Design a program that asks the User to enter a series of 5 numbers. The program should store the numbers in a list then display the following data: 1. The lowest number in the list 2. The highest number in the list 3. The total of the numbers in the list 4. The average of the numbers in the list
Answers
Answer:
The program in Python is as follows:
numbers = []
total = 0
for i in range(5):
num = float(input(": "))
numbers.append(num)
total+=num
print("Lowest: ",min(numbers))
print("Highest: ",max(numbers))
print("Total: ",total)
print("Average: ",total/5)
Explanation:
The program uses list to answer the question
This initializes an empty list
numbers = []
This initializes total to 0
total = 0
The following loop is repeated 5 times
for i in range(5):
This gets each input
num = float(input(": "))
This appends each input to the list
numbers.append(num)
This adds up each input
total+=num
This prints the lowest using min() function
print("Lowest: ",min(numbers))
This prints the highest using max() function
print("Highest: ",max(numbers))
This prints the total
print("Total: ",total)
This calculates and prints the average
print("Average: ",total/5)
Related Questions
Dani wants to create a web page to document her travel adventures. Which coding language should she use?
a
HTML
b
Java
c
Python
d
Text
Answers
Different network scenarios require the use of different tools. The tools you may consider should EXCLUDE:_________
Answers
Complete Question:
Different network scenarios require the use of different tools. The tools you may consider should EXCLUDE:
a. Port scanner
b. Banner grabbing tools
c. Vulnerability scanner
d. Honeypots
e. Protocol analyzer
f. Viruses
g. Honeynets
Answer:
f. Viruses
Explanation:
Different network scenarios require the use of different tools. The tools you may consider should include:
a. Port scanner: this is a program used by network administrators to scan various application, transport, internet and network ports which may be exploited by hackers or attackers when found vulnerable.
b. Banner grabbing tools: it is used to gather informations of a computer residing on a network and various services running on its open ports using telnet, zmap, netcat and nmap.
c. Vulnerability scanner: used for the detection of vulnerabilities in a network or systems.
d. Honeypots: it is used to detect and redirect or prevent any unauthorized use of information of a network by mimicking the potential target systems.
e. Protocol analyzer: it is used to analyze traffic and packet captures in a network. Software programs such as wireshark, tshark can be used for protocol analysis.
f. Honeynets: is a combination of one or more honeypots used for attracting and trapping potential attackers.
However, a virus is a malicious program that can replicate and cause severe damage to a computer system.
Draw raw a program Flowchart that will be use to solve the value ofx im a quadratic equation +(x) = ax²tbxtc.
Answers
A program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
Sure! Here's a basic flowchart to solve the value of x in a quadratic equation:
```Start
|
v
Input values of a, b, and c
|
v
Calculate discriminant (D) = b² - 4ac
|
v
If D < 0, No real solutions
|
v
If D = 0, x = -b / (2a)
|
v
If D > 0,
|
v
Calculate x1 = (-b + √D) / (2a)
|
v
Calculate x2 = (-b - √D) / (2a)
|
v
Output x1 and x2 as solutions
|
v
Stop
```In this flowchart, the program starts by taking input values of the coefficients a, b, and c. Then, it calculates the discriminant (D) using the formula D = b² - 4ac.
Next, it checks the value of the discriminant:
- If D is less than 0, it means there are no real solutions to the quadratic equation.
- If D is equal to 0, it means there is a single real solution, which can be calculated using the formula x = -b / (2a).
- If D is greater than 0, it means there are two distinct real solutions. The program calculates both solutions using the quadratic formula: x1 = (-b + √D) / (2a) and x2 = (-b - √D) / (2a).
Finally, the program outputs the solutions x1 and x2 as the result.
For more such questions on Flowchart,click on
https://brainly.com/question/6532130
#SPJ8
The Probable question may be:
Draw a program Flowchart that will be use to solve the value of x in a quadratic equation f(x) = ax²+bx+c.
Imagine that you want to build a radio telescope and an optical telescope and that you want them to both have the same angular resolution, assume that both telescopes can reach the diffraction limit. Which telescope will have to have a larger diameter? Explain your reasoning.
