting and filtering are tools that let you organize your data. When you sort data, you are putting it in order. Filtering data lets you hide unimportant data and focus only on the data you're interested in.
Explanation:
Hope this will help
The term “sorting” is used to refer to the process of arranging the data in ascending or descending order.
Example: Statistical data collected can be sorted alphabetically or numerically based on the value of the data.
FilteringThe process of data filtering involves selecting a smaller part of your data set to view or analyze. This is done by using that subset to view or analyze your data set as a whole.
Example: A complete set of data is kept, but only a portion of that set is used in the calculation, so the whole set is not used.
Hope this helps :)
What will be the value of sum? after executing the code snippet below. Use summation notation to compute the time complexity of the code snippet below?
sum = 0; for (i = 0, i < n, i++) { for (j = n, j > 0, j==) { sum = sum + i * j;}}
Answers
The value of "sum" after executing the code snippet will depend on the value of "n." The time complexity of the code can be computed using summation notation, which indicates the number of iterations performed by the nested loops.
The given code snippet initializes the variable "sum" to 0. It then uses two nested loops to iterate over the values of "i" and "j." The outer loop iterates from 0 to "n" (exclusive), and the inner loop iterates from "n" to 1 (inclusive). In each iteration, the code increments the value of "sum" by the product of "i" and "j" (i * j).
The final value of "sum" will depend on the value of "n" and the number of iterations performed by the nested loops. The code snippet calculates the sum of products for each combination of "i" and "j" in the given range.To compute the time complexity of the code snippet, we can use summation notation. The outer loop iterates "n" times, and the inner loop iterates "n" times as well. Therefore, the total number of iterations is the product of "n" and "n," which is n^2. The time complexity can be expressed as O(n^2), indicating that the code has a quadratic time complexity with respect to the input size "n."
Learn more about nested loops here:
https://brainly.com/question/30895403
#SPJ11
______ is a way of preventing errors when data is copied from one medium to another.
Answers
Answer:
Verification.
Explanation:
A database management system (DBMS) can be defined as a collection of software applications that typically enables computer users to create, store, modify, retrieve and manage data or informations in a database. Generally, it allows computer users to efficiently retrieve and manage their data with an appropriate level of security.
A data dictionary can be defined as a centralized collection of information on a specific data such as attributes, names, fields and definitions that are being used in a computer database system.
In a data dictionary, data elements are combined into records, which are meaningful combinations of data elements that are included in data flows or retained in data stores.
This ultimately implies that, a data dictionary found in a computer database system typically contains the records about all the data elements (objects) such as data relationships with other elements, ownership, type, size, primary keys etc. This records are stored and communicated to other data when required or needed.
Verification is a way of preventing errors when data is copied from one medium to another. The verification process doesn't check to confirm if the data copied is within an acceptable boundary (range) or if it makes sense (logical). Instead, it would only ensure that the data copied is the same as those from the original source.
what are the three basic storage of computer
Answers
Answer:
hard disk drive, Rom and USB flash memory
Explanation:
I hope it helps you
Answer:
RAM,ROM ,Magnetic tape,
Explanation:
CD ROM,DVD ROM,
Answer:
RAM,ROM ,Magnetic tape,
Explanation:
CD ROM,DVD ROM,
What aws feature permits you to create persistent storage volumes for use by ec2 instances (including boot)?
Answers
The AWS feature that permits you to create persistent storage volumes for use by EC2 instances (including boot) is called Amazon Elastic Block Store (Amazon EBS).
Amazon Elastic Block Store (Amazon EBS) is a block-level storage service provided by AWS that allows you to create and attach persistent storage volumes to EC2 instances. It provides durable block-level storage that can be used as primary storage for boot volumes or additional storage for data and applications.
Here are some key features and capabilities of Amazon EBS:
1. Persistent Storage: Amazon EBS volumes are independent storage units that persist independently of the EC2 instances they are attached to. This means that data stored on EBS volumes remains even if the associated EC2 instance is terminated or stopped.
2. High Durability: Amazon EBS volumes are replicated within an Availability Zone (AZ) to provide high durability. This replication ensures that your data is protected against hardware failures.
3. Flexibility: You can create Amazon EBS volumes of different types and sizes to meet your specific storage requirements. You can also attach multiple volumes to a single EC2 instance, allowing for increased storage capacity and performance.
