Camille wants to buy a game online for her little sister’s birthday. She would like it to be a surprise but is worried that her sister will find a record of the purchase on the family computer. Camille can keep this a secret by:
A.
erasing her digital footprint.
B.
using only certain gaming sites.
C.
clearing her browser history.
D.
stopping advertisers from using her information.
Answers
Answer:
Clearing her browser history.
Explanation:
Related Questions
Which of the following statements about meta tags is TRUE?
A.Meta tags are a way of filtering items online so that you only see the items that connect to your interests.
B.Meta tags are large amounts of data that websites collect from their users. C.Meta tags are snippets of text that describe the content of a page or object. D.All of the above are true
Answers
Answer:
I guess c no. is the answer
orphan record example?
Answers
Answer:
If we delete record number 15 in a primary table, but there's still a related table with the value of 15, we end up with an orphaned record. Here, the related table contains a foreign key value that doesn't exist in the primary key field of the primary table. This has resulted in an “orphaned record”.
what do these two parts of the lift that go down a mine do
Answers
they transport miners and equipment down the mine
Please! I need help matching this.
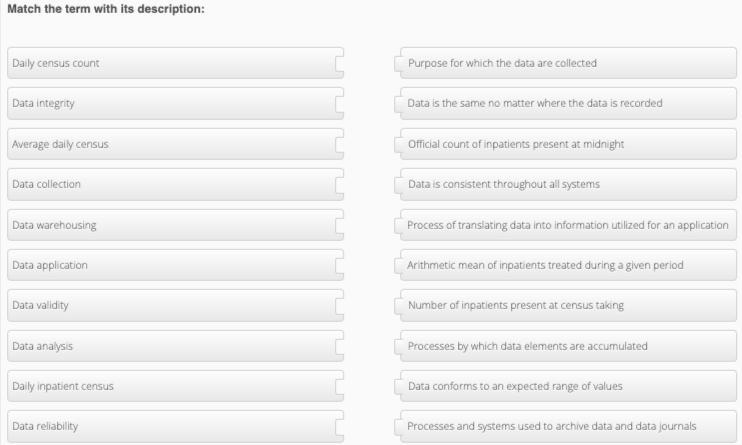
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
one name for a computer that has been hijacked or taken over by another is
Answers
A name for a computer that has been hijacked or taken over by another is "botnet.A botnet is a type of malware infection in which the attacker takes over several computers to form a network that can be controlled remotely by the attacker. It's a combination of the terms "robot" and "network."
The attacker can use the network to send spam emails, launch DDoS attacks, mine cryptocurrencies, and commit identity theft, among other nefarious activities. The computers in the botnet are referred to as "bots" or "zombies," and they are controlled by a central command-and-control (C&C) server. The attacker can issue commands to the bots via the C&C server, and the bots will follow them. Botnets are frequently utilized in cyber attacks and are one of the most significant cyber threats in the modern era.A 100-word answer on a name for a computer that has been hijacked or taken over by another is "botnet." A botnet is a type of malware infection in which the attacker takes over several computers to form a network that can be controlled remotely by the attacker.
To know more about network visit:
brainly.com/question/15060177
#SPJ11
Which symbol is at the beginning and end of a multiline comment block? &&& """ %%% ###
Answers
Answer:
#
Explanation:
I have notes on it we learned it in 8th
###
the other guy was correct.
You are concerned that if a private key is lost, all documents encrypted using your private key will be inaccessible. Which service should you use to solve this problem
Answers
Answer:
Key escrow.
Explanation:
Cyber security can be defined as preventive practice of protecting computers, software programs, electronic devices, networks, servers and data from potential theft, attack, damage, or unauthorized access by using a body of technology, frameworks, processes and network engineers.
In Cyber security, encryption is a form of cryptography and typically involves the process of converting or encoding informations in plaintext into a code, known as a ciphertext.
Typically, an information or data that has been encrypted can only be accessed and deciphered by an authorized user.
