do you use AI in answers
Answers
AI can be used to provide answers to various questions and tasks. AI refers to the ability of computer systems to perform tasks that would typically require human intelligence, such as perception, reasoning, and learning.
How can AI be used?AI can be used in various applications, such as natural language processing, image and speech recognition, and machine learning. For example, AI can be used in chatbots and virtual assistants to provide personalized responses to users' questions, and in recommendation systems to suggest products or content based on users' preferences.
In addition, AI can be used in industries such as healthcare, finance, and transportation to automate processes, improve efficiency, and make better decisions based on data analysis. AI can also be used in scientific research to analyze and interpret large datasets and to discover new insights.
Overall, AI has the potential to revolutionize many industries and improve our daily lives in various ways.
Learn more about AI on
https://brainly.com/question/20339012
#SPJ1
Related Questions
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
explain computer system architecture
Answers
Answer:
specification detailing how a set of software and hardware technology standards interact to form a computer system or platform.
Explanation:
Computer architecture is a specification detailing how a set of software and hardware technology standards interact to form a computer system or platform. In short, computer architecture refers to how a computer system is designed and what technologies it is compatible with.
of what is famous Ted Nelson?
Answers
Answer:
Nelson proposed a system where copying and linking any text excerpt, image or form was possible.
Explanation:
Ted Nelson is one of the theoretical pioneers of the world wide web who is best known for inventing the concept of hypertext and hypermedia in the 1960s. As one of the early theorists on how a networked world would work.
How I know:
I goggle it.
When Jenna borrows her dad's office chair, it's too big for her, so her feet dangle and don't reach the floor—which can cause what?
A: eye strain
B: carpal tunnel syndrome
C: a repetitive motion injury
D: slouching posture
Answers
Answer:
D
Explanation:
Answer:
B: carpal tunnel syndrome
Explanation:
YYou have to have your hand on the ddesk.
What is the importance of knowing the concept of programming?
Answers
Answer:
Computer programming is important today because so much of our world is automated. Humans need to be able to control the interaction between people and machines. Since computers and machines are able to do things so efficiently and accurately, we use computer programming to harness that computing power.
write a qbasic programme to find the volume of a box asking length,breadth, and height from user
Answers
Answer:
CLS
Input "length of box" ; L
Input "breadth of box" ; B
Input "height of box" ; H
LET Volume(V) = L*B*H
Print Volume
END
___________ is a global issue and there is a requirement to find out the interdependencies among the customers and suppliers.
Answers
Answer:
Supply chain disruption is a global issue and there is a requirement to find out the interdependencies among the customers and suppliers.
Explanation:
The context suggests we are discussing some type of challenge involving the relationships between customers, suppliers and a larger supply chain. A "global issue" involving "interdependencies among the customers and suppliers" points to potential supply chain disruption or issues in a supply network.
Since there is a "requirement to find out the interdependencies" between customers and suppliers, this suggests we need to identify and analyze how they are connected and dependent upon each other in order to resolve the broader "global issue." This information could then be used to make changes, build resilience or manage risks in the supply chain.
Hope this helps!
Answer:
Internet is global issues
what is volitile memory?
Answers
Answer:
do you mean volatile? Volatile memory is a type of storage whose contents are erased when the system's power is turned off or interrupted.
Explanation:
hope this helps have a good rest of your day :) ❤
example of graphics packages
Answers
Answer:
adobe photoshop, ms paint, corel draw..and more
what type of model does the Web use?
Answers
Answer:
Microsoft, Firefox, Google, and Office onenote webisite
Explanation:
cause they are a model
Your company has been assigned the 194.10.0.0/24 network for use at one of its sites. You need to calculate a subnet mask that will accommodate 60 hosts per subnet while maximizing the number of available subnets. What subnet mask will you use in CIDR notation?
Answers
To accommodate 60 hosts per subnet while maximizing the number of available subnets, we need to use a subnet mask that provides enough host bits and subnet bits.
How to calculateTo calculate the subnet mask, we determine the number of host bits required to accommodate 60 hosts: 2^6 = 64. Therefore, we need 6 host bits.