Answers
Answer:
The radio telescope will have to have a larger diameter than the optical telescope in order to achieve the same angular resolution. This is because radio waves have a longer wavelength than optical waves, and the angular resolution of a telescope is inversely proportional to the wavelength of the radiation it is observing. Since the radio waves have a longer wavelength, the telescope observing them will need a larger diameter in order to achieve the same level of resolution as a telescope observing optical waves. Additionally, the diffraction limit for radio telescopes is greater than for optical telescopes, so the radio telescope will need to be larger to reach the diffraction limit.
Which two peripherals are not required to browse the internet?
O A. CPU
B. Monitor
O C. Headphones
D. DVD drive
Answers
Answer:
DVD Drive, Headphones
Explanation:
You need a CPU for sure, it is the main component known as the Central Processing Unit, and it provides instructios for the computer. A monitor is needed to visually see the internet, without a monitor, you would just be looking at your PC.
Headphones are not necessary because they are for personal audio, and most of the time, the internet is not audio.
A DVD drive is used to play DVD disks, which contains videos, movies, games, etc. The internet is not on a DVD.]
-Chetan K
Complete the method, isPerfectSquare(). The method takes in a positive integer, n. It returns a boolean that is true if n is a perfect square, false otherwise. A perfect square is an integer whose square root is also an integer. You may assume that n is a positive integer.
Hint: find the square root of n, cast it to an int value, then square it and compare this square to n.
Starter code:-
public class Square {
public static boolean isPerfectSquare(int n) {
//TODO: complete this method
}
}
Answers
Answer:
public class Square { public static boolean isPerfectSquare(int n){ int sqrt_n = (int) Math.sqrt(n); if(sqrt_n * sqrt_n == n ){ return true; }else{ return false; } } }Explanation:
Firstly, use sqrt method from Math package to calculate the square root of input n (Line 3). Cast the result to integer and assign it to sqrt_n variable.
Next, square the sqrt_n and check if it is equal to input n (Line 4). If so, return true, if not, return false (Line 4-8).
UNIT 1 ACTIVITY 1
How Many Sevens?
Required Materials
OnlineGDB (login required)
Word processing software
You’ve learned about lists and defining your own functions. Now, you will put those skills together by writing a program that will print how many times the number 7 appears in a list.
Step 1: Practice
But before we do that, let’s visualize a bit of code to be sure you understand how it works. We are going to run the code in a visualizer. A visualizer shows you not just the output of the code but also what is happening step by step.
Go to Python Tutor Visualizer.
Then, type in this code:
my_list = [1, 2, 3, 4, 5]
for x in range(len(my_list)):
print(my_list[x])
Now, click on the Visualize Execution button. You will see a screen that has your code on the left and a blank area on the right.
Press the Next > button to begin stepping through the program. On the right, you will see a visual representation of the fact that the code has created a list; you will also see the items in the list as well as their index numbers.
Press the Next > button until you have finished the program. Did you notice how the red and green arrows showed you which lines of the program had just executed and which ones were about to execute during each step of the way through the program?
Now, let’s review the program itself. The first line of this code creates a list called my_list . Then, the second line is the command to iterate over the list using a variable that we call x . We did this iteration by making the range equal to the length of the list. For each iteration, it printed the item from the list that had the same index as the iterating variable. Now, you should be comfortable with iterating over a list and accessing each item in the list as you iterate over the list by using the incrementing variable as the index number.
Step 2: Program
Now, we’re ready to program! Leave the visualizer and go to OnlineGDB to write your program. Here is the pseudocode for your program:
Define a function called “seven_checker” that will do the following things:
Iterate over a list.
Check to see whether the number 7 is in the list.
Print how many times the number 7 appears in the list.
Create a list with 10 numbers in it. Then call the function and pass your list to the function as a parameter.
When you have tested your program, click the save button. Then click Share and copy the program link. Paste the link in a word processing document and submit using this unit’s dropbox. If your program does not work properly, also include a paragraph explaining what you did to troubleshoot it.
