The data structure used for file directory is called
Select one
a. process table
b. mount table
C. hash table
d file table
Answers
Data structures used for file directories typically have a hierarchical tree structure, referred to as a directory structure. The tree has a root directory, and every file in that system has a unique path.
The simplest method of implementing a directory is to use a linear list of file names with pointers to the data blocks. But another way that you can format a file directory is by using a hash table. With this method, the linear list stores the directory entries, but a hash data structure is also used. The hash table takes a value computed from the file name and return the pointer to the file name any linear list.
So I think it’s C. But I’m not 100% sure.
I hope that helps.
Related Questions
What are the disadvantages of using folders
Answers
Answer:
√ folders can cause some inconvenience situation...
√ The decompress / compress action takes time.
√ When you double-click on a file inside a “folder”, what really happens is the file gets extracted to a temporary folder.
heres one:
when you delete a folder, he stuff inside gets deleted, and there isnt a way to get it back.
Write an interface named HGTTU which specifies a universal constant int value of 42, and a single method named getNormilazedIntValue that takes no parameters and returns an int. The purpose of which is to get the value of the object's int instance variable, add the universal constant and return the result.Next, write a second named myInt which is composed of a single int instance variable (and the minimal set of customary methods) that implements HGTTU.
Answers
Answer:
Hope this helps.
//HGTTU.java
public interface HGTTU {
int universalConstant = 42;
public int getNormilazedIntValue();
}
//MyInt.java
public class MyInt implements HGTTU {
int instanceFiled;
Override
public int getNormilazedIntValue() {
return instanceFiled+universalConstant;
}
}
Explanation:
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
If you can photoshop please text me i need help for my digital media class 7862381441
Answers
Answer:
I don't know what that is but what type of work you need help with
have a good day :)
Explanation:
What does the acronym SMART stand for
Answers
Specific, Measurable, Achievable, Relevant, Time-bound
Assume the variable s is a String and index is an int. Write an if-else statement that assigns 100 to index if the value of s would come between "mortgage" and "mortuary" in the dictionary. Otherwise, assign 0 to index.
Answers
Using the knowledge in computational language in python it is possible to write a code that Assume the variable s is a String and index is an int.
Writting the code:Assume the variable s is a String
and index is an int
an if-else statement that assigns 100 to index
if the value of s would come between "mortgage" and "mortuary" in the dictionary
Otherwise, assign 0 to index
is
if(s.compareTo("mortgage")>0 && s.compareTo("mortuary")<0)
{
index = 100;
}
else
{
index = 0;
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

1. What are the two main functions of an operating system?
Answers
Answer:
(1) manage the computer's resources, such as the central processing unit, memory, disk drives, and printers, (2) establish a user interface, and (3) execute and provide services for applications software.
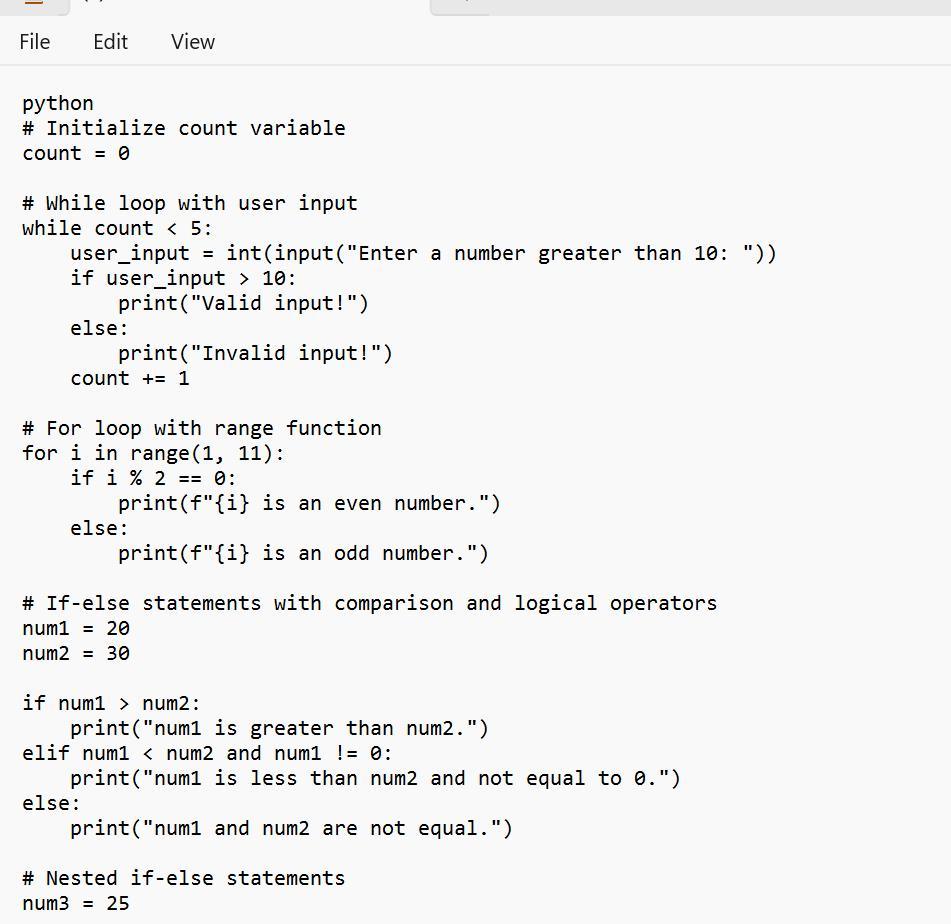
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

Where does blood travel when it leaves the right ventricle of the heart
Answers
Please rewrite and correct the following sentences:
1. Their dog ran away last night, and now their looking for him.
2. The company lost there biggest client last year.
3. Who is you going to the party with tonight?
4. The museums is open on Saturdays from 10am to 5pm.
5. Neither the boys or their father have any idea where the car keys is.
Answers
1.Their dog ran away last night, and now they are looking for him.
2. Their company lost their biggest client last year.
3. With whom you are going to the party with tonight?
4. The museums are open on saturdays from 10 am to pm.
5. Fathers or Boys no one knows where the car keys are?
Thus, English has three tenses: past, present, and future. When writing about the past, we employ the past tense.
When writing about facts, opinions, or regular occurrences, we employ the present tense. To write about upcoming events, we utilize the future tense. Each of those tenses has additional characteristics, but we won't cover them in this session.
It's crucial to maintain the same tense throughout a writing endeavor after you've decided on one. To communicate yourself clearly, you may need to switch up the tense from time to time.
Thus, English has three tenses: past, present, and future. When writing about the past, we employ the past tense.
Learn more about Tenses, refer to the link:
https://brainly.com/question/29757932
#SPJ1
When Jenna borrows her dad's office chair, it's too big for her, so her feet dangle and don't reach the floor—which can cause what?
A: eye strain
B: carpal tunnel syndrome
C: a repetitive motion injury
D: slouching posture
Answers
Answer:
D
Explanation:
Answer:
B: carpal tunnel syndrome
Explanation:
YYou have to have your hand on the ddesk.
what are the 6 fastest expansion slots?
Answers
The six fastest expansion slots are:
PCI Express 4.0
PCI Express 5.0
Thunderbolt 4
USB 4
NVMe M.2
U.2
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
Advantages and disadvantages of isolated I/O
Answers
Answer:
Input and output devices (I/O) are the parts of a computer system, such as the keyboard or the modem, that send or receive information to and from the computer's processors. In memory-mapped I/O systems, I/O devices use part of the computer's memory as the address for transmitting messages. In computers with isolated-memory systems, I/O and memory have different addresses.
I/O
Computer systems can map I/O to an address in the memory banks because the process of messaging I/O devices is similar to exchanging data with computer memory. The same bus -- the electronic pathway for transmitting information to and from the processors -- serves to access both memory and input and output devices. One disadvantage to isolated memory is that memory-map systems are simpler for the bus, as it uses the same set of addresses for I/O and memory operations.