Hence, if a private key is lost, all documents encrypted using that private key will be inaccessible to the users. Thus, the service that can be used to solve this problem is a key escrow because the cryptographic (private) keys kept in an escrow system are protected and would not be released to anyone other than the original user (owner).
A key escrow can be defined as a data security method of storing very essential cryptographic keys.
Simply stated, key escrow involves a user entrusting his or her cryptographic key to a third party for storage.
As a standard, each cryptographic key stored or kept in an escrow system are directly linked to the respective users and are encrypted in order to prevent breach, theft or unauthorized access.
Write a program that takes the length and width of a rectangular yard and the length and width of a rectangular house situated in the yard. Your program should compute the time required to cut the grass at the rate of two square metres per minute using console
Answers
To create a program that calculates the time required to cut the grass in a rectangular yard, we need to follow a few simple steps. First, we need to prompt the user to input the length and width of the yard and the house situated in the yard.
Once we have the dimensions of the yard and house, we can calculate the area of the yard by multiplying the length and width. We then subtract the area of the house from the total yard area to get the area that needs to be cut.
Next, we can calculate the time required to cut the grass by dividing the area that needs to be cut by the rate of two square meters per minute.
We can then display the time required to cut the grass to the user using the console. The code for this program would involve using input statements to get the necessary dimensions, performing the calculations, and printing the result to the console using print statements. With this program, users can quickly and easily determine how long it will take to cut their grass.
You can learn more about the program at: brainly.com/question/14368396
#SPJ11
Why are volt guards necessary to connect with the computer? .:
Answers
the Method of
getting
information out
of the computer
Answers
Answer:
There's alot of ways to read data from a computer. One way is to create a file pointer and read the bytes of data starting at that adress.
Identify six specific skills that a computer software engineer is expected to demonstrate.
Answers
1.) Team work
2.) Disciple
3.). Creativity
4.) Attension To Deatil
5.) Time Mangament
Explanation:
Answer:
A computer programmer needs to demonstrate that they are:
1. A team player
2. Able to meet deadlines
3. Able to solve problems logically and efficiently
4. Able to create programs that fulfill their intended purpose
5. Able to be flexible (do many different types of jobs)
6. Able to adapt to new changes and be able to learn new skills
Explanation:
Computer programmers are tasked with creating software that works effectively with the given hardware and the people using it, and to do that, they have to be very skilled in many areas.
An article in the Transportation Research Part E Journal ["Arc Routing Problems to Restore Connectivity of a Road Network" (2016)] considered ways of re-establishing the connectivity of road networks after a natural disaster − earthquake. Estimates of the probabilities of a randomly chosen road being under light debris, moderate debris, and heavy debris conditions after different disaster magnitudes are shown in the following table. Disaster magnitude is equally likely to be low, moderate or high. Given that a road had light debris after an earthquake, what is the conditional probability that the disaster magnitude was low? Round your answer to two decimal places (e.g. 98.76). P=
Answers
The conditional probability that the disaster magnitude was low, given that a road had light debris after an earthquake, is approximately 0.33.
It applies Bayes' theorem to calculate the conditional probability of the disaster magnitude being low, given that a road had light debris after an earthquake.
Here's a summary of the solution:
Let P(A) be the probability that the disaster magnitude was low, and P(B) be the probability that a road has light debris.
P(A) = P(disaster magnitude is low) = 1/3 (since disaster magnitude is equally likely to be low, moderate, or high)
P(B) = P(Light debris) = 0.2 (given in the table)
The conditional probability P(A|B), which represents the probability of the disaster magnitude being low given that a road had light debris after an earthquake, is calculated using Bayes' theorem:
P(A|B) = P(B|A) * P(A) / P(B)
Where:
P(B|A) is the probability of light debris given that the disaster magnitude was low (from the table) = 0.2
Substituting the values:
P(A|B) = (0.2 * 1/3) / 0.2
P(A|B) = 0.33 (approximately)
Note: The solution provides a clear explanation of the steps involved and uses Bayes' theorem to calculate the required conditional probability.