Answers
Answer:
Step 1:
def seven_checker(my_list):
count = 0
for num in my_list:
if num == 7:
count += 1
print("The number 7 appears in the list " + str(count) + " times.")
my_list = [1, 2, 3, 4, 7, 5, 7, 8, 9, 7]
seven_checker(my_list)
Step 2:
In this program, I first defined a function called "seven_checker" which takes a parameter "my_list" which is the list that we want to check for the number of times the number 7 appears in it.
In the function, I initialized a variable "count" to 0, which will keep track of the number of times 7 appears in the list.
Then, I used a for loop to iterate over the list, and for each number in the list, I checked if it is equal to 7. If it is, I incremented the count variable by 1.
Finally, I printed out the number of times 7 appears in the list using the count variable.
I then created a list with 10 numbers and called the function, passing the list as a parameter to it.
I tested the program and it gave the correct output, "The number 7 appears in the list 3 times."
I did not face any issues while writing the program and it worked as expected.
I understand that you want to create a Python program that counts the number of times the number 7 appears in a given list. Below is a Python code to achieve this
def seven_checker(input_list):
count = 0
for num in input_list:
if num == 7:
count += 1
return count
# Example list with 10 numbers
my_list = [3, 7, 2, 8, 7, 4, 7, 9, 1, 7]
# Call the function with the example list and print the result
result = seven_checker(my_list)
print("The number of sevens in the list is:", result)
How will the above program work?You can run this code in your Python environment or OnlineGDB to see how it works. It defines a function seven_checker that takes a list as input, iterates over the elements in the list, and counts how many times the number 7 appears.
The example list my_list contains 10 numbers, and we call the function with this list to get the count of sevens in it. The result will be printed as the output.
Learn more about Phyton at:
https://brainly.com/question/26497128
#SPJ2
Who is responsible for having Account/Relationship level Business Continuity Plan (BCP) in place?
Answers
The responsibility for having an Account/Relationship level Business Continuity Plan (BCP) in place usually lies with the company or organization providing the service or product. This is because they are responsible for ensuring the continuity of their operations and minimizing the impact of disruptions on their customers. However, it is also important for customers to have their own BCPs in place to ensure their own business continuity in case of a disruption. Ultimately, it is a shared responsibility between the service provider and the customer to have robust BCPs in place.
In a business or organizational context, the responsibility for having an Account/Relationship level Business Continuity Plan (BCP) in place typically falls on the account manager or relationship manager.
What is the BusinessAccount/relationship level BCP is a plan made specifically for a client or customer account or relationship to deal with their special needs and risks.
These plans are really important for businesses that have important clients or relationships to make sure that they can keep providing necessary services or products even if something unexpected happens like a natural disaster, cyberattack, or emergency.
Read more about Business here:
https://brainly.com/question/18307610
#SPJ2
"The constructor signature is defined as the constructor __________ followed by the __________. (3 points)
1) name, parameter list
2) name, return type
3) definition, body
4) definition, parameter list
5) header, body"
Answers
"The constructor signature is defined as the constructor name followed by the parameter list. (Option A)
What is a constructor?A constructor is a specific sort of subroutine that is invoked to build an object in class-based, object-oriented programming. It is responsible for preparing the new object for usage by receiving parameters that the constructor uses to set needed member variables.
A constructor is a particular function in Java that is used to initialize objects. When a class object is formed, the constructor is invoked.
It is called a constructor because it builds the values when an object is created. A constructor does not have to be written for a class. It's because the java compiler generates a default constructor if your class lacks one.
Learn more about Constructor:
https://brainly.com/question/17347341
#SPJ1
Which property of a DBMS lets you change the database structure without requiring you to change the programs that access the database
Answers
Answer:
"Integrity constraints " is the correct answer.
Explanation:
A successful DBMS offers integrity constraints, which have been an option that allows you to modify the database layout without modifying the applications accessing the repository.A principle or requirement which the data in something like a database should therefore obey.So that the above is the correct choice.
Can someone help me answer this someone please.

Answers
Answer:
2. The tower that is balencing on a giant hand and the humans that is standing on the giant hand.
3. The artist show proportion by the relationship of the picture that create harmony in the picture and the meaning of this picture is friendly and it shows proportionate size, color and shape it works together to make the picture bounce.