4. Snapshot and Backup: Amazon EBS provides the ability to take point-in-time snapshots of volumes, which can be used for backup, replication, and data migration purposes. Snapshots are stored in Amazon Simple Storage Service (S3) and can be used to create new volumes.
Amazon Elastic Block Store (Amazon EBS) is the AWS feature that allows you to create persistent storage volumes for EC2 instances. With its durability, flexibility, and snapshot capabilities, Amazon EBS provides reliable and scalable storage solutions for a variety of use cases, including boot volumes and additional data storage for EC2 instances.
To know more about AWS , visit
https://brainly.com/question/14014995
#SPJ11
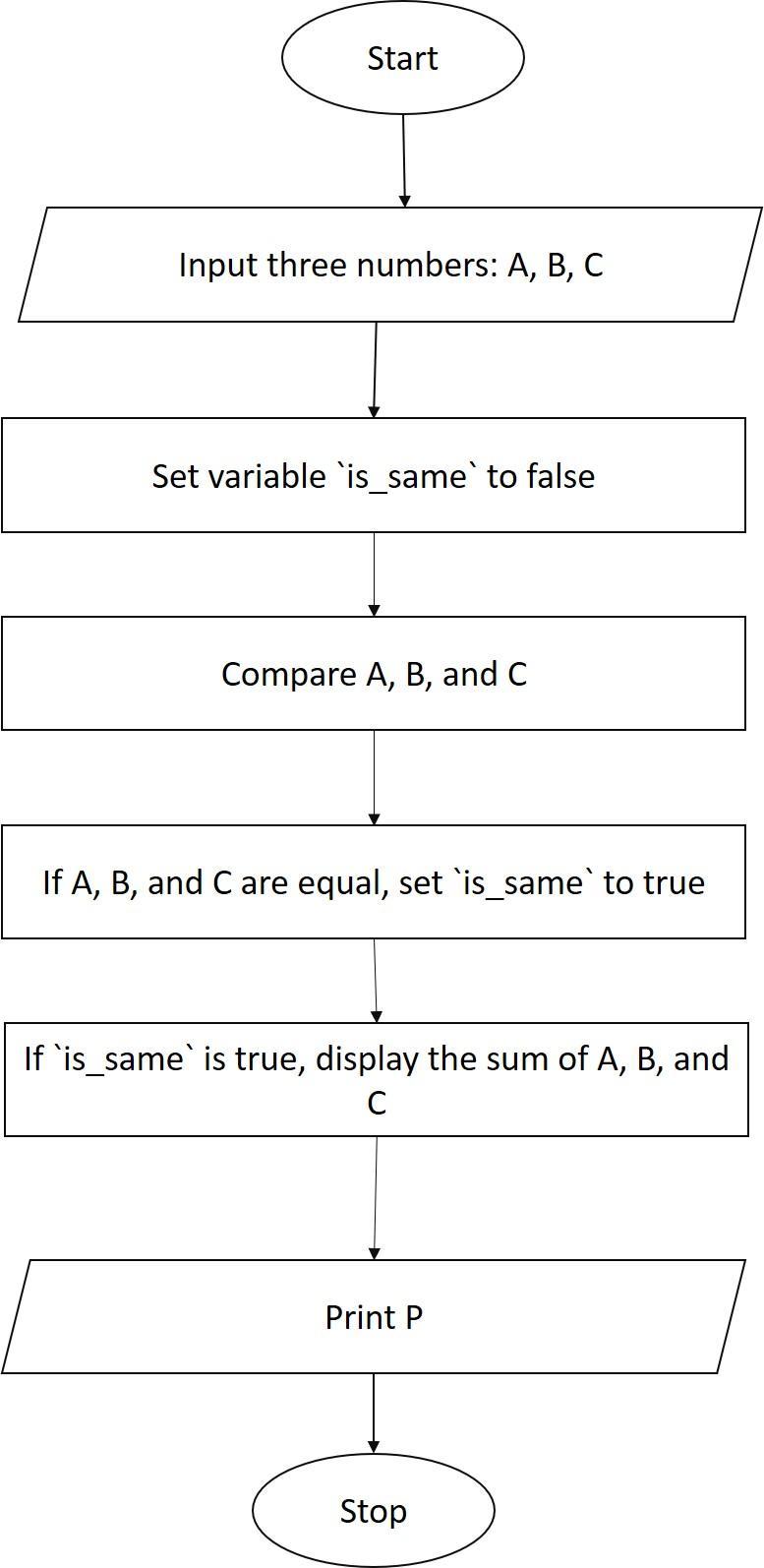
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
write some general rules used while chatting
Answers
Answer:
Well,
Explanation:
Well, this topic is a very broad one and I'm not exactly sure what kind of information you' like provided, but I got a few ideas in mind.