Understanding the concept and applying the formula correctly is crucial in solving such probability problems.
To know more about magnitude visit:
https://brainly.com/question/31022175
#SPJ11
Transcribed image text: In a single formula, IF statements can be nested: • Once • Twice • Thrice • Many times Question 7 (1 point) The order for arguments in IF statements is: • Test, action if true, action if false • Action if true, action if false, test • Test, action if false, action if true • Action if false, test, action if true
•
Answers
IF statements can be nested many times means that one IF statement can be written inside another IF statement, and this nesting can continue with multiple levels of IF statements. Each nested IF statement serves as a condition that is evaluated based on the result of the outer IF statement, allowing for more complex logical evaluations and decision-making within a formula.
Option d is correct.
The order for arguments in IF statements is: Test, action if true, action if false means that the first argument is the logical test or condition that is evaluated. If the test is true, the second argument specifies the action or value to be returned. If the test is false, the third argument specifies the action or value to be returned in that case.
This order allows for conditional execution based on the result of the test, determining which action or value should be taken depending on the outcome.
Option a is correct.
Learn more about statements https://brainly.com/question/32478796
#SPJ11
What is a computer? What is computing? Define this in your own words and then check your understanding with a dictionary. Have you ever thought about how many computers are in your home? Have a look here and then brainstorm a list of items that could be considered a 'computer.' Next, group the items in the list. Think about how and why you are grouping the items. Select one type of computer group that you feel you could not live without and why. Share your list with groupings and the one group you would not live without and your rationale. PLEASE HELP
Answers
Answer:
A computer is a machine that accepts data as input, processes that data using programs, and outputs the processed data as information. Many computers can store and retrieve information using hard drives. Computers can be connected together to form networks, allowing connected computers to communicate with each other.
Computing is any activity that uses computers to manage, process, and communicate information
yes i have thought of it before.
central processing unit (CPU), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.
we can not live without motherboard or any of these .It is like a human without bones even one part missing would be dangerous.
Explanation:
In design-by-contract, the code responsible for making sure the precondition (requires clause) is true when a method is called is:
Answers
The client code or the calling code is responsible for ensuring that the precondition (requires clause) is true in design-by-contract.
In design-by-contract, the responsibility of ensuring that the precondition (requires clause) is true lies with the client code or the calling code. The design-by-contract approach emphasizes the mutual obligations and expectations between the code providing a service (the supplier) and the code using that service (the client). The supplier specifies the preconditions that must be satisfied before the method is called, and the client is responsible for fulfilling these preconditions. If the client fails to meet the preconditions, it violates the contract, and the behavior of the method is not guaranteed. This approach promotes clear communication and helps in building reliable and robust software systems.
Learn more about calling code here:
https://brainly.com/question/29308166
#SPJ11
how do I fix this tech problem I'm having when I press ctrl it mute my sound and when I press the windows key on my keyboard it turns the pc off how to fix this issue
this was not happening yesterday please help me
Answers
Answer:
You can try reinstalling your keyboard drivers.
You can do this by right clicking the windows icon in the bottom left and click on Device Manager, find the keyboard tab and expand it, right click on your keyboard driver (it will be the same name as your keyboard, or it might have a generic name), then right click it, and press uninstall, then restart your computer to see if it worked.
If that didn't work, you can try reinstalling the USB controller drivers.
You go into device manager just like before, but find the 'Universal Serial Bus controllers' tab and uninstall the devices there, then restart.
If neither of those work, you sadly might have to get another keyboard.
Hope this helps
internet-based development treats the traditional systems development environment as the platform, rather than just a communication channel
Answers
For internet-based developmnent many applications require substantial desktop computing power and resources, so the correct answer is option (c).
As a result, we can observe that a standard systems development environment involves the usage of a significant portion of the desktop's processing power and resources, both of which are being utilised by many apps simultaneously.