4. Maybe the artist could make the background more bouncy and clear and could use a little bit more details.
3
Drag each label to the correct location on the image.
An organization has decided to initiate a business project. The project management team needs to prepare the project proposal and business
justification documents. Help the management team match the purpose and content of the documents.
contains high-level details
of the proposed project
contains a preliminary timeline
of the project
helps to determine the project type,
scope, time, cost, and classification
helps to determine whether the
project needs meets business
needs
contains cost estimates,
project requirements, and risks
helps to determine the stakeholders
relevant to the project
Project proposal
Business justification
Answers
Here's the correct match for the purpose and content of the documents:
The Correct Matching of the documentsProject proposal: contains high-level details of the proposed project, contains a preliminary timeline of the project, helps to determine the project type, scope, time, cost, and classification, helps to determine the stakeholders relevant to the project.
Business justification: helps to determine whether the project needs meet business needs, contains cost estimates, project requirements, and risks.
Please note that the purpose and content of these documents may vary depending on the organization and specific project. However, this is a general guideline for matching the labels to the documents.
Read more about Project proposal here:
https://brainly.com/question/29307495
#SPJ1
1) What is the first compartment of the 3 Sink Setup filled with?
O Multi-purpose detergent solution and water at least 110°F/37°C
O Baking soda solution and water at least 110°F/37°C
Isopropyl alcohol solution and water at least 110°F/37°C
Sanitizer solution and water at least 110°F/37°
Answers
The first compartment of the 3 Sink Setup is typically filled with option D: a Sanitizer solution and water at least 110°F/37°
What is the first compartment of the 3 Sink Setup filled with?The first part of the 3 Sink Setup is for cleaning and getting rid of germs. People often call it the spot where you sanitize things. In this compartment, we mix a special cleaning liquid with water to make a sanitizer solution. We suggest keeping the water in this area at least as warm as 110°F/37°C.
Sanitizer is used to get rid of germs on things like dishes and kitchen surfaces. It stops germs from spreading and makes sure food is safe.
Learn more about Sanitizer solution from
https://brainly.com/question/29551400
#SPJ1
China is selling school supplies in the United States for very low prices, even lower than the
preventing prices in China, and thus making it extremely difficult for American manufacturers to
compete. This is referred to as
Answers
Answer:
dumping.
Explanation:
dumping. China is selling school supplies in the United States for very low prices, even lower than the prevailing prices in China, and thus making it extremely difficult for American manufacturers to compete. This is referred to as DUMPING.
program a macro on excel with the values: c=0 is equivalent to A=0 but if b is different from C , A takes these values
Answers
The followng program is capable or configuring a macro in excel
Sub MacroExample()
Dim A As Integer
Dim B As Integer
Dim C As Integer
' Set initial values
C = 0
A = 0
' Check if B is different from C
If B <> C Then
' Assign values to A
A = B
End If
' Display the values of A and C in the immediate window
Debug.Print "A = " & A
Debug.Print "C = " & C
End Sub
How does this work ?In this macro, we declare three integer variables: A, B, and C. We set the initial value of C to 0 and A to 0.Then, we check if B is different from C using the <> operator.
If B is indeed different from C, we assign the value of B to A. Finally, the values of A and C are displayed in the immediate window using the Debug.Print statements.
Learn more about Excel:
https://brainly.com/question/24749457
#SPJ1
actions taken by a computer when a module is called such as allocating memory for the local variables and the parameters is called group of answer choices overhead
Answers
Actions taken by a computer when a module is called such as allocating memory for the local variables and the parameters is called overhead.
What is allocating memory?Computer programs and services can be given access to physical or virtual memory space through a process called memory allocation. Memory allocation is the process of allocating a full or partial chunk of computer memory for the use of applications and processes. Memory allocation is accomplished using a procedure called memory management.
Although it is primarily a hardware operation, memory management is controlled by the operating system and software programs. Physical and virtual memory management processes for allocating memory are quite similar.