While chatting online, a big letdown for most people is if you curse and especially if you do it excsessivley. Doing so will make you seem toxic and most people would just try to avoid you.
Talking about toxicity, being a toxic person online is petty and quite pathetic. Gloating and raising your ego won't make you any more of a liekable person online, or even in the real world.
Last but not least, another general rule of online chatting is to make sure you know who you're talking too. Talking to strangers online can be very dangerous, in some cases leading to things like pedophilia etc.
Umgc had an improving university teaching conference from july 21-24, 1997. what city hosted it?
Answers
Answer:
Brazil, Rio De Janeiro hosted the event.
Assume count is a variable name, which of the following operations is atomic?
Select one:
A. count++
B. count--
C. both of the above
D. none of the above
Answers
The atomic operation among the given options is A. count++.
The operation "count++" is an atomic operation because it is a shorthand notation for incrementing the value of the variable "count" by 1. In programming, atomic operations are those that are executed as a single, indivisible unit. In this case, the increment operation (++) is typically implemented as an atomic operation, ensuring that it is performed in a thread-safe manner, even in concurrent or multi-threaded environments.
On the other hand, the operation "count--" (decrementing the value of "count" by 1) is not necessarily atomic. It can be subject to race conditions and potential inconsistencies when multiple threads are involved, as it requires reading the current value, decrementing it, and storing the new value back.
Know more about atomic operation here:
https://brainly.com/question/30881937
#SPJ11
which exploit disguises malware as a legitimate system process without the risk of crashing the process? the key to this exploit is creating a process in a suspended state. this is accomplished by loading the process into memory by suspending its main thread. the program will remain inert until an external program resumes the primary thread, causing the program to start running.
Answers
The exploit that disguises malware as a legitimate system process without the risk of crashing the process is called "process hollowing".
Process hollowing involves creating a new process in a suspended state, then replacing its code and data with that of the malicious program. This allows the malware to run under the guise of a legitimate process without triggering any alarms or causing any noticeable disruptions.
The technique is commonly used by hackers to bypass security measures and gain access to sensitive systems.
To know more about malware visit:
https://brainly.com/question/14276107
#SPJ11
the array index can be any positive integer less than or equal to the array size.a. true b. false
Answers
The statement "the array index can be any positive integer less than or equal to the array size" is false because the array index can be any non-negative integer (including zero) that is less than the array size.
Remember that array indices start at zero, so the valid range for an array index is from 0 to (array size - 1).
The array index is typically a zero-based integer, which means it starts from 0 and goes up to the array size minus one. Therefore, the valid array index ranges from 0 to array_size - 1.
For example, if you have an array with a size of 5, the valid indices would be 0, 1, 2, 3, and 4. Attempting to access an array element using an index outside this valid range may lead to unexpected behavior, such as accessing memory that is not part of the array or causing a runtime error.
It's important to adhere to the correct index range when working with arrays to ensure proper access and manipulation of elements within the array.
Learn more about array here: https://brainly.com/question/29989214
#SPJ11
what is computer graphics uses of computer graphics
Answers
Answer:
The technology that deals with the design and pictures on computer is called computer graphics.
It is displaying art and image data effectively and meaningfully to the consumer.
It is also used for processing image data received from the physical world, such as photo and video content.
1. Summarize the main idea of the article. 2. If you were given the option, which side of the argument would you support and WHY? (Give at least one fully supported reason that is mentioned in the article) (At least 3 sentences)
Story : Issue Overview: Should we have zoos? - Newsela Article
Answers
Answer:
have a nice day
Explanation:
im a beginner programmer. what languages should i learn and how do i get better
Answers
Answer: Python, Coding, JavaScript and there's more out there but it's been a while since I have taken Tech classes in a while!