Subsequently, we determine the optimal quantity of subnet bits needed to increase the quantity of accessible subnets: the formula 2^n >= the amount of subnets is used. To account for multiple subnets, the value of n is set to 2, resulting in a total of 4 subnets.
Therefore, we need 2 subnet bits.
Combining the host bits (6) and subnet bits (2), we get a subnet mask of /28 in CIDR notation.
Read more about subnet mask here:
https://brainly.com/question/28390252
#SPJ1
what is MIS when it refers to the dat base
Answers
A management information system (MIS) is a computerized database of financial information organized and programmed in such a way that it produces regular reports on operations for every level of management in a company. It is usually also possible to obtain special reports from the system easily.
Answer: A management information system (MIS) is a computerized database of financial information organized and programmed in such a way that it produces regular reports on operations for every level of management in a company. It is usually also possible to obtain special reports from the system easily.
HOPE THIS HELPS
Servers can be designed to limit the number of open connections. For example, a server may wish to have only N socket connections at any point in time. As soon as N connections are made, the server will not accept another incoming connection until an existing connection is released. Please write pseudo-code to implement the synchronization using semaphore.
Answers
Answer:
The pseudocode is as follows:
open_server()
connections = N
while (connections>0 and connections <=N):
if(new_client == connected):
connections = connections - 1
for i in 1 to N - connections
if (client_i == done()):
releast_client(client_i)
connections = connections + 1
Explanation:
One of the functions of a semaphore is that, it is a positive variable whose value will never fall below 1. It is often shared among threads in order to keep a process running.
Having said that, what the above pseudocode does is that:
Once the server is opened, it initializes the number of connections to N.
When a new client, the semaphore decreases the number of connections is reduced by 1.
Similarly, when an already connected client is done, the client is released and the number of connections is increased by 1.
This operation is embedded in a while loop so that it can be repeatedly carried out.
Unemployment rate is a macroeconomic measure that describes:
O A. the percentage of people who are looking for a job but cannot find
one.
B. the value of the goods produced in a country divided by its
population.
c. the total value of goods and services a country produces in a year.
D. the increase in prices of consumer goods over a period of time.
Someone help me ASAP pleaseeee
Answers
Answer:
c
Explanation:
Three friends decide to rent an apartment and split the cost evenly. They each paid $640 towards the total move in cost of first and last month's rent and a security deposit. If rent is $650 per month, how much was the security deposit?
a.
$10
b.
$207
c.
$620
d.
$1,270
Please select the best answer from the choices provided
Answers
Answer:
c. $620
Explanation:
To find the cost of the security deposit, we need to subtract the amount paid towards the first and last month's rent from the total move-in cost.
Each friend paid $640 towards the total move-in cost, which includes the first and last month's rent and the security deposit. Since they split the cost evenly, the total move-in cost is 3 times $640, which is $1920.
The monthly rent is $650 per month, so the first and last month's rent combined is 2 times $650, which is $1300.
To find the security deposit, we subtract the first and last month's rent from the total move-in cost:
Security deposit = Total move-in cost - First and last month's rent
Security deposit = $1920 - $1300
Security deposit = $620
Therefore, the security deposit was $620.
Option c. $620 is the correct answer.
Help me with this somebodyy

Answers
Answer:
1. His mother
2. He took the goose over first and came back. Then he took the fox across and brought the goose back. Next he took the corn over. He came back alone and took the goose.
3. advice
1. His mother
2. He took the goose over first and came back. Then he took the fox across and brought the goose back. Next he took the corn over. He came back alone and took the goose.
3. advice
What is stream?Stream is the heavy flow of water of a river or channel that can be passed by boat.
1. The doctor was not the boy's father, then doctor will be his mother.
2. All will safely get through the stream when the goose over first and came back. Then he took the fox across and brought the goose back. Next he took the corn over. He came back alone and took the goose.
3. Advice is such a thing that everybody asks for but never takes it.
Learn more about stream.
https://brainly.com/question/27291754
#SPJ1
Which directory contains the initrd file? in suse linux
Answers
The directory that contains the initrd file is known as /boot directory,
What is a directory?This refers to the file system of cataloging structure which contains references to other computer files and as well the other directories.