Depending on their needs, programs and services are given a specific amount of memory when they are executed. The memory is released and given to another program or combined with the main memory once the program has completed its task or is idle.
Learn more about Memory allocation
https://brainly.com/question/29833602
#SPJ4
Do you think that dealing with big data demands high ethical regulations, accountability, and responsibility of the person as well as the company? Why?
Answers
Answer:
i is struggling
Explanation:
In the flag, the RGB values next to each band indicate the band's colour.
RGB: 11111101 10111001 00010011
RlGB: 00000000 01101010 01000100
RGB: 11000001 00100111 00101101
First, convert the binary values to decimal. Then, to find out what colours these values correspond to, use the Colour names' handout (ncce.io/rep2-2-hw) or look up the RGB values online. Which European country does this flag belong to?
Answers
Answer:
To convert the binary values to decimal, you can use the following steps:
Start with the rightmost digit and assign it the value of 0.
For each subsequent digit moving from right to left, double the value of the previous digit and add the current digit.
For example, to convert the first binary value, 11111101, to decimal:
10 + 02 + 04 + 08 + 016 + 132 + 164 + 1128 = 253
So the first binary value, 11111101, corresponds to the decimal value 253.
Using this method, you can convert the other binary values to decimal as well. To find out what colours these values correspond to, you can use the Colour names' handout or look up the RGB values online.
To determine which European country this flag belongs to, you can try looking up the colours and seeing if they match any known flags. Alternatively, you could try searching for flags of European countries and see if any of them match the colours you have identified.
How could you use a spreadsheet you didn't like to simplify access also the problem
Answers
Explanation:
......
Which data storage or software tool is used to unify vast amounts of raw data of all types from across an organization
Answers
A data lake is a type of repository that stores large sets of raw data of all types from across an organization.
What is a data lake?A data lake is a central location in which to store all data, regardless of its source or format, for an organization at any scale.
Characteristics of a data lakeIt is low cost, easily scalable, and are often used with applied machine learning analytics.It allows to import any type of data from multiple sources in its native format, this allows organizations to scale in the size of the data as needed.Therefore, we can conclude data lakes are a vital component in data management as it stores all data across an organization.
Learn more about data lakes here: https://brainly.com/question/23182700
The following statements describe the use of graphics in presentations. Responses Graphics should be large enough to be seen by the audience. Graphics should be large enough to be seen by the audience. Graphics should be used on every slide. Graphics should be used on every slide. Graphics should be used when they are relevant to the content. Graphics should be used when they are relevant to the content. Lots of graphics will make a boring presentation interesting. Lots of graphics will make a boring presentation interesting.
Answers
Answer: No!
Explanation:
No, lots of graphics will not necessarily make a boring presentation interesting. The use of graphics should depend on the content of the presentation and the purpose of the presentation. If the graphics are used for the purpose of illustrating a point or helping the audience to understand the content better, then they can be helpful. However, too many graphics can be distracting and take away from the main message. Therefore, it is important to use graphics judiciously and only when they are relevant to the content.
some context free languages are undecidable
Answers
assume all integers are in hexadecimal and two's complement notation. remember to indicate overflow if necessary.(2AF6)+(7017)=?16 16
Answers
The sum of the two hexadecimal numbers (2AF6)16 and (7017)16 is (9B0D)16.
1. Convert the hexadecimal numbers to binary:
(2AF6)16 = (0010 1010 1111 0110)2
(7017)16 = (0111 0000 0001 0111)2
2. Add the two binary numbers:
0010 1010 1111 0110
+ 0111 0000 0001 0111
= 1001 1011 0000 1101
3. Convert the binary sum back to hexadecimal:
(1001 1011 0000 1101)2 = (9B0D)16
4. Check for overflow:
Since the sum is a valid 16-bit number, there is no overflow.
Therefore, the sum of the two hexadecimal numbers (2AF6)16 and (7017)16 is (9B0D)16.
Learn more about hexadecimal numbers
https://brainly.com/question/11293449
#SPJ11

Please help me!! It's due today!