Explanation: I recommend you use typing.com and code.org for coding! I don't know how else to answer this question but this was all I could say!
what would you calculate is the approximate minimum size of the partition structure needed for a debian system? assume memory size is 4 gb and that you will allocate twice the ram size for swap.
Answers
The minimum size required for the partition structure of a Debian system would be approximately 12 GB, consisting of 8 GB for the swap partition and 4 GB for the operating system.
The recommended size for the swap partition is usually twice the size of the RAM. In this case, since the RAM size is 4 GB, the swap partition size would be 8 GB. Additionally, you would need to allocate space for the operating system and other files, which typically require at least 4 GB. Therefore, the approximate minimum size of the partition structure would be 8 GB for the swap partition plus 4 GB for the operating system, totaling to approximately 12 GB.
You can learn more about Debian system at
https://brainly.com/question/31239178
#SPJ11
during a mail merge what item aer merged
Answers
Answer: The mail merge process involves taking information from one document, known as the data source.
Explanation:
log(10×
\(log(10x4 \sqrt{10)} \)
a technician wants to configure the computer to send an alert when the cpu usage is above 95% for an arbitrary length of time. which utility should be used?
Answers
To configure the computer to send an alert when CPU usage is above 95% for an arbitrary length of time, a monitoring and alerting utility is typically used. One commonly used utility for this purpose is a system monitoring tool or software.
There are several options available for system monitoring and alerting, such as:
1. Performance Monitor (perfmon): This utility is built into Windows operating systems and allows you to monitor various system performance counters, including CPU usage. You can set up alerts using Performance Monitor to trigger when the CPU usage exceeds a specified threshold. 2. Third-party monitoring tools: There are numerous third-party applications available that provide comprehensive system monitoring and alerting capabilities. Examples include Nagios, Zabbix, PRTG, and SolarWinds, among others. These tools often offer more advanced features and customization options for monitoring CPU usage and sending alerts
Learn more about system monitoring here:
https://brainly.com/question/30022843
#SPJ11
HELP ME PLZ IM AM STUCK ON THIS I NEED AWNSERS

Answers
Answer:
What are your cards?? I may be able to help you if you put your cards. :)
Explanation:
it's a memory stick for the computer . I use it to ?
Answers
Answer:
USB memory sticks, also called pen drives or flash drives, are becoming more and more popular for the temporary storage and transfer of large amounts of electronic data. They should not be used as main data storage or to make permanent backups.
Explanation:
Can someone please explain this??

Answers
Answer:
you've completed 9% and ur score for what you have completed is 66.66%
Explanation:
hope this helps
Assignment Directions:
Can you find programs on the Internet that are running on a cloud-computing platform? How can you tell? There is a difference between a program that runs in a script like the Java-based HTML editors or RadInks, an online SFTP program. These are not cloud-computing examples.
Research cloud-computing vendors and see what they are offering in terms of free trials. When you find two different examples, write a comparison. Ask yourself the following questions: What are the benefits of the cloud-based application? It what ways is it different from or the same as a program that runs locally? What is cumbersome or difficult about the program offered on the cloud platform, and how would the problem be alleviated by a program running on your local machine? Be specific. If you cannot tell the difference, ask yourself why.
You may create this report on PowerPoint or as a live website using your trial WordPress account. Include illustrations and video if possible. Make a compelling argument for your point of view.
Answers
There are several cloud-computing platforms that offer programs or applications as a service (PaaS) or infrastructure (IaaS).
Can you find programs on the Internet that are running on a cloud-computing platform?To identify if a program is running on a cloud platform, you can look for the terms "cloud-based" or "as a service" in the description or marketing materials of the program. Additionally, cloud-based programs usually offer access through a web browser or mobile app, and they are hosted on remote servers, allowing users to access and use them from anywhere with an internet connection.
Two examples of cloud-based programs are Mi,crosoft 365 and Go.ogle Workspace. Both of these platforms offer free trials and provide users with access to a suite of productivity tools such as word processing, spreadsheets, and email.
One benefit of cloud-based applications is that they are accessible from anywhere with an internet connection, allowing users to work remotely or collaborate with others easily. Additionally, cloud-based applications do not require users to install or maintain software on their local machines, reducing the need for hardware upgrades or software updates.