The conventional systems development process is available to any organisation that needs to create a system. To achieve some outcomes and produce the needed system, system designers and developers must follow and finish a series of steps in these techniques.
The planning, system analysis, system design, development, implementation, integration, testing, and operations and maintenance phases of the systems development life cycle are included.
Learn more about internet-based development:
https://brainly.com/question/15100546
#SPJ4
The complete question is ''Which of the following is true of a traditional systems development environment? a. Systems are developed and delivered in an Internet-based framework such as .NET or WebSphere. b. Systems are easily scalable and can run on multiple hardware environments. c. Many applications require substantial desktop computing power and resources. d. Internet-based development treats the traditional systems development environment as the platform, rather than just a communication channel''.
Select all the correct answers.
Which statements are true regarding system and application software?
System software consists of only the OS and application software.
A program is a set of instructions that helps the user understand the functioning of the computer.
An OS acts as an interface between the hardware and the user.
Application software allows users
perform various tasks.
Disk cleaner, resource monitor, etc. are all examples of application software.
Answers
Answer:
all the points are correct apart from the first one..
User can fill numbers in a column by using _______ command, ________ is a built-in formula in Excel to do calculations, Entering data into a cell means to _______ data into a cell, The MIN function displays the ________ value in a given list of values
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This question is about fill-in-the-blank. The correct options in these fill-in-the-blanks are given below:
User can fill numbers in a column by using Down, Right, Up, Left, Series and Justify command
You can use these commands to fill numbers in columns. You can find these commands in the HOME tab under the Editing group of commands.
AutoSum is a built-in formula in Excel to do calculations
Autosum is a built-in formula that helps you to perform calculations, such as to calculate sum, average, and to find the minimum and maximum value. You can find the AutoSum command in the Home tab under the Editing group of commands.
Entering data into a cell means to put/insert data into a cell.
The MIN function displays the minimum value in a given list of values.
You use the MIN() function to display the minimum value in a given list of values or in the columns.
HELP PLS!!! In a presentation, what is layout?
Answers

Months Write a program that will ask the user for a month as input in numeric format and print out the name of the month. Here is a sample run: Enter the Month: 9 It is september!
Answers
The program prompts the user to enter a month in numeric format and then prints the corresponding name of the month. For example, if the user enters 9, the program will output "It is September!" as the result.
To implement this program in Python, we can define a dictionary that maps numeric month values to their corresponding names. The program will ask the user to input a numeric month value. It will then retrieve the corresponding month name from the dictionary and print it along with a message. Here's an example implementation:
def print_month_name():
month_dict = {
1: "January",
2: "February",
3: "March",
4: "April",
5: "May",
6: "June",
7: "July",
8: "August",
9: "September",
10: "October",
11: "November",
12: "December"
}
month_number = int(input("Enter the Month: "))
if month_number in month_dict:
month_name = month_dict[month_number]
print("It is", month_name + "!")
else:
print("Invalid month number.")
print_month_name()
In this program, the dictionary month_dict maps numeric month values (keys) to their corresponding month names (values). The program prompts the user to enter a month number. If the entered number exists as a key in the dictionary, the corresponding month name is retrieved and printed along with the message "It is [month name]!". If the entered number is not found in the dictionary, an error message is displayed.
Learn more about Python here: https://brainly.com/question/30427047
#SPJ11
Can someone please type a code that makes a house in python and turtle graphics i need help
Answers
Answer:
import turtle
turtle.speed(2)
#shape
turtle.forward(100)
turtle.left(90)
turtle.forward(100)
turtle.left(45)
turtle.forward(100)
turtle.left(90)
turtle.forward(100)
turtle.left(45)
turtle.forward(100)
turtle.left(90)
turtle.forward(100)
#door
turtle.left(90)
turtle.forward(50)
turtle.left(90)
turtle.forward(25)
turtle.left(90)
turtle.forward(50)
#windows
turtle.penup()
turtle.right(90)
turtle.forward(20)
turtle.right(90)
turtle.forward(20)
turtle.pendown()
turtle.forward(25)
turtle.left(90)
turtle.forward(40)
turtle.left(90)
turtle.forward(25)
turtle.left(90)
turtle.forward(40)
Explanation:
here :)
Many active elements fire at almost the same time in phased array scanner.
a. true
b. false
Answers
The statement that is Many active elements fire at almost the same time in phased array scanner is false because there is only one active element in a mechanical scanner.