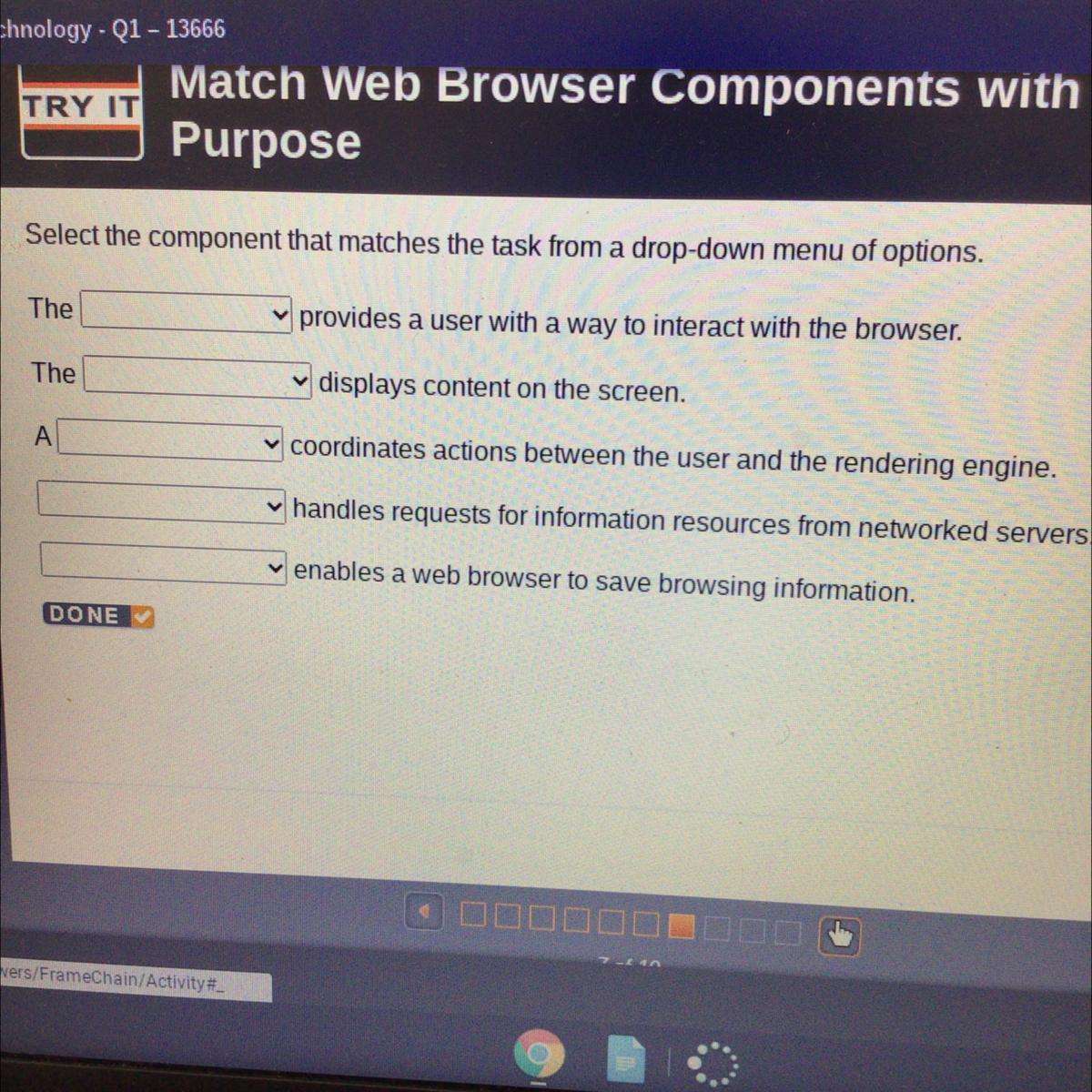
Answers
Answer: whats the options?
Explanation:
Give an example of a class and an example of an object. Describe what a class is, what an object is, and how they are related. Use your examples to illustrate the descriptions.
Answers
Answer:
Science. Science is where you learn about the worlds enviroment.
Book. A Book is a object that has words in it that you can read. It has sometimes thick pages or thin pages.