Explanation:
hope that this helps
Infringement Less than 13km/h over the speed limit At least 13km/h but not more than 20km/h over the speed limit More than 20km/h but not more than 30km/h over the speed limit More than 30km/h but not more than 40km/h over the speed limit More than 40km/h over the speed limit Penalty amount $177 $266 $444 $622 $1.245 Demerit points 1 3 4 6 8 Note: the way the government website has written this (and we've copied it) is NOT efficient in terms of decision structures. This written for each condition to stand alone (if, if, if) but we can tell its mutually exclusive and so know a better tool for the job don Avoid a 6-month suspension by writing a program to ask for the user's: • speed and the • speed limit
program in python?
Answers
The example of the program in Python to help one to calculate the penalty amount as well as the demerit points based on the speed and speed limit provided by the user is given in the code below
What is the program?python
def calculate_penalty(speed, speed_limit):
penalty_amount = 0
demerit_points = 0
if speed <= speed_limit:
return penalty_amount, demerit_points
overspeed = speed - speed_limit
if overspeed <= 13:
penalty_amount = 177
demerit_points = 1
elif overspeed <= 20:
penalty_amount = 266
demerit_points = 3
elif overspeed <= 30:
penalty_amount = 444
demerit_points = 4
elif overspeed <= 40:
penalty_amount = 622
demerit_points = 6
else:
penalty_amount = 1245
demerit_points = 8
return penalty_amount, demerit_points
# Get user input
speed = int(input("Enter the recorded speed (in km/h): "))
speed_limit = int(input("Enter the speed limit (in km/h): "))
# Calculate penalty and demerit points
penalty, points = calculate_penalty(speed, speed_limit)
# Display the results
print("Penalty amount: $", penalty)
print("Demerit points: ", points)
Read more about python here:
https://brainly.com/question/30113981
#SPJ1
Probability of theft in an area is 0.03 with expected loss of 20% or 30% of things with probabilities 0.55 and 0.45. Insurance policy from A costs $150 pa with 100% repayment. Policy with B, costs $100 pa and first $500 of any loss has to be paid by the owner. Which data mining technique can be used to choose the policy?
Answers
Answer:
Decision trees
Explanation:
Decision trees mainly include categorization and estimation. It is often used as a measure of selection. This also encourages the usage and choice of particular data within the overall structure.
In the given situation, we should choose Policy A has cost $150 as it has 100% repayment while on the other hand Policy B has cost $100 and the first $500 of loss would be paid by the owner
So for choosing the policy, we use the decision tree data mining technique as we have to take the decision with respect to minimizing the cost
Data mining technique which can be used to choose the policy is decision tree.
The data mining technique that can be used are as follows,
Categorization and estimate are the two major functions of decision trees,Decision tree frequently used as a selection criterion. This promotes the use and selection of specific data within the broader framework.According to given data,
We should pick Policy A, which costs $150 and has a 100% payback rate.Whereas, the owner would be responsible for the first $500 of loss under Policy B, which costs $100.Here choosing the correct policy, decision tree is used.
Learn more: brainly.com/question/15247828
Your friend Brady says he doesn’t want to play Mass Effect, a popular role-playing game, because he already knows how it ends. What could you say to convince him to play the game again?
A.
“Even though Mass Effect has the same story every time, you should still play it again because it’s a classic game.”
B.
“You should still play Mass Effect because I’m your friend and I want to play it.”
C.
“You should play Mass Effect again because this kind of game allows you to shape the story, so each playthrough can be different.”
D.
“Even though Mass Effect is a predictable game with the same ending every time, you should still play it because it will help you develop your problem-solving skills.”
Answers
Answer:
c
Explanation:
i have played mass effect
Please Help I'm Very Stressed, my school is holding a competition of making the best video game and the winner gets 1000$ and I really want 1000$, the problem is that I can't make any good games or don't have any ideas for anything the game has to have lore and a plot and characters and it's really stressing so please help me get a idea or something easy enough to make
Answers
Answer:
make a game like fun run
Explanation:
Answer:
u should make an competive game where people battle each other sorry if i cant spell good its cause im rushing
Explanation:
what is computer hardware / software
Answers
Answer: Computer hardware is any physical device used in or with your machine, like for example, a mouse, or a keyboard. Computer software is a collection of programming code installed on your computer's hard drive it can process billions of data and inputs through this.
Hope this helps!
If cell A2 contains "Today is Monday," the result of the function =LEN(A2) would be __________. Fill in the blank space.
Excel Quiz.