Each element has a width between 100 and 200, corresponding to a wavelength's worth. False or True To produce a two-dimensional image, phased array transducer devices in all applications direct ultrasonic pulses in numerous directions.
An electronic component that provides power to a circuit is called an active component. Electron flow can be electrically controlled by active components (i.e. the flow of charge). At least one active component is required in every electrical circuit.
Because it will have internal energy at the moment of manufacture, a diode is an active element. Therefore, active elements are those that have internal energy at the moment of manufacturing, such as all types of sources, diodes, transistors, and SCR family, among others.
Learn more about active elements:
https://brainly.com/question/3875001
#SPJ4
True or False, A variable can be called or referenced before it has been defined.
Answers
Answer:
false?
Explanation:
im 99% sure
in most interfaces, output items appear in label controls, because users should not be able to edit the value of an output item while an application is running.
Answers
In most interfaces, output items appear in label controls, because users should not be able to edit the value of an output item while an application is running is a true statement.
What is Label Control?A label is known to be a form of a graphical control tool that is often used to show text on a form.
It is known to be used a lot in a static control. It is on that do not have no interactivity. A label is one that is often seen as a tool that is used to know a close by text box or other kinds of widget.
Windows Forms Label controls are said to be tools or elements that are often used to show text or images that is one a person is unable to edit.
Note that they are said to be tool that are often used to know objects on a form so as to give a description of what a certain control will act as.
Therefore, in most interfaces, output items appear in label controls, because users should not be able to edit the value of an output item while an application is running is a true statement.
Learn more about label controls from
https://brainly.com/question/14327891
#SPJ1
in most interfaces, output items appear in label controls, because users should not be able to edit the value of an output item while an application is running.True/false
Your team is about to introduce and lunch a product never seen before in Barbados, an Ultrasonic Pest Repellent, that repels pests (small insects) while causing no harm to your pets, yourself, or any animals in range.
1) In your own word, state the market objectives your team wishes to attain with the lunch of this new product. Ensure your objective are written clearly and S.M.A.R.T.
ii) Identify any concerns that may affect the completion of the objective.
Answers
Market Objectives are Increase Market Share, Generate Revenue and Build Brand Awareness. Concerns are as follows Market Acceptance, Competitive Landscape and Regulatory Compliance.
i) Market Objectives:
1. Increase Market Share: Increase the market share of the Ultrasonic Pest Repellent in Barbados by 20% within the first year of launch.
(Specific: Increase market share, Measurable: 20% increase, Achievable: Based on market demand and competition, Relevant: Aligns with the product launch, Time-bound: Within the first year)
2. Generate Revenue: Achieve a sales target of $100,000 in the first six months after product launch.
(Specific: Achieve sales target, Measurable: $100,000, Achievable: Based on market potential and pricing strategy, Relevant: Revenue generation, Time-bound: Within the first six months)
3. Build Brand Awareness: Increase brand recognition and awareness of the Ultrasonic Pest Repellent among the target audience by implementing a comprehensive marketing campaign, resulting in 75% brand recognition within the first year.
(Specific: Increase brand awareness, Measurable: 75% brand recognition, Achievable: Through effective marketing strategies, Relevant: Brand building, Time-bound: Within the first year)
ii) Concerns:
1. Market Acceptance: There may be concerns regarding the acceptance and adoption of the Ultrasonic Pest Repellent among consumers in Barbados. Awareness and education campaigns may be required to overcome skepticism and build trust in the product's effectiveness.