Write a program that calculates and displays a person’s body mass index (BMI). The BMI is often used to determine whether a person with a sedentary lifestyle is overweight or underweight for his or her height. A person’s BMI is calculated with the following formula:
BMI = weight x 703 / height2
where weight is measured in pounds and heightis measured in inches. The program should ask the user to enterhis/her weight and height. The program should display a message indicating whether the person has optimal weight, is underweight, or is overweight. A sedentary person’s weight is considered optimal if his or her BMI is between18.5 and 25. If the BMI is less than 18.5, the person is considered underweight. If the BMI valueis greater than 25, the person is considered overweight
Answers
Answer:
This program is written using C++
Comments are used to explain difficult lines
Program starts here
#include<iostream>
using namespace std;
int main()
{
//Declare variables
float BMI, Height,Weight;
// Prompt user for inputs
cout<<"Ener Height (in inches): ";
cin>>Height;
cout<<"Enter Weight (in pounds): ";
cin>>Weight;
//Calculate BMI
BMI = (Weight * 703)/(Height * Height);
cout<<"Your Body Mass Index (BMI) is "<<BMI<<endl;
//Test and print whether user is underweight, overweight or optimal
if(BMI>=18.5&&BMI<=25)
{
cout<<"You have an optimal weight";
}
else if(BMI<18.5)
{
cout<<"You are underweight";
}
else if(BMI>25)
{
cout<<"You are overweight";
}
return 0;
}
See attachment for .cpp source file
Different types of users in a managed network, what they do, their classification based on tasks
Answers
In a managed network,, skilled can be miscellaneous types of consumers accompanying various roles and blames.
What is the network?Administrators are being the reason for directing and upholding the network infrastructure. Their tasks involve network arrangement, freedom management, consumer approach control, listening network performance, and mechanically alter issues.
Administrators have high-ranking approach and control over the network. Network Engineers: Network engineers devote effort to something designing, achieving, and claiming the network foundation.
Learn more about network from
https://brainly.com/question/1326000
#SPJ1
Follow the instructions for starting C++ and viewing the Introductory21.cpp file, which is contained in either the Cpp8\Chap11\Introductory21 Project folder or the Cpp8\Chap11 folder. (Depending on your C++ development tool, you may need to open the project/solution file first.) The program should calculate the average stock price stored in the prices array. It then should display the average price on the screen. Complete the program using the for statement. Save and then run the program.
Answers
Explanation:
I would use a for loop cycling through the array and adding the arrays values into a variable, then keep track of how many items in the array you have. Finally divide the total by the amount of stock prices and output it.
C++ code
Your task is to write a program that parses the log of visits to a website to extract some information about the visitors. Your program should read from a file called WebLog.txt which will consist of an unknown number of lines. Each line consists of the following pieces of data separated by tabs:
IPAddress Username Date Time Minutes
Where Date is in the format d-Mon-yy (day, Month as three letters, then year as two digits) and Time is listed in 24-hour time.
Read in the entire file and print out each record from April (do not print records from other months) in the format:
username m/d/yy hour:minuteAM/PM duration
Where m/d/yy is a date in the format month number, day number, year and the time is listed in 12-hour time (with AM/PM).
For example, the record:
82.85.127.184 dgounin4 19-Apr-18 13:26:16 13
Should be printed as something like:
dgounin4 4/19/18 1:26PM 13
At the top of the output, you should label the columns and the columns of data on each row should be lined up nicely. Your final output should look something like:
Name Date Time Minutes
chardwick0 4/9/18 5:54PM 1
dgounin4 4/19/18 1:26PM 13
cbridgewaterb 4/2/18 2:24AM 5
...(rest of April records)
Make sure that you read the right input file name. Capitalization counts!
Do not use a hard-coded path to a particular directory, like "C:\Stuff\WebLog.txt". Your code must open a file that is just called "WebLog.txt".
Do not submit the test file; I will use my own.
Here is a sample data file you can use during development. Note that this file has 100 lines, but when I test your program, I will not use this exact file. You cannot count on there always being exactly 100 records.