One drawback of cloud-based applications is that they rely on internet connectivity, and their performance can be affected by slow or unstable internet connections. Additionally, users may have concerns about the security and privacy of their data, as cloud-based applications store data on remote servers that may be vulnerable to cyber-attacks or data breaches.
In contrast, locally installed programs offer the advantage of faster performance and more control over data security and privacy. However, users are responsible for maintaining and updating the software, which can be time-consuming and require hardware upgrades.
Overall, the choice between a cloud-based or locally installed program depends on individual needs and preferences. Cloud-based programs offer greater flexibility and accessibility, while locally installed programs offer greater control and security.
Read more on cloud-computing here:https://brainly.com/question/19057393
#SPJ1
Periodic Table Question 2:
Please leave clear answer choices,
Best answer, desc, and reply will earn Brainliest.
Please don't report this, lots of my questions have been getting flagged, I'm not sure whether it's a bug or intentional but I'm not sure why any of my posts have been getting Vetoed. Rip my 10 points.

Answers
Answer:
D
Explanation:
It could be reported because it is a test. That's the only reason I can see.
The answer to this question is D -- it's conductivity can be changed. Anything with a semiconductor in it is normally made of Silicon (or Germanium). These elements have the virtue of being able to control the current going through them which is the same thing as saying that the conductivity can be changed.
Electronics has changed drastically since Bell labs developed them in the 1947, but the principle is the same.
For questions 1-3, consider the following code: x = int (input ("Enter a number: ")) if (x != 8): print ("A") if (x >= 10): print ("B") if (x < 10): print ("C") if (x % 2 == 1): print ("D") What is output if the user types in 13?
Answers
Answer:
ABD
Explanation:
13 not equal 8, greater than 10 and odd. Ifs will be executed step-by-step
Question 2
5 pts
(3.01 LC)
Which is an example of a built-in function in Python's library? (5 points)
O input()
O graphic
O output
O parameter
Answers
Everything, that has brackets after it - is a function, so the right answer is 1 - input(), and yes, it's a built-in function.
Answer:
Input() is your answer!
Explanation:
I got it right :)
NEED ANS ASAP THANK YOU

Answers
Answer:
1)text area
2) document view
4) title bar
6) window controls
8) command group
9) formatting toolbar
10) command tabs
11) zoom
12) scroll bars
13) toolbar
14)status bar
Consider the following code segment. Int count = 5; while (count < 100) { count = count * 2; } count = count 1; what will be the value of count as a result of executing the code segment?
Answers
Using the while loop, the value of count as a result of executing the following code segment is 161.
int count = 5;
while (count < 100)
{
count = count * 2; // count value will 10 20 40 80 160 then exit the while loop as count<100
}
count = count + 1; // here, 161 +1
When a condition is not satisfied, a "While" loop is used to repeat a certain piece of code an undetermined number of times. For instance, if we want to ask a user for a number between 1 and 10, but we don't know how often they might enter a greater number, until "while the value is not between 1 and 10."
While the program is running, the statements are continually executed using both the for loop and the while loop. For loops are used when the number of iterations is known, but while loops execute until the program's statement is proven incorrect. This is the main distinction between for loops and while loops.
To learn more about While loop click here:
brainly.com/question/29102592
#SPJ4
22. What does String [] args represent in the code below? (3pts) public class Demo { public static void main(String[] args) ( int a = Integer.parseInt(args[0]); int b= Integer.parseInt(args[1]); Syste
Answers
In the given code snippet, "String[] args" represents the command-line arguments passed to the Java program when it is executed. It is an array of strings that holds the values provided as arguments from the command line.
In Java, the "main" method serves as the entry point for the program execution. It accepts an array of strings as a parameter, conventionally named "args." The "args" parameter allows the program to receive inputs from the command line. Each element in the "args" array represents a separate argument provided when running the program.
In the code snippet, the values of "args[0]" and "args[1]" are parsed as integers using the "Integer.parseInt" method. These values can be accessed and used within the "main" method for further processing or calculations.
Learn more about command here
brainly.com/question/32329589
#SPJ11
the force of impact is
Answers
Answer:
the force of impact is the force generated when objects meet