2. Competitive Landscape: Competitors already offering pest control solutions may pose a challenge. It is important to differentiate the Ultrasonic Pest Repellent and effectively communicate its unique selling points to gain a competitive advantage.
3. Regulatory Compliance: Ensuring compliance with local regulations and safety standards regarding the sale and usage of pest control products is crucial. Failure to meet regulatory requirements could result in delays or restrictions on product launch.
Learn more about marketing campaign :
https://brainly.com/question/30237897
#SPJ11
Which of the following should you use if you want to get an opinion on something from your website visitors in the form of a paragraph to be typed into one of your forms?
Answers
To get an opinion from website visitors in the form of a paragraph to be typed into a form, you should use a text input field or a textarea input field.
To gather an opinion from website visitors in the form of a paragraph, you can provide a text input field or a textarea input field in your form. Both options allow users to enter multiple lines of text, including paragraphs, to express their opinions. A text input field is suitable when you expect a shorter response or a single line of text. It is commonly used for capturing names, email addresses, or short comments. On the other hand, a textarea input field is more appropriate when you want users to provide longer responses, such as paragraphs or detailed explanations. The textarea input field provides a larger text box that can accommodate multiple lines of text, allowing visitors to type their opinions in a more comfortable and spacious format.
By including a text input field or a textarea input field in your form, you can effectively collect opinions from website visitors in the form of paragraphs or longer responses.
Learn more about format here: https://brainly.com/question/13308068
#SPJ11
What three key sequence will bring up the task manager?
Answers
Answer:
ctrl-shift-esc
Explanation:
A trackerball is a pointing device
Answers
Answer:
nice
Explanation:
How does making a call differ when using a cell phone public phon box? consider the kinds of user, types of activity and context of use
Answers
Answer:
Explanation:
Making A Call:Public Cell Phone:
A public telephone box is a fixed and noncompact gadget that is associated by the means of electrical wires and is utilized for correspondence by making telephone calls. For settling on the telephone decision, both the telephones ought to be working appropriately and the wires interfacing both the cases ought to likewise be working appropriately without any harm. The voice is communicated starting with one gadget then onto the next as electrical signals pass across the wires.
Cell Phones:
A cellphone is a mobile and versatile gadget whose essential capacity and purpose are to build up correspondence by settling on telephone decisions. Dissimilar to the public telephone box, we don't utilize any wires, rather the correspondence is finished by the methods for a sim card in the telephone which is answerable for building up correspondence between the cellphone and the relating network tower. For the correspondence to occur or call to happen the sim in both the mobile phones should be working appropriately and should be associated with their separate or closest organization towers. The signs are moved from the gadgets to the organization towers which will be additionally moved to wanted cellphones and the other way around or vice versa.
Considering the device design based on:
a) The kinds of User:
Individuals who don't utilize the telephone every now and again and talk for long hours sometimes when they use the telephone, for the most part, lean toward public telephone box since, supposing that you have a mobile cell phone and assuming you don't utilize it much, it is simply misused of cost. Be that as it may, in wireless the expenses are fixed upon the measure of time utilized for settling on telephone call decisions.
b) Type of activity:
Public telephone boxes can be utilized distinctly for settling on telephone decisions whereas personal digital assistance (PDAs, i.e cell phones) can be utilized to settle on telephone decisions, access the web, send instant messages, share pictures and video, and numerous different things.
c) Context of usage:
The context of usage whereby public telephone box is utilized when less often calls are made and the correspondence at whatever point made is for longer periods then public telephone boxes are utilized and furthermore individuals who don't wish to carry and move about with a cell phone and charge each an ideal opportunity to keep up the cell phones for the most part incline toward public telephone box. Individuals who are open to carrying the cell phones and have no issues charging the mobile and who need to settle on telephone decisions oftentimes buy the idea of cell phones over public telephone boxes.