On most computers, these directories are known as folders, drawers or analogous to the traditional office filing cabinet.
However, on the typical computer, the directory that contains the initrd file is known as /boot directory,
Read more about directory
brainly.com/question/27962427
#SPJ1
Document templates are available online.
True
False
Answers
Answer:
true
Explanation:
anything is avalible onlkne
Which feature of a website takes you to a different part of the website or a totally different website when you click on it? A. graphics B. formal text C. hyperlink D. animation
Answers
Answer: C
Explanation:
Answer:
hyperlink
Explanation:
The feature of a website that takes you to a different part of the website or a totally different website when you click on it is called a hyperlink. Hyperlinks are typically underlined and appear in a different color than the surrounding text. They can be used to navigate between pages on the same website or to link to external websites.
I've got the answer, I just need someone to explain it, please!
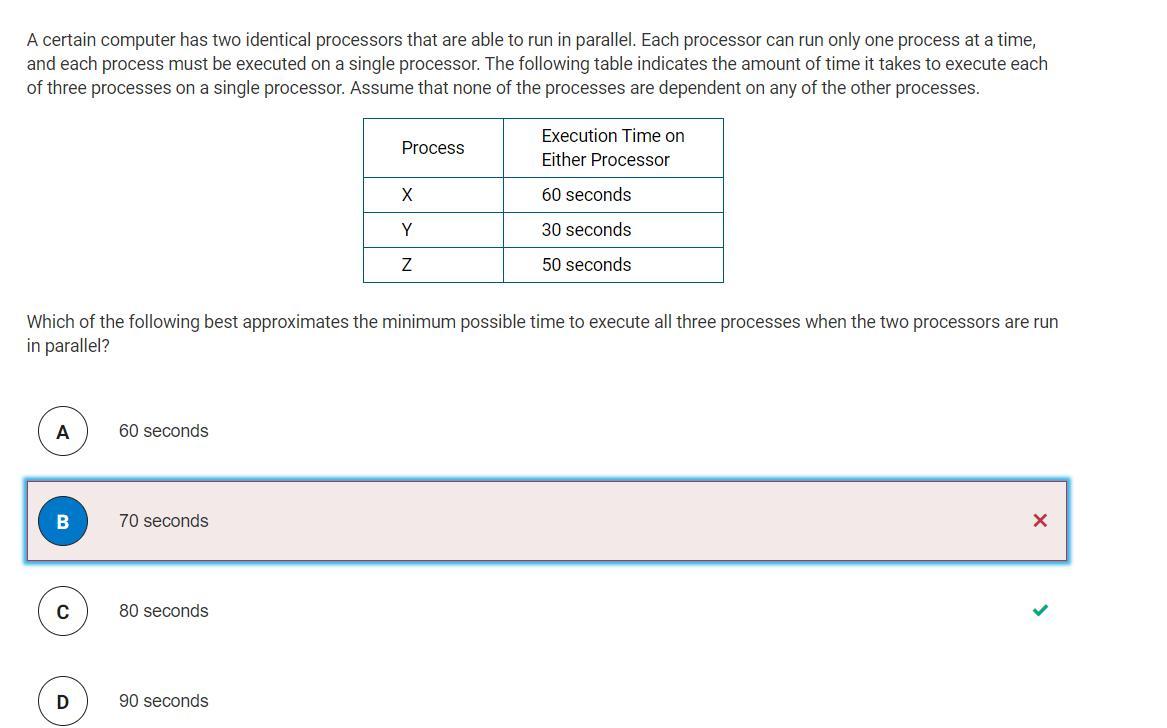
Answers
answered
How would you measure user satisfaction with a registration program at a college or university? What are the important features that would make students and faculty satisfied with the system?
Answers
Answer:
You could think about this in several ways with several approaches.