Answers
If cell A2 includes the phrase "Today is Monday," the result of the function =LEN(A2) would be 15, which is the number of characters in the cell.
How can I figure out how many characters there are in Excel?Type =LEN(cell) in the formula bar and hit Enter to invoke the function. In many instances, cell refers to the cell that you want to count, like B1. Enter the formula, then copy and paste it into further cells to count the characters in each cell.
What does Len have to offer?A number is returned by LEN after it counts the characters in the text, including spaces and punctuation. LEN is set to zero if text is an empty string ("") or a reference to an empty cell.
To know more about cell visit:-
https://brainly.com/question/8029562
#SPJ1
This is science I just couldn’t find it

Answers
Answer:
69
Explanation:
It is 69 because it is the most for that degree.
PROJECT: RESEARCHING THE HISTORY OF THE INTERNET
The Internet has had a profound effect on how we conduct business and our personal lives. Understanding a bit about its history is an important step to understanding how it changed the lives of people everywhere.
Using the Internet, books, and interviews with subject matter experts (with permission from your teacher), research one of the technological changes that enabled the Internet to exist as it does today. This may be something like TCP/IP, the World Wide Web, or how e-mail works. Look at what led to the change (research, social or business issues, etc.) and how that technology has advanced since it was invented.
Write a research paper of at least 2, 000 words discussing this technology. Make sure to address the technology’s development, history, and how it impacts the Internet and users today. Write in narrative prose, and include a small number of bullet points if it will help illustrate a concept. It is not necessary to use footnotes or endnotes, but make sure to cite all your sources at the end of the paper. Use at least five different sources.
Submission Requirements
Use standard English and write full phrases or sentences. Do not use texting abbreviations or other shortcuts.
Make any tables, charts, or screen shots neat and well organized.
Make the information easy to understand.
Answers
It can be used to send messages, links, images and files, essentially everyone on the planet who uses computers will use e-mail. It powers business and connects families together across continents, and the best part of all is that it is essentially free. People use e-mail on personal computers, mobile phones, tablets, even on ‘smart’ televisions!
Every e-mail address has an inbox. This is where new messages are deposited. An e-mail message has a status called “unread” which disappears after the e-mail has been opened. A typical e-mail inbox will also have a ‘Sent’ folder for viewing messages that you have sent in the past. It also will have an ‘Outgoing’ folder, where messages stay until they have been fully transmitted. It is also common to have a ‘Drafts’ folder for messages that were started but never sent, and a ‘Spam’ folder, where unwanted marketing messages will usually be directed. You can of course setup your own folders and sort your e-mails however you like .
You have a Direct Mapped cache with following parameters
Cache Data Size (C) 128
Block Size (b) 4
After partitioning the address, which is 32 bits big, into Tag, Set, and Offset, how many bits will be in each field?
Answers
A smart phone is a technology used in businesses.
True or False
Answers
Answer:
True
Explanation:
Smart phones and computers are technologies used in business all the time
A pitch can help convey important information in pre-production for it to receive the green light into production. True or false
Answers
Submit your design an informative computer safety brochure for a specific cybercrime that targets an audience of your choice.
Answers
A poll predicted that 68% of voters plan to vote for the current mayor in the upcoming election. If the poll had a standard deviation of 4%, what is the margin for error?
Answers
what is the meaning of compiler
Answers
Answer:
in computing it means a program that converts instructions into a machine-code or lower-level form so that they can be read and executed by a computer.
Which tool would you use if you wanted to arrange a list of words in alphabetical order?
A. Sort ←
B. Format Painter
C. Conditional Formatting
D. Arrange
Answers
A
Explanation:
You can quickly and easily sort the text of a bulleted or numbered list in Microsoft's popular Word program so that your text is in alphabetical order. In the Sort Text dialog box, under Sort by, click Paragraphs and Text, and then click either Ascending or Descending.
NEED HELP 100 POINTS FOR CORRECT ANSWER
In the application activity, you had to choose between two options, Scenario 1: Building a Website or Scenario 2: Printing Band Posters.
Review the feedback you got for your answer, then enter your revised answer here.
Answers
Answer: I think number 1 would be best
Explanation: Number 1 because you would get noticed more often so people can but your products
Hope this helps :)