Hints
Make sure you can open the file and read something before trying to solve the whole problem. Get your copy of WebLog.txt stored in the folder with your code, then try to open it, read in the first string (195.32.239.235), and just print it out. Until you get that working, you shouldn't be worried about anything else.
Work your way to a final program. Maybe start by just handling one line. Get that working before you try to add a loop. And initially don't worry about chopping up what you read so you can print the final data, just read and print. Worry about adding code to chop up the strings you read one part at a time.
Remember, my test file will have a different number of lines.
You can read in something like 13:26:16 all as one big string, or as an int, a char (:), an int, a char (:), and another int.
If you need to turn a string into an int or a double, you can use this method:
string foo = "123";
int x = stoi(foo); //convert string to int
string bar = "123.5";
double y = stod(bar); //convert string to double
If you need to turn an int or double into a string use to_string()
int x = 100;
string s = to_string(x); //s now is "100"
Answers
A good example C++ code that parses the log file and extracts by the use of required information is given below
What is the C++ code?C++ is a widely regarded programming language for developing extensive applications due to its status as an object-oriented language. C++ builds upon and extends the capabilities of the C language.
Java is a programming language that has similarities with C++, so for the code given, Put WebLog.txt in the same directory as your C++ code file. The program reads the log file, checks if the record is from April, and prints the output. The Code assumes proper format & valid data in log file (WebLog.txt), no empty lines or whitespace.
Learn more about C++ code from
https://brainly.com/question/28959658
#SPJ1


In the QuickSort algorithm, the partition method we developed in class chose the start position for the pivot. We saw that this leads to worst case performance, O(n2), when the list is initially sorted. Try to improve your QuickSort by choosing the value at the middle, instead of the value at the start, for the pivot. Test your solution with the Driver you used for homework. Upload the output produced by the Driver, and your modified QuickSort source file.
====================================================
ORIGINAL
public class QuickSort> implements Sorter
{
List list;
public void sort(List list)
{
this.list = list;
qSort(0, list.size() -1);
}
public void qSort(int start, int end)
{
if(start >= end)
return;
int p = partition(start,end);
qSort(start, p-1);
qSort(p+1,end);
}
public int partition(int start,int end)
{
int p = start;
E pivot = list.get(p);
for(int i = start+1; i <= end; i++)
if(pivot.compareTo(list.get(i)) > 0)
{
list.set(p, list.get(i));
p++;
list.set(i,list.get(p));
}
list.set(p,pivot);
return p;
}
}
====================================================
Driver
public class DriverQuicksort
{ static final int MAX = 20;
public static void main(String[] args)
{
Random rand = new Random(); // random number generator
List numbers = new ArrayList ();
Sorter sorter;
sorter = new QuickSort ();
// Test QuickSort with random input
System.out.println ("Testing Quicksort");
for (int i=0; i
numbers.add (rand.nextInt(50)); // random int in [0..49]
System.out.println ("Before sorting:");
System.out.println (numbers);
sorter.sort (numbers );
System.out.println ("After sorting:");
System.out.println (numbers);
System.out.println ();
// Test QuickSort with ascending input
numbers.clear();
for (int i=0; i
numbers.add (i * 10); // initially in ascending order
System.out.println ("Before sorting:");
System.out.println (numbers);
sorter.sort ( numbers);
System.out.println ("After sorting:");
System.out.println (numbers);
System.out.println ();
// Test QuickSort with descendng input
numbers.clear();
for (int i=0; i
numbers.add (MAX-i); // initially in ascending order
System.out.println ("Before sorting:");
System.out.println (numbers);
sorter.sort ( numbers);
System.out.println ("After sorting:");
System.out.println (numbers);
System.out.println ();
numbers.clear();
numbers.add(75);
numbers.add(93);
numbers.add(35);
numbers.add(0);
numbers.add(75);
numbers.add(-2);
numbers.add(93);
numbers.add(4);
numbers.add(6);
numbers.add(76);
System.out.println ("Before sorting:");
System.out.println (numbers);
sorter.sort(numbers);
System.out.println ("After sorting:");
System.out.println (numbers);
System.out.println ();
}
}