- Survey
- User testing in groups
- On the actual registration program, 3 questions pop up
With general open ended questions and by talking to users
Explanation:
- Demographics
- Ask them what they like about the registration program
- What they use the registration for
- What they would do to improve it
Let T be the statement: The sum of any two rational numbers is rational. Then T is true, but the following "proof is incorrect. Find the mistake. "Proof by contradiction: Suppose not. That is, suppose that the sum of any two rational numbers is not rational. This means that no matter what two rational numbers are chosen their sum is not rational. Now both 1 and 3 are 1/1 and 3 3/1, and so both are ratios of integers with rational because 1 a nonzero denominator. Hence, by a supposition, the sum of 1 and 3, which is 4, is not rational. But 4 is rational because 4 4/1 , which is a ratio of integers with a nonzero denominator. Hence 4 is both rational and not rational, which is a contradiction. This contradiction shows that the supposition is false and hence statement T is true.
Answers
Answer:
the mistake is in the first statement.
Explanation:
Now lets us put the statement into consideration:
"The sum of any two rational numbers is irrational"
The negation is: " there exists a pair of rational numbers whose sum is irrational". (Existence of at least one of such a pair).
The negation is not "the sum of any two rational numbers is irrational"
Therefore the mistake is in the first statement and it is due to incorrect negation of the proof.
Integers limeWeight1, limeWeight2, and numKids are read from input. Declare a floating-point variable avgWeight. Compute the average weight of limes each kid receives using floating-point division and assign the result to avgWeight.
Ex: If the input is 300 270 10, then the output is:
57.00
how do I code this in c++?
Answers
Answer:
Explanation:
Here's the C++ code to solve the problem:
#include <iostream>
using namespace std;
int main() {
int limeWeight1, limeWeight2, numKids;
float avgWeight;
cin >> limeWeight1 >> limeWeight2 >> numKids;
avgWeight = (float)(limeWeight1 + limeWeight2) / numKids;
cout.precision(2); // Set precision to 2 decimal places
cout << fixed << avgWeight << endl; // Output average weight with 2 decimal places
return 0;
}
In this program, we first declare three integer variables limeWeight1, limeWeight2, and numKids to hold the input values. We also declare a floating-point variable avgWeight to hold the computed average weight.
We then read in the input values using cin. Next, we compute the average weight by adding limeWeight1 and limeWeight2 and dividing the sum by numKids. Note that we cast the sum to float before dividing to ensure that we get a floating-point result.
Finally, we use cout to output the avgWeight variable with 2 decimal places. We use the precision() and fixed functions to achieve this.
The student can code the calculation of the average weight of limes that each kid receives in C++ by declaring integer and double variables, getting input for these variables, and then using floating-point division to compute the average. The result is then assigned to the double variable which is displayed with a precision of two decimal places.
Explanation:To calculate the average weight of limes each kid receives in C++, declare three integers: limeWeight1, limeWeight2, and numKids. Receive these values from input. Then declare a floating-point variable avgWeight. Use floating-point division (/) to compute the average weight as the sum of limeWeight1 and limeWeight2 divided by the number of kids (numKids). Assign this result to your floating-point variable (avgWeight). Below is an illustrative example:
#include
cin >> limeWeight1 >> limeWeight2 >> numKids;
}
Learn more about C++ Programming here:
https://brainly.com/question/33453996
#SPJ2
1. Design a DC power supply for the Fan which have a rating of 12V/1A
Answers
To design a DC power supply for a fan with a rating of 12V/1A, you would need to follow these steps:
1. Determine the power requirements: The fan has a rating of 12V/1A, which means it requires a voltage of 12V and a current of 1A to operate.
2. Choose a transformer: Start by selecting a transformer that can provide the desired output voltage of 12V. Look for a transformer with a suitable secondary voltage rating of 12V.
3. Select a rectifier: To convert the AC voltage from the transformer to DC voltage, you need a rectifier. A commonly used rectifier is a bridge rectifier, which converts AC to pulsating DC.
4. Add a smoothing capacitor: Connect a smoothing capacitor across the output of the rectifier to reduce the ripple voltage and obtain a more stable DC output.
5. Regulate the voltage: If necessary, add a voltage regulator to ensure a constant output voltage of 12V. A popular choice is a linear voltage regulator such as the LM7812, which regulates the voltage to a fixed 12V.
6. Include current limiting: To prevent excessive current draw and protect the fan, you can add a current-limiting circuit using a resistor or a current-limiting IC.
7. Assemble the circuit: Connect the transformer, rectifier, smoothing capacitor, voltage regulator, and current-limiting circuitry according to the chosen design.
8. Test and troubleshoot: Once the circuit is assembled, test it with appropriate load conditions to ensure it provides a stable 12V output at 1A. Troubleshoot any issues that may arise during testing.
Note: It is essential to consider safety precautions when designing and building a power supply. Ensure proper insulation, grounding, and protection against short circuits or overloads.
For more such answers on design
https://brainly.com/question/29989001
#SPJ8
give the synyax and example of any three mathematical functions in spreadsheet
Answers
Answer:
The answer to this question is given below in the explanation section
Explanation:
There are different mathematical functions that can be used in the spreadsheet for performing some required calculations on data such as taking the average of numbers, adding numbers, multiplying the numbers.
But most commonly used three mathematical functions in the spreadsheet is given below:
1. AVERAGE(): The average function is used to find the average of a given number of cells.
Syntax of Average() function: average(number1, number2,.....).
2. SUM(): The sum function is used to add all the values within a range of cells.
Syntax: of sum() function: sum(cell address1: cell address2)
3.COUNT(): Count () function is used to count the number of data.
Syntax of Count() function: count(cell address1: cell address2)
compare and contrast the various write strategy used in cache technologies
Answers
Answer:
The abiotic factors are non-living factors in an ecosystem that affect the organisms and their lifestyle. In this case, low temperature and low humidity lead to the conditions that are unfavorable for birds. So, the birds must adapt to these factors by hiding the food in the caches.
Explanation:
Which of the statements is correct about Smart Guides and Rulers?
Answers
Answer:
Hey! here's ur answer
Explanation:
Specify these angles in the Smart Guides preferences. When you move an object or artboard, use the Smart Guides to align the selected object or artboard to other objects or artboards. The alignment is based on the geometry of objects and artboards. Guides appear as the object approaches the edge or center point of other objects.
-Uh, hope this helps!
A number is a palindrome if its reversal is the same as itself. Write a program ReverseNumber.java to do the following:
1. Define a method call reverse, which takes a 4-digit integer and returns an integer in reverse. For example, reverse(1234) should return 4321. (Hint: use / and % operator to separate the digits, not String functions)
2. In the main, take user input of a series of numbers, call reverse method each time and then determine if the number is a palindrome number, for example, 1221 is a palindrome number, but 1234 is not.
3. Enhance reverse method to work with any number, not just 4-digit number.
Answers
The reverse method takes an integer as input and reverses it by extracting the last digit using the modulus operator % and adding it to the reversed number after multiplying it by 10.
The Programimport java.util.Scanner;
public class ReverseNumber {
public static int reverse(int number) {
int reversedNumber = 0;
while (number != 0) {
int digit = number % 10;
reversedNumber = reversedNumber * 10 + digit;
number /= 10;
}
return reversedNumber;
}
public static boolean isPalindrome(int number) {
return number == reverse(number);
}
public static void main(String[] args) {
Scanner scanner = new Scanner(System.in);
System.out.print("Enter a number: ");
int number = scanner.nextInt();
if (isPalindrome(number)) {
System.out.println(number + " is a palindrome number.");
} else {
System.out.println(number + " is not a palindrome number.");
}
}
}
Read more about Java program here:
https://brainly.com/question/26789430
#SPJ1
Which of the following is the general term used to describe software code that isdesigned to cause damage to a computer system?
A) Virus
B) Malware
C) Adware
D) Madware
Answers
Answer:
B. Malware
Explanation:
Malware is the general term used to describe software code that is designed to cause damage to a computer system
Malware also known as malicious software. It is a single term which refers to virus, trojans, adware spy ware, rogue, scare ware, worm etc.
They are intentionally designed to cause damage to a computer system.
Question 10 (5 points)
Which of the following represents the PC speed rating of a DDR4-1600 SDRAM
DIMM?
OPC4-12800
OPC4-6400
PC4-200
PC-200
Answers
Answer:
The PC speed rating of a DDR4-1600 SDRAM DIMM is PC4-12800.
Explanation: